Week 03: 10 – 17 January
Evacuations from High-Risk Locations Call +44 (0)1202 308810 or Contact Us →
Executive Summary
- The largest Ukrainian long-range attack against Russia in the war so far will almost certainly lead to significant Russian retaliation strikes against urban centres.
- If confirmed, the ceasefire between Hamas and Israel will highly likely allow for a short term improvement in the humanitarian situation in the Gaza Strip.
- There is a realistic possibility that violent unrest will decline in Mozambique following President Chapo’s inauguration.
- There is a realistic possibility that another attack on the police in Thailand is indicative of an intensification of the southern Thailand insurgency.



AMER
Venezuela: President Nicolas Maduro sworn in for third term.
Bolivia: Former President Morales supporters organise protests in La Paz.
EMEA
Ukraine: Ukraine launches largest ever long-range attack on strategic targets within internationally recognised Russia.
Syria: Syrian administration carries out multiple security operations
Israel and Gaza: Israeli and Hamas officials on the verge of reaching ceasefire.
Mozambique: President Chapo inaugurated after disputed election and widespread unrest.
Southeast Africa: Cyclone Dikeledi impacts Madagascar, Mayotte and Mozambique.
APAC
South Korea: Authorities arrest President Yoon Suk Yeol.
Thailand: Nine rangers and one tourist injured by bomb in restless south.
North, Central and South America
Venezuela: President Nicolás Maduro sworn in for third term
On 10 January, Venezuelan President Nicolás Maduro was sworn in for his third term despite widespread allegations of electoral fraud during the presidential election. Few international leaders attended the inauguration and only two Latin American leaders were present, President Daniel Ortega of Nicaragua and President Miguel Díaz-Canel of Cuba, both of whom share Maduro’s far-left authoritarian stance.
Protests occurred in the run-up and during the inauguration but did not reach the levels witnessed during the presidential election. The US, UK and the EU imposed new sanctions on the Maduro regime following the inauguration, with US sanctions including an increased reward for information leading to Maduro’s arrest to USD 25 million from USD 15 million.
Maduro denounced sanctions as an “economic war” on Venezuela and threatened to seize Puerto Rico from the US.
Solace Global Assessment:
Maduro’s third term will likely be marked by continued and widespread repression of the opposition, with the regime overly dependent on the military and police to ensure its survival. The scale of protests during the inauguration was likely limited by the arrest of key opposition leaders, a tactic that will almost certainly continue as Maduro consolidates power and curbs the influence of the opposition, civil society groups, journalists and any other critic of the regime.
The low international turnout and the imposition of new sanctions reflect the broader international condemnation of Maduro’s presidency and its lack of legitimacy. These trends will likely push Caracas further towards the orbit of states hostile to the West, including Russia, China and Iran despite BRICS recent rejection of Venezuela- a move caused by Brazil’s veto.
Maduro’s threat towards Puerto Rico is almost certainly sabre-rattling designed to rally his base, with Venezuela lacking the military strength to mount any viable challenge to the US. However, now that Maduro has begun his third term, there is a realistic possibility of increased hostilities with Guyana, with Venezuela claiming the oil-rich Essequibo region. As Maduro consolidates his grip on power, he may seek to intensify these tensions to distract from domestic issues and rally nationalist support.
Bolivia: Former President Evo Morales supporters march on La Paz
Supporters of former Bolivian President Evo Morales marched on Bolivia’s administrative capital, La Paz on 13 January. Protestors have clashed with police on multiple occasions and have tried to gain entry to government buildings, including the vice-presidency building. The police have deployed crowd dispersal methods in response, including the use of tear gas.
The protests, predominantly led by Bolivia’s Indigenous community, are partly a reaction to the reissuance of an arrest warrant for Morales in December for charges of statutory rape. However, they are also fuelled by economic hardship and a belief that President Arce is using legal charges against Morales to diminish his influence ahead of the August 2025 presidential election.
Solace Global Assessment:
With inflation reaching ten per cent, major fuel shortages, critical shortages in imported goods and a lack of foreign reserves, Bolivia is potentially heading for a major economic crisis that will likely sustain unrest until the 2025 presidential election and potentially beyond.
However, the protests, particularly those led by Bolivia’s Indigenous community, have likely exacerbated the country’s economic challenges. Roadblocks, which have become a common tactic in these demonstrations, have significantly disrupted the flow of goods and services, particularly along major supply routes where they have often been erected. The roadblocks are assessed to have cost the economy in excess of USD 2 billion and have exacerbated inflation and fuel supply issues.
The prolonged targeting of Morales combined with the police’s forceful response to indigenous protests, is likely to lead to an increased mobilisation of the indigenous community and heightened tensions, with previous examples suggesting that such tactics only fuel more unrest.
With mounting economic pressures, continued unrest and heightened tensions, Bolivia is likely to enter into a cycle of political instability, further deepening the economic crisis and likely shaping the conditions for a volatile and often violent run-up to the 2025 presidential election.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
US to remove Cuba from “state sponsors of terrorism” risk and ease sanctions
The announcement is likely to be one of the last major foreign policy moves made by the Biden administration and follows the precedent set by the Obama White House. Donald Trump reversed President Obama’s move towards the end of his first term, and it is likely that the same will happen once the transition is completed. It is therefore unlikely that this development will be anything more than a symbolic gesture before the return of the Trump administration, with the incoming president likely to sustain his tough stance on the Caribbean nation.
Security, Armed Conflict and Terror
US presidential inauguration to occur on 20 January
President-elect Donald Trump is set to be inaugurated on 20 January for his second term in office, an event that will likely bring severe traffic disruption to central Washington D.C. and a massive security deployment of around 25,000 military and law enforcement personnel.
The highly visible nature of the ceremony makes it an attractive potential target for violent extremists, including domestic and foreign actors. While FBI Director Christopher Wray stated that no specific or credible threats have been identified, this does not rule out the possibility of an attack. Self-radicalised lone actors pose the greatest threat, particularly given the relative ease of obtaining firearms in the US compared to other Western nations. Security agencies have also warned of potential disruptions from anticipated protests,
Environment, Health and Miscellaneous
Over one million now displaced within Haiti
The United Nations International Organization for Migration (IOM) has stated that over one million people, more than half of whom are children, have now been displaced within Haiti due to escalating gang violence. This figure is three times that of December 2023 and is largely in part to the gangs’ near-total control of Port-au-Prince and other highly populated areas.
The agency warned that shelters are overcrowded, and access to basic necessities such as food and water remains critically limited. Deportations from neighbouring countries, mainly the Dominican Republic, have exacerbated the humanitarian strain, which aid agencies are struggling to deal with.
The IOM has called for urgent aid and long-term solutions; however, with the gangs consolidating power in the capital and disrupting air travel from the island nation, major improvements are unlikely without a major international intervention.
Flooding crisis in eastern Brazil
Since 12 January, the flooding crisis in eastern Brazil has worsened due to ongoing heavy rains, with at least 26 deaths and 3,270 displaced in Minas Gerais as of 16 January. Sixty-three municipalities are under a state of emergency, and emergency responders are overwhelmed by calls in Divinopolis.
Other affected states include Bahia, Pernambuco, and Sergipe, with specific warnings for Rio Grande do Sul and Santa Catarina. Authorities have issued warnings for continued heavy rains, which will highly likely lead to more severe flooding and a high threat of major landslides.
Europe, Middle East & Africa
Ukraine: Ukraine launches largest long-range strikes against Russia in war so far
Overnight on 13-14 January, Ukraine conducted a large-scale series of long-range strikes against multiple targets on multiple axes between 200-1,000km into Russia. The attack reportedly used six UK-provided Storm Shadow air-launched cruise missiles (ALCMs) and US-provided ATACMS tactical ballistic missiles (TBMs), in addition to at least 146 one-way attack uncrewed aerial vehicles (OWA-UAVs, or attack drones).
The targets included an oil refinery and oil storage facility, glide bomb and cruise missile warehouses, chemical plants, a thermal power plant and military-industrial facilities. These targets were struck in the oblasts of Bryansk, Saratov, Tula, as well as in the Republic of Tatarstan.
Solace Global Assessment:
In the largest such attack by Ukraine against Russia in the war thus far, the strikes were primarily conducted against strategic, rather than tactical, targets. Strategic long-range strikes seek to degrade a state’s ability to wage war by destroying the basis of that state’s military capability.
The attack, therefore, likely indicates to the incoming Trump administration and other key Western allies that Ukraine is capable of continuing the fight against Russia for some time yet. There is a realistic possibility that while Ukraine only has a limited number of Western-provided advanced missile systems, Ukraine has built up a substantial stockpile of domestically produced OWA-UAVs that it can use to conduct further periodic large-scale strategic attacks into Russia.
The attack emulated the tactics, techniques and procedures (TTPs) of large-scale Russian long-range attacks, by layering large quantities of cheap OWA-UAVS that can overwhelm air defences with advanced missile systems. With the advent of the OWA-UAV, this is highly likely a new universally applicable tactic of warfighting to penetrate advanced modern air defence, which will almost certainly be replicated by other state militaries as well as capable non-state actors (such as the Houthis in Yemen).
Russia is highly likely to retaliate. The November 2024 decision by the Biden administration to allow the use of ATACMS and Storm Shadow against targets in internationally recognised Russian territory led to large-scale Russian retaliation strikes. The retaliation strikes included the use of the new Oreshnik intermediate-range ballistic missile (IRBM).
There is a realistic possibility that in addition to the regular large-scale attacks against Ukrainian critical national infrastructure (CNI), such as a 14-15 January series of strikes, Russia will launch a notably significant wave of attacks against Ukrainian urban centres. These attacks could include the use of Oreshnik (largely due to its symbolic value) and the indiscriminate targeting of civilian targets.
Syria: Syrian administration carries out multiple security operations
On 11 January, intelligence officials of Syria’s new government announced they thwarted a plan by the Islamic State (IS) to bomb a Shiite shrine in the Damascus suburb of Sayyida Zeinab.
On 14 January, local channels reported the arrest of the Egyptian citizen Ahmad al-Mansur, who had reportedly sought to start an Islamist movement, named the “January 25 Revolutionaries”, to launch an insurrection against Egyptian leader al-Sisi.
On 15 January, other reports indicated that HTS forces had killed Bassem Hussam al-Din, the commander of a Latakia-based militia that had threatened the transition government weeks ago and had reportedly kidnapped multiple security forces members.
Solace Global Assessment:
The new Syrian administration is likely focusing significant efforts on domestic security and counterterrorism as it seeks to bolster its domestic and international credibility as a long-term administrator for the country. At home, the administration is balancing multiple possible vectors of instability. The various anti-Assad rebel groups and splinter units that have remained armed after the regime’s fall may increasingly become attractive springboards for foreign-backed efforts to destabilise Syria, or may develop into radical formations.
Abroad, the new Syrian administration has taken considerable steps to reassure regional powers, as well as the West, of its viability as a diplomatic partner. The immediate decapitation of the January 25 movement can likely be interpreted in this light. Additionally, Syria’s forces counterterrorism operation against IS is a political victory for the new government, which has pledged to protect religious and ethnic minorities in the country.
Israel and Gaza: Ceasefire agreement on the verge of approval
During this reporting period, representatives of Hamas and the Israeli government negotiating in Doha reportedly reached a “breakthrough”, making the approval of a ceasefire in Gaza imminent. By 16 January, reports indicated that the two sides agreed on a three-phase ceasefire framework.
During the first phase, which is to last 42 days, hostilities will end, and Israeli troops will withdraw to the border, retaining control over the Philadelphi corridor at the Gaza-Egypt border. Surviving Israeli hostages as well as the remains of those who died in captivity would then be exchanged for Palestinian prisoners (with a 30:1 or 50:1 ratio, the latter for women and underage hostages). Gradual hostage exchanges would then continue, while humanitarian aid to Gaza would be considerably boosted.
In phase two, also 42 days-long, Israeli forces will completely withdraw from Gaza. Phase three will mostly focus on reconstruction efforts.
On 16 January, the final approval to the agreement was reportedly delayed by internal disagreements within the Israeli government. Minister of Finance Bezalel Smotrich’s party “Religious Zionism” threatened to pull support from Netanyahu’s government if the deal were to be approved. Similarly, hard-right Minister of National Security Itamar Ben-Gvir also threatened to quit.
A meeting to finalise the ceasefire’s approval was delayed and is scheduled to be held on 17 January.
Solace Global Assessment:
The ceasefire achieves some but not all of the Netanyahu government’s stated war goals. It achieves the liberation of the remaining hostages and secures, at least for a period, Israeli control over the vital Egypt-Gaza border. However, the ceasefire does not include the disbandment of Hamas. While Hamas’ has been significantly weakened and depleted by the war and is unlikely to be able to fully replenish its strength during the ceasefire, it has survived the conflict. Hamas will almost certainly use the ceasefire to reinfiltrate parts of Gaza, especially in the north, and to carry out operations against other Palestinian militias operating in Gaza, which have threatened its authority.
In the short term, the ceasefire is almost certain to boost the delivery of much-needed aid to Gaza. This is likely to be compounded by renewed humanitarian efforts by EU and Gulf states. After phase one, there is a realistic possibility of the ceasefire breaking down, especially if the hard-right parties that support the Netanyahu government retain their maximalist positions. The first foreign policy actions of the Trump administration, set to begin on 20 January, are likely to be crucial for the viability of the ceasefire.
In Israel, the ceasefire will highly likely threaten the stability of the Netanyahu administration. The hard-right and pro-war activists are likely to see the ceasefire as “betraying” the goal of destroying Hamas in Gaza. Conversely, anti-war activists, generally on the left, will accuse the Netanyahu government of arbitrarily prolonging the war. Anti-government sentiment from both the left and hard right will likely result in large-scale demonstrations in Israeli urban centres.
If sustained, the ceasefire is likely to have an impact at the international level. A prolonged truce followed by reconstruction will likely lead to a reduction in pro-Palestine protests, although this will likely increase should either party renege. However, the threat posed by radicalisation after the war almost certainly will remain extant, with a high chance of lone-actor attacks in the West regardless of the ceasefire’s success.
Southeast Africa: Madagascar, Mozambique and Mayotte hit by Tropical Cyclone Dikeledi
After starting as a tropical depression in the Indian Ocean, the storm Dikeledi intensified into a tropical cyclone with maximum windspeeds of 169km/h. On 11 January, Cyclone Dikeledi made landfall in northern Madagascar, causing widespread flooding, landslides and heavy rainfall, resulting in at least three deaths.
After making landfall, Dikeledi weakened into a tropical storm and tracked west in the Mozambique Channel south of Mayotte and Comoros. In Mayotte, at least 14,500 people sought refuge in emergency shelters and heavy rainfall caused flooding and landslides.
The storm then again intensified into a cyclone and briefly made landfall in Mozambique east of Nampula on 13 January, before tracking south. In Nampula, authorities report at least five deaths, over 5,000 houses destroyed, and 35,000 people affected.
Solace Global Assessment:
The most severe storm of the current South West Indian Ocean cyclone season so far, Cyclone Chido, devastated the French overseas department of Mayotte in December 2024. Mayotte was far less impacted by Dikeledi, although the ongoing recovery efforts from Chido have highly likely been impeded.
This current cyclone season is forecast to run from November 2024 to April 2025 (excluding Mauritius and the Seychelles, which is forecast to end in May 2025). The island nations and overseas territories in the South West Indian Ocean are highly vulnerable to the impact of cyclones.
In the event of a severe natural disaster, evacuation options for business travellers and employees in the region would be limited to difficult and costly maritime options in the event of critical airport closures.
Mozambique: President Chapo inaugurated after disputed election and widespread unrest
On 15 January, Frelimo candidate Daniel Chapo was inaugurated as President of Mozambique. In his inauguration speech, Chapo announced several measures, promising to slim down government, reduce the number of ministries, and scrap the central-level State Secretariats. He stated that he would redirect the money to education, health, agriculture, water, roads, and energy.
As the third day of the announced three days of strikes, protests occurred across several cities in Mozambique including Maputo and Nampula. Demonstrations occurred directly outside the inauguration ceremony. Security forces responded with live ammunition and tear gas, killing at least eight people. Footage was shared on social media of security forces hitting an unarmed woman. According to local NGOs, approximately 303 people have been killed in Mozambique since the post-election unrest began.
On 17 January, Frelimo is set to destroy all ballot papers from the October 9 general election. The destruction is set to take place publicly at the District and City Elections Commissions ‘before representatives of candidates, political parties, coalitions of political parties, groups of proposing voters, observers, journalists, and voters in general’, according to the National Elections Commission (CNE). On 8 January, the Public Integrity Center (CIP) reportedly filed an appeal with the Administrative Court to halt the destruction of the ballots.
Solace Global Assessment:
It is highly likely that Chapo is attempting to present himself as a reformer to portray a distinction between his ministry and the previous government. Now Frelimo have successfully inaugurated their candidate, they will likely attempt to appease protesters with reforms. While the destruction of the ballot papers will likely be incendiary in the immediate term, with protesters likely attempting to storm the District and City Elections Commissions, it may inject a sense of defeatism into opposition forces since they will no longer able to concretely prove that the election was fraudulent.
Opposition leader Venâncio Mondlane has declared that he is the legitimate head of state and will announce a program for the ‘first 100 days of his term in office’ on 17 January at 15:00 local time (13:00 UTC). Given he does not have access to state resources, these measures will likely be highly symbolic. He has previously stated that Mozambique requires a new flag; this will likely feature on the agenda. Mondlane has also indicated an end to the protests over the coming months as he implements his shadow government. While the details are yet to be released, this is highly likely to take the momentum out of the demonstrations, which have relied on Mondlane’s organisation since the election.
There is a realistic possibility that Chapo’s inauguration marks a turning point for unrest in Mozambique. The inauguration period has now ended, and Frelimo will almost certainly aim to portray Chapo as a fresh leader with ambitions to better the population, as reflected in Chapo’s inauguration speech. Furthermore, international pressure will likely decrease as other countries set out to strengthen relations with Mozambique’s new government.
Whether demonstrations continue to escalate is almost certainly dependent on Mondlane’s announcement on 17 January. While security forces attempting to arrest Mondlane would also almost certainly incentivise demonstrations, the government has, so far, refrained from taking such measures. It is likely they will continue to refrain from inflaming demonstrations. Without a clear route to power, the widespread perception that Frelimo have “won”, and exhaustion from the economic disruption from the unrest, there is a realistic possibility that demonstrations will gradually diminish over the coming months.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
German far-right congress blocked by 10,000 protesters
The demonstrators blocked the entrance to the planned event, in the east German town of Riesa, Saxony, which had been organised by the Alternative for Germany (AfD) party. Germany is holding general elections on 23 February, and the AfD is polling at 21 per cent, which would be the party’s best-ever result in national elections. Party leader Alice Weidel was nominated as the AfD’s official candidate for the chancellorship despite the disruptions. Further protests against the far-right are almost certain in the run-up to the elections, with previous demonstrations attracting hundreds of thousands of participants.
Davos summit likely to drive civil unrest in Western urban centres
The World Economic Forum (WEF) will host its annual meeting in Davos, Switzerland, between 20 and 24 January. The Davos summit is a preferred target for environmentalists, anti-capitalist left-wing groups, and other organisations, and is likely to attract protests. Civil unrest is highly likely to occur in Davos itself, causing some disruptions. Other protests are likely to occur in large Western urban centres, like London, Paris, or Brussels. There is a particularly high likelihood of small-scale symbolic actions by anti-WEF groups, including actions meant to disrupt public transport in target cities.
Thousands demonstrate in Belgrade
On 12 January, 20,000 people gathered in a student-led anti-government protest outside the Constitutional Court of Serbia in Belgrade to commemorate victims of the railway station roof collapse in Novi Sad on 1 November 2024 which left 15 dead. The roof collapse has been blamed on sloppy reconstruction work due to corruption; the Novi Sad railway station building was renovated in a deal with Chinese state companies.
A separate protest also occurred in Nis. Protesters demanded that those responsible be brought to justice. The unrest follows a series of protests which occurred in November and December 2024. The demonstrations reflect a broader frustration with perceived failings of the government. President Aleksandar Vucic is increasingly perceived as shifting towards autocratic rule by curbing democratic freedoms and infringing on civil rights. Further unrest in Serbia is highly likely.
Former Georgian prime minister hospitalised after beating by unidentified individuals
Anti-government protests have continued in Georgia, with levels of political violence escalating. Alongside the deployment of draconian riot police tactics against protesters, the role of pro-government plainclothes provocateurs continues to increase. Called “Titushky” by opposition supporters, a Ukrainian name which derives from the pro-Russian “thugs” who frequently attacked pro-European Ukrainians during the Euromaidan movement, they have highly likely been used to suppress the pro-European movement in Georgia with violence.
On 15 January, footage surfaced showing unidentified men attacking participants of a strike that had gathered in central Tbilisi. On 14 January, Giorgi Gakharia, a former prime minister of Georgia between 2019-2021 who now leads the For Georgia opposition party, was hospitalised after being severely beaten in the lobby of the Sheraton hotel in Batumi. The attack, highly likely conducted by “Titushky”, is likely indicative of an increasingly violent crackdown on the Georgian opposition.
Nawaf Salam is the new Lebanese Prime Minister
Nawaf Salam is the head of the International Court of Justice and was widely supported by Christian, Druze, and Sunni members of parliament, while the Shiite representatives, Hezbollah and its ally the Amal Movement, failed to field a candidate. The appointment of Salam is a political setback for Hezbollah and may underscore a greater boldness by its Lebanese opponents to confront its position as an informal “second military” in Lebanon.
Last week, President Joseph Aoun vowed to ensure that only the state retains control of all arms in the country, a statement that was obviously directed at Hezbollah. While no concrete measures are in place to disarm Hezbollah, such a plan is almost certainly too ambitious to be implemented by the Lebanese government.
More realistically, Salam could work to reduce Hezbollah’s influence in the judiciary and legislature while directing “kinetic” efforts to ensure the continuation of the ceasefire agreement with Israel south of the Litani river, a move that may also send positive signals to Lebanon’s southern neighbour and its allies in Washington.
Mali forces seize gold stocks at Canadian mining company site
The government of Mali began enforcing a provisional order to seize gold at the Loulo-Gounkoto site operated by the Canadian Barrick Gold mining company. The move follows Mali blocking gold shipments by the company, and detaining company employees. It almost certainly continues to highlight the worsening security and viability of Western private actors in the Sahel. There is a realistic possibility that similar developments will follow in Burkina Faso, Niger, and potentially Chad.
Security, Armed Conflict and Terror
NATO to increase force posture in Baltic Sea after multiple cables cut
The North Atlantic Treaty Organisation (NATO) has initiated operation “Baltic Sentry” in response to a rise in suspected incidents of underwater sabotage that have primarily targeted undersea internet cables. The operation will include the deployment of frigates, maritime patrol aircraft and autonomous vehicles, including uncrewed surface vessels (USVs).
The operation will almost certainly involve an increase in surveillance on suspected Russian “shadow fleet” vessels, civilian flagged vessels that are alleged to work at the behest of Russian intelligence. However, with Russia’s shadow fleet estimated to contain hundreds of vessels, the NATO task group will likely struggle to actively monitor and deter Russia vessels capable of engaging in Russia’s maritime grey zone strategy.
Anarchist activist firebombs Italian army barracks
On the night of 13 January, a barracks operated by the Carabinieri (Italy’s gendarmerie) in Borgo San Lorenzo, near Florence, was attacked with Molotov cocktails, causing some damage but no injuries. An individual, reportedly an Anarchist activist, was arrested in connection to the incident. There is a realistic possibility that the firebombing was linked to ongoing anti-police protests in central and northern Italy, which have been sparked by the killing of a 19-year-old during a police chase.
Armenia to join global coalition against the Islamic State (IS)
Armenian and American officials announced the beginning of closer defence cooperation between Armenia and the United States, including the former joining the global coalition against IS. Politically, the announcement follows previous Armenian efforts to pivot towards the West following the significant deterioration of its relations with Moscow, following the Nagorno-Karabakh conflict.
The announcement almost certainly highlights a growing US interest in the Caucasus, where IS presence is growing through the increased recruitment of Islamic State-Caucasus Province (IS-CP) . In late 2024, an IS-CP cell was discovered in north Azerbaijan and IS-CP has recently claimed attacks in Dagestan, Russia.
Spanish tourist reportedly kidnapped in southern Algeria
Uncorroborated reports indicate that on 15 January a female Spanish tourist was kidnapped from near the southern Algeria town of Tamanrasset, approximately 300km away from the borders with Mali and Niger. The woman was then taken across the border to Mali, where much of the northern region remains largely lawless.
Reports suggest that the woman was captured by militants belonging to the Islamic State Sahel Province, an affiliate of the Islamic State that has grown substantially because of the destabilisation of the Sahel. The kidnappers will now likely attempt to secure a ransom from the Spanish government to fund future operations.
Russia and Iran scheduled to sign 20-year strategic pact
On 17 January, the Iranian President Masoud Pezeshkian and Russian President Vladimir Putin are scheduled to meet in Moscow and sign strategic partnership deal that will govern relations between Russia and Iran for the next 20 years. The deal is claimed to include the further expansion of bilateral ties in trade, investment, transportation, and humanitarian sectors, as well as a deepening of cooperation in defence and security.
Russo-Iranian cooperation is already significant, with Iran supplying Russia with large quantities of Shahed series one-way attack uncrewed aerial vehicles (OWA-UAVs), attack drones that Russia uses to conduct almost daily attacks against Ukraine. In 2024, the Kremlin made a similar strategic partnership with Pyongyang, leading to the deployment of over 10,000 North Korean troops which are currently engaged in high-intensity combat operations against Ukraine in the Kursk salient. It is unlikely, however, that Iran will send troops.
The agreement is an immediate challenge for the shortly forthcoming Trump administration, with Trump having previously adopted a distinctly hawkish foreign policy posture towards Iran. The agreement likely indicates that Moscow is unwilling to distance itself from Tehran and risk losing critical attack drone supplies in an effort to appease Trump.
Niger and China sign pipeline security memorandum
On 14 January, the Chinese pipeline operator WAPCO signed a framework covering security at its Niger-based operations. The development not only highlights China’s growing economic and strategic footprint in the Sahel, partially accelerated by the West’s retrenchment but also likely Beijing’s growing worries about Islamist groups targeting its assets and citizens in at-risk countries. Attacks on Chinese economic interests have been pervasive in Pakistan, and there is a high likelihood that as China’s footprint grows, African Islamist groups, particularly those affiliated with transregional groups like al-Qaeda and the Islamic State, will increasingly target Chinese interest in the region.
Sudanese Armed Forces (SAF) make progress in Gezira state, take Wad Madani
SAF units reportedly pushed out Rapid Support Forces (RSF) from the city in Gezira state. Wad Madani is a key logistical hub on the Blue Nile, which controls supply routes to Khartoum, located just to its north, and to eastern regions of the country. The offensive is likely to be important for future SAF efforts to secure control of Gezeira state. There is a realistic possibility that the capture of Wad Madani will strengthen the Sudanese government’s position in Khartoum, where SAF advances have recently resumed.
Environment, Health and Miscellaneous
Icelandic authorities increase aviation alert level in response to seismic activity
On 14 January, the Icelandic Meteorological Office elevated the aviation alert level from green to yellow as a precaution. The decision was taken after 130 earthquakes were detected beneath Iceland’s Bardarbunga volcano, provoking concerns over an eruption. The earthquakes included a magnitude 5.1 tremor and 17 others registering above magnitude 3, likely indicating magma accumulation beneath the volcano. The volcano is one of six volcanic systems located under Europe’s biggest glacier Vatnajokull, and in the event of a subglacial eruption, there is a substantial risk of an ash eruption and subglacial flooding
Marburg outbreak suspected in northwest Tanzania
An outbreak of Marburg Virus Disease (MVD), a severe haemorrhagic fever with no known treatment or vaccine, is suspected in Tanzania’s Kagera region, near the borders with Rwanda and Burundi. Nine suspected cases have been reported, including eight deaths, resulting in a case-fatality ratio of 89 per cent. Healthcare workers are among the affected.
The World Health Organization (WHO) has raised concerns about the potential for further spread, particularly given Kagera’s position as a transit hub with frequent cross-border movement. A recent MVD outbreak in Rwanda, which affected 66 people and caused 15 deaths, was declared over in December 2024. In response, rapid response teams have been deployed, a mobile laboratory and treatment centres have been established, and ongoing laboratory tests and contact tracing are underway.
Asia–Pacific
South Korea: Authorities arrest President Yoon Suk Yeol
On 15 January, authorities detained Yoon after he failed to comply with multiple summonses from police and investigators. Yoon stated that he would cooperate with investigators but criticised his arrest as illegal. Investigators have 48 hours to question him at the corruption agency’s headquarters in Gwacheon before applying for a detention warrant that could extend his detainment for up to 20 days. On 17 January, South Korea’s anti-corruption agency stated that it would seek to extend Yoon’s detention. Yoon’s defence team is seeking a review of his arrest warrant, and his impeachment trial is set to continue.
The arrest followed a standoff at the presidential residence in Seoul, where authorities faced resistance from Yoon’s supporters and the acting chief of presidential security, who was subsequently detained for obstruction. Approximately 3,000 police officers were deployed to arrest Yoon. A similar incident occurred on 3 January, whereby authorities were prevented from arresting Yoon after being blocked for approximately six hours. The situation remains fluid, with Yoon’s legal team negotiating for his voluntary appearance before investigators.
Solace Global Assessment:
Yoon is the first sitting president of South Korea to be arrested. He reportedly faced hours of questioning after his arrest but has not yet been charged. If found guilty of insurrection, Yoon faces the prospect of a heavy fine or life imprisonment. The crime also technically carries the death sentence, but this outcome is highly unlikely due to a long-standing moratorium on executions.
Yoon’s arrest constitutes an important step in restoring normality in South Korean politics. Since Yoon’s declaration of martial law on 3 December, uncertainty has persisted after Yoon refused to step down despite efforts by opposition forces to impeach him, which eventually succeeded on 14 December. The longer Yoon resisted arrest, the greater the chances of further unrest and clashes between his supporters and anti-Yoon movements and government forces. Furthermore, the authorities’ failure to arrest Yoon constituted a source of embarrassment for South Korea’s security forces. If Yoon successfully evaded arrest, it may embolden politicians to curb democratic institutions to retain power.
Thailand: Thai police targeted in IED attack in restless south
On 13 January, an improvised explosive device (IED) detonated near Muang Pattani police station in Thailand’s southern province of Pattani, injuring nine paramilitary rangers and one Malaysian tourist. The bomb was attached to a motorcycle, which was left by a suspect who fled on foot. Police cordoned off the area and jammed mobile phone signals, fearing that suspected insurgents might have planted a second bomb to ambush officers.
Solace Global Assessment:
This attack adds to a growing series of militant assaults in southern Thailand, a region long plagued by insurgent activity, largely attributed to separatist Islamist groups such as the Barisan Revolusi Nasional (BRN), Pattani United Liberation Organization (PULO) and the New Pattani Revolutionary Front (BPP). Although the latest attack did not result in fatalities, it marks yet another example of the increased use of IEDs by separatist groups in the region.
These attacks have largely escaped international attention, partly due to the lack of high-profile casualties and the Thai authorities’ efforts to downplay the violence to protect the tourism industry and foreign investment. However, the increase in attacks may indicate a resurgence of the insurgency, with peace talks failing to make meaningful progress.
On 16 January, Prime Minister Paetongtarn Shinawatra visited the three southern provinces of Pattani, Yala, and Narathiwat, despite the threat of militancy. Her visit was likely a bid to reassure the public and demonstrate the government’s commitment to the restive south, as well as to reassure Chinese visitors, millions of whom visit Thailand during the Chinese Lunar year which begins on 29 January.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Former Pakistani Prime Minister Imran Khan sentenced to 14 years in prison
The sentence is linked to a corruption case. Khan was accused of exchanging government land for favours by a major real estate developer. Khan, who has been in prison since August 2023, is the leader of the Pakistan Tehreek-e-Insaf (PTI) and remains hugely popular in the country and among the Pakistani diaspora community. PTI activists and other supporters have staged sporadic large-scale protests since Khan was imprisoned.
In November 2024, protests led to multiple cities in Pakistan being paralysed, six deaths, and over 1,000 arrests. There is a high likelihood that this development will lead to further protests. Moreover, there is a realistic possibility of civil unrest in cities with a large Pakistani community, including London and other UK urban centres.
Security, Armed Conflict and Terror
Pakistani army expands operations against Baloch militants
At least 27 militants, most belonging to the Balochistan Liberation Army (BLA), have been killed by Pakistani army operations in the restless Balochistan province. Army operations targeted several militant hideouts, as well as weapons and ammunition depots, resulting in the capturing of lethal material. The raids were initiated after a series of BLA and Balochistan Liberation Front (BLF) which killed multiple government troops.
However, both militant groups have responded with IED attacks on government forces. This is likely to demonstrate strength and to exploit the current overstretching of the Pakistani military which is also contending with a border conflict with the Afghan Taliban, an increase in attacks attributed to Tehreek-e-Taliban Pakistan (TTP), and a wave of sectarian violence in the west of the country.
Beijing deploys its largest coastguard vessel in the Philippines’ waters
On 14 January, Beijing deployed a 164.89-metre-long coastguard vessel 5901 (IMO: 9756028) nicknamed “The Monster” approximately 77 nautical miles off the coast of Philippines’ Zambales province. Manila criticised the act as intended to ‘intimidate fishermen’ and reflective of Beijing’s ‘increasing aggression’. In response to the vessel’s presence, the Philippine Coastguard deployed two of its largest vessels and demanded the withdrawal of the vessel from its exclusive maritime economic zone (EEZ).
On 17 January, the Philippine navy conducted drills near the contested Scarborough shoal in the South China Sea, an act almost certainly conducted in response to perceived Chinese aggression. This incident constitutes the latest spat amid frequent brinkmanship between Philippine and Chinese maritime forces around the contested waters.
Environment, Health and Miscellaneous
Magnitude 6.9 earthquake off Miyazaki, Japan
On 13 January, a magnitude 6.9 earthquake struck off the coast of Miyazaki Prefecture in Japan, prompting a tsunami advisory for coastal areas in Miyazaki and Kochi prefectures. The Japanese meteorological agency reported multiple aftershocks with magnitudes between 3 and 4.1. Following the earthquake, evacuation orders were issued for the coastal areas of Takanabe and Kadogawa. A 10-centimetre wave was observed at Cape Muroto and Tosashimizu, while tide gauges reported a 20-centimetre sea level rise at Miyazaki and Aburatsu ports.
The tsunami advisories and warnings were later lifted, with no reports of significant damage. In the aftermath, local authorities reported minor disruptions, including water outages in the Ikime area of Miyazaki due to apparent pipe damage. At least one person sustained minor injuries in Oita Prefecture. Authorities have called for people to remain alert for further strong tremors in the week following the earthquake.
Eruption of Mount Ibu in Indonesia
On 16 January, Mount Ibu in Indonesia’s North Maluku region erupted Authorities have initiated evacuations for approximately 3,000 residents living in the vicinity of the volcano. As of the latest reports, 182 individuals have taken refuge in evacuation centres. The Indonesian disaster agency has issued a warning to the public to refrain from engaging in activities within a three-mile radius of the volcano’s active crater. Emergency responders have been deployed to manage the situation, following the elevation of the alert status to its highest level. The eruption has prompted swift action to ensure the safety of the local population, which numbers around 13,000 people.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.

Executive Summary
- Further destruction is almost certain as wildfires continue to tear through Southern California.
- Significant protests are highly likely to continue in Venezuela as Maduro is inaugurated and will almost certainly be met with violent suppression by the regime.
- A major attack in northern Benin is almost certainly indicative of the growing threat posed to West African countries by jihadist groups highly active in the Sahel junta states.
- Significant unrest is highly likely in Mozambique as the formerly exiled opposition leader Mondlane returns to Maputo.



AMER
Canada: Prime Minister Trudeau resigns
USA: Multiple wildfires spread through Southern California
Venezuela: Arrests and planned protests ahead of Maduro inauguration
EMEA
Austria: Far-right party gets mandate to form government
Ukraine & Russia: Ukrainian forces launch limited counteroffensive in Kursk
Benin: Benin army sustains heavy losses after attack in the north
Chad: 24 individuals appear to attempt to storm presidential palace
Mozambique: Opposition leader Mond-lane arrives in Maputo
APAC
China: 7.1 magnitude earthquake hits southern Tibet
Taiwan: Taipei accuses China of underwater sabotage
North, Central and South America
Canada: Prime Minister Justin Trudeau resigns
On 6 January, Justin Trudeau, who has served as Canada’s prime minister since 2015, announced that he would step down as the leader of his party, with the leadership election scheduled for 9 March.
Federal elections are scheduled to be held in Canada by 20 October 2025. The main opposition party is the Conservative Party, which currently polls between 20 and 24 points ahead of the Liberal Party. Furthermore, recent polls indicate that the Liberals risk falling behind the New Democrats, Canada’s third-largest party.
Solace Global Assessment:
Trudeau’s resignation follows significant internal pressures within the Liberal Party, as well as considerable domestic and international political setbacks. Trudeau’s political situation had likely become close to unrecoverable following the resignation of long-term ally and Deputy Prime Minister Chrystia Freeland in December, who openly accused Trudeau of failing to do enough to meet the challenge posed by US President-elect Donald Trump’s call to impose heavy tariffs on Canadian goods. Freeland’s resignation mobilised large parts of the Liberal Party to increase their calls for the prime minister to step down.
However, even prior to December, Trudeau’s position had gradually deteriorated following repeated setbacks at home and abroad. Canada’s severe cost of living crisis, marked by significant housing shortages, has particularly affected some of the Liberals’ key constituencies.
Domestic protests, such as the COVID-19 and trucker’s protests, a stagnant economy characterised by rising inflation, and growing concerns with immigration also influenced by developments in Europe and south of the border, have all likely contributed to damage Trudeau’s popularity.
On the international stage, the Canadian government has been heavily criticised by pro-Palestine groups, it has engaged in an ongoing diplomatic crisis with India over the alleged targeted assassination of a Sikh independence activist on Canadian soil and has clashed with the incoming US administration.
While a new candidate may boost the Liberal Party’s chances at the elections, it remains highly likely that the Conservatives will win decisively. The first weeks and months of the Trump administration are likely to be particularly crucial. If the promised tariffs are implemented, these are likely to have extremely negative effects for the new Canadian administration. In fact, there is a realistic possibility that Washington will leverage the Liberals’ extremely precarious political position to extract concessions in the areas of security, foreign policy, and trade.
United States: Significant wildfires tear through Southern California
As of 10 January, fast-moving wildfires are currently ongoing in California. At least five separate blazes are currently ongoing around the Pacific Palisades (Palisades Fire), Pasadena (Eaton Fire), Sylmar (Hurst Fire), Acton (Lidia Fire), and Hollywood Hills (Sunset Fire) neighbourhoods of Los Angeles.
The Palisades Fire has burned through over 20,000 acres, causing significant damage, including the destruction of beachfront homes in Malibu; it is approximately six per cent contained. The Eaton Fire has spread to nearly 14,000 acres and is zero per cent contained. The Kenneth Fire has impacted approximately 960 acres and is 35 per cent contained. The Hurst Fire has grown to 800 acres and is 37 per cent contained. The Lidia Fire has grown to approximately 400 acres but is 75 per cent contained.
Mandatory evacuation orders have been issued for nearly 180,000 people in Southern California. Ten deaths have been reported so far. Over 1,400 firefighting personnel have been deployed to combat the blazes and Governor Gavin Newsom declared a state of emergency.
Major roads including Sunset Boulevard and part of the Pacific Coast Highway became gridlocked as residents fled the wildfires. Highway lanes near Topanga Canyon Boulevard closed due to the wildfire’s fast expansion. Drivers abandoned their cars on Sunset Boulevard, forcing The Los Angeles Fire Department to deploy bulldozers to Sunset Boulevard to allow fire crews to pass abandoned vehicles.
Solace Global Assessment:
The fires began on 7 January after a bush fire was caught by a windstorm, spreading the fire into surrounding areas. California is currently affected by the northeasterly Santa Ana winds of approximately 100 km/h, which are caused by high pressure over the Great Basin. These winds have fuelled many of California’s worst wildfires in the past, including the 2018 Woolsey fire, which killed three people.
Peak wildfire season in California typically occurs between July and October each year. Although wildfires are unusual in January, high winds have combined with particularly dry conditions in California to contribute to fertile conditions for the wildfire to spread. Rains of over 0.25 centimetres have not been experienced in Southern California since May 2024. The Santa Ana winds have exacerbated the dry conditions by reducing the humidity levels.
Fire hydrants have reportedly run out of water in the Palisades area. While water tanks are currently being used to supply water to fire fighters, this severely limits the extent to which the fire department can tackle the ongoing wildfires. The reason for the water shortage is currently unknown, but water shortages at fire hydrants may occur because of power outages, high demand during large fires, broken water mains, or drought conditions. Given the recent dry weather, the issues are likely influenced by low water supplies in Southern California.
In the aftermath of the wildfires, residents who have had their property destroyed are likely to ask questions regarding the lack of water in the fire hydrants. Much of California’s water infrastructure was built in the 1960s and 1970s, lacking advanced modern technology and prone to leaks and inefficiency. Furthermore, Los Angeles mayor Karen Bass cut the fire department’s budget in 2024 by approximately USD 17 million. Given California has one of the highest water needs in the US, the federal and state authorities are likely to come under increasing pressure to modernise California’s water infrastructure in the months following the wildfire and increase fire department spending.
Venezuela: Opposition arrests ahead of Maduro inauguration and planned protests
Ahead of President Nicolas Maduro’s inauguration for a third six-year term on 10 January, the Venezuelan opposition has warned of a surge in arrests of activists and opposition figures.
Prominent arrests have included press freedom advocate, Carlos Correa, opposition politician Enrique Marquez and briefly, the leader of the opposition, María Corina Machado.
The arrests coincide with planned protests against Maduro’s inauguration, with opposition groups continuing to dispute the results of July’s presidential election, which they allege was marred by fraud and voting irregularities. Several foreign nationals have also been detained on suspicion of conspiracy or sabotage.
Solace Global Assessment:
The increase in arrests is likely strategic messaging by the Maduro administration aimed at limiting the extent of planned protests during his inauguration. The strategy, whilst limited to only a handful of prominent individuals, has likely been designed to limit the abilities of key individuals to mobilise protests across Venezuela, as well as rally international support. The detention of foreign nationals is a common occurrence in Venezuela and is often done to portray the idea that the opposition is corrupt and influenced by enemies of the state. Moreover, foreign nationals with current or past associations with foreign governments or militaries are most at risk of being detained, regardless of their true motivations.
Despite the arrests, major disruptive protests in multiple Venezuelan towns and cities during the inauguration are highly likely and will almost certainly be violently suppressed by the government. There is also a realistic possibility of targeted attacks on the inauguration. In 2018, two uncrewed aerial vehicles (UAVs) detonated explosives in Caracas near where Maduro was addressing the Bolivarian National Guard. While some have dismissed this as a false flag attack aimed to bolster support for the regime, the high-profile nature of the inauguration and proliferation of UAV technology likely increase the credibility of such a threat.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
Greenland PM pushes for independence as Trump row resumes
The Prime Minister of the Danish autonomous territory, Mute Egede, called for an acceleration of the process to secure independence from the Danish crown. Greenlandic independence is contemplated under the self-rule law of 2009, which posits that it would need to be approved via a referendum. While Egede is part of a well-established independentist movement, the recent comments were almost certainly prompted by US President-elect Donald Trump’s call for the US to buy the strategically important territory from Denmark. In addition to massive reserves of natural resources, Greenland is positioned to strategically control the Arctic, an area where both the US and Russia are increasingly looking to strengthen their positions.
Trinidad and Tobago prime minister to resign before end of term
Prime Minister Keith Rowley announced his plans not to seek re-election and to vacate his post before the end of his term in August 2025. The announcement comes at a time when Trinidad and Tobago struggles with increasing rates of gun violence, which have prompted the government to issue a state of emergency. The ruling People’s National Movement (PNM) will now have to nominate a replacement for Rowley, who will be then appointed by the President.
Venezuela and Paraguay sever diplomatic ties
On 6 January, Venezuela and Paraguay severed diplomatic ties after Paraguayan President Santiago Pena expressed support for Venezuela’s opposition. Pena spoke with opposition leaders and backed Edmundo Gonzalez, who is in exile and whom the opposition claims won the 2024 Venezuelan presidential elections, after an election marred by accusations of fraud.
Security, Armed Conflict and Terror
Artificial intelligence reportedly used in Las Vegas Cybertruck attack
On 31 December, US Army solider Matthew Livelsberger detonated an improvised explosive device (IED) inside of a Tesla Cybertruck outside of the Trump International Hotel in Las Vegas. Authorities have confirmed that Livelsberger had used the AI chatbot ChatGPT to plan the attack, which would mark the first known use of the platform in support of the development of an IED. The incident has triggered concerns over how easily available AI can be exploited for nefarious means and will likely contribute to demands for stricter regulations on AI platforms.
Central American police arrive in Haiti to reinforce United Nations mission
The first group of a planned 150 military police officers, mostly from Guatemala and El Salvador, arrived in the country to bolster the UN mission, which has so far been led by their Kenyan counterparts.
UN operations in Haiti have so far been relatively unsuccessful at deterring and containing the gangs that control much of the country. The gangs have implemented a terror-reliant strategy, characterised by attacks on hospitals, airports, civil society groups and NGOs, aimed at preventing other actors from establishing control in parts of Haiti, and at maintaining the local civilian population reliant on criminal networks.
It is highly likely that the new deployments will result in a harsh reaction by local gangs, who may accelerate attacks on transport hubs in Port-au-Prince, or carry out killings among the local civilians.
With no involvement by major international players like the US or France, it is unlikely that small countries’ deployment of police forces will manage to stabilise the situation in Haiti in the short term.
Environment, Health and Miscellaneous
Polar vortex in the US and Canada
A polar vortex continues to bring severe winter weather to the US and Canada, prompting widespread disruptions. Georgia’s Governor Brian Kemp has declared a State of Emergency ahead of a winter storm expected on 10 January.
Tennessee’s National Weather Service issued a winter storm warning for Middle Tennessee, forecasting major travel disruptions. In Virginia, Henrico and east Goochland counties remain under a boil water advisory due to storm damage at a Richmond water treatment plant.
Schools in North Texas, including districts like Denton, Dallas, and Fort Worth, have closed for 9 and 10 January. The polar vortex has already triggered a state of local disaster declaration in Saline County, Kansas, after record-breaking snowfall. Power outages have affected thousands in Kentucky, southwestern Indiana, and southeastern Illinois, with restoration ongoing. In Richmond, water production has resumed, though the boil water advisory continues.
Extreme heat and wildfire threat across Chile
Chile’s National System for Disaster Prevention and Response (SENAPRED) has issued multiple yellow alerts across the country warning of intense heat. Yellow alerts have been issued for the Valparaiso, Bio Bio, Maule and metropolitan region which includes the capital, Santiago. Temperatures are set to approach 40 degrees Celsius in several places and are likely to cause or exacerbate many of the wildfires Chile is currently struggling to contain.
Europe, Middle East & Africa
Austria: Freedom Party (FPÖ) gets mandate to lead government
On 6 January, Herbert Kickl, the FPÖ leader, was tasked by President Van der Bellen with forming a new government, after Austrian People’s Party (ÖVP) leader and Chancellor Karl Nehammer failed to do so.
FPÖ won the most votes, 28.8 per cent, at Austria’s parliamentary election in September, while the OVP finished second with 21 per cent.
ÖVP’s efforts to form a coalition with the Social Democrats and the liberal Neos failed over disagreements on key policy issues, leading Nehammer to hand in his resignation as chancellor (Nehammer will be replaced on 10 January by Alexander Schallenberg, who will rule until a new government is appointed).
Solace Global Assessment:
As every other Austrian party has refused to form a coalition with FPÖ, the party’s only option is to make a deal with the ÖVP. The FPÖ has already been in multiple governing coalitions with ÖVP, always as a junior partner (2000-2005, 2017-2019). This time, the party will almost certainly demand the chancellorship, as well as other key government roles. FPÖ currently bargains from a position of strength, as a decision to walk away from the talks would highly likely trigger new elections, where the party would almost certainly improve on its previous vote tally (currently, polls project FPÖ would win 36 per cent of the vote, with ÖVP falling to 21 per cent).
A government led by Kickl, were it to follow FPÖ’s stated policy proposals, would almost certainly drive an increase in civil unrest in Austria.
Some of FPÖ’s pledges are extremely controversial, such as the restriction of welfare benefits to citizens alone, the banning of “political Islam”, and “remigration” – the return of citizens of non-European ethnic backgrounds to the countries their families originate from.
In addition to almost certainly clashing with multiple European institutions and treaties, these proposals are likely to provoke a reaction from multiple civil society actors both on the left and the centre and may likewise drive an increase in political violence. Moreover, FPÖ’s anti-Islam policies are likely to be leveraged by extremist actors to drive recruitment in Austria, increasing the risk of radicalisation and terrorism.
Ukraine & Russia: Ukrainian forces launch a limited counteroffensive in the Kursk salient
On 5 January, the Armed Forces of Ukraine (AFU) launched a limited mechanised offensive against Russian positions in the Kursk salient. AFU forces advanced northeast of Sudzha into Berdin and Novosotnitskii. Initially, the Ukrainian General Staff described the operation as a “new offensive”, however, the Telegram statement was later edited to remove this. Russian forces, meanwhile, reportedly attacked the villages of Malaya Loknya, Sverdlikovo, and Leonidovo from the Kursk salient’s western flank.
Solace Global Assessment:
The surprise August 2024 Ukrainian offensive into Kursk Oblast rapidly captured ground and temporarily shifted the ‘narrative’ of the conflict. By successfully capturing ground in internationally recognised Russian territory, Kyiv was highly likely hoping to divert considerable Russian forces from offensives in Donetsk and to provide a ‘win’ in the face of increasing Russian momentum in the war. The Kursk offensive, however, was contained without a strategically decisive diversion of forces (the deployment of North Korean personnel to the Oblast is almost certainly part of this effort) and Russia has been gradually but slowly pushing back Ukrainian forces in the north and west of the Kursk salient over the last few months.
It is likely that the current limited offensive operation by the AFU in the east-northeast of the salient has been calculated to exploit potential weaknesses in Russia’s defensive position – Russian forces have focused offensive efforts in the north and west. A breakthrough in the vicinity of Berdin could threaten the outmanoeuvring of Russian forces positioned in the salient’s north, although the diversion of Ukrainian forces from defensive efforts elsewhere in the Kursk salient is risky and has likely factored into the past week’s attempted Russian advances. In addition to the potential tactical advantage, there is a realistic possibility that the limited Ukrainian counteroffensive could have been a probing operation to test the strength of Russian defences in support of a more significant future counteroffensive – Kyiv likely seeks to have a ‘win’ before Trump is inaugurated on 20 January and any territorial gains could put it in a stronger position during anticipated peace negotiations.
Any notable Ukrainian advances would highly likely be met by retaliation by the Kremlin, as part of Russia’s strategy of deterrence. The most likely retaliation would involve significant (larger than in general) long-range strikes using missiles and one-way attack uncrewed aerial vehicles (OWA-UAVs) against Ukraine’s major urban centres, possibly using the new Oreshnik intermediate-range ballistic missile (IRBM). The use of the Oreshnik with a non-nuclear conventional warhead has likely enabled Putin to reduce nuclear brinkmanship, by providing a means of escalatory retaliation without having to resort to a tactical nuclear strike.
Benin: Benin armed forces suffer major casualties in northern attack
On 9 January, the Benin army suffered heavy losses after one of its most well-defended positions was attacked in the north of the country. Beninese troops had been stationed in the area to prevent cross-border attacks from neighbouring Burkina Faso and Niger, where there are ongoing Islamist insurgencies. The military did not disclose a casualty count; however, the main opposition party has suggested around 30 soldiers were killed in the attack.
Solace Global Assessment:
The attack marks one of the worst losses for the Benin Armed Forces since the escalation of the Islamist insurgencies in the Sahel.
No group has currently claimed responsibility for the attack; however, it is highly likely that it was conducted by the al-Qaeda affiliated Jama’at Nusrat al-Islam wal-Muslimin (JNIM). JNIM, which has initiated an insurgency in neighbouring northern Togo, is likely attempting to achieve several objectives in Benin and the wider West African region.
JNIM’s strategy likely involves establishing a buffer zone by destabilising the areas of countries adjacent to its key area of operations in Burkina Faso and Niger. Such a buffer zone would provide JNIM greater freedom of movement and fix regional militaries within the coastal nations, limiting their ability and will to deploy resources to the Sahel.
A destabilised northern Benin would also provide JNIM with greater opportunities to increase both its revenue and recruitment, with major attacks demonstrating its growing capabilities.
Should JNIM succeed in recruiting disenfranchised Muslims from Benin, this will provide the extremist group with expanded local knowledge and capabilities but would also free up Sahelian fighters to focus on operations within the Sahel itself.
Moreover, with the sustained trend of Western forces being expelled from the region, extremist groups like JNIM will find it easier to expand their operations unless countries like Benin agree to the hosting of Western forces on their soil.
In the long term, if JNIM successfully destabilises the north and establishes a presence there, it could expand its operations further south, ultimately threatening coastal capitals like Porto-Novo and Lomé- coveted targets due to their strategic location and symbolic value.
Chad: Chadian authorities claim to have repelled attack on presidential palace
On 9 January, Chadian authorities claim that 24 individuals armed with knives and machetes attempted to storm the presidential palace with President Mahamat Deby Itno inside. According to authorities, some vehicles appeared to break down at the entrance of the palace before the assailants walked out and stabbed the four entrance guards, killing one. Guards reportedly shot at the assailants, killing 18 and arresting six, repelling the attack.
Solace Global Assessment:
The apparent attack comes shortly after Chad held elections, with results planned to be released on 15 January. There is significant speculation regarding whether the incident was conducted by Boko Haram, a rival military faction, another armed insurgent group, staged by the government, or the result of confusion with an armed group of civilians. Given the reliance on knives and machetes and relative disorganisation, the attack is unlikely to constitute a coup attempt by a rival military faction.
While Boko Haram typically uses firearms and explosives, there is a realistic possibility that the assailants were associated with the terrorist group, who may have been taking advantage of the withdrawal of French forces in December 2024.
Alternatively, a government-staged coup attempt would likely provide the government with a pretext to bolster security ahead of expected protests. However, authorities appear to be playing down the significance of the attack, implying they were akin to drunken “Pieds Nickeles”. This could indicate an attempt to minimise the threat of armed groups and project stability ahead of the expected election victory. Alternatively, there is a realistic possibility that security forces mistakenly perceived a group of workers as a threat and shot them before they could attack the presidential palace.
Mozambique: Opposition leader Venâncio Mondlane arrives in Mozambique
According to local NGOs, approximately 289 people have been killed in Mozambique since the post-election unrest began. The most recent “TurboV8” phase resulted in the highest death toll of any phase so far and was set to be followed by the “ponta de lança” (spearhead) phase. However, this stage was subsequently postponed due to fears of opposition candidate Venâncio Mondlane’s assassination. Supporters threatened to block all roads if Mondlane did not appear live on Facebook,, which he did on 6 January.
After announcing his return to the capital Maputo, Mondlane arrived in Mozambique on 9 January ahead of the 15 January inauguration of President-elect Daniel Chapo. Mondlane asked his supporters to “welcome” him at Maputo International Airport (MPM) at 08:05 local time. After greeting Mondlane, a procession of people accompanied Mondlane’s car from the airport to the centre of Maputo. Mondlane then spoke at the Mercado Estrela at approximately 10:00 local time, whereby he reaffirmed his claims of an election victory. Security forces subsequently used live ammunition and tear gas in central Maputo to disperse crowds gathered in support of Mondlane, reportedly charging at the crowd and triggering a stampede.
Solace Global Assessment:
Despite speculation over whether authorities would attempt to arrest Mondlane upon arrival, Mozambique’s Supreme Court has announced that no arrest warrant has currently been issued. However, the Public Prosecutor’s Office has reportedly opened proceedings against Mondlane as the architect of the unrest. If the government targets Mondlane via arrest or assassination, significant unrest will almost certainly take place. In the long term, however, the loss of Mondlane’s leadership may enable the government to suppress demonstrations through curfews and mass arrests, with protests likely to diminish in the absence of his ability to mobilise the opposition.
On 6 January, Frelimo announced the next key dates in the electoral process. In addition to the inauguration of the parliament and president on 13 and 15 January, the date for the destruction of the 9 October election materials was announced as the 22 January. If the government is still in power on 22 January, demonstrations will almost certainly occur on this date as it will likely be perceived as the final step in the government’s consolidation of power following the election. There is a realistic possibility that protesters will target Frelimo offices, particularly in Maputo, in order to prevent the potential destruction of evidence of alleged electoral fraud.
Mondlane continues to state that he will take office on 15 January and that he will announce further details of the new phase of unrest titled “ponta de lança” (spearhead). Significant demonstrations are almost certain in the lead up to the inauguration. There is a realistic possibility that Frelimo will use Mondlane’s presence in country and attempt to inaugurate himself as president as proof of an ongoing coup. If this happens, the government will likely accelerate efforts to crack down on demonstrations and delegitimise Mondlane, who will pose a significant threat to the government’s legitimacy given he appears to have the backing of the majority of the population.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Romania sets date for presidential election repeat
The new vote will take place in two rounds on 4 and 18 May. The previous elections were annulled by the judiciary after the first round on 24 November 2024 as Calin Georgescu, a virtually unknown independent candidate who largely campaigned on social media espousing anti-establishment, anti-NATO and anti-EU positions, won the most votes. The Constitutional Court’s decision was explained as a reaction to allegedly widespread Russian meddling in the campaign, although no claims of direct interference in the voting process were reported.
Georgescu’s bid for the presidency has been boosted by the first vote’s annulment, and he remains the favourite to win in May. However, there is a realistic possibility that Georgescu will not be allowed to run, as the Constitutional Court may declare him ineligible over funding irregularities during the first campaign. If this were to happen, there would be a high likelihood of severe civil unrest in Romania, with other anti-establishment candidates and parties likely to throw their political weight behind Georgescu.
Georgian protests continue as non-recognition bill set to be proposed by US Congress
Anti-government protests continue in Georgia, notably on Orthodox Christmas Eve (7 January) when thousands set off from churches and converged at the church opposite the parliament building. A bill is set to be introduced to the US Congress that will prohibit recognition of the Georgian Dream government. The bill is quoted as making specific reference to Bidzina Ivanishvili, the oligarch and founder of Georgian Dream who was sanctioned by the US in December 2024.
Salome Zourabichvili, a figurehead for the pro-Europe opposition who was ousted as president in a contested December indirect election, continues to claim to be the legitimate president of Georgia. On 9 January, Zourabichvili told journalists that she will travel to the US to attend Donald Trump’s 20 January presidential inauguration, after being invited by a US Congress member.
There are numerous US politicians sympathetic to the pro-Europe Georgian opposition movement – it is likely that significant international pressure from the US would embolden the protest movement, but also further isolate the Georgian Dream government which could accelerate its alignment with Moscow.
Lebanon’s parliament elects new president after two-year vacancy
Following two rounds of voting held in Lebanon’s parliament on 9 January, the commander of the Lebanese Armed Forces, Joseph Aoun, was elected as the fourteenth President of the Lebanese Republic.
The presidency must be occupied by a Maronite Christian, according to Lebanon’s constitution. As Lebanon is a parliamentary republic, the presidency is a predominantly ceremonial role, though can still wield considerable discretionary reserve powers. The presidency has been vacant since 2022 due to political divisions, with Lebanon’s political system struggling since the end of the previous president’s, Michel Aoun (not related), term. Lebanon has struggled with the aftermath of the 2020 Beirut port explosion, chronic economic crisis and Israel’s military operations against Lebanese Hezbollah.
Joseph Aoun’s election will likely bolster Lebanon’s political stability. With approval from the US, Aoun’s election is likely indicative of the declining influence of Hezbollah in Lebanon after being severely degraded by the Israel Defense Forces (IDF). As per the terms of the ceasefire agreement, the IDF’s 60-day withdrawal period from Lebanon expires on 26 January – with this deadline looming, fears regarding the state of the ceasefire, if the IDF continues to occupy areas of southern Lebanon, have likely pressured Lebanese lawmakers to elect Aoun who will continue to have a key role in maintaining the ceasefire.
Security, Armed Conflict and Terror
Attempted attack on Belgian prime minister
On 6 January, Belgian Prime Minister Alexander De Croo was targeted in a knife attack outside his home, though the perpetrator was arrested. Little is currently known about the assailant; however, the incident likely reflects a broader rise in violent attacks on political leaders. Uncorroborated reports indicate that the alleged attacker had attempted a similar attack on the US Embassy in Brussels in April.
Greek Anarchists plan “International Week of Action”
The organisation Revolutionary Struggle (RS) has announced a week of political action (between 10 and 16 January) in support of two of its members currently imprisoned in Chalcis. RS has claimed responsibility for carrying out bombings at multiple Greek ministry buildings, the Athens Stock Exchange, the Bank of Greece, the US Embassy in Athens, and IMF offices. There is a high likelihood that Anarchists will carry out attacks in the coming days, likely targeting buildings. There is a realistic possibility that other European Anarchist groups associated with RS, especially in Italy, Spain, and Germany, will carry out actions during the “week of action”.
Attack on Israeli vehicles near al-Funduq, West Bank, kills three and injures eight
The shooting was reportedly carried out by at least three individuals, who targeted civilian vehicles transiting on Route 55. While no claims of responsibility have been made for the attack, it was praised by other Palestinian militias. Israeli sources claimed that the attackers have been nevertheless identified as residents of Jenin. The attack will likely prompt an escalation in Israeli raids in the area, with additional incidents in the West Bank likely leading to increased clashes between Israeli settler communities and Palestinians.
Mali forces capture Islamic State leader
The armed forces of Mali announced the capture of Mahamad Ould Erkehile, alias Abou Hach, who is one of the key leaders of the Islamic State – Sahel Province (ISSP), formerly Islamic State Greater Sahara (ISGS). The operation leading to Abou Hach’s capture was carried out in the Amasrakad area of the Gao region.
There is a high likelihood that ISSP operatives will carry out retaliatory attacks against Malian security forces and civilians. Since the death of its leader Adnan Abu Walid al-Sahrawi in 2021, ISSP has sought to restructure its presence in areas of operations, gradually and partly shifting towards a strategy aimed at establishing a structured governance of local populations. This has however made its leaders more visible, allowing junta forces and their allies to carry out more successful decapitation strikes.
Ivory Coast to cut military ties with France
President Alassane Ouattara has announced that French troops are expected to leave the country in January. This makes the country the sixth to have cut military ties with Paris in Africa. The setback in the Ivory Coast follows Senegal’s and Chad’s recent ousting of French forces, and the previous fallout of relations between Paris and the Sahelian juntas.
France will likely have to turn to other regional powers to maintain a presence in the region. The reduction of France’s footprint elsewhere in West Africa and the Sahel has largely coincided with the growth of Russian operations in the region.
However, with Russia’s overextension having been demonstrated in Syria, and also through Wagner and Africa Corps forces’ failures in the Sahel, it is highly likely that the retrenchment of Western forces will leave a security vacuum that could be exploited by regional Islamist groups, who maintain a strategic aim to expand their presence towards the African coast.
M23 Movement captures strategic town in North Kivu
On 5 January, the M23 Movement captured the mineral-rich town of Masisi, the capital of the Masisi territory, 80 kilometres from North Kivu’s provincial capital Goma. Masisi is strategically important due to its richness in agriculture, livestock, and minerals as well as its access to Goma, a long-term target for M23.
Some conflicting reports indicate that the Armed Forces of the Democratic Republic of the Congo (FARDC) alongside its allies, the Wazalendo, a group of irregular forces allied with the military, may have regained control of Masisi. The mixed reporting indicates that the territory is likely contested, with the FARDC launching offensives to recapture the town.
The M23 rebels have recently made significant gains in North Kivu, seizing control of Katale near Masisi. Fighting in other areas of Masisi territory, including Sake and Ngungu also occurred over the past week, reportedly causing approximately 100,000 people to be displaced.
Environment, Health and Miscellaneous
Storm Floriane causes disruptions in France and Sweden
Storm Floriane caused significant disruptions across Europe, starting in France on 6 January with orange weather alerts being issued due to strong winds. The worst-hit regions in northern France, such as Charleville-Mézières, Châlons-en-Champagne, and Bar-le-Duc, experienced gusts between 80 and 110 km/h. Rail travel was particularly affected due to cancellations, delays, and speed restrictions.
The winter storm then moved across the North Sea into Sweden, bringing violent wind speeds and heavy snowfall, leading to extensive travel disruptions. The Swedish Meteorological and Hydrological Institute issued 28 weather warnings. Train routes were closed due to fallen trees and debris, and public transport services were delayed or cancelled.
Storm Dikeledi, tracking towards northern Madagascar, forecast to become tropical cyclone
Forming on 7 January in the southern Indian Ocean, the low-pressure storm system Dikeledi is tracking westwards towards northern Madagascar. The storm is forecast to strengthen into a tropical cyclone with potential maximum windspeeds of 179 km/h and is expected to make landfall in northern Madagascar between 11-12 January. The Madagascan regions most likely to be impacted are Diana, Sava and Ambatosoa.
In addition to Madagascar, Mozambique and Malawi could also be impacted, with meteorological authorities from both countries issuing statements urging their populations to monitor for potential weather warnings. Depending on the direction the storm system takes, the French overseas island of Mayotte could also be impacted.
Mayotte was recently devastated by Cyclone Chido in December 2024, it is likely that heavy rainfall from Dikeledi could further hamper ongoing recovery efforts.
Asia–Pacific
China: 7.1 magnitude earthquake hits southern Tibet
At 09:05 local time (01:05 UTC) on 7 January, a powerful magnitude 7.1 earthquake struck Tingri County in southern Tibet. The epicentre was located approximately 80 kilometres north of Mount Everest at a depth of ten kilometres. The main tremor was followed by aftershocks of above 5.0 magnitude. The earthquake has caused widespread damage across Tingri County, including the city of Shigatse. Tremors were also felt in neighbouring countries, including Nepal and northern India, although no significant damage has so far been reported in these locations.
Initial reports confirm at least 126 fatalities, with more than 1,000 buildings damaged or destroyed. While the mountainous Tingri County is scarcely populated, approximately 7,000 people live within 20 kilometres of the epicentre. The city of Shigatse, the second largest in Tibet, has around 800,000 residents. Local sources reported that the earthquake has disrupted local power and water supplies, and damage to local roadways has also been recorded. In January, the area has daily minimum temperatures of below -15 degrees Celsius, and daily average temperatures of -7.5 degrees Celsius.
Solace Global Assessment:
The earthquake is one of the deadliest China has experienced in recent years. On 23 January 2024, a magnitude 7.0 earthquake struck Xinjiang, China. The death count was significantly lower, however, with only three deaths. In 2008, a large earthquake in Sichuan province killed nearly 70,000 people. Southwestern regions of China are frequently affected by earthquakes. This is largely due to the region lying at the convergence zone of the Indian Plate and Eurasian Plate, which periodically releases tectonic stress as earthquakes. Furthermore, the region has numerous active fault systems including the Longmenshan Fault Zone, which triggered the 2008 earthquake, and the Xianshuihe Fault Zone.
The Lhasa block, also known as the Lhasa terrane, is a significant geological region in southern Tibet, situated between the Bangong-Nujiang suture zone to the north and the Indus–Yarlung Zangbo suture zone to the south. This positioning generates north-south compression, resulting in crustal shortening and uplift, as well as west-east stress, which drives lateral crustal movements. These geological processes play a crucial role in the formation of the Himalayas and significantly impact regional fault systems and seismic activity. Several aftershocks were felt in Tibet and Nepal; further aftershocks are highly likely in the coming days.
The government’s response to the earthquake is likely to be viewed through the lens of historical Tibetan grievances. Given the mountainous topography of the region and potential aftershocks, relief efforts will likely be hampered, potentially opening the government up for criticism regarding its effectiveness at governing in the region. In the aftermath of the earthquake, there is a realistic possibility that those sympathetic to Tibetan independence will scrutinise the government response and call for self-determination.
Taiwan: Taiwan accuses China of deliberate undersea sabotage
Taiwanese authorities are investigating a Chinese-linked ship which they suspect of deliberately dragging its anchor over an undersea fibre optic cable which connects Taiwan to the US. The Cameroon-registered and Tanzania-flagged vessel Shunxing 39 (IMO: 8358427) was briefly detained by Taiwan’s coastguard on 3 January but was subsequently released. Chunghwa Telecom of Taiwan stated that services across the island were largely unaffected and that it had promptly redirected data through alternative cables.
Solace Global Assessment:
Unconfirmed reports indicate that this may be the 21st Chinese attempt to sever Taiwan’s undersea internet infrastructure. As an island nation, with approximately only a dozen undersea internet cables landing on its shores, Taiwan is highly vulnerable to undersea sabotage. Despite attempts to accelerate its development of satellite-based backup systems to ensure connectivity during crises, this technology is in its infancy and cannot provide adequate redundancy. China likely calculates that the severing of multiple cables simultaneously would help to isolate Taiwan and hugely damage its economy. It is highly likely that if this is observed, it would be indicative of shaping activity for a full-scale invasion of Taiwan.
Like Russia, China commands a huge fleet of civilian-flagged vessels which answer directly to the state. Beijing has almost certainly observed Russia’s increased use of civilian vessels to conduct low-cost, hard-to-prove, and deniable acts of undersea sabotage and will likely continue to incorporate this into its own “grey zone” strategy. While China’s primary target for undersea sabotage is Taiwan, there is a realistic possibility that these incidents will migrate to other regions, particularly those heavily dependent on critical undersea infrastructure. This could include areas in the South China Sea, in the waters around South Korea and Japan, and further afield as China continues to expand its maritime presence.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Second arrest warrant issued for President Yoon Suk Yeol
A fresh arrest warrant has been issued for President Yoon after police failed to execute the first one, which ended 6 January. Investigators were prevented from entering the presidential palace, blocked by supporters and security. The chief prosecutor, Oh Dong Woon, has declared that he will “prepare thoroughly” for the second attempt to arrest Yoon, implying that it may be the final opportunity to arrest him. Yoon will almost certainly use his security and supporters again to prevent investigators from executing the warrant. On 9 January, Yoon declared that he would accept the decision of the Constitutional Court if it decides to back the impeachment case. This is almost certainly with the aim of moving on from the incident and dissuading prosecutors from conducting further attempts to arrest him.
Indonesia to joins BRICS
Jakarta’s bid to join the group was approved in 2023. Indonesia’s accession to BRICS almost certainly represents a major development in the country’s traditionally “non-aligned” foreign policy stance However, it is unclear to what extent it will trigger significant regional security developments. Indonesia, like fellow BRICS member India, maintains warm ties to the West, and is concerned about China’s footprint in the region. There is a realistic possibility that Indonesia’s foreign policy will continue to maintain elements of non-alignment while using BRICS to improve Jakarta’s range of foreign policy options.
Security, Armed Conflict and Terror
Eight police officers and driver killed in Maoist attack in Chhattisgarh, India
On 6 January, a bomb blast killed at least eight police officers and a driver. The bomb was reportedly planted by Maoist Naxalite group in the latest of a series of attacks targeting security forces. The Naxalite movement began in 1967 in West Bengal and gained traction in Chhattisgarh in the late 1980s. The government has responded by deploying paramilitary forces and local police to combat the Naxalite group. While the intensity of the insurgency has seen a decline in recent years, it is an ongoing challenge for the government, with sporadic attacks occurring in central India.
Bomb blast injures three police officers in southern Thailand
An improvised explosive device (IED) detonated in front of a school in Sai Buri on 3 January. The device was reportedly placed near a “stop” sign the police left near the school while they were off duty. It is highly likely that the perpetrators of the blast were local separatist insurgents. A low-intensity civil conflict has been ongoing for more than 50 years in southern Thailand, including the Patani region where Sai Buri is located, driven by groups like the Patani United Liberation Organisation, which aim at separating the majority-Malay Muslim south from the rest of the country. Local media posited that the blast may have been planned to coincide with the 20th anniversary of a raid on a military camp in the Cho Airong district of Narathiwat, which represented a significant escalation in the civil conflict.
Former Cambodian politician assassinated in Bangkok
On 7 January, Lim Kimya, a 74-year-old former Cambodian opposition lawmaker and dual Cambodian-French citizen, was fatally shot in Bangkok’s Old Quarter shortly after arriving from Cambodia. Thai authorities have issued an arrest warrant for a 41-year-old motorcycle taxi driver suspected of the murder. The suspect is believed to be a Thai national and has acted as a hitman. Lim Kimya was associated with the Cambodia National Rescue Party (CNRP), an opposition group dissolved ahead of the 2018 election amid controversial treason charges. Human Rights Watch has called for a thorough investigation, noting the harassment of former CNRP members by the Cambodian government. Despite denying any involvement, there are major suspicions that this was an assassination sponsored by the Cambodian government which could trigger a diplomatic spat between the two Southeast Asian countries.
Environment, Health and Miscellaneous
Increase in hMPV cases in China
China is dealing with a rise in human metapneumovirus (hMPV) cases, particularly in the north of the country, as well as other seasonal respiratory illnesses like influenza and respiratory syncytial virus (RSV). However, the World Health Organization (WHO) and the European Centre for Disease Prevention and Control (ECDC) confirm that these levels remain within the expected seasonal range, and there is no indication of a pandemic-like threat. China’s healthcare system is operating within capacity, with hospital utilisation lower than the previous year, and no emergency response has been initiated. Symptoms are typically mild, resembling the common cold or flu, with severe cases being rare and mostly affecting vulnerable populations.
Fire at market in Zhangjiakou, Hebei province, China kills at least eight
At approximately 08:40 local time on 4 January, a fire broke out at the Liguang vegetable market, a busy market in Zhangjiakou, killing eight and wounding 15. The blaze took approximately two hours to extinguish. Relaxed building codes in China increase the likelihood of fires. Furthermore, traditional markets in China are typically tightly packed, exacerbating the risk to shoppers by making it difficult to escape potential fires.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence

Power Outages and Evacuations Across LA Amidst Growing Wildfires
Intelligence cut off: 15:00 GMT 08 January 2025
Fast moving wildfires are currently ongoing in California. At least three separate blazes are currently ongoing around the Pacific Palisades (Palisades Fire), Pasadena (Eaton Fire), and Sylmar (Hurst Fire) neighborhoods of Los Angeles.
The Palisades Fire has burned through over 3,000 acres, causing significant damage, including the destruction of beachfront homes in Malibu; the Eaton Fire has spread to 1,000 acres; the Hurst Fire has grown to 500 acres. None of the wildfires have been contained as of the time of writing.
No deaths have been reported so far. Over 1,400 firefighting personnel have been deployed to combat the blazes and Governor Gavin Newsom declared a state of emergency.
Mandatory evacuation orders have been issued for over 80,000 people in Southern California. The Palisades Fire has triggered mandatory evacuation orders for the Pacific Palisades and surrounding areas. Residents in Malibu not currently under evacuation orders have been informed that they should prepare for evacuation anyway due to the how fast the wildfires are moving. A smoke advisory is in place around the Malibu Coast, Santa Monica, and Beverly Hills.
The Eaton Fire has prompted mandatory evacuation orders for the area north of Orange Grove/Rosemead Boulevard, east of Lake Avenue, and west of Michillinda Avenue. The Hurst Fire has triggered evacuation orders for northwest Sylmar and surrounding areas.
Major roads including Sunset Boulevard and part of the Pacific Coast Highway became gridlocked as residents fled the wildfires. Highway lanes near Topanga Canyon Boulevard closed due to the wildfire’s fast expansion. Drivers abandoned their cars on Sunset Boulevard, forcing The Los Angeles Fire Department to deploy bulldozers to Subset Boulevard to allow fire crews to pass abandoned vehicles.
The extreme conditions have resulted in widespread power outages, affecting more than 200,000 customers in Los Angeles County. Emergency shelters have been opened at Westwood Recreation Center and Ritchie Valens Recreation Center for evacuees from the Hurst and Palisades fires.
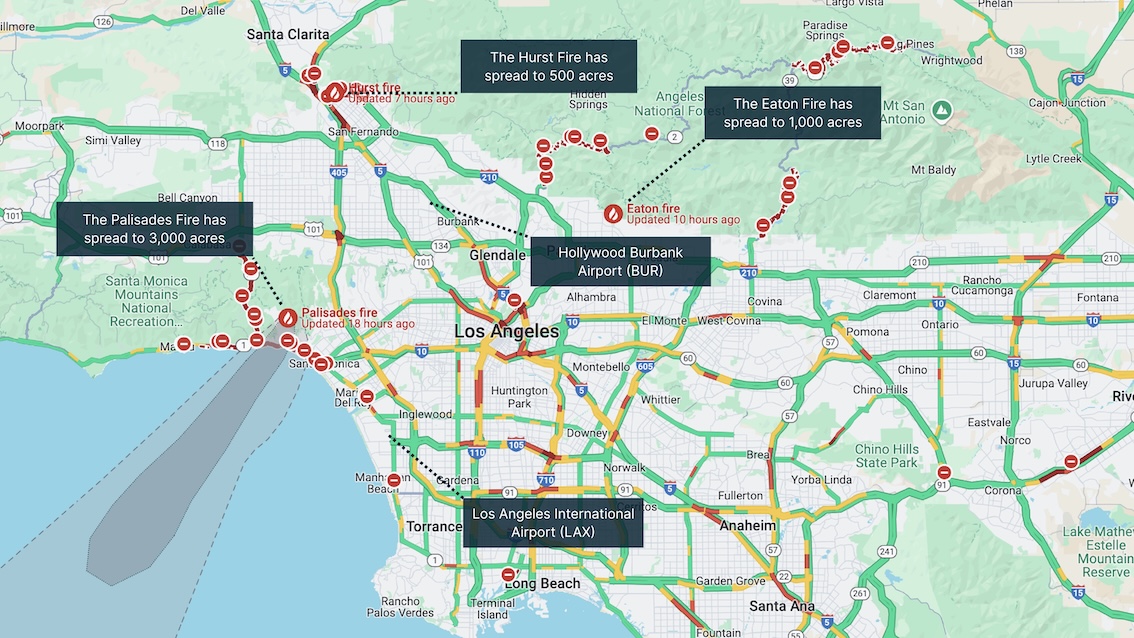
Map of the Palisades, Eaton, and Hurst fires to the north and west of Los Angeles.
SOLACE GLOBAL COMMENT
Evacuation and Response to 2025 LA Wildfires
The fires began on 7 January after a bush fire was caught by a windstorm, spreading the fire into surrounding areas. California is currently affected by the northeasterly Santa Ana winds, which are caused by high pressure over the Great Basin. These winds have fuelled many of California’s worst wildfires in the past, including the 2018 Woolsey fire, which killed three people.
The winds have reached speeds of approximately 100 km/h, and could reach 160 km/h in the mountains and foothills, areas which have not experienced substantial rain for months. Winds are expected to worsen on 8 January and continue into 9 January. They will highly likely continue to spread the wildfire, despite the fire department’s efforts.
Peak wildfire season in California typically occurs between July and October each year. Although wildfires are unusual in January, high winds have combined with particularly dry conditions in California to contribute to fertile conditions for the wildfire to spread. Rains of over 0.25 centimetres have not been experienced in Southern California since May 2024. The Santa Ana winds have exacerbated the dry conditions by reducing the humidity levels.
Fire hydrants have reportedly run out of water in the Palisades area. While water tanks are currently being used to supply water to fire fighters, this severely limits the extent to which the fire department can tackle the ongoing wildfires. The reason for the water shortage is currently unknown, but water shortages at fire hydrants may occur because of power outages, high demand during large fires, broken water mains, or drought conditions. Given the recent dry weather, the issues are likely influenced by low water supplies in Southern California.
The northeasterly winds are reportedly pushing smoke southwest towards Malibu. The South Coast Air Quality Management District (AQMD) predicts that PM2.5 levels will remain in the Unhealthy category in the Air Quality Index. Authorities have advised that residents utilise respirators when outside.
INTELLIGENCE ANALYSIS
Wildfire Spread in Southern California: High Winds and Infrastructure Strain
The fire department will highly likely continue to struggle to contain the fires. Increasing windspeeds and dry conditions already make it difficult to prevent the fast spread of the fire. This issue is exacerbated by the water shortages in the Palisades area, which is the location of the largest wildfire. Furthermore, the high windspeeds have meant that they have been unable to launch firefighting aircraft.
Given windspeeds are set to increase over the course of 8 January, wildfires are highly unlikely to die down over the next 24 hours. Despite the fire department utilising bulldozers to clear roads, the large quantities of abandoned vehicles will highly likely continue to hinder fire fighting operations.
Fire hydrants running out of water is not unprecedented. Recently, fire departments encountered low water pressure when tackling wildfires in Camarillo, California in November 2024, causing two water pumps to become inactive. While this slowed firefighting efforts, firefighters prioritised life-saving missions over protecting property and reportedly reduced the potential fatalities. Similar focus will almost certainly be employed in the Palisades area, where there is a water shortage.
In the aftermath of the wildfires, residents who have had their property destroyed are likely to ask questions regarding the lack of water in the fire hydrants. Much of California’s water infrastructure was built in the 1960s and 1970s, lacking advanced modern technology and prone to leaks and inefficiency. Given California has one of the highest water needs in the US, the government is likely to come under increasing pressure to modernise California’s water infrastructure in the months following the wildfire.
United Airlines has issued a travel waiver enabling itinerary changes for flights booked out of Hollywood Burbank Airport (BUR) and Los Angeles International Airport (LAX) between 7 and 9 January. Some flights into BUR, situated approximately in the middle of the three wildfires, have been diverted to LAX because of smoke from the fires. LAX has not yet had significant flight disruptions but is approximately 30 kilometres south of the Pacific Palisades.
The Palisades fire is currently burning in a westerly direction, according to the Los Angeles Fire Department. Therefore, there is a realistic possibility that LAX will avoid significant disruptions. However, if there is a shift in winds causing the Palisades fire to spread further south, then it will likely result in significant airport disruptions. While significant shifts in Santa Ana winds are unlikely, changes in the pressure systems could influence the wind direction.
Travel Risk Advice: Precautions for LA Wildfire Zones
- Adhere to all evacuation warnings issued by authorities promptly.
- Do not attempt to extinguish fires on your own; leave firefighting to professionals.
- Pack a grab-and-go bag containing essential items such as water, a flashlight, a portable charger, important documents, non-perishable food, and first aid supplies.
- Stay informed by monitoring local news and official updates regarding the wildfire’s spread.
- Familiarise yourself with the locations of government-designated evacuation shelters.
- Wear protective clothing, including long-sleeved shirts, long trousers, gloves, and an N95 mask, to safeguard against smoke and heat exposure.
- Avoid using water unnecessarily if firefighters are operating in your area, as resources may be limited.
- Plan multiple escape routes in advance, considering possible congestion or blockages caused by fires.
- If driving, keep windows closed and set your vehicle’s air conditioning to recirculate to minimise smoke exposure.
- Drive cautiously and at reduced speeds in areas with poor visibility due to smoke.
- If you plan to fly, confirm flight status with your airline to avoid complications from cancellations.
- Do not return to your home until authorities officially declare it safe to do so.
- Be aware that smoke may persist in the air even after the wildfire is extinguished. Continue wearing an N95 mask when returning to affected areas.
Subscribe to free weekly intelligence

Widespread Damage in Tibet: Earthquake Strikes Near Mount Everest
Intelligence cut off: 11:00 GMT 07 January 2025
At 09:05 local time (01:05 UTC) on 7 January, a powerful magnitude 7.1 earthquake struck Tingri County in southern Tibet. The epicentre was located approximately 80 kilometres north of Mount Everest at a depth of ten kilometres. The main tremor was followed by aftershocks of above 5.0 magnitude. The earthquake has caused widespread damage across Tingri County, including the city of Shigatse. Tremors were also felt in neighbouring countries, including Nepal and northern India, although no significant damage has so far been reported in these locations.
Initial reports confirm at least 95 fatalities and over 130 injuries, with more than 1,000 buildings damaged or destroyed. While the mountainous Tingri County is scarcely populated, approximately 7,000 people live within 20 kilometres of the epicentre. The city of Shigatse, the second largest in Tibet, has around 800,000 residents.
Local sources reported that the earthquake has disrupted local power and water supplies, and damage to local roadways has also been recorded. In January, the area has daily minimum temperatures of below -15 degrees Celsius, and daily average temperatures of -7.5 degrees.
The Chinese Air Force has initiated rescue efforts and deployed drones to the affected area. At least 1,500 firefighters and rescue workers have also been dispatched, alongside supplies including cotton tents, quilts, and folding beds.
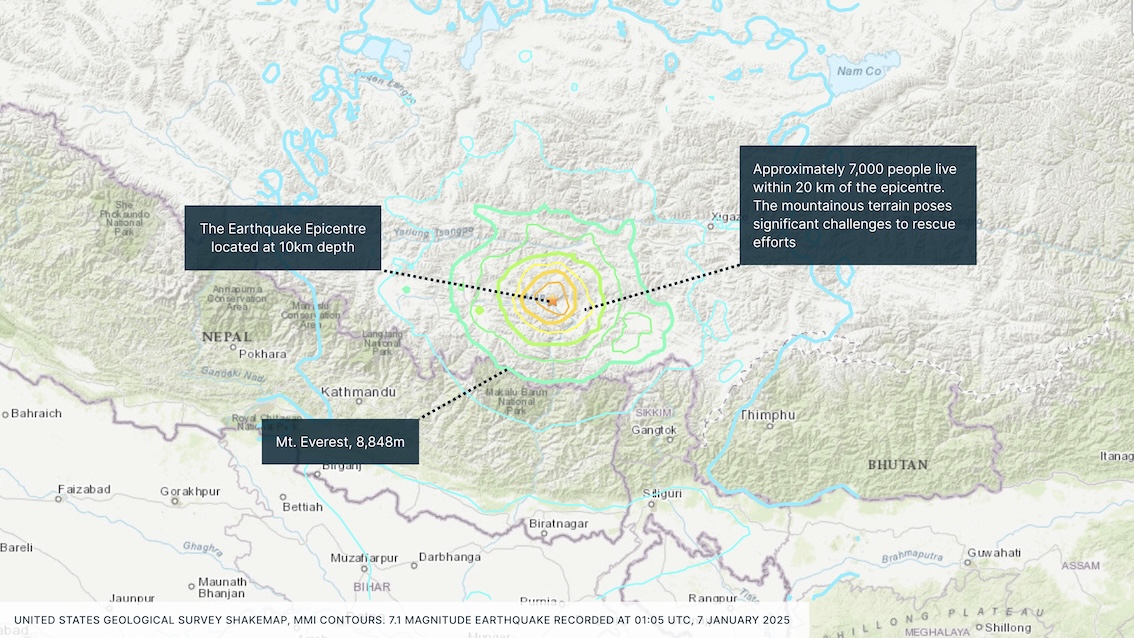
7.1 Magnitude earthquake recorded at 01:05 UTC, 7 January 2025. United States Geological Survey ShakeMap, MMI Contours
SOLACE GLOBAL COMMENT
Geological Context of 2025 Tibet Earthquake
The earthquake is one of the deadliest China has experienced in recent years. On 23 January 2024, a magnitude 7.0 earthquake struck Xinjiang, China. The death count was significantly lower, however, with only three deaths. In 2008, a large earthquake in Sichuan province killed nearly 70,000 people.
Southwestern regions of China are frequently affected by earthquakes. This is largely due to the region lying at the convergence zone of the Indian Plate and Eurasian Plate, which periodically releases tectonic stress as earthquakes. Furthermore, the region has numerous active fault systems including the Longmenshan Fault Zone, which triggered the 2008 earthquake, and the Xianshuihe Fault Zone.
The Lhasa block, also known as the Lhasa terrane, is a significant geological region in southern Tibet, situated between the Bangong-Nujiang suture zone to the north and the Indus–Yarlung Zangbo suture zone to the south. This positioning generates north-south compression, resulting in crustal shortening and uplift, as well as west-east stress, which drives lateral crustal movements. These geological processes play a crucial role in the formation of the Himalayas and significantly impact regional fault systems and seismic activity.
INTELLIGENCE ANALYSIS
Relief Challenges in Tibet: Topography, Aftershocks, and Political Scrutiny
While the United States Geological Survey measured the earthquake’s magnitude as 7.1, the China Earthquake Networks Center recorded a magnitude of 6.8. Differences in earthquake readings is relatively common due to the utilisation of different magnitude scales, algorithms, frequency sensitivity, distance from the epicentre, and the complexity of the fault movement.
Several aftershocks have already been felt in Tibet and Nepal; further aftershocks are highly likely in the coming days. While the aftershocks are unlikely to reach a similar magnitude to the initial earthquake, further aftershocks of approximately 5.0 magnitude may still occur. This could further damage structures that have already been weakened by the initial tremor and hinder relief efforts.
Power and water have been significantly disrupted in the region, which could further exacerbate humanitarian issues as residents cope with the aftermath. More deaths will almost certainly be confirmed as authorities verify fatalities amidst ongoing rescue efforts.
Shigatse, the closest city to the epicentre, is regarded as one of Tibet’s holiest cities and contains the Tashilhunpo Monestary which houses the seat of the Panchen Lama, a central figure in Tibetan Buddhism, second only to the Dalai Lama. It is an important pilgrimage site for Tibetan Buddhists. Furthermore, because of its proximity to the Nepalese border, it is an important trade hub. The earthquake will almost certainly disrupt trade through the region as recovery efforts continue.
The area is also a notable tourist site. Since Tingri county is located at the foot of Mount Everest, tourists often base themselves in the region. Mount Everest sightseeing tours have been cancelled in the aftermath. However, no significant damages were recorded at Mount Everest base camp.
The government’s response to the earthquake is likely to be viewed through the lens of historical Tibetan grievances. Given the mountainous topography of the region and potential aftershocks, relief efforts will likely be hampered, potentially opening the government up for criticism regarding its effectiveness at governing in the region. In the aftermath of the earthquake, there is a realistic possibility that those sympathetic to Tibetan independence will scrutinise the government response and call for self-determination.
Travel Risk Advice: Precautions for Tibet Erthquake Zones
- Closely monitor local news reports and government alerts
- Expect aftershocks. Be prepared to Drop, Cover, and Hold On in case of further tremors.
- During a tremor:
- If outside, avoid entering buildings. Move away from buildings, trees, streetlights, and overhead lines.
- If inside, pick a safe place, such as under a sturdy table or desk, or against an interior wall. Stay away from windows and heavy furniture. Do not leave until the shaking stops.
- If evacuating a building, always use the stairs.
- Be alert to fires and falling debris.
- Adhere to all instructions issued by authorities.
- Follow evacuation orders and travel to government-designated shelters if it is safe to do so.
- Ensure important documents and medications are safely stored.
- Prepare an emergency “go bag” with essentials, including bottled water, batteries, important documents, and medications.
- Confirm flights are operating before checking out of hotels or travelling to the airport.
- Prepare for potential power outages, communication disruptions, and travel delays.
- Avoid damaged buildings and affected areas until authorities declare them safe.
- Management should maintain communication with affected individuals until the situation is fully resolved.
Subscribe to free weekly intelligence

Solace Global Risk Expands with Acquisition of Independent AI Platform Nuraling to Elevate Security Offering
Solace Global Risk has officially acquired Nuraling, an independent artificial intelligence innovation, bringing tailored machine learning solutions to Solace Secure and other services. This collaboration strengthens our commitment to safeguarding people, assets, and reputations, offering our clients unparalleled control, privacy, and precision in managing risks globally.
Empowering Clients Through Advanced Technology
Nuraling’s platform empowers organisations to protect sensitive data, making it ideal for sectors where privacy and intellectual property are paramount. This ensures companies can leverage machine learning while maintaining full control of their AI capabilities.
Scalable Solutions: Nuraling’s adaptive AI capabilities cater to both technical and non-technical users, fostering seamless scalability.
Tailored Data Privacy: Ensures operational and travel data are securely managed.
Decision Accuracy: By flagging uncertainties in analysis, Nuraling reduces risks linked to premature or incorrect conclusions.
Seamless Integration into Solace Secure
With Nuraling, Solace Secure evolves into a dynamic tool that combines AI precision with human expertise. The platform will provide enhanced proactive risk insights, without compromising data integrity or overwhelming users with alert fatigue.

Leon Storey, Founder & Head of AI at Nuraling
David Peach, CEO and Founder of Solace Global Risk expressed his enthusiasm about the acquisition: “Welcoming Nuraling and Leon (Storey) to Solace Global represents an important step in our commitment to innovation and excellence. By integrating Nuraling’s technology, we are positioning Solace Global Risk and the wider Group to remain at the forefront of the industry, enabling us to support our clients with intuitive, secure, and reliable solutions. This acquisition aligns with our core mission to protect people and assets, ensuring peace of mind for organisations navigating challenging risk landscapes.”
Leon Storey, Founder & Head of AI at Nuraling commented: “Nuraling’s strategic roadmap for 2025 will see its technologies applied to bolster Solace Global Risk’s offerings through targeted use cases. This will enhance client confidence in both routine operations and high-stakes scenarios, supporting Solace’s promise of going further to deliver personal, agile, and technology-driven solutions.”
With this acquisition, Solace Global Risk underscores its unique position as an independently owned risk management provider, combining the agility of innovative technology with expert human insight.
Together, Solace and Nuraling will lead the way in shaping the future of risk management, ensuring that clients continue to operate safely and securely, wherever their journey takes them.
DISCOVER MORE
Enhancing resilience and business continuity planning
Solace Global Risk is a leading provider of comprehensive risk management solutions, serving clients globally with a commitment to excellence. With a worldwide presence and a team of seasoned experts, Solace Global Risk empowers organisations to navigate complex risk landscapes with confidence and resilience.
Journey Risk Management
Global Security and Threat Intelligence
Risk Management Software
Diligent in-country travel security
Be one step ahead to prevent a crisis
Travel with confidence
Your duty of care doesn’t end the moment your people set foot in their destination – and neither does ours.
From transfers to ongoing security and emergency evacuations, our travel risk services always have you covered.
Arm yourself with the knowledge to avoid a potential threat from turning into a crisis. Intelligence advisories give you tailored reports to anticipate possible disruptions, mitigate risk and help you make well-informed decisions, faster.
Give your people peace of mind when they travel for work, so they remain focused on the job at hand. We mitigate risks, manage incidents if they occur, and support your people with security advice or help in a crisis.
Executive Summary
- The IS-inspired lone wolf attack in Louisiana almost certainly shows IS’s growing ability to motivate terrorist action in the West. There is a realistic possibility of copycat attacks.
- A government crackdown on unrest highly likely in the lead-up to Chad election results on 15 January.
- There is a realistic possibility that ongoing protests against abductions in Kenya could escalate, with many of the issues that sparked unrest in June unresolved.
- A border conflict between Pakistan and the Taliban in Afghanistan is likely to further over-stretch Pakistani security forces and present militants with opportunities to attack.



AMER
USA: IS-linked New Year’s vehicle attack in New Orleans
Haiti: Gangs attack reopening of Haiti’s largest hospital
Trinidad & Tobago: Government declares state of emergency
EMEA
Finland: Finnish authorities board Russian vessel suspected of sabotage
Georgia: Protests continue as new anti-West president inaugurated
Azerbaijan & Russia: Plane bound for Chechnya crashes in western Kazakhstan
Syria: New leader indicates agenda for Syria as SNA-SDF clashes continue
Kenya: Widespread civil unrest over abductions
Chad: First parliamentary, municipal, and regional elections in a decade
Mozambique: At least 176 dead in “TurboV8” phase of unrest
APAC
Afghanistan & Pakistan: Taliban launch attacks after Pakistani strikes
South Korea: Difficulties executing arrest warrant for Suk Yeol Yoon
North, Central and South America
USA: IS-inspired terrorist attack in New Orleans, Louisiana
During the New Year’s celebrations, a man rammed a vehicle into crowds gathered on Bourbon Street in the city’s historic French Quarter, killing 15 and injuring more than 30. The attacker also engaged in a firefight with intervening police officers before being killed.
After the attack, the perpetrator was identified as a US citizen who reportedly had pledged allegiance to the Islamic State (IS), and an IS flag was retrieved from the back of the vehicle used to carry out the attack. Videos from the perpetrator’s Facebook page, posted prior to the attack, included multiple statements of support for the Islamic State. The FBI stated that agents found an unused improvised explosive device (IED) in the vehicle.
Solace Global Assessment:
Initially, US law enforcement agents stated that they believed that the perpetrator did not act alone. This assessment, which was then refuted, was almost certainly due to the use of multiple weapons used or present during the attack, most notably IEDs.
The attack nevertheless shares many similarities with other “lone wolf” attacks in Europe and North America. The attacker targeted a busy, high visibility area (the French Quarter, a popular tourist destination in New Orleans and a symbol of the city’s history and culture), used low-complexity and easily obtainable weapons (noting that firearms are more easily accessible in the US compared to most West European countries and that the IEDs prepared by the attacker resembled rudimentary “pipe-bombs”), and made multiple symbolic gestures, such as releasing video pledges of allegiance to IS or carrying and IS flag, that clearly associated his actions to the extremist group.
The timing of the attack also further demonstrates how public holidays and celebrations are often targeted by lone actors due to their high visibility.
It is almost certain that the attack was inspired by other IS attacks that used vehicles as primary weapons. In 2017, a man who had pledged allegiance to IS drove a pickup truck into a bike path in Manhattan, killing eight; in 2016, more than 80 people were killed when another IS supporter used a truck to attack a Bastille Day celebration in Nice; in the same year, another truck attack at a Christmas market in Berlin killed 12.
In the United States, vehicle attacks have not solely been carried out by groups or individuals affiliated with IS. In 2017, a man rammed a car into a crowd that was protesting a far-right rally in Charlottesville, Virginia, killing one. In 2020 alone, more than 60 car attacks were recorded targeting protesters linked with the Black Lives Matter movement.
There is a realistic possibility that the New Orleans attack will result in further copycat attacks. Online propaganda channels, which are often only loosely affiliated with the Islamic State act as independent broadcasters of pro-IS narratives, and are almost certain to capitalise on the attack to call for further action targeting civilians in the United States and Europe.
In this sense, it is important to note that the number of IS-related arrests in the US increased to 14 in 2024, from nine in 2023. Of these 14, five entailed concrete attack plots, with varied targets including Christian and Jewish places of worship, as well as political events (election day) and other high-visibility events (a pride parade in Phoenix).
Haiti: Gangs attack reopening of Haiti’s largest hospital
On 24 December, the coalition of gangs known as the Viv Ansanm attacked the reopening of the State University of Haiti Hospital in Port-au-Prince, the country’s largest medical facility. The attack resulted in at least four deaths, including two Haitian National Police officers, and more than 15 injuries, several of which were journalists.
The hospital was set to reopen following a previous gang attack in February which had forced it to suspend operations. One of the prominent Viv Ansanm leaders, Johnson “Izo” André, claimed responsibility for the attack and stated that the gang coalition had not authorised the reopening of the hospital.
The attack also led to dismissal of the Haitian health minister who has been temporarily replaced by the country’s justice minister.
Solace Global Assessment:
The reopening of the hospital was set to be widely covered by the media and serve as a significant achievement for the Haitian government, marking a rare instance of progress amidst widespread violence and instability. The gangs almost certainly attacked the hospital to undermine both the government’s credibility and its ability to restore essential services, with media coverage offering them an opportunity to gain widespread publicity. Furthermore, it is likely that the gangs would have interpreted the reopening of the hospital as a direct challenge to their own power, likely setting a precedent for future attacks.
Most hospitals in Port-au-Prince are now in gang-controlled territory or remain inaccessible due to the extent of violence. The attack on State University of Haiti Hospital combined with these wider trends has hugely disrupted the provision of healthcare in Haiti and will likely lead to a further increase in medical professionals fleeing the country (estimates suggest 40 per cent have already fled) as well as denying the opportunity to train new ones.
NGOs and non-profit organisations will likely be forced to take on even greater responsibility to meet growing healthcare needs but are already overstretched, underfunded, and themselves frequently targeted by gang violence. The collapse of Haiti’s healthcare system is likely to exacerbate the already dire humanitarian situation, resulting in increases in disease outbreaks, preventable deaths and levels of food insecurity.
Trinidad and Tobago: Government declares state of emergency in response to criminal activity
Trinidad and Tobago’s government declared a state of emergency on 30 December in response to the growing criminal activity in the country. The most recent incident involved the gunning down of five men in a neighbourhood on the outskirts of Port of Spain in an act of vengeance over a murdered gang member. The measure reportedly comes in response to advice from the Trinidad and Tobago Police Service, who has stressed the threat to public safety.
The state of emergency is set to last 15 days, after which time the government will be able to vote on its extension for up to three months. The measure will give the police and army authority to detain individuals without charge and search properties without a warrant. No curfew or ban on public gatherings will reportedly be part of the emergency measures.
Solace Global Assessment:
The state of emergency is the first since Covid measures were introduced in 2021 and comes as high-calibre automatic firearms are increasingly used by criminal gangs. Murders have reportedly reached 623 out of a population of 1.5 million in 2024, placing the country’s murder rates as among the highest in Latin America and the Caribbean.
Gangs are largely responsible for the homicide rate increase; they have taken advantage of the country’s proximity to Venezuela, porous borders, and transportation routes to Europe and the US to ship narcotics. In the wake of the recent spate of killings, the police reportedly expect an increase in reprisal shootings between criminal gangs.
The measures will expand the powers of security forces to crack down on criminal gangs in the country to make it uncomfortable for them to operate. Reducing the prevalence of firearms is a target of these emergency measures, with security forces increased powers to search individuals and properties a key deterrent. People found in the company of anyone owning firearms are also liable to arrest to disrupt criminal gang networks.
Exploiting states of emergency to crack down on criminal gangs have been used by other Latin American countries with varying degrees of success. El Salvador’s March 2022 state of emergency led to the arrest of over 81,000 individuals, significantly increasing the country’s safety. Honduras implemented similar measures in December 2022; while the number of murders dropped by 356 in the first two months compared to the same period in the preceding year, gang violence is still a prevalent issue in the country.
To combat the gang violence, these countries utilised the state of emergency to crack down on the gangs with mass arrests and the use of the military, measures which would not have been constitutionally possible without the government decree. It is highly likely that Trinidad and Tobago will follow similar tactics to these countries, using the state of emergency to crack down on gangs with significant force.
The state of emergency has been imposed as the country prepares for a general election to be held before August 2025. Opposition leader and former prime minister Kamla Persad-Bissessar is expected to pose a significant threat to Prime Minister Keith Rowley’s People’s National Movement. These emergency measures, therefore, are highly likely influenced by public perception of Rowley’s administration, which is projecting itself as tough on crime.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
Thousands of Cubans march on US Embassy
On 20 December, tens of thousands of Cubans, led by Raul Castro and President Miguel Diaz-Canel, marched in front of the US embassy in Havana to protest Washington’s long-standing sanctions on Cuba and over concerns of harsher sanctions under President-elect Donald Trump. Cuba has recently suffered from a range of economic issues including inflation, systemic power outages and severe shortages of essential goods, which many Cubans blame the US for and have been the drivers of civil unrest against the Cuban government.
The march, organised by the incumbent government, is likely an attempt to deflect hostility away from the government but may also signal a shift in Cuba’s approach to the US, especially with mounting fears of harsher sanctions under Trump.
El Salvador lawmakers overturn metals mining ban
On 23 December, El Salvador’s legislature has voted in favour of overturning a ban on metals mining in a bid to boost economic growth and granted the government sole authority over mining activities. The country was the first in the world to impose a ban, which had been in place for seven years. President Nayib Bukele has been striving to overturn it since taking office in 2019.
Environmental groups oppose the overturning of the ban, with the Economic and Social Development Santa Marta Association (ADES) labelling it “the biggest attack on water, health, and life in El Salvador”. Bukele has defended the move, emphasising El Salvador’s gold reserves. The move will likely attract significant foreign investment and boost employment, something which is key for El Salvador’s debt-ridden economy. However, water contamination is a significant issue which led to the ban in the first place and environmentalists have staged demonstrations against the government measures.
President-elect Donald Trump threatens to return the Panama Canal to the US
On 21 December, Trump claimed on X that the Panama Canal fees are ‘ridiculous’ and that if they are not reduced then he ‘will demand that the Panama Canal be returned to us’. Trump also emphasised that the canal is under threat of falling under China’s influence. The canal is a vital waterway for trade; over 40 per cent of consumer goods traded in 2023 between north-east Asia and the US east coast were reportedly transported through the canal.
Fees have increased in recent years due to droughts, which have reduced the canal’s capacity and driven up variable rates. Trump’s rhetoric is in line with his America First agenda, which aims to reduce perceived exploitation of the US’ goodwill. The ‘canal giveaway’ was a source of humiliation for many in the US, who view it as a loss of a key strategic asset. Pressuring Panama’s authorities to reduce operating costs for US businesses and reduce Chinese influence is, therefore, likely perceived to be a popular measure.
Security, Armed Conflict and Terror
Likely car bomb detonates outside Trump Hotel in Las Vegas, Nevada
On 1 January, a Cybertruck manufactured by Tesla exploded outside the entrance to the Trump Hotel in Las Vegas. The truck’s driver, a former Green Beret, was killed, and seven people were injured in the explosion. According to local authorities, the truck, which had been rented hours before the explosion, was found to be filled with fireworks and fuel canisters. It is highly likely that the incident was a planned attack, rather than an accidental detonation.
In addition to the presence of fireworks and fuel (the Cybertruck is an electric vehicle) on the scene, the brand Tesla is owned by billionaire Elon Musk, who has been a key player in Donald Trump’s 2024 electoral campaign. While the attack’s dynamics make it highly likely that it was planned, the perpetrator’s motive remains so far unclear.
Environment, Health and Miscellaneous
90-day environmental emergency declared in Peru after oil spill
On 20 December, a leak was detected as oil was being loaded onto a tanker belonging to state-owned company Petroperu on Las Capullanas beach. The spill reportedly covers an area of approximately 10,000 square metres of seawater and has spread to at least seven beaches. Wildlife including birds and marine fauna has reportedly been significantly affected by the spill.
The public prosecutor’s office has launched an investigation regarding environmental contamination against the company, which has been engaged in cleanup efforts. During the state of emergency, authorities must carry out recovery and remediation work at the affected locations.
Bridge over Tocantins River in Brazil collapses.
On 22 December, the Juscelino Kubitschek de Oliveira Bridge, which connected the towns of Estreito in Maranhão and Aguiarnopolis in Tocantins, Brazil, collapsed. The collapse sent vehicles, including tankers with hazardous chemicals, into the Tocantins River. 11 people were killed because of the incident.
Search and rescue operations have been ongoing, with six people still reported missing. The local government and emergency services have been actively involved in the recovery and search operations. The Brazilian transportation minister has issued an emergency decree to expedite the rebuilding of the bridge. Despite the hazardous materials involved, the governor of Maranhão has emphasised that there is no risk of contamination to the Tocantins River; water collection from the river has resumed. Investigations into the cause of the incident are ongoing.
Nationwide power outage in Puerto Rico.
On 31 December, Puerto Rico experienced a power outage that affected over one million customers due to a technical fault at a transmission facility in Costa Sur. The blackout led to widespread disruptions, including the suspension of the Tren Urbano rail service and affected essential services like hospitals and medical centres in San Juan.
Power restoration efforts began immediately but there were renewed outages affecting more than 300,000 customers on 1 January. The exact cause of these subsequent outages was unclear, as it was not determined whether they were due to planned load shedding or technical faults. By 2 January, 99 per cent of customers reportedly had their power restored. While efforts to stabilise the power grid are ongoing, further disruptions are likely.
Europe, Middle East & Africa
Baltic Sea: Finnish authorities board Russian “shadow fleet” vessel suspected of sabotage
On 26 December, Finnish police and border guards boarded and seized the Cook Island-flagged crude oil tanker, Eagle S (IMO: 9329760), after it was suspected of conducting undersea sabotage. On 25 December, an undersea electricity cable, the Estlink 2, was damaged in the Baltic Sea, disrupting the delivery of power between Estonia and Finland.
Preliminary investigations have discovered anchor drag marks on the seabed several kilometres in length suspected to have been caused by the Eagle S. Upon boarding the vessel, it was discovered that the tanker was equipped with transmitting and receiving devices designed for espionage, allowing it to monitor NATO naval and aircraft activities.
Solace Global Assessment:
The Eagle S incident follows a series of suspected undersea sabotage incidences in the Baltic attributed to Russia, whereby civilian-flagged vessels have been accused of conducting highly deniable forms of sabotage, primarily targeting vulnerable seabed infrastructure with anchors. The incident likely highlights Russia’s increasing use of commercial vessels which form part of its “shadow fleet” as part of a wider hybrid warfare strategy used to deter support to Ukraine.
The discovery of surveillance equipment on board the vessel also likely suggests that the vessel is directly linked to Russian intelligence, which has likely tasked it to monitor NATO assets and where to conduct sabotage.
Despite NATO promises to increase patrols in the Baltic, the active monitoring of potentially hundreds of repurposed civilian vessels directed by Russian intelligence will almost certainly be incredibly challenging, especially with NATO military assets also tasked with monitoring Russia’s conventional military capabilities. Moreover, the boarding of a vessel is difficult due to legal constraints, the need for international cooperation, potential diplomatic fallout, and operational challenges.
Consequently, it is almost certain that Russia will continue to exploit this disruptive yet low-cost and highly deniable form of sabotage as the West continues to pledge support for Ukraine.
Georgia: Anti-West president inaugurated as pro-Europe president refuses to step down
Following a controversial presidential election, Mikheil Kavelashvili was sworn in as Georgia’s new president on 29 December. The election was conducted with an indirect electoral college whose makeup was derived from the contested October 2024 parliamentary election. Kavelashvili, an anti-West ally of the ruling Georgian Dream party, is set to replace Salome Zourabishvili, a pro-Europe figurehead for the anti-government protest movement which has gripped Georgia since October 2024.
Zourabishvili has refused to step down, labelling the presidential election illegitimate, but has vacated the presidential palace.
Major protests have continued across Georgia, primarily in Tbilisi but also in other cities such as Batumi. Protests of varying size and intensity have been organised in Tbilisi in the vicinity of Georgia’s parliament building every day for the past 37 days as of 3 January. While mostly peaceful, the more significant protests have been marked by violent clashes and draconian riot police enforcement methods; the protests during the inauguration on 29 December led to at least seven arrests.
Solace Global Assessment:
Zourabichvili’s decision to vacate the presidential palace was likely made due to the potential threat of arrest, with multiple political opponents (including the prime minister) having called for her arrest if she did not step aside. If Zourabishvili is arrested, intense protests will almost certainly break out in support of her, likely marked by violent clashes.
The founder of the ruling Georgian Dream party, the oligarch and former prime minister Bidzina Ivanishvi, is almost certainly the most influential figure in Georgian politics, essentially constituting the de facto political leader of the country. In a notable development, the US has imposed sanctions on Ivanishvi due to the claimed erosion of democratic institutions and human rights abuses by security forces. These sanctions include the freezing of his US assets and follow earlier imposed sanctions against senior Georgian Dream interior ministry officials, as well as UK sanctions.
While the EU’s parliament is considering imposing sanctions, these proposals have been hampered by countries perceived to be pro-Russian, namely Hungary and Slovakia.
Unless deposed, it is highly likely that the Georgian Dream government will take Georgia closer into Russia’s sphere of influence. The suspension of EU accession talks has notably led to the most significant escalation in protests. The protest movement, therefore, is likely an existential moment for Georgia towards either a western-aligned pro-Europe or anti-West pro-Russia future. While this fear has almost certainly sustained the protest movement, the feasible options for ousting the ruling Georgian Dream party are slim and it is unlikely that significant concessions that cannot be easily undone will be granted.
Azerbaijan & Russia: Plane bound for Grozny, Chechnya crashes near Aktau in western Kazakhstan
On 25 December, An Azerbaijan Airlines flight en route from Baku, Azerbaijan to Grozny, Chechnya crashed during an emergency landing near Aktau, Kazakhstan. The crash resulted in at least 38 fatalities and 29 hospitalisations.
Initial reports suggest that the aircraft was likely hit by shrapnel from a Russian surface-to-air missile while flying over Grozny where Russian air defences were reportedly targeting Ukrainian drones. While Russian officials have speculated that the crash occurred because of a bird strike or exploding oxygen tank, the damage appears consistent with Russian surface-to-air missiles. This has yet to be officially confirmed, however.
Azerbaijan Airlines has suspended flights to several Russian cities, citing potential safety risks. Russian President Vladimir Putin has issued an apology to Azerbaijan’s President Ilham Aliyev for the incident, acknowledging that it occurred in Russian airspace.
Solace Global Assessment:
Azerbaijan’s President Ilham Aliyev has expressed anger at Moscow’s handing of the incident. After the plane was shot down, emergency landing permission in Russian territory was allegedly denied, something which could have potentially led to fewer fatalities. Moscow’s lack of acceptance of responsibility has caused significant outrage in Azerbaijan, notably from state-owned and pro-government media, which has recently typically avoided criticising Russia.
This incident comes amidst Moscow and Baku’s relationship having strengthened in recent years. This is largely due to Moscow’s de facto enabling of the Azerbaijani incursion into Nagorno Karabakh in September 2023, which was formerly an autonomous Amenia-aligned breakaway state that was internationally recognised as part of Azerbaijan.
Russian peacekeeping forces stood back to enable the Azerbaijani military offensive before withdrawing completely. Russian support for the Azerbaijani offensive occurred despite Armenia, Azerbaijan’s regional rival, being a member of the Russian-led military alliance Collective Security Treaty Organization (CSTO).
Baku, likely in response to Moscow’s enabling of Azerbaijan’s presence in Nagorno Karabakh, has avoided taking a side in Russia’s war in Ukraine. Yerevan has since announced its intention to leave the CSTO.
Despite Azerbaijan not being a member of CSTO, economic, diplomatic, and cultural factors make good relations important for each country. Russia is one of Azerbaijan’s key trading partners, with Russian companies investing significantly in Azerbaijani energy and infrastructure. Furthermore, Azerbaijan has the largest Russian presence in the South Caucasus and Russian is widely spoken in the country. Simultaneously, a significant Azerbaijani diaspora resides in Russia.
Despite this high-profile plane crash representing a point of tension for the two nations, their shared interest in maintaining good relations makes a major diplomatic severing undesirable for each country. Therefore, a significant worsening of relations is unlikely in the aftermath of the plane crash, despite public anger.
Syria: New Syria leader sets out agenda for country’s future as clashes continue in northern Syria
The de facto leader of Syria and the emir of Hay’at Tahrir al-Sham (HTS), Ahmed al-Sharaa (formerly known by his nom de guerre Abu Mohammed al-Golani), gave an interview with Al Arabiya on 29 December in which he laid out an agenda for Syria’s future. Some of the key points made included a transitional process involving a constitution writing process which may take three years, elections which may take four years (that will require a comprehensive population census prior), the dissolution of HTS, no federalisation and the integration of Kurdish forces into the new Syrian military, and the maintenance of a relationship with Russia.
Furthermore, pro-Assad supporters killed at least 14 interior ministry troops on 26 December near Tartus, one of the deadliest attacks by regime loyalists since the overthrow of Assad by rebel forces.
Clashes and military operations have continued in northern Syria between the Kurdish-led and US-backed Syrian Democratic Forces (SDF) and the Turkish-led Syrian National Army (SNA) with support from the conventional Turkish military. The most intense fighting has occurred in the eastern countryside of Manbij in the vicinity of the strategically important Tishreen Dam, despite a Pentagon statement on 30 December that claimed a ceasefire “is holding”. The Turkish Air Force has provided close air support (CAS) for the SNA, and the Turkish military has conducted extensive artillery strikes on numerous villages.
Solace Global Assessment:
Iran is likely to be the state actor that loses most from Syria’s new geopolitical direction. Notably, al-Sharra made a particular effort to be conciliatory regarding Russia, despite Moscow’s key role in militarily supporting the Assad regime (which included indiscriminate bombing campaigns against previously rebel-held urban areas such as Aleppo and Idlib). Al-Sharaa stated that Russia is the “second most powerful country in the world” and Syria has “strategic interests” with Russia.
The Russian military still maintains a presence in Syria, although significantly reduced since the lightning HTS-led offensive that overthrew the regime. There is a realistic possibility that a deal may be reached between Russia and Syria’s new government that formally allows Russia to continue its leasing of the Hmeimim airbase and Tartus naval base.
China’s exclusion is notable, with a sizable contingent of Uyghurs from the Chinese territory of Xinjiang fighting for HTS. Uyghurs have been given senior military roles in Syria’s new armed forces – it is likely that the strong anti-Beijing sentiment of HTS’ Uyghur fighters will factor into Damascus’ new foreign policy towards China.
The largest threat to stability in post-Assad Syria likely remains the status of the Kurdish-led SDF-controlled areas of north-northeastern Syria. Al-Sharaa, in addition to other senior HTS figures, has explicitly stated that federalisation will not be pursued. This highly likely presents a challenge to the prospective future autonomy of Kurdish-controlled areas of Syria.
Without substantial support from the US (which may be limited due to the incoming Trump administration, with Trump stating a desire to be disentangled from Syrian affairs) and amidst the ongoing conflict between Turkish-led forces and the SDF (which may further escalate), it is likely that aligning themselves with HTS is one of few options for the SDF to avoid an escalation in conflict that could pose an existential threat to the Kurdish population.
While Turkey has given substantial support to HTS, HTS are almost certainly far less influenced by Ankara than the SNA and al-Sharra has expressed that the Kurds are “an integral part” of Syria. This has highly likely conditioned an SDF statement that they are ready to cooperate with al-Sharra to be the “nucleus of the Syrian army”, despite the significant risks posed to the Kurds by the SDF losing its autonomy through integration.
Kenya: Widespread civil unrest over Abductions and protests
In mid-December, protests were sparked in Kenya over the alleged abduction of critics of the President William Ruto-led Kenya Kwanza government. The allegations stipulate that the government has illegally apprehended dozens of people who were believed to be involved in the June protests sparked by deeply unpopular taxes.
The Kenya National Human Rights Commission (KNHRC) estimates that over 80 people have gone missing, with at least seven more being abducted since mid-December. Small-scale protests that were primarily organised in central Nairobi have spread to other parts of the capital and have also been recorded in other major population centres, including Mombassa, Eldoret, Embu and Kisumu.
Protests have also grown in size and have led to several instances of violent clashes with the police, the deployment of tear gas and multiple arrests, including the arrest of an opposition senator who had publicly criticised the abductions.
Solace Global Assessment:
The government’s continued abductions, use of crowd dispersal measures and arrest of opposition figures will highly likely sustain protest activity which is likely to increase in scale and spread to other cities. Following the June protests and proposed tax increases, the Ruto administration remains deeply unpopular, especially with the youth who have been the instigators of much of the unrest.
Critics have even warned of a general trend of democratic backsliding and a return to the repressive use of tactics that were witnessed under President Daniel Moi (1978-2002), which was marked by the detention, torture and disappearance of critics, journalists, activists and members of the opposition.
Moreover, despite the withdrawal of many of the controversial planned tax increases following the June protests, multiple new taxes will be introduced in 2025 that will help shape the conditions for more unrest.
In 2024, there were an estimated 1,800 demonstrations held across Kenya, indicating the level of dissatisfaction with the current administration. Most of these protests also continued despite the government’s use of force, which in some cases involved the firing of live ammunition. Given the underlying drivers and unresolved grievances that have previously contributed to unrest, there is a high likelihood that the current anti-abduction protests will be co-opted, especially by Kenya’s youth, and develop into violent unrest comparable to the protests observed in June 2024.
Chad: First parliamentary, regional, and municipal elections in a decade
On 29 December, Chad held its first parliamentary, regional, and municipal elections in over a decade. 8.3 million people are registered to vote in Chad and voted for legislators in a 188-seat parliament, 95 of which are required for a majority.
The election was marked by significantly low voter turnout, with opposition parties, including the primary opposition party, the Transformers Party, boycotting the election over concerns about the credibility of the electoral process, raising concerns over the election’s transparency and fairness.
The election was marked by significant repression, with the Chadian National Election Management Authority (ANGE) prohibiting pictures and photographs of the results, citing the threat of manipulated results being uploaded. Furthermore, online newspapers were banned from broadcasting videos related to the election on 4 December. ANGE has declared that vote counting is under way and provisional results are expected by 15 January.
Solace Global Assessment:
Since the death of President Idriss Déby in 2021, Chad has been led by a transitional military government led by the former president’s son, Mahamat Déby, who has run as part of the Patriotic Salvation Movement. These elections mark a key transition point in the move away from military rule, with the election formally ending the “transitional period”. The elections were initially promised in 2020 but were postponed due to the COVID-19 pandemic. Chad is the first of the recently coup-hit Sahel countries to hold elections. Déby, whose family has ruled Chad since 1991, will almost certainly claim victory in the provisional results.
Many opposition figures have criticised the elections as fraudulent. Déby has been criticised over utilising the elections to consolidate power. Security forces reportedly killed opposition candidate Yaya Dillo, Déby’s biggest challenger, in February 2024. According to a poll issued by the Center for Development Studies and the Prevention of Extremism, 50.94 per cent of respondents claimed that they did not believe in the credibility of Chad’s electoral authorities. More than 90 per cent of the registered voters reportedly adhered to opposition calls for election boycott. Without full opposition participation, human rights organisations including Amnesty International have claimed that the election is likely to be unfair.
Given the widespread view in Chad that the elections are fraudulent, civil unrest is highly likely as ANGE publishes the provisional results, with small-scale demonstrations already held in the capital N’Djamena. Chad’s government, which has previously cracked down on protests with live ammunition, tear gas, arbitrary detentions, and media censorship, will highly likely turn to these measures again if unrest reaches a significant level. Notably, after Déby postponed elections due in October 2022, security forces killed over 100 people with live ammunition after demonstrations erupted against the government.
Mozambique: At least 176 dead in “TurboV8” phase of unrest
The most recent phase of unrest, labelled “TurboV8”, was sparked in response to the Constitutional Council ruling in favour of the government on 23 December. It has constituted the most violent phase yet, with at least 176 deaths, and has triggered the FCDO to issue an advisory against all but essential travel to Mozambique. In the “TurboV8” phase, demonstrations occurred across major cities in Mozambique including Maputo, Beira, and Nampula. In Maputo, protesters set several buildings on fire. In Beira, protesters blocked multiple roads and set tyres on fire. In Maganja da Costa and Namicopo, armed individuals reportedly invaded police stations.
Most bus services from Maputo to other provinces have been halted after protesters vandalised the main terminal in the city. There is a fuel shortage in Maputo and Matola due to fuel stations being targeted by protesters. Security forces responded to unrest with tear gas and live ammunition. According to local NGOs, approximately 261 people have been killed in Mozambique since the post-election unrest began.
On 25 December, at least 6,000 inmates escaped from the maximum-security Central Prison of Maputo following prison riots whereby prisoners overpowered guards and seized their weapons. Among the escapees were Islamic State Mozambique (ISM/Shabaab Cult) militants. Around 13,000 people have reportedly crossed the border into southern Malawi via the Shire River and Ruo River to escape the unrest. A further 1,000 have requested asylum in Eswatini. This is indicative of the lack of end in sight and continued deterioration of the country’s security situation.
Solace Global Assessment:
Opposition candidate Venâncio Mondlane has set 15 January as the date to be sworn in as president, the same day Frelimo candidate Daniel Chapo is set to be sworn in. Mondlane has laid the groundwork for potential rule in 2025, expressing that he will remove the weapon from Mozambique’s flag, revise its constitution, and change the names of streets named after communists. Furthermore, he has called for Mozambicans to elect their own regional leaders in elections on 6 and 7 January. Unrest will almost certainly continue until the government steps down, something that is unlikely to happen without significant pressure, with demonstrations highly likely to increase in intensity as 15 January nears.
Opposition candidate Venâncio Mondlane has announced a new phase of unrest titled “ponta de lança” (spearhead). While he was set to announce the details on the phase on 2 January, this was postponed. Mondlane has indicated that this phase will encompass a “five-day tolerance” period for international humanitarian and investigative organisations to assess alleged human rights abuses by security forces.
Mondlane has declared the prison break a calculated government move to distract from the protests and manipulate public opinion. This is unlikely to be the case; however, since the addition of more IS fighters to the ongoing insurgency in the Cabo Delgado region will almost certainly further strain government resources as it diverts assets to tackle the insurgency. The inmates, likely calculating that law enforcement resources are strained and unable to focus on securing the prison, almost certainly used the context of the protests to take advantage of reduced security measures. This prison escape will likely add to the pressure from demonstrations.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Anti-government protests in Albanian capital
On 23 December, Albania’s main opposition party, the Democratic Party, organised protests in central Tirana to demand a technocratic caretaker government ahead of the May 2024 elections. The demonstrations, led by recently released party leader Sali Berisha, accused Prime Minister Edi Rama’s left-wing government of corruption and election manipulation. The protests blocked several main intersections in the capital and police intervened after 90 minutes, leading to clashes. Further protests are likely ahead of the May elections, especially as the accusations of corruption, government overreach and electoral manipulation are damaging Albania’s progress towards EU integration.
Recep Tayyip Erdoğan announces plans to change Turkey’s constitution
On 21 December, Erdoğan renewed his long-standing aim for a new constitution upholding ‘democratic, inclusive, and libertarian’ values during a speech in Muğla in southwest Turkey. Erdoğan is currently serving his third and apparently final term, with the next presidential election not due until May 2028.
By creating a new constitution, it is highly likely that Erdoğan will seek to eliminate constitutional limits on presidential terms, which would allow him to run for president again in 2028. If Erdoğan proceeds with measures to amend the constitution, significant unrest is highly likely.
According to local news polls, 66.3 per cent of the Turkish population oppose a constitutional amendment which would enable Erdoğan to run in 2028. A successful referendum on Turkey’s constitution was held in 2017, with the population voting to change the country from a parliamentary system into a presidential republic. Another amendment would almost certainly help Erdoğan further consolidate power.
Protests in Iran over economic conditions
Merchants and business owners in Tehran’s historic bazaar staged a rare strike on 29 December to protest rising inflation and the soaring devaluation of the Iranian rial, which has surpassed 810,000 to the dollar. The strike, initially led by shoe sellers, quickly spread to other sectors and key commercial hubs. Merchants cited skyrocketing raw material costs, reduced consumer demand, and widespread closures of workshops as driving factors, with over a third of the population now living below the poverty line. While security forces were deployed and gatherings subsided by day’s end without reported violence, the unrest highlights the dire economic state of Iran under US-led sanctions which could become more common and potentially violent if the incoming Trump administration increase sanctions on Iran.
Zimbabwe abolishes the death penalty
On 31 December, President Emmerson Mnangagwa approved a law to abolish the death penalty with immediate effect. The death penalty has not been used since 2005, largely because of a general reluctance to take up the job of state executioner. Mnangagwa has publicly opposed the death penalty since 2017, leveraging his presidential powers several times to commute death sentences of inmates. By the end of 2023, approximately 60 people were on death row; they will be re-sentenced. Zimbabwe will be the 113th country globally to abolish the death penalty, according to Amnesty International.
Security, Armed Conflict and Terror
Rare mass shooting in Montenegro
On 1 January, a mass shooting in the town of Cetinje resulted in the deaths of 12 people, excluding the gunmen who died by suicide. The shooting occurred after an altercation at a bar and is almost certainly an isolated incident. However, this is the second mass shooting in three years in Cetinje and the incident will likely spark calls for stricter gun control in Montenegro and may lead to protests similar to those witnessed in neighbouring Serbia after it suffered two mass shootings.
Palestinian militants increase rate of attacks in north Gaza Strip
Between 30 and 31 December, Israeli sources reported a growing number of “multi-wave” attacks by Hamas and Palestinian Islamic Jihad (PIJ) fighters on Israel Defence Forces (IDF) positions near Jabalia. These attacks, which were carried out by reportedly groups of up to 30 fighters at a time, were larger than any attack on Israeli forces in Gaza in recent months. According to the IDF, approximately 100 Palestinian fighters were killed during the attacks. The IDF has been seeking to clear Jabalia for months, after isolating the northernmost refugee camps in the Gaza Strip, and Israeli forces assess that approximately 200 fighters remain in the area.
Nigerian military strike kills civilians on Christmas Day
On 25 December, a Nigerian military airstrike killed at least 10 people and injured several others in the northwestern Sokoto state. The operation was reportedly targeting the newly formed Lakurawa terrorist group that may have links to regional jihadist coalition, Jama’at Nasr al-Islam wal Muslimin (JNIM).
The strike follows a series of largely aerial Nigerian military operations that have accidentally killed civilians which has led to calls to review targeting procedures and enhance intelligence, surveillance and reconnaissance (ISR) capabilities, with such strikes likely enabling extremist groups’ recruitment and propaganda campaigns.
The Nigerian government has conducted a probe into the strike and has determined that the fatalities were attributed to “secondary explosions” and not airstrikes, a claim that will likely be widely refuted.
Clashes between Somali and Ethiopian forces
On 23 December, Somali and Ethiopian forces reportedly clashed in the border town of Doolow in Somalia’s Gedo region. The incident occurred amidst heightened tensions between Mogadishu and the Jubaland region, which recently elected its president for a third term in elections viewed as illegitimate by the federal government.
Ethiopia, which has forces situated in the country as part of the peacekeeping African Union transition mission in Somalia (ATMIS), has been accused of backing Jubaland against the government in a bid to stabilise Ethiopia’s eastern border against al-Shabaab. Since the controversial Jubaland election on 25 November, Somali federal forces and Jubaland Derawish forces have clashed several times as Mogadishu attempts to assert control over Somali territory.
According to Mogadishu, Ethiopia violated its sovereignty which ‘will not go unanswered’. This incident comes shortly after a Turkey-brokered treaty between Mogadishu and Addis Ababa to settle the Somaliland port dispute. Given that this treaty has done little to prevent clashes, further tensions between Mogadishu and Addis Ababa are highly likely.
UN authorises new peacekeeping mission in Somalia
On 27 December, the UN adopted the resolution for a new peacekeeping mission, African Union Support and Stabilization Mission in Somalia (AUSSOM), which will support the deployment of up to 12,626 personnel and replace the existing African Union Transition Mission in Somalia (ATMIS). The mission aims to support Mogadishu in its ongoing conflict with the al-Qaeda affiliated al-Shabaab, which is currently waging an insurgency in Somali territory.
Mogadishu is still deciding which countries will contribute troops. Ethiopia, a focus of recent tensions, is notably excluded from the mission. Egypt, a regional rival of Ethiopia, has announced plans to participate in the mission. Burundi’s government has declared that it would not contribute troops due to a lack of consensus with Mogadishu over troop numbers.
While AUSSOM will help Mogadishu combat the insurgency, its effectiveness will likely be limited. ATMIS encountered significant challenges and was not able to significantly degrade al-Shabaab. Mogadishu, amidst ongoing struggles to consolidate power over Somalia, will likely continue to struggle against ongoing al-Shabaab and Islamic State insurgencies despite the peacekeeping presence.
Islamic State Somalia Province (ISSP) launches large-scale attack in Puntland, Somalia
On 31 December, ISSP forces launched a large scale attack on Puntland forces in Dharjaale. According to available Puntland sources, ISSP forces used multiple suicide bombers and suicide vehicle borne IEDs (SVBIEDs) to attack their military targets, killing at least 20.
In the attack’s aftermath, pro-IS channels noted how the operation was led by foreign fighters, mostly from North Africa and the Arab Peninsula. The large scope and sophistication of the operation and the use of foreigners almost certainly demonstrate the growing importance of the Somali branch of IS, led by Abdul Qadir Mumin.
Mumin, who some reports (likely incorrectly) identified as IS’ “Caliph”, has a large influence over the group due to ISSP’s central role in routing flows of funds to other African and Asian IS branches.
Allied Democratic Forces (ADF) kill 21 civilians in the Democratic Republic of the Congo (DRC)
The series of attacks began on 21 December after the ADF made an incursion into the village of Robinet in the North Kivu region, killing six civilians. On 22 December, the ADF entered the neighbouring village of Kodjo and killed 12 more civilians. Three more civilians were killed on 25 December after the ADF entered Makele, another village in the area.
The attacks all happened around the resource-rich Manguredjipa and represent a fresh escalation of terror attacks in the region. The ADF is a militant Islamist group that originated in Uganda in 1995 and pledged allegiance to Islamic State in 2019.
While both DRC and Ugandan forces are currently fighting the ADF, they have been unable to contain the group, which has expanded its operations since 2021 and conducted numerous attacks targeting civilians in both the DRC and Uganda. Further attacks targeting civilians in North Kivu are highly likely in the coming weeks.
Journalist arrested in Tehran as possible “retaliation” for US-backed arrests of IRGC supporters
An Italian journalist, Cecilia Sala, was arrested in Tehran days after arriving in the country over an unspecified “violation” of Iranian law. The arrest took place days after two Iranian citizens were detained in an international police operation coordinated by Washington, over allegedly providing material support for the Islamic Revolutionary Guards Corps (IRGC). One of the two suspects, Mohammad Abedini Najafabadi, was arrested at the Milan airport, where he landed on a flight from Turkey. The arrests could precipitate a diplomatic crisis between Tehran and the European Union at a time where the Pezeshkian administration is cautiously signalling its willingness to improve its relations with Brussels.
Environment, Health and Miscellaneous
Nigeria establishes emergency response centre to address Lassa fever outbreak
Nigeria has activated an emergency response centre to address a Lassa fever outbreak that has killed 190 people and infected 1,154 across six states this year. The disease, transmitted through contact with rodent-contaminated items or bodily fluids, peaks during the dry season (October to May). The Nigeria Centre for Disease Control (NCDC) categorised the risk as high, with the response centre coordinating efforts to manage the viral haemorrhagic illness, which causes symptoms ranging from fever to death. Lassa fever is classified by the WHO as a priority disease due to its epidemic potential and the absence of approved vaccines.
Sudan suspends participation in hunger monitoring system
On the eve of a critical report expected to reveal famine spreading to five regions in Sudan, the Sudanese government has withdrawn from the Integrated Food Security Phase Classification (IPC) system, citing concerns about sovereignty and the reliability of IPC reports. The decision will almost certainly reduce the ability of external actors to access the humanitarian situation on the ground and will likely undermine the efforts of aid agencies and NGOs operating in the country, where an estimated 25 million people are experiencing crisis levels of hunger.
DRC government releases most Chinese nationals held for illegal mining
On 25 December, the DRC government released 14 of 17 Chinese nationals arrested over the operation of an illegal gold mine after they were unable to provide the necessary documentation. The arrests were part of a broader crackdown on illegal mining in the resource-rich country. The government has struggled to maintain control of these resources amidst armed groups and unlicenced mining companies exploiting them illicitly.
Asia–Pacific
Afghanistan & Pakistan: Taliban attack Pakistani border posts after airstrikes in Afghanistan
On 24 December, Pakistani airstrikes targeted alleged Tehrik-e-Taliban Pakistan/Pakistani Taliban (TTP) camps, training facilities, and rear areas in Afghanistan’s Paktika province. The strikes reportedly caused multiple civilian casualties, as claimed by the Afghan Taliban, with the UN supporting these claims with credible evidence. In response, the Afghan Taliban summoned Pakistan’s envoy in Kabul to protest the attack. On 28 December, the Afghan Taliban launched retaliatory attacks on Pakistani border posts, with violence primarily concentrated in the Waziristan region in the Khyber Pakhtunkhwa province on the international border.
Solace Global Assessment:
Pakistan’s airstrikes in Afghanistan likely reflect an escalation in its counter-terrorism operations against the TTP, which has long used the border areas as a safe haven to sustain its activities and has been supported by the Afghan Taliban. Pakistan has endured its worst year of terrorist attacks in a decade, which have increased since the Taliban retook power in Afghanistan.
With limited resources to conduct a major ground offensive in parts of Pakistan where the TTP hold influence, Pakistan likely calculates that airstrikes within Afghanistan are its best course of action to degrade the TTP whilst retaining its own combat power. Moreover, Pakistan is under pressure from China to address its security challenges to protect Beijing’s Belt and Road Initiative (BRI) investments.
Consequently, there is a realistic possibility that Pakistan will increasingly use airstrikes within Afghanistan, with ground forces overstretched due to ongoing insurgencies, terrorist attacks and widespread civil unrest.
The Afghan Taliban is unlikely to attempt to restrain TTP activities over fears of a backlash and defections to the Islamic State Khorasan Province (ISKP). Other efforts, such as relocating TTP militants deeper into Afghanistan or diplomatic engagements have largely failed. These trends will likely sustain the current hostilities and invite further Pakistani attacks within Afghanistan.
The Taliban’s response will likely include increased attacks on Pakistani military outposts in the border regions but could also include the sponsoring of major TTP attacks within Pakistan. Whilst primarily based in the border regions, the TTP is known to have sleeper cells and networks throughout Pakistan and has previously conducted mass casualty attacks in cities like Islamabad, Rawalpindi, Karachi and Lahore.
The current cross-border conflict could signal a dangerous cycle, with both sides unlikely to back down, increasing the risk of broader regional instability and increased attacks within Pakistan.
South Korea: Prosecutors issue arrest warrant for impeached president Suk Yeol Yoon
The South Korean judiciary has been actively pursuing legal actions against Yoon and other officials involved in the martial law declaration. The South Korean court has issued arrest and search warrants for Yoon on charges related to sedition and abuse of power. The prosecutors have been consulting with police to execute these warrants, which are set to expire on 6 January.
However, Yoon’s legal team argues that the requirements for his arrest have not been met, and they question the prosecutorial authority to investigate sedition. Acting president Han Duck-soo has also been impeached over his refusal to appoint judges to the Constitutional Court, a move that opposition lawmakers claim was politically motivated. The finance minister Choi Sang-mok has assumed the acting presidency.
Solace Global Assessment:
It is unclear whether investigators will be able to execute the warrants before they expire. Yoon’s security team have blocked investigators from entering the presidential office grounds and Yoon’s residence for searches. On 3 January, police forces called off an arrest operation after they were blocked for six hours. Yoon continues to retain a support base among the population. There is a realistic possibility that protesters will prevent police from arresting Yoon, something that has occurred in the past after authorities have attempted to arrest politicians in the past. Further attempts to arrest Yoon will almost certainly be met with resistance.
Several military officials also face charges over the declaration of martial law. The commander of the Intelligence Command and the Army Chief of Staff, among others, have been arrested or indicted for their roles in the martial law implementation. These actions reflect the broader efforts by South Korean authorities to hold accountable those who participated in what is viewed as an unlawful and politically motivated imposition of martial law.
As the Constitutional Court prepares for the next hearing in Yoon’s impeachment trial set for 3 January, the political and legal challenges facing South Korea remain acute. The outcomes of these proceedings will have significant implications for the country’s governance and the future of its democratic institutions.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Shia communities stage protests across Pakistan
Shia groups and communities are staging indefinite sit-in protests across multiple Pakistani cities, including Karachi and Lahore, to condemn sectarian violence that has been targeting Shia Muslims in northwestern Pakistan since late November. The protests, which include blockades in Karachi and Kurram District’s Parachinar, have caused significant disruptions, particularly in Karachi, where major intersections and key roads, including routes to Jinnah International Airport.
Despite the imposition of a state of emergency in the areas where Shia communities are being targeted, the violence is unlikely to decrease in the short term given the wealth of security issues the government is being forced to contend with, including Baloch uprisings, Taliban assaults on the border and other forms of militancy.
There is a realistic possibility of the protests increasing and spreading to other cities, leading to further transport disruptions, clashes with the police and the issuing of Section 144s by the authorities.
Significant transport disruption in Punjab during farmer’s protest.
On 30 December, farmers in Punjab, supported by transporters, workers, traders, and religious groups, caused an effective shutdown between 07:00 and 16:00 local time. The shutdown included a suspension of bus services, train cancellations, and over 200 major highway blockages. Protesters are demanding a debt waiver, pensions, frozen electricity tariffs, the withdrawal of police cases, the reinstatement of the Land Acquisition Act, and justice and compensation for victims of the 2021 Lakhimpur Kheri vehicle-ramming, drive-by shooting, and mob lynching. Jagjit Singh Dallewal, the leader of the protesters, has been hunger striking for over a month, refusing all medical treatment. Further disruptions are highly likely.
Hong Kong issues new arrest warrants for pro-democracy activists.
In a move that has been condemned by the US and other Western nations, Hong Kong issued arrest warrants for six overseas pro-democracy activists and bounties of HKD one million on 24 December. The activists face charges of secession, subversion, and collusion with foreign forces under the national security law which has been used extensively to quash dissent but at the expense of Hong Kong’s reputation as an international finance hub.
Authorities impose curfew in Noumea and three neighbouring municipalities in New Caledonia
French officials have imposed a curfew in the capital Noumea and three neighbouring municipalities on 1 and 2 January, following months of unrest related to a proposed constitutional change. The curfew, which comes just weeks after the previous one was lifted on 2 December, is a response to the ongoing tensions and concerns about potential public disorder during the festive season. The reinstatement of the curfew also follows a rise in road fatalities since the lifting of the previous curfew. The traditional car parades which typically take place in Noumea over the festive season have been cancelled as a result of the curfew. The authorities are likely aiming to curtail any further accidents or violent incidents, as the region grapples with social unrest.
Security, Armed Conflict and Terror
State of emergency declared in parts of Pakistan’s Khyber Pakhtunkhwa province
On 23 December the Khyber Pakhtunkhwa (KP) provincial cabinet approved the imposition of a state of emergency in the districts of Kurram and Khyber in response to the deteriorating security situation in the region. Months of sectarian violence between Sunni and Shia communities has resulted in hundreds of deaths through violence and an estimated 120 children have died as a result of medicine shortages caused by road blocks according to a former minister. However, relief efforts will likely be delayed by militant and Taliban attacks along Pakistan’s border with Afghanistan.
Bangladeshi Christian homes set on fire on Christmas Eve
On Christmas Eve at least 17 homes belonging to the minority Christian community were set on fire in the Bangladesh’s Chittagong Hill Tracts area. This act is likely further evidence that the ousting of Prime Minister Sheikh Hasina has led to the emboldening of extremism in Bangladesh, with attacks on the Hindu minority community also having been widely reported since the changing of the government.
China’s President Xi threatens Taiwan in New Year’s speech
China’s President Xi Jinping reiterated in his New Year’s speech that China’s “reunification” with Taiwan is inevitable, warning against pro-independence forces. The veiled threat follows a year marked by an increase in Chinese military incursions in Taiwan’s waters and air space, with almost daily violations, including several exercises simulating the encirclement of the island nation. Whilst most of this activity has been designed to intimidate Taiwan, isolate Taipei and normalise Chinese military presence in the area, the increase in military activity has almost certainly heightened the risk of miscalculation that could trigger a broader conflict. On 3 January, China doubled down on its stance by imposing sanctions on 45 US entities accused of providing arms to Taiwan, further escalating tensions.
Environment, Health and Miscellaneous
Plane crashes at South Korea’s Muan Airport
On 29 December, a Jeju Airlines flight crashed at Muan Airport in South Korea. Emergency services confirmed that 179 of 181 passengers were killed, with two individuals rescued from the wreckage. The crash led to the closure of Muan Airport until 1 January, affecting all domestic and international flights. The South Korean transport ministry reported that a bird strike warning was issued shortly before the crash, and eyewitnesses captured video evidence of an engine failure just before the aircraft crash-landed. As of 30 December, South Korean officials reported that one of the two black boxes from the crashed plane was retrieved but partially damaged. The investigation into the cause of the crash is ongoing, with the damaged black box potentially hindering progress. Hundreds of people gathered at the airport in the aftermath to express their frustration at the length of time body identification has taken. Jeju Air chief executive Kim E-bae was barred by authorities from leaving the country pending investigation into the cause of the crash.
Authorities tackle wildfires in Australia’s New South Wales and Australian Capital Territory
On 30 December, 52 wildfires simultaneously occurred in New South Wales and Australian Capital Territory. Residents in parts of the Tamworth Local Government Area were advised to prepare to evacuate due to a wildfire burning to the south of the town. Earlier in the season, crews successfully took control of the Scrubby Gully Road Fire near Walcha, which had burned through 172 acres of grassland. The high number of uncontrolled fires signifies a continued risk and the need for vigilance and preparedness in the affected areas. Further wildfires are almost certain during Southeast Australia’s wildfire season which runs from December to February.
Vanuatu hit by a 6.1 magnitude earthquake
The earthquake occurred on 22 December approximately 30 kilometres west of Port Vila at a depth of 39.9 kilometres, resulting in no casualties or significant damage. The tremor occurred five days after the country was struck by a 7.3 magnitude earthquake. The initial earthquake killed 14 and injured 200, causing significant damage to the country’s infrastructure. In response to the earthquakes, Australia operated military flights delivering humanitarian aid and flying 568 citizens out of the country. Vanuatu is in the seismically active Pacific Ring of Fire region, which accounts for 90 per cent of the world’s earthquakes. Further earthquakes can occur spontaneously and may trigger tsunami warnings.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence

Executive Summary
- The reissuing of an arrest warrant for former Bolivian President Evo Morales will likely trigger widespread unrest if signed by a judge.
- The collapse of the German government and the scheduling of elections in February will likely result in an election period marked by increased unrest and political violence.
- It is likely that a Turkish-led offensive against Kurdish-controlled northeast Syria is imminent, posing an existential threat to Kurdish autonomy.
- It is highly likely that the devastation caused by Cyclone Chido in Mayotte will exacerbate underlying tensions, which may trigger civil unrest against the French government.



AMER
Bolivia: Another arrest warrant issued for Evo Morales
EMEA
Germany: Scholz fails confidence vote leading to February elections
Georgia: New anti-West president elected as pro-Europe protests continue
Syria: Kurdish-controlled northeast Syria under imminent threat of Turkish offensive
Ghana: Supreme Court blocks challenges to repressive LGBT bill
Mozambique: Pause on protests until Constitutional Court decision
Mayotte: Region recovering from Tropical Cyclone Chido
APAC
Pakistan: Militants launch attacks on final vaccination drive of 2024
Vanuatu: Magnitude 7.3 earthquake causes severe damage in Port-Vila
North, Central and South America
Bolivia: Arrest warrant reissued for former President Evo Morales
On 16 December, an arrest warrant was issued for former Bolivia President Evo Morales over allegations that he fathered a child with a fifteen-year-old girl in 2016 when he was in office.
The arrest warrant differs from the previous one issued in September 2024, which was issued for the same reasons but halted after Morales’ lawyers launched a successful appeal. The new warrant has been reissued after Morales defied an order to testify but must still be approved by a judge. Morales has denied any wrongdoing and accused his political opponents of trying to eliminate him from the upcoming presidential election, scheduled for 10 August 2025.
Morales has reportedly taken refuge in the central province of Chapare, where he is afforded considerable political support.
Solace Global Assessment:
The issuing of the original arrest warrant in September was interpreted as a political manoeuvre executed by President Arce to bar Morales from the 2025 presidential election.
Morales supporters, largely from his Movement for Socialism (MAS) party, organised widespread protests across Bolivia, which included strikes, sit-ins and roadblocks. The demonstrations led to multiple violent clashes with the security services, severely disrupted transportation networks, and public services and cost the Bolivian economy almost USD 2 billion.
The Bolivian government’s increasing use of force to disrupt the protests resulted in an escalation of violence, leading to hundreds of injuries and over 20 fatalities.
Morales’ base will almost certainly become galvanised if a judge signs the arrest warrant, perceiving it once again as a politically motivated attempt to bar Morales. This will likely result in a resumption of major protests and road blockades across Bolivia, causing further major disruptions, shortages, price increases and multiple incidents of violence, which may continue periodically until the August election.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
Severe fuel shortages in Cuba
Cuba is suffering from severe fuel shortages, resulting in the closure of many gas stations and long queues for fuel. The fuel crisis follows a series of major electricity blackouts that caused widespread disruption and led to incidents of civil unrest. The fuel and electricity crises have almost certainly placed huge pressure on the communist-run Cuban government, which is receiving fewer fuel deliveries from its major suppliers, Mexico and Venezuela. Should the crisis continue unresolved, there is a high likelihood of unrest in the Caribbean island nation.
Security, Armed Conflict and Terror
Possible lone wolf terror attack at school in Wisconsin, USA
On 16 December, a 15-year old reportedly carried out a school shooting at a private Christian school in Madison, Wisconsin. Two people were killed, a student and a staff member, and six were injured. The attacker, who was found dead at the scene, reportedly shared a manifesto online. The document, if authentic, makes the shooting more likely to be a case of lone wolf terrorism, as the publishing of self-authored statements is a key part of lone wolves’ actions, especially in Western states. The case almost certainly is a further demonstration of the growing trend of extremely young suspects in similar cases.
Major prison riot with multiple deaths may drive protests in Tabasco state, Mexico
At least seven inmates were killed during a mass riot at a detention centre in Villahermosa, Tabasco, on 19 December. According to local authorities, the riot began after two inmates were scheduled to be transferred to a different facility. Following the riot, relatives of the inmates gathered on the Frontera-Villahermosa highway in protest. There is a high likelihood of increased security in the area. There is a realistic possibility of protestors establishing road blocks in the near future.
Gangs in Haiti hijack boat, kidnap dozens
On 13 December, “armed bandits” were reported to have boarded the vessel Nono, which was carrying 52 passengers and 6 crew, during a crossing between La Gonâve and Arcahaie. The hijackers then took the vessel to Maryani, a stronghold of the Bout Ba gang. The worsening of the economic and political situation in Haiti has almost certainly made it easier for gangs to successfully carry out hijacking operations. In August, gangs briefly captured a cargo ship carrying 60,000 bags of rice and kidnapped the crew off the coast of Port-au-Prince. In the ensuing firefight, at least two police officers were killed.
Environment, Health and Miscellaneous
Government-mandated power cuts in Ecuador
Despite President Noboa’s November declaration that power in Ecuador will be restored in December, the government has introduced mandated power cuts that are expected to last throughout December. The power outages will affect millions of Ecuadoreans and have resulted in at least seven major companies being disconnected from the public grid. The government’s inability to resolve the crisis will likely damage the economy, increase crime rates, jeopardise security systems and could lead to anti-government demonstrations in Ecuador’s major cities.
Wildfire season begins in Araucanía, Chile
On 16 December, Chilean authorities issued a red alert for the town of Lonquimay due to a blaze approaching the urban centre. The latest emergency notice is part of an increase in wildfires since late November, with the area of Carahue also affected. The Chilean wildfire season usually begins in early-to-mid December and can last for three months. Due to the difficult terrain in parts of Chile, controlling wildfires can be extremely difficult, and, especially in rural areas, residents risk becoming trapped by the blazes. There is a high likelihood that the pace and severity of wildfires will increase over the coming weeks, as temperatures in the region reach their yearly average maximums in January.
Europe, Middle East & Africa
Germany: Chancellor Scholz loses vote of no confidence
On 16 December, German Chancellor Olaf Scholz of the Social Democrats (SPD) party lost a vote of confidence in the Bundestag, which resulted in the dissolution of parliament and the calling of snap federal elections scheduled for 23 February 2025.
Out of the 717 votes cast, 207 supported Scholz, 394 opposed him, and 116 abstained. Until a new government is formed, Scholz will continue in a caretaker capacity.
The vote follows the disbandment of Germany’s ruling “traffic light” coalition of the SPD, the Greens and the Free Democratic Party (FDP) after the withdrawal of the FDP from the alliance following major disagreements over the country’s fiscal policies.
Solace Global Assessment:
In early November, Chancellor Scholz dismissed Finance Minister Christian Lindner of the FDP over escalating disputes relating to Germany’s economic policies and how to manage an expected recession. The FDP’s subsequent withdrawal resulted in the coalition government losing its parliamentary majority, triggering a broader political crisis and the scheduling of early federal elections.
Current polls indicate that Germany will drift to the right, with the centre-right Christian Democratic Union (CDU) leading with almost 32 per cent of the vote. The next highest polling party is the far-right populist party, the Alternative for Germany (AfD), which is achieving almost 20 per cent of the vote share. However, all mainstream parties have refused to enter a coalition with the AfD.
This suggests that the next government will likely be another rainbow or grand coalition, involving both right- and left-leaning parties. With the SPD, the third-highest polling party at only 17 per cent, it is highly likely that at least three parties will need to form a coalition which could take months to achieve and will likely result in a high degree of political instability.
With the rise of the AfD and the increasing popularity of the far-left populist Bündnis Sahra Wagenknecht (BSW) party, the German electoral campaign will almost certainly be characterised by increased anti-immigration rhetoric and calls to end or limit funding for Ukraine. The threat from the populist parties will also likely force the CDU to drift further right, particularly in regard to immigration.
The combined effect of increased anti-immigration rhetoric, populist rallies, increased deportations and Germany’s recent decision to suspend Syrian asylum applications will likely increase the threat of terrorism and political violence in Germany, potentially leading to incidents similar to the 2024 attacks in Mannheim.
Germany’s political polarisation will also almost certainly lead to large-scale rallies and counter-demonstrations, as witnessed during the 2021 federal elections. In 2021, AfD rallies in the East German cities of Berlin, Dresden and Leipzig often attracted thousands of participants and were met by counter-protests, frequently leading to violent confrontations.
In West Germany, where the AfD has traditionally achieved less support, large-scale and potentially disruptive protests against the AfD are likely to take place in major cities like Munich, Hamburg and Cologne. Such protests are likely to be larger and more energised than before in response to the AfD’s current polling, success in state elections and after a series of scandals and accusations of extremism.
Georgia: New anti-West president elected as pro-Europe opposition protests continue
On 14 December, Mikheil Kavalashvili was elected as president in the first Georgian presidential election conducted using an indirect vote system through a 300-member College of Electors that is composed of MPs and local government representatives.
225 electors attended the vote, with 224 voting for Kavalashvili. Kavalashvili is staunchly anti-West and a leader in the People’s Power party, which split from the ruling Georgian Dream party in 2022 but still supports the government.
Concurrently, daily pro-European anti-government protests continued, with tens of thousands still attending demonstrations which are primarily taking place on Rustaveli Avenue in the vicinity of the parliament building in Tbilisi.
European Union (EU) sanctions against Georgian officials proposed by the new High Representative Kaja Kallas were reportedly vetoed by Hungary and Slovakia, although a plan to suspend visa-free travel for Georgian officials holding diplomatic passports advanced, pending a formal proposal by the European Commission.
Solace Global Assessment:
The election of Kavalashvili constitutionally now entails the replacement of the pro-European incumbent President Salome Zourabichvili, with Zourabichvili’s term expiring on 29 December.
While the role of president in Georgia is largely ceremonial, Zourabichvili has used her position to be a figurehead for the pro-European opposition movement. She has previously vowed to remain in office when her term expires (due to accusations that the Georgian parliament is illegitimate following the allegedly fraudulent October election) and called Kavalashvili’s election “a mockery of democracy”.
The opposition protest movement has likely gradually lost momentum over the past two weeks, with the scale of demonstrations reducing, although daily protests have continued.
However, the demonstrations have thus far failed to pressure the government to compromise. With the opposition parties lacking any political mechanisms to challenge the government, in addition to the protest movement currently losing the ‘battle on the streets’ with riot police, it is highly unlikely that Georgian Dream will be compelled to make meaningful concessions.
Nonetheless, 29 December will be a key date for potential escalation. If Zourabichvili refuses to step down, as promised, she may be forcibly ousted or even arrested. This would highly likely trigger further unrest.
Alternatively, Zourabichvili may extract negotiated concessions from the government in return for stepping down, though it is likely that any concessions Georgian Dream is willing to make will be merely symbolic.
Syria: Kurdish-controlled northeast Syria under imminent threat of Turkish-led offensive
The leader of Hay’at Tahrir al-Sham (HTS) Ahmed al-Sharaa (commonly known by his former nom de guerre Abu Mohammed al-Golani) stated that all rebel factions in Syria will be “disbanded and the fighters trained to join the ranks of the defence ministry”. Furthermore, a senior HTS commander called for a unified Syrian state without federal regions, raising serious questions about the prospects of the Kurdish-occupied territories in northeast Syria.
Clashes have continued between the Turkish-backed Syrian National Army (SNA) with conventional Turkish military support and the Kurdish-led Syrian Democratic Forces (SDF). While a US State Department official stated on 17 December that a ceasefire around Manbij had been extended until the end of the week, on 19 December Turkish defence ministry officials stated that no such ceasefire talks have taken place and that Turkish-backed forces will ultimately control the Kurdish areas in northern Syria. In reaction, the SDF vowed to fight Turkey and called on residents in Kobani to take up arms.
Solace Global Assessment:
In the past week following the initially scheduled expiration of the Manbij ceasefire (which was highly likely not comprehensive in effect even when active), clashes with heavy weaponry and artillery barrages have taken place at key strategic locations along the Euphrates River at the Qereqozaqê Bridge and Tishreen dam. It is likely that in the near future, Turkish-backed forces with the support of conventional Turkish artillery and airpower will escalate operations against the SDF. There is additionally a realistic possibility that Turkish ground forces will launch an offensive against Kobani.
Currently, Kurdish forces are being pushed back to the Euphrates River, which likely provides a more advantageous defensive position against further SNA offensives from the west. HTS, which controls the interim government in Damascus, has received significant support from Turkey, although it is almost certainly not a Turkish proxy force in the same manner as the SNA. Nonetheless, HTS proposals that essentially imply that the SDF should disarm pose an existential threat to Kurdish control in northeast Syria.
It is unclear how the forthcoming Trump administration will treat the issue, however, Trump has stated on social media that the US should “not get involved” in Syria. Without substantial US support, it is likely that the SDF will struggle to maintain autonomy in the face of significant Turkish-led offensives. It is highly likely, given the threat, that the SDF will refuse to disarm. It is almost certain that a conventional Turkish military invasion would drastically increase the likelihood of attacks conducted by the Kurdistan Workers’ Party (PKK) in Turkey.
Ghana: Supreme Court dismisses challenges to new LGBT legislation
On 18 December, the Supreme Court of Ghana rejected two separate legal challenges against the country’s proposed anti-LGBT legislation. The rejection will enable President Nana Akufo-Addo to sign the bill into law, who had delayed signing it in response to the legal challenges. The bill was unanimously approved by Ghana’s parliament in February and has also been widely supported by a coalition of Christian, Muslim and traditional leaders.
Solace Global Assessment:
With such widespread support it is highly likely that President Akufo-Addo will pass the bill. This is despite international condemnation and warnings as to how the bill might affect Ghana’s economy, with fears it may jeopardise financial assistance from both the World Bank and the International Monetary Fund.
The bill has been described as one of the most restrictive anti-LGBT laws in Africa and likely reflects a conservative backlash. Whilst same-sex sexual activity was already punishable by up to three years, the bill will increase the prison sentence to five years and also cover the support and promotion of LGBT activities. This last component is vaguely defined and will likely be exploited to target not only individuals engaging in same-sex relations but also those who advocate for LGBT rights or provide support to LGBT communities.
The broad and ambiguous nature of the law could lead to its use against a wide range of activities, including public demonstrations, media discussions and online speech. The passing of the bill will likely serve to legitimise both anti-LGBT sentiment and violence, which will likely increase in Ghana in the long term, leading to major safety concerns and discrimination for both LGBT local nationals and foreign travellers. Foreign LGBT travellers will likely have to adopt a more cautious approach when visiting Ghana and avoid any activities that could be interpreted as promoting or supporting LGBT rights.
Mozambique: Protests halted until Constitutional Council declares election validation results on 23 December
Protests have been ongoing in Mozambique since the October elections. On 16 December, security forces reportedly shot dead two mourners at the funeral of a popular blogger in Ressano Garcia. The incident occurred after mourners blocked roads with trucks, which security forces responded to using live ammunition.
Opposition leader Venâncio Mondlane announced a suspension of protests until the Constitutional Council announces its verdict on electoral results on 23 December. Mondlane has declared the schedule until this date, calling for protesters to undertake four days of mourning from 19-22 December, maintaining normal work activities and refraining from protesting.
On 23 December, Mondlane requested that all activity must stop in Mozambique and that citizens must stay in their homes or in the vicinity of the Constitutional Council to listen to its judgement. According to Mondlane, if the Council, which is currently in the process of validating the election results, declares Frelimo as the legitimate winner, then the “TurboV8” phase of protests will begin. As he stated in his latest announcement, “everything is in the hands of the Constitutional Council”.
Solace Global Assessment:
Protesters have, so far, generally adhered to Mondlane’s schedules. Therefore, country-wide unrest across multiple cities will be unlikely to take place over the 19-23 December period. However, there is a realistic possibility that localised demonstrations will occur in reaction to perceived heavy-handedness by security forces.
It is unclear whether the “TurboV8” phase will begin immediately on 23 December following the Council’s announcement. It is highly likely that Mondlane will use Facebook to livestream the details of the “TurboV8” phase shortly after the announcement if the Council rules in favour of Frelimo. While Mondlane may harness popular outrage to call for protests to begin the same day, there is a realistic possibility that the “TurboV8” phase will begin on 24 December.
The Constitutional Council is generally viewed as an arm of the government and will likely declare the results valid. The Mozambican Bar Association has criticised the Council’s process, declaring it illegal. They claim the only response should be a vote recount or a cancellation of the elections. The Council has instead claimed that its review is limited to verifying the results sheets and polling station minutes, rather than recounting original ballots. This method may expose discrepancies such as mismatches with party-held copies or inconsistent totals but will not be as thorough as a full recount.
The Council of State, which advises the President of Mozambique, has called for reforms to the country’s electoral legislation. Podemos, the opposition party, has called for a vote recount. As a further indication of mounting political pressure on the government, Angola has urged South Africa to find a regional solution to the instability.
Mayotte: Tropical Cyclone Chido inflicts significant damage in multiple regions
Cyclone Chido left a significant impact on the French department of Mayotte and neighbouring regions including Comoros, northern Madagascar, the Cabo Delgardo region of Mozambique, and Malawi. As of December 19, the United Nations reports that at least 31 people have died and around 100,000 individuals have been displaced in Mayotte due to the cyclone.
French President Emmanuel Macron has declared a national mourning day on December 23 to honour the victims. Macron is currently in Mayotte to assess the damage and visit remote areas affected by the storm. The cyclone has caused widespread power and communication outages, leaving approximately 76,000 people without power or internet in the Mecufi District of northern Mozambique. The death toll in Mozambique has risen to 45, with over 174,000 people impacted. In Malawi, the storm has resulted in seven deaths and affected more than 7,700 households.
The situation in Mayotte remains critical, with authorities implementing curfews to maintain order as they continue recovery and relief efforts. The Red Cross has reported losing contact with 200 volunteers due to the outages. The French government and international organizations are actively working to assist and restore services in the affected areas. Mayotte’s only international airport has experienced major damage, making it difficult for authorities to restart operations.
Solace Global Assessment:
Mayotte, a French overseas department, has experienced significant political tensions driven by illegal migration and economic frustrations. Its high levels of poverty and crime alongside overwhelmed infrastructure from the high numbers of migrants make it France’s poorest department. The French government has recently attempted to revoke birthright citizenship, changing Mayotte’s constitution and conducting mass deportations, a highly controversial move.
The damage from the tropical cyclone is highly likely to exacerbate tensions by further straining Mayotte’s infrastructure, damaging its crops, and pushing more residents below the poverty line. Mayotte’s population may, therefore, direct its anger against the ruling authorities and conduct significant social unrest to express their frustration. Macron’s declaration of a National Day of Mourning is likely indicative of his concern over popular sentiment.
In Comoros, strained resources, deforestation, and coastal erosion have worsened poverty, with 40 per cent of the population living below the poverty line. The recent cyclone has caused significant damage, further disrupting communities and affecting agriculture, which employs over 35 per cent of the population. Parliamentary elections on 12 January 2025 are highly likely to be impacted, with heightened tensions and potential unrest likely escalating in the coming weeks.
In Mozambique, the cyclone has affected the Cabo Delgado region, an area experiencing an ongoing insurgency. Moreover, significant unrest regarding the October election has been ongoing in the region. The government’s ability to commit resources to the areas affected by the cyclone will highly likely be significantly hindered. While the coming days may see reduced unrest as communities seek immediate safety in the aftermath of the cyclone, unrest in Pemba will likely increase in the coming weeks.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Libya’s rival factions resume talks in Morocco
On 18 December, delegations from Libya’s two rival warring factions resumed talks near Rabat, Morocco. The talks were held between the country’s two legislative bodies, the High Council of State based in Tripoli in the west and the House of Representatives based in Benghazi in the east, which emerged after the collapse of the Gadafi regime. However, major disagreements over proposed electoral processes, candidate eligibility, and the legitimacy of the rival governments will likely
impede progress towards a lasting resolution.
These factions remain entrenched in their positions, with the House of Representatives insisting on the legitimacy of its government in the east, while the High Council of State in the west refuses to recognise it.
BBC banned in Niger by junta government
The Nigerien junta has banned the BBC from operating in the country for three months after alleging that the media outlet spread false information. The accusation suggests that the BBC spread false information regarding a jihadist attack that reportedly killed 90 government troops. The junta has argued that the report will undermine troop morale, embolden militants and destabilise the country. However, the BBC is just the latest Western media outlet to be banned in the country and it is likely that the junta is attempting to limit its exposure to international criticism as such reporting is likely to increase internal condemnation of an increasingly fragile government.
Liberian parliament building torched during protests
On 18 December, the parliament building in Monrovia was set on fire during severe civil unrest. The protests were driven by ongoing debates about the House of Representatives’ push to remove House Speaker Konati Koffa over allegations of corruption. According to local media, “dozens” of protesters were arrested between 17 and 18 December, and police deployed tear gas to control the crowds. There is a realistic possibility of the protests increasing in severity as the political situation develops.
Security, Armed Conflict and Terror
Beginning of Catholic Jubilee to affect terrorism and sabotage risk in Italy
The year-long event begins on 24 December. It is expected that the event will result in a significant increase in tourist arrivals in Rome and other major Italian cities. The jubilee is likely to result in increased anti-tourism incidents in Rome, Florence, Bologna, Milan, and other cities. Possibly, action will include vandalism of private businesses, hotels, and vehicles, or attacks on transport and energy infrastructures.
There is a realistic possibility of a terror attack due to the high visibility of the event and its Catholic identity. Note that, in September, the US State Department increased Italy’s travel threat level to 2 (“exercised increased caution”) due to the possibility of a terror attack.
Growing Islamic State presence in northeast Azerbaijan
An alleged Islamic State (IS) supporter was shot and killed during a confrontation with police forces in the Qusar district. This is the second reported case of IS activity in Qusar in a few months. In September, multiple Azeri police officers were killed in a clash with militants which was claimed by IS as the first “official” attack in Azerbaijan. The recent killing is likely a further demonstration of the growing IS presence in the Qusar area.
More broadly, IS operations in the Caucasus may benefit from multiple factors: Russia’s growing difficulty in allocating resources to police its at-risk regions, the growing traction of Asia-based IS networks and groups, and the return of Azeri foreign fighters previously active in Syria.
US imposes new sanctions on Yemen’s Houthis after escalation with Israel
The US government has imposed new sanctions on the Houthi Movement, which follows a recent escalation between the Iranian-backed group and Israel. On 19 December, a school in the city of Ramat Gan in the Tel Aviv district was damaged by a partially intercepted ballistic missile launched by the Houthis after a series of other attempted attacks on Israel. Israel retaliated with strikes on Houthi targets, including port and energy infrastructure in both Sana’a and al-Hudaydah.
The Houthis have likely increased their Iranian-sponsored attacks in response to Iran’s strategic loss of influence in the Middle East following the collapse of the Assad regime in Syria and the degradation of Lebanese Hezbollah. There is a high likelihood that new US sanctions, Israeli attacks and recent US Central Command (CENTCOM) strikes on the Houthis will result in an increase in Houthi attacks on merchant shipping near Yemeni waters.
Peace talks cancelled between DRC and Rwandan governments
DRC President Felix Tshisekedi and Rwanda’s President Paul Kagame were scheduled to meet as part of the Angola-mediated peace talks. However, the Rwandan delegation reportedly declined to participate, citing the condition for dialogue between the DRC and the Rwanda-backed M23 rebels, which the Congolese government had rejected. According to a UN report, 3,000 to 4,000 Rwanda Defence Force troops are fighting alongside the M23 Movement in the North Kivu Region.
While Kigali has been accused of providing material and logistical support to M23, the group is not directly beholden to Kigali. Furthermore, Kigali has frequently denied directly backing the M23 rebels, which has been accused of numerous war crimes including killing civilians. Taking part in peace talks without engaging the group would, therefore, be an admission of direct influence on the group, which Kagame is unlikely to accept.
Intense clashes in the region have occurred this week, with M23 rebels taking control of the Bingi village near Lubero on 18 December amidst an ongoing northern offensive against the DRC military. Thousands of civilians have reportedly fled the Lubero area amidst the M23 advance.
Environment, Health and Miscellaneous
Widespread power outage in Kenya
On 18 December, a six-hour power outage occurred across most of Kenya. The power outage resulted in network connectivity metrics dropping to approximately 50 per cent in Kenya and neighbouring Tanzania. The cause has yet to be officially determined, with Kenya Power stating that investigations are underway. However, the Kenyan Cabinet Secretary of Energy, Opiyo Wandayi, and anonymous Kenya Power sources have suggested that the outage resulted from a fault in Tanzania on the Kenya-Tanzania power corridor. Kenya has struggled with power outages in recent months, with other recent major blackouts also being blamed for regional connections with neighbouring countries.
Asia–Pacific
Pakistan: Militants continue attacks on polio vaccination teams
Militants in Pakistan’s restive Khyber Pakhtunkhwa province have continued their attacks on polio vaccination teams as the government attempts to complete the last vaccination drive of 2024. Twin attacks on 16 December in the Bannu and Karak district targeted the security forces assigned to protect the vaccination teams. In Karak, gunmen opened fire on a police convoy escorting polio workers, killing one officer and injuring a health worker. In Bannu, a police officer guarding a vaccination team was injured after being shot by an assailment on a motorcycle.
Then on 17 December, three police officers were killed after an improvised explosive device (IED) detonated on the roadside in Dera Ismail Khan district.
Solace Global Assessment:
No group has claimed responsibility for the attack; however, the most likely group was the Tehrik-i-Taliban Pakistan (TTP) or Pakistani Taliban. The group has long supported conspiracy theories that polio vaccinations are a Western attempt to sterilise Muslim children and has been responsible for a series of historical attacks on health workers and their security escorts.
However, there is also a realistic possibility that Baloch militants such as the Balochistan Liberation Army (BLA) could have conducted the attacks as they are in the southern districts of Khyber Pakhtunkhwa province close to Balochistan. The timing of the attack is unlikely to be coincidental. The attacks were timed to take place on the starting day of the final 2024 vaccination drive and are likely a direct response to Prime Minister Shehbaz Sharif’s recent declaration that Pakistan will win the war against polio.
The attacks will likely disrupt the vaccination drive and will likely continue if the drive isn’t suspended. A drive in Balochistan was postponed on 18 December in response to the attacks. Previous attacks, which disproportionately target the security services, have previously resulted in police strikes that have forced suspensions. However, the high-profile nature of the attacks has attracted international attention, with the campaign supported by the Bill & Melinda Gates Foundation and the World Health Organization (WHO).
Under international attention and with polio rates continuing to increase, Islamabad is unlikely to call off the vaccination drives. To enable the continuation of vaccination campaigns, the authorities will likely issue Section 144s to limit militants’ opportunity to attack and will have promised to deploy more security resources to areas like Khyber Pakhtunkhwa and Balochistan. Given the ongoing insurgencies in both provinces and the already overstretched Pakistani forces, these measures could lead to more attacks on security forces. Militant groups will likely target both the vaccination campaigns and government forces elsewhere in a bid to further overstretch the security services and undermine the government’s authority.
Vanuatu: Magnitude 7.3 earthquake caused severe damage in Vanuatu’s capital city
On 17 December, a magnitude 7.3 earthquake at a depth of 57.1km occurred 30km west of Vanuatu’s capital, Port-Vila. As a result, Port-Vila experienced severe shaking which caused considerable damage. A tsunami was initially issued, but withdrawn after two hours. Being so close to Vanuatu’s most populous urban area, the powerful earthquake has caused at least 14 deaths, with 200 people being treated for injuries. Telecommunications, electricity and water supply were each significantly impacted. The acting Prime Minister of Vanuatu, Charlot Salwai, declared a state of emergency that is in effect until at least 23 December, with a 18:00-06:00 local time curfew.
Solace Global Assessment:
Vanuatu is one of the most natural disaster-prone countries in the world, due to the frequency of both earthquakes and tropical cyclones that impact the archipelago. This earthquake, however, is almost certainly one of the worst natural disasters to affect Vanuatu in decades, due to the intensity of the earthquake and its close proximity to the capital. The UN estimates that 116,000 people could be affected and major humanitarian challenges have resulted.
Port-Vila is without water due to reservoirs being destroyed, and there is a near-total internet outage due to a submarine cable being damaged. Due to the nature of these damages, it is unlikely that they can be rapidly fully repaired. Reports indicate that despite the internet outage, Starlink customers have been able to access the internet with Starlink coverage of Vanuatu becoming officially available in October.
Port Vila Bauerfield International Airport (VLI) was closed for 72 hours except for relief flights – despite the scheduled 21 December reopening, it is likely that access to the airport will remain difficult due to blocked roads and bridges.
A snap election had been called for 14 January 2025 following the dissolution of parliament by Salwai, with a constitutional challenge to the dissolution by opposition MPs being dismissed by the Vanuatu Chief Justice merely days before the earthquake. There is a realistic possibility that the election will be postponed, which would likely prolong Vanuatu’s current political crisis.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Protesters block trains in ‘rail roko’ protests in Punjab, India
As part of long-standing farmers protests in the Punjab, protesters on 18 December blocked railway tracks to press their demands. These protests have been labelled the ‘rail roko’ protests, and resulted in disruptions to train services across the state. The farmers have numerous demands, including minimum price controls and pensions. Previously, farmers have used tractor convoys and road blockades.
A key current trigger for civil unrest is the condition of a farmer protest leader, Jagjit Singh Dallewal, who on 19 December entered his 24th day of a “fast-unto-death” hunger strike. Dallewal’s condition has reportedly turned critical and the Supreme Court has directed the Punjab government to intervene.
If Dallewal either dies of starvation or is force-fed (a dangerous and often violent procedure), it is likely this will further inflame unrest.
Protests erupt in Taiwan over proposed opposition amendments
On 19 December, over 10,000 people gathered near the Legislative Yuan in Taipei to join an organised protest over proposed amendments put forward by Taiwan’s current opposition party, the Kuomintang (KMT). The demonstrations were sparked by proposed amendments to key laws, including the Public Officials Election and Recall Act, the Constitutional Court Procedure Act, and the Act Governing the Allocation of Government Revenues and Expenditures.
Protestors have stated that the amendments are undemocratic and would curtail judicial independence. If the amendments are approved in the Legislative Yuan on 20 December, they will be sent to the president for signing into law—an outcome that is likely to spark further and potentially more intense unrest.
Security, Armed Conflict and Terror
Indian police arrest Bangladeshi militants plotting terror attack
On 18 December, police in the Indian state of Assam apprehended five members of the Islamist militant group Jamaat-ul-Mujahideen Bangladesh (JMB) which reportedly foiled an impending terror plot. JMB is a proscribed terrorist group whose main objective is to establish an Islamic state in Bangladesh to replace its secular democracy.
It is highly likely that the plot was inspired by the wider tensions between India and Bangladesh. Since the ousting of Prime Minister Sheikh Hasina in Bangladesh, there have been multiple incidents of sectarian violence in both India and Bangladesh between Hindus and Muslims, a trend that is likely to continue with Hasina seeking shelter in India.
Environment, Health and Miscellaneous
Reports that Myanmar junta coerced NGOs into not reporting food scarcity figures
According to a report released by Reuters, the military government of Myanmar carried out arbitrary detentions and other intimidation actions to discourage food security researchers from reporting on widespread hunger in areas of the country under government control. The report is notable as it highlights growing risks faced by humanitarian workers in Myanmar.
The junta, which continues to lose ground against the many rebel groups it is facing, likely has a strong interest in portraying itself as the only capable administrator for the country. As the junta’s diplomatic and military situation worsens, it is likely that the suppression of NGOs will continue.
Moreover, disruptions of aid operations may have broader spillover effects in the region, for instance by increasing refugee flows to Bangladesh’s Cox Bazaar area, which continues to house hundreds of thousands of people displaced from Myanmar.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence

Cyclone Chido: Mayotte, Comoros, and Mozambique Face Crisis
Intelligence cut off: 12:00 GMT 16 of December 2024
On 14 December 2024, Cyclone Chido hit the French Overseas Territory of Mayotte in the Indian Ocean. Cyclone Chido is considered the most severe cyclone to hit the region in almost 100 years, making landfall in Mayotte at Intense Tropical Cyclone strength with maximum wind speeds exceeding 225 km/h (139 mph).
At least 14 fatalities have been recorded; however, authorities currently assess that the death toll could reach 1000 with thousands more displaced. Hundreds of homes have been destroyed and several government buildings have been severely damaged, including Mayotte Hospital and multiple medical centres have been rendered non-operational.
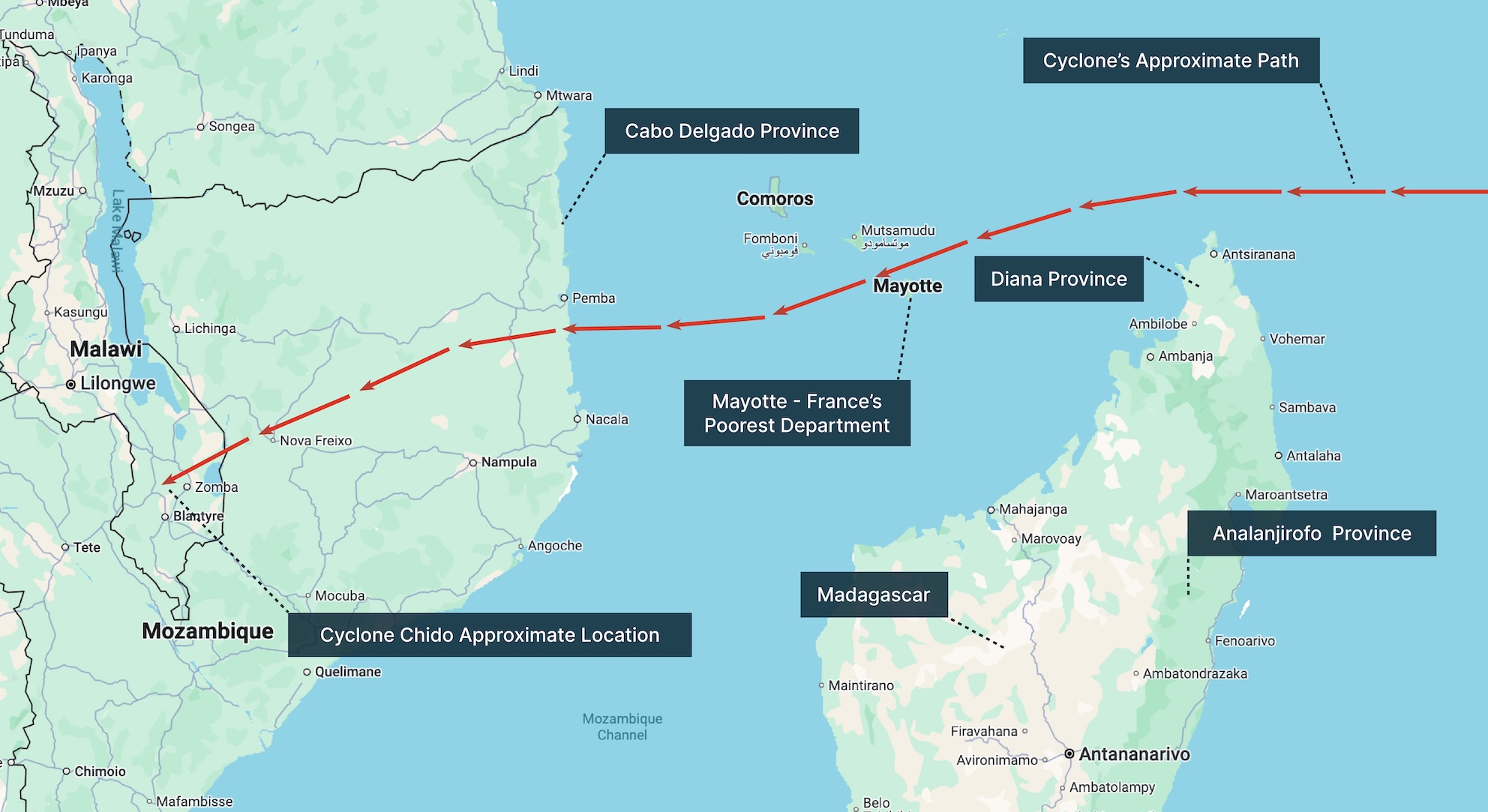
Cyclone Chido Path
In Comoros, storm surges caused by Cyclone Chido resulted in widespread flooding in the capital Moroni and other coastal towns. Flooding has damaged multiple homes, businesses, fishing infrastructure, and roads, disrupting transport and delaying emergency responses.
In Madagascar, the northern regions of Diana and Analanjirofo regions were primarily affected by flooding, resulting in damage to transport infrastructure, homes and energy infrastructure, leading to blackouts.
Cyclone Chido made landfall in the Cado Delgado province in Mozambique early 15 December, threatening 1.7 million people. The storm damaged or destroyed homes, schools, and health facilities, and numerous flights were cancelled at Pemba Airport. Cabo Delgado has reportedly experienced large-scale internet disruptions caused by the storm. Authorities have warned of potentially having to evacuate low-lying areas.
SOLACE GLOBAL COMMENT
Cyclone Chido Recovery: France Mobilises Rescue Teams for Devastated Mayotte
Recovery efforts are ongoing in Mayotte and the death toll is almost certain to rise. France has mobilised rescue teams and supplies from mainland France and the French territory of Reunion, with 160 firefighters and soldiers being sent to Mayotte to bolster the 110 French military personnel currently undertaking rescue operations. The immediate effort of French rescue teams is to establish an air and sea bridge to Mayotte to facilitate the delivery of humanitarian aid.
There are severe transport disruptions in Mayotte, including mass flight cancellations at Dzaoudzi Pamandzi International Airport (DZA), which has been subjected to significant levels of damage. The French interior ministry is set to host a crisis meeting on the situation to determine response. Travellers to the area should expect mass disruption to healthcare provision and significantly slowed emergency response times.
Due to the intense rainfall in northern Mozambique, there is a high risk of landfalls. Furthermore, authorities have indicated that communities may be cut off from schools and health facilities for weeks due to damaged infrastructure. Mozambique’s meteorological agency has issued warnings for multiple provinces due to strong and dangerous winds until midnight on 17 December.
The storm weakened into a moderate tropical storm then a remnant low on 16 December as it tracked into Malawi. As of 16 December, sustained windspeeds have reduced to approximately 50 km/h (31 mph). Malawi is unlikely to be significantly impacted by the storm, but transport-related disruptions cannot be ruled out.
SOLACE GLOBAL ANALYSIS
Storm Damage Likely to Trigger Unrest as Mayotte, Comoros , and Mozambique Grapple with Recovery
Areas that Tropical Cyclone Chido has affected will almost certainly experience transport disruptions. Mayotte’s only international airport has experienced major damage, making it difficult for authorities to restart operations. Damage to infrastructure in areas affected by the storm may affect recovery efforts and will almost certainly exacerbate health and poverty issues in the coming weeks. Death tolls will almost certainly continue to rise as authorities confirm casualties from the storm.
Mayotte, a French overseas department, has experienced significant political tensions driven by illegal migration and economic frustrations. Its high levels of poverty and crime alongside overwhelmed infrastructure from the high numbers of migrants make it France’s poorest department. The French government has recently attempted to revoke birthright citizenship, changing Mayotte’s constitution and conducting mass deportations, a highly controversial move.
The damage from the tropical cyclone is highly likely to exacerbate tensions by further straining Mayotte’s infrastructure, damaging its crops, and pushing more residents below the poverty line. As such, Mayotte’s population may direct its anger against the ruling authorities and conduct significant social unrest to express their frustration.
In Comoros, resources are generally strained. Deforestation and coastal erosion have caused significant damage to local communities and approximately 40 per cent of the population lives below the poverty line. The cyclone has caused significant damage, which will almost certainly further disrupt local communities and strain government resources, displacing many. Agriculture, which accounts for over 35 per cent of employment, will likely be affected by damaging winds and flooding, pushing more residents below the poverty line. Parliamentary elections are set to take place in Comoros on 12 January 2025. The damage inflicted by the storm is highly likely to exacerbate tensions, which are already high and may contribute to unrest in the country.
In Mozambique, the cyclone has affected the Cabo Delgado region, an area experiencing an ongoing insurgency. Moreover, significant unrest regarding the October election has been ongoing in the region. As such, the government’s ability to commit resources to the areas affected by the cyclone will highly likely be significantly hindered. While the coming days may see reduced unrest as communities seek immediate safety in the aftermath of the cyclone, unrest in Pemba will likely increase in the coming weeks.
Travel Risk Advice: Precautions for Cyclone Chido-Affected Zones
- Closely monitor local news reports and government alerts.
- Adhere to all instructions issued by the authorities.
- Follow evacuation orders and travel to government-designated shelters if it is safe to do so.
- Do not return to your residence until authorities have declared it safe.
- Ensure that important documents and medications are stored in a waterproof container.
- Maintain communication with an emergency contact and conduct regular check-ins.
- Prepare an emergency “go bag” with essentials such as bottled water, batteries, important documents, and medications.
- Confirm that booked flights are operating before checking out of hotels or travelling to the airport.
- Prepare for power outages, communication disruptions, and travel delays.
- Due to the risk of flooding, avoid low-lying coastal areas and locations near bodies of water whenever possible.
- Stay away from damaged buildings and affected areas until authorities have deemed them safe.
- Do not drive or walk through flowing water, even if it appears relatively shallow.
- Exercise caution around downed power lines and unstable structures.
- Dispose of any food that has been exposed to floodwater.
- Do not use damaged electrical appliances.
- If you smell gas, leave the area immediately.
- Monitor yourself and others for symptoms of waterborne diseases and seek medical advice immediately if symptoms appear.
- Management should maintain communication with affected individuals until the event has concluded.
Subscribe to free weekly intelligence

Executive Summary
- The mass killing of almost 200 elderly people in Haiti’s capital almost certainly underscores the collapse of state control and its ability to maintain law and order.
- The government’s sustained crackdown on opposition figures and the upcoming presidential election will highly likely intensify protests in Georgia.
- There is a realistic possibility that a second civil war could break out in Syria following the fall of the regime, with multiple challenges facing Damascus’ new HTS-led government.
- Unrest is highly likely to continue in South Korea until President Yoon Suk Yeol is impeached or steps down.



AMER
Haiti: Gangs kill more than 180 over voodoo accusations
Colombia: Government conducts first air strikes on armed group
EMEA
Georgia: Protests continue amidst increasing political violence
Syria: Assad regime falls after lightning rebel offensive
Iran: Tehran re-assessing its geopolitical stance following Assad fall
Somalia: Fighting starts between Mogadishu and Jubaland
Mozambique: “4×4” unrest phase ends as “TurboV8” phase announced
APAC
Afghanistan: Senior Taliban leader killed in suicide bombing
South Korea: Impeachment fails as opposition prepares second attempt
North, Central and South America
Haiti Gangs massacre 184 people over voodoo accusations
On 6 and 7 December, at least 184 people, most of whom were elderly, were killed in Cite Soleil with guns, machetes, and knives. The murders were reportedly orchestrated by gang leader Monel Felix, or “Mikanò”, of the Micanor gang who reportedly acted upon the belief that his child’s illness was caused by witchcraft. In response, Haiti’s government has promised to “mobilise all its forces to track down and annihilate” the perpetrators.
Despite the severe violence, Doctors Without Borders (MSF) announced it would resume some operations in Haiti on 11 December, with however a limited scope due to the security situation. On the same day the government announced that Port-au-Prince airport would reopen for civilian flights, after it was forced to shut when multiple planes were hit by gunfire.
Solace Global Assessment:
The mass-killing occurred in Cite Soleil, which is one of the most impoverished parts of the Port-au-Prince metropolitan area. The Wharf Jeremie neighbourhood, which includes the eponymous port, in Cite Soleil is the stronghold of the Micanor gang. According to local media, the massacre occurred at a time when gangs are increasing their attacks on poor neighbourhoods of Port-au-Prince amidst an overall worsening security situation. Last week, two police officers were killed in the Nazon area during a shootout with members of the gang coalition Viv Ansamn, which controls much of the capital.
As gangs continue to operate with impunity in most of the capital, the international peacekeeping mission led by Kenyan police has likely failed to restore a degree of order. In early December, reports emerged that around 20 officers had resigned from the UN-backed mission due to unpaid wages, which Kenyan officials deny. The likely economic pressures will further add to domestic opponents of the Kenyan government, which have protested the use of government resources abroad as a personal prestige-seeking effort by President William Ruto.
The security situation in Haiti is likely to remain extremely deteriorated. Gangs have adopted a strategy aimed at destroying all alternative administrative authorities in the country, including by targeting missions and NGOs, and at paralysing communications and contacts with the outside world. It is likely that, as flights resume and intensify, gangs will once again begin firing on civilian aircraft, possibly resulting in casualties and prompting further airport closures.
Colombia: Petro government conducts first air strikes on armed groups
On 9 December, the government of leftist President Gustavo Petro announced that it had conducted its first ever air strikes on the Gulf Clan.
The air strikes targeted the powerful organised crime group in the department of Antioquia in northwest Colombia, a key stronghold of the Gulf Clan, where it oversees extensive operations in drug trafficking, human trafficking, and illegal gold mining and controls an estimated 52 per cent of the municipalities.
The strikes resulted in the deaths of at least four members of the Gulf Clan and were aimed at denying the group the ability to build up its resources in the department of Antioquia where it already poses a credible threat to the government.
Solace Global Assessment:
For over half a century, successive right-wing governments in Colombia relied on airstrikes to combat cartels and left-wing guerrilla groups, including the Marxist FARC movement, which disarmed following a historic peace agreement in 2016.
This strategy was abandoned by President Petro’s government, which has tried to minimise collateral damage and establish “total peace” in Colombia. However, various armed groups have exploited ceasefire deals to consolidate power and build up their capabilities rather than commit to genuine peace talks.
The head of Colombia’s armed forces recently indicated that this has been the case in what was likely a challenge to the Petro administration. The resumption of air strikes may indicate a shift in strategy by the Colombian armed forces and is likely to threaten the progress of continued ceasefire agreements.
The Gulf Clan is one of the fastest growing criminal organisations in Colombia which was formed from remnants of right-wing paramilitary groups that had been disbanded under the peace process.
The group dominates much of the drug routes in Colombia, has destabilised rural locations, has been implicated in multiple attacks on the government and has established itself in at least 24 of Colombia’s 32 departments.
The government’s use of air strikes likely enables it to disrupt Gulf Clan operations without having to commit to major and often costly ground offensives in rural areas. Moreover, there is a realistic possibility that the strikes also serve as strategic messaging to FARC dissidents who have refused to engage in peace talks and are also heavily involved in organised crime.
The extension of air strikes targeting other armed groups cannot be ruled out; however, this shift will likely be a major roadblock towards Petro’s plans of total peace and will likely provoke retaliatory attacks by the armed groups.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
Donald Trump vows to end US birthright citizenship, pardon some 6 January rioters
The President-elect likely lacks the ability to carry out the former reform, as it is enshrined in the US Constitution, and attempts to abolish it by executive decree are almost certain to meet significant opposition by the legislative and judiciary branches of government.
Meanwhile, the second pledge falls within the president’s powers and could be carried out on “day one” of the presidency.
Both moves are likely to be extremely politically contentious if implemented or even just attempted, and are likely to result in widespread protests, especially in large urban areas like New York and Washington, as well in areas with a large presence of first-generation US citizens.
Mexican truck drivers block major roads to protest the non-payment of bills
On 10 December, truck drivers staged blockades on two major highways, one near Mexico City and another in the Yucatán Peninsula, to protest unpaid wages from government subcontractors.
The subcontractors claimed they withheld payments because the government had not settled its debts with them after their work on a trainline. The government announced it had begun releasing funds to these companies, which is expected to reduce the likelihood of further protests from truck drivers who worked on this project.
This event reflects a larger problem of delayed government payments, stemming from significant deficits incurred to fund projects initiated under the previous administration. If companies continue to withhold wages from workers due to unpaid government contracts, additional protests are likely.
Security, Armed Conflict and Terror
NGO report reveals human rights abuses in Nicaragua
A report by the Nicaragua Never Again Human Rights Collective released on 8 December has indicated that at least 229 people detained for political reasons in the country over the last seven years have suffered torture and other forms of human rights abuses.
The NGO documented at least 40 different types of torture used by the Ortega regime, which has also recently passed reforms to extend the powers of the police, military and the president to curb internal unrest.
The Office of the United States Trade Representative will now also launch an investigation into Nicaragua’s government for persistent attacks on labour rights, human rights and the rule of law, with much of the abuse aimed at NGOs, civil society organisations, journalists and the Catholic Church.
Mexican congressman killed in Veracruz
On 9 December, Congressman Benito Aguas Atlahua of the Ecologist Green Party of Mexico (PVEM), was gunned down in the Mexican state of Veracruz.
The killing is part of a wider trend of political violence across Mexico, which led to over two dozen politicians being killed in the run-up to the 2024 elections. However, those targeted are typically local politicians and the killing of a federal congressman who is also part of the ruling coalition will likely present a major challenge to President Claudia Sheinbaum and has raised questions over her internal security policies.
The high-profile nature of the attack is likely to add extra pressure on the government to curb cartel violence and break from its current strategy of “hugs, not bullets”.
Environment, Health and Miscellaneous
Large wildfires in Malibu, California destroy homes and force evacuations
The “Franklin Fire” ignited on 9 December near Malibu and advanced towards the town, burning, as of 12 December, an area of approximately 4,000 acres.
The fire prompted mass evacuations from the area, with approximately 22,000 people estimated to be affected. This is the latest in a series of severe wildfires that have affected the Los Angeles area of California over the past months and have been exacerbated by dry and warm conditions during the summer.
Extinguishing these wildfires is further complicated by the mountainous geography of southwestern California, which makes accessing the affected areas more difficult. As of the time of writing, the fire is assessed as being 20 per cent contained.
Central and South America experiences record year for dengue fever
Pan American Health Organisation (PAHO) has stated that 2024 was a record year for dengue fever across Central and South America, with Brazil, Argentina, Colombia, and Mexico worst affected.
The increases have largely been driven by a hotter and wetter climate which has been exacerbated by poor waste management, creating stagnant bodies of water which are ideal breeding grounds for dengue carrying mosquitoes.
The report warned that the virus is posing a higher than usual risk to children, with children making up around 70 per cent of dengue related deaths in Guatemala and a significant proportion in other parts of Latin America.
Wildfire season in Chile’s Valparaiso region
Recent fires in Chile’s Valparaiso region have prompted evacuation orders and emergency responses from authorities. On December 7, a red alert was issued in Quillota, where evacuation orders were enforced in the Enrique Arenas area due to a significant blaze. Similarly, a yellow alert was declared in Cartagena.
On 10 December, a large forest fire occurred near Calle Larga, southwest of Los Andes. In Catemu, Valparaíso, a red alert was put into effect as a wildfire consumed over 345 acres, leading to the evacuation of at least 25 people and affecting five homes. These events underscore the ongoing severity of the wildfire season in the region; further wildfires are to be expected. Chile’s wildfire season typically begins in early December and runs for approximately 19 weeks.
Europe, Middle East & Africa
Georgia: Ongoing anti-government unrest in Georgia amidst increasing political violence
Protests against the Georgian Dream government which intensified following an announcement that EU accession talks would be suspended until 2028, have continued and remain marked by violent clashes.
The largest protests have taken place primarily on Rustaveli Avenue in the vicinity of the Georgian parliament building in Tbilisi, although smaller demonstrations have also occurred in the past week outside the Georgian Public Broadcaster’s offices and in Kutaisi.
Security forces continue to deploy tear gas and water cannons against protesters, and protesters in turn are increasingly using fireworks against the riot police. What is almost certainly a government-led crackdown on dissent has continued and expanded, with the police conducting regular raids of protester residences, opposition political party headquarters, as well as civil and journalistic organisations. Additionally, multiple reports indicate that cases of “gangs” of masked individuals violently attacking opposition politicians, activists, and journalists are increasing.
Solace Global Assessment:
It is highly likely that the levels of political violence in Georgia are increasing, with pro-government gangs (that are called “titushky” by opposition supporters—the term used for the pro-Russian plain-clothed provocateurs in Ukraine before and during the Euromaidan movement) having escalated a campaign of violence against the opposition.
The increasingly regular use of fireworks by protesters, indicates that protester tactics are developing as they attempt to resist the so far generally successful clearance operations conducted by riot police.
Overall, it is likely that the demonstrations lost momentum over the past week. Multiple factors could be contributing to this, including ‘protest fatigue’ and the impact of the government crackdown. However, the upcoming presidential election, scheduled for 14 December, is likely to trigger renewed unrest, as incumbent pro-opposition President Salome Zourabichvili is expected to be ousted, primarily due to the new presidential electoral system.
Syria: Rebels overthrow Assad regime after 13 years of civil war
On 8 December, Damascus was seized by opposition forces just one week and four days after Hayʼat Tahrir al-Sham (HTS) led a rebel offensive that rapidly overwhelmed the regime’s Syrian Arab Army (SAA).
Syria’s now former dictator, Bashar al-Assad, fled the country and has been granted asylum in Russia. In the aftermath of the decisive rebel victory, HTS installed a transitional government headed by Mohammed al-Bashir, who was previously the prime minister of the Syrian Salvation Government (SSG) in HTS-controlled Idlib.
Concurrently, the Israel Defence Forces (IDF) moved forces into Syria north of the Golan Heights (which Israeli officials claim is to establish a “buffer zone”) and conducted nearly 500 aerial strikes against Syrian military assets. These included naval vessels, air defence systems, aircraft, and weapon stockpiles.
The IDF claimed they destroyed 70-80 per cent of the Syrian state’s military capabilities in the operation, called “Operation Bashan Arrow”.
Meanwhile, the Turkish-backed Syrian National Army (SNA) launched an offensive against Kurdish-led and US-backed Syrian Democratic Forces (SDF) controlled Manbij. The conventional Turkish military also conducted airstrikes against Kurdish targets in northeast Syria, including an airstrike in Raqqa (the first since 2017).
On 11 December, the Kurdish-led force announced a US-brokered ceasefire in Manbij with the SNA.
Solace Global Assessment:
Leading HTS figures have attempted to present an image of moderate technocratic pluralism since coming to power. Their leader, Abu Mohammed al-Golani (who now refers to himself by his real name, Ahmad al-Sharaa, rather than his nom de guerre), exemplifies this shift.
Al-Golani had initially been sent to Syria by Abu Bakr al-Baghdadi (who later became the first caliph of the Islamic State) to establish the Syrian branch of al-Qaeda, al-Nusra Front. HTS, however, emerged as an organisation from al-Nusra and other Islamist rebel groups following the breaking of ties with al-Qaeda.
Al-Golani has since attempted to cultivate an image that is much more palatable to Western observers, though HTS is still designated by the US State Department as a foreign terrorist organisation.
Syria’s new leaders presently have four key challenges. Firstly, the conflict between the SNA (with conventional Turkish military support) and the SDF remains unresolved, and there is a realistic possibility that these tensions could result in a second civil war.
Secondly, Israel’s freedom of action to conduct considerable military operations in Syria is a fundamental challenge to Syrian sovereignty. It is notable that when pressed by a journalist for a reaction to the Israeli air strikes, an HTS spokesperson evaded the question and spoke instead of the need for institutions and the provision of services—this is indicative of the likely HTS strategy to presently avoid as far as possible any antagonism with Israel and instead focus on state-building.
Thirdly, the remnants of the regime, backed by Iran and Tehran’s ‘Axis of Resistance’, will likely continue to hold some appeal amongst Syria’s Alawi, Ismaili and Shia minorities (although efforts have been made by HTS representatives to develop ties with these communities). The fall of Assad is a critical defeat for the Iranian grand strategic objective, pioneered by the late Qasem Soleimani, of control of the Shia Crescent through proxies and allies, which created a sphere of influence across the Middle East and a ‘land bridge’ between Iran and Hezbollah in Lebanon. It is highly unlikely that senior Iranian Quds Force commanders will entirely abandon their objectives in Syria.
Fourthly, the Islamic State of Iraq and Syria (ISIS) have highly likely attempted to exploit the retreat of the SAA to reestablish a foothold in Syria, which has been met by dozens of airstrikes by US Central Command (CENTCOM) forces. SDF-controlled facilities house over 9,000 ISIS fighters. If the SDF are forced to abandon these prisons due to an escalation in hostilities, the potential escape of these detainees poses a threat not only to Syria, but also to the European countries from which many imprisoned ISIS foreign fighters originate.
Somalia: Fighting breaks out between Mogadishu and Jubaland amidst tensions with Ethiopia
On 7 December, Ethiopian forces entered the Somali town of Doolow in the contested administrative Gedo region of the semi-autonomous state of Jubaland. Somali federal forces and residents reportedly blocked further advancements into Buulo Hawo, also in Gedo.
This incursion comes as Mogadishu has accused Addis Ababa of smuggling arms to Jubaland and flying Jubaland’s Deputy President Mahmud Seiyd Aden to Ethiopia, viewing its actions as an attempt to destabilise Somalia and a violation of its territorial integrity. As such, Mogadishu has vowed to defend Somali territory if continued “violations” occur and take measures against those who collaborate with Addis Ababa.
On 11 December, fighting broke out between Mogadishu and Jubaland. Jubaland Derawish forces reportedly captured the strategically important Oodow well, Raaskanbooni’s water source, after federal Government troops allegedly initiated combat. In response, Mogadishu deployed more forces to the city before withdrawing them on 12 December to “prevent further violence”.
Solace Global Assessment:
Recent weeks have seen heightened tensions between Mogadishu and Jubaland. On 25 November, Ahmed Madobe was re-elected for a third term in Jubaland after the state’s constitution was amended to remove presidential term limits. Mogadishu responded by declaring this election illegal since they were held without federal government involvement.
In the aftermath, each region issued arrest warrants for each other’s presidents. Despite Mogadishu withdrawing its forces, tensions between Mogadishu and Jubaland will almost certainly continue as each authority attempts to assert its control over southern Somalia.
Mogadishu has accused Addis Ababa of illicitly supporting Jubaland in a bid to secure Ethiopia’s border. Addis Ababa has significant security concerns over the region, viewing Jubaland as a potential buffer zone against cross-border incursions by extremist groups including al-Shabaab which operate in the area.
The Gedo region is on the Jubaland-Ethiopia border, and is, therefore, strategically important for Addis Ababa to control to prevent incursions. As such, Addis Ababa has armed clan militias and seized key airports in Gedo. Mogadishu and Jubaland are also vying for administrative control of the region, which acts as an important gateway for trade and security. Moreover, Mogadishu views control of Gedo as a means of asserting federal authority over Jubaland, weakening the state’s autonomy. The Marehan clan, prominent within Somalia’s federal government, is also predominant in Gedo, culturally linking Mogadishu to the contested region.
Recent tensions over Gedo contribute to general animosity between Mogadishu and Addis Ababa. Addis Ababa made a deal with Somaliland’s government in January 2024, which has leased access to its port in exchange for official recognition. Mogadishu, who considers Somaliland’s government to be secessionist and illegitimate and, therefore, unable to grant access of this kind to Somali territory, considers this deal illicit.
In response, Mogadishu made a deal with Cairo to receive Egyptian weaponry, military training, and Egyptian troop deployments to Somalia. Under Turkey’s mediation, Somalia and Ethiopia reportedly agreed to work together to resolve the Somaliland port dispute on 12 December. However, given Ethiopia’s strategic interests in Somalia to protect its borders, combined with Mogadishu’s inability to rein in the motivations of semi-autonomous states including Somaliland and Jubaland, further tensions between the two governments are almost certain.
Mozambique: Opposition leader Venâncio Mondlane announces “TurboV8” phase of unrest
Opposition leader Venâncio Mondlane initiated a “4×4” phase of protests from 4-11 December. Local NGOs report that approximately 110 people have been killed and over 300 injured since Mozambique’s post-election unrest began. During the 4×4 phase, protests escalated nationwide, with roadblocks in Maputo, vandalised government buildings, police stations attacked, and a tourist complex damaged.
In one instance, a detention centre was targeted by protesters, resulting in 46 inmate escapes. Another event saw protesters target the Ressano Garcia and Gigawatt power stations near the South African border, disrupting electricity generation. Public utility EDM implemented power cuts, resuming operations on 9 December after reaching an agreement with the protesters. On 7 December, Mondlane claimed that a second assassination attempt was conducted against him. This, in turn, intensified demonstrations. He announced plans for a “TurboV8” protest phase if demands remain unmet.
Solace Global Assessment:
Mondlane’s demands remain unmet and demonstrations show few signs of abating. Protesters have increasingly targeted government facilities after discovering hundreds of voter cards in a Frelimo headquarters in Muecate on 4 December. Recent unrest has also expanded focus to also target national infrastructure such as power stations. This indicates that protesters, guided by Mondlane, are increasingly inclined to pressure the government by shutting down state functions.
While Mondlane has not yet announced what the “TurboV8” phase will involve, it is highly likely to focus on public institutions to scale up the pressure.
Security forces continue to utilise forceful measures including tear gas and live ammunition to disperse protests. This has generally proved unsuccessful; protests have typically spiralled into clashes and the targeting of police institutions once security forces use more forceful measures against protesters. Historically, security forces in Mozambique have utilised forceful measures to quell unrest, including the 2010 Bread Riots, which resulted in 13 deaths. The insurgency in Cabo Delgado region in northern Mozambique has compounded pressure on the government to control the unrest by similarly challenging its ability to govern its territory.
Given the steadily increasing pressure on the government, security forces will almost certainly continue to use repressive measures against demonstrators to prevent unrest spiralling further.
Iran: Fall of the Shia Crescent forces Tehran to reconsider its foreign policy
On 6 December, members of the Islamic Revolutionary Guard Corps (IRGC) began evacuating Syria as the al-Assad regime neared collapse after days of rebel offensives. By 10 December, all IRGC elements left Syria, alongside an estimated 4,000 Iranian citizens. In the days following the fall of Syria, Tehran reportedly remains in an extremely cautious state, and international media has reported growing infighting at the highest levels of Theran’s military and political establishment, with significant questions being raised about President Pezeshkian and the current leadership of the IRGC.
Particularly severe criticisms are being raised at the leader of the elite Quds Force, Esmail Qaani, accused of responsibility for the rout of the Syrian regime’s army. To prop up the Assad regime during more than a decade of civil war, Iran spent billions of dollars and supplied large quantities of resources, including an estimate of 50-70,000 barrels of crude oil per day, weapons, industrial products, and human resources.
Solace Global Assessment:
The collapse of the al-Assad regime, the degradation of Hezbollah, and the repeated failures of Iran’s deterrence towards Israel and the West have almost certainly constituted Tehran’s largest geopolitical setback in decades. With the ousting of Assad, Iran has lost a major component of its “Shia Crescent”, which has almost certainly disrupted its main facilitation route to Lebanon. The effect of this will limit Hezbollah’s ability to replenish its arsenal and in the long-term is likely to severely weaken Iran’s primary proxy force and main strategic deterrent against Israel.
Tehran’s failure to support the Assad regime effectively in the face of rebel advances has likely conveyed significant messages to Iran’s regional adversaries regarding the true strength of its military capabilities and willingness to support allies. This failure is likely to undermine Iran’s future efforts in establishing deterrence.
Iran is almost certainly at its weakest position in decades. The regime will almost certainly be forced to significantly alter its foreign policy in light of the new developments in Syria. In the immediate term, the collapse of the Assad regime could result in a reshuffle in the leadership of the IRGC and within the broader government. However, Tehran is likely reticent to introduce overly destabilising changes at such a crucial moment, with the regime looking weak to an internal audience.
In the short term, Iran is likely to avoid further escalation with Israel, instead prioritising internal security and the strengthening of its proxy forces. With the facilitation route through Syria severely disrupted, Iran will likely prioritise its smuggling routes through Jordan into the West Bank, where it has attempted to establish an additional front against Israel.
With Iran’s proxy forces degraded and the Assad regime deposed, Iran’s long-term strategy at re-establishing deterrence against Israel, the West and regional Arab rivals will almost certainly evolve. This will likely involve increased investment in long-range conventional military capabilities such as drones and ballistic missiles, capabilities that can reach Israel and breach it’s air defence when launched in large-scale and layered salvos.
However, to truly achieve deterrence, Tehran likely calculates that its best option is to accelerate its nuclear programme, with voices within Iran starting to challenge Ayatollah Khamenei’s 2003 fatwa against nuclear weapons and demanding that Iran withdraw from the Nuclear Non-Proliferation Treaty. Growing support for a potential reversal of Iran’s non-nuclear status is also reflected in the country’s accelerated production of 60 per cent enriched uranium, drawing censure from the International Atomic Energy Agency (IAEA). These developments are unlikely to lead to an immediate nuclear test, as Iran is focused on renewing negotiations with the West and avoiding a regional backlash. However, Tehran may be using this brinkmanship to apply pressure, particularly on Brussels and Washington.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Farmers’ protest escalates in UK capital
On 11 December, hundreds of tractors arrived in Westminster, London to protest the Labour government’s recent budget and its planned changes to inheritance tax for agricultural businesses. The initial protest was set to be held in Trafalgar Square but was to large, promoting its diversion to Westminster, with protests also being staged on major roads outside of the capital. The protests caused significant disruption and are likely to be held again with the incumbent government refusing to amend its proposed policy changes.
François Bayrou appointed as new French Prime Minister
President Emmanuel Macron named Bayrou to succeed Michel Barnier, who was ousted by a no-confidence vote over the 2025 budget a little more than a week ago. Bayrou is a centrist politician and was a government minister early in Macron’s first term. Bayrou’s appointment is likely to disappoint the left, whose moderate elements had been in discussions with Macron over a possible left-wing appointment to replace Barnier.
Five dead in refinery explosion near Florence, Italy
The explosion, which occurred on 9 December, also injured approximately 26 people. Authorities are yet to establish the cause of the explosion. However, the incident has resulted in strikes by local labour unions, with a general demonstration jointly organised by unions of Tuscany’s main urban areas on 11 December.
Burkina Faso junta shuffles government
Ibrahim Traore, who heads the country’s military government, announced the dismissal of Prime Minister Kyelem da Tambela and his government, and replaced him with Rimtalba Jean Emmanuel Ouedraogo. The reshuffle occurred only days after the allied junta in Mali did the same. However, unlike in Mali’s case, the new prime minister is not a member of the military. Ouedraogo is the country’s former communications’ minister and is therefore already well-connected to the junta. Traore gave no reason for the change in government, but it is likely that it is a reaction to the worsening security and socioeconomic situation in Burkina Faso.
Security forces teargas protesters against gender-based violence in Kenya
On December 10th, security forces made numerous arrests and used teargas to disperse protests against femicide rates in Kenya. The country has seen a significant number of gender-based violence cases, with 97 women reportedly killed since August, mostly by male partners.
These clashes are the latest in a series of cases of unrest in Kenya in 2024. Demonstrations against a government Finance Bill in June spiralled into violent clashes between protesters and security forces. Kenya’s underlying economic issues continue to be present, with demonstrations threatening to escalate multiple times since.
Security forces’ reaction to the protests against gender violence is highly likely an attempt to prevent demonstrations from spiralling again. As such, security forces will likely continue to use forceful measures to quell unrest.
Security, Armed Conflict and Terror
Three students arrested in France for planning attacks on behalf of IS
The suspects are reportedly all under 21 years of age and had managed to prepare improvised explosive devices to allegedly use in attacks in the cities of Nimes and Nantes, targeting French security forces. According to authorities, the suspects stated that they expected that their attacks would trigger a civil war and eventually the establishment of an Islamic state in France. The case is further evidence of increased radicalism amongst the European youth, which may further increase as a result of developments in the Middle East.
Multiple Islamic State (IS) supporters arrested for planning attacks in Germany
On 10 December, German police announced the arrest of three individuals from Hesse and Mannheim on suspicion of planning a terror attack on an unspecified target on behalf of IS. Notably, authorities seized an “assault rifle” from the suspects. Days prior, an Iraqi national was arrested in Bavaria for allegedly planning an attack on a local Christmas market, also in support of IS. The recent cases continue to highlight the high threat posed by lone-wolf terrorism and self-radicalised terrorists in Europe. IS-linked terrorists continue choosing high-visibility targets, such as Christmas markets.
Romanian police arrests armed men en route to Bucharest
The security situation in Romania has worsened since the constitutional court made the unprecedented choice to annul the first round of the presidential elections over concerns of Russian interference in helping anti-NATO candidate Calin Georgescu. The 20 individuals arrested on 8 December, armed with bladed weapons and firearms, allegedly included individuals who had links to the Wagner Group.
Russian security forces detain Islamist terrorists in Dagestan
The arrests took place on 7 December, with Moscow stating that the 12 suspects were planning a “major terrorist attack” at an unspecified location in Russia. Authorities also seized two explosive devices, firearms and ammunition. There is a realistic possibility that the arrests will be followed by further moves to increase state surveillance in regions that Russia deems at risk from terrorist activity, such as Dagestan and Chechnya. Multiple channels close to the Kremlin have noted that the fall of Assad in Syria raises the profile of Russia as a possible target for terrorist actors, who may increase recruitment in Russia or in its peripheral regions such as the Caucasus.
Growing likelihood of escalation between Palestinian Authority (PA) and militants in West Bank
On 8 December, the PA launched a counterterrorism operation in Jenin – notably, the first in years – following a threat by Palestinian Islamic Jihad (PIJ) militants that they would attack PA government buildings. The raid resulted in at least three PA security officers being injured, as well as the alleged killing of a 17-year-old Palestinian civilian by PA officers.
This latter incident has provoked an escalation in the tensions between the PA and local Palestinian armed groups, including PIJ and elements of Hamas, with clashes recorded in Jenin, Nablus, Tulkarm and Tubas. There is a realistic possibility that the growth of PA operations, as well as the willingness to carry out a counterterrorism operation in Jenin in the first place, is a response to PA officials’ growing interest in exploiting the weakness of local Palestinian militant groups.
At the same time, the PA remains widely disliked in the West Bank and continues to remain on the edge of financial collapse. If tensions escalate, Israeli forces are likely to step in to support the Palestinian Authority, which is viewed by Tel Aviv as a stabilising entity for both the West Bank and a potential post-Hamas Gaza.
Series of terrorist attacks in Niger close to Burkina Faso border
There have been a series of terrorist attacks in western Niger close to the Burkina Faso border targeting both the Nigerien military and civilians. The Niger Army reported that 21 civilians and 43 soldiers were killed in one attack near Tera on 5 December, with additional attacks in the west of the country occurring on both 11 and 12 December.
The government has attributed the attacks to the Islamic State’s Sahel Province (ISSP), which has traditionally used the border regions as a hideout. With the Benin-Niger border intermittently closed due to sanctions and escalating extremism in the region, Niger is increasingly reliant on trade routes through Burkina Faso for essential goods.
Violent extremist organisations (VEOs) like ISSP are likely attempting to disrupt these routes in a bid to undermine and isolate the junta government in Niamey.
French forces begin withdrawing from Chad
French Mirage jets left their base in N’Djamena on 10 December for Nancy, weeks after Chadian authorities annulled their defence cooperation agreement with Paris. French officials have stated that the phases of the withdrawal and their specifics are still being discussed with their Chadian counterparts.
The withdrawal of French troops constitutes a significant setback for France in the Sahel and may result, as highlighted in Niger, in a security vacuum that could be exploited by Islamist violent extremist organisations (VEOs) or groups looking to oust the junta government.
While Sahel states have looked to Russia for help to replace departing Western forces, Moscow’s setbacks in Syria and its expenditure of resources in Ukraine and elsewhere in the Sahel may reduce its ability to effectively replace Western forces.
Suspected bandits kidnap 50 in northwest Nigeria
The Nigerian army has deployed more resources to the state of Zamfara in northwest Nigeria in response to the abduction of civilians from a village within the Maradun Local Government Area. On 8 December, suspected bandits kidnapped an estimated 50 women and children from the village and have to date refused to accept ransom payments for some of the victims.
The kidnappings are part of a wider trend in northern Nigeria that is being driven by poverty, high rates of unemployment and the proliferation of illegal firearms. Moreover, government forces are overstretched by an Islamist insurgency in the north and separatist movements in the south.
IED attack on Jewish community in Cape Town, South Africa
Early on 6 December, an improvised explosive device (IED) was thrown at a Jewish community centre in Cape Town. The device failed to detonate, and thus the attack resulted in no injuries. Attacks on Jewish community centres and places of worship, as well as private homes, have increased since 7 October 2023 across most countries, with notable cases in France and Australia. However, similar cases have been relatively less frequent in South Africa. The attack is likely to provoke some symbolic protests in Cape Town, although these are unlikely to result in large-scale transport disruptions.
Environment, Health and Miscellaneous
Offices, colleges, and schools to close in Tehran due to air pollution
Over the weekend, elementary schools and kindergartens were closed and football matches were cancelled due to soaring pollution levels. To prevent further pollution, the government-imposed measures such as traffic restrictions including a 48-hour ban on diesel trucks. This did not reduce pollution levels in the immediate term and on 10 December, government offices, schools, and universities will close in Tehran for two days due to pollution.
In January, The Health and Climate Change Department of the Ministry of Health reported that 14 per cent of natural deaths in Iran are associated with air pollution levels. The human cost is reportedly between USD 12 and 20 billion each year. This is largely due to the use of mazut, a form of fuel oil utilised in power plants and industries, which releases high levels of particulate matter.
While authorities have attempted to reduce air pollution by halting the burning of mazut for electricity generation, these measures alone are unlikely to considerably reduce air pollution levels.
Nigeria experiences 11th nationwide power outage in 2024
On 11 December, Nigeria’s national grid collapsed marking the 11th time in 2024. The blackout affected much of the country, including Lagos and Abuja, with outages expected to last for several days in parts of Nigeria, with the restoration of power being prioritised in major cities.
The blackout has disrupted telecommunications and traffic systems and will likely jeopardise many security systems. Periodic blackouts have also been one of the main drivers of civil unrest in Nigeria and there is a realistic possibility of demonstrations being held in the upcoming days, especially as the central government has recently established a team to overcome this issue.
Asia–Pacific
Afghanistan: Senior Taliban official killed in suicide bombing
In the morning of 11 December, a suicide bombing attack occurred in central Kabul near the refugees ministry building. The attack killed at least 12 people, among them Khalil Haqqani, a Taliban government minister and one of the key leaders and founders of the Haqqani network, a semi-independent militia in charge of Afghanistan’s domestic security. Haqqani is the highest-profile member of the Taliban killed since the group took power in 2021. Taliban officials have stated that the Islamic State Khorasan Province (ISKP) was responsible for the attack, and ISKP have also claimed it.
Solace Global Assessment:
The killing continues to highlight the significant failures of the Taliban to establish a degree of security, even in Kabul, and underscores the regime’s continued difficulties in combating the existential threat of ISKP, alongside pressures from the rebel National Resistance Front (NRF) and neighbouring Pakistan and Iran. For ISKP, the attack likely represents a significant success, as it both demonstrates the Taliban’s overall weakness, and thus advances the goal of destabilising the regime, and reinforces local perceptions of the Islamic State’s capabilities.
In practice, the killing is unlikely to affect the Haqqanis’ strength in the short term or the actual functioning of the Taliban government, as elderly Khalil Haqqani’s post as the head of the refugee ministry was mostly ceremonial despite his large political influence. Nevertheless, the attack is likely a significant strike to the power centres of the Taliban regime and may impact internal power dynamics. In particular, the security failure may exacerbate latent tensions between the Haqqanis and the rest of the Taliban government. Sirajuddin Haqqani, currently the interior minister of Afghanistan and the de facto head of the Haqqani network, has repeatedly been described as a dissenting voice, opposed to the Kandahari Taliban faction led by Afghan supreme leader Hibatullah Akhundzada.
The Haqqani network will almost certainly respond violently to the attack. This may entail carrying out retaliatory attacks in eastern regions of Afghanistan that have a higher ISKP presence, like Kunar and Nangarhar. Moreover, Taliban officials have repeatedly accused Pakistan of sheltering ISKP members in its territory, and there seems to be a widespread belief among senior Taliban that ISKP actions are at least in part sanctioned by Pakistani intelligence. The recent attack could therefore once again widen fault lines between Islamabad and Kabul, with adverse security impacts in the border regions of the two countries, where the Taliban and ISKP both have a strong presence.
South Korea: Attempt to impeach President Yoon Suk Yeol fails as opposition files second impeachment bill
Following President Yoon’s temporary imposition of martial law on 3 December, an impeachment bill filed by the National Assembly failed on 7 December. Yoon’s People Power Party (PPP), at least eight of whom were required to achieve the required two-thirds majority, refused to participate in the proceedings and boycotted the vote.
The president has accused the opposition of obstruction and election fraud, justifying his actions during the martial law period, and has stated he has no intention of resigning early. Opposition parties filed a second impeachment bill against President Yoon on 12 December, with a vote scheduled for 14 December.
Yoon is also under investigation for the crime of insurrection, a crime that carries a potential death sentence. As part of the investigation, police forces have raided his office and other key government buildings, but the Presidential Security Service has blocked investigators from accessing the Presidential Office Building. Yoon has been issued a travel ban while investigations are underway. A court has issued an arrest warrant for former Defence Minister Kim Yong-hyun, accusing him of sedition and abuse of power. While in detention, Kim attempted to take his own life.
Solace Global Assessment:
Opposition forces have vowed to hold an impeachment vote every Saturday until Yoon is no longer president. Yoon held a speech on 12 December defending his actions as an act of governance, denying claims of insurrection. Given Yoon has remained defiant, he appears unlikely to step down willingly.
While Yoon’s party failed to back the first impeachment bill, Yoon-loyalist Kwon Seong-dong has indicated that he is in favour of impeaching Yoon. Protests have occurred daily in Seoul since Yoon imposed martial law. They are highly likely to continue until he is either impeached or steps down. Demonstrations and growing frustration with Yoon will almost certainly add pressure on the PPP to back impeachment proceedings. If Yoon’s party fails to back the 14 December vote, unrest will likely escalate.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
India and Bangladesh hold talks to defuse tensions amidst protests in Dhaka
On 9 December, Indian and Bangladeshi foreign secretaries met in Dhaka to discuss growing tensions after Sheikh Hasina’s deposition. Recent tensions have revolved around accusations by Hindu-majority India that Hindus are being persecuted in Muslim-majority Bangladesh. Hindu rights groups in India and Bangladesh have criticised the interim government of facilitating violence against Hindus, leading to fears that Muslim-Hindu tensions will flare up in reciprocal violence.
In Dhaka, protesters rallied around the Bangladesh diplomatic mission on 10 December in protest of this violence. Hindus have been historically persecuted in Bangladesh. With the removal of Hasina, who kept extremist Islamist sentiments largely in check, these fears have reignited. Given the recent ousting in the country and unstable political situation, potential for violence to flare up is particularly concerning.
Bangladeshi officials have accused India of attempting to undermine the interim government by exaggerating violence against Muslims. The meeting indicates an important step in reducing tensions between the two nations, something that could have a knock-on effect in easing fears of renewed Hindu persecution in Bangladesh.
At least 55 arrested following protests at the presidential palace in the Maldives
The protesters, who are migrant workers from India and Bangladesh, claimed they had not been paid in more than six months. According to local media, the protests have resulted in the opening of an investigation by local authorities.
While protests sometimes occur in the Maldives, these are often met violently by authorities, and also by pro-government supporters. It is unlikely that the recent protests will result in further unrest by local civil society actors. However, as relations between India and the Maldives remain at historic lows, the arrests could result in diplomatic tensions between the two countries.
Security, Armed Conflict and Terror
Pakistani military continues targeted operations amid surge in militant attacks
The Pakistani military has continued its intelligence lead operations in the militant strongholds of Khyber Pakhtunkhwa and Baluchistan where it is attempting to kill or capture senior figures within militant groups, particularly in the Tehrik-i-Taliban Pakistan (TTP) and Baluchistan Liberation Army (BLA). However, the operations have likely inspired a wave of militant attacks, with the BLA conducting multiple attacks on government forces throughout the reporting period.
An Islamabad-based think tank has reported that there were at least 61 militant attacks in Pakistan across November 2024. This marks a 27 per cent increase in attacks but the attacks resulted in a 69 per cent increase in fatalities. This likely indicates that militant attacks are becoming larger and more deadly- a trend that is likely to increase in response to government operations.
Rebels in Myanmar claim full control of border with Bangladesh
On 10 December, one of the largest ethnic rebel groups in the Myanmar civil war, the Arakan Army, announced that it captured the last junta military outpost in the strategic western town of Maungdaw in Rakhine State. The Arakan Army now claims to have secured full control of Myanmar’s 271-kilometre border with Bangladesh.
The seizure of Maungdaw will likely put the Arakan Army in a more favourable position to secure autonomy from the junta, will likely embolden other rebel forces and will place considerable pressure on an increasingly isolated regime. However, the Arakan Army has been accused of human rights abuses and uncontested control of large parts of Rakhine State could result in greater persecution of Myanmar’s Rohingya Muslim minority, leading to more inter-ethnic violence and migration flows to neighbouring Bangladesh.
China conducts large-scale military exercise around Taiwan
On 9 December, China’s People’s Liberation Army Navy (PLAN), People’s Liberation Army Air Force (PLAAF) and Chinese Coast Guard (CCG) conducted a major military exercise simulating the isolation and invasion of Taiwan. The exercise is one of the largest ones held by China to date, involving an estimated 90 PLAN and CCG vessels, combined with 47 aircraft being detected within Taiwan’s Air Defence Identification Zone (ADIZ).
The exercise was likely a direct response to Taiwan President Lai’s recent diplomatic visits to nations that recognise Taiwan, including the US. China has now staged four large-scale military exercises around Taiwan in just two years, the regularity of which will likely make it increasingly challenging to identify a genuine invasion of Taiwan.
Melbourne synagogue set on fire
The building, located on the outskirts of the Australian city, was burned by two unidentified individuals in the early hours of 6 December. The fire injured one worshipper who was on the premises for morning prayers. Days later, on the night of 10 December, a further series of acts of vandalism, including a car being torched and anti-Israel graffiti were reported in Sydney.
Since 7 October 2023, antisemitic attacks in Australia have grown exponentially. The government has called for the establishment of a task force to combat antisemitism after the synagogue attack. However, attacks on places of worship are difficult to prevent due to the ease of maintaining anonymity for perpetrators and the lack of community and police resources to protect the sites. There is a realistic possibility of further copycat actions against Jewish places of worship in Australia.
Environment, Health and Miscellaneous
Kanlaon Volcano erupts in central Philippines
The Kanlaon volcano in central Philippines erupted on 9 December, prompting significant emergency responses and safety measures. The eruption led to the evacuation of tens of thousands of residents from affected areas, particularly in the Western and Central Visayas regions. The Philippines’ seismological agency has maintained an alert level three and warned of potential rain-induced lahars on the southern slopes of the volcano in Negros Occidental. This alert level indicates increased volcanic unrest, necessitating close monitoring and readiness for possible escalation.
Local authorities have implemented several precautionary measures. The governor of Negros Occidental declared a red alert due to “magmatic unrest,” and forced evacuations were ordered in high-risk areas across five barangays in Canlaon City. Additionally, schools in Isabela, Negros Occidental, were closed and a mandatory masking order along with a 22:00 curfew for minors and businesses was enforced. Cebu Pacific cancelled flights to and from Iloilo, and several police stations in Negros Oriental were placed on heightened alert to monitor ash plumes.
Despite the disruption, regional airports reported no significant operational impacts from the eruption. However, the civil defence office highlighted that at least 54,000 people were affected by the volcanic activity. The situation remains dynamic, with authorities continuing to monitor the volcano closely and prepare for any further developments.
Thousands affected by landslides and flash flooding in Indonesia’s West Java
Landslides and flash floods have severely impacted West Java, Indonesia, particularly affecting the Sukabumi Regency as a result of torrential rains. More than 176 villages have been affected, resulting in at least 10 fatalities. The situation has prompted a large-scale evacuation and major disruption with over 30 bridges and 80 roads damaged. Sustained heavy rain is forecasted for much of the region, with up to three tropical cyclones set to bring adverse weather conditions in the following days.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence

Executive Summary
- The Barnier government’s collapse will highly likely worsen France’s political and economic situation in the short term and will likely drive unrest in large urban centres.
- The HTS-led offensive highly likely presents an existential threat to the regime and has almost certainly triggered a resurgence of hostilities amongst other factions across Syria.
- The detention of foreign executives in Mali is almost certainly part of a broader effortto exact money from Western mining companies operating in the country.
- President Yoon Suk Yeol highly likely to be impeached after temporarily imposing martial law in South Korea.



AMER
Mexico: Sinaloa cartel infighting results in 500 deaths
Colombia: Military chief warns of groups exploiting peace talks
EMEA
France: Barnier government collapses after vote of no confidence
Georgia: Anti-government protests further intensify
Syria: HTS-led offensive continues to rapidly gain ground
Israel, Gaza & Lebanon: Ceasefire holds as Gaza operations continue
Mali: Junta government sets precedent of detaining foreign mining employees
Mozambique: Opposition orders another round of demonstrations
APAC
Pakistan: Government initiates offensive against militants
South Korea: President faces impeachment after martial law
North, Central and South America
Mexico: Sinaloa Cartel infighting leads to 500 dead
Recent reporting indicates that since the US detention of the Sinaloa Cartel leader Ismael “El Mayo” Zambada in July 2024, the factionalism of the cartel and subsequent infighting has resulted in over 500 deaths, with hundreds remaining missing. Mexican business leaders have also stated that the violence has led to over USD 1 billion in losses.
On 29 November, Mexico’s Ministry of Defense (SEDENA) began reinforcing its presence in the state by sending dozens of additional special forces personnel to counter the escalating violence between the “Los Chapitos” and “La Mayiza” factions of the Sinaloa Cartel.
In a separate operation, Mexican authorities announced the seizure of over a tonne of fentanyl on 3 December. The seizure was the country’s largest synthetic opioid seizure, equivalent to 20 million individual doses.
Solace Global Assessment:
Despite the increased deployment of Mexican forces to Sinaloa, the cartel violence is showing no signs of abating. Moreover, there are indications that Sinaloa is increasingly becoming a staging ground for a proxy war between other cartels seeking to exploit the factionalism of the Sinaloa Cartel.
In November, two prominent Tijuana Cartel bosses pledged allegiance to the La Mayiza faction. This has been followed by recent reports that the Beltrán Leyva Organisation (BLO), an original part of the Sinaloa Cartel, has now offered its support to the Los Chapitos faction. Both the BLO and the Tijuana Cartel are likely attempting to establish control over the Sinaloa Cartel and the state’s lucrative smuggling routes and narcotic production facilities.
Both groups will likely commit many resources to the current conflict, resulting in an escalation of violence despite the increase in Mexican forces deployed to the region. Furthermore, the involvement of these groups could lead to the migration of violence outside of Sinaloa and other areas like Baja California. Engaging in the ongoing cartel conflict will be costly, and cartels will likely escalate narcotics trafficking to the US to fund their operations.
The record seizure of fentanyl is likely a direct consequence of President-elect Trump’s threat to implement 25 per cent tariffs on Mexican goods unless it cracked down on the flow of both migrants and drugs, with only 130 kilograms seized from January to June nationwide. However, increased seizures combined with an enhanced security posture in Sinaloa will likely result in an escalation of violence and an expansion of retaliatory attacks by the cartels.
Colombia: Head of Colombian armed forces warns armed groups have exploited peace negotiations
Colombia’s Military Forces Commander, Admiral Francisco Cubides, has warned that several armed groups in Colombia have exploited the country’s ambitious plans to establish total peace to expand their military and economic influence.
Cubides stated that groups like the Revolutionary Armed Forces of Colombia (FARC) dissident group, the Segunda Marquetalia, and the organised crime gang the Clan del Golfo have used ceasefire negotiations to exert greater control over drug trafficking and illegal mining activity.
They have suggested that groups which once espoused leftist ideologies have now morphed into violent organised crime groups.
Solace Global Assessment:
President Gustavo Petro’s government has attempted to establish “total peace” within Colombia since 2022, after six decades of fighting which has killed almost half a million people. However, his policy of pursuing bilateral agreements with a range of groups has increasingly led to the splintering of armed groups and criminal enterprises.
These smaller groups have often fought each other, resulting in higher rates of violence in rural areas or have formed new alliances, enabling them to exercise more control over illegal enterprises whilst also putting them in a stronger position to counter government forces. Record seizures of almost 600 tonnes of cocaine in 2024 are almost certainly indicative of the government’s strategy backfiring.
It also likely suggests that criminal organisations are using the guise of compliance to successfully entrench themselves in economically important regions. The continuation of Petro’s plans risks inadvertently strengthening armed groups, allowing them to expand their influence and making it increasingly more difficult for Colombia’s military to dislodge them from their areas of operations.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
UN begins investigation into Venezuelan election
The United Nations Human Rights Council launched an investigation into allegations that Venezuelan President Nicolás Maduro manipulated the results of the July presidential election. The investigation has been prompted by a petition from Latin American jurists who claim that the presidential election was marred by widespread electoral fraud which included the refusal to release voting records and that there is evidence to suggest that the opposition candidate, Edmundo González, won by a large margin.
The Maduro administration is unlikely to comply with the demands of the investigation and there is a realistic possibility that the regime will increase its suppression of dissent in response.
On 5 December, Maria Corina Machado, one of the main opposition leaders, stated that Venezuelan officials are likely to storm the Argentinian embassy in Caracas, where six political refugees are sheltering, in the coming days. If this were to happen, it would almost certainly precipitate a diplomatic crisis with Buenos Aires.
Paraguay expels Chinese diplomat
On 5 December, Paraguay expelled a senior Chinese diplomat after he allegedly attempted to influence the country’s relationship with Taiwan. The diplomat, Xu Wei, had arrived in the country for a UNESCO meeting and reportedly urged lawmakers to reconsider Paraguay’s diplomatic ties with Taiwan, suggesting such a change would result in economic growth. Paraguay is the only South American nation that maintains formal relations with Taiwan and will likely attract increase pressure from Beijing to sever them.
Security, Armed Conflict and Terror
Children now make up 50 per cent of gang members in Haiti and Kenyans resign
The United Nations has reported that children now make up around 50 per cent of armed gang members in Haiti, with recruitment increasing by 70 per cent in the past year. These children are forced into roles including informants, cooks, and sex slaves, and are also forced into perpetrating violence against rival gangs or the security services. The increased recruitment of children will almost certainly complicate the disruption of gang operations, adding a complex ethical component to the operations.
In addition, Kenyan police deployed to Haiti as part of a UN mission have begun to submit resignation letters because of pay delays and poor conditions. Further resignations are almost certain to follow, with reports that the Kenyan force is suffering from ammunition shortages and is increasingly being attacked by the gangs.
Further attacks after at least 15 killed in prison riot in Ecuador
On 4 December, at least 11 people were injured in a grenade attack at a prison in Guayaquil, in southern Ecuador. In mid-November, clashes broke out in the same prison. At least 15 people were killed and 14 injured before authorities could halt the violence.
The El Litoral facility, where the recent riot took place, is partly under the control of gangs, whose members can easily access firearms inside the facility. According to local sources, at least eight separate gangs are present in the 12 blocks of the prison; in some cases, multiple gangs share one cell block, leading to greater tensions.
It is highly likely that the riot and recent grenade attack were linked to the murder of Braulio Obando, the leader of the organised criminal group “Mafia-18”, one day prior to the riot, which seemingly broke a precarious truce between armed gangs in the area.
As previous cases have highlighted, outbreaks of violence in El Litoral often spread out to the suburbs of Guayaquil. It is likely that further targeted killings will occur in the coming weeks.
Environment, Health and Miscellaneous
Magnitude 7.0 earthquake recorded off the coast of California
The tremor occurred at 18:44 (local time) on 5 December, approximately 80 kilometres from Rio Dell, northwest of Sacramento. Authorities in California and neighbouring Oregon issued a tsunami warning that was subsequently lifted. No serious damages were reported on land. However, there is a realistic possibility of aftershocks following the tremor.
Cuba suffers another major power outage
On 3 December, a nationwide blackout was recorded in Cuba after a major failure at the Antonio Guiteras power plant in Matanzas. The blackout left millions of Cubans without electricity, resulting in the closure of schools and non-essential businesses.
The government has begun restoring power, partially using generator systems. While power was partially restored on 5 December, planned outages are likely to resume.
This incident is just the latest blackout in a series of power outages caused by hurricanes, fuel shortages and an outdated grid, with previous outages resulting in major protests against the government.
Europe, Middle East & Africa
France: Barnier government falls
Prime Minister Michel Barnier resigned on 5 December after his government was toppled in a no-confidence vote on the day prior. The vote was sponsored by the left-wing coalition, the New Popular Front (NFP), and was supported by the right-wing National Rally (RN). The latter’s support for the no-confidence motion, which followed months of tensions concerning the 2025 budget, broke the precarious equilibrium that had allowed the centrist bloc to support Barnier for three months.
Constitutionally, National Assembly elections cannot be held until the summer of 2025, meaning that the parliament will continue to be divided into three incompatible blocs. President Macron has so far stated that Barnier will remain at the head of a caretaker government.
In a televised speech, on 5 December, Macron publicly stated that he rules out resigning before the end of his term in 2027, despite Barnier’s fall.
Solace Global Assessment:
The collapse of Barnier’s government is largely RN’s doing. With the 2025 budget now likely out of discussion, the 2024 budget will likely be renewed automatically as per the constitution. This will almost certainly upset Brussels due to the worsening deficit that will result, although this is far from Paris’ main concern.
With Barnier’s ousting, President Emmanuel Macron has a shrinking number of options. The first, and seemingly likeliest considering the speech on 5 December, is to push ahead with reinstating Barnier (or another figure from the centre or centre-right) to head a caretaker government with virtually no power until the following National Assembly elections. This matches Macron’s own repeated pledges to remain President until the end of his term in 2027.
With the 2024 budget again in place, a new caretaker government could perhaps hope to restore the informal “truce” with RN until 2025. However, there is no guarantee that RN would acquiesce to this. The verdict for RN leader Marine Le Pen’s trial, which threatens to bar her from running for office, is expected on 31 March 2025 and the party, therefore, has an incentive to maximise gains before it is at risk of being “decapitated” (it is notable that even if the trial went to the appeal stage, a guilty verdict would still bar Le Pen from running provisionally).
The second option is to resign. This option would result in snap presidential elections which would almost certainly result in a second-round contest between Le Pen and Jean Luc Mélenchon, the leader of France Unbowed (LFI), a populist left party that leads NFP (or, as some analysts have noted, potentially another NFP leader with a less “polarising” brand than Mélenchon). While providing for a fresh political start, the new president would still have to deal with the tripartite parliament, creating a highly unstable political environment.
A last scenario, which does not involve Macron’s choice, is the beginning of another impeachment procedure against the president. While NFP continues to call for Macron’s impeachment, their motion (if it were to be supported by RN) would fall short of the required two-thirds of the National Assembly (364 votes against the needed 385). With the centrist parties supporting Macron having little to gain by defecting, it is unlikely that they would tilt the balance in favour of the opposition forces.
A third, and potentially increasingly likely, option, is to attempt to bolster the centrist bloc by looking to the Socialists (PS). On the morning of 6 December, Oilivier Faure, PS’s leader, stated on French radio that he was open, at least in principle, to discuss a “short-term” agreement with the conservatives and Macron to avoid the country’s political apparatus breaking down. Obviously, like the other forces of the NFP, the PS wants to avoid being seen as supporting Barnier-style spending cuts, and striking an agreement with them will therefore need to entail significant compromise from Macron’s side.
Nevertheless, PS’ support has been an unspoken possibility for a while. The party has been languishing on the left despite winning almost as many seats as LFI in July, and continues to be worried about losing votes to both LFI and the Greens. Moreover, there realistically is no way for PS to field a candidate to challenge Mélenchon as the left’s representative in 2027, but the party also opposes LFI’s populism and personalism, which has involved repeated attacks on NFP allies like PS. By striking a deal with Macron, PS could gamble that it will reinforce its position as a “responsible” centre-left force. In doing so, it would likely collapse the NFP. The growing instability of the French political system is highly likely to result in growing civil unrest in France. If Macron refuses to resign, it is highly likely that NFP leaders will call for street protests that, considering recent instances, have a high likelihood to become violent in cities like Paris, Marseille and Lyon. However, even if Macron resigns, an NFP-RN presidential race is also likely to result in growing unrest, as highlighted by the increase in protests after the first round of the 2022 presidential elections.
Georgia: Anti-government protests further intensify with increasing clashes
Pro-European opposition protesters have continued a wave of civil unrest across Georgia. These protests have escalated in both scale and intensity following the Georgian Dream government’s decision to suspend EU accession talks on 28 November. The largest demonstrations have taken place in Tbilisi in the vicinity of the Parliament of Georgia on Rustaveli Avenue, with daily clashes between riot police and protesters. Smaller protests have also reportedly taken place in Rustavi, Batumi, Kutaisi, Zugdidi, Telavi, Khashuri, Poti and Gori.
Security forces have deployed water cannons, tear gas, and rubber bullets against protesters. Over 300 protesters have been detained, with reports that detainees are being beaten while in custody. While there have been dozens of hospitalisations, no deaths linked to the unrest have so far been reported. There are additionally strong indications of a government crackdown against the political opposition, with an office raid and detainment of Nika Gvaramia, the leader of the Ahali party, on 4 December.
Solace Global Assessment:
The protests are highly likely now both larger and more intense than the March 2023 and April-June 2024 “anti-foreign agents” bill protests. Demonstrators have attempted to set up protest camps and barricades on Rustaveli Avenue in central Tbilisi, reminiscent of the 2013-2014 Ukrainian pro-Europe ‘Euromaidan’ protests that led to the overthrow of the pro-Russia Yanukovych-led government. While Georgian riot police have generally successfully dispersed protesters overnight through the use of significant force, on each day the following morning, protesters have regathered outside Georgia’s parliament.
The civil unrest is highly likely to continue into the following weeks. While the disruptions and violent clashes are currently localised to specific protest hotspots, there is a realistic possibility that the unrest could further escalate.
Triggers for further escalation include the now-scheduled 14 December Presidential election and its aftermath, which will be the first conducted using an indirect vote system through a 300-member College of Electors and will highly likely give a result in favour of the Georgian Dream nominated candidate Mikheil Kavalashvili. The pro-Europe incumbent and leading voice of the protest movement, President Salome Zourabichvili, has vowed to remain in her post until new parliamentary elections are held. This will likely generate a key point of political conflict.
Another trigger for an escalation in unrest could be the killing of protesters by security forces. In the Ukrainian Euromaidan movement, the increased use of lethal force (including live ammunition) by security forces against protesters led to a dramatic intensification of the protest movement. There is a realistic possibility that Georgian protesters could become more resilient at holding off dispersal by riot police, and/or escalate protest tactics to the occupation of government buildings, which could in turn increase the deployment of lethal force by security forces.
Syria: HTS-led offensive captures Hama and rapidly reaches Homs in lightning advance
Abu Mohammed al-Golani, the leader of the Syrian Islamist rebel group Hayʼat Tahrir al-Sham (HTS), declared on 4 December that the HTS-led offensive had captured Hama. This followed the surprise lightning offensive launched by HTS on 27 November that quickly captured Aleppo. The regime’s Syrian Arab Army (SAA) had initially provided resistance and halted the advance for the first time in the countryside north of Hama, exploiting the elevated terrain just north of Hama on the mountain of Jabal Zayn al-Abidin.
However, the HTS offensive rapidly outmanoeuvred the SAA and bypassed the mountain, with their entry into Hama leading to the urgent withdrawal of SAA forces. The HTS-led offensive then continued southwards towards Homs. As of the time of writing on 6 December, rebel forces are reportedly already in the outskirts of Homs.
Additionally, the Turkish-backed rebel group Syrian National Army (SNA) and the Kurdish-led and US-backed Syrian Democratic Forces (SDF) have engaged in heavy fighting in northwestern Syria, with the SNA seizing the town of Tal Rifaat from the SDF. The SDF had earlier withdrawn from Aleppo following negotiations with HTS.
In central and eastern Syria, the SDF has advanced into regime territory in operations that are stated to halt the expansion of the Islamic State of Iraq and Syria (ISIS), with ISIS making an announcement declaring control over significant portions of Sria’s central desert region. The US also conducted airstrikes on ISIS targets in Deir ez-Zor in eastern Syria.
Solace Global Assessment:
The lightning advance of the HTS-led offensive against the regime has dramatically reignited the Syrian Civil War and has triggered a resurgence of hostilities among various factions within the country. A pattern is currently emerging of the SAA quickly withdrawing and ceding significant ground to the rebels. On the one hand, this could mean that SAA battlefield losses have been low relative to the substantial gains the rebels have made, which could indicate that the SAA has maintained enough combat effectiveness to conduct counteroffensives at a later stage.
On the other hand, however, the fragility of the SAA may have been exposed by the surprise offensive, with the Assad regime having relied considerably on Iranian proxy forces and Russian support previously to resist and reverse advances made by Syrian rebels.
If the rebel offensive captures Homs, which may occur imminently unless the SAA stands its ground, the coastal Tartus and Latakia Governorates which provide the regime access to the Mediterranean Sea may be quickly cut off from routes to Damascus. These regions hold prominent strategic value to Russia. Russia operates the Khmeimim Air Base in Latakia and a naval facility in Tartus, the Kremlin’s only foreign naval base.
Russia has withdrawn multiple naval vessels from Tartus, highly likely fearing the threat posed by HTS one-way attack uncrewed aerial vehicles (OWA-UAVs) and the imminent threat by ground offensives. While heavily degraded by the war with Israel, unverified sources indicate that Lebanese Hezbollah has reportedly started to send hundreds of fighters to Syria, and Hezbollah’s new leader Naim Qassem has pledged to stand by the regime.
The reignition of the civil war has almost certainly set the conditions for increased ISIS activity, with the SDF advancing into regime territory to halt claimed ISIS expansion. While ostensibly neutral with the regime, the SDF are highly likely filling the vacuum left by regime forces that are redeploying. However, the SDF are highly likely struggling to contain parallel offensive actions by the Turkish-backed SNA, and there is a realistic possibility that the conventional Turkish military could further increase aerial operations against targets in both Syrian and Iraqi Kurdistan.
Israel, Gaza and Lebanon: Israeli forces continue operations in north Gaza while Hezbollah begins recruitment drive
Units of the Israel Defence Forces (IDF) have continued their focused operations in northern Gaza, aimed at destroying the last remaining groups of Palestinian militants. On 3-4 December, IDF units carried out further clearing operations in Beit Lahia. On 5 December, Amnesty International released an investigation concluding that Israel “is committing genocide against Palestinians in Gaza”. Also on 5 December, Hamas officials announced they had met with Fatah representatives in Cairo to agree on a post-war “committee” to administer the Gaza Strip.
The Lebanese Armed Forces (LAF) have continued to develop in southern Lebanon where, despite occasional strikes and reports of Hezbollah operations south of the Litani River, the ceasefire continues to hold. According to LAF officials, up to 5,000 troops will be deployed in the area as part of the ceasefire agreement. Israeli and international observers have noted that Hezbollah has begun reorganising immediately after the ceasefire, including by carrying out recruitment drives among its supporter base.
Solace Global Assessment:
Israel is likely to continue raids across the Gaza Strip to degrade Hamas and prevent the group from re-forming units capable of organised resistance.
The finding of an additional hostage’s body, reported on 4 December, months after six other hostages had been found killed in a tunnel in Khan Yunis, highlights Hamas’ continuing policy of killing hostages if they expect that they will be freed by IDF forces.
Protracted IDF operations in Gaza are likely to continue driving significant international and domestic pressure on the Netanyahu administration to agree to a ceasefire deal with what remains of Hamas.
Hamas’ apparent willingness to allow Fatah to re-enter Gaza almost certainly highlights the significant losses suffered by the group, which have impeded its ability to carry out administrative functions inside Gaza and have thus created opportunities for alternative local groups to operate outside of Hamas’ control.
Hezbollah is almost certain to continue recruitment and rearmament efforts in the medium term. While the loss of much of its leadership creates a short-term vulnerability, Hezbollah’s ability to replace leaders showcases a significant resilience that, alongside a reduction in combat following the ceasefire, will likely ensure the organisation’s recovery.
However, developments in Syria will likely impact Hezbollah’s ability to replenish its rocket and missile arsenals. With the Assad regime under pressure from HTS and other rebel groups, Tehran’s supply route to Hezbollah via Syria may be redirected to help Damascus.
Moreover, Damascus’ retreats could result in fewer border crossings becoming available for Iranian weapons shipments to Lebanon, which in turn would make Israeli airstrikes at the Syria-Lebanon more likely to result in significant personnel and material losses.
Mali: Junta government detains more Western mining employees
On 26 November, Mali’s junta government arrested four senior employees of the Canadian mining company Barrick Gold. Those arrested are employed at Barrick Gold’s Loulo-Gounkoto mining complex in western Mali, close to the Senegalese border. Barrick Gold has rejected the charges, which remained unspecified, but has released a statement indicating that they are working with the Malian government to secure the release of those detained.
Solace Global Assessment:
The recent detention of Barrick Gold’s employees is almost certainly part of a broader effort to exact greater revenue from Western mining companies operating within Mali. Barrick Gold employees were briefly detained in September 2024; in December, the CEO of Australian company Resolute Mining and two of its employees were arrested.
Resolute Mining‘s employees were only released after the company agreed to a settlement involving an upfront payment of USD 80 million and a commitment to an additional USD 80 million.
The detentions follow a government audit of Mali’s mining sector in 2023 and the adoption of a new mining code, which has been enforced retroactively. The new code increases state and local interests in new projects from 20 per cent to 35 per cent, allowing the government an initial 10 per cent stake, the option to purchase an additional 20 per cent within two years of production, and allocating 5 per cent to local communities.
Dwindling government revenues, sanctions, high poverty levels and endemic separatist and jihadist violence has likely forced the junta to adopt such an aggressive policy towards the mining companies, with foreign companies now facing increased risks, including detentions of personnel and additional financial liabilities if they fail to comply.
Whilst this action is likely to undermine Mali’s international reputation and deter foreign investment, it provides a short-term financial boost to the military government. Moreover, the junta has likely been emboldened by Russian support, calculating that the Kremlin will step in to fill any void left by departing Western investors.
Russian support will likely entail more favourable resource agreements, military aid, and security guarantees for an increasingly threatened junta government. Should this policy prove successful, there is a realistic possibility that it is emulated by the junta governments in Burkina Faso and Niger or that it migrates to other sectors outside of gold mining.
Mozambique: Seven-day “4×4” wave of unrest begins
Since a controversial election on 9 October which declared the incumbent Frelimo party as victor, Mozambique has experienced significant unrest. After several three-day waves, opposition leader Venâncio Mondlane has called for a “4×4” (four by four) phase of protests planned to last seven days, from 4-11 December.
During this phase, Mondlane has called for a total shutdown from 08:00 to 15:30 during each day of this phase. This shutdown is to involve protesters parking vehicles on major roads and congregating in key neighbourhoods and avenues of major cities. From 21:00 to 22:00, people are to make as much noise as possible with vuvuzelas.
So far, the first days of this phase have seen significant unrest and clashes between protesters and security forces. Protesters have blocked roads and “tolls” are reportedly being collected at roadblocks outside of the Maputo International Airport. At least 13 people have been killed and 34 shot in the latest stage of protests, with Nampula being a notable hotspot for the volume of injuries and accounting for at least seven deaths.
Solace Global Assessment:
Repressive measures by security forces will almost certainly continue. On 3 December, the government promised to use “all means at its disposal” to prevent demonstrations. Security forces have utilised tear gas and live ammunition during each phase of unrest.
In response, protesters have targeted police and Frelimo assets, burning down several police stations and vehicles. On 4 December, local media reports that protesters invaded the Frelimo headquarters in Muecate, Nampula discovering hundreds of voter cards, which they scattered on the street.
Whether or not this report is accurate, this publicised event is highly likely to lead to more Frelimo headquarters being targeted by protesters, who will be incentivised to hunt for more evidence of election rigging.
A political resolution is unlikely to appear soon. While Mondlane expressed support for a second “virtual meeting” with President Nyusi, the government and Mondlane remain at an impasse regarding the agenda, with Mondlane refusing to meet unless his agenda is granted. Mondlane has warned that he will keep urging for demonstrations through Christmas unless “the truth about the elections” is disclosed. His goal is reportedly to compel the government to engage in dialogue. To achieve this, Mondlane believes the protests “need to carry on for longer, maybe two to three months, at the same pace”.
Significant economic damage has resulted from business disruptions and the repeated temporary closure of the Lebombo border crossing, Mozambique’s busiest border crossing with South Africa. President Filipe Nyusi has emphasised that payment to public employees may be jeopardised due to demonstrations and that private companies and supplies may also be impacted.
In the most recent wave, Mondlane has called on protesters to target airports for the first time and to halt flight activity to and from Mozambique. While flights have, so far, been largely unaffected, Mondlane’s aim appears to be to disrupt business operations in the country.
This is likely to both increase internal pressure on the government, which will face mounting anger the longer unrest continues, and increase external pressure as surrounding countries’ economies continue to be negatively impacted by the disruption.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Pre-Christmas travel strikes expected across Europe
Strikes across Europe are causing significant travel disruptions in the run-up to Christmas. In Italy, a nationwide strike will impact trains, trams, and airports on 13 December, with further disruptions on 15 December.
In France, rail and port strikes begin on 11 December, which is expected to last until Christmas, while easyJet workers in the country will continue their strike until 16 December.
In Spain, a nationwide bus strike that started in November is ongoing, with the strike particularly affecting Murcia and Andalusia.
Finnair is also cancelling 300 flights on 9 and 13 December due to a strike by pilots. Additional impromptu transport strikes across the continent are likely in the run-up before the holidays.
Centre-right dominates Irish General Election
In the 2024 Irish General Election, Fianna Fáil emerged as the largest party, with its leader, Micheál Martin, claiming a significant win after the counting process. The focus will now shift to coalition negotiations, with Fianna Fáil is expected to form a government alongside its centre-right ally Fine Gael.
Sinn Féin, despite its strong performance, remains unlikely to join the coalition due to opposition from the two main centre-right parties, which have ruled out collaboration with the left-wing party. However, smaller parties like the Social Democrats and Labour are expected to play a crucial role in the formation of the new government in the weeks to come.
Italian parliament approves migration reform
The new legislation expands the list of “safe countries”, possibly affecting asylum claims of migrants arriving via the central Mediterranean route. Moreover, it shifts the responsibility for the rejection of migrants to the courts of appeals, grants authorities the ability to inspect migrants’ personal devices, and seals information regarding border control agreements with third countries.
The law is the government’s reaction after the de facto stalling of its plan to relocate migrants whose asylum claims need to be processed to Albania. Civil society actors and NGOs have attacked the law, claiming that it infringes upon migrants’ rights.
There is a realistic possibility of localised protests following the law’s passing in cities including Rome, Florence, and Bologna.
Romanian parliamentary election see populists gain, liberals lose
The vote, held on 1 December, resulted in the Social Democrats (PSD) finishing first with 22 per cent of the total votes, despite losing six points compared to their 2020 showing. Their coalition ally, the National Liberal Party (PNL) collapsed to 14.3 per cent (11 points less than in 2020).
Far-right and anti-establishment forces made important gains. The Union of Romanians (AUR), which last week threw its weight behind anti-EU presidential candidate Georgescu, won 18 per cent of the vote and more than doubled its 2020 share. The far-right SOS Romania improved upon poll predictions and secured 7 per cent of the total votes. AUR-splinter, the anti-establishment and far-right Party of Young People (POT) won 6.4 per cent of the vote.
The election results make a new PSD-PNL alliance likely, possibly with a much weaker PNL and the participation of smaller centrist and regionalist formations.
The upcoming second round of the presidential elections will almost certainly be decisive to chart Romania’s political future and may have repercussions for the entire EU bloc. If Georgescu wins, which current polls say is likely, he will cohabit with a less stable centrist, EU-friendly coalition, which may create opportunities for greater populist gains. Moreover, Georgescu’s ongoing conflict with the Romanian state security council, which has accused him of being “boosted” by a Kremlin-promoted covert information operations effort, may materialise in severe civil unrest following the second round of voting.
Niger junta seizes French-run uranium mine
The French group Orano announced on 5 December that Nigerien authorities took control of its uranium mining unit. Orano spokespeople had highlighted a worsening operational environment, with repeated cases of “interference” dating back months. The seizure likely follows the cases discussed above in Mali and continues to underscore the juntas’ willingness to sever its economic and political ties to Western states.
Niger is one of the world’s leading uranium producers and the loss of access to its reserves is an important setback for Paris, which has had its influence in the Sahel hugely reduced in recent years. Even if Niger’s junta is not directly responding to Moscow’s pressures, the move is likely to be well-received by its Russian partners.
Ghanaians set to elect new president on 7 December
Ghana’s presidential election will be held on 7 December alongside parliamentary elections for 275 constituencies. Polling indicates that the main opposition leader, John Dramani Mahama, is set to win the presidential election, placing him ahead of the main rival, incumbent Vice President Muhamudu Bawumia but with 11 other candidates running.
The election is set to be dominated by concerns over the economy, jobs, education, and the state of the country’s infrastructure, with both candidates presenting plans to boost the economy. The polling results are close and there is a high likelihood that a presidential run-off vote will be required to determine the winner. However, no party has ever secured more than two consecutive terms, a pattern that favours the opposition.
Namibia set to elect first female president
On 3 December, Namibia’s electoral commission announced that Vice President Netumbo Nadndi-Ndaitwah of the incumbent SWAPO party was set to become the nation’s first female president. Nadndi-Ndaitwah won with 57 per cent of the vote and her SWAPO party retained its parliamentary majority. However, the election was marred by technical errors and delays, with several opposition parties refusing to recognise the results and promising to begin a legal appeal.
Security, Armed Conflict and Terror
Swedes charged for preparing to conduct terror attacks for the Islamic State
On 2 December, Swedish counter-terrorism operations led to the detention of four male Swedish citizens allegedly planning to conduct terrorist attacks for the Islamic State (IS). Three of the suspects were charged with planning violent acts and for aiming to instil fear or destabilise Swedish society.
The group has ties to an Islamic group in Tyresö, links to organised crime in Sweden, and were attempting to recruit underage individuals for attacks. The group reportedly had connections to the Islamic State Somalia Province (ISSP), a branch of IS that has grown in importance in recent years after the relative demise of IS in the Middle East and an increase in IS activity in Africa.
ISSP’s leader was recently made head of the General Directorate of Provinces and is partially responsible for the group’s external operations. Somalia likely serves as a key link between IS senior leadership in the Middle East and its affiliates in Africa, with ISSP potentially increasingly targeting the Somali diaspora in the West for recruitment purposes.
UN warn of critical conditions in Sudanese refugee camp after RSF attacks
The United Nations and the NGO Doctors Without Borders (MSF) have warned that conditions within the Zamzam refugee camp near El Fasher in Sudan’s North Darfur state have reached critical levels. The warning follows the reported shelling of the camp on 1 and 2 December by the Rapid Support Forces (RSF) paramilitary group. The shelling has killed several people and has severely disrupted the provision of healthcare within the camp, which houses over half a million displaced persons. The camp has been under siege for months, which resulted in the declaration of famine conditions in August.
At least 56 people killed in football-related violence in Guinea
A stampede and clashes resulted in dozens of deaths and injuries in Nzérékoré, the country’s second-largest city, during a football match at the municipal stadium. The violence reportedly broke out following a controversial refereeing decision. According to local media, the death toll and the number of injuries have paralysed local healthcare facilities, creating widespread delays and disruptions.
There is a realistic possibility that the incident will result in localised civil unrest, as some civil society actors have blamed the government for failing to put in place adequate security measures and for allegedly underreporting the actual casualty numbers. Moreover, as the match was being held “in honour” of junta leader Mamady Doumbouya, the violence is likely to be linked to the junta’s rule, making unrest likelier.
Ceasefire does little to deter conflict in eastern Democratic Republic of Congo (DRC)
Since 3 December, clashes between the Kigali-backed M23 Movement and the Congolese army have escalated in the northern regions of M23 operations, particularly in the Lubero region. This comes amidst the revived Luanda process, which is an Angola-brokered ceasefire agreed on 30 July 2024 between the Congolese and Rwandan governments, the latter of which has been accused of providing support to the M23 militia.
The DRC’s eastern North Kivu province has been wracked by instability for decades. Since 2021, the ethnically Tutsi M23 militia, backed by Kigali, has seized large areas of land and has threatened to take its capital, Goma. Their stated objectives are to protect the interests of the Tutsi and Kinyarwanda-speaking minorities in the region, which are threatened by Hutu militias including the Democratic Forces for the Liberation of Rwanda (FDLR).
In their efforts against DRC forces, the M23 Movement has perpetrated various human rights violations including executions, sexual assault, and the utilisation of child soldiers. Ceasefire prospects are complicated by the fact that the M23 rebels, while backed by Kigali, are not directly under their control. As such, while Kigali provides operational support to the group, it is unclear how much a ceasefire between the two governments can bind the rebel group to its terms.
Despite the ceasefire’s significance in representing progress between Kinshasa and Kigali, the M23 Movement’s ongoing operations represent its limitations in stabilising the humanitarian situation in North Kivu.
Environment, Health and Miscellaneous
Storm Darragh to batter United Kingdom
The United Kingdom’s Meteorological Office has issued multiple red, amber and yellow warnings in anticipation of Storm Darragh which is set to cause significant disruption from 6 December. The storm is set to bring 140 kph winds to the UK, prompting the rare issuing of red warnings which are typically associated with life-threatening weather. Large waves, power cuts, falling trees, travel disruptions, and mobile or internet disruptions are highly likely.
UNRWA pauses aid deliveries through Kerem Shalom crossing
The announcement was made on 1 December and follows increasing cases of looting and violence towards humanitarian workers. The depletion of Hamas’ manpower has emboldened other groups to seize aid entering Gaza from the main open crossing. As such, there is a greater risk of violence between groups resulting in injuries for workers and civilians. The pausing of UNRWA aid deliveries is highly likely to contribute to already severe delays in the delivery of vital aid to southern Gaza.
At least 7 dead as standoff between police and miners continues in South Africa
More than 1,000 people are assessed as trapped in a disused gold mine in Stilfontein in South Africa’s North West province. They are engaged in a weeks-long standoff with South African police. The illegal gold miners, many of which come from neighbouring countries have mostly continued refusing to resurface (approximately 25 have done so over the reporting period). On the other hand, police forces cannot realistically enter the mine shafts due to considerable safety hazards. Despite courts’ calls to allow emergency workers to enter the mines, the situation continues to be extremely precarious, with a high likelihood of further casualties in the coming weeks.
Asia–Pacific
Pakistan: Pakistan increases counter-terrorism operations in response to wave of militant attacks
The Pakistani military’s media wing, the Inter-Services Public Relations (ISPR), has stated that it has initiated intelligence-based operations against terrorist entities in parts of the country’s restless Khyber Pakhtunkhwa province. The operations have resulted in the deaths of dozens of militant fighters and several Pakistani military personnel, with most operations targeting militant senior leadership. The operations have been launched amid a wave of extremist and separatist attacks in Pakistan, with over 850 attacks already recorded in 2024, surpassing the 645 attacks recorded in 2023.
Solace Global Assessment:
In November, Prime Minister Shehbaz Sharif announced that the government had approved a “comprehensive military operation” against militant groups after a wave of deadly attacks by the extremist group Tehrik-i-Taliban Pakistan (TTP) and the separatist group Balochistan Liberation Army (BLA). However, a lack of funds, inadequate local support, significant internal unrest and the overstretching of the security forces has likely denied the government the ability to launch large-scale offensives. In addition, the militant groups are often afforded local support and have increased their capabilities in recent years.
Consequently, the military’s actions will likely be constrained to small-scale and targeted operations against key figures within the militant groups. Moreover, without sufficient access to advanced intelligence, surveillance, and reconnaissance (ISR) technology such as drones and communication equipment, the effectiveness of such operations will likely be constrained.
However, the operations, which have likely been partially initiated by Chinese pressure after attacks on Beijing’s interests, have almost certainly sent a strategic message to the militant groups who will likely escalate their attacks in response. Such a reprisal strategy will likely worsen Pakistan’s already volatile security situation and likely translate into more militant attacks in areas outside of their control. This will likely include increased militant attacks in major population centres like Karachi, which was attacked by the BLA in October.
South Korea: President Yoon Suk Yeol faces impeachment after temporarily imposing martial law
On 3 December, President Yoon imposed martial law for the first time since South Korea became a democracy, its last use being in 1979 during a coup. In justification, Yoon claimed that it was needed to defend the country from internal pro-North Korea forces and that the National Assembly was “attempting to paralyse” the government. Martial law enables rule by military authorities and involves the suspension of civil rights including freedom of the press and freedom of assembly.
Yoon also ordered striking doctors to return to work. Upon declaring martial law, the military, alongside the police, deployed to the National Assembly building while thousands of members of the public turned out to protest.
According to South Korea’s constitution, martial law should only be used in “wartime, war-like situations or other comparable national emergency states”. The constitution also grants the National Assembly to lift martial law with a majority vote. As such, South Korea’s parliament gathered in the National Assembly and unanimously voted against its imposition 190-0. Yoon’s own party, People Power Party, joined the opposition in voting against it.
Shortly after the vote, Yoon lifted martial law, six hours after it was imposed. On 4 December, impeachment proceedings against Yoon were initiated and, in the aftermath, Defence Minister Kim Yong-hyun took responsibility and offered his resignation.
Solace Global Assessment:
Yoon’s decision to impose martial law comes amidst what is essentially a political deadlock. Since the opposition won a landslide in the April 2024 general election, Yoon has been a “lame duck” president, unable to pass any bills while vetoing bills passed by the opposition. A doctors’ strike in opposition to his bill to increase the number of medical school enrolment numbers, alongside several corruption scandals, has only increased pressure on his administration.
The imposition of martial law is viewed as an extreme measure to be taken at times of national emergency and opposition members view Yoon’s actions as not meeting the constitutional requirement. Yoon is now facing impeachment, with a vote taking place later this week, which requires support from two-thirds of the National Assembly. Consisting of 300 seats, 192 of which are held by opposition members, at least eight members of Yoon’s party will need to join the opposition in voting for his impeachment.
While members from Yoon’s party initially rallied behind him, on 6 December the party chief expressed support for suspending Yoon’s constitutional powers, suggesting impeachment is highly likely. If approved by the National Assembly, the impeachment trial would be conducted by the Constitutional Court, where six out of nine justices must vote in favour of impeachment to formally remove Yoon from office.
Yoon is currently also being investigated for the crime of “insurrection”, something that carries the death penalty in South Korea. While proceedings are unlikely to go this far, partially because it is difficult to prove, it is unclear how far lawmakers will go; however, previous crimes conducted by former presidents have carried long jail sentences.
In the most likely scenario, whereby Yoon is impeached, Prime Minister Han Duck-soo would take over presidential duties. If this happens, a snap election will almost certainly be called. If Yoon survives the impeachment process and refuses to resign, an outcome that is highly unlikely, protests will almost certainly continue and will add pressure to an already deeply unpopular leader.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Protests in India and Bangladesh over arrest of Hindu Hare Krishna priest
The arrest of Hindu Hare Krishna priest Chinmoy Krishna Das in Chattogram, Bangladesh has sparked significant unrest, leading to protests both within Bangladesh and in neighbouring India. On 2 December, protestors in Agartala, India attempted to breach the Bangladesh mission, causing damage to the building.
In Bangladesh, the authorities have frozen the bank accounts of 17 individuals linked to the International Society for Krishna Consciousness in response to the unrest. The unrest is almost certainly linked to the increased persecution of Hindus in Bangladesh following the ousting of Prime Minister Sheikh Hasina, who has sought sanctuary in India, with New Delhi’s refusal to hand her over further provoking sectarian tensions.
Indian farmers set to march on New Delhi by 6 December
On 2 December, approximately 5000 farmers from the Indian state of Uttar Pradesh began marching towards New Delhi to protest and demand better compensation and lower costs for farming. The protestors are set to arrive in the capital by 6 December. Additional farmer protests are set to take place within the provinces of Kerala, Uttarakhand, and Tamil Nadu where they will march towards their respective legislative assemblies on 6 December. The protests are unlikely to be as large or disruptive as the farmer protests in February which resulted in major roadblocks, detentions and the use of force; however, transports disruptions and localised clashes with the police are likely.
Security, Armed Conflict and Terror
Sectarian violence in Pakistan’s Khyber Pakhtunkhwa province kills over 130
Armed clashes between Sunni and Shia Muslim tribes in Kurram, a district in Pakistan’s Khyber Pakhtunkhwa province, have resulted in over 130 deaths as a result of retaliatory attacks following the ambush of a Shia convoy on 21 November. A temporary ceasefire has failed to last, and road closures have led to food and medical shortages. With the clashes gaining a lot of traction on Pakistani media, there is a realistic possibility that the Shia minority will be targeted in attacks in other parts of the country.
Major Myanmar rebel group signals intent to engage in peace talks
One of the largest rebel groups in the Myanmar civil war and member of the Three Brotherhood Alliance (TBA), the Myanmar National Democratic Alliance Army (MNDAA) has expressed a willingness to engage in peace talks with the junta government and has declared a unilateral ceasefire. The MNDAA has made significant gains in Shan State, including the capturing of the major border town of Lashio.
The MDDAA’s decision has likely been influenced by Beijing, who is increasing its involvement in the conflict after much of China’s border regions have been destabilised. The Chinese closing of borders and restriction of supplies has likely forced the MNDAA into accepting a course towards peace or face the risk of being isolated and ill-prepared to continue its war with the regime.
China and Philippines accuse each other of escalating in South China Sea
China and the Philippines have traded accusations after each party accused the other of conducting dangerous manoeuvres in the disputed South China Sea. Manila claims that Chinese Coast Guard vessels used water cannons and dangerous manoeuvres to deter Filipino vessels from patrolling near the Scarborough Shoal. Conversely, Beijing claims the Filipino vessels initiated the confrontation and has ordered Manila to stop its infringements into Chinese waters and cease its propaganda.
The incident follows a diplomatic dispute in November after China outlined territorial waters around Scarborough Shoal and submitted new nautical charts to the United Nations to assert its claim.
Environment, Health and Miscellaneous
Multiple killed by severe flooding in southern Thailand and Malaysia
As of 6 December, the death toll has risen to over 30 in Thailand’s southern provinces as a result of severe flooding which is estimated to have affected over 600,000 people. Thailand’s Ministry of Public Health has stated that 33,000 people have been forced to evacuate their homes in the five most affected provinces, Pattani, Narathiwat, Songkhla, Nakhon Si Thammarat, and Phatthalung. Floodwaters have continued to rise and further rain is forecast, which will almost certainly continue to cause major disruptions to essential services like healthcare and transportation.
Neighbouring northern Malaysia has also been affected, with tens of thousands displaced and at least six fatalities. Health authorities in Malaysia are also on high alert in preparation for a surge in waterborne diseases following the flooding.
UN talks on global plastic treaty falter in South Korea
The treaty would have imposed new global regulations on plastic waste management, as well as introduced caps on plastic production. This latter point provoked the opposition of oil-producing
nations, including the Gulf States and Russia. The treaty would have likely been the most important
environmental treaty since the Paris one. Instead, its failure follows similarly disappointing outcomes at the COP29 and COP16 summits. There is a realistic possibility of environmentalist activists in Western states staging protests with the aim of causing traffic disruptions in cities like London, Paris, or Berlin in the aftermath of the summit.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence

Executive Summary
- The suspension of EU accession talks will highly likely continue to intensify civil unrest in Georgia, and the December presidential election will highly likely also trigger unrest.
- The HTS-led rebel offensive in Syria has almost certainly escalated the civil war after four years of relatively reduced combat intensity.
- The terms of the ceasefire between Hezbollah and Israel highly likely reflect Hezbollah’s weakness and likely constitute a success of Israeli operations in Lebanon.
- Government repression of PTI unrest highly likely to continue in Pakistan after protesters marched to Islamabad in defiance of a government ban.



AMER
Haiti: UN begins partial withdrawal from capital
US & Mexico: Trump team debates military intervention in Mexico
EMEA
Romania: Anti-NATO candidate wins first round of presidential elections
Albania: Anti-government protests continue in Tirana
Georgia: Unrest intensifies after government suspends EU accession talks
Syria: HTS-led offensive rapidly reaches the outskirts of Aleppo
Israel & Lebanon: Israel and Hezbollah agree to a ceasefire
Chad: France ordered to withdraw military
Mozambique: Unrest continues after meeting breaks down
APAC
Pakistan: Unrest in Islamabad after demonstrators defy protest ban
India & Sri Lanka: Cyclone approaches India after hitting Sri Lanka
North, Central and South America
United States & Mexico: Trump administration reportedly considering US military deployment against Mexican cartels
President-elect Donald Trump’s team is reportedly debating the nature and limitations of an invasion into Mexico to combat the cartels. Despite the controversial nature of the proposal, several of Trump’s cabinet picks, such as the nominated secretary of defence, secretary of state, national security advisor and “border czar” have publicly supported the idea of potentially deploying the US military to Mexico.
Undisclosed sources close to Trump have stated that the plan which has gained the most traction is that of a “soft invasion”, whereby US special forces will be deployed to assassinate cartel leaders on Mexican soil.
Solace Global Assessment:
There is a high likelihood that plans to deploy US forces to Mexico are simply posturing by the Trump team to force Mexico into adopting more forceful measures against the cartels. While Trump may be able to deploy military forces for short-term operations under the War Powers Resolution, a long-term deployment would likely necessitate the approval of Congress, which would be challenging to secure. Such a plan would present a direct challenge to Mexico’s sovereignty and would almost certainly strain relations with the US’ southern neighbour.
Additionally, the deployment of US forces to Mexico in any capacity would likely lead to security issues in both countries. In Mexico, the assassination of cartel leaders would lead to power vacuums and increased cartel violence, as evidenced by the civil war that erupted in the Sinaloa Cartel following the July 2024 US arrest of Ismael “El Mayo” Zambada. The cartels could also escalate violence on US citizens and assets within Mexico, resulting in attacks on US tourists, increased kidnappings, and attacks on US businesses.
The Mexican public could also turn strongly against the US, resulting in anti-American protests and potential boycotts of US businesses. The cartels could escalate violence on US streets through increased gang conflict or targeted killings, while also intensifying drug trafficking to the US to exacerbate domestic issues such as addiction, overdoses, and associated crime.
Haiti: UN initiates partial withdrawal of staff from capital
The United Nations (UN) has initiated a partial withdrawal of staff from Port-au-Prince, Haiti in response to escalating gang violence. The UN has been evacuating staff from the capital via helicopter, moving some staff to safer areas like Cap-Haitien. As of 27 November, the UN reported that more than 40,000 people had been displaced from the capital in the previous ten days.
Solace Global Assessment:
The partial withdrawal of UN staff and widespread displacement of people within the capital is highly likely indicative of the gangs seizing more territory and an increase in gang violence. However, the UN’s withdrawal from Port-au-Prince is unlikely a signal that the organisation is ceasing operations altogether in Haiti. The partial withdrawal is likely a strategic downsizing of staff in the capital to ensure the ability to conduct a full and rapid evacuation if the security situation further deteriorates and has almost certainly been triggered by the gangs previous targeting of airplanes heading to Toussaint Louverture International Airport, which has forced multiple airliners into suspending operations to the capital.
A reduced staff footprint in the capital will almost certainly reduce the UN’s ability to coordinate humanitarian operations and may also influence NGOs to reduce or cease operations in Haiti. Moreover, the UN’s partial withdrawal will likely foster perceptions of abandonment amongst the civilian population. This dynamic will likely to play into the hands of the gangs who are increasingly becoming the main provider of protection, aid and other necessities in many of the areas under their control, enabling them to increase control and recruitment.
The withdrawal will also likely embolden gangs, who are likely to assess that their campaign of violence is producing the desired objectives. There is a realistic possibility that the reallocation of UN staff to areas like Cap-Haitien will lead to an increase in internally displaced people (IDPs) seeking assistance in the northern and rural regions where the gangs have a reduced presence. This trend will likely overstretch both the security forces and humanitarian efforts.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
UK-Argentina tensions flare up over Falklands oil drilling
Tensions between the UK and Argentina have escalated as the Falklands government has approved plans for offshore oil exploration, with production expected to begin in 2027. The Sea Lion field, located 220 km from the islands, is being developed by Israeli company Navitas and British firm Rockhopper Exploration.
Argentina has expressed its disapproval of the project, claiming it is an illegal resource extraction in disputed waters, in a challenge to UK sovereignty. The development could produce up to 80,000 barrels per day, significantly affecting both the Falklands’ economy and likely escalating the regional dispute with Argentina.
Left wing wins elections in Uruguay
The opposition’s candidate Yamandú Orsi narrowly secured victory by approximately 13,000 votes. Orsi is a moderate and ran a very conciliatory campaign, which will result in the Broad Front returning to power after five years of conservative rule. It is unlikely that the election results, which were swiftly accepted by the losing side, will drive protests in the coming weeks.
Security, Armed Conflict and Terror
Multiple bomb threats against Trump cabinet nominees
Several of the president-elect’s picks for the next administration’s key posts have received bomb threats and have been the victims of “swatting” since their appointments. The incidents follow an escalation of violence and threats targeting US politicians, which included the two assassination attempts against Donald Trump. The individuals responsible for the threats have not yet been identified.
Swatting, the practice of making a hoax call to emergency services to prompt the deployment of an armed police force to an address, is widely employed by extremist political activists in the US due to its low cost and risk of identification for the caller, and its severe mental and possibly physical harm it inflicts on its targets.
Colombia-led operation leads to seizure of record amounts of cocaine
A Colombian-led operation labelled Operation Orion, which involved cooperation between 62 countries, has resulted in the record seizure of 225 tonnes of cocaine and over 400 arrests in six weeks. The operation also led to the interdiction of six semi-submersible vessels, which identified the existence a new major trafficking route to Australia.
The operation will likely result in a limited disruptions of the cartels’ drug trafficking networks. However, there is a realistic possibility that the success of the operation will lead to cartel reprisals, most often characterised by direct attacks on law enforcement, the military or politicians responsible.
Environment, Health and Miscellaneous
Mass power outages in Sao Paulo, Brazil
On 28 November, more than 130,000 residents of Sao Paulo were left without electricity due to ongoing infrastructural disruption due to heavy rain and winds, which followed high temperatures of 35 degrees Celsius. Protracted power outages can result in indirect but severe disruptions, including civil unrest. While local authorities have successfully reduced the number of affected households by the morning of 29 November, further forecasted extreme weather conditions could result in further power outages.
Europe, Middle East & Africa
Romania: Outsider wins first round of presidential elections which adds uncertainty for parliamentary vote
Romania held the first round of its presidential elections on 24 November. Călin Georgescu, an independent and anti-establishment candidate, won 22.9 per cent of the total votes, placing first and progressing to the second round, which will be held on 8 December. He is joined by Elena Lasconi, of the Save Romania Union (USR), who obtained 19.17 per cent of the total vote, and barely surpassed Prime Minister Marcel Ciolacu, the Social Democratic Party (PSD) candidate.
The election results are a massive upset, with pre-election polling placing Georgescu, who does not belong to a party and campaigned mostly on social media, at 5 per cent. Moreover, Ciolacu’s failure to reach the second round is likewise unexpected.
On 1 December, a week before the presidential vote, parliamentary elections are set to take place in Romania. Here, the PSD leads the overall polling (at around 30 per cent support) but is followed by the anti-establishment Alliance for the Union of Romanians (AUR), which has endorsed Georgescu.
Solace Global Assessment:
The first-round result has been a political shock not only for Bucharest, but also for Brussels. On 26 November, Valerie Hayer, who heads the reformist Renew group in the EU Parliament, called on the CEO of Chinese-owned social media company TikTok to speak at the parliament over concerns about disinformation. On 28 November, the Constitutional Court ordered the election votes to be recounted.
Georgescu has a realistic chance to win in the second round, also thanks to AUR’s endorsement. Lasconi’s position is not particularly strong, as the centre-right candidate needs to win the support of centre-left voters. Georgescu can instead appeal to a large and “post-ideological” reservoir of disenfranchised voters. In this sense, he can benefit from past political developments that have increased anti-institution sentiments, such as the judiciary’s decision to ban Diana Sosoaca, leader of far-right party SOS Romania, from the list of eligible presidential candidates in October.
The parliamentary vote is likely to be extremely important for the second round of the presidential elections. The Social Democrats suffered a political setback with Ciolacu’s defeat and have ended their alliance with another centre-right force, the National Liberal Party (PNL). This, alongside Lasconi’s USR’s unwillingness to work with PSD, creates a deeply fragmented centre, which may benefit anti-establishment forces.
If results on 1 December match the polls’ predictions, there is a realistic possibility of a parliament divided into three fronts: one led by the PSD, a liberal one, and an AUR-dominated right. In this case, a possible Georgescu win on 8 December could prove an extremely politically destabilising development, as the new president could make the creation of a precarious centrist coalition difficult. This, in turn, could create a situation that is extremely conducive to civil unrest driven by anti-establishment forces.
A weakening of the Romanian political system could open an opportunity for outside powers to increase their influence operations. Russian intelligence has almost certainly engaged in a large-scale effort to encourage acts of Sabotage in European states, especially in the bloc’s northeast. Similar efforts, which have often hinged on disaffected locals with no ideological commitment to Moscow, could be replicated in Romania if the country’s internal situation worsens.
Albania: Anti-government protests continue in Tirana
On 26 November, hundreds of anti-government protesters gathered in central Tirana and blocked roads. For approximately three hours, protesters blocked roads in the vicinity of Tirana City Hall, Elbasan Street, Wilson Square, Black Bird and Palace of Arrows. Efforts by police to disperse the protesters led to violent clashes, with security forces deploying tear gas and water cannons. According to local media, 35 protesters were arrested. On 27 November, an opposition Democratic Party MP announced on social media that 21 protesters had been released from custody.
Solace Global Assessment:
Civil unrest has been ongoing in Albania since late April 2024, marked by confrontations between demonstrators and law enforcement. Previously, protesters have used Molotov cocktails during clashes with police. The protesters are demanding that the incumbent Socialist Party Prime Minister of Albania, Edi Rama, resign and that a technocratic caretaker government be put in place until the 2025 elections. The leaders of the largest opposition parties, Sali Berisha of the Democratic Party and Ilir Meta of the Freedom Party have both been charged with corruption offences. They have said that the charges are politically motivated and accused the Albanian government of orchestrating them.
Protests are highly likely to continue until at least the 2025 parliamentary elections, which are expected to take place in Spring. 11 May 2025 has been proposed by the head of the Central Election Commission in Albania, and the ruling Socialist Party has expressed that the date is suitable.
The latest polling data suggests that the Socialist Party will win the election, an eventuality that would likely be conditioned by the division of the opposition parties splitting the vote. If the Socialist Party win the election, it is highly likely that civil unrest will follow. International actors such as the US and the European Union (EU) have urged the opposition to engage in dialogue with the government rather than engage in violent protest, with the violence hampering Albania’s accession to the EU which the Socialist Party hopes to achieve by 2030.
Georgia: Unrest continues through week and intensifies after government suspends EU accession talks
On 25 November, the Georgian parliament in Tbilisi inaugurated its first session since the contested October parliamentary elections. The opening was marked by protests in Tbilisi, with civil unrest ongoing in varying degrees of intensity since the contested election results were announced. Protesters blocked roads near the parliament and Heroes Square but mostly dispersed by the evening.
The following day, 26 November, parliament set the date for the next presidential election, which is now scheduled for 14 December. The ruling party, Georgian Dream, nominated a candidate from the pro-government and anti-West People’s Power party, Mikheil Kavelashvili, to be president.
In a significant development, the government announced on 28 November that they were suspending European Union (EU) accession negotiations until the end of 2028. The announcement followed just hours after the EU’s parliament adopted a non-binding resolution that rejected the results of October elections in Georgia due to “significant irregularities”.
Significant protests quickly erupted in Tbilisi outside the Georgian parliament from the pro-European opposition movement, marked by violent clashes between riot police and demonstrators. Security forces deployed water cannons, reportedly using water mixed with pepper spray, to disperse protesters, and several journalists have reported being injured as a result. Protesters, meanwhile, set up a barricade on Rustaveli Avenue and set it alight. The authorities claim that at least 43 arrests were made, and 32 officers were injured.
Solace Global Assessment:
Firstly, it is highly likely that the Georgian Dream nominated candidate Kavelashvili will win the presidential election. A former footballer who played for the British football team Manchester City, Kavelashvili was one of the founders of the People’s Power party, which split from Georgian Dream in 2022. People’s Power is even more openly anti-West and pro-Russian than Georgian Dream, though still supports the Georgian Dream government, and proposed the controversial “foreign agents” bill that led to significant civil unrest in March 2023 and April-June 2024.
The presidential election will be the first conducted using an indirect vote system via a 300-member College of Electors, instead of a direct popular vote, following a 2017 constitutional change. Georgian Dream is projected to easily win as they have a majority in the electoral college, with at least 156 electors (89 from parliament, 54 from local representatives, and 13 from Adjara) either Georgian Dream or People’s Power members.
While the presidency in Georgia is a primarily ceremonial role, the head of state and commander-in-chief, the position has been used by the pro-European incumbent Salome Zourabichvili as a platform to effectively lead the opposition. It is highly likely that Zourabichvili’s ousting will further diminish the strength of the opposition, and the presidential election will likely be a trigger for further political instability and civil unrest.
The suspension of EU accession talks will almost certainly continue to act as a significant trigger for the intensification of civil unrest. Prospective membership of the EU is a central pillar of the pro-European opposition movement. While Georgian Dream has previously made efforts to present an ostensive willingness to progress EU accession, this development is almost certainly indicative of both increased establishment hostility to the EU due to its reaction to the contested election result, and Georgian Dream using its newfound position of strength to pursue an even more overtly anti-West and pro-Russian agenda.
It is highly likely that this will lead to continuing and intensified protests over the coming weeks, which will likely be marked by increased levels of violent clashes between protesters and riot police.
Syria: HTS launch offensive in Aleppo Governorate in largest escalation in civil war in four years
On 27 November, the Salafi-jihadist Syrian rebel group Hayy’at Tahrir al-Sham (HTS)launched a major offensive against Syrian Arab Army (SAA) regime forces in the Aleppo Governorate in northern Syria. At least 200 people have died so far during the offensive. The surprise assault led by HTS, highly likely in collaboration with other Syrian opposition forces, seized several settlements in the countryside west and southwest of Aleppo City and has rapidly reached the outskirts of the city.
A local journalist has claimed that opposition officials informed them that the recapturing of Aleppo is one of the goals of the offensive. The offensive has cut off the Damascus-Aleppo international M5 highway. After 30+ hours of non-stop combat, HTS advances captured at least 37 villages west of Aleppo.
As of 29 November, combat is reportedly ongoing in close proximity to the New Aleppo area of Aleppo, which is indicative of the threat posed to the regime-controlled city by the offensive. Other rebel factions, including Turkish-backed militias, have allegedly joined the offensive. The Russian air force conducted numerous airstrikes, reportedly resulting in civilian casualties, and additionally allegedly struck a Turkish-backed Syrian National Army (SNA) headquarters, highly likely to deter SNA involvement in the offensive.
However, early reports suggest that a limited number of rebel forces affiliated with the SNA have already participated in the offensive. HTS fighters made unverified claims to have eliminated Russian drone teams during the advance. The SAA has reportedly mobilised security forces following the implementation of an emergency law, and is almost certainly urgently redeploying forces from across regime-controlled Syria.
Solace Global Assessment:
This is the most significant escalation in the Syrian Civil War since 2020. HTS as an organisation evolved from the defunct Syrian al-Qaeda-affiliated Jabhat al-Nusra. While nonetheless maintaining a Salafi-jihadist ideology, however, HTS is almost certainly not affiliated with al-Qaeda and has engaged in significant conflict with the pro-al-Qaeda al-Nusra successor group Tanzim Hurras al-Din.
The HTS offensive has so far been highly successful, which has almost certainly been largely achieved through the element of surprise. As an example, HTS reportedly captured Khan al-Assal on the outskirts of Aleppo in just a few hours, whereas rebel forces took weeks to capture the district during intense fighting in 2013. Since the Syrian Civil War drastically reduced in intensity in 2020, HTS has gradually become the most militarily capable rebel group in northwest Syria, solidifying its presence in Idlib and enhancing its arsenals with new offensive and reconnaissance capabilities such as one-way attack uncrewed aerial vehicles (OWA-UAVS) and first-person view (FPV) UAVs.
Counter to the assessment that the HTS offensive could highly likely threaten the regime’s control of Aleppo, historical rebel offensives in northwest Syria generally followed the trend of rebels quickly penetrating SAA positions manned largely by conscripts in the initial stages, before Damascus stabilised and reversed the situation by deploying more capable units. While this may still happen, the capture of key urban positions and advantageous elevated terrain in the outskirts of Aleppo increases the likelihood that HTS will be able to maintain their newly acquired ground against SAA counteroffensives.
Turkish security sources claim that the purpose of the “limited offensive” is to prevent Russia-backed regime attacks against civilians in Idlib and to restore the “boundaries of the Idlib de-escalation zone” which was initially agreed in 2019 by Russia, Turkey and Iran. It is likely, however, that the considerable gains made may embolden HTS forces to advance further into Aleppo City, if they are not halted by SAA counteroffensives.
It is likely that a factor in the HTS leadership’s decision-making is the calculation that Russian support for the Assad regime will be more limited due to a reallocation of resources to Ukraine. However, Russian air superiority will still pose a considerable challenge to overcome, despite early indications that HTS militants have captured man-portable air defence systems (MANPADS) from the SAA. The offensive will highly likely lead to continued intense combat over the coming weeks.
Israel and Lebanon: Israeli government and Hezbollah agree to ceasefire deal
The agreement, signed by the governments of Lebanon and Israel, came into effect at 04:00 local time on 27 November. The deal’s key points include:
1) The withdrawal of Hezbollah to the north of the Litani river and the dismantling of military infrastructure south of the Litani.
2) The phased withdrawal of Israeli troops from Lebanese territory over a period of 60 days (25 January 2025).
3) The increased deployment of Lebanese Armed Forces (LAF) units south of Litani to enforce the ceasefire.
4) The affirmation of Israel’s right of self-defence, essentially allowing Tel Aviv to retaliate if Hezbollah violates the ceasefire terms.
Notably, the deal contains no mention of Gaza.
Solace Global Assessment:
The ceasefire almost certainly represents a strategic victory for Tel Aviv, which has achieved most of its stated objectives in Lebanon without having to compromise on its parallel efforts in Gaza.
Since the intensification of its conflict with Hezbollah in September, Israeli forces have effectively decapitated the organisation by killing most of its senior leadership, destroyed a considerable portion of its missile and rocket stocks, and have thus decreased its value as a proxy deterrent for Iran, which is likely why Tehran assented to the deal.
Importantly, the ground operation in Lebanon did not result in a protracted and costly deployment of the Israel Defence Forces (IDF).
The ceasefire deal reaffirms Israeli aims to push Hezbollah back to the Litani River and effectively grants Tel Aviv an “open door” to return to Lebanon should Hezbollah fail to comply with the terms. Most importantly, the deal allows Tel Aviv to continue its operations in Gaza, while reducing the likelihood and practicality of further involvement by Iran and Hezbollah in support of Hamas.
Notably, the deal shifts significant responsibility on the LAF, which represents an important source of political leverage for Tel Aviv and its allies. However, the LAF faces significant challenges in exerting control over Hezbollah, a powerful political force in Beirut. Increased LAF involvement south of the Litani River is likely to escalate tensions between Hezbollah and other Lebanese political factions, potentially deepening divisions within the country’s fragile political landscape.
For Hezbollah, whose officials have nevertheless declared the ceasefire deal as a “victory”, the deal is both a political and strategic defeat. By accepting a deal that does not include Gaza, Hezbollah has de facto reneged on its stated political aim for its involvement in the conflict, which may compromise its standing at home among its key constituencies.
Moreover, the agreement to a phased Israeli withdrawal and a monitored intervention of the LAF will likely result in Hezbollah’s loss of multiple pre-prepared positions south of the Litani, whose reconstruction will necessitate considerable time and resources. Finally, Iran’s support for the deal likely restricts Hezbollah’s ability to re-engage in the conflict in the short term and will likely frustrate Hezbollah’s ability to replenish its weapon stocks.
The deal may result in a shift in Iran’s approach to supporting the Palestinian militias. The deal is likely to lead to a short-term escalation in Tehran’s attempts to make the West Bank a more important front in the conflict. Notably, on 27 November, Israeli forces seized a shipment of weapons in Jenin, including heavier weapon systems that are seldom used by West Bank militias like mortars and rockets. Iran’s strategy is likely to overstretch the IDF and isolate Israel on the international stage by forcing it to increase military operations in the West Bank.
Chad: Military cooperation with France ends
On 28 November, the government of the Republic of Chad announced that it would be terminating its military cooperation with France, citing concerns about its sovereignty. Chad’s Ministry of Foreign Affairs stated that the decision to terminate the deal will enable the government to redefine its strategic partnerships. France currently has approximately 1,000 soldiers and several warplanes in Chad, its last military foothold in the wider Sahel region.
Solace Global Assessment:
After the military coup in 2021, Chad was the only military government that remained open to the staging of Western forces within its borders. The sudden change in strategy has likely been greatly influenced by public opinion that has often translated into anti-French protests.
Many Chadians likely perceive the presence of French forces as undermining their national sovereignty, associating it with neo-colonialism and undue interference in domestic affairs. They have also likely been influenced by Russian information campaigns. Furthermore, despite France’s contributions to counter-terrorism efforts in Chad and the wider region, many likely believe that the presence of Western forces legitimises Chad as a target for extremist groups.
An effective expulsion from Chad would be a major blow to France’s international standing and weaken its position in Africa. French forces have already been expelled from Mali, Burkina Faso and Niger. This has left the western states with almost no military presence in the Sahel, leaving junta governments to deal with a major increase in extremist attacks without access to critical capabilities such as intelligence, fast air and heavy air transport. Violent extremist organisations (VEOs) like Jama’at Nusrat al-Islam wal-Muslimin’ (JNIM) and Islamic State in the Greater Sahara (ISGS) will almost certainly seek to exploit this vacuum.
Western states, on the other hand, are attempting to re-establish a military presence in coastal West African states to contain the violence in the Sahel. However, France’s forced withdrawal is likely indicative of a wider regional shift away from the West and a realignment with Russia. The Senegalese President Bassirou Diomaye Faye has stated that France should close its military bases in the country, likely observing the destabilising effect of foreign forces in the Sahel and also citing concerns over sovereignty.
Chad, as well as potentially some of the West African states, will likely turn to Russia for military assistance. Russian private military companies (PMCs) like the Wagner Group (which has a presence in neighbouring Libya, the Central African Republic and Sudan) offer several advantages. As a PMC, they are not as directly associated with the Russian government and have less of a destabilising effect on the government and their presence is less likely to be viewed as an infringement on national sovereignty. Russia also has no colonial legacy in the region and any agreement will likely be transactional, with security exchanged for access to natural resources.
However, with a track record of human rights abuses, resource exploitation, supporting oppressive regimes and contributing to corruption, a pivot towards Russian PMCs may eventually backfire and play into the hands of the VEOs.
Mozambique: Unrest re-ignites as the government fails to respond to Venâncio Mondlane’s meeting agenda
A planned meeting on 26 November, which was set for the government, led by President Filipe Nyusi, to discuss the post-election crisis with opposition figures, only lasted a few minutes before falling apart. The opposition leader and primary instigator of unrest Venâncio Mondlane, having received no response to his proposed agenda, did not attend. As such, a second meeting will reportedly be scheduled, but no date has been set.
Following the failure of the planned talks, Mondlane called for another three days of protests between 27-29 November. During this wave, multiple instances of violent clashes between protesters and security forces have taken place. Security forces have deployed tear gas and live ammunition to disperse protesters. On 27 November, a woman was run over by an armoured military vehicle and footage of the incident was quickly disseminated across social media.
So far, there have been over 70 deaths since protests began after the FRELIMO party, which has governed for 49 years, claimed victory in the 9 October election.
Solace Global Assessment:
There is growing pressure on the government of Mozambique to re-examine the election results. Mondlane has continued to call for demonstrations and will almost certainly continue to do so until the government grants another meeting and consents to his agenda. The United States, Britain, Canada, Norway, and Switzerland have condemned the government for using excessive force against civilians. In addition, opposition party Podemos demanded the resignation of Nyusi and three other officials.
Economic damages will likely increasingly amplify external pressure on Nyusi. There have been significant disruptions at the Lebombo border crossing, the main border crossing between Mozambique and South Africa. Businesses have been forced to shut across multiple cities as workers are unable to travel to their workplaces and major ports and highways have also repeatedly been interrupted, further exacerbating economic damages. Maputo is a key corridor for supply chains in the region. If surrounding nations start to be significantly damaged economically by the unrest, they will likely add their voices to the growing list pressuring the government.
Nyusi has, so far, withstood pressure to re-examine the election results, utilising security forces to suppress demonstrations. This trend is highly likely to continue; the government has reportedly used plain-clothed National Criminal Investigation Service officers, who are allegedly driving unmarked vehicles and shooting demonstrators.
Since unrest shows little sign of slowing amidst a popular belief that election results were fraudulent, repression of demonstrations remains the primary tool for the government. The Constitutional Council is validating the election results to “establish electoral truth”, which are set to be announced around 23 December.
Nyusi is likely holding out for the Constitutional Council to ratify the election results and contradict popular opinion. Given the perceived corruption of the FRELIMO government, however, this is unlikely to shift public opinion.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
EU Parliament approves second Von der Leyen commission
A total of 370 MEPs voted in favour of the commission, with 282 against, making the vote the one with the smallest majority in EU history. Von der Leyen’s majority is mostly built on the centrists’ and conservatives’ support, and its approval process was fraught by the opposition of large parts of the left.
The new commission is almost certain to continue maintaining previous EU policy commitments in fields such as sustainability and border security, while further emphasising the EU’s ongoing efforts to boost its defence capability vis-à-vis Russia.
Due to the uncertainties regarding the future Trump administration, a key point of focus is likely to be that of trade policy, although here Brussels cannot afford to act proactively, but will have to wait until January.
Austria’s far-right FPO wins elections in Styria
The Freedom Party of Austria (FPO) won an election in the state for the first time in its history, winning 35.3 per cent of the vote, nine points ahead of the conservative Austrian People’s Party (OVP). While unlikely to have an immediate impact at a national level, it may prove politically relevant.
First, the vote demonstrates the FPO’s continuing growth despite its exclusion from the national government after the general elections in late September. Second, Styria may become a testing ground for FPO’s ability to create a coalition. While at a national level the president nominates a party to attempt to form a majority, in Styria that prerogative is automatically afforded to the elections’ winner.
FPO will therefore have the “initiative” to attempt to form a coalition. If this succeeds, it may highlight weaknesses in the “cordon sanitaire” formed by the centrist parties.
Protests in Milan’s outskirts following death of 19-year-old during police chase
The youth reportedly died in the early hours of 24 November during a car chase with local police, the dynamic of which has still not been clearly established. Following the first reports of the incident, demonstrations were organised in the area of Corvetto, located southeast of Milan’s centre. These became violent and continued until 26 November, resulting in multiple arrests and at least four injuries. There is a realistic possibility of further unrest in Milan following developments in the police investigation of the incident.
Slovakia’s Prime Minister to attend WWII Victory Day parade in Moscow
Prime Minister Fico publicly stated that he accepted a Russian invitation to visit Moscow for the event. Fico has maintained warm relations with Moscow despite his country’s membership in the EU and has blocked the country’s aid to Ukraine after assuming office. There is a realistic possibility of protests in Bratislava before 9 May, possibly targeting the airport where Fico may depart to Russia from.
Mali again detains Western mining sector employees
On 27 November, Canadian gold mining company Barrick Gold announced that four of its employees, working at the Loulo-Gounkoto mine, were arrested by security forces under unclear charges. The employees are notably the same who were briefly detained in September.
The case highly likely demonstrates the growing trends of arbitrary detentions of Western employees and executives by the Sahel juntas for coercive purposes. It is likely that the growing frequency of these cases will alter the risk appetite of mining sector actors operating in the area.
Moreover, there is a realistic possibility that the Canadian company’s case will be resolved in a way similar to last week’s deal between the Malian government and Australian company Resolute Mining, where the latter agreed to pay approximately USD 160 million to the former as part of securing the release of detained employees.
Jubaland and Mogadishu issue reciprocal arrest warrants for each regions’ president
On 27 November, A judge in Somalia’s Jubaland region issued an arrest warrant for Somali President Hassan Sheikh Mohamud on several charges including crimes against humanity, orchestrating civil war, weapon trafficking, collaboration with al-Shabaab, abuse of power, and corruption. The warrant enables the arrest of Mohamud anywhere in Somalia. If he is found guilty, these charges would result in a long-term prison sentence or the death penalty.
This comes shortly after a cluster of Somali lawmakers filed a lawsuit against Mohamud over “violations of human rights and due process in the illegal and forced deportation of Somali asylum seekers” at the European Court of Human Rights. In response to the arrest warrant, Mogadishu has issued its own arrest warrant for Jubaland president Ahmed Madobe on charges of treason and revealing classified information to foreign entities. This occurred amidst tensions between Mogadishu and Jubaland; on 25 November, Madobe was re-elected for a third term after Jubaland amended its constitution to remove presidential term limits. Mogadishu has declared these elections illegal since they were held without federal involvement.
Tensions between Mogadishu and Somalia’s regional entities will almost certainly continue as Mogadishu faces challenges from ongoing insurgencies from the Islamic State and al-Shabaab.
Namibian election marred by technical failures and ballot shortages
On 27 November, Namibians headed to the polls to elect the president and members of the National Assembly. The country has been ruled solely by the incumbent South West Africa People’s Organisation or SWAPO party since Namibia gained independence from apartheid South Africa in 1990. Election polls have indicated that SWAPO is in danger of losing power for the first time.
However, the election has been marred by technical failures and ballot shortages, which have resulted in several political parties stating that they will challenge the validity of the election. Results are anticipated to be released by 30 November; however, should SWAPO declare victory after the election’s contentious circumstances, significant unrest could arise, especially among Namibia’s youth, which makes up a significant proportion of the country’s electorate and has expressed increasing dissatisfaction with the ruling party.
On 26 November, the Namibian government issued the satellite internet provider Starlink to cease operations in the country. There is a realistic possibility that this move is aimed at limiting the dissemination of information that could contribute to the spread of election-motivated civil unrest.
Security, Armed Conflict and Terror
NATO warships surround Chinese vessel suspected of sabotage in Danish waters
Several NATO warships have surrounded the vessel, Yi Peng 3 (IMO: 9224984), a Chinese-flagged bulk carrier that is suspected of sabotaging two undersea fibre optic cables in the Baltic. Preliminary investigations allege that the vessel deliberately dragged its anchor for over 100 nautical miles after leaving the Russian port of Ust-Luga on 15 November, with the vessel also failing to transmit its location on its automatic identification system (AIS).
Several Western intelligence sources have indicated that the vessel in question was partially crewed by Russians, and they suspect that Russian intelligence agencies were behind the deliberate underwater sabotage. However, under international maritime law, NATO ships can’t force the vessel to sail to one of its ports and must seek Beijing’s permission before questioning the crew.
EU, UK and Iranian diplomats hold nuclear talks in Switzerland
The meeting will be held on 29 November in Geneva and was described by Iranian officials as the continuation of talks held during the United Nations General Assembly summit in New York. The decision to hold the latest round of talks likely follows last week’s resolution by the International Atomic Energy Agency (IAEA) calling on Iran to cooperate with the UN watchdog. Iran responded to the resolution by claiming to have accelerated its efforts to acquire greater quantities of enriched uranium.
The new Pezeshkian government has declared itself open to resuming nuclear talks with its EU counterparts but likely is aware of how returning to a pre-2018 framework will be difficult during a second Trump term. The meetings are likely therefore aimed at assessing Brussels and London’s positions and willingness to pursue some form of détente independently from Washington.
Gunman killed during attack on security outside Israeli embassy in Jordan
The attack occurred in the Rabiah neighbourhood of Amman on 24 November and resulted in three security guards being wounded. While the exact motive of the attack was not disclosed, it is highly likely that it is related to the ongoing war in Gaza. Multiple pro-Palestine protests have occurred in the vicinity of the Israeli embassy. There is a realistic possibility that the lack of a ceasefire in Gaza will result in further unrest in Jordan, where almost half the population have Palestinian lineage.
Islamic State (IS) network dismantled in Cote d’Ivoire and Madagascar
Reports of multiple arrests of Syrian and Iraqi citizens, which took place in July, were released by French media. The arrests were carried out via a US-French joint intelligence operation and were aimed at preventing extremist plans to carry out attacks during the Paris Olympics.
While the presence of IS in coastal West African states is well-attested, Madagascar is increasingly used by IS affiliates to evade detection and as a logistics hub for the rerouting of funds to other branches of the organisation. In West Africa, IS has sought to smuggle sympathisers and militants through irregular migration routes to Europe via the Canary Islands.
The fact that the detained individuals were Syrians and Iraqis underscores how the group’s centre of gravity remains in the Middle East and may be indicative of an attempt to revive IS external operations.
Environment, Health and Miscellaneous
At least five dead in the United Kingdom due to heavy floods and landslides
Storm Bert caused heavy rains, winds of up to 125 kph, and landslides across west and southwest England and Wales, with multiple traffic disruptions reported including at London airports like Gatwick and Stansted, with more than 400 flights being cancelled or diverted. The storm also caused significant infrastructural damage and damage to properties, with more than 500 properties reported as having been flooded. As of 29 November, delays and disruptions in transport, especially affecting the rail network in south England, continue to be recorded and will likely remain in place during the weekend.
Nationwide mobile service outage across Denmark
On 28 November, Denmark experienced a major nationwide mobile service outage that disrupted the services of its largest network provider, TDC. The outage caused significant disruptions, particularly affecting rail services and police communications. Rail services were halted due to the impact on the digital signal system, while police departments across the country struggled with downed phone lines, leading to the deployment of additional patrols to ensure public safety. TDC later confirmed that the issue was technical in nature and assured that it was not caused by any malicious forces.
Landslides and flooding in eastern Uganda
Heavy rainfall in Eastern Uganda has led to damaging landslides and floods, particularly affecting the Bulambuli district. At least 15 bodies have been recovered, and 15 injured individuals have been rescued and taken to medical centres following a landslide that buried more than 40 homes in the Buluganya region. Over 100 people remain missing. Furthermore, the River Nabuyonga has overflowed, causing significant flooding in Mbale and the surrounding area. Rescue efforts by the Red Cross and local authorities are ongoing; the Ugandan army reported one fatality during rescue efforts. The eastern regions of Uganda face heavy seasonal rainfall, which, along with poor drainage and low-lying terrain, leads to occasional flooding and landslides. The situation is worsened by extensive deforestation and rapid urban development, resulting in inadequate drainage and poor infrastructure for managing rainwater.
Asia–Pacific
Pakistan: Almost 1,000 pro-Imran Khan protesters arrested during unrest in Islamabad
This week, a planned demonstration by Imran Khan’s Pakistan Tehreek-e-Insaf (PTI) party in Islamabad turned violent as protesters clashed with security forces. The PTI urged supporters to march from nearby regions to the capital on 24 November. In response, the government enforced Section 144 of the Code of Criminal Procedure, prohibiting protests from November 23 to 25. As a further measure to dissuade demonstrators from marching to Islamabad, security forces (including paramilitary forces) set up barricades on major routes into the capital and cut off internet access.
Despite government measures, tens of thousands of PTI supporters gathered in Islamabad. As protests escalated on 26 November, the military was called in and security forces resorted to using live ammunition, tear gas, and mass arrests to disperse protesters. 954 protesters were arrested, 210 vehicles and weapons were seized, and PTI leaders claim that several protesters were killed, the numbers ranging from 10 to 200, though this is disputed by the government.
On 27 November, authorities successfully dispersed protesters and cleared roads and barricades as the PTI called for a temporary suspension of the protests. The same day, a senior official declared that “the operation has been successfully concluded and normalcy is being restored”. Motorways have resumed operations and business activities have restarted. In the wake of the unrest, the government has issued a series of charges, one related to “terrorism”, against Khan, his wife, Bushra Bibi, and hundreds of PTI supporters for inciting violence this week.
Solace Global Assessment:
Protests were called by Khan to denounce judicial reforms by the government, unjust arrests, as well as a “stolen mandate”. Protesters also demanded the release of Khan, who is currently in jail after being arrested under anti-terrorism laws shortly after being granted bail.
Pakistan has seen significant unrest driven by Khan’s PTI party. In May 2023, Khan’s arrest led to widespread unrest in Islamabad, Karachi, Lahore, and Peshawar as supporters clashed with security forces. Demonstrations led to eight deaths as protesters lit fires, threw stones, and blocked highways.
The government has since been wary of any protests planned by the PTI. Since passing Section 144 into law, the government has the power to ban protest activity and has primarily utilised it to prevent PTI from proceeding with planned protests.
Given Khan’s continued imprisonment and the government’s repressive response, the PTI will almost certainly call another mass protest. PTI leader Ali Amin Gandapur has emphasised that protests will continue until Khan calls an end to them.
The government is highly likely to continue to impose Section 144 to try to prevent future demonstrations, particularly given the scale of the unrest of this week’s protest. Given that the government’s pre-emptive measures did little to deter PTI supporters, future protests are likely to face a severe crackdown.
This likelihood is further increased by the fact that the repressive actions taken by security forces during this week’s protests successfully compelled the PTI to halt their demonstrations. The government will almost certainly continue to use the legal system to punish demonstrators who fail to abide by protest bans to dissuade leaders from organising demonstrations.
There is a realistic possibility that the government will expand its legal powers even further to stop further disruptive unrest from occurring.
India and Sri Lanka: Tropical cyclone approaches southeast India after affecting Sri Lanka as a tropical depression
Tropical depression Fengal moved past Sri Lanka on 26 and 27 November, causing heavy rainfall and flooding. The death toll has risen to at least 12 people, with 17 others injured. Additionally, one person remains missing, and search efforts are ongoing for at least two students after a tractor was swept away by floodwaters in Karaitivu; four bodies have been recovered so far.
Many residents have been evacuated in vulnerable areas due to landslide risks, particularly in Kandy, Matale, and Nuwara-Eliya districts. The Sri Lankan Disaster Management Center has reported that more than 230,700 people have been affected across 17 districts, with substantial damage to infrastructure, including a bridge collapse in Ampara and road blockages due to fallen trees.
Solace Global Assessment:
The tropical depression has now intensified into a tropical cyclone, as confirmed by the Indian Meteorological Department. Initially forming over the Bay of Bengal, the system has been moving north-north-westwards and is expected to make landfall on the north Tamil Nadu-Puducherry coast by 30 November with sustained windspeeds of approximately 50-60 kph. As of 29 November, the cyclone is currently positioned approximately 250 miles southeast of Chennai, Tamil Nadu.
In India, the meteorological department has forecasted heavy rainfall for coastal Tamil Nadu and Puducherry, urging residents to prepare for the cyclone’s impact. The Regional Meteorological Centre has issued a Red Alert, indicating conditions that pose a significant threat to life and property, for the Tamil Nadu districts of Chengalpattu, Villuppuram, Cuddalore, Mayiladuthurai, and Nagapattinam and the town of Puducherry and municipality of Karaikal in Union Territory of Puducherry. Educational institutions in Puducherry and Karaikal have been closed as a precautionary measure.
The Indian Navy has activated a disaster response plan, stationing teams equipped with relief supplies in vulnerable areas in anticipation of flooding and damages. Significant transportation disruptions are highly likely due to flooding and debris blocking roads and railways. Authorities may issue evacuation warnings with little notice. Although the storm is expected to weaken as it moves inland, it will likely still bring heavy rainfall to regions such as Kerala, Mahe, and Karnataka.
Cyclones in the Bay of Bengal have increased in intensity in recent years, something which can largely be attributed to climate change. According to many experts, four main factors are linked to this phenomenon: rising ocean temperatures energise storms; warmer air retains more moisture, leading to heavier rainfall; rising sea levels exacerbate flooding; and changing atmospheric circulation patterns have shifted cyclone pathways. These have all allegedly contributed to more intense and damaging tropical cyclones.
The last tropical cyclone to affect Tamil Nadu was Cyclone Michaung in December 2023. The cyclone caused significant heavy rainfall in Chennai and other regions nearby, causing widespread disruption, property damage, and flooding. It resulted in 17 fatalities and the displacement of thousands of residents. The Tamil Nadu government offered financial relief to families affected by the storm. It is highly likely that Tropical Cyclone Fengal will result in similar effects.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Religious clashes over detained Hindu leader in Bangladesh
On 26 November, protests occurred in Chattogram after a Hindu leader, Krishna Das Prabhu, was detained over charges of sedition. Supporters of the detainee clashed with local officials and Muslim residents, resulting in at least one death and dozens of arrests. Local lawyers have pledged to boycott the courts, while Prabhu’s followers have denied responsibility for the killing. There is a realistic possibility that the case will result in cases of sectarian violence in Bangladesh, and possibly India, as tensions between Hindu and Muslim communities in the region remains high after the ousting of Prime Minister Sheikh Hasina.
President of Taiwan set to visit Pacific Allies
Taiwan’s President Lai was set to conduct diplomatic visits to its Pacific allies of the Marshall Islands, Tuvalu and Palau from 3-6 December. Taiwanese diplomatic visits often include unannounced stop-overs to the US, its primary diplomatic and military ally, with visits to Hawaii and the US territory of Guam being announced last minute. The visits will likely provoke Beijing and as evidenced by historical examples, are likely to result in the staging of Chinese military exercises around Taiwan.
Security, Armed Conflict and Terror
China and Philippines tensions escalate as maritime militia amass in disputed waters
Satellite derived imagery has indicated that China is amassing vessels near Thitu Island in the South China Sea, a key Philippine outpost. The vessels are primarily Chinese fishing vessels, which belong to Beijing’s People’s Armed Force Maritime Militia (PAFMM), a fleet of repurposed fishing vessels, often with reinforced hulls and retrofitted intelligence, surveillance and reconnaissance (ISR) equipment. The role of the PAFMM is likely to provide China with enhanced situational awareness in the contested area, especially as the US becomes more involved in backing Manila’s claims.
China investigates top military leaders
Beijing has suspended and placed under investigation Defence Minister Dong Jun and Admiral Miao Hua, a high-ranking member of the Central Military Command (CMC), which is the highest military leadership institution in the country and is directly chaired by Xi Jinping. Both individuals are being investigated for “violations of discipline”, which is used by Beijing as a euphemism for corruption. The actions likely follow previous efforts by Xi to root out corruption from the Chinese armed forces, which have coincided with the removal of other high-ranking officials.
China warns New Zealand of negative consequences if country joins AUKUS
The government of New Zealand is considering adhering to Pillar II of the organisation, which also includes the US, Australia, and Britain, which entails the delivery of advanced capabilities and technology and increasing interoperability between members’ combat forces. The acceleration of the effort to enter into AUKUS was heralded by New Zealand’s new coalition government after October 2023, which has characterised the Indo-Pacific as a “deteriorating” environment, echoing Canberra and Washington.
China’s response is almost certainly a reflection of Beijing’s worry about the AUKUS framework serving as a tool for the US and key allies to evade Nuclear Non-Proliferation Treaty directives, and to increase US power projection in the southwest Pacific, a trend that will help arrest China’s ambitions of becoming an expeditionary naval force.
Environment, Health and Miscellaneous
More than 240,000 families displaced due to extreme weather in Thailand
The Meteorological Department of Thailand (TMD) has issued a series of warnings covering ten provinces due to expected heavy monsoon rains. Southern regions, including the popular tourist areas of Chumphon, Surat Thani, and Nakhon Si Thammarat, are expected to be hit hardest, with the potential for flash floods and landslides.
Areas of southern Thailand, including parts of Pattani, Narathiwat and Yala provinces in the deep south have already been affected by major flooding, with heavy rain and high winds forecasted to last until 30 November. The Gulf of Thailand is also under advisories for rough seas with waves anticipated to reach two metres.
According to local reports, at least 240,000 families have been displaced across seven provinces in southern Thailand due to the flooding as of 29 November.
Heavy rains trigger deadly landslides in Western Indonesia
At least 27 people have been killed, dozens injured, and several remain missing after heavy rain in Indonesia’s Sumatra Island triggered multiple landslides. The torrential rain has caused widespread disruption in North Sumatra province and delayed voting in regional elections. Rescue teams with heavy machinery have been deployed to the area to clear roads and search for missing people. Authorities have warned that extreme weather, exacerbated by the La Niña phenomenon, is likely to persist into 2024 and will remain a major hazard in mountainous and flood-prone areas.
At least five dead in South Korea due to heavy snow
Since 28 November, extremely heavy snowfall has affected much of South Korea’s territory, with local media reporting that the phenomenon is the “heaviest in 100 years”. Parts of Seoul have received approximately 40 cm of snow according to local reports as of 29 November.
The heavy snowfall has resulted in disruptions to the power grid and the cancellation of hundreds of domestic and international flights. Heavy snow was also recorded in North Korea. Disruptions to the power grid are likely to have spillover health effects, for instance preventing residents from adequately heating their homes. While snowfall is common across much of South Korea’s territory, the months that are usually most affected are December, January, and February.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence

Executive Summary
- There is a realistic possibility that the consecutive severing of undersea internet cables in the Baltic Sea is indicative of Russian sabotage.
- There is a realistic possibility that the current French government is heading towards a political crisis in late December or January, as multiple factors threaten its stability.
- It is likely that anti-government protests will continue into at least the next few weeks in Georgia, although the opposition will likely struggle to overturn the October election results.
- In Pakistan, if Imran Khan’s call to protest is heeded by his supporters, incidents of violent civil unrest are highly likely.



AMER
Haiti: Humanitarian flights limited in response to gang violence
Colombia: FARC dissident group splinters, rejecting ceasefire
EMEA
The Baltic Sea: Damage internet cables indicative of increased Russian sabotage
France: Budget stalemate and RN trial push government closer to crisis
Georgia: Anti-government protests intensify
Nigeria: Boko Haram conducts two major attacks on military on consecutive days
APAC
Pakistan: Major nationwide protest scheduled for 24 November
China: Increase in “random” attacks on civilians
North, Central and South America
Haiti: Humanitarian flights limited in response to targeting of aeroplanes
In response to the deliberate targeting of aircraft with small arms fire by Haitian gangs, the US Federal Aviation Administration (FAA) banned all flights to the Caribbean nation on 12 November. On 20 November, the ban was amended, allowing flights to resume to the northern part of Haiti but with flights to Port-au-Prince banned until 12 December 2024. The UN Humanitarian Air Service (UNHAS) also resumed flights to northern Haiti on 20 November, focusing on areas outside the capital to continue supporting humanitarian efforts.
Solace Global Assessment:
The ongoing targeting of planes with gunfire highlights the failure of Haiti’s internal security forces to effectively combat gang activity. Despite the critical need for security around Toussaint Louverture International Airport, authorities have not implemented a basic security cordon of only a few hundred metres to prevent small arms fire from reaching aircraft.
The partial suspension of flights will almost certainly lead to a deterioration of the humanitarian situation and will play into the hands of the gangs, who are increasingly controlling the limited resources that are in high demand by the wider population. Despite the resumption of flights to northern Haiti, it is unlikely that aid agencies will be able to provide adequate aid to the capital area, where approximately 30 per cent of Haitians live. The gangs have established roadblocks and control many of the key access points.
The humanitarian situation has been further compounded by the suspension of operations from Doctors Without Borders (MSF), who have ceased operations in Port-au-Prince and its surrounding areas in response to increasing gang violence and threats made by the Haitian police. MSF is one of the largest providers of healthcare in Haiti after increasing its presence after the 2010 earthquake. The cessation of MSF operations will have a major effect on the provision of healthcare in the capital region, with less than a quarter of medical facilities remaining operational.
These attacks are likely part of a wider gang strategy to curtail foreign influence and help gangs extend control in the capital region. On 20 November, the UN Security Council largely supported the conversion of the Multinational Security Support (MSS) mission in Haiti into a formal peacekeeping operation, despite opposition from China and Russia. This shift in approach likely reflects growing international recognition of the need for a more structured peacekeeping presence in Haiti and acknowledgement that the Kenyan-led task force has failed to address the security concerns.
Colombia: FARC dissidents split amid government ceasefire negotiations
On 20 November, one of the largest dissident groups of the Revolutionary Armed Forces of Colombia (FARC), the Segunda Marquetalia, announced that it was splitting in response to internal division. The split comes at a time when elements of Segunda Marquetalia are engaging in ceasefire talks with the Colombian government, headed by President Gustavo Petro. However, Segunda Marquetalia’s parent faction has stated that it will remain committed to peace talks but admitted that there had been a “clear breakdown in unity” within the group.
Solace Global Assessment:
The Segunda Marquetalia was formed in 2019 by former FARC members who accused the Colombia government of failing to comply with the 2016 peace agreement, citing insufficient protection for former guerillas and sustained violence against leaders and ex-combatants. The group’s split likely indicates that elements are still committed to the revolutionary cause and remain hostile to the government.
However, the Segunda Marquetalia has become entrenched in both illegal mining and the trafficking of narcotics in its stronghold in the mountainous jungle terrain of northeastern Colombia. Tactics employed by the group include armed attacks, assassinations, extortion, hostage takings and attacks on critical infrastructure.
The fracture of the group could have significant consequences for the security in northeastern Colombia. Internal divisions may escalate violence, with competing factions attempting to exert control over narcotic routes and illegal mining operations. This could also result in increased attacks, particularly as the absence of the former leadership’s control may remove prior constraints. Additionally, the smaller faction of the group may seek to strengthen its relationships with other militant groups, organised crime networks and even the Venezuelan government to help sustain their operations.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
Western far-right groups meet in Tennessee for 2024 American Renaissance Conference
The meeting is held every two years and is sponsored by US-based white supremacist political figures and think tanks. While normally mostly aimed at coordinating and favouring networking between US-based far-right groups, this year the conference will be attended by key figures in the European identitarian movement, including the Italian neofascist “Casapound” and the Austrian chapter of the pan-European “Generation Identity”.
Argentina orders arrest of Brazilian participants in 2023 Brasilia insurrection
In January 2023, supporters of former Brazilian President Jair Bolsonaro stormed various government buildings in the centre of Brasilia with the aim of toppling the government. In the failed insurrection’s aftermath, dozens of participants escaped to Argentina to avoid imprisonment. As not complying with Brazil’s extradition requests would put further outside pressure on Milei’s position for likely minimal political gain, Buenos Aires is likely to continue efforts to arrest the rioters.
Security, Armed Conflict and Terror
FBI arrests man for allegedly planning bombing of New York stock exchange
The arrest occurred on 20 November in Florida. According to available information, the suspect allegedly sought to carry out the attack during the Thanksgiving celebrations, thus seeking to maximise casualties while also targeting a highly visible location. The suspect, moreover, was allegedly a supporter and possibly member of far-right, anti-government militant groups operating in the US, and intended the attack to result in the collapse of the US government.
Brazilian authorities uncover previous plot to assassinate President Lula
Brazilian police have uncovered a past military plot designed to kill President Lula before his 2023 inauguration. The 2022 coup plot allegedly planned to use explosives or poison to kill Lula and other political figures before the appointment of retired generals to leadership roles, with most implicated individuals either being current or former members of the military.
Investigators have also suggested that former President Bolsonaro was implicated in the plot. Such an accusation will almost certainly increase political tension in Brazil and will likely scuttle Bolsonaro’s attempt at a comeback, especially as the public discovery of the plot follows from a failed bomb attack on Brazil’s Supreme Court which has been linked to far-right extremism.
Environment, Health and Miscellaneous
Ecuador declares state of emergency in response to wildfires
Authorities in Ecuador have declared a 60-day state of emergency due to widespread forest fires that have been exacerbated by a three-month drought. Thirteen active wildfires and nine controlled ones have been reported, with the provinces of Azuay and Loja being the hardest hit. The local rugged terrain has complicated relief efforts, denying ground access to firefighters who, however, cannot be replaced via air due to the lack of aircraft suitable for firefighting.
Europe, Middle East & Africa
The Baltic Sea: Two undersea fibre optic cables damaged in close succession
On 17 November, the Lithuania-Sweden undersea fibre optic internet cable was damaged at approximately 10:00 local time. On the following day, the C-Lion1 Cable, which runs from Helsinki, Finland, to Rostock, Germany, was also damaged at approximately 04:00 local time near the Swedish island of Öland.
In response, Finland and Sweden have planned to set up a joint team to investigate the incidents as potential sabotage. The German Defence Minister, Boris Pistorius, has stated that the incidents were “hybrid” action and that it must be assumed that this was an example of sabotage, dismissing the possibility of legitimate anchor snags but without presenting any credible evidence.
Solace Global Assessment:
The areas in which the two cables were damaged are both within major shipping lanes and the Baltic Sea is an area of dense fishing activity, increasing the likelihood of accidental damage from anchors or fishing equipment responsible for most subsea cable incidents. Moreover, the Baltic Sea is an incredibly shallow body of water, with average depths of approximately 55 metres, suggesting that it could be accidental damage caused by a ship not used to operating there.
However, damage to two separate undersea cables in close succession is highly suspicious and there is a realistic possibility that these incidents were acts of deliberate sabotage. Both locations are near Kaliningrad, home to much of Russia’s Baltic Fleet and where many Russian survey ships operate from, which have a history of surveying sensitive areas of the Baltic. However, these ships are extensively monitored by NATO military assets.
If Russia were responsible, it is more likely that Russian intelligence services like the Main Intelligence Directorate (GRU) would have repurposed a civilian ship to drag its anchor over the cables. Speculation suggests that a Chinese ship, captained by a Russian, may have been involved, and the Danish Navy has seized the vessel.
This tactic would be highly deniable and if the vessel had its automatic identification system (AIS) turned off, it is unlikely that NATO can effectively monitor all Russian-linked civilian flagged vessels. An act of state-sponsored undersea sabotage by Russia would fit within the wider picture of Russian sabotage across Europe.
Russia has created a gig economy for disaffected Europeans to conduct low-level sabotage in exchange for remuneration, resulting in damage to warehouses, factories and transport infrastructure linked to the facilitation of lethal aid to Ukraine. There is a realistic possibility that Russia has migrated these tactics to the maritime domain as part of an expansion of its sabotage campaign.
Russia may be attempting to send a strategic message to Europe aimed at deterring it from supporting Ukraine. With the Trump administration likely to suspend aid to Ukraine, Europe will be forced to assume greater responsibility, indicating that the scale and frequency of Russian sabotage in Europe is likely to increase.
France: Le Pen trial and 2025 budget near end, increasing the risk of a political crisis
The end of the embezzlement trial involving multiple National Rally (RN) members, including the party’s leader Marine Le Pen, is scheduled to end next week. The trial’s verdict, which could bar Le Pen from running in the 2027 presidential election if she is found guilty, is due to be issued in early 2025.
Also next week, the contentious 2025 budget of Prime Minister Michel Barnier heads to the Senate after a revised version of it, proposed by the populist left-wing France Unbowed (LFI) party was rejected at the National Assembly. Barnier’s budget seeks to cut the state’s deficit from six to five per cent in 2025 and involves a series of tax hikes and spending cuts, which are opposed by the left.
While RN has de facto supported Barnier’s precarious minority government (which was formed after the latest, inconclusive National Assembly elections this summer) by refusing to support a motion of no confidence in October, its leaders have repeatedly indicated that they are displeased with the proposed budget.
Solace Global Assessment:
Currently, the next “steps” in an increasingly likely French political crisis have a somewhat clear timeline. After being debated by the Senate, which will introduce further changes to the bill, the budget will then be subject to a vote by lawmakers from both houses on 12 December.
If it fails to pass this vote, then Barnier is highly likely to use Article 49.3 to bypass the legislative branch and force the bill through. If this takes place, a no-confidence motion will almost certainly follow. Here, the centre would highly likely support Barnier whereas the left-wing coalition, the New Popular Front (NFP), will almost certainly back the motion as it did in October, leaving the RN to again play a kingmaking role.
If, however, RN votes against Barnier, and the government collapses, this will not constitutionally be followed by new National Assembly elections, due to constitutional constraints that elections must be separated by at least 12 months.
After Barnier, therefore, President Macron would almost certainly have to opt to nominate a caretaker government. Moreover, following the failure of the 2025 budget to pass, the 2024 one would be reinstated as per the constitution. However, the 2024 budget is already far outside of EU regulations.
The resulting situation is one in which the ruling centre and Macron would have little political power and the parliament would be “stuck” with a budget that both the left and the right (and Brussels) strongly oppose.
In such a scenario, Macron could either openly oppose his allies in Brussels, thus likely destroying the centrist bloc as a Europhile force in French politics and caving in to either the left or right, likely dooming his coalition to a complete rout at the next presidential elections; resign and cause snap presidential elections; or, more likely that the previous option, attempt to rule by decree until 2027.
This last scenario, however, would almost certainly result in extremely severe civil unrest spearheaded by RN and NFP. Possibly, a worsening position for Macron will give some momentum to LFI’s “nuclear option”: trying to impeach Macron. This, however, would again require an agreement with RN, an unlikely scenario due to the political relevance of the move.
While not directly connected, the Le Pen trial and the ongoing budget debate will likely increase the risk of France collapsing into a more severe political, and possibly fiscal, crisis. RN’s current president (and Le Pen’s de facto deputy and representative at the EU Parliament) Jordan Bardella, has repeatedly hinted at the possibility of collapsing the government if the final budget does not reflect RN’s concerns over areas such as the cost-of-living crisis. The introduction of a judicial threat to RN likely increases the party’s incentives to end its truce with Barnier. However, Le Pen and Bardella could also assess that collapsing the Barnier government could go to the party’s detriment, and shift RN’s moderate supporters towards the politically weaker, but more established Republicans (LR).
Georgia: Protests against contested election results intensify in Tbilisi
Following the 26 October parliamentary elections, which the ruling Georgian Dream party claimed to have won, protests amid allegations of electoral fraud have intensified in Tbilisi.
On 16 November, pro-Europe opposition protesters turned out in the tens of thousands to demonstrate, block major roads in central Tbilisi and clashing with local security forces. The protests continued over the following days, with opposition protesters establishing sit-ins and protest camps around Tbilisi State University.
On 19 November, Georgian police engaged in clearing operations, detaining at least 16 demonstrations and dismantling protest camps. Furthermore, on 19 November, the pro-opposition Georgian President, Salome Zurabishvili, requested that the constitutional court annul the results of the October elections over claims of vote rigging, according to her lawyer.
Solace Global Assessment:
In comparison to the unrest which gripped Georgia during the anti-‘foreign agents’ bill protests in March 2023 and April-June 2024, the protests have so far been less attended and less intense.
However, the trajectory of the levels of unrest has been accelerating since the 26 October elections. In the immediate aftermath of the elections, protests were relatively restrained and peaceful. This past week’s protests mark an escalation in their intensity, with protesters increasingly deploying methods of direct action such as sit-ins and protest camps.
It is likely that hypothetical events such as the arrest of the pro-opposition President Zurabishvili, with former Russian president Dmitry Medvedev having called for her arrest in late October, would lead to further escalation in the levels of unrest. Moreover, it is generally likely that protests will continue into at least the next few weeks.
In terms of the probability that the protest movement will succeed in overturning the election result and/or overthrowing the Georgian Dream government, which they criticise as being pro-Russia, there are key factors which diminish the capability of the opposition movement to challenge the government both politically and in the streets through direct action.
Firstly, the movement is politically highly fragmented, with numerous opposition parties such as United National Movement (UNM), Lelo, For Georgia, Droa and European Georgia each contesting political leadership of the opposition.
Secondly, the opposition protesters have struggled to contest with the Georgian riot police in street battles, evidenced by the relative success of clearing operations on 19 November. In contrast, the November 2013-February 2014 ‘Euromaidan’ protests in Ukraine, which ultimately overthrew the pro-Russian government, were supported by militant far-right groups such as Right Sector which contributed to a paramilitarisation of the protest movement and increased the capability of the anti-government protesters to challenge the Berkut riot police.
In Georgia, while not entirely homogenous, the militant far-right are typically anti-opposition, more sceptical of Western influence and more sympathetic to Russia. The liberal left and centrist base for the opposition movement, meanwhile, is not generally characterised by violent militancy.
Nigeria: Boko Haram conduct two major attacks in two days across Nigeria
On 18 November, a convoy belonging to the Nigeria Security and Civil Defence Corps (NSCDC) was ambushed when patrolling around a National Grid installation in Kaduna State. The ambush was reportedly conducted by the Islamist group Boko Haram and involved 200 insurgents armed with sophisticated weapons from advantageous high ground. The ambush allegedly resulted in the deaths of over 50 Boko Haram militants but seven NSCDC troops were captured by the militants.
The following day, Boko Haram launched another major attack on a Nigerian army camp in Borno State in northeast Nigeria, near their main stronghold in the Lake Chad region. The attack killed several soldiers and four soldiers remain missing.
Solace Global Assessment:
Two major Boko Haram attacks in two days in different parts of Nigeria is likely indicative of how the Islamist group has strengthened as a result of the wider destabilisation of the Sahel region. The rise of extremism in Mali, Burkina Faso and Niger has almost certainly resulted in a proliferation of arms in Nigeria and likely accounts for the group’s use of “sophisticated weaponry”.
Moreover, the Sahel’s destabilisation has likely contributed to the overstretching of Nigerian government forces which have deployed more resources to the border regions, a move that has almost certainly provided domestic militants with more freedom of movement. The scale of the Boko Haram assaults may also indicate that the group has managed to boost its recruitment, improve the coordination of operations and has been emboldened by Nigeria’s decreased internal security.
There is a realistic possibility that these attacks were purposefully timed and coordinated by senior leadership in a move to further overstretch government resources. Such a strategy would complicate commanders’ allocation of resources and limit the government’s ability to conduct major offensives on Boko Haram in its main area of operations. Government efforts will almost certainly be further undermined by the capture of personnel. The abductions were likely intended objectives of the attacks, designed to degrade troop morale, disrupt cohesion and to provide the group with leverage for ransom demands or political concessions.
The targeting of energy infrastructure will likely become a more integral element of the group’s strategy, with power outages serving to undermine the government and deter foreign presence or investment, one of Boko Haram’s primary objectives.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Protests in separatist Abkhazia in Georgia lead to resignation of Abkhazia’s President
The so-called Republic of Abkhazia, a separatist region of Georgia which is de facto independent, had intense protests against the ratification of a Russian investment deal. The breakaway region is highly influenced by Russia and is described by most UN member states as being a Russian-occupied territory. Protesters argue that the proposed investment grnats Russian oligarchs unfettered access to Abkhazia.
On 15 November, protesters stormed the Abkhazian parliament building in Sukhumi and clashed with security forces. Following negotiations between opposition leaders and the Abkhazian government, on 19 November a deal was made for protesters to leave government buildings in return for the resignation of President Aslan Bzhania and new elections, which soon followed.
A member of the so-called Central Election Commission of occupied Abkhazia later stated that elections will be held within three months. It is likely that this development will reduce levels of unrest in Abkhazia.
Iran vows “proportionate” response if Western-backed resolution passes at the IAEA
Iranian Foreign Minister Abbas Araghchi was warned that Iran will be forced to enact a “proportionate” response if a Western-backed resolution is passed at the International Atomic Energy Agency (IAEA), the United Nations nuclear agency. The resolution criticises Iran for its lack of cooperation with the agency and advocates for increased scrutiny and diplomatic consequences.
The move follows the recent sanctioning of Iranian state airliner Iran Air and shipping company Islamic Republic of Iran Shipping Lines (IRISL) for their involvement in the delivery of arms to Russia for use in Ukraine. Hardliners in Iran have called for the closure of the Strait of Hormuz; however, such an action would likely harm Iran’s own interests and almost certainly alienate Tehran from the Gulf nations with which it has recently improved relations.
Senegal’s new government secures parliamentary victory
Legislative elections in Senegal, held on 17 November, have resulted in a significant victory for the ruling Pastef party with a reported 79 per cent of the vote. The opposition has acknowledged the results and conceded defeat, a move which will likely help curb the potential for major unrest, with many of Senegal’s previous elections marred by disruptive protests and political violence.
Australian mining company strikes expensive deal to secure release of CEO and employees in Mali
The employees had been detained over unclear charges of “false evidence” and “misappropriation of public goods”. The “memorandum of understanding” agreed by Resolute Mining and the Mali junta entails an “initial settlement payment” of USD 80 million and an extra USD 80 million in future payments. The case is likely to be influential for Western private actors operating in the Sahel, who face a greatly deteriorated legal environment as part of the Sahel juntas’ increasing transition towards international isolation.
Gabon referendum on new constitution passes in landslide
The “yes” vote, which introduces a new constitution with term limits for the president, won with the support of around 91.8 per cent of the participating electorate. The Gabonese junta, which took power in an August 2023 coup which removed the long-term President Ali Bongo, hailed the result as a positive step towards re-establishing democracy. The success of this process is, however, likely to be a reflection of the junta’s willingness to allow for a retrenchment of the military’s political position.
SADC extends mandate to keep troops in eastern Democratic Republic of the Congo
At a summit on 20 November, the Southern African Development Community (SADC) extended its mandate to keep troops in the Democratic Republic of the Congo (DRC). The mandate, initially implemented on 15 December 2023, consists of roughly 3,000 troops primarily from Tanzania and Malawi and aims to “support the Congolese army in fighting and eradicating the M23 and other armed groups that continue to disrupt peace and security.”
The decision comes as the Kigali-backed M23 rebel movement, the primary rebel group in the region, has made significant territorial gains in North Kivu, which has seen over 7 million people displaced. Despite the Luanda Process aimed at restoring peace between the DRC and Rwanda, violence in North Kivu will almost certainly continue despite the presence of SADC and United Nations peacekeeping forces.
Opposition party wins presidential election in Somaliland
On 19 November, results for Somaliland’s presidential election were published, revealing that opposition leader Abdirahman Mohamed Abdullahi of the Waddani party won 63.9 per cent of the vote. Abdullahi has voiced opposition over the previous government’s deal to lease Ethiopia a section of Somaliland’s coastline to setup a naval base due to its perceived lack of economic benefit. The deal has caused significant complications with Mogadishu, who do not recognise Somaliland as an independent territory. The election comes amidst Somaliland’s push for global recognition, with many expecting President-elect Donald Trump to recognise Somaliland after assuming office. Given the election’s success in demonstrating Somaliland’s commitment to democracy, the election will likely contribute positively towards its international recognition.
Security, Armed Conflict and Terror
16-year-old Chechen arrested for planning attack on synagogue in France.
The target was a place of worship located on the outskirts of Le Mans. It is highly likely that the attack plan was partially influenced by previous attacks on synagogues in France, including an arson attack in August in La Grande-Motte. Moreover, the suspect’s youth further corroborates the trend of increasingly younger “lone wolves” becoming self-radicalised in Europe and North America.
Tunisian coast guard vessel reportedly intentionally rammed and sank migrant boat
According to Italian media, a Tunisian coast guard vessel deliberately rammed into a small vessel on 7 November. The small vessel was carrying approximately 80 people, of which 52 died and the rest were rescued by local fishermen. A similar case, which occurred in 2022, sparked significant condemnation in Tunisia and Italy.
Tunisian President Saied has increasingly sought to establish his administration as a key partner for south European governments, especially Italy, seeking to decrease migrant arrivals to the continent. Saied has managed to ensure an in-flow of approximately EUR 150 million from the EU to fund Tunisian anti-migrant efforts, but NGOs have noted how much of the funding has effectively been redirected towards bolstering Saied’s efforts to suppress dissent at home.
Wagner troops targeted by JNIM in southern Mali
On 21 November, a convoy of Wagner mercenaries and government forces was attacked with firearms and improvised explosive devices (IEDs) in the vicinity of Bankass, near the Mali-Burkina Faso border. According to both Malian and JNIM sources, the ambush resulted in the deaths of at least six Wagner members. The ambush is the latest in a series of setbacks and defeats, as well as episodes of brutal conduct towards civilians, which have increased scrutiny of Wagner’s performance both in the Sahel and Moscow.
Since Prigozhin’s death, Wagner in Africa has been increasingly moved towards a greater government control under the Africa Corps umbrella, a change that Prigozhin’s successors decry. Moscow has leveraged the latest failures by the group to accelerate this process, as a more controllable Wagner likely allows the Russian regime a greater leverage over the juntas.
Burkinabe junta freezes assets of suspected terrorists and imposes six-month travel ban
The 100 people that were targeted include former president Paul-Henri Sandaogo Damiba, as well as former politicians, journalists, military officers and other civilians. The junta justified the move as directly targeting the Islamic State and JNIM. It is, however, more likely that the freezes, which targeted the country’s intelligentsia, are meant to quash possible sources of internal dissent, and may be a reflection of growing instability within the junta. There is a realistic possibility that further measures will be taken against the targets, including imprisonment.
Foreign terrorist fighters flocking to Somalia to join the Islamic State (IS)
A UN report has identified that foreign terrorist fighters are transiting to Somalia’s Puntland region via both land and maritime routes to join the Islamic State’s Somalia Province (ISSP). The report indicates that ISSP has doubled in size to around 600-700 fighters, with foreign militants principally arriving from Syria, Yemen, Ethiopia, Sudan, Morocco, and Tanzania. The influx of fighters have bolstered ISSP’s operational capabilities and has likely put it in a better place to challenge government forces and regional rival, the al-Qaeda-affiliated al-Shabaab.
The affiliate’s strength has also grown as a result of al-Karrar, an IS regional office established in Somalia in 2022, which supports global IS operations. In addition, former leader, Abdul Qadir Mumin, has been elevated to oversee IS affiliates in Africa, indicating that IS senior leadership in the Middle East is likely attempting to expand its influence in Africa and deflect international resources from the Middle East.
Environment, Health and Miscellaneous
Evacuations ordered after seventh eruption of Icelandic volcano
On 20 November, evacuation orders were issued after a volcano on the Reykjanes Peninsula erupted for the seventh time since December. Several homes near the volcano as well as guests at the popular Blue Lagoon spa resort were told to leave the area after lava spurted from a two-mile fissure. However, the eruption was considerably smaller than the most recent one in August and is unlikely to disrupt air travel.
Cholera outbreak suspected of causing mass deaths in al-Hilaliya, Sudan
At least 150 people have died of illness in a few days in the city in eastern al-Jazira state, which has been besieged by the Rapid Support Forces (RSF) for weeks. In early November, the RSF massacred more than 120 people in the town, and, according to the authorities, RSF troops have systematically destroyed civilian infrastructures, further depriving civilians of clean water and medical care. Sudanese activists assessed approximately ten days ago that the siege has already resulted in 450 deaths.
Asia–Pacific
Pakistan: Imran Khan’s PTI organises nationwide protest for 24 November
The Pakistan Tehreek-e-Insaf (PTI) party is set to hold a major nationwide demonstration on 24 November after calls to protest from imprisoned PTI founder, Imran Khan. The party has refused to enter negotiations with the government and has stressed that PTI’s entire leadership will be part of the march which will demand a revocation of the 26th Constitutional Amendment, the restoration of democracy and the constitution, and the release of all political prisoners.
Solace Global Assessment:
Khan has called on workers to join the protest and has warned party members to disassociate themselves from the party if they fail to attend. PTI’s leadership is urging supporters to join large convoys that will travel along major roads, including a primary convoy that will head to the capital Islamabad from Peshawar. PTI has called on its supporters to video record the convoys as they head to Islamabad and other major cities.
Pakistan’s government has prohibited all public gatherings of five or more people, processions, rallies and demonstrations for two months in the federal capital by imposing a Section 144 order for Islamabad, with further Section 144s likely to be issued for other cities. The Minister of the Interior has approved the deployment of the Pakistan Rangers and Frontier Constabulary (FC) to counter potential unrest and violence in the capital.
On 20 November, the Islamabad High Court (IHC) granted bail to Khan for a recent Toshakhana case in what was likely a last-ditch effort to sap the energy from the protests. However, Khan was arrested hours later under anti-terrorism charges, a development that has almost certainly galvanised his base.
Calls from Khan and other party members combined with threats to remove members for not joining will likely guarantee that the protests will attract tens of thousands of participants. The protests are likely to result in significant disruptions throughout Pakistan, and despite warnings not to, protestors will likely attempt to enter Islamabad’s Red Zone. Increased security checks, roadblocks and internet shutdowns are likely to occur. There is a high likelihood of violent interactions between protestors and the security services including the use of tear gas and other forms of crowd dispersal.
2023 protests erupted after Khan’s arrest on corruption charges, which led to incidents of rioting, vandalism and clashes, with at least eight protestors killed, hundreds injured and over 5,000 arrests. There is a realistic possibility that the 24 November protests will eclipse those of 2023 given the government’s sustained crackdown on PTI leaders and supporters and its overseeing of democratic backsliding.
There is a realistic possibility that extremist groups may seek to attack large convoys monitored by the security services, with the filming of the convoys potentially amplifying the visibility and propaganda value of such an attack.
China: Increase in “random” attacks on civilians
On 16 November, eight people were killed and 17 injured in a knife attack at a vocational school in Yixing in China’s Jiangsu province. The suspect allegedly was a student, and the triggering motive for the attack was his failure at recent examinations. On 18 November, a 39-year-old man reportedly deliberately drove an SUV into students and bystanders outside a primary school in Changde, Hunan province. The attack resulted in at least “a dozen” injuries, although officials have not stated whether the incident resulted in any deaths. The two incidents occurred only days after a vehicle attack in Zhuhai, Guangdong, which reportedly killed 35 and injured 45. Moreover, other attacks have occurred in the past months. For example, on the eve of National Day in October, a man carried out a stabbing attack in Shanghai. In May, a knife attack at a hospital in Yunnan province resulted in two deaths and at least 21 injuries. Notably, in June 2024, four US college instructors were stabbed in a public park in the northern province of Jilin.
Solace Global Assessment:
The attacks have some notable commonalities that set them apart from the relatively narrow lens of lone actor terrorism that characterises previous incidents in Europe and North America. In general, Chinese attackers target areas that are high traffic, but not necessarily high visibility. Apart from the national day stabbing, which coincided with a politically relevant date (although it is not clear if this had any relevance for the attacker), all the other attacks were seemingly only carried out by targeting spaces with a high-density of victims, like hospitals or schools.
In all cases, no clear ideology could be identified. While some speculation exists regarding whether the attack on US college instructors had to do with their identity, no decisive information regarding this has been released by media or government channels. None of the attackers, according to available data, made overly political or religious statements, or adopted behaviours similar to those of “Western” lone wolves, such as writing an ideological manifesto, pledging allegiance to a cause or organisation, or carrying symbols associated with a particular ideology.
The only notable commonality is the use of non-sophisticated methods, such as vehicles or bladed weapons, but this almost certainly reflects constraints that are intrinsic to the dynamic of lone-perpetrator attacks.
The paucity of available information is almost certainly a reflection of Chinese media and authorities’ self-censorship concerning similar episodes. However, the lack of a clear ideological motive or affiliation between the various attackers appears likely by factual elements such as the choice of target and lack of overt promotion of symbols. Still, the similarities between the attacks makes a “copycat” element likely, especially due to the high engagement and coverage rates following the attacks in Chinese social and legacy media, which make it likely that attackers had access to previous cases.
The closest parallel to the attacks in China are likely the so-called “mudjima” (“don’t-ask-why”) stabbings recorded in South Korea, which share the same lack of an ideological component, as well as characteristics such as target type and method.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Bangladesh interim government seeks Hasina’s extradition
Interim government leader Muhammad Yunus has called for Hasina to be tried for crimes against humanity. Hasina is currently in India, where she sought refuge after her government was toppled. It is unlikely that the request will be met with a positive response in the short term. While the Indian government may have an interest in surrendering Hasina if Bangladesh’s position stabilises in a way that makes it unavoidable for Delhi to have to coexist with a post-Awami League political system, this scenario currently appears remote.
If Delhi ignores the request or responds negatively, however, there is a likelihood of this resulting in episodes of “bulldozer justice” and mob violence against the Hindu minority in Bangladesh.
Vanuatu changes law to ban same-sex marriages
The Vanuatu parliament has explicitly prohibited same-sex marriage, amending its Marriage Act to prevent the registration of such unions and will revoke the licence of any official performing a same-sex marriage. This decision follows the formation of a committee to draft a national policy banning LGBTQ advocacy, which has reportedly been prompted by concerns from the Council of Traditional Chiefs about the impact of LGBTQ activities on traditional values and Christian beliefs.
Mass protests spearheaded by New Zealand Māori community
On 19 November, more than 40,000 protesters peacefully assembled near the country’s parliament in Wellington to oppose the Treaty Principles Bill, which was introduced to parliament for a preliminary vote on 14 November. The bill was introduced by the libertarian ACT Party and seeks to narrow the interpretation and principles of the Treaty of Waitangi (1840), which is a key founding document for New Zealand that established parameters for the relations between the Māori community and the British crown.
Opponents of the bill argue that it is in violation of the original treaty and would infringe upon Māori indigenous rights. Considering the unpopularity of the bill for both the right and the left, and ACT’s relatively small presence in parliament, the bill is unlikely to pass.
Security, Armed Conflict and Terror
Shia convoy attacked in Pakistan’s restless northwest
On 21 November, an estimated 40-50 Shia Muslims were killed after militants opened fire on vehicles travelling through Pakistan’s northwest Khyber Pakhtunkhwa province, marking one of the deadliest sectarian attacks in years. No group has claimed responsibility for the attack; however, given the location of the attack near the Afghan border, it was likely either Tehreek-e-Taliban Pakistan (TTP) or the Islamic State Khorasan Province (ISKP). Large crowds have amassed in the city of Parachinar to protest the incident and the government’s inability to guarantee the Shia community’s security.
India develops first hypersonic missile capability
India has successfully tested its first domestically produced long-range hypersonic missile, putting it within a small group of nations that have already acquired this capability. The range of the missile is assessed at 1500 kilometres, enabling the Indian military to strike all of Pakistan and much of China and to better evade enemy air defence by manoeuvring mid-flight. The missile has reportedly been designed to carry a multitude of payloads, but India has not declared whether it is nuclear capable- a development that will almost certainly be a major concern to Beijing and Islamabad.
Six tourists die from suspected methanol poisoning in Laos
As of 22 November, six tourists (two Australian, one American, and two Danish nationals) have died after consuming alcohol suspected to have been contaminated with methanol. The poisoning reportedly occurred in the Nana Backpacker Hostel in the backpacker town of Vang Vieng. Methanol, a colorless and odorless alcohol used in cleaning and industrial products, is sometimes illegally substituted for ethanol due to its lower cost. Even 30 millilitres can be lethal, causing symptoms like nausea, vomiting, and heart and respiratory failure.
Multiple governments have issued warnings to tourists in the wake of this incident to be cautious of contaminated alcohol. Laos is currently affected by inflation and low levels of economic growth. Furthermore, because of Laos’s poor infrastructure, safety regulations are often not strictly reinforced. These factors have likely influenced the use of methanol as an alcohol substitute in Vang Vieng, which will likely see reduced tourism levels in the wake of this highly publicised event.
Insurgents launch attacks in southern Thai provinces
On 20 November, insurgents in the restive Thai provinces of Yala and Songkhla launched arson and grenade attacks on construction sites. Suspected Muslim separatists attacked a construction site of a Chinese goddess statue in Thepa district in Songkhla, which is set to be the tallest statue of its type in the world. In Yala province, insurgents conducted at least seven arson attacks on surveillance cameras and utility poles in three distinct districts. These attacks have been conducted in the context of increased militant attacks in southern Thailand and follow a recent warning that extremists would target Israeli tourists at Thailand’s famous full moon parties.
US signs intelligence-sharing deal with the Philippines
In response to increased hostile action by China in the South China Sea, Washington and Manila have signed an intelligence-sharing deal that will permit the exchange of classified information. The move is a further indication of US support for the Philippines and the defence of maritime law in the South Chia Sea as specified by the United Nations Convention on the Law of the Sea (UNCLOS).
The deal will provide the US with more oversight of Chinese naval and coastguard activity in the region and will almost certainly improve the Philippines’ situational awareness if provided access to data captured by US strategic intelligence assets, such as satellites. Moreover, the deal could be expanded to incorporate other South China Sea claimants like Malaysia, a move that could provide the US with an intelligence advantage without having to allocate its own resources to the area.
Environment, Health and Miscellaneous
Air pollution in New Delhi reaches “hazardous” levels
On 18 November, air pollution levels in New Delhi reached 493 in the air quality index (AQI), placing it in the “severe plus” category. This level is more than 30 times higher than the recommended limit set by the World Health Organization (WHO), with some areas of the city reaching pollution levels of over 50 times the recommended limit. In response, India’s government has enforced stage 4 of a graded response action plan (GRAP 4) to combat air pollution in New Delhi, closing schools, staggering office timings, banning non-essential construction, banning non-essential trucks from entering, and deploying water tankers and mechanised sweeping to settle the dust.
India’s heavy dependence on coal for electricity production, along with vehicle emissions and construction fumes, significantly contribute to the pollution problem. Over the weekend, farmers in Uttar Pradesh set fire to their fields, leading to smoke drifting into New Delhi and exacerbating the already high pollution levels. It is estimated that more than 1.6 million deaths in India each year are attributed to diseases caused by pollution. While pollution levels may reduce in the short term as government measures take effect, pollution levels will almost certainly remain high despite government initiatives to clean up pollution.
Copyright © 2024 Solace Global Risk Limited. All rights reserved. No part of this document may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence

Executive Summary
- The recent attacks on inbound flights to Haiti are almost certainly a deliberate strategy by gangs to further discourage international aid to the country and maintain a state of chaos.
- Israeli forces will highly likely continue to expand operations in south Lebanon, while seeking to create a favourable situation to strike a ceasefire agreement with a weakened Hezbollah.
- Further unrest in Mozambique is highly likely, as the country experiences its fourth wave of protests.
- The halting of exports of advanced AI chips by Taiwan’s TSMC to China is highly likely part of the developing ‘AI arms race’ between the US and China, with global implications.



AMER
Haiti: Gangs open fire on inbound flights
Martinique: Civil unrest reignited by arrest of key protest leader
EMEA
Israel & Lebanon: Israel expands operations in south Lebanon
Nigeria: New Islamist group carries out first notable attack
Mozambique: Fourth wave of unrest causes further disruptions in Mozambique
APAC
Thailand: Warning of impending attack targeting Israeli citizens.
Taiwan & China: TSMC halts export of advanced AI chips to China
Philippines: Super typhoon hits as another approaches
North, Central and South America
Haiti: New Prime Minister appointed; gangs open fire on inbound flights
Alix Didier Fils-Aimé was appointed as the country’s new Prime Minister on 10 November by the transitional council, replacing his predecessor Garry Conille after six months of rule. Fils-Aimé is the country’s former Chamber of Commerce president and has pledged to eradicate the gang violence currently plaguing the country.
On the following day, the Port-au-Prince airport was shut down after a Spirit Airlines flight from Florida was hit by gunfire, which injured one.
Coinciding with the removal of Conille, leaders of the Viv Ansanm alliance, likely the most powerful in the country, called for an intensification of the violence. At least two further cases of planes being fired upon occurred following the first incident.
Solace Global Assessment:
Conille’s dismissal is unlikely to signal a fundamental shift in the council’s approach to the conflict and is almost certainly more a product of infighting within the transitional body than of strategic considerations. Conille, in particular, refused the council’s calls for a cabinet reshuffle and recently sought to sack three council members accused of corruption.
With no real political legitimacy behind the new appointment, there is a high likelihood that the change in administration will result in an increase in the infighting within the already precarious transitional government apparatus.
The Haitian gangs’ seeming attacks on inbound flights may be particularly important to understand the armed group’s objectives and current strategy. The fact that multiple incidents took place makes it highly unlikely that the shootings were independently carried out with no hierarchical direction. It instead appears likelier that they are deliberate efforts by local gangs to stop airport operations in Port-au-Prince.
Of note, attacks on aircraft have come after gangs blocked access to the main port in Port-au-Prince in September, forcing Haiti to rely heavily on air transport for critical humanitarian aid. The attacks are likely part of the gang’s ongoing strategy to undermine the transitional government and other international efforts. Gangs have previously targeted alternative administrative authorities and welfare providers in the country, including hospitals and Christian missions, to coerce the local population into relying on them for basic necessities.
Interrupting reliable travel to and from Port-au-Prince may likewise serve gang’s economic interest to maintain a monopoly on migration routes, and simultaneously discourage foreign actors and international organisations from operating in Haiti. It is likely that, given the success of the latest action, gangs will continue to carry out attacks on the Port-au-Prince airport and other transport hubs in Haiti.
Martinique: After ten days of relative calm, civil unrest is reignited by arrest of key protest leader
On 11 November, the French Minister of the Overseas, François-Noël Buffet, arrived in Martinique for a scheduled visit, which lasted until 14 November. The visit by the minister was made in the context of protests linked to the high cost of living which have gripped Martinique since September.
The leader of key protest group the Rally for the Protection of Afro-Caribbean Peoples and Resources (RPPRAC), Rodrigue Petitot (known as “Le R”), entered the prefectural residence on 11 November demanding to meet the visiting minister, before being escorted off the premises by police. Subsequently, on the afternoon of 12 November, in Canal Alaric, Fort-de-France, Petitot was arrested on charges of home invasion and acts of intimidation against people exercising a public function.
After ten days of relative calm in Martinique, the arrest triggered a resurgence in violent unrest in Fort-de-France. Between 100 and 350 demonstrators convened in front of the police station on Boulevard General de Gaulle demanding the release of Petitot. Violent clashes ensued, with security forces deploying tear gas and stun grenades, and some protesters allegedly opening fire with live ammunition in the direction of security forces. Three police officers were treated for minor injuries.
Buffet left Martinique on 14 November. Although the minister did not ultimately meet with RPPRAC during his visit, Buffet told a journalist that a meeting would happen in the future.
Solace Global Assessment:
The security profile of Martinique had almost certainly drastically improved before the 12-13 November clashes, with a nightly curfew and other administrative police measures being lifted since 5 November. The arrest of the key protest figure Petitot, however, reignited civil unrest and there is a realistic possibility that if renewed civil unrest continues, authorities may be compelled to reimpose a curfew.
Since the 12-13 November clashes, however, there have not been any reports of any notable further incidents. This has highly likely been at least partly conditioned by the release of Petitot from custody on 14 November. Petitot’s lawyers stated that he will be tried on 15 November under the immediate appearance procedure by the Fort-de-France criminal court. The events of the trial will likely be significant in determining the intensity and frequency of any further unrest.
Furthermore, Buffet’s promise to meet RPPRAC leaders may reduce tensions, although this meeting will highly likely need to now take place in Paris.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
Trump cabinet picks likely hint at future US foreign policy
US President-elect Donald Trump announced the first picks for the cabinet that will take office in Washington in January 2025. It is a remarkedly “anti-establishment” cabinet so far, for instance including a newly formed position for billionaire and ally Elon Musk, overseeing “government efficiency”.
From a foreign policy perspective, some of Trump’s nominees likely suggest that the new administration will adopt a foreign policy in line with that espoused in the 2017-2021 period. The two top foreign policy positions, Secretary of State and National Security Advisor, are projected to be occupied by Marco Rubio and Mike Waltz, respectively. The former rival-turned-ally and the Republican congressman share hawkish views on China, as well as espouse the president view that European NATO allies need to become more independent from a defence perspective. Rubio has also advocated for reaching a quick “conclusion” to the Ukraine war, another promise of the Trump campaign.
For the Middle East, Trump is set to appoint Steven Witkoff as a special envoy to the region, and Mike Huckabee as the new Ambassador to Israel. Both are staunchly pro-Israel, and are likely to continue Trump’s previous efforts to establish closer military and economic ties with Saudi Arabia and the UAE.
Future Defence Secretary Pete Hegseth, a FOX News host, is an “outsider” and loyalist who is expected to support efforts to challenge the “Pentagon’s establishment”. Likewise, Trump’s pick for the head of the CIA, former Director of National Intelligence John Ratcliffe, is a loyalist who helped efforts to investigate President Biden’s son Hunter and has previously heavily criticised the intelligence agency’s practices.
Cubans protest following blackouts
Multiple arrests were carried out by Cuban authorities in Havana, Ciego de Avila and the province of Mayabeque after unrest broke out following protracted power outages during the weekend. Protracted outages are increasingly common in Cuba, as the government continues to struggle with a stagnating economy, worsened by a mass-exodus of citizens and past damages from extreme weather events.
In particular, the Cuban electric grid was severely affected by the recent hurricanes, particularly Category 3 Hurricane Rafael which hit the western half of the island in early November, and, on 10 November, by a 6.8 magnitude earthquake which caused some damage in east Cuba. It is unlikely that the government has the means to provide emergency relief following the latest extreme weather events.
While last weekend’s protests seem to have been effectively contained as of the time of writing, there is a realistic possibility of more severe unrest breaking out in the short term.
Evo Morales barred from contesting 2025 Bolivian presidential election
The decision by the constitutional court reiterates a 2023 ruling and the pre-existent constitutional two-term limit for the president’s office. The ban comes a month after Morales alleged that he was targeted in as botched state-sponsored assassination attempt, a claim that the ruling government rejects.
It is likely that the ruling will further embolden supporters of the former president to continue civil unrest, with crowds continuing to block roadways and clash with police forces in several parts of the country. According to Reporters without Borders (RSF), protesters have attacked at least 25 journalists at blockade points since the beginning of the latest stage of demonstrations.
Security, Armed Conflict and Terror
Man dies in likely attempt to carry out bomb attack at Brazil supreme court
On the night of 13 November, a man died while an explosive device on his person detonated while he was trying to enter the compound of the Supreme Court in Brasilia. The individual was highly likely aiming to carry out an attack on the building. The incident occurred five days prior to the G20 summit, which Brazil is set to host.
It is highly likely that the incident is a case of lone wolf terrorism, although it is not fully clear what the ideological affiliation of the attacker was there are indications that he has linked to the far-right. The Brazilian Supreme Court has recently been involved in multiple high-profile political controversies.
Dozens killed in Ecuadorian prison riot
On 12 November, a prison riot in Ecuador’s Guayaquil resulted in the deaths of at least 15 inmates and several more injured. The riot may be an indication of the failure of President Noboa’s strategy to conduct mass arrests and incarcerations in a similar manner to El Salvador to curb street violence.
The strength, reach and resilience of Ecuador’s heavily funded and cartel-linked gangs has likely been underestimated, with the gangs controlling their operations from within the prison system. With arrests continuing to mount, overcrowding and poor conditions will likely to lead to further riots, with the potential for prison feuds to be played out on the street.
Environment, Health and Miscellaneous
Tropical Storm Sara heads north and intensifies after causing damage in Honduras
After causing heavy flooding and damage in Honduras, Tropical Storm Sara is intensifying and heading north, likely posing significant threats to Central America, the Gulf of Mexico, and potentially the southeastern United States.
Favourable conditions, such as warm waters and low wind shear, are expected to fuel its development into a robust tropical storm and possibly a hurricane, with alerts currently in place across Honduras, Belize, Nicaragua, and Mexico’s Yucatan Peninsula.
State of emergency declared in response to flooding in Colombia
On 12 November, authorities in Colombia declared a nationwide state of emergency in response to major flooding that has affected much of the country and thousands of people. The northwest of the country has been worst affected, particularly the Choco Department; however, rainfall has also led to severe flooding in the capital Bogota.
The extreme weather, worsened by the onset of La Niña, has caused widespread flooding, landslides, significant infrastructure damage and major travel disruptions. Forecasters warn that the severe weather pattern is expected to intensify throughout November.
Europe, Middle East & Africa
Israel & Lebanon: Israeli forces intensify strikes on Beirut while ceasefire talks continue
On 13 November, the newly appointed Israeli Defence Minister Israel Katz publicly stated that, while the Israel Defence Forces (IDF) had essentially “defeated Hezbollah”, the war in south Lebanon would continue and expand in scope, with IDF forces approaching the second line of towns within Lebanon (approximately 6-7 km deep at some points).
On the following day, reports emerged that US and Israel are in the final stages of agreeing on a draft ceasefire proposal for Lebanon. Hezbollah’s attacks into northern Israel have continued, although significantly declined in volume due to IDF operations in the country. Israeli strikes during this reporting period have been particularly focused on Baalbek and the outskirts of Beirut, with a single strike on 11 November killing at least 23 people.
Solace Global Assessment:
The acceleration and expansion of IDF operations in the south of Lebanon is consistent with Tel Aviv’s war aim of destroying Hezbollah forces and assets south of the Litani River and creating the conditions for the return of Israeli civilians to previously evacuated areas of north Israel. Tel Aviv almost certainly wants to avoid committing to a protracted deployment of troops in south Lebanon, which is a costly and politically unpopular endeavour.
However, Israel likely wants to retain troops in a position whereby the IDF can strike Hezbollah if it attempts to re-establish positions south of the Litani River, especially prior to a ceasefire agreement. This requirement essentially bypasses the international mandate of UNIFIL and also the domestic security prerogative of the armed forces of Lebanon.
Israeli strikes have likely degraded Hezbollah’s missile arsenal and the expansion of strikes in Baalbek are likely aimed at disrupting the facilitation of lethal aid from Syria.
Hezbollah is likely to reject a ceasefire proposal reflecting the Israeli position. First, this is due to the group still assessing that it can maintain a presence in parts of south Lebanon and that Israel likely lacks the resources, willingness, and diplomatic capital to commit to a long term occupation. Second, Hezbollah’s acceptance of an Israeli-drafted ceasefire plan would constitute a significant political defeat for the group at home and with its core constituencies.
Still, Hezbollah’s officials’ decreasing public mentions of Gaza in connection with the ceasefire negotiations hint at the group’s willingness to “decouple” the conflict in Lebanon from the one in Gaza, and thus from Hamas’ position and survival.
The US election results will also likely play an important role in shaping Tel Aviv’s (and Tehran’s) considerations regarding the possibility of a ceasefire. The Trump administration has nominated pro-Israel figures to occupy key Middle East-oriented roles, a sign that the new administration will likely continue its 2017-2021 foreign policy stance vis-à-vis Israel. However, Trump’s presidential campaign was also successful due to the massive defection of Arab Americans from the Democrat Party, achieved by promoting a foreign policy based on “ending wars”.
Moreover, Trump’s previous Middle East foreign policy was built on improving relations with Saudi Arabia, but this rapprochement has been partly stifled by the war in Gaza, with Saudi Arabia worryingly repeatedly sending positive signals to its traditional rival Iran. Faced with these factors and constraints, the Netanyahu administration will likely take advantage of the US’ transitional period to improve its battlefield position in Lebanon as much as possible.
Nigeria: New Islamist group kills 15 in northwest Nigeria
On 8 November, a new Islamist group operating in the northwest of Nigeria conducted an attack on Mera village in Kebbi State, approximately 50 kilometres from the border with Niger. The group, which has adopted the name Lakurawas, is thought to primarily operate within four local government areas in Sokoto State, namely Binji, Gudu, Tangaza, and Silame, as well as parts of Kebbi State.
The group has reportedly been enforcing strict Islamic law, has been engaged in radical preaching, has imposed mandatory Zakat on the communities where it operates and has coerced parents into marrying off their daughters.
Solace Global Assessment:
Whilst the Nigerian Defence Headquarters has described the Lakurawa group as a new terrorist organisation, there is evidence to suggest that group has existed for years and has made earlier attempts to establish itself in northwest Nigeria. The group primarily consists of Malians and Nigeriens, who were allegedly first invited to northwest Nigeria in 2017 by local leaders in Sokoto State to protect communities from bandits.
However, the group has increased its ranks, likely exploiting the 2023 coup in Niger, the general destabilisation of the Sahel and the overstretching of Nigerian security services who have struggled to contain a host of domestic security challenges, most notably a resurgent Boko Haram in the northeast. The Malian and Nigerien composition of the group may allude to connections to the al-Qaeda affiliated Jama’at Nusrat al-Islam wal-Muslimin (JNIM), an alliance of local jihadist groups that has excelled at exploiting local grievances and weak governance and has managed to ally diverse ethnicities, tribes and other marginalised groups under its core message of the establishment of Sharia Law and rejection of Western influence.
If the Lakurawas group is indeed the latest franchise of JNIM, this will invariably be a major concern to Abuja and is further evidence of the JNIM’s efforts to spread beyond the Sahel.
For JNIM, fostering a new insurgency in northwest Nigeria would present several advantages. Firstly, it could help fix Nigerian forces in Nigeria, decreasing the chances of Abuja launching operations in neighbouring Niger, where JNIM has significant influence. Secondly, destabilised border regions will help facilitate JNIM cross-border operations, enabling it to more easily move people, arms, resources and illicit goods from country to country, likely increasing the group’s funding. Thirdly, it could help expand JNIM’s reach, potentially making it easier to conduct attacks on more high-profile or Western-linked targets in Nigeria, a development that would help boost JNIM’s profile, recruitment and propaganda efforts.
For Nigeria, an increased threat in the northwest may force it to allocate resources here ahead of other areas, like the northeast, potentially providing opportunities to Boko Haram and the Islamic State West Africa Province (ISWAP).
Mozambique: Nation Faces Fourth Wave of Unrest
Mozambique is currently experiencing its fourth wave of unrest. On 13 November, protests reportedly occurred in Maputo, Ressano Garcia, Quelimane, Manica, Inhassunge, and Nampula. Police reportedly used live ammunition in Nampula, killing two protesters, and a combination of live ammunition and tear gas in Quelimane. In Inhassunge, protesters are claimed to have torched a police station and police vehicles, and allegedly killed Luís Joaquim Salimo, the local President of the District Elections Commission (CDE).
On 14 November, protests occurred in at least Maputo, Lichinga, and Xai-Xai. Security forces reportedly deployed tear gas and made arrests to disperse demonstrators in Lichinga. In Maputo, police used tear gas against a group of motorcycle taxi service providers, who signalled their protest by honking their horns while driving through the streets. The Lebombo border crossing with South Africa has intermittently closed, causing significant trade disruption. The Southern African Development Community (SADC) has scheduled an emergency summit to address the situation between 16 and 20 November.
Solace Global Assessment:
Since Mozambique’s electoral commission declared that Daniel Chapo of the incumbent FRELIMO party was elected president on 24 October, the country has experienced intense periods of civil unrest, provoked by accusations of electoral fraud. Security forces have deployed teargas and live ammunition to disperse protesters, with at least 30 deaths being recorded since demonstrations began.
Reports indicate that over 150 shops have been vandalised and roughly EUR 354 million lost during the unrest. The government has used internet shutdowns and social media restrictions to prevent the spread of further protests.
The killing of a FREMLIMO member on 13 November indicates efforts by sections of the protest movement to specifically seek out and target pro-FRELIMO officials with violence, which could inadvertently put uninvolved civilians at risk due to potential cases of mistaken identity.
The border disruption has reportedly affected trade, causing food shortages in Mozambique. According to the president of the Confederation of Economic Associations of Mozambique (CTA), roughly EUR 6 million has been lost due to transport disruptions during the unrest.
Blocking the border has been a key protest tactic to pressurise Mozambique’s government, with Mondlane specifically calling for truck drivers to block key roads and border posts. Given that approximately 40 per cent of Mozambique’s imports and 20 per cent of exports pass through South Africa, this is particularly disruptive for the region.
According to The South African Road Freight Association, South Africa’s economy has also been impacted, with the ongoing unrest costing USD 550,000 daily. It is almost certain that further economic disruptions will occur in Mozambique and South Africa if unrest continues, and border crossings are affected.
It is highly likely that protests will continue. Sources indicate that some military personnel sympathise with protesters, with videos of some soldiers signalling their support for Mondlane circulating online. It is likely that a growing dissatisfaction within the military will add pressure to a government already experiencing significant condemnation from international agencies and its population.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Protests likely to occur in western Europe during the weekend for International Students Day
Demonstrations between 15 and 17 November have already been planned in Bologna, Paris, and other European cities. There is a high likelihood that France will be particularly severely affected by protests due to the recent developments in Lebanon and Gaza, as well as the recent unrest in Paris.
Protests in Paris on Nations League match week
Pro-Palestine demonstrations occurred in Paris on 13-14 November 13 and 14. On 13 November, protesters gathered in multiple parts of the capital to protest a planned fundraiser event for the IDF. Clashes between protesters and police were reported in different parts of the city, with the latter deploying tear gas. Moreover, multiple cases of storefronts being vandalised were reported, targeting international chains that are accused of being “Zionist”.
On 14 November, the Stade de France hosted a Nations League match between the French and Israeli team. The match was highly policed, which likely prevented disorders outside the stadium. Nevertheless, clashes between Israeli and French fans inside the stadium were reported.
France’s parliament rejects new budget bill, deepening political crisis
The legislative body rejected an already-amended text of the bill that included proposals by the left-wing opposition, the New Popular Front (NFP), to increase taxes by an estimated EUR 75 billion to avoid the spending cuts favoured by Prime Minister Barnier’s supporters. The NFP proposal, which included some measures also espoused by the far-right National Rally (RN), was described by some lawmakers as likely being largely illegal from a constitutional perspective.
While the parliament’s vote frees Barnier to again attempt to present a more palatable bill, it also further deepens the rift between the three blocks that currently constitute the French parliament, and poses a serious threat of a continuing deadlock. Moreover, continuing political instability is likely to have an impact at the street-level. France, and Paris especially, are currently undergoing severe protests by groups supporting their counterparts in Martinique. These have been attended by NFP politicians.
There is a realistic possibility that the NFP’s parliamentary defeat, if followed with a protracted stall or a rapprochement between Macron’s centre and the right, will result in a increase in civil unrest.
German plans February election as ruling coalition collapses
German leaders have settled on 23 February as the date for a snap general election after collapse of the centre-left coalition headed by Chancellor Olaz Scholz and his Social Democratic Party of Germany (SPD). The coalition, which primarily collapsed over disagreements as to how to fund Ukraine, has likely provided an opportunity for Germany’s far-right anti-immigration party Alternative for Germany (AfD) to exploit, whose support has recently risen to almost 20 per cent of the polled electorate.
An increasingly polarised campaign season is likely to be marked by increased anti-immigration rhetoric, protests and counter-protests and potentially political violence.
Israeli Knesset passes preliminary approval of new surveillance bill
The legislation increases the scope for the legal use of spyware by law enforcement agencies, allowing its use even without the knowledge of the target device’s owner and on the basis of its possible utility to “prevent” an offence. The bill was advanced by the far-right Otzma Yehudit party of Minister of National Security Ben Gvir. It is highly likely that the bill is a direct political attack on Justice Minister Yariv Levin, who recently authorised a committee to investigate the possible unlawful use of spyware by police. Levin is hugely unpopular with the governing coalition’s right-wing and with the ultra-orthodox community due to the controversy surrounding the draft law reform. If enacted, the bill would pose a significant security risk to travellers to Israel, especially in terms of the protection of sensitive information.
Phone call between Saudi and Iranian leaders before upcoming Arab-Islamic summit
On 10 November, Saudi Arabia’s (KSA’s) Crown Prince and Prime Minister Mohammed bin Salman received a call from Iran’s President Masoud Pezeshkian. The leaders reportedly discussed the upcoming 18 November joint Arab-Islamic follow-up summit in Riyadh that will discuss issues relating to Israel’s campaigns in Gaza and Lebanon, with Pezeshkian praising KSA’s initiative to host the summit. High-ranking military figures from Iran and KSA additionally met in Tehran to discuss common interests and possible cooperation.
Before a China-brokered deal in 2023 that improved relations between the two regional powers, a de facto proxy conflict or ‘cold war’ existed between Iran and KSA, an antagonism that had a considerable impact on influencing the entire Middle East and beyond.
During his previous presidency, President-elect Donald Trump’s administration, who in contrast to a trend of ‘America First’ isolationism was distinctly hawkish regarding Iran, highly likely leveraged the Saudi-Iran cold war to further anti-Iranian strategic goals in the region.
With tensions at a generational high between Israel and Iran, Trump’s new administration will highly likely need to wrestle with a significantly different geopolitical landscape in the Middle East that is marked by rapprochement between Iran and the Gulf states.
Senegalese prime minister has called for revenge over campaign violence
Senegal’s Prime Minister Ousmane Sonko has called on supporters of his ruling party, Pastef, to take revenge for alleged violence against them during the campaign for the 17 November parliamentary election. Sonko condemned attacks on his supporters in Dakar and other major cities, urging retaliation through a social media post, stressing a “legitimate right to respond”. Sonko’s call, combined with the recent violence and violence observed in the March presidential elections, could gain traction among much of the country’s youth, leading to potentially violent protests in Senegal.
Guinean opposition demands return to civilian rule
On 12 November, a coalition of opposition groups, civil society organisations, and activists, known as the Forces Vives, called for the establishment of civilian rule by 1 January. The call comes in response to the military government’s promise of a two-year transition to civilian rule but with few indications of progress. Failure to acknowledge this demand and make any steps towards democracy will likely lead to protests, with previous demonstrations against the junta often leading to deadly confrontations.
Mauritius Prime Minister Jugnauth concedes defeat
The ruling coalition was defeated at the latest legislative elections held on 10 November, amidst multiple scandals and poplar opposition to a brief social media ban imposed by the government. The opposition coalition Alliance of Change, led by two-time Prime Minister Navin Ramgoolam, obtained 62.6 per cent of the votes and, under the country’s “winner takes all” system, is set to take 60 of the 62 available seats in the National Assembly. The change in power is unlikely to drastically affect Mauritius’ foreign policy, with Ramgoolam historically taking a balanced approach to both China and India.
Security, Armed Conflict and Terror
Belgian police arrests six after online calls for violence against Antwerp Jewish community
According to local media, the group, at least one of which is a minor, called for a “Jew hunt” to take place in the historical Jewish quarter in the Flemish city. It is likely that the calls for violence were meant to capitalise on last week’s violence between Israeli football fans and pro-Palestine protesters in Amsterdam, which attracted international attention. However, available information seems to indicate that no concrete plan for action had been implemented by the suspects. Coinciding with the online calls to violence, anonymous channels shared a video allegedly showing a targeted attack on a Jewish youth in Antwerp.
Turkish teenager arrested for Christmas market attack plan in Germany
The suspect, who allegedly planned to carry out an attack using a truck, similar to the 2016 Berlin Christmas market terror attack, was arrested via a joint US-German effort. According to available sources, he planned to launch an attack in the town of Elmshorn, in Schleswig-Holstein. The plot continues to underscore the growing trend of teenagers becoming self-radicalised and engaging in lone wolf terrorism, which is evident in recent cases of both Islamist and far-right terror.
US CENTCOM strikes Iranian-backed forces in Syria
US Central Command (CENTCOM) has conducted a series of strikes against weapon caches and logistic nodes linked to Iranian-backed proxy forces in Syria. The strikes are almost certainly in response to a 12 November rocket attack on a US base in Hasakah province, believed to have been conducted by Iranian-aligned groups. There is a realistic possibility that tit-for-tat strikes will continue to escalate until the inauguration of Donald Trump, who has hinted at a full US withdrawal from Syria.
Two Saudi military personnel killed in Yemen
The attack occurred on 9 November in a military camp in the city of Seiyun, in the Hadhramout governorate under government control. The person responsible for the attack was reportedly a Yemeni soldier, with no clear motive currently known. The Houthis did not claim responsibility for the attack, but nevertheless praised as a blow to the “invaders”. As a member of the Yemeni armed forces, it is likely that the soldier was Sunni and could have been motivated to attack Saudis for Riyadh’s tepid stance towards Israel or increasingly stronger ties with Iran.
Mali junta arrests Australian mining company executives
Three executives of the Australian gold mining company “Resolute Mining” were arrested on 8 November, under unclear charges. Resolute Mining holds an 80 per cent stake in the Syama gold mine, the remaining stake being held by the government. The arrests follow a similar episode in September, when four employees of a Canadian mining company were also detained for days. Mali’s gold mines have long been a key Russian strategic interest. Whilst Russia has slowly increased its involvement in Mali, the junta has expressed caution regarding Russian involvement, partly due to concerns over the Wagner Group’s activities in critical economic sectors.
Islamic State Sahel Province (ISSP) and JNIM clash in north Burkina Faso, IS official killed
Groups of fighters from the two jihadist groups reportedly engaged in a firefight in the town of Dori. According to IS channels, at least nine JNIM fighters were killed in the engagement.
While in theory ISSP and JNIM are enemies, both groups have pragmatically engaged in informal non-aggression agreements, which have made engagements like the latest one relatively rare. There is a realistic possibility that the continuing breakdown of government authority in the Sahel, and especially in Burkina Faso and Niger, will result in a growing number of clashes between various insurgent groups seeking to control territory and expand their influence.
Further validating this assessment, on 11 November local sources reported that the leader of a regional ISSP sector in the Tessit region of Burkina Faso was assassinated by militants who defected to JNIM.
Environment, Health and Miscellaneous
Approximately 4,000 illegal miners cut off from supplies by South African government
Illegal mining operations are prevalent in the country’s gold-rich North West province, and is often carried out by transnational armed groups. To deter it, the government has implemented a program known as “Vala Umgodi”, or “close the hole”, as part of which police is used to cut supplies to locations where illegal mining operations are ongoing, in an effort to force the illegal miners to surface.
The approach reduces risks for police officers, who would face environmental hazards, as well as the threat of armed opposition, if attempting to carry out arrests inside the mines. However, faced with imprisonment, miners often choose to remain underground for protracted periods of time.
Approximately 4,000 miners are trapped in one mineshaft in Stilfontein, of which only a few dozen have surfaced so far.
Argentina’s envoy to COP29 recalled from Azerbaijan
President Milei’s decision to recall his team from the summit only a few days after its beginning is a politically important gesture and may be a nod to the future US administration, as Trump previously took the US out of the Paris Climate Agreement over accusations of it being unfair to American businesses.
The COP29 summit has been marred by political failures. During the event, for instance, the EU Parliament voted to amend and significantly “water down” a bill to impose due diligence obligations on traders importing raw materials into Europe, which was strongly supported by Green parties and environmental activists.
Asia–Pacific
Thailand: Thai authorities warn of impending attack targeting Israeli citizens
On 12 November, the Prime Minister’s Office of Thailand issued an alert relating to a “growing fear of attacks on Israelis and Jews across Thailand,” with Thai police specifically warning of a terror plot to target the 15 November Full Moon party on the tourist island of Koh Phangan. The party island is popular with Israeli tourists who are either banned from entering several countries in the region or have to meet strict conditions to enter.
The Israeli intelligence agency, the Institute for Intelligence and Special Operations which is known more commonly as Mossad, has confirmed that it has received concrete intelligence of the plot and has advised Israeli citizens from highlighting their nationality or religion when in Thailand and to avoid large gatherings throughout the country.
Solace Global Assessment:
The nature of the alert specifically warns about an attack targeting Israelis, however, the indiscriminate nature of many attack methodologies, such as improvised explosive devices, small arms fire and even mass stabbings pose a serious threat to all tourists. Thailand has recently struggled with a resurgence in the south Thai insurgency, which is typically confined to attacks on the army and police in the provinces of Narathiwat, Pattani and Yala. However, it is likely that militants like Barisan Revolusi Nasional (BRN) have a high degree of movement throughout Thailand and networks established throughout much of the country.
Attacks on tourists are typically rare and would potentially serve to undermine their cause. However, a string of attacks in popular tourist areas like Hua Hin, Surat Thani, Trang and Phuket suspected to have been conducted by Muslim separatists killed four and injured 36 in 2016. A separate attack at a Bangkok Shrine in 2015 killed 20 and was attributed to Pan-Turkic ultra-nationalists, indicating vulnerabilities in Thailand’s security apparatus.
Whilst Thailand’s separatists have traditionally rejected jihadist ideology, rates of radicalisation have likely increased as a result of the war in the Middle East and as a consequence of setbacks in ceasefire talks, increasing the likelihood of separatists conducting a high-profile attack in a tourist location frequented by multiple nationalities. Alternatively, there is a realistic possibility that the alert is linked to foreign nationals who may have exploited Thailand’s relatively lax visa policies to establish a footprint in the country, with groups like the Islamic State and al-Qaeda known to have previously used Thailand as a base for logistics, recruitment and fundraising.
Taiwan & China: TSMC halts the provision of advanced AI chips to China
Starting 11 November, the Taiwan Semiconductor Manufacturing Company (TSMC) has halted the provision of advanced chips to clients in the People’s Republic of China. These sophisticated chips, seven nanometre or below designs, are often used for artificial intelligence (AI) and graphics processing units (GPUs).
According to unnamed sources, the US Department of Commerce ordered TSMC to do this. Unnamed sources also stated that “any future supplies of such semiconductors by TSMC to Chinese customers would be subject to an approval process likely to involve Washington.”
The Department of Commerce has declined comment, and a TSMC spokesperson simply stated that TSMC are a “law abiding company” and will comply with all “domestic and international regulations”.
Solace Global Assessment:
There is a realistic possibility, particularly with the election of Donald Trump, that such chip shipment bans could in future be expanded to include “central processing units (CPU), autonomous-driving chips” and “smartphone chips”. With China reportedly accounting for “11 per cent of TSMC’s third-quarter revenue”, it is almost certain that chip export bans have been made for geopolitical purposes. The US and China are highly likely in a de facto ‘AI arms race’, with AI promising to have significant commercial and military utility.
The decision to halt shipments of advanced chips to Chinese clients comes just weeks after the US Commerce Department was informed by TSMC that one of their chips had been found in a Chinese multinational technology corporation Huawei produced “AI processor”, in “apparent violation of export controls” due to Huawei’s inclusion on a restricted trade list. Major US chip manufacturers Nvidia and AMD have had restrictions from the Commerce Department on exports of AI-related chips to China since 2022.
The US is almost certainly already far ahead in the AI arms race against China, and this new development will almost certainly further curtail Beijing’s ambitions to catch up with the US in the development of advanced AI, with the Kunlun II processor used in AI chips produced by the Chinese tech company Baidu, for example, being made by TSMC.
President-elect Donald Trump has indicated that he will impose a considerable increase on already high tariffs on Chinese imports, which would likely renew the ‘trade war’ with China that occurred in Trump’s previous presidency. Trump’s prior statements that Taiwan should pay for its own defence, which prompted fears of the unreliability of US security guarantees for Taiwan against a hypothetical Chinese invasion in a new Trump presidency, were likely part of Trump’s foreign policy of ‘transactional diplomacy’, the leveraging of international overreliance on US security guarantees and attempts to gain benefits for the US’ domestic economy.
Trump has long complained about TSMC’s global monopoly on the production of advanced semiconductors, desiring greater manufacturing of such chips in the US. On 7 November, Taiwan’s Minister of Economic Affairs J.W. Kuo reaffirmed that Taiwan’s technology protection rules prohibit TSMC from producing two nanometre chips abroad, likely targeted at concerns that TSMC will be forced by Trump to produce these chips ahead of schedule at fabrication facilities in Arizona.
It is likely that Trump will apply such pressure, and it is likely that the new TSMC advanced chip export ban to China will increase China-Taiwan tensions.
Philippines: The Philippines hit by super typhoon as another approaches
Storm Usagi strengthened to super typhoon status before making landfall near Baggao in Cagayan, the Philippines, with maximum winds reaching 185 km/h on 14 November. This prompted the government to issue a Wind Signal 5 warning for northeast Cagayan, the highest level of alert in the country.
In the aftermath of the storm, significant damage was reported, including the collapse of a bridge in Gonzaga, Cagayan province, the Philippines, highlighting the destructive power of Usagi. The storm caused severe flooding and landslides in Cagayan and Isabela provinces, with warnings issued for similar conditions in six other provinces.
At least one person was reported dead, and two others were missing in Cagayan due to the storm’s impact.
Solace Global Assessment:
After travelling through the Philippines, Typhoon Usagi has weakened, with current maximum sustained winds of around 100 km/h. Taiwan’s weather agency issued land warnings for Kaohsiung, Pingtung, and Taitung as the storm approached and it is set to make landfall late 15 November. As the Philippines recovers from Typhoon Usagi, Typhoon Man-yi is set to hit the Luzon region again, due to make landfall in Luzon on 17 November with sustained winds of approximately 225 km/h. The Philippines is almost certain to experience further damage once Typhoon Man-yi makes landfall.
Usagi is the fifth major storm to hit the Philippines within three weeks, during which time at least 160 deaths and nine million displacements have occurred. The United Nations reportedly counts 207,000 houses damaged or destroyed over the past month due to typhoons and has requested USD 32.9 million in aid for the worst affected regions.
Much of the Philippines is low-lying land, which makes it particularly vulnerable to flooding caused by precipitation and storm surges. The repeated flooding of farmland will likely affect replanting efforts and impact the populations’ access to food. Despite being typically exposed to 20 typhoons a year, the country does not have resilient infrastructure; many roads, buildings, and buildings are poorly constructed and maintained, adding to their susceptibility to damage.
While the government has responded by evacuating citizens and providing relief, its capabilities are limited by resource constraints and the typhoons’ frequency. Defence Secretary Gilberto Teodoro has appealed to neighbouring countries to assist with disaster relief efforts.
Climate change has increased the frequency and intensity of typhoons in the Philippines in recent years. Because oceans are warmer, storms can pick up more energy while they track, causing intensified wind speeds. Moreover, the risk of flooding has escalated due to increased precipitation rates driven by a warmer atmosphere. Additionally, storm surges are now reaching further inland due to the rise in ocean levels. As a result, typhoons reportedly form closer to land, intensify quicker, and last longer, increasing their risk to local populations.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Bangladesh opposition takes to the streets to call for new elections
The Bangladesh Nationalist Party (BNP), an Islamist party which represented one of the key opposition forces to the Hasina regime and now provides vital political support to the interim government of Muhammad Yunus, staged a demonstration in Dhaka calling for new elections and the formation of a political government.
The BNP has likely sought to amplify its political sway in Bangladesh in the last month, also trying to establish its control over the informal systems of administrations and clientelism that were previously governed by the Awami League, Hasina’s Party. Elections are highly likely to benefit BNP beyond the prospect of a more active role in government.
By legitimising the new political status quo, elections would also stop Hasina’s supporters’ efforts to question the validity of the new executive, and allow the former opposition more freedom to challenge the remnants of the Awami League.
The Philippines pass new laws on maritime territory, angering Beijing
The two measures, which were signed into law by President Marcos on 8 November, reaffirm Manila’s claims over areas of the South China Sea that China claims as its own. The approval was met with a formal protest by Beijing. Notably, the laws include a provision that all artificial islands constructed within Filipino territory are Manila’s sovereign territory, and at least one Chinese-built reef base would theoretically fall within this category.
While it is still unclear how Manila will implement the new laws, it is highly likely that they will contribute to heightened tensions with China, and may result in further provocative actions, including clashes between the two country’s coast guards in disputed waters.
Japan’s Prime Minister Ishiba re-appointed after disastrous election
The new Japanese parliament, fresh from a watershed election which resulted in the ruling Liberal Democratic Party (LDP) losing its majority in the lower house of parliament, voted for incumbent Prime Minister Shigeru Ishiba to retain his position. Ishiba recently won a highly contested leadership vote in the LDP, and called the elections after his nomination.
After his re-election, Ishiba chose to retain most of his cabinet members, and indicated a willingness to cooperate with opposition forces, especially the moderate Democratic Party for the People. While the parliament vote is unlikely to resolve the political weakness of the new administration, it will likely allow Ishiba to carry out a series of key diplomatic and domestic tasks in the next few months, including crucial summits with regional partners and a likely meeting with US President-elect Donald Trump.
Security, Armed Conflict and Terror
11 dead in clashes between militants and security forces in Manipur, India
On 11 November, 11 camouflaged Kuki-Zo militants died in a gunfight with security forces in the Jiribam District of Manipur. Militants reportedly fired indiscriminately at a police station and Central Reserve Police Force (CRPF) camp, injuring two CRPF members. In response to the violence, the Kuki-Zo Council imposed a curfew from 05:00 to 18:00 local time and prohibited the carrying of anything that could be used as an offensive weapon.
Coming after a brief lull, this marks a fresh escalation in violence in the Manipur region, which has seen over 260 deaths since 7 November 2023, when a Hmar tribal woman was burned alive. The multiple tribal communities, the main three being the Kuki-Zo, Meiteis, and Nagas, have clashed primarily over land rights, representation, and resource allocation since Manipur achieved statehood.
The 11 November attack represents a broader failure of local security forces to bring the conflict under control in a region that is central to India’s Look East policy of strengthening trade and commerce in the region. It is highly likely that this attack will trigger further ethnic violence in Manipur from rival tribal groups, primarily the Meitei, causing further displacement and civilian casualties.
Indian Naga insurgents threaten to restart violence
The latent insurgency, which is composed of a network of ethnic Naga groups seeking to establish an independent state (“Nagalim”) in India’s North-Eastern Region (NER), is the oldest still active in the country, having begun in the mid-1950s. However, a ceasefire has been in place between Delhi and the National Socialist Council of Nagaland (NSCN), the main Naga militant group, since 1997, which was renewed in 2015.
On 8 November, NSCN leaders threatened to resume violent action after accusing India of “betraying” the “spirit” of the agreement. If violence were to resume, it is highly likely that the resulting destabilisation will impact nearby provinces, including Arunchal Pradesh. The continued destabilisation of neighbouring Myanmar has likely provided militants with an opportunity to acquire arms, a development that would hinder India’s ability to contain the conflict should it restart.
More than 30 dead after vehicle attack in Zhuhai, China
On the evening of 11 November, a 62-year-old man drove a vehicle into crowds at stadium in Zhuhai, killing 35 and injuring dozens more. The motive for the attack, which was almost certainly deliberately carried out to maximise casualties, is unclear, but Chinese media has indicated that there seems to be no indication that the suspect espoused an extremist ideology. The attack likely is the deadliest “random” attack in China in years, and follows similar cases from earlier this year, including a stabbing and shooting attack in Shandong in February 2024 which killed 21.
Environment, Health and Miscellaneous
Pathogenic avian influenza identified for eighth time this year at Japan poultry farm
The latest case was reported in Asahikawa in the Hokkaido island. The first outbreak of bird flu in Japan this season was recorded in mid-October, also in Hokkaido. The virus usually spreads with migration patterns in the fall. The identified strand of highly pathogenic avian influenza virus (HPAIV) is the subtype H5, which is particularly deadly. The H5 strand affects birds and can be transmitted to mammals. In the US, there are recent cases of dairy and poultry workers contracting the virus.
Subscribe to free weekly intelligence

Executive Summary
- The election of Donald Trump as the 47th US President will almost certainly affect the geopolitical landscape of Europe. It will likely result in an increased threat of political violence in the US.
- Despite a 72-hour humanitarian pause, large-scale unrest will almost certainly continue in Bolivia due to protestors’ unmet demands and the president’s refusal to resign.
- A Russian-linked plot to ignite incendiary devices on Western-bound planes is likely indicative of an escalation of the Kremlin’s hybrid warfare strategy.
- The government’s use of violence and the opposition’s repeated calls for protests will almost certainly sustain widespread violent unrest throughout Mozambique.



AMER
US: Trump wins presidential elections
Bolivia: Protestors instigate 72-hour humanitarian pause
EMEA
Germany: Incendiary device planted on UK-bound plane
Chad: President threatens to withdraw from regional task force
Sudan: RSF on the offensive in Darfur
Mozambique: Violence nationwide unrest continues to escalate
APAC
India: Jammu and Kashmir’s assembly demands restoration of special status
Philippines: Manila holds military exercises simulating island landings
North, Central and South America
United States: Donald Trump wins presidency, defeating Kamala Harris
On 5 November, US citizens voted to elect their 47th President, as well as representatives for the two houses of Congress. Donald Trump, the former president and Republican Party candidate, defeated Kamala Harris by winning all seven “swing states” and, most notably, winning the popular vote, a feat that no Republican candidate, winning or losing, had achieved in two decades.
The Republican Party also obtained positive results in Congress, winning control of the Senate and (as of the time of writing, this is still unconfirmed but appears almost certain) retaining control of the House.
The victory will put the new Trump administration – set to take office in January 2025 – in a strong position, with control over both the executive and legislative branches, alongside the continuing presence of a right-leaning Supreme Court. Harris and current President Joe Biden have conceded the election and called for an orderly transfer of power.
Solace Global Assessment:
A new Trump presidency is likely to provoke important changes in the US’ foreign relations. On hearing the election results, a notable signal towards likely changes was sent by the leaders of European powers. French President Macron and German Chancellor Scholz almost immediately released a statement calling for the EU to become more united and independent on defence matters. The statement almost certainly reflects widespread European worries about US commitments towards the defence of Eastern Europe, and especially Ukraine, under Trump’s second term.
Trump has repeatedly stated his position that the Ukraine war was at least partially caused by Zelensky and that Western aid to support Ukraine’s war efforts is, at best, misplaced. Russia’s recent, and likely future, battlefield progress in Donetsk, is likely to confirm the new administration’s worries regarding the feasibility of Ukraine’s long-term defence and the prospect of drawing out the conflict at huge expense to the US.
Russian forces will likely increase their long-range attacks on Ukrainian population centres and critical national infrastructure (CNI) to deplete Ukraine’s air defence stock, hoping that a future suspension of US aid will put Kyiv in a difficult position, increasing the chances of forced negotiations.
Domestically, Trump’s election is likely to be a driver of civil unrest and increased political violence. On the night of 5 November, clashes between far-left militants and police officers were recorded in Seattle, although these have had a limited impact. There is a realistic possibility of targeted political violence following the elections and in the months approaching the inauguration of the new administration.
The two (possibly three) assassination attempts on Trump have had a massive level of political visibility and have demonstrated that copycat attacks represent an increasingly realistic threat. Likewise, recent cases demonstrate a growing threat from radical groups carrying out sabotage actions in efforts to destabilise national and local governments.
There is a realistic possibility that such groups, mostly but not exclusively on the far left, will seek to stage sabotage actions similar to the ones that targeted the Tesla “megafactory” in Germany or the French high-speed railway service just before the Olympics.
Bolivia: Protestors instigate 72-hour humanitarian pause of blockades after a week of intensified unrest
On 6 November, protestors announced a 72-hour suspension of blockades amidst rocketing food and fuel prices. According to the Bolivian Highway Administration, no roadblocks remain in Bolivia as of 6 November. While some were peacefully dismantled, there were multiple incidents of violence as security forces attempted to remove the roadblocks by force.
Because of Bolivia’s topography, protestors commonly use roadblocks to pressure the government by isolating major cities and slowing economic activity. The government has, therefore, blamed the rise in food and fuel prices on these blockades, a fact disputed by protestors.
The humanitarian pause comes after a week of steadily escalating unrest after an alleged assassination attempt on ex-President Evo Morales on 27 October. 1 November saw alleged armed supporters of Morales reportedly taking over 200 military personnel hostage and seizing weaponry and ammunition in Cochabamba. On the same day, Morales called for an end to the blockades, launching a hunger strike to demand a meeting with the government.
Protests, primarily in locations with strong support bases for Morales such as Cochabamba and Mairana, have developed into violent clashes with the police as protestors have utilised projectiles including firecrackers, homemade explosives, and stones fired from slingshots. According to government figures, 127 people have been injured, 92 of which were police officers, and 180 arrests have been made, with demonstrators being accused of various crimes including terrorism.
Solace Global Assessment:
The past week of intensified violence comes after an alleged assassination attempt on Morales. The facts are disputed, with the government instead claiming that shots were fired at Morales’ vehicle after it ran a police checkpoint and hit a police officer. Given the tension between Morales’ supporters and the government, the disputed event has likely been enough to energise an escalation in popular unrest in support of Morales.
Unrest is highly likely to continue over the coming week since the government is unlikely to bow to protestors’ demands of President Luis Arce’s resignation and their allowing Morales to run in the 2025 election. Given its effectiveness at pressuring the government, reportedly causing USD 1.7 billion in economic damages by preventing food and fuel from entering major cities, there is a realistic possibility that protestors will restore blockades once the 72-hour pause ends if the government does not adhere to their demands.
This will likely trigger Arce, who has already threatened to use his constitutional powers if blockades do not cease, to take more forceful measures. If a state of emergency is declared, the government may utilise the military and impose curfews to quell unrest. This would likely cause protests to spread further and affect the administrative capital, La Paz, which has been relatively free of unrest.
In the longer term, given Bolivia is set for a presidential election in 2025, unrest will likely ignite periodically until then. Morales, an Indigenous Bolivian, has a large support base amongst the Indigenous members of the population, who feel marginalised by the Arce government and oppose its economic and environmental policies.
Furthermore, protests were sparked over issues of the economy, before Morales’ arrest warrant was issued, which means that they are not solely tied to Morales achieving a positive outcome. Should Morales be allowed to run in 2025 and achieve dialogue with the government, the economic pressure on Bolivia’s population means that protests will likely re-ignite into 2025 until there is a change of government or the economic issues are addressed.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
Mexican Supreme Court fails to curb judicial reform
The Supreme Court of Mexico has rejected a last-ditch attempt by the opposition to limit the incumbent government’s controversial reform of the country’s judiciary. The result has likely averted a threatened constitutional crisis between the court and the newly elected government of President Claudia Sheinbaum.
The original reform, which will make it mandatory for all Mexican judges and magistrates to stand for election, was heavily criticised over concerns it would politicise the judiciary and weaken the separation of powers. This has been a major catalyst for unrest throughout the country and there is a realistic possibility of renewed protests in response to the Supreme Court’s decision.
Nightly curfews and other security measures end in Martinique
On late 4 November, the Prefect of Martinique released a statement announcing the end of the nightly curfew and all other administrative police measures from 5 November. This decision was justified by the Prefect as being “no longer justified by serious risks to public order”, due to a “week without urban violence or roadblocks”. During the past week, the impact of civil unrest and protests in Martinique has been minimal.
On 3 November, however, a solidarity protest did take place in Paris, with leaders from the primary protest organisers the Rally for the Protection of Afro-Caribbean Peoples and Resources (RPPRAC) in attendance, having flown from Martinique. François-Noël Buffet, the Minister of Overseas Territories, will be officially visiting Martinique on 14-16 November, and RPPRAC have stated that they wish to meet the minister, with or without an invitation.
While the unrest in Martinique has considerably diminished in intensity, there is a realistic possibility that with the lifting of the curfew, the forthcoming visit from the Minister of Overseas Territories, ‘solidarity’ protests in mainland France and the continued demands of RPPRAC, civil unrest may resurface in the coming weeks.
Security, Armed Conflict and Terror
Increase in terrorist messaging in the US during and after the election.
Multiple far-right and mostly online-based groups in the United States have called on supporters and sympathisers to carry out acts of terrorism against government and security institutions during the elections. Groups that have significantly increased calls to violence in the days surrounding the elections include fringe formations like the ”satanic” far-right Order of the Nine Angels (O9A) or identitarian groups like the Blood Tribe (BT).
Alongside far-right calls to violence, Islamist and far-left channels have also called for attacks and targeted assassinations of US officials. On 6 November, the FBI arrested one individual in Michigan for reportedly calling for further assassination attempts on President-elect Trump from an Anarchist position.
Environment, Health and Miscellaneous
Cuba suffers another major blackout.
On 6 November, Cuba experienced a further nationwide blackout caused by Hurricane Rafael, which brought winds of up to 185 km/h (115 mph) to the island nation. The hurricane’s impact led to the failure of the national energy grid, leaving millions without power. This blackout is part of a series of recent outages that have severely affected the country, exacerbating the ongoing economic and infrastructure challenges which may result in unrest.
Severe flooding in northern Panama.
There have been several days of severe flooding and landslides in Panama, particularly in Veraguas and northern regions. As of 8 November, hundreds remain in shelters and the current death toll stands at five. More than 30 landslides in Veraguas have forced hundreds to evacuate, while infrastructure damage includes destroyed bridges, especially in Coclé Province, which has disrupted travel. The government has maintained a Red Alert in five provinces and is working with emergency services on evacuations, rescue efforts, and aid distribution.
Europe, Middle East & Africa
Germany: Western officials accuse Russia of planting incendiary device on UK-bound plane
Western intelligence officials have implicated Russia in a July plot which involved the ignition of an incendiary device on a plane heading to the UK after an incendiary device hidden in a DHL package containing massage pillows and erotic gadgets caught fire in Leipzig, Germany. The device is similar to one that ignited at a DHL warehouse in Birmingham, UK.
The devices are thought to originate from Lithuania but have also been found in Poland, leading to the arrest of four Polish individuals. Western intelligence assesses that Russia’s Main Intelligence Directorate (GRU) orchestrated the plot and that the UK-bound flight may have been a dry-run for a more ambitious flight heading to the US.
Solace Global Assessment:
In response to the West’s support for Ukraine, Russian intelligence has leveraged multiple attack methodologies like sabotage as part of its comprehensive “hybrid” warfare campaign. This has included multiple incidents of arson and other forms of physical attacks on facilities and infrastructure linked to the facilitation of lethal aid to Ukraine, such as warehouses and the railway network. To date, these attacks have not resulted in any civilian loss of life; however, as Russia continues to lose personnel and materiel on the battlefield, there is a realistic possibility that it may seek to escalate its hybrid strategy.
Moreover, the expulsion of Russian intelligence officers from Europe after the invasion of Ukraine has forced Russia to rely heavily on criminal entities and disaffected populations to carry out cash-induced and highly deniable, but often reckless acts of sabotage. However, an attack on an aircraft would mark a major and likely deadly escalation of Russian tactics. There is a realistic possibility that the attack was designed to fail, to send a clear strategic message to the West without escalating.
Nevertheless, Russian-sponsored acts of sabotage will almost certainly continue and likely escalate as the West continues to support Ukraine. However, Donald Trump’s and the Republican Party’s victory in the US elections will likely lead to decreased arms deliveries to Ukraine, forcing Kyiv to rely more heavily on European assistance. This dynamic will almost certainly shift Russian intelligence’s operational focus to Europe, resulting in both an expansion and escalation of its sabotage campaign.
Chad: President threatens to pull out of regional task force
Chadian President Mahamat Idiss Deby has stated that his country is ready to withdraw its commitments from the Multinational Joint Task Force of the Lake Chad Basin Commission (MNJTF). Déby cited inadequate coordination among member states in countering extremist threats, like Boko Haram, as the reason for the move. The decision follows the 27 October Boko Haram attack on a Chadian Army garrison near Ngouboua, close to the Nigerian border, which killed over 40 soldiers.
Solace Global Assessment:
The MNJTF, originally organised in the 1990s, was reactivated in 2015 by the African Union to combat the rise of jihadism and cross-border security issues in the Lake Chad region. Benin, Cameroon, Chad, Niger, and Nigeria currently all contribute troops to the MNJTF, which has approximately 10,000 soldiers, which according to some assessments is less than the size of Boko Haram. Boko Haram and other militant groups like Islamic State West Africa (ISWA) have long exploited the Lake Chad Basin’s weak governance, poverty and porous borders to establish safe havens and to facilitate operations in Nigeria, Chad, Niger, and Cameroon.
The recent Boko Haram attack is likely indicative of a worsening security situation in the wider region and has almost certainly served as a catalyst for Chad’s withdrawal from the MNJTF. However, there are likely more strategic justifications for Chad’s threat to withdraw. Chad may view its withdrawal as a way to achieve more operational flexibility by not having to rely on or coordinate with underperforming or overstretched partner militaries.
The withdrawal could also enable Chad to expand its operations into neighbouring countries, especially Nigeria, by removing the constraints of coalition agreements. Whilst this may allow Chad to take more direct action against militants, there are some potential major disadvantages with this course of action. Uncorroborated reports indicate that the Chadian Army has already conducted operations in Borno State, Nigeria and killed dozens of misidentified fishermen in retaliation for the recent Boko Haram attack.
An increase in Chadian cross-border operations without sufficient local intelligence is likely to lead to more collateral damage, and displacement and will almost certainly play into the hands of groups like Boko Haram that will exploit these trends for propaganda and recruitment. In addition, if Chadian forces are perceived to be filling a security vacuum within Nigeria, this could force Abuja to recommit forces to the Lake Chad region, drawing resources away from other critical security priorities, such as operations against banditry and insurgent activities in other parts of Nigeria, leaving gaps that violent extremist groups could exploit to expand their influence
Sudan: Rapid Support Forces (RSF) try to take al-Fasher
According to local media, on 4 November the RSF launched a new offensive against the government-controlled city of al-Fasher, the last stronghold of the Sudanese Armed Forces (SAF) in Darfur. Efforts to take the city, which would grant the RSF complete control over Darfur, began in April 2023, with the most recent phase of the fighting starting in April 2024 with renewed RSF operations. The SAF has conducted some partly successful relief efforts, including the successful deployment of reinforcements in October.
Solace Global Assessment:
Both the RSF and SAF consider al-Fasher vital for their strategic objectives. Gaining control of the city would allow the RSF to mobilise considerable resources towards the pacification of Darfur and the creation of a more stable political authority alternative to Khartoum. Moreover, it would allow them to shift troops towards areas of the front where government forces have applied increasing pressure over the past weeks. The RSF’s control of Darfur will almost certainly result in escalating violence against civilian populations, particularly against ethnic groups seen as sympathetic to opposition forces. This could lead to widespread displacement, mass killings, and a systematic campaign of ethnic cleansing
It is highly likely that the timing of the offensive follows development elsewhere in Sudan. In late September, the SAF launched its biggest offensive so far in the conflict towards the capital of Khartoum. While the attack succeeded in pushing RSF out of positions in Omdurman and the portion of Khartoum north of the Blue Nile, it has stalled with much of the capital remaining under RSF control. The Khartoum operation was launched to coincide with General Abdel Fattah al-Burhan’s address at the United Nations’ General Assembly and was highly likely meant to provide both a political boost to the government, and to leverage a localised weakness of RSF units’ positions in the area.
Mozambique: Violent unrest continues throughout Mozambique
Violent unrest has continued throughout much of Mozambique since the declaration of the winner of the general elections on 24 October. On 7 November, the largest protests to date were organised in the capital Maputo and in other major cities like Beria and Nampula. The police fired tear gas at protestors in Maputo and there have been multiple reports of police firing live ammunition, with Amnesty International reporting that at least 20 people have been killed.
The government has continued to shut off access to internet sites and social media platforms, resulting in a record number of Virtual Private Network (VPN) users. The opposition leader, Venâncio Mondlane, has fled to Johannesburg, South Africa, where he has alleged that he was a victim of a government-sponsored assassination attempt.
Trucks entering Mozambique from South Africa have been forced to stop by protestors with reports of trucks being looted. South African officials have temporarily closed its busiest border crossing with Mozambique due to violence on the border and the attempts of Mozambicans to flee into the country, leading to incidents of South African police firing rubber bullets and stun grenades toward Mozambique nationals.
Solace Global Assessment:
The scale of unrest in Mozambique has almost certainly escalated in response to police tactics, the opposition’s sustained calls for unrest, and the alleged assassination attempt on Mondlane. The widespread use of VPNs has likely enabled protestors to circumvent government restrictions and disseminate media or organise protests at a greater scale. Increased internet access has also provided more fidelity on the government’s response, which will likely contribute to further unrest. Due to the scale of unrest, there is a realistic possibility that the government will deploy further troops in support of the police, a move that is likely to result in higher casualties.
The looting of trucks on the border and South Africa’s closure of a major border crossing will likely disrupt trade, potentially leading to critical shortages and will also restrict options to leave Mozambique. There are early indications that the Islamic State Mozambique (ISM) is exploiting the unrest to expand its operations, with reports of increased attacks and activity in the Cabo Delgado region. If the government redeploys troops from the region, it is almost certain the ISM will seek to leverage this development, with increased attacks on civilians and possibly the oil and gas industry.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Thousands of Serbs protest after collapse of railway station
On 5 November, thousands of Serbian opposition supporters gathered in Novi Sad to protest the recent collapse of the city’s railway station which killed 14 people. Protestors have blamed the government for the disaster, levelling accusations of negligence and corruption. Protestors broke windows at the city hall, threw flares and firecrackers, and sprayed liquid manure. They also targeted the Serbian Progressive Party’s office with eggs, bottles, and bricks. The police have deployed tear gas to disperse crowds and cordoned off access to state and municipal offices in the city.
Protests erupt over Turkey’s replacement of elected Kurdish mayors
Almost one hundred people have been arrested in Turkey’s Kurdish-majority regions of Mardin, Batman, and Halfeti after protests were sparked by the government’s replacement of elected Kurdish mayors with appointed trustees due to “terrorism-related” charges. The police have used plastic bullets, water cannons, and tear gas to disrupt the protests; these measures will likely escalate protests in the short term.
French gendarmes arrested by Israeli police in Jerusalem
The two police officers were arrested on the evening of 7 November and briefly detained, while they were guarding a church compound owned by France. The arrest took place as the French Foreign Minister prepared to visit the compound. The incident highly likely constitutes a violation of the 1961 Vienna Convention on Diplomatic Relations, which enshrines the principle of diplomatic immunity in international law. The episode is highly likely to increase domestic pressures on the Macron government to distance itself from Tel Aviv.
Mali set to criminalise homosexuality
Mali’s de facto parliament, the National Transitional Council, has passed a law which will criminalise same-sex acts and any activity which promotes it. The law still requires approval from the ruling military junta, who are likely to pass it. The penalties for breaking the law are yet to be determined, although they are expected to be harsh and could include the imposition of the death penalty.
Kenyan government accused of human rights abuses during anti-finance bill protests
Recent reporting from Human Rights Watch has accused the Kenyan government and security services of abduction, arbitrary arrests, torture, and extra-judicial killings between June and August during the country’s anti-finance bill protests. The accusations also allege that even after the unrest, government forces continued to target protest leaders, detaining them in secret and without legal rights. There is a realistic possibility that the accusations will reignite tensions and lead to further unrest.
Mauritius to hold general election on 10 November
Mauritius is preparing for elections on 10 November, amid growing tension and controversy. The government had initially imposed a social media blackout in response to a wiretapping scandal but reversed the decision on 4 November following widespread public backlash. The scandal, which involved the leak of private conversations among high-ranking officials, has deepened political divisions and eroded trust in the government. Heightened security measures are in effect, with protests and rallies expected to take place during the election.
Security, Armed Conflict and Terror
Israeli football fans and pro-Palestine protesters clash in Amsterdam
On the evening of 7 November, clashes erupted between football supporters and protesters after the Ajax-Maccabi Tel Aviv Europa League game in Amsterdam. At least ten people were injured in the clashes, and 60 were arrested as of the time of writing. Videos available online show early tensions beginning before the game started, with police clashing with demonstrators in the city centre during the afternoon, as well as cases of vandalism reportedly carried out by Maccabi fans. Other footage from later in the day shows apparent mob attacks on isolated individuals in different parts of the city. The incident follows previous cases of harassment and attacks on Israeli nationals during sporting events.
Germany arrests members of far-right group
Eight members of a group known as “Saxony Separatists” (“Saechsische Separatisten”, a name that is a reference to the Schutzstaffel or SS, the Nazi state’s paramilitary wing) were arrested on 5 November during multiple raids in eastern Germany, near the German-Polish border. Authorities report that the group, potentially consisting of several dozen members, aimed to establish an independent neo-Nazi state in eastern Germany following what they viewed as the “inevitable” collapse of the German state
Elements of the group’s ideology signal that it may espouse a form of far-right “accelerationism”, a set of beliefs which sees society as in terminal decline due to structural factors, and importantly claims that a revolution can only be obtained by promoting, rather than opposing, these destabilising trends. Accelerationist ideology inspired, among others, the perpetrator of the 2019 Christchurch Mosque shooting.
Islamists imposing religious tax on Mali’s Christian community
Jihadist militants in Mali are increasingly persecuting the country’s Christians by imposing an Islamic jizya tax on the community. Recent reporting from the village of Douna-Pen indicates that a tax of 25,000 CFA francs (approximately USD 41) is being imposed on Christian adults in one of the world’s poorest countries where GDP per capita is less than USD 900. Those unable or unwilling to pay face threats of church closures or violence.
Groups like Jama’at Nasr al-Islam wal Muslimin (JNIM) and Islamic State in the Greater Sahara (ISGS) have been implicated in this practice and are almost certainly using it to generate funds to facilitate operations against the junta government and its foreign allies.
Nigerian authorities warn of new Islamist group in Sokoto state
On 5 November, state officials reported an increase in activity from a newly formed group named “Lakurawas”. While little is currently known about the group’s activity beyond possible attempts at creating alternative administrative structures in Sokoto, their apparent use of “Arewa” as a term designating their area of operations likely highlights some possible strategic objectives. Arewa is sometimes used to refer to the part of northern Nigeria under the control of the 19th century Sokoto Caliphate. Its use by the group therefore likely indicates an intention to create a politico-religious entity in the north of Nigeria.
Environment, Health and Miscellaneous
Anger at authorities as Spanish floods death toll rises
The death toll from the flooding that devastated Valencia in Spain has risen at least 217, with more than 60 of these deaths in a suburb of the city Valencia, Pairporta. The Spanish King and Queen visited Pairporta, and were pelted with mud by furious crowds. The anger against the management of the natural disaster by authorities has been significant, with particular criticism being made against the tardiness of flooding alerts.
Vigilante protection groups have been reported as setting up patrols in towns such as Pairporta, highly likely due to the perception that the authorities have failed to provide adequate support. The Spanish Prime Minister Pedro Sanchez has stated that 15,000 personnel from the military and police forces have now been deployed to aid in recovery efforts.
It is likely that the backlash against authorities stemming from the floods, which were almost certainly the most deadly natural disaster in modern Spanish history, will continue to lead to instances of civil unrest.
No humanitarian aid to enter north Gaza Strip, state Israeli officials
On 5 November, Israeli Defence Forces (IDF) officials stated that, due to the threat of Hamas re-infiltration and the exodus of civilians, no humanitarian aid will be allowed to enter the “northern Gaza Strip” (highly likely indicating the area north of the new corridor that cuts off Beit Lahia, Beit Hanoun and Jabalia from the rest of the Gaza Strip). The announcement, which coincides with a significant increase of Israeli operations to clear remaining Hamas fighters from the north of Gaza, highly likely signifies the long-term displacement of residents of northern Gaza to the south. It is highly likely that such a scenario will put further pressure on the already overstretched humanitarian efforts present elsewhere in Gaza.
Nigeria suffers ninth major blackout of 2024
Nigeria’s national power grid experienced a partial collapse on 5 November causing widespread blackouts, marking the ninth such incident in 2024. The Transmission Company of Nigeria (TCN) stated the disturbance was caused by multiple line and generator failures which destabilised the system. Power was quickly restored to Abuja, but outages persisted in other regions, with the grid currently only capable of distributing a third of Nigeria’s energy output. Suspensions in power often force people to rely on costly fuel generators and have often been a trigger for unrest in Nigeria, exacerbated by other underlying issues such as high inflation and accusations of corruption.
Asia–Pacific
India: Jammu and Kashmir’s assembly passes resolution demanding a restoration of special status
On 6 November, Jammu and Kashmir’s legislative assembly passed a resolution demanding partial autonomy be restored to the Indian-administered territory. While the resolution is non-binding, it calls for dialogue to be initiated with the government of India. This decision comes in the wake of the Jammu and Kashmir National Conference (NC) winning the first regional election in a decade on a platform of a return to self-rule.
Solace Global Assessment:
The resolution is highly likely to lead to unrest. The BJP has rejected the resolution, labelling it illegal and akin to “waging a war against the Indian constitution, Supreme Court, and Parliament”. This is a tense issue since India’s Hindu nationalist Prime Minister Narendra Modi’s Bharatiya Janata Party (BJP) rejected the territory’s special status in 2019 by repealing Article 370, which had granted the region semi-autonomy since 1954. While resonating among the Indian Hindu community, Kashmir’s Muslim population heavily opposed the decision, fearing demographic changes in the region from Hindus purchasing land.
Because of the expected unrest, the BJP initiated a heavy security crackdown, consisting of a curfew, the arrest of political leaders, the suspension of internet and communications services, and the deployment of tens of thousands of additional troops to the territory to prevent unrest. Widespread unrest occurred, nevertheless, with protestors defying curfews and clashing with security forces. Security forces responded forcefully, using tear gas and rubber bullets to quell unrest.
If significant unrest breaks out in Jammu and Kashmir, it is highly likely to spread amongst the Muslim community in India. Tensions have been high between Hindus and Muslims since Modi’s winning of power in 2014. A Hindu nationalist, Modi has been accused of marginalising the Muslim community and encouraging anti-Muslim sentiment.
Since Jammu and Kashmir is the only India-administered region with a Muslim majority, protests in support of the territory have erupted during periods of heightened tension. After the rejection of Article 370, for example, Muslim demonstrations occurred across multiple major cities including Delhi, Mumbai, and Kolkata. The NC’s mandate to negotiate the issue of self-rule for Jammu and Kashmir is, therefore, likely to act as a trigger for unrest.
Philippines: Filipino forces simulate island invasion
On 6 November, Filipino forces staged a military exercise in the South China Sea which, for the first time, included a mock scenario in which allied forces retake an island after its invasion by a hostile force. The exercise took place in Kota/Loaita Island, part of the Spratly Islands chain, contested by China, Vietnam and Taiwan. Chinese warships were present in the waters near the island for the duration of the exercise, although Beijing avoided reacting to the episode.
Solace Global Assessment:
The exercise, the first Filipino combat exercise in the contested area, is almost certainly meant to send a signal to Beijing regarding Manila’s determination to defend the Spratly Islands. The Chinese and Filipino coast guards have recently engaged in low-intensity clashes in the South China Sea, with repeated cases of vessel collisions and clashes between crews. Chinese vessels have also recently had incidents with the coast guards of Indonesia and Malaysia.
Furthermore, the exercise coincided with the announcement that Filipino forces have almost finished improving hangar facilities and other infrastructure on Pagasa Island, also in the Spratly chain. The improvements carried out on Pagasa, which cost at least USD 50 million, are likely meant to strengthen the Philippines’ position in its western waters while simultaneously also seeking closer cooperation on defence with the US and other Western partners.
It is notable in this sense that recent Filipino procurement efforts have moved in directions favourable to Washington, for instance via the purchase of Aero-class gunboats from Israel as part of its efforts to bolster its South China Sea maritime presence.
For Manila, increased spending and high-visibility military exercises may also be a way to “keep Washington close” during the next administration’s term. While the first Trump administration began an openly confrontational stance vis-à-vis China, the President-elect has also repeatedly stated that he sees US defence assistance as dependent on partners’ willingness to play to Washington’s global economic interests and to “foot the bill” of military expenditure.
As in the case of Taiwan, whose leaders approved the purchase of USD 2 billion in arms from the US in October, the Philippines likely has an interest in demonstrating its capability to incur greater costs in directly containing Chinese expansion in the southwestern Pacific Ocean.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Myanmar junta chief on rare foreign trip
On 6 November, the leader of Myanmar’s Tatmadaw junta, Min Aung Hlaing, arrived in China for his first visit since the 2021 coup that precipitated the country’s civil war. In addition to meeting their Chinese counterparts, Tatmadaw officials also held informal talks with representatives of Thailand, a key neighbour of Myanmar with which it shares a 2,400 km border.
The junta’s talks with China are likely meant to restore some level of political confidence in Min Aung Hlaing, whose handling of the civil war has been marked by increasing setbacks for the junta in its fight against a myriad of ethnic and nationalist rebel groups. This has likely worried officials in Beijing, challenging their willingness to possibly bear the growing political cost of maintaining the junta as its preferred diplomatic interlocutor.
The question of the Myanmar-Thailand border is likewise almost certainly essential. The area has become an active conflict zone, with some clashes having spillover effects into Thai territory. Moreover, the breakdown of stability has created room for manoeuvre for organised criminal groups engaged in smuggling weapons and drugs. Myanmar has returned, in 2023, to being the biggest producer of opium globally, after the Taliban cracked down on opium farming in Afghanistan.
Security, Armed Conflict and Terror
Iran and Pakistan conduct joint operations in Balochistan
Uncorroborated reports indicate that Iran and Pakistan are conducting joint operations against militants in Iran’s Sistan and Balochistan province, and Pakistan’s Balochistan province. The intended targets of the strikes are reportedly senior leadership of the Baloch Sunni militant group, Jaish Al-Adl, and follow a recent meeting between the Iranian and Pakistani Foreign Ministers in Islamabad, where they agreed to cooperate on cross-border security and terrorism. It is highly likely that Jaish Al-Adl will conduct reprisal attacks in both countries as a result of the strikes.
Militants establish pattern of attacking police officers in southern Thailand
On 4 November, a senior police officer in Thailand’s troubled Pattani province was shot at and injured by assailants after returning from evening prayers. This marks the third recent attack on serving or former police officers returning from mosques in southern Thailand and may indicate a trend of separatist militants targeting Muslim police who they perceive as collaborators.
Indonesia holds first ever joint naval drills with Russia
On 4 November, the Indonesian Navy conducted joint military exercises with elements of the Russian Federation Navy’s Pacific Fleet in the Java Sea. The drills are the first to be held between the two respective navies and likely mark a step towards greater defence ties after the recent inauguration of Indonesian President Prabowo Subianto. However, Jakarta has stressed it remains committed to a non-aligned foreign policy with the exercises aimed at promoting regional security rather than being directed against any other country or military alliance.
New Zealand mosque targeted in arson attack
On 5 November, a mosque in Auckland, New Zealand, was reportedly deliberately set on fire. While attribution for the fire remains unclear, reports from 6 November indicate that authorities charged a 19-year-old man over the arson. If confirmed, there is a high likelihood that the attack was an ideologically motivated action meant to terrorise the local Muslim community. Arson targeting places of worship frequently appears in anti-Islam rhetoric within far-right online spaces. Furthermore, arson is often linked to conspiracy theories and narratives alleging that events such as the 2019 Notre Dame fire were caused by Islamist terrorists.
Environment, Health and Miscellaneous
Pakistani regional government shuts schools over high air pollution levels.
On 6 November, authorities in the Punjab province of Pakistan ordered schools in some areas to shut down for up to two weeks over extremely high pollution levels, which pose a significant threat to the health of children. The province contains Lahore and about half of Pakistan’s total population and is characterised by high levels of vehicle-linked pollution. Swiss group IQAir assessed that the Air Quality Index (AQI) of Lahore was 730 on 7 November, making it the most polluted major city in the world (for comparison, Delhi is in second place and recorded a score of around 360 on the same day).
Indonesia’s Mount Lewotobi Laki-laki erupts, killing several.
On 4 November, Indonesia’s Mount Lewotobi Laki-laki erupted, killing at least ten people and impacting seven villages on Flores Island in East Nusa Tenggara province. Authorities have issued the highest alert, mandating a 7 km evacuation zone and relocating residents to areas 20 km away. Indonesia’s disaster agency has declared a 58-day state of emergency to support 10,000 affected residents, warning of potential flash floods and cold lava flows. Smaller eruptions occurred from 5-7 November and due to fears of further deadly eruptions, the government is planning to permanently relocate thousands of people.
Subscribe to free weekly intelligence

We’re proud to share that we’ve achieved an NPS® (Net Promoter Score®) of 83 – a world-class rating that reflects our clients’ trust and satisfaction. But what exactly is an NPS® score, and why does it matter?
The NPS® is a widely used measure of customer loyalty and satisfaction. It’s calculated by asking clients a single question: How likely are you to recommend our services to others?
Our score of 83 places us among the top-rated companies in the risk management industry, indicating that our clients see real value in the services we provide.

“Achieving a world-class NPS® score of 83 means we not only met but exceeded client expectations. Now, our commitment is to keep going beyond what’s expected.”
Shari-Anne Bradnick, Customer Success Manager
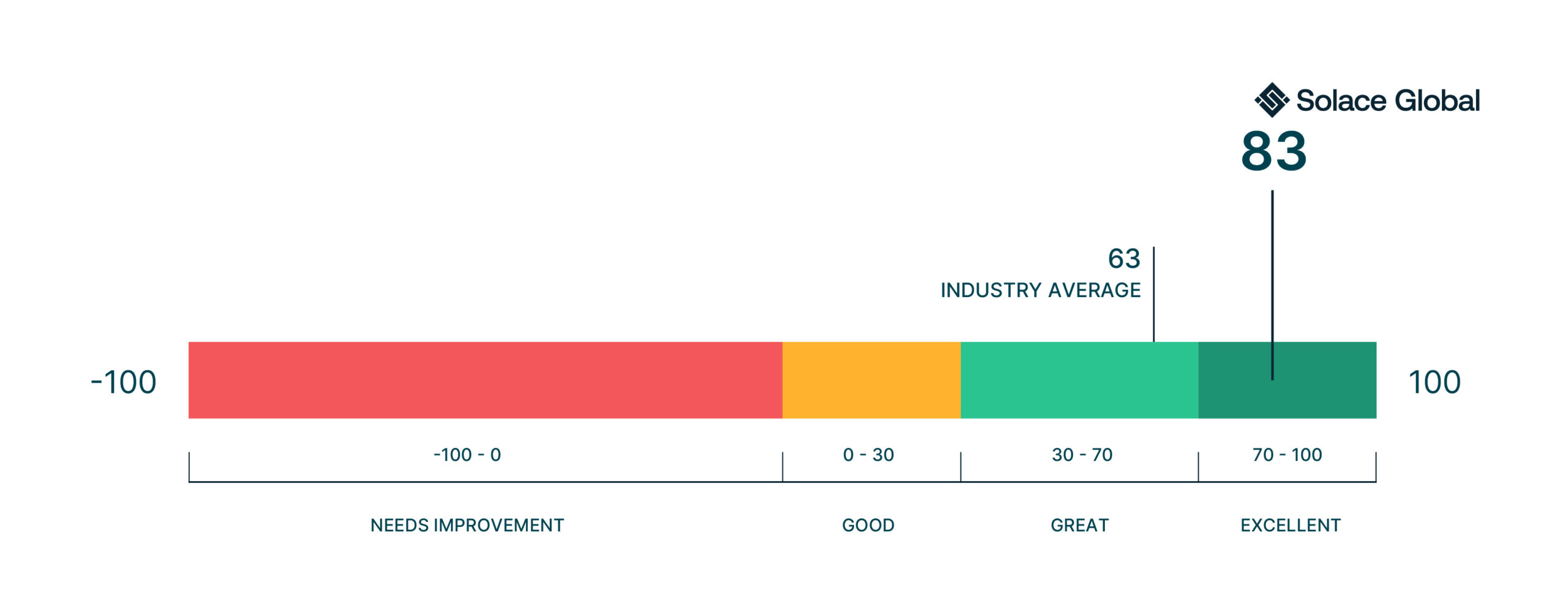
Commitment to Quality in Risk Management Solutions
For Solace, this score goes beyond numbers; it’s a testament to our dedication to delivering people-centred, reliable risk management. Across sectors – from corporate and government organisations to NGOs – clients rely on us for secure, seamless solutions, including corporate security, travel risk management, and journey management. We thank our customers
We are grateful for the continued trust of our clients – because together, we go further.
CASE STUDIES
Discover more from Solace Global
Security Support for Beirut Explosion, Lebanon
Medical & Security Soltions for Caribbean Hurricane
Low Profile Security for Documentary Crew
On the 4th August 2020 an explosion devastated Beirut, killing at least 220 people, injuring more than 6,000 and displacing over 300,000.
In the immediate aftermath of the explosion, Solace Global Risk, a leading provider of risk management solutions, identified the explosion before mainstream media, to promptly make security managers aware and confirm the safety of travellers within Beirut during this critical time.
In the aftermath of Hurricane Maria, a catastrophic natural disaster, the Caribbean region experienced widespread disruption.
A British employee was deployed to the British Virgin Islands to assist in the recovery efforts, with Solace Global assisting with a comprehensive journey management plan, that included security vehicles and highly vetted close protection operatives to safeguard against local threats and disruption.
The production of the series Narco Wars, set across Central and South America, delves into the illicit narcotics trade and the individuals entangled in the drugs cartels. This ambitious project heavily relies on the presence of knowledgeable in-country “fixers” to facilitate smooth filming operations in complex and high-risk locations.
Understanding the inherent risks associated with filming in these challenging environments, Solace Global provided comprehensive solutions to enhance the safety and security of the media team.
Executive Summary
- A claimed assassination attempt on former Bolivian President Evo Morales will almost certainly exacerbate political tensions and help sustain nationwide unrest.
- The Israeli retaliation strikes against Iran have likely severely degraded Iran’s integrated air defence system, highly likely enabling more effective hypothetical future operations by Israel.
- The opposition’s call for a week of strikes and protests in Mozambique will almost certainly result in widespread demonstrations, major disruptions and violent clashes.
- North Korea’s longest-ever ICBM test is likely indicative of its ability to strike the US mainland with nuclear-armed missiles and reflective of Russian technological cooperation.



AMER
Martinique: Unrest continues and curfew is extended
Bolivia: Former president targeted in assassination attempt as unrest continues
Uruguay: Presidential election has no winner and will head to a runoff
EMEA
Spain: Storm DANA results in major flooding and multiple casualties
Georgia: Pro-European rally in Tbilisi ahead of upcoming election
Israel & Iran: Israel conducts strikes against Iran, primarily targeting military sites
Syria: US conducts series of strikes on ISIS targets in Syria
Mozambique: Opposition calls for week-long protests and strikes
APAC
Pakistan: Militants attack health centre to disrupt polio vaccinations
North Korea: Longest-ever ICBM launch conducted
Myanmar: Rebel forces to switch operations to central regions
North, Central and South America
Martinique: Unrest continues and curfew is extended.
Unrest in Martinique continues as French authorities have extended a curfew in five municipalities until 4 November, due to ongoing protests against the high cost of living. The curfew order will now only apply to the municipalities of Case-Pilote, Fort-de-France, Lamentin, Saint-Joseph and Schoelcher, from 00:00-05:00.
Disturbances during the past week have included the attempted erection of barricades in Fort-de-France, the blocking of roads with bonfires in Le Francois and Le Vauclin, and vehicles being set ablaze in Bellefontaine and Fond Lahaye. During the night of 25-26 October, at least one person was killed in La Trinite and four others were injured in multiple incidents of shootings across Martinique, and attacks against police and firefighters using Molotov cocktails and projectiles have continued.
The protests have also led to significant disruptions, such as the suspension of refuse collection in central Martinique and the closure of schools.
One of the main protest organisers, The Rally for the Protection of Afro-Caribbean Peoples and Resources (RPPRAC), released a statement on 27 October denouncing the violence, calling instead for peaceful marches and blockades.
Solace Global Assessment:
Overall, the past week of disorder has highly likely been less intense than in weeks prior. The unrest that started in September was triggered by demands for price parity for basic goods with mainland France, with food prices, for example, being 40 per cent higher in Martinique.
The relative decline in the intensity of violent unrest likely suggests that efforts by authorities to quell the protests, including the curfews, are having an effect, in addition to the ameliorating impact of a deal signed on 16 October that promised to lower the cost of some food items by an average of 20 per cent.
Due to the extent of the commercial and tourism disruption, the President of the Executive Council of Martinique Serge Letchimy stated on 25 October that he had asked France’s Prime Minister, Michel Barnier, for emergency funding relief of EUR 100 million to support “disaster-stricken businesses” in Martinique. The French government, however, announced on 28 October an additional EUR 5.2 billion in national spending cuts, and French austerity will likely be a limiting factor in the level of financial aid available to the Department of Martinique.
Despite the public efforts of RPPRAC to restrain the violence of the protests in Martinique, it is unlikely that the organisation has strong enough influence over the violent fringes of the protest movement. Nonetheless, it is unlikely that the unrest will reach the same scale and intensity as the May 2024 New Caledonia unrest, which precipitated the mass evacuation of foreign nationals.
Bolivia: Former president claims government has attempted to assassinate him
On 27 October, former Bolivian President Evo Morales’ car was fired upon by unidentified men while travelling in the Chapare region, a traditional stronghold for Morales’ supporters. Morales, who shared a video of the incident, has claimed that the attack was an assassination attempt orchestrated by the government of President Luis Arce Catacora.
The government has in turn claimed that the assassination attempt was staged by Morales to gain political traction before the next Bolivian presidential elections scheduled for August 2025.
Solace Global Assessment:
Bolivia has been gripped by severe civil unrest since early October after prosecutors issued an arrest warrant for Morales accusing him of statutory rape and human trafficking. The allegations from both sides of the political divide have almost certainly significantly heightened political tensions in the country, with Morales supporters threatening to paralyse the country.
Roadblocks erected on major roads for over two weeks have disrupted the delivery of essential supplies like food and fuel across the country. Protests in cities like La Paz, Sucre, Santa Cruz and several smaller settlements have involved violent clashes with the police, resulting in multiple injuries and the deployment of tear gas.
President Arce has accused Morales of destabilising Bolivia for political gain and has demanded an end to the disruptions, indicating that it has already cost the Bolivian economy approximately USD 2 billion.
The country’s strained economy – characterised by declining natural gas production, dwindling foreign reserves, and rising inflation has only exacerbated tensions. As Bolivia approaches the 2025 presidential election, the convergence of economic hardship and polarised politics is likely to result in periodic unrest, potentially destabilising the country, undermining its democratic institutions and straining the economy.
Uruguay: Presidential election has no winner and will head to runoff
As no candidate secured a majority in the 27 October presidential election, a runoff vote will now take place on 24 November. The coalition Broad Front’s centre-left candidate Yamandu Orsi won the most votes, with 44 per cent, while the ruling National Party’s centre-right candidate Alvaro Delgado came second with 27 per cent.
The conservative vote was split, with the liberal-conservative Colorado Party candidate Andres Ojeda gaining 16 per cent of the vote. Ojeda has since pledged to back Delgado in the runoff election.
There were also two referenda, the first regarding a pension reform proposal and the second regarding enabling nighttime police raids across the country, with both being rejected by the electorate.
Solace Global Assessment:
The election campaigns were markedly civil and the election in general is almost certainly indicative of the stability and relative lack of political polarisation in Uruguay compared to many other South American countries. There is a broad political consensus among all the leading candidates regarding the continuation of the pro-business policies of the current President Luis Lacalle Pou.
The turnout rate was 89 per cent, though this is almost certainly conditioned by laws that make voting compulsory in Uruguay. While Uruguayan politics has been primarily dominated by two big-tent coalitions, this election was notable in that Ojeda managed to secure 16 per cent.
With the centre-right vote split between Delgado and Ojeda in this first round, it is likely that the runoff election will be a tight contest between Orsi and Delgado.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
Sikh separatist warns of Indian clandestine activity in US and Canada
The Sikh separatist and dual US-Canadian citizen, Gurpatwant Singh Pannun, has warned of an established Indian intelligence network operating in the US and Canada. Pannun alleges that India is directly targeting Sikh separatists in North America, which includes attempted assassinations.
The accusations are likely to strain relations between India the US and Canada and have the potential to drive greater radicalisation of the Sikh community both within India and North America.
The Canadian signals intelligence agency, Communications Security Establishment (CSE) has also warned that the dispute is likely to lead to an increase in Indian cyber espionage targeting the Canadians.
Mexican government curbs power of the judiciary
Mexico’s lower house, the Chamber of Deputies, has approved a measure that bars judicial review of constitutional reforms, reinforcing changes advanced by the ruling party, Morena, and its allies. With Senate approval last week, the measure prevents the judiciary from challenging reforms, including the recent judicial overhaul. Opposition lawmakers have lambasted the move as authoritarian, over concerns regarding judicial independence. The latest reform has resulted in eight of eleven justices on Mexico’s Supreme Court resigning and is likely to lead to unrest in several parts of the country.
Argentina to champion diplomatic route to gain Falkland Islands
In response to the UK’s handing over of the Chagos Islands to Mauritius, President Javier Milei of Argentina has stated that it is possible to gain control of the Falkland Islands via diplomatic processes despite UK claims that its sovereignty is non-negotiable. Argentina’s foreign minister has also stated that the conditions are now in place to resume flights between Argentina and the Falklands after four years of suspension, in a move that is likely reflective of a more conciliatory approach from Buenos Aires.
Island-wide power outage and unrest in Guadeloupe
Striking Electricite de France (EDF) workers caused an island-wide power outage in the French overseas department of Guadeloupe on 25 October after giving rise to an emergency shutdown at the Pointe Jarry thermal plant.
The outage had initially left the entire French Caribbean territory in darkness, disrupting water supply and internet access. By 26 October, power was gradually being restored, with 77 per cent of customers having electricity back by the evening, and full restoration was achieved by 27 October. The strike, which began in September, is unrelated to the more severe civil unrest in Martinique. However, there were reports of looting in Pointe-a-Pitre, and authorities imposed a curfew in ten municipalities in response to these incidents and the blackout.
Security, Armed Conflict and Terror
Haitian gang attacks lead to US evacuations
The US is set to evacuate 20 embassy staff from Port-au-Prince, Haiti in response to escalating violence in the city. Criminal gangs have increased their assaults on the remaining areas of the capital outside of their control, with recent developments including opening fire on a UN World Food Programme (WFP) helicopter and attempts to target US embassy vehicles.
The WFP is becoming increasingly reliant on aircraft to complete its mission, with roads being deemed too dangerous due to gang attacks and the establishment of roadblocks. The gangs are likely attempting to attack all foreign entities assisting and disrupting aid deliveries to undermine the government and assert their influence over the country.
Increased gang violence is also likely indicative of Kenya’s failed intervention to reestablish law and order in the country.
Mexican authorities fail to curb cartel violence in Sinaloa State
A wave of cartel violence has continued in the Mexican state of Sinaloa, which Mexico is blaming on the US for the July arrest of cartel leader Ismael “El Mayo” Zambada. At least 14 people were murdered on 26 October alone, with most of the killings occurring in the state capital, Culiacán, where clashes between criminal groups have disrupted daily life and led to school and business closures.
Since 9 September, authorities have reported almost 200 fatalities and over 200 missing persons despite the mass deployment of troops from other parts of Mexico.
Argentina discloses head of Hezbollah operations in Latin America
Argentina’s Defence Minisiter Patricia Bullrich has publicly identified the head of Hezbollah operations in Latin America as Hussein Ahmad Karaki. She also alleged that he was responsible for the 1992 Israeli Embassy and 1994 Argentine Israelite Mutual Association (AMIA) bombings in Buenos Aires, which collectively killed over 100 and injured around 500.
The accusations indicate that Hezbollah operations in South America are facilitated by Venezuela and that the Iranian-backed group had established direct ties to organised crime groups in the region, especially the Brazilian cartels Primeiro Comando da Capital (PCC) and Comando Vermelho, which have reportedly become narco-terrorist networks under Hezbollah’s influence and have been responsible for much violence.
Environment, Health and Miscellaneous
Mexico to celebrate Day of the Dead festival on 2 November
An estimated seven million people will take part in Mexico’s, Día de los Muertos, or Day of the Dead festival on 2 November, which will culminate in a major procession in central Mexico City. Almost 20,000 extra security personnel will be deployed, and major traffic disruptions are anticipated in the capital city. Whilst the festival is typically peaceful, it has sometimes led to impromptu protests and clashes with the authorities, with the recent judicial overhaul potentially serving as a catalyst for unrest.
Europe, Middle East & Africa
Spain: Storm system DANA causes devastating flooding
On 29 October, an entire year’s worth of rain fell in just eight hours in parts of the Valencian Community (the political and administrative region), leading to severe flash flooding. The death toll across Spain is currently 158, although this is highly likely to rise in the coming days.
Almost all of the deaths occurred in the Valencian Community, although flooding also occurred in Castile-La Mancha, Andalusia, Aragon and Catalonia. The Valencia and Castellon provinces in the Valencian Community suffered the worst impact, particularly the towns of Torrent, Pairporta and Chiva, with rescue operations still ongoing.
Over 150,000 people lost power, and mass disruptions to transport were caused, with dozens of flight cancellations at Valencia Airport and the suspension of most train services in the region.
Solace Global Assessment:
DANA is a Spanish acronym for high-altitude isolated depression. These storm systems develop due to the convergence of cold and warm air, which can form independently of polar or subtropical jet streams. Due to Spain’s location between the Atlantic Ocean and the Mediterranean Sea, the country is especially vulnerable to the formation of such storm systems, particularly in the east and south.
While it will take time to determine a definitive connection between this particular storm and climate change, the mainstream consensus amongst the scientific community is that climate change highly likely worsens both the frequency and intensity of these weather events.
With 158 deaths so far reported, the storm has caused the most flood-related deaths in Europe since the 2021 European floods, which caused over 200 deaths, primarily in Germany and Belgium. Storm system DANA has also highly likely caused one of the deadliest natural disasters in modern Spanish history.
There is a realistic possibility that backlash against perceived inadequacies in the preparedness measures of authorities will lead to incidents of civil unrest.
Firstly, criticism has been made regarding the inadequacy of accurate forecasts for heavy rainfall being solely sufficient to forewarn populations of the imminent threat to life.
Secondly, evacuation alerts were allegedly sent to people’s phones too late in multiple reported instances, having been triggered when substantial flooding had already occurred and reportedly leading to panicked fleeing evacuees being forced to abandon their vehicles and urgently seek refuge due to already severely rising floodwaters. Developed economies that regularly experience tropical cyclones, such as Taiwan, have developed rigorous preparedness and resiliency measures that mitigate against the worst impact of storm-related flooding. Due to the relative infrequency of such events in Europe, however, many European states do not yet have equivalently comprehensive disaster management procedures.
Syria: US conducts series of strikes on ISIS targets in Syria
On 28 October, US Central Command (CENTCOM) conducted a series of airstrikes targeting Islamic State of Iraq and Syria (ISIS) camps in the Badiya Desert in southern Syria. The strikes reportedly killed up to 35 ISIS insurgents, including senior leadership. CENTCOM has announced that the strikes will disrupt ISIS’ ability to “plan, organize, and conduct attacks against civilians, as well as U.S., allies, and partners throughout the region and beyond.”
Solace Global Assessment:
The CENTCOM strikes are part of a wider trend of US and coalition forces targeting a resurgent ISIS throughout the region, which still presents a credible threat in both Iraq and Syria. The targeting of senior leadership will almost certainly help to deny ISIS’ resurgence, especially in the Badiya Desert on the Iraqi border where there is minimal coalition activity.
However, multiple regional and international developments are working in the favour of ISIS regrouping. Firstly, the war between Israel and Hamas has likely increased rates of radicalisation and a potential wider conflict has diverted attention and resources away from ISIS. Additionally, expanded Turkish operations in Iraqi and Syrian Kurdistan have overstretched Kurdish forces, who were pivotal in the defeat of the caliphate.
Most importantly, the US is set to conclude a phased withdrawal of its 2500 troops from Iraq by 2026. If Iraqi forces are ill-prepared to deal with the ISIS threat, the terrorist group will likely exploit a reduced security presence and intelligence gaps to re-emerge in Iraq, enabling it to also regroup in Syria. This development could set the conditions where ISIS can recruit, raise funds and increase its attacks with the ultimate objective of destabilising the region and reasserting its influence. In the long term, a resurgent ISIS will likely be in a better position to plan and conduct external operations in places like Europe. Moreover, a stronger ISIS in the Levant may enhance its ability to coordinate efforts with the Islamic State’s network of affiliates such as Islamic State Khorasan Province (ISKP) in Afghanistan, and a host of other affiliates spread throughout the world.
Georgia: Georgian Dream party claims victory in elections amid allegations of fraud
According to the published 26 October parliamentary election results, Georgian Dream won almost 54 per cent of the vote, despite all exit polls aside from the one commissioned by the pro-government Imedi TV predicting victory for the combined vote of the opposition parties. The pro-Europe President Salome Zourabichvili refused to accept the election results and called for protests in Tbilisi. Tens of thousands gathered outside the Georgian parliament building on 28 October, contesting the election result and demanding a re-run.
Solace Global Assessment:
Relative to both the scale and levels of violence in the protests against the “foreign agents” bill in March 2023 and April-June 2024, the post-election demonstrations thus far have been smaller and calmer. It is likely, however, that the civil unrest will grow in both size and intensity over the coming weeks.
Following President Zourabichvili’s refusal to accept the results and her call for protests, Zourabichvili was summoned to the Prosecutor’s Office to testify. While this is ostensibly due to possible evidence Zourabichvili has that is relevant to an investigation regarding the allegations of election fraud, Zourabichvili has indicated a refusal to comply, likely due to fears of institutional backlash against the Georgian opposition.
Meanwhile, international reaction has almost certainly further inflamed the stark political divisions in Georgia. Russian former President Dmitry Medvedev publicly called for the “puppet President of Georgia” to be impeached and arrested, the European Commission has stated that the election irregularities “must be clarified and addressed”, and US President Joe Biden expressed deep concern about “recent democratic backsliding”.
It is likely that political violence from Georgia’s far-right against the opposition will increase, and it is likely that further opposition demonstrations will involve violent clashes between protesters and security forces.
Iran & Israel: Israeli retaliation attack against Iran primarily targets air defence and military-industrial sites
Following a large-scale missile attack by Iran against Israel on 1 October, Israel conducted retaliation strikes against Iran on 26 October. These strikes were primarily limited to military targets, particularly targets relating to Iran’s air defence and long-range fire capabilities. Over 100 aircraft, including F-15s, F-16s, possibly F-35s and uncrewed aerial vehicles (UAVs), were used in the attack which has been codenamed by Israel as Operation Days of Repentance.
Approximately 20 targets in the vicinity of Tehran and western Iran were struck, including three to four S-300 air defence batteries, air defence command-and-control sites, radars (including a sophisticated Ghadir early detection radar in Ahvaz), and defence industrial sites such as the Parchin and Khojir complexes near Tehran. Additionally, satellite imagery reveals damage to a storage unit at the Abadan Oil Refinery in Khuzestan.
Solace Global Assessment:
In the aftermath of Iran’s 1 October attack against Israel, multiple possible scenarios of Israeli retaliation strikes were assessed to be plausible (and in some instances threatened by Israeli officials and politicians), each with varying degrees of potential escalatory impact. These included decapitation strikes against high-profile Iranian figures, strikes against Iran’s oil production facilities and energy infrastructure, and strikes against Iran’s nuclear program.
Overall, the strikes were ultimately primarily limited to military targets, which is highly likely one of the least escalatory scenarios that could have occurred. Nonetheless, the degradation of Iranian air defence capabilities has sent a strategic message to Tehran, highlighting Israel’s ability to penetrate Iranian air defence and likely setting the conditions that will increase the success rates of future Israeli operations against Iran.
Despite calls for strikes against Iran’s nuclear program, it was unlikely that such operations could have been anything more than symbolic, due to the requirement to use airframes carrying bunker-busting bombs that would need to penetrate deep into Iranian airspace and be highly vulnerable to air defence and interdiction. Nonetheless, the strikes on the Parchin complex are related, as the complex has likely been previously used for high explosives testing as part of its nuclear weapons development program, and traces of uranium were found at the site by international inspectors in 2015, although there is no indication that the site is currently used for Iran’s nuclear program.
However, by degrading Iran’s ballistic missile development and manufacturing capabilities, there is a realistic possibility that Iran’s nuclear ambitions have been hampered, as ballistic missiles would almost certainly serve as delivery systems for nuclear warheads. It is also likely that the Iranian supply of ballistic missiles to Russia and Axis of Resistance (the informal network of Iranian-backed and supported groups, ranging from Hezbollah to the Houthis) members will be disrupted as a result of the strikes, with the provision of ballistic missiles to Russia by Iran thought to be a particular danger to Ukraine due to the weaknesses in Ukraine’s air defence in intercepting ballistic missiles.
While damage has been reportedly confirmed at oil facilities in Iran, such as the storage unit at Abadan oil refinery, the main targets in the vicinity of Iranian energy infrastructure struck were air defence sites and it is unlikely that Iran’s oil production has been meaningfully impacted. This highly likely reduces the risk that retaliation by Iran and Iran-backed proxy forces will be against Western energy interests in the region, as was previously threatened by Iranian officials if Iran’s oil industry was significantly targeted. The attempts by various senior defence officials and politicians to characterise the strikes as “minor” may influence Iran to refrain from a major retaliation; however, threats of retaliation have still been made. Any response from Iran is likely to be limited and strategically designed to remain below the threshold that would provoke further significant Israeli operations.
Mozambique: Opposition calls for week-long protests and strikes
Since Mozambique’s electoral commission declared that Daniel Chapo of the incumbent FRELIMO party had been elected president on 24 October, the country has struggled with civil unrest provoked by accusations of electoral fraud. On 29 October, the opposition candidate Venâncio Mondlane called for week-long protests and strikes beginning on 31 October. Reporting from Mozambique is currently limited; however, there are indications on social media that protests are ongoing across many of the country’s largest cities, including Maputo, Beira, and Nampula.
Solace Global Assessment:
Mondlane’s calls for nationwide protests will almost certainly result in widespread unrest and violent confrontations with the security services. Mondlane is hugely popular with Mozambique’s youth who are primarily involved in the recent unrest which erupted in several major cities across the country.
However, the internet observatory group, NetBlocks, which monitors and reports on internet disruptions has warned that social media and messaging platforms in Mozambique have been restricted, making it challenging for external observers to accurately monitor the scale and nature of the unrest. These measures are almost certainly representative of the government’s attempt to disrupt the spread of unrest and obfuscate its violent handling of the protests.
Local medical groups have warned that the government’s previous crackdown on post-election protests involved the firing of live ammunition which resulted in at least ten deaths and 63 injured, although the real numbers are likely much higher. The government’s use of violence to suppress unrest has almost certainly increased tensions and will act as a catalyst for further unrest.
Aid workers have stated that the unrest has disrupted the delivery of humanitarian aid to the northern Cabo Delgado region where members of al-Shabab, a local Islamist group affiliated with the Islamic State, but distinct from the Somalian-based group, have been targeting local communities. There is a realistic possibility that militants will exploit the current unrest to conduct attacks on local communities and the security services.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
UK Conservative Party set to announce new leader
Following Rishi Sunak’s resignation, the Conservative Party are set to appoint their new leader. The remaining candidates, Kemi Badenoch and Robert Jenrick, are both from the right of the party, potentially signalling a shift in policy towards more traditional conservative values to counter the Reform Party. Such a shift could help legitimise some of the ideas of the far-right, potentially leading to a more polarised UK, anti-migrant rhetoric and increased incidents of far-right violence.
Second round of Moldovan presidential runoff set for 3 November
Two weeks after the first round of a presidential election and EU accession referendum marked by significant Russian interference, Moldovans will go to the polls in the second round of the presidential election. Pro-Western President Maia Sandu, who secured the most votes in the first round, will go head-to-head with the pro-Russian candidate Alexandr Stoianoglo. Russian disinformation campaigns and cyber-attacks attempting to influence the election are likely and the authorities have also warned of Russian-backed criminal groups attempting to disrupt the electoral process.
Security, Armed Conflict and Terror
Lebanon’s Hezbollah appoint Naim Qassem as new leader
Following the death of long-term leader Hassan Nasrallah in an Israeli airstrike, Hezbollah has appointed Naim Qassem as the new Secretary-General of the militant group. Israel has dismissed Qassem’s appointment as temporary and has almost certainly designated him as a tier-one target, and reports indicate he has sought shelter in Iran.
However, the assassination of Hamas’ Haniyeh demonstrated Israel’s reach, with a further assassination on Iranian soil likely to provoke Iran into retaliatory attacks. Early indications suggest Qassem may seek a more cautious approach than his predecessor, potentially opening the door for a truce with Israel.
However, there is a realistic possibility that his relocation to Iran and alleged poor leadership may jeopardise Hezbollah’s ability to maintain cohesion within the group.
JNIM claim attack on Nigerien military on outskirts of capital
On 26 October, the Islamist group and al-Qaeda affiliate Jama’at Nasr al-Islam wal-Muslimin (JNIM) claimed an attack on a Nigerien army checkpoint just 10 kilometres from the capital Niamey. The attack purportedly killed one soldier and resulted in JNIM seizing weaponry and military equipment.
This incident marks the closest jihadist attack to Niamey since the military coup in July 2023, highlighting the growing threat posed by armed groups in the region and potentially a change in strategy. The attack follows recent JNIM attacks in the regional capitals Ouagadougou and Bamako, with militants likely attempting to destabilise the country and undermine junta governments by attacking their centres of authority which are also used by international organisations to coordinate humanitarian efforts.
Boko Haram attack kills 40 Chadian soldiers
At least 40 Chadian soldiers were killed on 27 October after the Islamist group Boko Haram attacked a Chadian Army garrison in the Lake Chad region. The attack has resulted in Operation Haskanite, the aim of which is to hunt down and root out the hundreds of Boko Haram militants responsible for the attack in the vast Lake Chad region, which the group have exploited as a safe haven. Boko Haram are almost certainly taking advantage of the wider destabilisation of the Sahel to conduct increased attacks, with attacks in Chad likely designed to undermine the Chadian government and to divert resources away from their traditional stronghold in northern Nigeria.
Sudan’s RSF kill hundreds of civilians in El Gezira village raid
The paramilitary force known as the Rapid Support Forces has been implicated in one of the deadliest attacks of the Sudanese civil war after Al-Suhra village in El Gezira State was attacked. The raid is estimated to have killed at least 124 people, mainly civilians. The attack follows the recent surrender of a high-ranking RSF officer and is likely an example of a revenge attack on communities supporting government forces and is also likely an example of genocide. These attacks have increased rates of displacement in Sudan, with the UN indicating that almost 50,000 had been displaced within only the last week. The attacks have also included the mass rape of women and girls, leading to high rates of suicide. With the highly mobile RSF pressing on multiple fronts, the Sudanese Armed Forces are likely becoming increasingly incapable of defending rural communities.
Ghana rejects notion that it is safe haven for Sahelian militants
Ghana’s government has dismissed claims that Islamist militants from Burkina Faso are exploiting northern Ghana as a logistical and medical support base. The claims indicated that militant groups like Jama’at Nasr al-Islam wal-Muslimin (JNIM) are using Ghana to sustain operations in the Sahel and has even established a de facto non-aggression pact with Ghana, a claim Accra refutes. It is likely that militants are currently refraining from conducting attacks in Ghana so as to not disrupt their supply lines into neighbouring Burkina Faso. However, if Ghana begins to change its strategy towards the militants, potentially in response to external pressures, it is likely that militants will adapt and seek to destabilise northern Ghana through direct attacks.
Environment, Health and Miscellaneous
Storm Jacob to hit southern Sweden
As of 1 November, Storm Jakob has hit southern Sweden, causing major weather disruptions. Yellow weather warnings are in effect for northern Gotland and southern Svealand, signalling potential hazards and disruptions to daily life with several ferry services to Gotland already cancelled.
UK confirms first case of new Mpox strain
The UK Health Security Agency (UKHSA) has confirmed the first case of the Clade Ib variant of mpox (formerly known as monkeypox) in the UK. Detected in London, the authorities stated that the patient had recently travelled to Africa. However, the UKHSA has stated that the risk to the public remains low, with health officials tracing fewer than 10 direct contacts.
Mauritius bans social media access in run up to general election
On November 1, Mauritius’s communications regulator ordered a suspension of social media access from November 1 to 11, following a wiretapping scandal which involved the leaked conversations of politicians and other senior figures. Prime Minister Pravind Kumar Jugnauth’s office stated the restriction is necessary due to the publication of sensitive audio clips. However, the opposition and civil society groups have criticised the decision, stating that it will harm the economy and deny a fair democratic process. The denial of access to social media platforms has likely been done to limit the public’s exposure to the leaked audio and to disrupt the organisation of protests during the election.
Asia–Pacific
Pakistan: Militants attack health centre and police involved in polio vaccination drive
On 29 October, militants attacked a health centre in Orakzai, a district in Khyber Pakhtunkhwa province in western Pakistan, leading to the deaths of two police officers and three militants. The health centre was involved in an anti-polio campaign and health workers were attacked as they prepared to go on a door-to-door vaccination campaign, which is typically escorted by the police.
No group has claimed the attack; however, the location is within a traditional stronghold of the Pakistani Taliban (Tehreek-e-Taliban Pakistan, or TTP).
On 1 November, at least seven people were killed after an improvised explosive device (IED) detonated near a girl’s school in southwestern Pakistan in the restless Balochistan province. The police claim that the intended target was police van which was going to pick up a polio vaccination team.
Solace Global Assessment:
Whilst no militant group has claimed responsibility for the attack in Khyber Pakhtunkhwa , the location and nature of the attack indicate that it was likely conducted by the TTP. Islamist militants in Pakistan and Afghanistan have long held the belief that polio vaccination drives are part of a Western conspiracy to sterilise Muslim children, a belief that has been reinforced by years of propaganda and misinformation. This has resulted in Pakistan and Afghanistan being the only two countries in the world where the spread of polio has never been stopped.
A recent resurgence of polio cases in the region has prompted vaccination drives in both countries. The Taliban administration in Afghanistan has moved away from its previous stance on polio vaccinations and authorised the resumption of nationwide immunisation campaigns, including allowing female health workers to participate. However, it is likely that the TTP and many extremists still harbour the belief that polio vaccination campaigns are part of a Western conspiracy and that female health workers should not be allowed to participate.
The location of the IED attack in Balochistan may indicate that separatist groups like the Balochistan Liberation Army (BLA), who are most active in the area, have also adopted the belief that vaccinations are a Western conspiracy. The recent attack underscore these beliefs and indicates that militants throughout the region are likely to attack health workers and healthcare facilities linked to the immunisation programmes, attacks that will likely disrupt the programmes and hinder regional efforts to eradicate polio.
North Korea: Longest-ever ICBM test conducted
On 31 October, North Korea conducted a test fire of an upgraded intercontinental ballistic missile (ICBM) in what Pyongyang has described as the “world’s most powerful strategic deterrent” and as a “warning to perceived enemies”. The missile, which can be nuclear-armed, was in the air for 87 minutes, reached an altitude of 7,000 kilometres and flew a distance of around 1,000 kilometres before falling into the Sea of Japan, approximately 200 kilometres west of Hokkaido, outside Japan’s Exclusive Economic Zone (EEZ).
Solace Global Assessment:
The timing of North Korea’s ICBM test is likely aimed at the US and serves as strategic messaging before the 5 November presidential elections. The claimed performance of the ICBM suggests that North Korean ICBMs are now likely capable of reaching the US mainland. Whilst the missile only landed west of Japan, it was fired at a lofted or high arc trajectory, ensuring it would land relatively close to North Korea. If fired on a more horizontal trajectory, the ICBM will likely be able to reach the US, a conclusion determined by the missile’s ceiling and time spent in the air.
The test is also likely an attempt to divert attention from North Korea’s recent controversial decision to deploy troops to Russia and Ukraine in support of the Kremlin. However, this development is likely indicative of increased military cooperation between the two countries. North Korea’s troop deployment may have been guaranteed in exchange for Russian assistance in developing ICBMs. The improved characteristics of North Korea’s ICBM may indicate improved access to Russian technology and expertise.
Closer cooperation with Russia has enabled North Korea to circumvent sanctions and there are early indications that North Korea is slowly being absorbed into a new, informal military alliance with China, Russia and Iran, colloquially referred to as “CRINK”. Such an alliance will likely allow North Korea to procure even more advanced weaponry, such as solid fuel propulsion and improved guidance systems. For Moscow and Beijing, an increasingly capable and aggressive North Korea serves as a strategic buffer to counter the US but will also likely force the West to reassess its military posture and alliances in the region, potentially affecting regional stability.
Myanmar: Rebel commanders to switch focus to central regions after one year of conflict
27 October marked the first anniversary of “Operation 1027”, an offensive launched by the Three Brotherhood Alliance (TBA), a tripartite coalition of ethnic rebel groups including the Myanmar National Democratic Alliance Army (MNDAA), the Arakan Army (AA), and the Ta’an National Liberation Army (TNLA). The TBA has since developed alliances with multiple other ethnic rebel groups, which primarily represent the ethnic minorities of the Karen, Kachin and Shan.
After a year of fighting, the rebel groups have seized large swathes or Myanmar, particularly in the northern and eastern parts of the country. To commemorate the anniversary of Operation 1027, Maung Saungkha, the leader of an ethnic Bamar resistance group, the Bamar People’s Liberation Army (BPLA). Has stated that it will shift its operations to focus on central Myanmar, with the objective of expelling junta forces from the Bamar-majority regions of Sagaing, Magwe, and Mandalay.
Solace Global Assessment:
Established after Myanmar’s 2021 coup, the BPLA differentiates itself from most of the other rebel groups by representing the Bamar people, the ethnic majority in Myanmar, which is the main ethnicity of the ruling junta. The success of the other ethnic rebel groups has likely diverted junta resources to other parts of the country, providing the BPLA with the opportunity to conduct operations in what has traditionally been an area where the junta has consolidated power.
As Bamar rebels, the BPLA is in an advantageous position to coordinate with other Bamar resistance groups and to conduct guerilla warfare in the central regions. This operational shift could challenge the junta’s control over central Myanmar. If the BPLA succeeds in disrupting the junta’s supply lines or compels it to divert resources to defend major cities like Mandalay, this could work to the advantage of rebel forces in other regions, as the junta might be forced to withdraw forces from these areas.
This operational shift could occur as early as November, with the rainy season typically ending in late October or early November, marking the onset of drier conditions that facilitate military operations. However, operations in central Myanmar are likely to attract more international attention and could prompt external powers like China to provide more support for the junta. Central operations will also likely exacerbate the ongoing humanitarian crisis in the region, especially if they threaten major population centres like Mandalay, with this likely leading to higher casualties, more internally displaced persons (IDPs), disruption of essential services and an increased refugee crisis in neighbouring countries like Thailand.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Protesters set fire to Jatiya Party’s office in Kakrail, Bangladesh
On 31 October, the central office of Bangladesh’s Jatiya Party in Dhaka was attacked and set on fire amid escalating tensions. The Jatiya Party, formerly allied with ousted Prime Minister Sheikh Hasina’s Awami League, had announced plans for a rally, prompting opposition from groups critical of the previous administration. Protesters, under the banner “Anti-fascist students, workers, and masses”, marched with torches near the Jatiya Party headquarters in Kakrail. Clashes ensued when individuals from the party’s office allegedly threw bricks at the demonstrators, leading to vandalism and the subsequent fire. This underscores the ongoing political volatility in Bangladesh following Sheikh Hasina’s outsitting in August.
Japan’s ruling coalition fails to maintain its majority
On 27 October, Japan’s incumbent coalition suffered a surprise defeat and lost their majority in the Japanese parliament. The ruling Liberal Democratic Party (LDP) and its coalition partner, failed to achieve a majority in the snap election, with voters likely indicating their disapproval of the government after corruption scandals and poor economic performance. The results have plunged Japan into a political crisis which could be exploited by China through increased intrusions into disputed Japanese territory.
Security, Armed Conflict and Terror
Baluch separatists attack major infrastructure project in western Pakistan
On October 29, 2024, five people were killed in an attack by militants at a dam construction site in Panjgur, Baluchistan, in what is likely another Baloch Liberation Army (BLA) attack on infrastructure projects in the region. Baluch separatists have conducted multiple attacks on infrastructure and foreign interests in the region to disrupt projects which they deem are exploitative and only benefit the central government and their foreign backers like China.
Mass stabbing outside school in Beijing, China
On 28 October, a knife attack near a prestigious primary school in Beijing’s Haidian district injured five people, including three children, with the suspect arrested at the scene. However, this attack is part of a growing trend in China of mass casualty and largely indiscriminate stabbings, with strict guns laws forcing attackers to use bladed articles. These incidents are likely increasing as a result of several domestic issues including economic hardship, unemployment and an increase with mental health issues, with attackers often selecting high-profile targets like schools and shopping malls for maximum publicity.
Environment, Health and Miscellaneous
Filipino authorities place the Metro Manila Department of Health on Code White
In the Philippines, The Department of Health in Metro Manila has placed all hospitals and health facilities in the National Capital Region on Code White alert from 31 October to 2 November. This alert level is a precaution to ensure that medical services are fully prepared to handle the anticipated increase in visitors to cemeteries and heightened travel during All Saints’ and All Souls’ Days.
Largest storm in 30 years leads to fatalities in Taiwan
Super Typhoon Kong-rey has heavily impacted Taiwan and is now affecting eastern China. As of November 1, the typhoon has resulted in two fatalities and 580 injuries in Taiwan, along with extensive damage, including power outages for 150,000 households and significant disruptions to public transport, notably the suspension of Taipei Metro services on overground lines. Cleanup operations are ongoing, and in Kaohsiung, approximately 370 people remain isolated due to flash flooding and landslides that have blocked access, with further landslides in the country likely.
In China, at least 282,000 people have been evacuated from Zhejiang Province as the storm moves northeast. Although Kong-rey has weakened into a tropical storm north of Taiwan, it continues to pose a threat with maximum sustained winds of 78 mph and is expected to bring heavy rainfall and strong winds. The Chinese government has issued an orange typhoon warning in anticipation of further adverse weather.
Subscribe to free weekly intelligence