Evacuations from High-Risk Locations Call +44 (0)1202 308810 or Contact Us →
Corporate Espionage: The Hidden Risks for Business Travellers

How to Protect Business Travellers from Data Theft
Business Travellers Face Growing Espionage Threats
Business travellers, especially those in sensitive industries, face escalating risks of corporate espionage, surveillance, and hacking. With the high value of intellectual property (IP) and business intelligence (BI), both state and non-state actors target travellers to access confidential data for a competitive edge.
The Financial Toll of Corporate Espionage
The FBI estimated in 2015 that espionage costs US companies about USD 300 billion annually. By 2021, corporate espionage cases, especially linked to foreign states like China, had surged. At least 23 nations target US businesses for proprietary information, though the true number is likely higher.
Why Business Travellers Are at High Risk for Espionage
In the past, stealing IP and BI was primarily conducted by rogue insiders. However, with the proliferation of smartphones, other portable devices and the expanding storage of data on cloud networks, malicious actors are increasingly able to access valuable information without leaving a trace, through a variety of both simple and sophisticated methods.
Heightened Risks for Business Travellers
Business travellers are particularly vulnerable to espionage in high-risk locations. Airports, hotels, and unfamiliar environments increase the risk of communication interception and data theft, especially when fatigue or unfamiliarity with local conditions come into play.
Country-Specific Insights
China: Advanced industrial espionage tactics and their impact on foreign businesses.
Hong Kong: Risks of commercial espionage post-National Security Law and implications for business.
Russia: Hybrid warfare tactics targeting Western companies, emphasising technology theft and surveillance.
France: Economic espionage strategies and collaboration between state intelligence and private sectors.
Corporate Covert Tactics: Corporate tactics for competitive advantage.
Target Industries at Risk of Corporate Espionage
The most targeted industries of economic espionage are those that have significant strategic and economic importance. The defence and aerospace sectors are prime targets due to their essential role in national security and access to sensitive, classified information.
Other sectors such as advanced engineering, bioengineering, nanotechnology, semiconductors, pharmaceuticals, energy, artificial intelligence (AI) and telecommunications are also at a higher risk due to their strategic value.
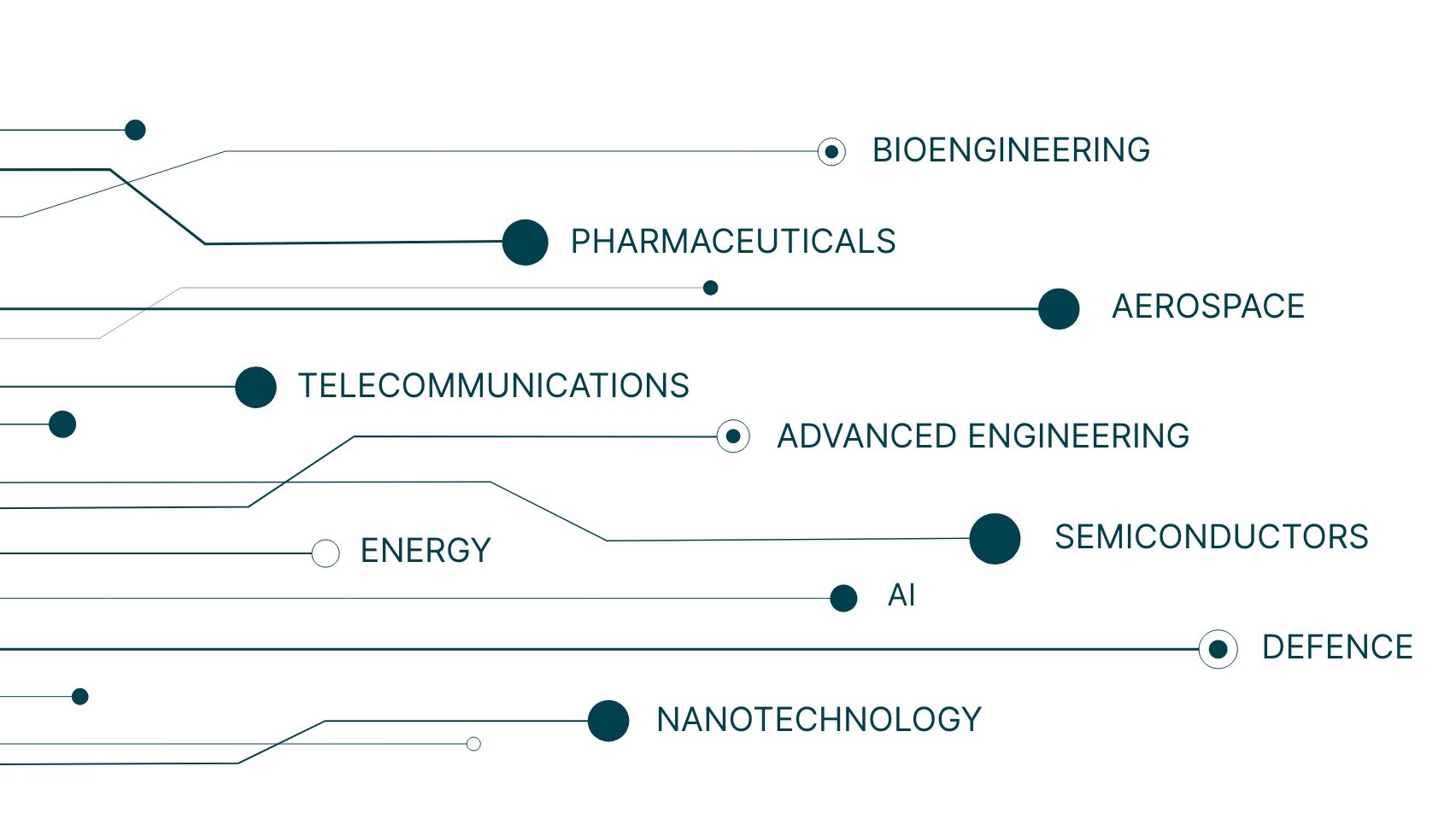
Espionage Hotspots: Key Industries at Risk
However, while such sensitive industries are more at risk of being targeted, all business travellers could be potentially impacted by economic espionage and surveillance. Criminals, rival companies and state actors can all stand to gain by accessing confidential business information. Individuals or companies with access to information with less intelligence value may also be targeted through indiscriminate forms of surveillance when travelling to high-risk destinations.
How Can Corporate Espionage in China Affect Your Business Strategy?
In recent years, China has been at the center of an escalating wave of corporate espionage, with 80% of U.S. economic espionage prosecutions linked to Chinese actors, according to the Department of Justice. The Chinese government prioritises advancements in key sectors to stay competitive, with both state and private entities benefiting from the theft of intellectual property (IP) and other sensitive information.
New laws in China, such as the National Counter-Espionage Law and the Law on the Guarding of State Secrets, have expanded government powers, allowing authorities to raid foreign businesses and access data under vague pretenses. Business travellers and companies operating in China face increasing risks, as even routine visits can result in the confiscation of devices or the misuse of private information.
Companies may remain unaware of cyber intrusions until it’s too late, as demonstrated by high-profile cases involving foreign organisations. The rise of espionage has forced many large firms to isolate their Chinese data from global systems to mitigate risk.
The Changing Nature of Corporate Espionage Risks in Hong Kong
Hong Kong has long been a global business hub, thriving under the “one country, two systems” framework. However, since the 2019 protests and the subsequent enforcement of the National Security Law, the region’s legal and business landscape has shifted dramatically. The law has expanded the government’s authority to monitor, access, and potentially misuse sensitive information, even from foreign nationals.
As the threat of corporate espionage rises, many global firms, particularly in high-tech industries like aerospace and semiconductors, have implemented strict security measures. It’s now common for audit and consultancy firms to advise staff to use burner phones when conducting business in Hong Kong.
Russia’s Espionage Tactics: Increasing Risks for Western Businesses
Russia has long engaged in corporate espionage as part of its hybrid warfare strategy, seeking to gain a technological and economic edge over its Western rivals. Following the 2022 invasion of Ukraine, this threat has only escalated, as sanctions and international isolation drive Russia to intensify its efforts to acquire foreign technology.
Russia’s surveillance capabilities are formidable, with systems like the Operative Search Measures (SORM) allowing state agencies to intercept communications and track internet activity with ease. Business travellers face a heightened risk, with U.S. citizens reporting that their electronic devices were searched upon entering Russia, and specialised Russian software capable of bypassing standard security measures.
Moscow has openly acknowledged the use of IP and patent theft for strategic purposes, going as far as to allow Russian companies to exploit foreign patents without compensation.
Is France’s Economic Espionage a Serious Challenge for Global Businesses?
While often associated with authoritarian regimes, economic espionage is not exclusive to them. France has a long history of using state intelligence to boost its private sector’s competitiveness. Since the Cold War, French intelligence has been involved in espionage activities targeting foreign businesses, especially in sectors like aviation and telecommunications. One notorious case involved bugging Air France’s first-class seats to spy on foreign executives.
Although counterterrorism has become a key focus for French intelligence in recent years, state-sponsored espionage continues, now with a stronger emphasis on cyber operations. France is listed alongside Russia and Israel as one of the leading cyberespionage actors targeting international businesses. The Directorate-General for External Security (DGSE) plays a central role in these efforts, with its Economic Security Service (ESS) dedicated to public-private intelligence collaboration.
Recent incidents, such as the 2016 detainment of a Franco-Swiss businessman by DGSE agents, highlight the ongoing risks for businesses operating in or traveling to France.
Corporate Espionage: How Companies Use Covert Tactics to Gain an Edge
Corporate espionage is not just the domain of state actors; businesses themselves frequently engage in covert operations to gain a competitive advantage. Companies often employ advanced techniques and substantial resources to gather sensitive information, mimicking the methods of national intelligence agencies.
One high-profile example occurred in 2017 when Uber’s Strategic Services Group (SSG) was accused of spying on rival Waymo to steal self-driving technology secrets. Allegations included tailing and videotaping Waymo vehicles, infiltrating competitor events, and using cyber operations to access proprietary data.
Another notable case involved GlaxoSmithKline (GSK), which hired a British private investigator in China to gather intelligence. The investigator was later sentenced to prison for illegal activities, revealing how far some companies will go to protect their interests.
How Can Business Travellers Protect Themselves from Espionage Threats?
Business travellers are prime targets for espionage, and both state and non-state actors employ a variety of covert tactics to extract sensitive information. From the moment you arrive in a foreign country to the time you leave, your personal and professional data is at risk. Here’s an overview of some of the most common methods used by malicious actors to spy on business travellers:
Airport Espionage
- Device Seizure and Data Extraction: Upon entering a country, border security can confiscate your electronic devices. Advanced tools can quickly bypass encryption and access passwords, allowing authorities to extract large amounts of sensitive data.
Hotel Espionage
- Bugging and Surveillance Devices: Hidden microphones and cameras can be placed in everyday objects such as smoke detectors, light fixtures, and even phone chargers. These devices can be pre-installed or planted once a target is identified.
- Room Intrusion: Your hotel room can be accessed while you’re away, either to search your belongings, plant bugs, or install malware on your devices via tampered phone chargers or USB ports.
Anywhere You Go
- Remote Interception: Authorities can legally monitor your communications or use Stingrays to intercept phone calls and data by mimicking cell towers. Fake Wi-Fi networks and Bluetooth vulnerabilities can also be exploited to access your devices.
- Physical Surveillance: Covert operatives may follow you, monitor your meetings, and eavesdrop on your conversations to gather valuable intelligence.
- Elicitation: Engaging in casual conversation at a bar or business event? Trained operatives may subtly extract sensitive information without you even realising it.
- Honey Traps: Be wary of personal or sexual relationships that seem too convenient. Intelligence agencies use honey traps to gain trust, gather information, or blackmail targets into cooperating.
Get the full insights: download the full report and equip your business with the knowledge to navigate espionage threats effectively.
SUBSCRIBE NOW
Join Our Global Intelligence Summary Mailing List
Sign up now to receive our weekly Global Intelligence Summary and quarterly Election Guide. Stay informed about key geopolitical events and upcoming elections that could spark unrest and shape the global landscape.