Evacuations from High-Risk Locations Call +44 (0)1202 308810 or Contact Us →
Overview: Active Exploitation of PAN-OS Vulnerability
Risk Factor: Critical
Date: 19th February 2025
Vulnerability: CVE-2025-0108
Get Help Now
Solace Cyber are specialists in securing network infrastructure. Get in touch if you need support.
What We Know
The Cybersecurity and Infrastructure Security Agency (CISA) and Palo Alto Networks have confirmed that CVE-2025-0108 is being actively exploited in the wild, making it a high-priority security concern for organisations using PAN Alto firewalls. Security researchers have observed that attackers are not exploiting CVE-2025-0108 in isolation, but instead, they are chaining this vulnerability with two others: CVE-2024-9474 and CVE-2025-0111, to escalate their privileges and achieve a complete system compromise.When combined, these vulnerabilities can grant attackers full root access to the firewall, leading to severe security breaches.
Recommend Actions
- Immediate Patching: Update your PAN-OS to the latest versions to address CVE-2025-0108 and related vulnerabilities.
- Restrict Management Interface Access: Limit access to the management web interface to trusted internal IP addresses only.
- Implement a Jump Box: Enhance security by using a jump box, ensuring that only authorised systems can access the management interface.
Solace Cyber is available to assist organisations with patching, hardening, and securing their firewall infrastructure against these threats.
Need Help?
Solace Cyber are specialists in securing network infrastructure. Get in touch if you need support.
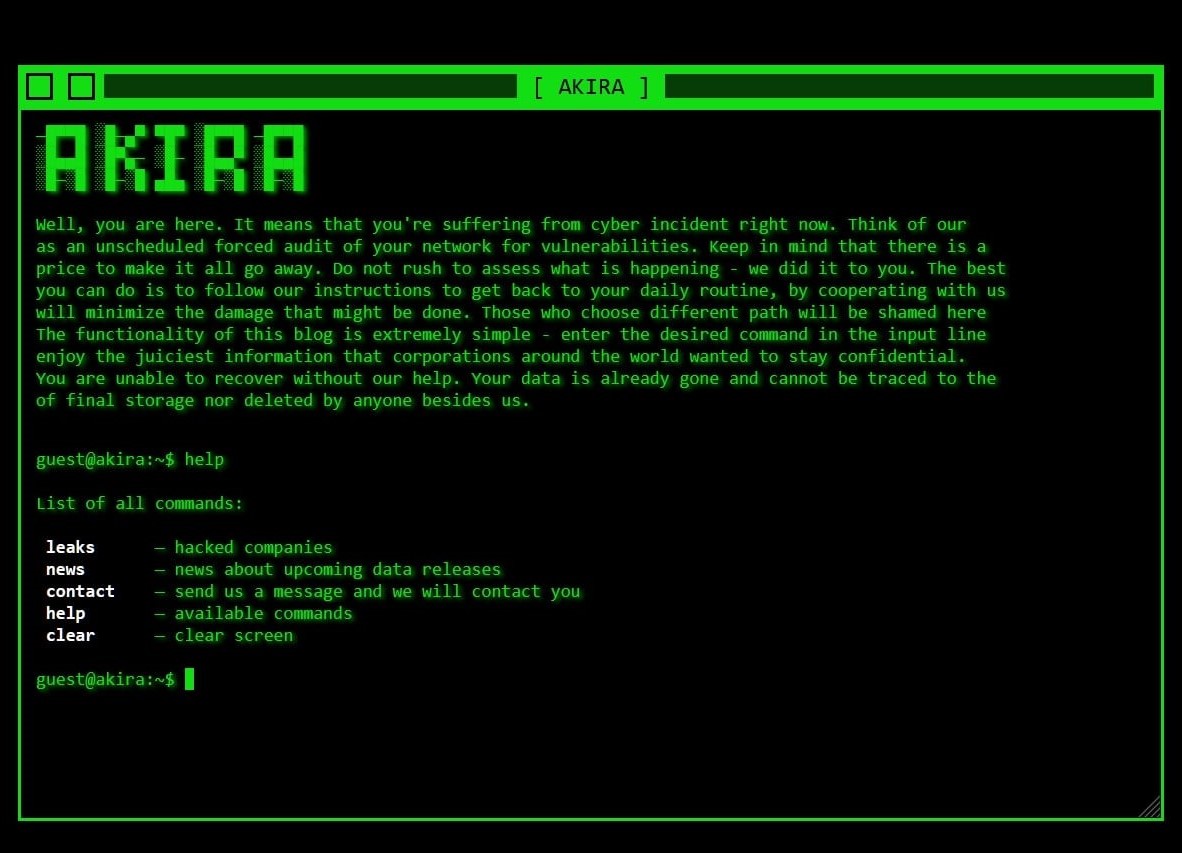
Overview: Akira Ransomware Group Exploiting SonicWall SSLVPN for Initial Access
Risk Factor: Critical
Date: 30th August 2024
Get Help Now
Solace Cyber are specialists in securing perimeter defences. Get in touch if you need support.
What We Know
In recent weeks, new intelligence from our incident response cases has revealed that the Akira ransomware group has started targeting SonicWall SSLVPNs to gain initial access to networks.
This tactic involves exploiting accounts with weak passwords and without Multi-Factor Authentication (MFA). This marks a significant shift in Akira’s initial access methods, which previously focused primarily on Cisco ASA firewalls.
While the possibility of exploiting SonicWall devices through known or unknown vulnerabilities cannot be entirely dismissed, multiple external sources are also reporting the group’s use of SonicWall SSLVPNs for initial access.
This change in Akira’s tactics highlights the critical importance of securing perimeter defences by enforcing strong password policies, regularly patching SonicWall devices, and implementing MFA across all VPN accounts to prevent unauthorised access to internal networks.
Solace Cyber Recommend:
- To ensure all user accounts with SSLVPN permissions, including any local accounts, are secured with multi-factor authentication.
- To conduct a recent audit of all VPN users and groups.
- Implement a strong password policy.
- Keep the SonicWall appliance updated with the latest patches and regularly review SonicWall releases for further patches.
- Enable external audit logging to extend the period of auditability, as SonicWall VPN login events typically do not cover more than 24 hours without external auditing.
Need Help?
Solace Cyber are specialists in securing perimeter defences. Get in touch if you need support.
Overview: Palo Alto has announced a critical zero-day vulnerability that is actively being used in the wild.
Threat Name: CVE-2024-3400
Risk Factor: Critical
Date: April 2024
Get Help Now
Solace Cyber security specialists can assist with updating your firewall to the latest version.
What We Know
CVE-2024-3400 represents a critical command injection vulnerability impacting the GlobalProtect Gateway functionality within PAN-OS. This flaw could be exploited by a remote, unauthenticated attacker to execute arbitrary code on a targeted firewall, granting them root privileges. The vulnerability has been categorised as critical as it poses a significant risk.
What Has Palo Alto Said?
Palo Alto Networks has acknowledged the issue and is working on a patch for CVE-2024-3400. Fixes are starting to become available. Not all versions of PAN-OS have a patch yet, so the advisory is to keep an eye on the Palo Alto Network official site.
Palo Alto Networks has also acknowledged that it’s “aware of a limited number of attacks that leverage the exploitation of this vulnerability.”
According to Palo Alto, the issue applies only to firewalls that have the configurations for both GlobalProtect gateway (Network > GlobalProtect > Gateways) and device telemetry (Device > Setup > Telemetry) enabled.
Recommendations For Navigating The Vulnerability.
When a vulnerability is identified, it’s crucial to take swift action to mitigate any potential risks. Specifically, for PAN-OS versions prior to:
- PAN-OS less than 11.1.2-h3
- PAN-OS less than 11.0.4-h1
- PAN-OS less than 10.2.9-h1
It’s highly recommended to prioritise patching as soon as the updates are released. These patches are vital for bolstering the security of your systems and safeguarding against potential exploitation.
As an interim measure, disabling device telemetry can serve as a temporary workaround until an official patch is made available. This step can help minimise exposure to vulnerabilities while awaiting the official fix.
Remaining vigilant is key. Continuously monitor official communications from Palo Alto Networks for any updates regarding the vulnerability and subsequent patches or mitigations. As soon as updates are released, promptly apply them to your systems to ensure optimal security posture.
It’s imperative to update your firewall to the latest version at the earliest opportunity. Solace Cyber stands ready to assist with this process, ensuring your firewall is promptly updated to the most recent version, thereby fortifying your defenses against potential threats.
Need support?
Solace Cyber security specialists can assist with updating your firewall to the latest version
Overview: Fortinet Warns of Critical FortiOS SSL VPN Flaw Likely Under Active Exploitation. Immediate action required.
Threat Name: CVE-2023-20198
Risk Factor: Critical
Date: 9th Feb 2024
Get Help Now
Solace Cyber security specialists can assist with updating your firewall to the latest version.
What We Know
On February 8, 2023, Fortinet issued a notice addressing a potentially exploited vulnerability in the wild. This vulnerability, found in the SSL VPN component, is classified as a pre-authentication vulnerability, with a critical severity rating of 9.6 CVSSv3. The identified flaw could enable a remote attacker to authenticate remotely by employing carefully crafted HTTP requests. Subsequently, the attacker may execute arbitrary code or commands, as reported by Fortinet.
What Has Fortinet Said About The Vulnerability?
Fortinet has emphasised that the only viable solution is to disable the SSL VPN entirely; opting to deactivate webmode is not considered a valid workaround. Urgent action is advised to promptly patch this vulnerability.
The affected versions and recommended solutions for FortiOS are as follows:
- FortiOS 7.6 is not affected, and no action is required (Not Applicable).
- FortiOS 7.4 versions ranging from 7.4.0 through 7.4.2, users are advised to upgrade to version 7.4.3 or above.
- FortiOS 7.2 with versions between 7.2.0 and 7.2.6, it is recommended to upgrade to 7.2.7 or above.
- FortiOS 7.0 users with versions from 7.0.0 through 7.0.13 should upgrade to 7.0.14 or above.
- FortiOS 6.4, versions 6.4.0 through 6.4.14, an upgrade to version 6.4.15 or above is recommended.
- FortiOS 6.2 users with versions ranging from 6.2.0 through 6.2.15 are advised to upgrade to 6.2.16 or above.
- FortiOS 6.0 in all versions, it is recommended to migrate to a fixed release.
What’s The Impact and Implementation Plan?
The flaw allows an attacker to remotely authenticate using crafted HTTPS requests. According to vuldb.com, technical details are unknown, but an exploit is available.
Swiftly upgrade your firewall to the most recent update. Solace Cyber is available to help you with the process of updating your firewall to the latest version.
Need support?
Solace Cyber security specialists can assist with updating your firewall to the latest version