11 – 17 April
Evacuations from High-Risk Locations Call +44 (0)1202 308810 or Contact Us →
Executive Summary
Americas (AMER)
Haitian gangs will almost certainly continue to expand their territorial control and increase attacks across the country until significant external intervention is achieved.
President Noboa’s securing of a second term in Ecuador was likely achieved by his tough stance on organised crime and will almost certainly result in a continuation of draconian policies aimed at curbing violence.
Europe, Middle East & Africa (EMEA)
The firebombings at French prisons are highly likely an escalation by criminal groups in response to Paris’ efforts to crack down on organised crime. There is a realistic possibility of further attacks on security personnel.
In the likely scenario that Russia does not extend the ‘energy ceasefire’, significant long-range strikes against Ukrainian energy infrastructure and urban centres will likely follow, almost certainly posing risks to civilians.
Lebanon’s push to disarm Hezbollah is unlikely to succeed, with recent moves by the militant group likely aimed at buying time to regroup and continue its armed resistance against Israel.
RSF attacks on displacement camps in western Sudan are likely aimed at forcing displacement, reducing foreign oversight and securing vital ground to undermine the SAF’s control of El Fasher.
Asia-Pacific (APAC)
Further and potentially violent protests are highly likely across India after the government passes controversial amendments to the Waqf Act.
Dangerous driving conditions are almost certain to lead to increased road traffic accidents across Thailand as the country celebrates the Songkran festival.
North, Central and South America
Haiti: Gangs continue attempts to expand territorial control.
Gang violence has continued to spread in Haiti and has resulted in a series of attacks in areas previously assessed as more secure. On 10 April, gangs launched an attack in Léogâne, located approximately 30km west of Port-au-Prince, marking the onset of a surge in violence. This was followed by another gang assault in Gode, situated in the northwest of the country, on 12 April. Additional gang attacks occurred on 13 and 14 April in Madelaine, near the area of Kenscoff, to the south of Port-au-Prince, and the gangs have continued attacks in Mirebalais, approximately 40km northeast of the capital.
In response to the increased violence, the United States Embassy in Haiti updated its security alert to include multiple regions of the country, advising American citizens to avoid travel. In addition, the Heads of Government of the Caribbean Community (Caricom) issued a statement on 14 April indicating that it is deeply concerned over reports of a coalition of armed gangs seeking to seize power by force and “disrupt the transitional arrangements currently in place.” Caricom has called on the international community, particularly the United Nations and the Organization of American States, to take “all necessary measures” to support the Haitian authorities during this critical period. On 16 April, the cruise line company, Royal Caribbean, suspended its port calls to the Haitian tourist destination of Labadee in the north of the country.
Solace Global Assessment:
Recent attempts to expand their area of operations likely indicate a concerted effort to undermine the government’s authority and deny humanitarian aid to areas under gang control, particularly in and around Port-au-Prince (PAP). This strategy is likely aimed at further destabilising the state by making communities dependent on the gangs for access to essential services and will likely involve increased attacks on public services and the looting of critical supplies, as evidenced by the looting of the hospital in Mirebalais.
On 14 April and in reaction to the effective loss of Mirebalais, the Haitian government adopted a “war budget” aimed at combating the gangs. However, the budget only included USD 275,000, indicating the lack of resources available to the government and the urgent need for greater external assistance. Approximately 40 per cent of the budget will go to the Haitian military and police, with nearly 20 per cent being used to enhance security at the border with the Dominican Republic, a key entry point for illicit weapons. The remainder will be spent on social programmes focused on education, health and humanitarian assistance.
However, given the expanding territorial control of the gangs, who have consistently blocked key supply routes, looted critical supplies, and currently maintain near-total control in several regions, it is highly unlikely that the budget will have any meaningful impact in countering the gangs’ influence or restoring state control. Until significant external intervention is achieved, the gangs will almost certainly continue their attempts to expand their control and increase their attacks, resulting in a deterioration in the humanitarian situation.
Ecuador: President Noboa secures second term
On 13 April, President Daniel Nobia was re-elected following the second round of Ecuador’s presidential election. Figure’s released by Ecuador’s National Electoral Council indicate that Noboa received almost 56 per cent of the vote compared to his rival, leftist lawyer Luisa Gonzalez, who secured 44 per cent of the vote. Gonzalez has demanded a recount of the vote, suggesting that the process was marked by ‘grotesque’ electoral fraud and that pre-election polls had put her ahead of President Noboa. The vote was monitored by international observers from the Organization of American States and the European Union, but neither body has released its official reports.
Solace Global Assessment:
Noboa’s re-election was almost certainly secured by his tough stance on organised crime, which closely mirrors the strategies implemented by President Bukele in El Salvador. However, unlike in El Salvador, the imposition of states of emergencies, the mass deployment of the police and the military, and the suspension of many civil liberties have yet to yield a significant improvement in Ecuador’s security environment.
Ecuador’s challenges differ substantially from those faced in El Salvador. Gangs in Ecuador are more sophisticated and involve transnational criminal organisations such as the Mexican Sinaloa and Jalisco New Generation cartels. These organisations have entrenched themselves in Ecuador, seeking to benefit from the country’s porous borders, proximity to the major cocaine producing nations of Peru and Colombia, and to exploit Ecuador’s access to the Pacific Ocean.
Moreover, these transnational criminal organisations are far better funded and armed than the gangs in El Salvador, likely suggesting that an emulation of Bukele’s tactics is not sufficient for effectively addressing the scale of Ecuador’s security challenges.
President Noboa has recently expressed that he is willing to host US military forces in Ecuador and would welcome US support in combating organised crime in the country. The Trump administration’s recent designation of organised crime groups, including the Sinaloa and Jalisco New Generation Cartels, as Foreign Terrorist Organisations (FTOs) could provide a foundation for increased US involvement. The designation, combined with Trump’s commitment to combating organised crime, could result in greater access to intelligence-sharing, specialised resources, and in the long term could potentially involve direct US military support to combat the cartels, although initial Ecuadorian plans only involve the US providing supportive roles, such as intelligence gathering and surveillance operations.
Ecuador is currently constructing a naval base in the city of Manta, and there are proposals to host the US military there. If the US establishes a naval presence on the Ecuadorian coast and is involved in maritime interdiction efforts, this could disrupt cocaine smuggling from Ecuador and ultimately deter transnational organised crime groups from operating in the country, a development that would likely improve Ecuador’s internal security.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
USA gets El Salvador’s support for further deportations
On 14 April, US President Donald Trump met his Salvadoran counterpart, Nayib Bukele, in Washington. The president of the Central American country endorsed Trump’s plans to carry out further deportations of migrants, and possibly US citizens who commit crimes, to his country. Moreover, Bukele backed Trump over the issue of a citizen of El Salvador who was deported despite having protected status, a decision that the White House has refused to reverse.
El Salvador, which in recent years has built massive prisons to house more than 80,000 individuals accused of having ties to criminal groups, has increasingly portrayed itself as a means for the US to “offshore” its migrants abroad. A growing partnership between San Salvador and Washington is likely to drive civil unrest in the US. High-visibility deportations, such as those of the Salvadoran citizen or those of Columbia University activists, are particularly likely to result in protests in large cities and near university campuses.
First report on Dominican Republic roof collapse released
The document was published by the government on 11 April. Notably, the report did not clarify what caused the incident, which killed 221 people at a packed nightclub in the country’s capital, Santo Domingo. The incident is one of the largest mass casualty events in the country’s history and has attracted massive domestic and international attention. Consequently, as more details emerge, there is a realistic possibility of civil unrest, especially if investigations indicate the government was at fault or the accident was a result of corruption.
Deaths of two football fans result in protests in Santiago, Chile
Two individuals, including a minor, were killed during a stampede at the Monumental Stadium on 10 April. On the following day, protests erupted in multiple parts of the capital, including downtown Santiago, La Pintana, Cerro Navia, and San Joaquín. According to local media, protests began peacefully as groups of fans of the Colo-Colo football club gathered near the stadium before a Copa Libertadores match. However, a group of protesters reportedly began to throw rocks at police and passing vehicles. The spread of the protests throughout the night resulted in limited traffic disruptions and some cases of vandalism.
Argentina secures USD 20 billion deal with the International Monetary Fund (IMF)
The announcement follows Buenos Aires’ decision to lift its strict currency controls, which limit the ability for Argentine nationals to purchase US Dollars, and to float the official Peso exchange rate. The IMF has stated that it would transfer USD 12 billion upfront on 15 April, an unusually large amount. The deal is a political victory for President Javier Milei, but the possibility of significant currency devaluation following the deal, which could push inflation higher, may drive short-term civil unrest.
Security, Armed Conflict and Terror
US Army to control parts of the US-Mexico border
On 15 April, the Trump administration announced the emergency transfer of nearly 110,000 acres of federal land along the US-Mexico border within New Mexico. The move is almost certainly part of Trump’s broader efforts to improve border security, disrupt drug smuggling and deter illegal immigration and could authorise the US Army to detain migrants. The move to detain migrants is likely to be challenged in the courts, although US Army personnel would technically not be detaining migrants but rather trespassers on military land.
The land only encompasses a 170-mile section of a nearly 2,000-mile border, but will likely drive migration flows to other parts, potentially enabling law enforcement to focus resources on a more concentrated area. Moreover, approximately 30 per cent of the US-Mexico border is federally owned, suggesting that such a strategy could be greatly expanded to cover additional sections of the border if deemed effective.
Environment, Health and Miscellaneous
Pennsylvania governor’s residence firebombed
On the night of 13-14 April, an individual reportedly broke into Governor Josh Shapiro’s residence and started a fire, which destroyed parts of the building but resulted in no injuries. The perpetrator reportedly turned himself in and stated that he planned to kill Shapiro. Early authority reports state that the perpetrator was motivated by a “deep hatred” for Shapiro.
The incident is almost certainly to be politically motivated and to be linked to the high visibility of the target. Shapiro is one of the key Democratic politicians in the early race for the 2028 presidential nomination and was considered a front-runner to be Kamala Harris’s running mate in 2024. Moreover, there is a realistic possibility that the attack was religiously motivated, as it took place only hours after a Passover Seder dinner.
Increasing signs of volcanic activity from Mount Spurr, Alaska
The US Geological Survey (USGS) has detected hundreds of small tremors within a 30-mile radius of Alaska’s Mount Spurr, resulting in it issuing an advisory warning that the volcano is likely, but not certain, to erupt in the next weeks to months. The volcano lies around 129 km (80 miles) west of Anchorage, the largest city in Alaska, which is comprised of almost 300,000 inhabitants. The authorities have instructed citizens to be vigilant and prepare in case of widespread disruption caused by ash and other volcanic material, which is likely to shut down air travel. However, this has reportedly resulted in panic buying in the area, with locals in anticipation of a state of emergency, amassing food, N95 masks and other critical supplies.
Aftershocks possible after earthquake registered near San Diego, California
On 14 April, a 5.1 magnitude earthquake was registered near Julian, California, with tremors felt in San Diego and as far away as Los Angeles. Initial damage assessments are ongoing, but no major damage has been recorded. However, at least seven aftershocks have been recorded, increasing the chances of structural strain in the affected areas. Governor Gavin Newsom has been briefed, and the authorities are reportedly on high alert to respond to any further seismic activity.
Europe, Middle East & Africa
France: Coordinated attacks against prisons
On the night between 14 and 15 April, coordinated firebombings and shootings occurred at various prisons across the French mainland, including in Valence, Marseilles, Nanterre, and Toulon. Some of the attackers reportedly wrote the acronym “DDPF” on torched police vehicles or prison walls. “DDPF” highly likely means “Droits des Prisonniers Francais” – Rights of French Prisoners. In the early hours of 16 April, another attack was recorded at a prison in the town of Tarascon in southern France, only hours after the French government commented on the first wave of incidents. The attacks, while not resulting in any casualties, are almost unprecedented in scale and scope.
Solace Global Assessment:
French media have claimed that the attacks were carried out by organised criminal groups, and that they are in response to the government’s prison reform efforts. Paris has recently pledged to open a new maximum-security facility in July 2025 to house approximately 100 drug trafficking leaders. Moreover, the government has more broadly intensified its efforts to combat drug trafficking, and drug seizures have increased in 2024 compared to previous years. This has continued in 2025: in March, French police seized ten tonnes of cocaine in Dunkirk in a single raid, an amount which is approximately equal to a fifth of the total seizures of 2024.
The attack almost certainly demonstrates a growing vulnerability of the French state against organised groups, and is meant to send a political message by attacking symbols of France’s security apparatus. French organised criminal groups are extremely well armed and have shown their ability to carry out sophisticated attacks. A notable example of this was the ambush on a prison van that led to the (temporary) escape of jailed drug trafficker Mohamed Amra in May 2024.
The scope and scale of the attacks pose an almost certainly immense pressure on the Macron government, which has long faced accusations of being unable to contain criminality in France. They will, therefore, highly likely force the government to respond aggressively, possibly tackling organised criminal groups in at-risk cities like Marseille, Nice, and Grenoble. However, such a development could result in tit-for-tat escalations on the part of the gangs. There is a realistic possibility of further coordinated attacks targeting security personnel and offices, which would pose a severe threat to bystanders.
Ukraine: Deadliest attack of the year on Sumy City and Kremlin reiterates war goals
On 13 April, two Russian ballistic missiles struck Sumy City during Palm Sunday, killing at least 35 people and wounding 117. The attack is the deadliest strike on Ukraine thus far in 2025. Moscow claims that the attack involved two Iskander ballistic missiles targeting a gathering of Ukrainian personnel, killing 60.
The US President Donald Trump called the attack “terrible”, but he had been told that Russia “made a mistake”. Trump furthermore restated his belief that Ukraine started the war. One of the missiles struck a road in Sumy’s busy city centre, which caused the most casualties.
Local media reports indicate that a medal ceremony for veterans was being held in Sumy on the day of the attack, with Ukrainian President Volodymyr Zelensky sacking Sumy’s regional chief on 15 April for hosting the event.
The attack occurred within the context of an assessed developing new spring offensive by Russian forces in northeastern Ukraine and ongoing attempts by Washington to engage in separate bilateral peace negotiations with both Ukraine and Russia. On 11 April, Trump’s Special Envoy to Ukraine, General Keith Kellogg, suggested that a ceasefire agreement could see partitioned areas of responsibility for Ukraine (as in post-WWII Germany) between an Anglo-French “reassurance force” alongside Ukrainian forces west of the Dnipro River, solely Ukrainian forces in Ukrainian-held eastern Ukraine, and Russian forces in Russian-occupied southern and eastern Ukraine, with a 29-kilometre-wide “demilitarised zone” across the current frontline.
The Kremlin and Kremlin-affiliated media channels rejected the proposal outright, and Russia’s head of the Foreign Intelligence Service and Foreign Minister both reiterated Moscow’s position that peace would require the fulfilment of Russian President Vladimir Putin’s stated war goals from his 14 June 2024 speech.
Solace Global Assessment:
Despite Washington’s efforts to broker a peace agreement between Moscow and Kyiv, the Kremlin has not yet indicated willingness to make even marginal concessions on any of its maximalist war goals. Stated most clearly in Putin’s June 2024 speech, and reiterated this past week, these include: the demilitarisation and ‘denazification’ (regime change with imposed puppet government) of Ukraine, annexation of all southern and eastern Ukraine (including currently unoccupied areas), and enforced Ukrainian neutrality with a ban on joining any security arrangements (particularly NATO).
This has been reflected by Russian military action, with the developing northeastern spring offensive highly likely intended to gain further leverage to achieve these maximalist objectives. The ballistic missile strikes on Sumy City, which resulted in significant civilian casualties, likely reflect Russia’s growing focus on targeting both Sumy and Kharkiv, as the two urban centres present the primary axes for the potential new northeastern offensive.
It is highly likely that intensified Russian strikes against these locations will continue in the coming weeks, with glide bomb and one-way attack uncrewed aerial vehicle (OWA-UAV) attacks already occurring in the days following the 13 April Sumy strikes, posing significant risks to both civilians and foreign nationals operating in these areas.
While Moscow previously presented a more optimistic narrative of the US-Russia negotiations, Kremlin officials have been increasingly forthright about the inability of the talks to provide results. It is likely that Moscow will continue to leverage the talks as far as possible to gain immediate concessions, so that it may better pursue its maximalist war goals on the battlefield.
This assessment is reflected by the likely continued use of the moratorium on long-range strikes against energy infrastructure as a means to pressure Washington to punish Ukraine for violations. Since the ‘energy ceasefire’ was implemented, Russia has accused Ukrainian forces of violations on an almost daily basis, most of which have been unsubstantiated. With the moratorium set to last 30 days and expiring on either 16 April or 23 April (due to the different understandings of when it actually began), there have been no indications yet of an extension. It is likely that Moscow will leverage the unsubstantiated claims of Ukrainian violations to justify not extending the moratorium.
In this scenario, it is highly likely that mass Russian long-range strikes against Ukrainian critical national infrastructure (CNI) will follow. These strikes could further deplete Ukraine’s stockpile of advanced air interceptor munitions (particularly Patriot), a depletion that Moscow is likely motivated to achieve given the reduced likelihood of replenishment under the Trump administration. Previous interceptor shortages, caused by delays in US Congress approval, led to a drastic increase in Russian long-range strike efficacy rates. An increase in strikes against Ukrainian CNI would almost certainly pose considerable risks of collateral damage, with even successful interceptions posing dangers due to debris.
Lebanon: President seeks to disarm Hezbollah this year
Lebanese President Joseph Aoun has stated that he hopes to achieve the disarmament of the Shia militant group, Hezbollah, by the end of 2025. President Aoun stated that his intent is for all of Hezbollah’s weapons to be withdrawn or that their possession will be restricted to the state. He also stated that Hezbollah was ultimately a Lebanese group and that members could join the Lebanese Armed Forces (LAF) if they participated in “absorption courses”. However, President Aoun stressed that Hezbollah would not be able to function as a distinct unit within the Lebanese Army.
A spokesperson for Hezbollah recently commented that the group would be willing to disarm if Israel fully withdraws from Lebanon, with the Israel Defense Forces (IDF) still holding five strategic locations in the south of the country. However, this statement has been denied by key figures within Hezbollah and by the group’s media office.
Solace Global Assessment:
The majority of Hezbollah military sites in southern Lebanon are now under the control of the LAF, after Hezbollah agreed to withdraw from 190 out of 265 positions as part of the ceasefire agreement achieved with Israel in November 2024. While this withdrawal could be interpreted as an act of good faith and a move that is in alignment with the provisions of UN Security Council Resolution 170, it is unlikely to be reflective of a broader effort to disarm or demobilise.
The IDF still maintain key terrain in southern Lebanon, in violation of the same resolution, and Israel’s Defence Minister, Israel Katz, stated on 16 April that IDF units will remain in Lebanon indefinitely to guarantee the security of Israel. It is highly unlikely that Hezbollah would accept disarmament while these conditions are present.
In addition, recent intelligence has purportedly uncovered Hezbollah external attack plans, European drone smuggling networks, the resumption of arms production within Lebanon and Iranian attempts to facilitate lethal aid to the group, via both maritime smuggling networks and attempts to reestablish ground lines of communication through Syria. Moreover, Hezbollah senior leadership, including Secretary-General Naim Qassem, have reiterated their commitment to the principle of armed resistance against Israel, framing it as a non-negotiable component of Lebanese national defence and urging for patience among Hezbollah’s base.
After Israel’s campaign against Hezbollah, which has destroyed much of the group’s key equipment and degraded its leadership, Hezbollah is almost certainly not in a position to sustain major operations against Israel, especially after losing its main supply routes in Syria. Recent actions have likely been intended to alleviate both domestic and international pressure on Hezbollah and to create space for the group to reorganise and regroup.
Hezbollah has likely adapted its targets, seeking more covert methods to resupply and has dispersed its forces to minimise opportunities to be further degraded by Israel. Further reporting may indicate that the group is evolving its attack methodology, with evidence that it has been planning external attacks against Israel in coordination with Iran, and uncorroborated reports suggest that as many as 400 Hezbollah commanders have relocated to South American countries, where the group has an established network primarily involved in illicit finance, logistics, and transnational organised crime in support of the group’s wider objectives.
The Lebanese government’s approach to Hezbollah’s disarmament has consistently favoured dialogue and political negotiation over the use of force. An attempt to forcibly disarm Hezbollah is unlikely to be successful and could provoke a violent retaliation, which could ultimately threaten civil war in Lebanon. The LAF are unlikely to be in a condition to actively confront Hezbollah without risking a major escalation, as the militant group still maintains an assessed fighting force close to 100,000 and a credible arsenal of weapons.
Furthermore, Hezbollah’s rank and file remain ideologically committed to armed resistance and perceive the group to be a guarantor of national defence, not a destabilising force within Lebanon. Even if progress towards disarmament, demobilisation or integration were to be made, there is a high threat of factionalism, especially after Israel’s recent campaign. Splinter groups would likely emerge from more hardline factions, which would likely operate independently of a centralised command and potentially align with other external actors of transnational organisations, a development that could jeopardise Lebanon’s stability or provoke further Israeli intervention.
Sudan: Paramilitary forces coordinate attacks on displacement camps
On 11 April 2025, the paramilitary Rapid Support Forces (RSF) launched a coordinated attack across North Darfur, which involved attacks on the besieged state capital, El Fasher, and several targets within the wider area. As part of the offensive, RSF claimed control of Zamzam and Abu Shouk displacement camps, stating they had “liberated” them from the Sudanese Armed Forces (SAF). RSF personnel reportedly began burning buildings and shelters within the camps in an effort to identify and capture SAF personnel allegedly hiding among civilians.
A separate RSF attack was carried out in Um Kadadah, approximately 180 kilometres east of El Fasher. Reports from the area indicate multiple fatalities, with accounts suggesting the killings were based on ethnicity.
Current estimates indicate that the attack on Zamzam camp has resulted in the displacement of between 60,000 and 80,000 households or up to 400,000 people, according to the UN’s International Organisation for Migration. At least 400 civilians have been confirmed killed during the operations, with the actual number assessed to increase substantially, with reports of ongoing killings and heavy use of artillery. Aid workers from Relief International operating a clinic in Zamzam camp were also reportedly deliberately targeted during the assault.
Solace Global Assessment:
The RSF attacks in the El Fasher area are highly likely reflective of a strategic effort by the group to consolidate control over the entire Darfur region. The RSF almost certainly views the capture of El Fasher, the last Sudanese Armed Forces (SAF) stronghold in North Darfur, as integral to achieving this objective and will likely continue their offensive operations in the area.
The RSF likely attacked the displacement camps for several reasons. Zamzam camp is located on the intersection of multiple main supply routes, the A5, A43 and B26. Control of Zamzam would likely enable the RSF to severely disrupt SAF logistics and deny SAF units the opportunity to mutually support one another, especially in El Fasher. The attacks were also likely a form of retaliation for the RSF’s recent loss of Khartoum, with the withdrawal of forces from the capital likely enabling the redeployment of RSF personnel and resources to Darfur.
The RSF’s broader strategy likely includes forced displacement and the deliberate targeting of civilians perceived to support the government. The RSF’s objective is likely to punish communities supportive of the SAF, to instil fear among the civilian population, deny humanitarian access and to expropriate critical aid resources such as food and medicine.
This campaign may also aim to forcibly remove ethnic communities from parts of Sudan, contributing to patterns of ethnic cleansing. The reports of the deliberate targeting of humanitarian actors may be intended to deter aid groups from operating within RSF-controlled areas, a strategy that will reduce international oversight and help enable the group to commit acts of genocide with impunity.
The attacks and subsequent displacement of an estimated 400,000 people are almost certain to result in the deterioration of the humanitarian situation. It is estimated that 25 million people, approximately half of Sudan’s population, are already facing extreme hunger, a number that has likely increased since the cessation of USAID, which accounted for almost half of all aid to Sudan.
Deliberate RSF attacks on displacement camps, the killing of aid workers, the disruption of aid routes and the destruction of critical infrastructure will almost certainly increase internal displacement, increase mortality rates, overstretch humanitarian efforts and lead to increased cross-border refugee flows.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Protests likely in London over UK Supreme Court gender identity decision
On 16 April, the UK’s highest court ruled that the definition of “woman” under equality legislation will only apply to the category of “biological sex”. The ruling relates to a case regarding gender recognition certificates, documents that certify someone’s gender transition. While the court stated that trans people would not be discriminated against under the new ruling, the landmark decision will likely provoke a reaction from LGBTQ advocacy groups.
Protests are likely in London during the 17-21 April bank holiday weekend. While these protests are likely to be small and peaceful, there is a realistic possibility of limited public transport or road blockades, particularly in London’s Strand area, where the court is located.
Spanish anti-tourism protests likely to intensify over Easter
Several anti-tourism groups have called for unrest during the 18-20 April weekend in opposition to perceived overtourism at high-visibility destinations. Locations where protests are likely to occur include the main towns in the Canary Islands, Malaga, Barcelona, Valencia, and smaller centres that have highly popular Easter celebrations, like Valladolid, Leon, and Segovia.
Anti-tourist sentiment has increased in Spain since the COVID-19 pandemic, and particularly since 2023. As the high tourist season approaches, protests are highly likely to intensify. While most of the unrest is peaceful, there is a realistic possibility of isolated cases of harassment, vandalism or violence against tourists or their property.
Protests likely in Italy on 25 April
The commemoration of Italy’s liberation from the fascist regime is likely to coincide with protests in Rome, Bologna, Milan, and other large cities. In 2024, clashes between pro-Palestine and pro-Israel protesters were recorded in Rome, while, in Milan, protesters clashed with responding police in Piazza Duomo. Protests in 2025 are likely to be particularly large, as the commemoration marks the 80th year since liberation (25 April 1945).
Hungary continues to repress LGBTQ+ community
On 14 April, the Hungarian parliament continued its repression of the LGBTQ community by passing an amendmentto the Hungarian constitution which permits the government to ban public events organised by the LGBTQ community. The amendment passed with 140 votes in favour and 21 against, easily surpassing the two-thirds majority that it required, despite opposition members and supporters attempting to block access to the parliament building.
The amendment is the most recent act of part of a broader campaign by Prime Minister Viktor Orbán and his ruling Fidesz-KDNP coalition, who are highly likely attempting to appeal to their conservative base ahead of the 2026 election. However, opposition parties, civil rights organisations, and many members of the Hungarian public have condemned these measures, describing them as authoritarian, intentionally discriminatory towards minority groups, and designed to restrict civil liberties.
The government’s agenda has already sparked widespread unrest and periodic demonstrations, some of which have led to violent interactions with the police. This latest amendment is likely to provoke further protests, as opposition to Orbán’s increasingly illiberal policies continues to grow. The threat environment for LGBTQ travellers to Hungary has almost certainly deteriorated, with these travellers increasingly likely to be targeted by harassment or even assault.
Serbian anti-corruption protests continue
Anti-corruption protests have continued to be organised across Serbia and were likely rekindled after Serbian President Vučić held a large rally in Belgrade to show support for his leadership amid the ongoing protests. On 14 April, protestors blocked the city administration office in Vrsac, followed by a protest outside the state-owned broadcaster in Novi Sad on 15 April. The same day, another protest took place at the state broadcaster RTS in Belgrade, and a student protest occurred in Nis.
The EU stated on 15 April that it will ban Serbia from joining the bloc if President Vučić attends a Victory Day parade in Russia on 9 May, after being invited by President Putin. President Vučić’s attendance would likely be a catalyst for further protests, with approximately 40 per cent of the country supporting joining the EU, although this number is likely to be much higher among the sections of the population currently involved in the anti-corruption protests.
Algeria expels 12 French diplomats
The announcement followed the arrest of an Algerian consular official in France, suspected of having participated in the abduction of a French-based Algerian anti-government influencer in 2024. The development marks a further escalation in tensions between Algeria and France, which encompasses the areas of security, immigration, and domestic politics.
The latest expulsions are likely to prompt a reprisal from Paris. However, this is likely to result in a tit-for-tat escalation. In France, there is a realistic possibility that growing tensions with Algeria will drive protests and possibly political violence. In January 2025, France arrested several influencers who had allegedly used social media to call for violence against French citizens in response to Paris-Algiers tensions.
Malian authorities shut down Canadian mining company
The authorities in Mali have shut down the office of the Canadian mining company Barrick Gold in the capital, Bamako, over the alleged non-payment of taxes. The move follows multiple disputes between Barrick Gold and the Malian government, following the junta’s imposition of a new tax code, which demanded the payment of retroactive taxes. This development is indicative of a wider trend across the Sahel, where military-led governments are increasingly asserting control over natural resource sectors and taking punitive action against Western firms, while increasing cooperation with strategic rivals like Russia and China.
Junta easily wins elections in Gabon
Exit polls on 13 April indicated that approximately 90 per cent of the vote went to General Brice Oligui Nguema, the leader of the junta that carried out a successful coup in 2023, ousting the powerful Bongo family that had ruled the country since 1967. While some observers remarked that the elections were fair and transparent, several irregularities were noted, including some reports of ballots being tampered with. The vote is almost certainly an important political boost for the junta, which has pledged to prioritise economic reform and a bolder foreign policy in the medium term.
Main opposition party barred from contesting election in Tanzania
Tanzania’s main opposition party, Chadema, has been disqualified from participating in the October 2025 elections after failing to sign a mandatory code of conduct by the mandated 12 April 12 deadline. The exclusion of Chadema follows the arrest and treason charges filed against the party’s leader, Tundu Lissu, who was charged on 6 April after he called for electoral reforms at a political rally.
Lissu had been expected to challenge President Samia Suluhu Hassan in the upcoming elections, with her Chama Cha Mapinduzi (CCM) party maintaining its grip on power since 1977. These developments have been widely criticised by both internal and external observers, raising fears of a push towards authoritarianism, despite Hassan’s initial praise for her efforts to reverse some of the more repressive policies of her predecessor.
There is a realistic possibility of civil unrest in the country after the disqualification of Chadema, the ongoing repression of opposition figures and general pattern of democratic backsliding.
Security, Armed Conflict and Terror
Anarchists bomb Hellenic Train offices in Athens, Greece
On the night of 11-12 April, an improvised explosive device (IED) detonated outside the offices of the Greek railway company in Athens. The attack damaged the office building but resulted in no casualties, and, according to local media, multiple anonymous calls were made to police warning them about the danger.
The attack was claimed by a local anarchist group, the Revolutionary Class Self-defence Group. In Greece, anarchists and other far-left activists often carry out bombings targeting state institutions or private companies. Most of these attacks happen at night to minimise the risk of civilian casualties. The bombing is almost certainly linked with the ongoing unrest related to the 2023 Tempi railway disaster, which killed 57 people, most of whom were students.
Kurdish-led SDF withdraw from Tishreen Dam in Syria after agreement with Damascus
On 14 April, the Kurdish-led and US-backed group Syrian Democratic Forces (SDF), which de facto autonomously controls northeastern Syria, withdrew from the strategically significant dam. The withdrawal follows an agreement made by the SDF with the transitional government led by President Ahmad al-Sharaa.
The issues of Kurdish rights, autonomy, and the aggression of Turkish-led Syrian National Army (SNA) militants, in addition to conventional Turkish forces, have been a key challenge to the stability of the new post-Assad Syria. With Tishreen Dam being the primary site of heavy fighting between the SDF and SNA (with Turkish air support) in the past few months, the deconfliction agreement will likely lessen tensions in the area and risks of further conflict escalation.
However, there remain key issues to be resolved despite agreement from the SDF to ultimately integrate into the national military, with the SDF commander-in-chief Mazloum Abdi stating that the SDF need both federalism and quasi-autonomy as a separate bloc within the national army, conditions that Damascus is unlikely to agree to.
Jordan arrests 16 involved in possible Hamas plot
Jordanian authorities stated, on 15 April, that they arrested a cell aiming to “threaten national security”, via improvised drones, rockets, and explosives. Local and international media quoted security sources’ allegations that the 16 were part of Hamas. It is highly likely that the cell was operating with Iran-sourced supplies, and to arm Palestinian militants in the West Bank.
Jordan remains the key country for Iranian smuggling routes towards the West Bank. The kingdom has likely aimed to remain ambivalent, seeking to both avoid a confrontation with Iran, which could drive protests among the largely pro-Palestinian public, and to reduce the destabilising impact of Iranian arms being present on its territory.
The latest arrests are likely either reflective of Jordanian security forces’ assessment that the cell constituted an unacceptable domestic security threat or, less likely, could be meant as a signal to Tel Aviv and, more broadly, Washington, at a moment where the situation in both Gaza and the West Bank is precarious.
Further briefings made regarding potential ground offensive against Houthis in Yemen
‘Yemeni and US officials’ briefed the Wall Street Journal (WSJ) in an article published on 15 April that Yemeni militias are planning a ground offensive against Houthi-controlled Hodeidah. This adds to previous briefings made to CNN in an article published on 6 April from ‘regional diplomatic sources’. Private American security contractors have reportedly advised the Yemeni factions on the potential offensive.
Riyadh is likely reluctant to return to open civil war in Yemen due to the reputational and economic costs associated, and the potential offensive would likely be mainly conducted using the United Arab Emirates (UAE)-backed Southern Transition Council’s (STC’s) forces with US air support. This assessment has been further supported by the WSJ report, which states that Saudi officials ‘have privately told American and Yemeni officials they won’t join or help a ground offensive in Yemen again’, although this position is likely to change if the Houthis directly attack Saudi Arabia.
Should the civil war be reignited with an STC-led ground offensive towards Hodeidah, it is likely that the Houthis will attempt long-range strikes with either or both ballistic missiles and long-range one-way attack uncrewed aerial vehicles (OWA-UAVs) against targets in the UAE. Previously, the Houthis primarily attempted to strike targets in the vicinity of Abu Dhabi, including oil refineries, the international airport and Al Dhafra airbase.
US and Iran begin talks in Muscat
On 12 April, delegations from Washington and Tehran met in Muscat, Oman, to begin negotiations regarding Iran’s nuclear program. Tehran previously refused the prospect of direct talks with the US; however, US President Donald Trump’s threats of a bombing campaign, in combination with increasing concerns of a planned Israeli attack later this year, likely compelled Tehran to concede to direct talks.
In the initial meeting, clear red lines were set by both delegations. The Iranian delegation, led by Foreign Affairs Minister Abbas Araghchi, stated that Tehran requires guarantees on sanction relief, access to its frozen assets, and the end of the ‘maximum pressure’ campaign spearheaded by the Trump administration. The US delegation, led by US Special Envoy to the Middle East Steve Witkoff, has indicated that their fundamental demand is the abandonment of Iran’s nuclear weapons program.
With the Iranian regime likely in its most geopolitically vulnerable position in decades, Tehran is likely highly susceptible to US pressure. Nonetheless, the incentive for a nuclear deterrent has almost certainly increased, precisely because of their current vulnerability following the fall of the Assad regime, the degradation of their previously primary regional deterrent, Lebanon’s Hezbollah, and the weakening of their air defence capabilities by Israeli military operations.
Should the talks fail to achieve results, it is likely that the US, with the support of Israel, will pursue a military solution that risks broader escalation across the Middle East. There is a realistic possibility that even if Washington feels it is making progress in the talks (or even agrees to a deal), Israel’s government could still pursue a military escalation with Iran later in the year.
Eight Pakistani citizens killed in eastern Iran
Islamabad has demanded answers after eight Pakistani nationals were killed on 13 April by separatists in Iran’s Sistan-Baluchestan province, which shares a border with Pakistan’s restless southwestern Balochistan province. The Baloch Nationalist Army (BNA), a Pakistani separatist group, has claimed responsibility for the attack.
The victims were all from the Punjab areas of Pakistan and were attacked when working at a workshop in Mehrestan county, located roughly 230km (142 miles) from the Pakistan border. The attack is likely indicative of increased cross-border operations by Baloch separatist groups, who have increased attacks on Punjabis, who are viewed as an extension of Pakistan’s government and military.
Iran and Pakistan have repeatedly accused each other of harbouring militants in their respective territories. Moreover, both nations have conducted strikes inside each other’s territory in support of counter terrorism operations, most notably in January 2024, when Iranian missile and drone strikes in Pakistan were met with retaliatory strikes.
There is a realistic possibility that Pakistan may retaliate if it deems Iran’s response to separatists insufficient, increasing the risk of cross-border tensions in the coming weeks.
Medical services suspended after looting of hospital in Upper Nile State, South Sudan
On 14 April, dozens of armed men stormed a hospital in Ulang, Upper Nile State operated by Médecins Sans Frontières (MSF) and stole vital medical supplies and equipment. The raid forced the hospital, which was the only functioning health facility in the area, to close. At least 100 patients were receiving treatment including trauma, maternity, and paediatric care at the time, and many were forced to flee.
Similar patterns of violence targeting healthcare in the region has taken place in recent months; in January 2025, armed men attacked two MSF boats on their way to Ulang. Violence has re-ignited in the White Nile State since early March 2025, when the White Army launched attacks targeting the South Sudan People’s Defence Forces in a conflict that has threatened to reignite the South Sudan civil war. Further targeting of healthcare facilities in the region is highly likely.
Al-Shabaab claim control of Adan Yabaal during the ongoing Somalia offensive
On 16 April, al-Shabaab militants released a statement claiming control of Adan Yabaal, a town in the Middle Shabelle region, northeast of Mogadishu. They also claimed to have overrun 10 military installations in the region. If true, this constitutes a major strategic loss for Somali forces, who have used the town as a launch pad for counterinsurgency operations in Middle Shabelle against the al-Qaeda-linked al-Shabaab.
The Somali military has denied the group’s capture of Adan Yabaal, claiming that government forces repelled an al-Shabaab attack. This is the latest in a series of government setbacks, with al-Shabaab recently seizing control of the Afgoye-Mogadishu and Mogadishu-Balcad corridors. Al-Shabaab will highly likely intensify attacks on the capital, Mogadishu, following their recent strategic gains.
Spate of attacks kills over 50 in Nigeria’s Plateau State
On 14 April, over 50 people were killed after villages were attacked in Nigeria’s Plateau State, with several others injured and over 2,000 displaced. The attackers, believed to be cattle herders belonging to the Muslim Fulani community, also looted and burned homes, with the majority of the victims reportedly Christian. This follows a series of deadly incidents in the region, including the killing of 52 people two weeks prior. Fighting between Fulani herders and Christian farmers is a regular occurrence in the region, but the attack has raised concerns that attacks are increasing in frequency, largely driven by resource competition resulting from the effects of climate change. There is a realistic possibility of increased attacks over the Easter holidays, with militants establishing a pattern of targeting Christian communities around significant religious dates.
Environment, Health and Miscellaneous
Storm Olivier triggers flooding in Spain
Storm Olivier has continued to cause significant disruptions across Spain. Spanish weather services have issued alerts for rain, storms, and snow in Castile and León. On 14 April, orange and yellow warnings for wind and heavy rain were in effect in northern and northeast Spain, as well as the Balearic Islands.
The storm has caused severe flooding in the Canary Islands, particularly on Lanzarote, where a state of emergency was declared on 12 April due to heavy precipitation, leading to 150 emergency calls in just two hours. Recovery efforts are underway as officials have organised fire crews to assist with pumping efforts. Five people sustained minor injuries, and there were power interruptions reported in Costa Teguise.
Various regions of Spain have been placed under weather alerts. On April 11, Andalusia was on an orange alert due to significant risks posed by the storm, while other regions like Asturias, Castillas, Extremadura, Galicia, and Melilla were on yellow alerts. Madrid experienced rain and hail, and a landslide blocked a road on Tenerife.
Asia–Pacific
India: Protests erupt over controversial Waqf bill
Widespread protests have broken out across India following the passage of controversial amendments to the Waqf Act by the Lok Sabha, which was originally passed on 4 April. Opponents of the amendments have argued that they would dilute the rights of Muslims to manage religious-based endowments or “waqfs.”
In particular, the inclusion of non-Muslims in the management of waqfs has generated fears that the federal government, which is led by the Hindu nationalist Bharatiya Janata Party (BJP), is engaging in discriminatory practices, and opponents have stressed that other religious communities can continue to retain full control over their respective faith-based institutions.
Prime Minister Narendra Modi’s BJP has defended the amendments, stating that they are intended to enhance transparency and address corruption and mismanagement within the waqf administration.
Protests have occurred across multiple cities in India, but have been particularly intense in West Bengal. In Murshidabad, violent demonstrations involving stone throwing and Molotov cocktails broke out on 11 April and have resulted in the deaths of at least three people and the arrest of 118.
In response to the violence, the Kolkata High Court ordered the deployment of central forces to Murshidabad, and the West Bengal home secretary has imposed restrictions on public gatherings and suspended internet services in certain areas. On 14 April, protesters blocked the national highway outside Kolkata and set multiple vehicles on fire, as well as gathering in Bhangar, setting a barricade alight. On 15 April, the regional Andhra Pradesh party filed a petition challenging the bill with India’s Supreme Court.
Solace Global Assessment:
Waqf, meaning “confinement and prohibition”, is a charitable endowment under Islamic law in which donated properties managed by waqf boards are used for schools, orphanages, hospitals, banks, and graveyards. Once established, these properties cannot be sold or transferred and are considered Allah’s property to be used for charitable purposes. Waqf properties have become a significant asset class in India, encompassing approximately 870,000 properties spread over 940,000 acres of land, making waqf India’s third-biggest property holder.
The waqf bill introduces significant changes to the management of waqf properties. Key provisions include restricting waqf creation to Muslims practising Islam for at least five years, the elimination of the “waqf by user” common law establishment of waqf properties, ensuring family waqf do not deny inheritance to female heirs, the inclusion of female Muslims, non-Muslims, and various Muslim sect representation in the Central Waqf Council and State Waqf Boards, and tightening the registration and procedures for waqfs.
These measures are controversial among India’s Muslim community, who view the amendments as eroding religious autonomy, breaking from tradition by giving non-Muslims, women, and other historically underrepresented Muslim sects more control over waqf administration, and potentially invalidating properties that are considered waqf but lack the formal documentation. While the act is framed as easing administration and introducing “progressive” measures, opponents argue that the bill will eliminate many existing waqf properties and expose waqf properties, including historic mosques, shrines, shops, graveyards, and vast tracts of land to legal disputes, state confiscation, or even demolition.
The bill is perceived as a deliberate repressive measure towards the Muslim community. Since gaining power in 2014, Modi, a Hindu nationalist, has employed anti-Muslim rhetoric and discriminatory acts towards the Muslim community. The act is highly likely designed to spark a backlash and inflame the Muslim community while appealing to the BJP’s Hindu nationalist base. The challenge to the Waqf Amendment Bill will almost certainly generate more publicity for opposition to the bill and drag out the public debate, which will highly likely inflame further protests.
Thailand: Surge in traffic accidents during Songkran celebrations
Statistics from 16 April, six days into what is domestically known as the “seven dangerous days”, list over 1,000 extra road traffic accidents (RTAs) during the Songkran holiday period. The increase in RTAs has resulted in almost 200 deaths and over 1,000 injuries nationwide.
The leading causes of accidents are speeding (44 per cent) and drunk driving (25 per cent), with motorcycles involved in over 80 per cent of all incidents. The highest number of fatalities has been recorded in Bangkok, although accidents have been observed nationwide, with the southern province of Phatthalung recording the most overall accidents. Thai authorities have deployed additional trains and buses to reduce congestion and support safer travel.
Solace Global Assessment:
Songkran, meaning “passage of the sun”, occurs from 13 to 15 April each year (although celebrations usually extend from 11 to 17 April) and celebrates the Thai/Buddhist New Year. It is one of Thailand’s most important holidays and is marked by nationwide celebrations including parades, religious festivities, and family gatherings. The festival attracts many tourists, stretching transportation networks and local infrastructure. In 2024, approximately 1.9 million foreign tourists visited Thailand during Songkran, which was a 37.54 per cent increase from the year before, something attributed to government measures to ease travel and post-COVID increases in tourism. Tourists typically cause an increased demand for public transport, including taxis and buses, further exacerbating the need for locals to use private transport.
Songkran causes a spike in road traffic accidents (RTAs). During this period, the RTA rate approximately doubles in a country already experiencing very high rates. From 11 to 17 April 2024, there were at least 480 RTA fatalities and over 2,000 injuries, equating to approximately 69 fatalities per day. This puts Thailand temporarily in the top 10 most dangerous countries in the world for RTAs during the Songkran period.
The slight reduction in deaths this year is highly likely due to the impact of the 28 March earthquake, which occurred in Myanmar, also impacting Bangkok. In the lead up to Songkran, the Thai Hotels Association (THA) predicted that tourism revenue would fall by approximately 10-15 per cent, with tourists cancelling their trips. Motorcycles account for most of the deaths, which are generally attributed to driving while intoxicated, speeding, cutting lanes, wet road surfaces, and inadequate safety wear.
While celebrations are widespread, travellers can face penalties for involving unwilling participants. Splashing water on people not involved in the celebrations can be considered causing a nuisance or damaging property, leading to potential prison sentences of up to one month or a 10,000-baht (228 GBP) fine. During the 2024 celebrations, for example, three tourists from Hong Kong were jailed for 28 days after splashing a police officer with water. Similarly, dumping powder on unwilling participants, an act which typically involves non-consensual contact, could result in a public indecency charge.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Around 60,000 Afghans deported from Pakistan in two weeks
The figure was announced on 15 April by the International Organisation for Migration (IOM). Pakistan has pledged to deport the approximately 800,000 Afghan nationals who have Afghan Citizen Cards (ACC), as part of larger efforts to repatriate the millions of individuals who have entered the country following the Taliban’s takeover in 2021.
Humanitarian organisations have noted that transiting through the poorly policed areas near the Durand Line poses a significant threat to returning migrants, and there have been several cases of extortion and violence carried out by Pakistani security forces. Moreover, the threat of terrorism in the area remains extremely high, with several Islamist groups likely attempting to recruit disenfranchised Afghans for radicalisation and potential attacks.
Hong Kong’s largest pro-democracy party set to disband
On 13 April, the Hong Kong Democratic Party, Hong Kong’s last remaining major opposition party, conducted a meeting approving arrangements to disband. The decision came after pressure from Beijing, which has allegedly warned the party in recent months to disband or face potential arrest.
There is currently no precise date for the dissolution of the party, but a final vote will be held in the coming months. A majority of 75 per cent will be required to pass the motion. It is highly likely that the motion will pass, marking the end of political opposition in Hong Kong. Pro-democracy movements in Hong Kong have been largely curtailed since Beijing imposed the National Security Law in 2020, which triggered major protests across the region.
Security, Armed Conflict and Terror
Three police officers killed and 16 injured in Pakistan bombing attack
On 15 April, an improvised explosive device (IED) placed on a parked motorcycle detonated while a convoy carrying around 40 police officers transited past it in Mastung, Balochistan. The attack was claimed by the Islamic State Khorasan Province (ISKP) and marks the first notable attack conducted by ISKP in weeks and follows an unusual period of inactivity for the group, which is one of the Islamic State’s more active branches.
While it is difficult to definitively assess the cause of this decrease in attack volume, it is likely that it has been partly driven by an internal reshuffle of ISKP’s leadership and key roles, which was launched by the group’s leaders in February-March 2025.
The Maldives bans entry for Israeli passport-holders
On 14 April, the Maldives’ parliament passed an amendment to its immigration law, which was subsequently approved by President Mohamed Muizzu on 15 April. A Cabinet statement declared that ‘The ratification reflects the government’s firm stance in response to the continuing atrocities and ongoing acts of genocide committed by Israel against the Palestinian people.’
A similar ban was in place in the early 1990s but was rescinded in 2010 during renewed relations. Given the low Israeli visitor rates to the Maldives, with only 59 people with Israeli passports (out of a total 214,000 visitors) entering in February 2025, protests across the archipelago are unlikely.
However, there is a realistic possibility that small-scale protests will occur outside the Maldives’ embassies in other major cities, including London, following the decision.
Russia requests access to Indonesian air base
Australia has raised concerns in response to reports that Russia has requested permission to base Russian Aerospace Forces (VKS) aircraft at an Indonesian air base in Biak, in the remote Papua region. Australian Prime Minister Anthony Albanese has stated that he considers Russia an authoritarian regime and reiterated Australia’s support for Ukraine.
A Russian military presence in Papua would almost certainly enhance its surveillance of the region, placing its aircraft within 1,400km of Darwin, home to an Australian air force and naval base that regularly hosts US military assets.
However, Indonesia has consistently pursued a policy of “independent and active” foreign policy doctrine, engaging with multiple global powers while maintaining strategic neutrality, and has persistently refused to host foreign militaries on its soil regardless of alignment.
Myanmar’s junta chief Min Aung Hlaing visited Bangkok, Thailand for a rare summit visit
On 3 April, Myanmar’s junta chief Min Aung Hlaing visited Thailand for a regional summit for a joint statement on the earthquake. The leaders from the seven Bay of Bengal Initiative for Multi-Sectoral Technical and Economic Cooperation (BIMSTEC) members attended: Bangladesh, Bhutan, India, Myanmar, Nepal, Sri Lanka, and Thailand. The invitation of the junta leader marks a break from the regional policy of not inviting junta leaders to major events.
For the junta, the attendance at the summit is highly likely a symbolic act amid growing criticism regarding the Tatmadaw’s handling of the earthquake, having been accused of violating the ceasefire and blocking aid to rebel-held areas. Former Thai Prime Minister Thaksin Shinawatra and Malaysian Prime Minister Anwar Ibrahim reportedly pushed for a continuation of the ceasefire imposed from 2-22 April as a humanitarian pause to support post-earthquake relief efforts.
There is a realistic possibility that they will extend the ceasefire, given that the earthquake primarily damaged junta-controlled regions of Mandalay and preventing a rebel offensive is almost certainly beneficial to the junta. However, given China’s ongoing economic and diplomatic support for the junta and the disunity of regional powers regarding intervention, it is unlikely that the Tatmadaw would cave to international pressure regarding a formal peace process.
Environment, Health and Miscellaneous
Earthquake kills one in Tajikistan
The 6.4 magnitude tremor struck the Rasht district at a depth of 16 kilometres, destroying approximately 100 houses and killing one person in the village of Ushturpasta. Multiple aftershocks of between 3 and 5 magnitude also occurred in the area. Tremors were also recorded in Myanmar and India around the same time. All the affected locations are near the borders between the Indian and Eurasian plates. This area is undergoing a higher frequency of seismic activity, which included the 28 March 7.8 magnitude earthquake in Myanmar that killed more than 5,000.
New Zealand hit by Tropical Cyclone Tam
Tropical Cyclone Tam is impacting New Zealand’s North Island, particularly the Northland region, with significant disruptions. Flights at Whangārei Airport (WRE) were cancelled on 16 and 17 April. At Auckland Airport (AKL), some international flights have been delayed until 18 April.
Firefighters in Northland have so far responded to 120 weather-related calls on 17 April. State Highway 1 near Umawera has experienced flooding, and nearly 15,000 people remain without power in Northland. The New Zealand MetService has issued warnings for coastal flooding and erosion due to large waves, and a power outage is affecting several hundred residents in the Whangārei and Kaipara districts. Cyclone Tam is expected to weaken into a subtropical low but may re-intensify later in the week.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.

Executive Summary
Americas (AMER)
Reports that the US is considering drone strikes on cartels in Mexico will likely strain bilateral relations and provoke retaliation from cartel groups if authorised.
The gangs’ occupation of Mirebalais, Haiti is likely to be a setback for the government and international forces. It will almost certainly give criminal groups more control over aid routes supplying Port-au-Prince.
Europe, Middle East & Africa (EMEA)
Protests in Spain, driven by rising living costs, are likely to continue over Easter and during this year’s high tourism season. While likely to be peaceful, there is a realistic possibility of isolated cases of harassment.
Russia is highly likely incentivised to launch its new spring offensive in northeastern Ukraine to gain further leverage to achieve its maximalist war goals, but its forces will likely struggle to successfully seize Sumy City.
Sustained Israeli strikes in Lebanon and reports that Iran is continuing to resupply Hezbollah through the Port of Beirut are likely to undermine the ceasefire agreement and increase the chances of renewed conflict.
The downing of a Malian drone in Algeria has precipitated a diplomatic crisis between the two countries. The incident likely showcases Algeria’s deteriorating position in the Sahel and vis-à-vis the junta states.
A return to civil war in Yemen, if unconfirmed reports of preparations for a ground offensive in Yemen are accurate, likely pose risks of renewed long-range strikes by the Houthis against Saudi Arabia and the UAE.
Al-Shabaab unlikely to imminently take control of Mogadishu, Somalia, but is likely to conduct more attacks in the capital amid significant territorial gains.
Asia-Pacific (APAC)
Multiple ceasefire violations in Myanmar almost certainly indicate that both sides are exploiting the aftermath of the earthquake to consolidate territory and advance under the cover of relief efforts.
North, Central and South America
US and Mexico: Trump administration considers drone strikes on cartels.
Reporting from current and former US officials indicates that the Trump administration is exploring the possibility of conducting drone strikes as part of a wider effort to counter narcotics trafficking on the US’ southern border. Proposals that include the White House, Pentagon and US intelligence agencies are in the early stages but have included the option of directly targeting Mexican cartel leaders in Mexico. Discussions have included the US conducting joint operations with Mexico as well as the potential for unilateral strikes.
Additional reporting indicates that the Central Intelligence Agency (CIA) is currently reviewing its authorities to use lethal force against Mexican cartels in Mexico and in other parts of the world. This has involved consultation with legal experts and operational planners to identify what operations the CIA could theoretically conduct and what would be the potential risks of those operations.
Solace Global Assessment:
Since coming to office, President Trump has made combating the illicit flow of narcotics, primarily fentanyl, into the US one his key objectives. Early moves have included the designation of several Mexican cartels as foreign terrorist organisations (FTOs), increased sanctions on cartels, and the deployment of advanced military intelligence, surveillance and reconnaissance (ISR) assets to the border and even over Mexican airspace. These actions have been further supported by the threat of imposing tariffs on Mexico if it does not take action against the cartels, forcing the Mexican government to increase arrests, extraditions, and seizures of cartel members and assets.
Reports suggest that the cartels are under unprecedented pressure and have been forced to adapt their operations as a result of pressure from Mexican operations, which have likely been supported by US intelligence. Advanced US ISR assets capable of signals intelligence (SIGINT) and imagery intelligence (IMINT) have likely afforded the US military and intelligence agencies with a comprehensive understanding of cartel operations, locations, networks and leadership. This has likely allowed the US to develop potential targets, should the use of direct action be sanctioned by the White House.
However, there are likely several factors limiting the US’ use of direct action against the cartels. Firstly, there is a realistic possibility that threats to conduct drone strikes and other forms of direct action are part of a gambit to exert increased pressure on Mexico to deal with the cartels independently. Secondly, while lethal force is theoretically permissible, the presence of a large number of US citizens in Mexico, some of whom are involved with the cartels, means the consequences of such actions could be far-reaching. Collateral damage, such as the accidental death of an American citizen, could create significant diplomatic and legal issues for both the CIA and the US government. Thirdly, using lethal force, especially unilaterally, would almost certainly strain relations with Mexico and could lead to a cessation of intelligence sharing with the US, a move that could ultimately weaken counter-cartel operations.
Most importantly, the use of direct action in any form could precipitate a major change in the security environment in Mexico that could threaten US interests, personnel and assets. The cartels may be forced to alter their tactics, which could involve more sophisticated counter-surveillance measures, more innovative ways to smuggle illicit goods into the US or an escalation in violence, both inside Mexico and potentially in the US. The targeting of cartels, especially leadership, is likely to lead to the fracturing of cartels and power vacuums, resulting in cartel infighting, territorial disputes and rival cartels attempting to exploit weaknesses.
In a worst-case scenario, the cartels may perceive increased US involvement as an existential threat to their operations and could respond with a range of retaliatory actions to deter further intervention. There is a realistic possibility that this could include increased cartel violence on the border, attacks on Mexican security services and assassinations of high-profile civilian targets such as politicians and journalists. A more extreme response could involve cartels deliberately targeting US interests in Mexico or beyond. This might include attacks on American businesses, kidnappings of US citizens or deliberate attempts to flood the US with higher volumes of narcotics and potentially more lethal varieties.
Haiti: Gangs take control of Mirebalais, north of Port-au-Prince.
After more than a week of fighting, gangs associated with the Viv Ansamn coalition have taken control of Mirebalais, north of Port-au-Prince. Gangs have subsequently launched an offensive toward Péligre, where a hydroelectric power plant is located, but have been contained by authorities. In Mirebalais and neighbouring Saut-d’Eau, at least 31,000 people have been displaced and more than 500 prisoners freed. Local sources have reported occasional cases of mob violence by local residents against suspected gang members. Moreover, the arbitrary killing of civilians by gangs has continued. Due to the attacks, the hospital in Mirebalais was forced to close and to evacuate all patients.
Solace Global Assessment:
Mirebalais is a strategic town located at the intersection of Route 305 and National Road 3, and controls part of the northern trade from the border to Port-au-Prince. It is also on the main route connecting the capital to Cap-Haïtien and, therefore, can be used to control or restrict aid flows to Port-au-Prince. This is especially the case due to the renewed gang attacks on Toussaint Louverture International Airport (PAP), which have rendered the airport non-operational and have therefore increased Cap-Haïtien’s importance as the main entry point into Haiti and aid distribution centre. After taking control of the town, the gangs have likely implemented their strategy meant to destroy all civil society and administrative institutions to force the population into a state of dependency. Measures in Mirebalais have included the forced “disappearance” of two journalists, as reported by the Association of Haitian Journalists (AJH), the forced closure of the hospital, and the killing of humanitarian workers, including at least two nuns. Finally, by occupying the town, the gangs are likely seeking to benefit from the smuggling of weapons and ammunition from the border with the Dominican Republic. Improving their position to the north of the capital will likely shape the conditions for a future attack on the remaining territory that the government forces and the Kenyan police mission maintain in Port-au-Prince.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
“Hands Off” protests in all 50 US states.
The protest movement opposes the Trump administration’s policies, particularly the cuts to government agencies being spearheaded by billionaire and government advisor Elon Musk. The “Hands Off” protests have been supported by multiple smaller organisations and movements, like the 50501 movements and other bodies adjacent to the Democratic Party. On 5 April, estimates of nationwide attendance reached three million across more than 1,000 locations. No notable violent incidents were recorded during the protests. The protests constitute the largest civil unrest instance since the beginning of the current administration. Organisers have called for a second large-scale demonstration on 19 April.
Large-scale mobilisation for Ecuador’s presidential elections.
Ecuador’s military is mobilising 1,800 reservists to provide extra security during the second round of presidential elections on 13 April, after the first round resulted in a tie. The reservists will be deployed to protect polling stations. The government has yet to announce what additional security measures will be in place. However, the first round resulted in temporary border closures with Colombia and Peru to limit the influence or organised crime, and curfews were imposed in 22 municipalities. There is a high likelihood of similar measures being introduced during the second round, with Ecuador currently struggling to contain a wave of violence attributed to transnational organised crime groups.
Peruvian transport workers strike over endemic crime.
On 10 April, major transport disruptions were recorded in Lima, Peru, after transport workers went on strike. Transport workers marched on Congress to demand action against a surge in crime in the country, with much of the crime involving the extorting of public transport. This has involved attacks on public transport networks after companies have refused to pay the extortion, resulting in high rates of civilian casualties. Much of the crime has been linked to well-financed and organised transnational criminal groups like Tren de Aragua. The government has recently declared a national emergency in the capital and has introduced emergency measures that will grant the Peruvian National Police greater powers to combat organised crime.
Indigenous groups stage multi-day protest in Brazilian capital.
An estimated 10,000 indigenous people from across Brazil have amassed in Brasília to advocate for land demarcation and to protest a 2023 law that limits their land rights and makes it more difficult for tribes to reclaim lands they were forced to abandon. The protests were organised from 7-11 April and have remained largely peaceful. However, on 10 April, Brazilian police used tear gas against the protestors after they approached government buildings in the capital. Observers have indicated that it is highly likely that indigenous groups will target the upcoming COP30 which is set to be held in the northern Brazilian city of Belem in November.No need to do anything with the section titles.
Security, Armed Conflict and Terror
Colombian dissidents agree to disarm.
A dissident faction of the National Liberation Army (ELN), the Comuneros del Sur, has agreed to demobilise and hand over its weapons as part of President Petro’s objective of securing total peace. While this will be viewed as a win for the incumbent administration, the Comuneros del Sur is only a minor rebel group with an estimated 100-300 fighters, dwarfed by the ELN, which is still fighting an insurgency in multiple parts of Colombia. The agreement will likely only be viewed as a symbolic win and is unlikely to have any significant security considerations for Colombia as a whole.
Environment, Health and Miscellaneous
Third measles death reported in Texas.
It is the third death to occur in the space of months, after ten years during which measles caused no fatalities in the US. Around 650 cases have been recorded so far this year, 500 of them in Texas, as part of an outbreak that likely started in local Mennonite communities, who have extremely low vaccination rates. Washington has deployed the Centers for Disease Control and Prevention (CDC) to assess possible responses to the multi-state outbreak. However, the CDC and the Department of Health, which is led by “vaccine-sceptic” R.F. Kennedy Jr., face severe challenges, including mass layoffs and trust issues among the most at-risk communities, which are likely to make response efforts more complex.
First confirmed human death from bird flu in Mexico.
Mexico has confirmed its first human death from H5N1 bird flu, as a 3-year-old girl in Coahuila, western Mexico, who died due to respiratory complications from the virus. The case marks the first known human infection in the country, though the exact source of transmission is still under investigation. The girl’s case follows a global trend of H5N1 infections, with the virus having spread among birds and a limited number of humans, particularly in the US, where 70 cases have been reported over the past year. The immediate threat to other humans is assessed as low, however, the authorities will almost certainly increase their surveillance and contact tracing to prevent further spread.
Roof collapse in Dominican Republic kills 221, injures hundreds.
On 8 April, the roof of the Jet Set nightclub in Santo Domingo collapsed during a performance. Search efforts to retrieve the bodies of the victims ended on 11 April. Authorities have launched an investigation to determine the causes of the collapse, which was one of the deadliest disasters in the Dominican Republic’s modern history. The investigation is highly likely to have high political visibility and, depending on the findings, could become a driver of civil unrest.
Europe, Middle East & Africa
Spain: Large-scale protests against cost of living crisis.
On 5 April, protests took place in around 40 Spanish cities, with residents calling for policies to reduce growing housing prices. In Madrid, the demonstration was attended by around 150,000 people. The protesters, who are supported by a network of civil society organisations and have increasingly received the support of mainstream left-wing parties like Podemos, made a series of demands including the lowering of rents, the banning of eviction practices, the end to the proliferation of short-term rental contracts aimed at tourists, and the seizing of empty apartments.
Solace Global Assessment:
Since the COVID-19 Pandemic, cities in Spain, particularly highly popular tourist destinations like Barcelona, Palma, or Málaga, have had double-digit increases in housing costs, effectively pricing out long-time residents. According to tenants’ unions, rents have on average increased by 18 per cent over the past two years. The first notable wave of protests related to this issue began in the Canary Islands in 2023 and rapidly expanded to the mainland. The housing protests are indissolubly linked with a growing anti-tourism sentiment, due to the increased number of properties being taken off the long-term rental market in favour of short-term, tourist-focused contracts. Past waves of protests in 2023 and 2024 have been especially intense during the high tourist season between May and September. Further protests will likely occur during the summer. Large-scale protests are also likely to occur on or near Easter, particularly in cities where Easter celebrations attract large numbers of tourists, such as Seville, Málaga, and Valladolid. While these protests are likely to remain peaceful, there is a realistic possibility of acts of vandalism or harassment against foreign travellers or their property.This is the paragraph.
Ukraine: Russian spring offensive in northeastern Ukraine intensifies.
In an interview published on 9 April, Ukraine’s Command-in-Chief Oleksandr Syrskyi stated that a new Russian spring offensive against the Sumy and Kharkiv Oblasts in northeastern Ukraine ‘has effectively already begun’. Syrskyi reported an ‘almost doubling’ of Russian offensive operations in the past week across multiple sectors on the Sumy and Kharkiv axes. Furthermore, Ukrainian President Volodymyr Zelensky stated that 67,000 Russian troops have amassed in preparation for an attack against Sumy City. The Russian Ministry of Defence claimed the capture of the Sumy village of Basivka over the weekend, which was disputed by the Ukrainian State Border Guard Service. Sumy City is only 30 kilometres from the Russian border and had a population of 256,000 in 2022.
Solace Global Assessment:
The intensification of Russian ground assaults in northeastern Ukraine is highly likely indicative of a newly launched strategic offensive, which Zelensky has previously indicated was initially planned to be conducted eight months ago but was delayed by the Ukrainian Kursk offensive. The approximately 60,000-70,000 Russian troops and national guardsmen (Rosgvardia) are primarily concentrated in Kursk Oblast, and are likely currently focused on ejecting the last remaining Ukrainian forces from positions south of Sudzha in the Kursk salient. These forces would likely only dedicate fully towards an offensive towards Sumy City once the Kursk salient has been fully recaptured, with the already ongoing offensive operations against nearby Basivka, for example, likely providing further pressure on Ukrainian forces in Kursk to withdraw. Russian forces will nonetheless likely require additional reinforcements and materiel to successfully seize Sumy City, which Moscow would likely find challenging due to the current significant demands on the Pokrovsk axis in the Donetsk Oblast.
With the senior Ukrainian official Pavlo Palisa reiterating Kyiv’s position on 10 April that an absolute red line for Ukraine in any peace talks would be the imposition of curbs to its military, the Kremlin is highly likely incentivised to launch a new offensive to gain further leverage in potential negotiations to achieve its maximalist war goals. Ukraine’s ability to repel the offensive would likely be significantly hampered by any further suspensions of US intelligence sharing, with Russian forces having made the most rapid advances in Kursk Oblast during the temporary pause in early March. Moscow will likely continue to leverage the limited and vaguely defined moratorium on long-range strikes against energy infrastructure to gain concessions, with a key goal of pressuring Washington to renew its withdrawal of military aid and intelligence sharing. The Russian Ministry of Defence, for example, stated on 9 April that Ukraine had violated the agreement with six attacks on Russian energy infrastructure over the past day. It is likely that Russian long-range and artillery strikes against the urban centres of Sumy and Kharkiv will continue to increase in the coming weeks, posing significant risks to civilians and foreign nationals deployed in the area.
Israel and Lebanon: Hezbollah exploiting maritime routes to rebuild.
Western security sources have indicated that Iranian Revolutionary Guards Corps (IRGC) Quds Force Units have been supplying Hezbollah with arms, equipment and money through maritime routes. The Quds Force Units reportedly involved in the smuggling, Units 190 and 700, are units known to be involved in the facilitation of lethal aid from Iran. The report suggests that Hezbollah maintains an established network of operatives at the Port of Beirut, enabling the organisation to smuggle weapons into the city without restriction. The Lebanese government has rejected the claim, asserting that the Port of Beirut has the same level of inspections and security as Beirut-Rafic Hariri International Airport.
Solace Global Assessment:
Since the collapse of the Assad regime in Syria and the banning of Iranian flights landing at Beirut-Rafic Hariri International Airport (effective February 2025), Hezbollah has effectively been isolated from its traditional ground lines of communication (GLOCs) and air lines of communication (ALOCs). As a result, Tehran has almost certainly prioritised the rearmament of its primary proxy force via sea lines of communication (SLOCs), with the Port of Beirut serving as the largest and most important port in Lebanon. Recent reporting also suggests that Hezbollah has restarted domestic weapons manufacturing in Lebanon, including the resumption of activity at an arms production facility concealed beneath residential buildings in Beirut, a site previously targeted by Israeli airstrikes in November 2024.
These reports contradict claims made by Hezbollah on 8 April that it is willing to disarm entirely if the Israel Defense Forces (IDF) withdraw from its positions on the five hills it currently holds in southern Lebanon and halts its strikes throughout the country. Moreover, the involvement of the Quds Force in the smuggling of arms into Lebanon likely indicates that the rearmament of Hezbollah has become a strategic priority for Iran. Iran is currently scheduled for talks with the US over the abandonment of its nuclear programme. If an agreement is achieved, moves to disarm Hezbollah would almost certainly be unacceptable for Tehran, with the proxy group serving as one of its main deterrents against Israel. This reality is almost certainly understood by key decision makers in Israel, which view Hezbollah’s military capability as an extension of Iranian influence on its northern border.
Israel is unlikely to agree to Hezbollah’s demands for a withdrawal from southern Lebanon, particularly in light of reports regarding renewed arms smuggling from Iran and Hezbollah’s resumption of weapon production. Israel has also demanded that it will not withdraw until the Lebanese Armed Forces (LAF) can fully secure southern Lebanon from Hezbollah, an objective the LAF is unlikely to achieve in the immediate future. To counter the threat of Hezbollah, Israel will likely maintain its positions in southern Lebanon and continue its strikes throughout the country, a course of action that could jeopardise the fragile ceasefire agreement.
Throughout April, the IDF has conducted multiple strikes in southern Lebanon, the Bekaa Valley and several strikes in Beirut against high-value targets within Hezbollah, including against a senior figure responsible for coordinating external attacks against Israel with Iran, strikes that are likely increasing the chances of Hezbollah attacks on Israel. There is a realistic possibility that the recent evidence of the Iranian sustainment of Hezbollah will result in Israel increasing its strikes within Beirut, including strikes on the Port of Beirut and weapon production facilities in the city to counter Hezbollah’s attempts to regroup.
Algeria and Mali: Tensions increase after Algeria shoots down Malian drone.
On 6 April, Malian authorities accused their Algerian counterparts of “exporting terrorism” after Algerian forces shot down a Malian drone which allegedly entered Algerian airspace. In response, Algiers announced a complete airspace closure with its southern neighbour, halting flights between the two countries. According to Malian authorities, the drone was shot down while still in Malian airspace, and as it was carrying out an operation against Azawad fighters present in the area. In addition to Mali, Alliance of Sahel States (AES) members Burkina Faso and Niger also recalled their ambassadors from Algeria over the diplomatic crisis.
Solace Global Assessment:
Mali is currently fighting multiple jihadist and independentist insurgent groups. Several Azawad independentist groups operate in the country’s north under the Strategic Framework for the Defense of the People of Azawad (CSP-DPA) and maintain ties with Jamaat Nusratul Islam wal-Muslimin (JNIM), a jihadist coalition of al-Qaeda-affiliated groups. Mali’s junta has deployed significant resources to root out CSP-DPA, including systems provided by its Russian allies. These have so far been unsuccessful, with the junta forces suffering several notable defeats. In July 2024, Azawad militants, later joined by JNIM fighters, ambushed a convoy of Malian forces and Wagner Group operatives in Tinzaouaten, killing over 80 while suffering small losses.
Algeria’s relations with Mali have significantly worsened following the latter’s January 2024 withdrawal from the 2015 Algiers Accords. Algiers is also highly likely sceptical of Russia’s involvement in the south. While Moscow is one of Algeria’s key allies, the deployment of Russian personnel under the Wagner Group (and later Africa Corps) banner has resulted in a series of atrocities against Tuareg civilians, which have likely increased local support for independentist Azawad groups. While these are mostly active south of the border, Algeria likely assesses that the insurgency has the potential to spill into its territory. Seeking to avoid a confrontation with Russia over Wagner’s destabilising impact, Algeria has so far maintained a balancing approach to diplomacy. However, the downing of the Malian drone likely demonstrates that Algiers is willing to adopt a more assertive approach towards Mali.
Yemen: Potential renewal of civil war poses threat of strikes against Saudi Arabia and UAE.
A CNN article published on 6 April stated that regional diplomatic sources briefed that preparations are underway by the Republic of Yemen Government (ROYG) for a ground offensive against the Houthis. The article indicates that the offensive ‘would be launched from the south and east, as well as along the coast’ and that it could involve ‘Saudi and US naval support in an attempt to retake the port of Hodeidah’. The potential ground offensive comes amidst an intensified US campaign of aerial strikes against Houthi-controlled Yemen since mid-March. On 8 April, the US Ambassador to Yemen, Steve Fagin, met with the leader of ROYG’s Presidential Leadership Council (PLC), President Rashad al-Alimi, to discuss ending the Houthi threat to maritime shipping. On 9 April, the Saudi Foreign Minister Prince Faisal bin Farhan met with the US Secretary of State Marco Rubio in the US and, according to an official statement, discussed eliminating the Houthi threat to the region.
Solace Global Assessment:
The Yemeni civil war, which was primarily fought between 2014-2022, has been essentially frozen, with a six-month UN-brokered ceasefire having officially lapsed in October 2022 but de facto having held since. The Saudi-led coalition that intervened, consisting of Saudi Arabia, the United Arab Emirates (UAE), Kuwait, Bahrain, Qatar, Egypt, Jordan, Morocco and Sudan, conducted over 25,000 airstrikes against the Houthis, the majority in Sanaa, and primarily using the Saudi military. The campaign, however, failed to dislodge the Houthis, and it is almost certain that airpower without comprehensive and capable ground support is insufficient to defeat the Houthis. Riyadh has highly likely been incentivised to avoid a return to war with the Houthis, with their previous intervention having accumulated high economic and diplomatic costs that likely pose a threat to the Saudi Vision 2030 government program to diversify the economy and make Saudi Arabia an inviting location for both investment and tourism.
Riyadh is likely reluctant to return to war, however, the Trump administration likely has a strategic priority to nullify the Houthi threat, an objective that highly likely could only be achieved with significant regional support and a ground offensive. It is likely that a ROYG ground offensive would be mainly conducted using UAE-backed Southern Transition Council (STC) forces, notably the Giants Brigades, with the formerly separatist STC likely controlling the most powerful forces in internationally recognised Yemen. A return to civil war, depending on the level of Saudi and Emirati involvement, could likewise see a return to Houthi long-range strikes against targets in Saudi Arabia and the UAE. In Saudi Arabia, the Houthis previously targeted Saudi Aramco and military facilities across the country, including in and around Riyadh. In the UAE, the Houthis targeted Abu Dhabi National Oil Company (ADNOC) targets, including the Mussafah facility in Abu Dhabi and ADNOC trucks outside Abu Dhabi International Airport (AUH), in addition to a new terminal under construction at AUH, and also targeted Al Dhafra airbase which hosts US forces in Abu Dhabi. A claimed Houthi attack against Dubai International Airport (DBX) was credibly disputed by a Bellingcat investigation.
Between 2015 and 2018, the Houthis conducted long-range attacks across the Arabian peninsula primarily with ballistic missiles, whereas between 2019 and 2022, Houthi attacks were primarily conducted with one-way attack uncrewed aerial vehicles (OWA-UAVs). While Houthi launch capabilities have likely been degraded by recent US and Israeli military action, it is highly likely that the Houthis have gained proficiency in the use of OWA-UAVs and other long-range weapon systems through their anti-shipping and anti-Israel campaign. Saudi and Emirati air defence is proficient, with Saudi Arabia having addressed their likely previous vulnerability to ballistic missiles with the addition of Terminal High Altitude Area Defense (THAAD) systems. Nonetheless, a return to regular long-range Houthi strikes against the Gulf states would likely cause significant air travel disruption with airport and airspace closures, and even successful interceptions can pose risks due to the danger of debris.
Somalia: Al-Shabaab make significant territorial gains, threatening Mogadishu.This is the title.
In the past week, al-Shabaab seized control of the Afgoye-Mogadishu and Mogadishu-Balcad corridors, tightening control on the outskirts of Mogadishu. The group has also escalated bombing campaigns in recent weeks. On 5 April, mortar rounds landed near the presidential palace in Mogadishu, injuring several people. The following day, al-Shabaab launched mortar strikes, which landed near the airport and near Halane military base, wounding two civilians and triggering flight cancellations from Turkish Airlines. At least six mortar rounds reportedly landed inside the airport compound. Meanwhile, clashes are ongoing across multiple frontlines in the Middle Shabelle region, where a major al-Shabaab offensive has been ongoing since 2025. The government has confirmed it has taken control of Adan Yabaal and a village in Adale. In response to al-Shabaab’s strategic gains, President Hassan Sheikh Mohamud proposed a platform to unite the fractured national government institutions, regional states, and opposition parties.
Solace Global Assessment:
The ongoing al-Shabaab offensive is capitalising on stretched government resources, with the Somali Armed Forces spread between combating al-Shabaab and Islamic State Somalia (ISS) insurgencies, weaknesses in the African Union Support and Stabilization Mission in Somalia (AUSSOM), and Houthi support for the group. Since February, attacks have reportedly increased by approximately 50 per cent compared to its 2024 average, with al-Shabaab recapturing several areas of the Middle Shabelle region. AUSSOM has, so far, been relatively ineffective and marred by funding shortages and internal disagreements, with Burundi recently withdrawing from the mission.
Given the weakness of Somalia’s armed forces, Mogadishu is heavily reliant on external support. The US has ramped up air support, with President Donald Trump relaxing the rules of engagement for field commanders, enabling air campaigns against al-Shabaab in the Middle Shabelle region, as well as ISS in Puntland. Turkey, meanwhile, has agreed to provide additional military aid, equipment, intelligence sharing, and the deployment of approximately 5,000 personnel from the President Recep Tayyip Erdoğan-aligned private military company SADAT. Turkey’s support is likely crucial for ensuring the survival of Somalia’s government, with its largest overseas base being in Mogadishu. Continued government survival is of significant interest to Turkey. Turkish companies manage critical infrastructure in Somalia, including Mogadishu’s port and airport, and Erdogan has emerged as an influential mediator in regional disputes in the Horn of Africa and a key security partner to Mogadishu.
The loss of the Afgoye-Mogadishu and Mogadishu-Balcad corridors will highly likely precipitate intensified attacks in central Mogadishu, with al-Shabaab likely having more chances to smuggle explosives into the capital. Furthermore, the Mogadishu-Balcad corridor connects Mogadishu to Middle Shabelle, which will highly likely weaken government efforts to counter the ongoing al-Shabaab offensive in the region. The capture of the corridors will also highly likely reduce trade and commerce in the region, driving up consumer costs and increasing pressure on the government. While an imminent complete capture of Mogadishu is unlikely due to the continued international support to the government, it will almost certainly further exacerbate the security situation by weakening government counteroffensive measures and easing al-Shabaab’s access to the capital.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Nationwide strike scheduled in Belgium throughout April.
Nationwide strikes have been organised throughout April in response to the federal government’s plans to cut social spending to reduce the federal budget. Following a 7 April nationwide strike, further strikes have been organised throughout the month, with several key sectors involved. Five railway trade unions are planning four 24-hour strike actions every Tuesday in April (8, 15, 22, and 29 April). A planned national strike on 29 April will likely result in major disruptions to public transport and other public services across the country, with previous strikes leading to the suspension of services at both of Brussels’ international airports.
Germany’s Christian Democrats and Social Democrats agree on coalition deal.
The so-called “grand coalition” between the Christian Democrat sister parties (CDU-CSU) and the Social Democrats (SPD) was the obvious outcome of the last elections, guaranteeing the survival of Germany’s cordon sanitaire against the far-right Alternative for Germany (AfD), now the second force in parliament. The CDU-led government will likely remain fragile. Chancellor Friedrich Merz has promised his voters harsher measures on migration, also intending to keep the AfD at bay. However, the implementation of these policies, such as turning away asylum seekers at Germany’s borders, may indirectly put pressure on the SPD, whose electorate remains opposes Merz on migration, threatening the coalition. Moreover, the new government, whose members recently agreed on revising Germany’s “debt brake” to increase defence spending, will likely have to confront a more pessimistic economic outlook resulting from the trade war with the US.
Large-scale protests in Rome against European rearmament.
Around 80,000 people gathered in the Italian capital on 5 April, under the lead of the populist 5 Star Movement (M5S) and some left-wing parties. The demonstrations opposed the Meloni government’s support for ReArm Europe, the EU’s military development and procurement plan aimed at reducing reliance on Washington. M5S, which, although founded as a big-tent party, has increasingly established itself as a populist left-wing alternative to the “establishment” Democratic Party (PD), is likely seeking to capitalise on the Italian electorate’s relatively high levels of scepticism towards Brussels’ support for Kyiv.
Thousands rally in Central African Republic (CAR).
On 4 April, thousands of protesters gathered in Bangui to peacefully protest the Wagner-backed President Faustin Archange Touadera’s plans to run for a third term in a rare demonstration of public anger. Demonstrations were organised by opposition parties who reject Touadera’s plans for a third term and come amid worsening living conditions and reports of Wagner’s extrajudicial killings, sexual violence, and looting by Wagner forces. Demonstrators signalled their anger at the governance of Touadera and his Wagner backers, calling for the protection of CAR’s sovereignty and for Touadera, and by extension Wagner, to be removed from power. The CAR was the first African country where Wagner established operations, helping the government prevent rebels from taking control of Bangui in 2021, propping up Touadera under the guise of protecting state sovereignty. The growing protest movement reflects an increasing loss of legitimacy for Touadera, who is perceived as dependent on Wagner to hold power, as well as a broader resistance to perceived foreign occupation. While the protest movement is likely to grow, Touadera will highly likely prioritise regime survival and use security forces to crack down on demonstrations with force.
Detained South Sudanese vice president ousted by his party.
On 9 April, Sudan People’s Liberation Movement-In-Opposition (SPLM-IO) members voted to replace Riek Machar as head of the party with peacebuilding minister Stephen Par Kuol as interim chair until Machar is released. Machar loyalists did not attend the meeting, with some having fled the country. The decision comes approximately two weeks after Machar was arrested following violence conducted by the Machar-linked White Army in Nasir, Upper Nile state. The arrest, triggered by criticism of the presence of Ugandan troops in South Sudan, has threatened to plunge the country back into civil war by violating the 2018 peace agreement, which stipulated power-sharing terms between the two sides. Despite Kuol’s reaffirmation of the peace commitments, replacing Machar with Kuol risks undermining the peace agreement by fragmenting the SPLM-IO and weakening its role in the unity government, undermining the division of power stipulated by the agreement’s terms.
Tanzanian opposition leader arrested.
On 9 April, Tanzanian opposition leader Tundu Lissu, chairman of the CHADEMA party and a prominent critic of the government, was arrested after a rally in Ruvuma in the south of the country. Lissu has been charged with treason, a capital offence, over allegedly making remarks inciting rebellion and disruption ahead of the 2025 general elections. The charges have been dismissed by the opposition as politically motivated and meant to eliminate Lissu, who had been the runner-up in the 2020 presidential election. The arrest has also drawn widespread international and domestic criticism of President Samia Suluhu Hassan’s human rights record after a series of arrests, abductions and the targeting of opposition figures. There is a realistic possibility that the arrest of Lissu will incite widespread and potentially violent unrest in Tanzania.
Security, Armed Conflict and Terror
Three arrested for planning attack in Dunkirk, France, on behalf of the Islamic State (IS).
French authorities discovered attack plans and, reportedly, an “explosive vest”. This likely makes the recent plot more sophisticated than other “lone wolf” attack plans and could imply that the suspects had some outside direction. Dunkirk is a high-visibility location due to its political relevance on both sides of the Channel, being both a tourist destination and one of the key transit points for migrants seeking to make the crossing to the United Kingdom.
Libyan authorities tell ten aid groups to stop operations helping migrants.
Authorities claim that the groups violate local law and commit “a hostile activity targeting the Libyan demographics” by helping migrants from Sub-Saharan Africa settle in Libya. The vast majority of migrants entering Libya and neighbouring Tunisia do so with the aim of crossing the Mediterranean. However, since the refugee crisis of 2015, the influx of migrants, who often remain for months or years in local towns prior to making the crossing, has driven a considerable increase in anti-migrant sentiment. The ban is likely to result in a worsening of the already poor humanitarian conditions of the migrants in Libya. Aid organisations provide migrants with essential goods and services like food, clothing, housing, and medical care. Without them, there is a realistic possibility of migrants being forced to rely more frequently on local criminal groups, exposing them to a significantly greater threat of violence and abuse, including enslavement.
Reports indicate Boko Haram is gaining ground in northern Nigeria.
The governor of Nigeria’s Borno State, Babagana Zulum, has warned that the jihadist group Boko Haram is staging a comeback. The comments were made after Boko Haram recently staged a series of attacks and seized control of some parts of the north-eastern state. Attacks have targeted Nigerian army bases and police stations, not just the civilian population. Moreover, some operations reportedly involved cooperation with the Islamic State’s West Africa Province (ISWAP). The central government has downplayed the situation, claiming that security in the region has improved. However, the central government has diverted military resources to the northwest of the country to deal with endemic banditry and the emergence of a new jihadist group linked to Niger, the Lakurawa, a move that has likely overstretched government forces and provided Boko Haram with greater freedom of movement.
Environment, Health and Miscellaneous
Severe flooding in Kinshasa, DRC, kills dozens.
At least 33 people have died in the capital of the Democratic Republic of the Congo (DRC) after days of heavy rains resulted in widespread flooding. The rains caused the Ndjili River to overflow, posing a particularly severe risk to the informal settlements located near its banks. The floods also temporarily blocked access to the airport, and to severely impacted parts of the city, complicating search and rescue efforts. Responses to the flooding are likely to be complicated by the ongoing conflict in the eastern DRC, which has both stretched Kinshasa’s resources and prompted the evacuation of international personnel, including some humanitarian workers, from the country.
Asia–Pacific
Myanmar: Fighting continues despite post-earthquake ceasefires.
After a 7.7-magnitude earthquake struck Myanmar on 28 March, the National Unity Government (NUG) and the Three Brotherhood Alliance, representing ethnic resistance groups across the country, announced a temporary ceasefire of one month beginning on 1 April. Under the unilaterally declared ceasefire, the rebel groups agreed not to initiate any offensive operations and would only engage in self-defence. After initial attempts to resist a ceasefire, Myanmar’s State Administration Council announced that it would observe one from 2 April to 22 April. However, multiple international observers, including the UN, have reported widespread ceasefire violations conducted on both sides. The NUG, a shadow government formed after the coup, has accused the junta military of conducting over 60 airstrikes and artillery barrages since the earthquake, resulting in the deaths of at least 68 civilians. Recent estimates indicate that over 3,000 people have now died, with the toll expected to rise significantly as the rubble is cleared. Hospitals are reportedly overwhelmed, and shortages of medical supplies, fuel, clean water and shelter are hampering relief operations.
Solace Global Assessment:
The junta government has a precedent of exploiting ceasefires to contain ethnic rebel groups under the guise of tentative truces. The junta has likely only agreed to a temporary ceasefire publicly to improve both its international and domestic image, with elections planned in late 2025 or early 2026. Reports on the ground even suggest that the junta is actively obstructing relief efforts while expanding operations in earthquake-affected areas. This has reportedly included the hindering of access to aid organisations, the blocking of aid and the seizure of supplies, combined with a continuation of air and artillery strikes.
After months of rebel advances, it is unlikely that the junta will cease offensive operations, likely fearing that the rebel groups will also exploit the ceasefire to regroup and continue their advance. Part of the junta’s strategy is likely to restrict the delivery of aid to areas under rebel control, thus restricting the rebel groups’ access to vital supplies such as water, food, medicine and other equipment, especially near the current lines of engagement.
However, with international aid organisations operating near earthquake-affected areas, there is likely more coverage of junta operations on the ground. As a result, the junta may adapt its strategy by increasing the use of airstrikes, targeting rebel-held or strategically significant areas further behind the front lines, such as Kachin State, Shan, and Kayin (Karen) States, which remains a key stronghold for the resistance forces and are critical to rebel supply chains and operations. High-value targets for the junta are likely to include rebel leadership, force concentration, ammo depots and other military targets. However, reports have also indicated that aid convoys have been targeted, as well as critical infrastructure like roads and bridges that sustain rebel operations and facilitate the delivery of humanitarian aid.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
South Korean election scheduled for 3 June.
On 7 April, South Korea’s cabinet voted to confirm a 3 June election date. The decision follows former President Yoon Suk Yeol’s impeachment and removal from office following his declaration of martial law on 3 December. In the 2022 election, Yoon had beaten opposition liberal Democratic Party Lee Jae-myung by a narrow margin, making him the frontrunner in the upcoming election. However, Lee faces legal challenges due to multiple charges, including violating election law and bribery. Kim Moon-soo will likely lead the incumbent conservative People Power party. A 4 April Gallup poll had 34 per cent of respondents supporting Lee and nine per cent backing Kim.
Garment workers’ protest in Bangladesh results in more than 50 injuries.
The clashes, which lasted for at least three hours, erupted in Rupganj, near Dhaka, outside a local manufacturing plant. According to local media, at least 120 workers, who had been reportedly fired prior to Eid, had been demonstrating in front of the plant for two days prior to the intervention of authorities. In addition to 50 injuries, at least ten workers have been arrested. Further protests regarding labour disputes during Eid have occurred in other parts of Bangladesh, with the garment industry a particularly notable hotspot for unrest.
US academic charged under lèse-majesté laws in Thailand.
The US State Department has expressed its alarm after an American academic, Dr. Paul Chambers, was charged under Thailand’s strict lèse-majesté laws. The laws, aimed at suppressing defamation of Thailand’s monarchy, can carry sentences of up to 15 years and are often used to suppress the opposition. Dr. Chambers, a lecturer at Naresuan University in central Thailand, was reportedly arrested due to his research on the political relationship between Thailand’s monarchy and military. The arrest of a foreigner under lèse-majesté laws is relatively rare, however, Dr. Chambers was likely viewed as an important target by ultra-loyalist groups, who have targeted him with disinformation and online hate campaigns in the past.
Security, Armed Conflict and Terror
Deportations of Afghans from Pakistan underway.
At least 1,600 Afghans had been deported from Punjab and Sindh by the beginning of the week, and authorities have reportedly detained 5,000 for repatriation. In total, around 9,000 people have been deported from Pakistan since 1 April, and an unspecified number have crossed the border spontaneously. A majority of them have Afghan Citizen Cards (ACCs), while a minority reportedly have no identifying documents. Taliban authorities have reacted negatively to the deportations, accusing Islamabad of mistreating its Afghan residents and using them for “political goals”. The deportations are likely to increase tensions between Pakistan and Afghanistan. There is a realistic possibility that the worsening security environment will drive terrorism in Pakistan. In Afghanistan, extremist groups like the Islamic State Khorasan Province (ISKP), which is particularly active in the country’s southeast, may seek to target returning Afghans to destabilise the Taliban government.
Mob violence in Bangladesh continues to rise.
The Daily Star, Bangladesh’s most circulated English-language newspaper, reported that, between February and March, cases of mob violence, including killings, have doubled across the country. This follows a widespread increase in insecurity and crime, particularly violent crime, that has accelerated since the August 2024 ousting of Sheikh Hasina. Recent notable cases of mob violence include an attack on the properties of Awami League (AL) party members in Sylhet, and vandalism of American-owned businesses in Chittagong during a pro-Palestine demonstration. While mob violence – and “bulldozer justice” – are long-standing issues in Bangladesh, the fall of Hasina’s Awami League has almost certainly created a security vacuum. Police forces, which were previously staffed by Hasina loyalists and dependent on AL support, are now at the centre of an often violent, political competition led by the remaining major parties, who seek to govern post-Hasina Bangladesh.
China conducts naval drills at Cambodian naval base.
On 6 April, the People’s Liberation Army Navy (PLAN) conducted naval drills outside of the recently enlarged naval base at Ream, Cambodia, in the Gulf of Thailand. China’s presence in the Gulf of Thailand has raised concerns that the PLAN is establishing a permanent footprint to the south of the South China Sea and will lead to a major increase in Chinese naval and coast guard activity in the contested waters, likely increasing the chances of escalation. Cambodia has repeatedly denied reports that it has agreed to a clandestine deal with China to station its forces at the base, reiterating its stance that it is open to hosting military vessels from other countries.
Environment, Health and Miscellaneous
Eruption at volcano in central Philippines leads to school closures and NOTAM.
On 8 April, the Kanlaon volcano on the island of Negros in central Philippines erupted, leading to a 4,000 metre high ash plume drifting southwest. A level three out of five alert issued by the Philippine Institute of Volcanology and Seismology (Phivolcs), which indicates a high level of volcanic unrest, has been in effect for Mount Kanlaon since another eruption in December 2024. The level three alert recommends all residents within a six-kilometre radius of the volcano to evacuate, with the evacuations having previously taken place in December, which almost certainly reduced the immediate danger of possible casualties. Philippine authorities reported that approximately 48,000 people were impacted by the 8 April eruption. Several precautionary measures have been implemented, including the suspension of schools in four districts west of the volcano in Negros Occidental, and the issuance of a Notice to Airmen (NOTAM) by the Philippines Civil Aviation Authority for flights near Kanlaon volcano.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence

Increased Risks Expected During Passover Celebrations
Intelligence cut-off: 13:00 GMT 07 April 2025
Passover, or Pesach, is one of the major holidays of the Jewish religious calendar, as it marks the Exodus of the Israelites from Egypt described in the Torah. In 2025, the holiday begins on the evening of 12 April and ends on 20 April.
Passover occurs against a backdrop of sharply rising global antisemitic incidents, which have escalated significantly following Hamas’s 7 October 2023 attack in southern Israel and Israel’s subsequent invasion of Gaza. The holiday also falls during renewed hostilities in Gaza, which reignited after the collapse of the ceasefire between Israel and Hamas in March 2025.
Over the past 18 months, there have been numerous cases of attacks targeting Jewish people and places of worship, as well as any entities associated with Israel. Many of these incidents have occurred on dates of particular significance to Jewish and Israeli communities. They have included religious observances, such as the firebombing of a Melbourne synagogue during Hanukkah; historical commemorations, such as the lone wolf attack on the Israeli consulate in Munich on the 2024 anniversary of the 1972 Olympics massacre; and events linked to Israeli entities, such as the Amsterdam riots on the day of a Europa League football match involving an Israeli team.
On 1 April, Israeli authorities stated that they had thwarted a joint terror attack plot involving Hezbollah, Hamas, and Iran. The alleged plan was to target Israelis abroad or the wider Jewish community in response to the resumption of hostilities in Gaza.
Timeline of Global Security Incidents Since October 7 2023
INTELLIGENCE ANALYSIS
Lone Actor and Organised Group Attacks Possible Around Passover
There is a realistic possibility of terror attacks on or near Passover. Lone wolves, particularly espousing radical Islamist or far-right ideologies, are likely to target Jewish places of worship or community centres. Places of interest associated with Jewish history, such as Holocaust memorials and museums, are also likely targets due to their high traffic and visibility. Attackers may target Israeli consulates and embassies, although the risk here is lower due to their enhanced security presence. Attacks on Jewish interests may not be confined solely to Israel and major Western cities, as evidenced by previous attacks or plots targeting Jewish communities in South America and East Asia.
In addition, organised terror groups may seek to stage attacks during or near the holiday. Groups like Hamas and Palestinian Islamic Jihad likely retain the ability to stage attacks in Israel and the West Bank, particularly targeting security personnel and Israeli civilians. Moreover, the Islamic State (IS) and its network of global affiliates have intensified efforts to stage external attacks over the past two years and may seek to capitalise on the high visibility of the religious holiday to stage a high-impact and symbolic attack.
There is also an elevated threat of civil unrest around Passover, particularly in cities with a history of Gaza-related protests. While most demonstrations are likely to be peaceful, isolated incidents of vandalism or direct action against businesses, diplomatic sites, or religious buildings linked to either side of the conflict remain possible. In 2024, Jewish anti-war protestors staged a demonstration in New York, demanding that the US cease military aid to Israel.
Travel Risk Advice: Safety Guidelines for High-Risk Events and Holidays
- Closely monitor local news reports and government alerts.
- Avoid all large gatherings, including, if possible, large celebrations in public spaces.
- Consider alternative transport routes. Avoid public transport.
- If attending an event, identify exit routes and safe points. Identify if and which authorities are present in the area.
- Maintain regular communication with management or other safe contacts. Establish clear communication protocols ahead of travel.
- Monitor alerts and updates on Solace Secure.
- Adhere to all instructions issued by authorities.
- Have local emergency numbers and other key contacts available and saved on your personal devices.
- When attending events, always carry personal identification documents with you.
Subscribe to free weekly intelligence

Key Safety and Risk Factors Ahead of Songkran 2025
Executive Summary
- Songkran, or the Thai New Year, occurs from 13 to 15 April each year, but typically causes disruptions from 11 to 17 April.
- Celebrations involve water fights, symbolising washing away bad luck and welcoming the new year.
- Various health risks are associated with high temperatures and potentially contaminated water.
- There is a high threat of road traffic accidents, with higher numbers of intoxicated drivers, speeding, and hazardous road conditions.
- Rates of petty crimes like pickpocketing and bag snatching increase during Songkran.
- Rates of violent crime often increase as a result of high levels of inebriation.
- Rates of sexual harassment increase during celebrations.
SITUATIONAL SUMMARY
What to Expect for Songkran 2025
Songkran, meaning “passage of the sun”, occurs from 13 to 15 April each year (although celebrations usually extend from 11 to 17 April) and celebrates the Thai/Buddhist New Year. It is one of Thailand’s most important holidays and is marked by nationwide celebrations, including parades, religious festivities, and family gatherings.
Widespread water fights are a primary feature of the festival, which symbolise washing away bad luck and welcoming the new year. Many Thais visit temples to “make merit” which typically consists of giving alms to monks and pouring water over statues of the Buddha. Thai residents, diaspora, and tourists usually travel to major cities in Thailand to spend time with their families and participate in the festivities.
Although Songkran is celebrated nationwide, the style of celebrations differs regionally. The largest celebrations typically occur in the capital, Bangkok, a hub for celebrations attracting thousands of nationals and tourists each year. In preparation for the festival, roads are closed and stations equipped with water guns are set up. Chiang Mai is one of the most popular destinations, with thousands gathering around the moat and Thapae Gate to conduct water fights and participate in parades. In Pattaya, the celebrations last until 19 April and include sand pagoda building and live shows.
Related festivals are also celebrated by Cambodia (Cambodian New Year), Laos, Sri Lanka (Sinhalese New Year), Myanmar (Thingyan), Arunachal Pradesh and parts of Assam in India (Sangken), in Xishuangbanna in China, and parts of northern Vietnam.
Myanmar Earthquake Impact on Songkran 2025
The Myanmar earthquake on 28 March 2025, which was felt in Bangkok, will almost certainly impact Songkran. The Tourism Authority of Thailand (TAT) has confirmed that Songkran will continue, despite the damage, but high-rise hotels will undergo inspections.
The Thai Hotels Association (THA) predicts that tourism revenue will fall by 10-15 per cent over the next two weeks, with tourists either cancelling their trips or changing their destinations to other Thai cities, including Pattaya and Phuket. This will highly likely reduce the density of the people celebrating Songkran in the capital but may conversely increase the density of revellers in other major cities, raising the associated risks.
TRAVEL RISKS: TRANSPORTATION
Travel Disruptions and Road Risks During Songkran
Songkran is one of the most congested periods of the year and typically causes significant travel disruptions. Many people travel to their hometowns or tourist attractions; with railways being overly crowded and flights being unaffordable, road travel is common, which increases the number of road users during this period. Around Thailand’s major cities, authorities typically close roads ahead of the celebrations and set up checkpoints to deter drunk driving.
The festival attracts many tourists, stretching transportation networks and local infrastructure. In 2024, approximately 1.9 million foreign tourists visited Thailand during Songkran, which was a 37.54 per cent increase from the year before, something attributed to government measures to ease travel and post-COVID increases in tourism. Tourists typically cause an increased demand for public transport, including taxis and buses, further exacerbating the need for locals to use private transport.
Songkran causes a spike in road traffic accidents (RTAs), and the week of festivities is known locally as the “seven dangerous days”. During this period, the RTA rate approximately doubles in a country already experiencing very high rates. From 11 to 17 April 2024, there were at least 480 RTA fatalities and over 2,000 injuries, equating to approximately 69 fatalities per day. This puts Thailand temporarily in the top 10 the most dangerous countries in the world for RTAs during Songkran. Motorcycles account for most of the deaths, which are generally attributed to driving while intoxicated, speeding, cutting lanes, wet road surfaces, and inadequate safety wear. Revellers throwing water at cars and motorcycles has also contributed to causing accidents.
TRAVEL RISKS: CRIME
Crime and Safety Concerns at Songkran Festivals
The large crowds and heavy tourist presence also raise the likelihood of petty theft, including pickpocketing and bag snatching. In 2024, organised gangs targeted festival-goers at the Pattaya Water Festival, stealing large amounts of cash, mobile phones, credit cards, and essential documents. Foreign travellers are often targeted because of their perceived higher wealth and unfamiliarity with the local area.
Violent crime typically also increases around Songkran due to the large crowds, widespread alcohol consumption, and road rage. In Pattaya, during the 2024 celebrations, a man was arrested after threatening others with a gun after a violent altercation. In the Isaan province of Roi Et the same year, six men were arrested for beating and stabbing two travellers after an argument linked to road congestion.
Men are generally disproportionately at risk of being violently assaulted, accounting for 82 per cent of deaths from assault during Songkran from 2009 to 2011. Attacks on foreigners are often linked to cultural and social misunderstandings perceived as disrespectful or insulting to Thai culture. Examples include excessive intoxication, criticism of the monarchy, wearing unsuitable attire at culturally significant sites, showing disrespect toward national symbols like the Thai flag or anthem, and engaging in overt public displays of affection.
Sexual harassment, sexual assault, and drink spiking also pose a risk to both locals and travellers, with women reporting cases of harassment during water fights. A survey taken in March 2024 found that 32.43 per cent of the Bangkok residents surveyed were sexually harassed at Songkran celebrations in the previous three years and 14.9 per cent did not join water fights due to fears of sexual harassment. Authorities typically launch anti-harassment campaigns leading up to Songkran, stressing its illegality.
While celebrations are widespread, travellers can face penalties for involving unwilling participants. Splashing water on people not involved in the celebrations can be considered causing a nuisance or damaging property, leading to potential prison sentences of up to one month or a 10,000-baht (228 GBP) fine. During the 2024 celebrations, for example, three tourists from Hong Kong were jailed for 28 days after splashing a police officer with water. Similarly, dumping powder on unwilling participants, an act which typically involves non-consensual contact, could result in a public indecency charge.
TRAVEL RISKS: HEALTH
Festival Health Risks: Water Quality, Heat, and Infections
The water fights, large crowds, and high temperatures during Songkran frequently result in elevated health risks. Songkran is often associated with higher rates of colds, flu, respiratory diseases, gastrointestinal diseases, skin diseases, and conjunctivitis. This is largely due to untreated water being used during water fights, which can carry bacteria, viruses, and other pathogens. For example, in Chiang Mai, water is often taken from the moat, while in other towns, it is often sourced from lakes and rivers.
In 2015, lab tests detected a large number of parasites in the Chiang Mai moat, triggering cleaning operations before the festival. In 2024, at least 65 children contracted rotavirus after attending a foam party in Suphan Buri. In the same year, new COVID-19 cases surged to a daily average of 143 during the week following Songkran. The combined risks of infection, road traffic accidents, and the aftermath of the earthquake will likely put a strain on hospitals during Songkran in 2025.
Tips for Staying Safe During Songkran 2025
- Plan your journeys in advance and allow extra time to accommodate road closures and disruptions.
- Avoid riding motorcycles, whether as a driver or passenger, from 11 to 17 April.
- If you must drive, ensure you utilise safety features such as a seatbelt.
- Be cautious when crossing the streets, as roads are often slippery, and drivers may be intoxicated.
- Avoid walking close to busy roads.
- Wrap valuables in waterproof material, such as plastic or zip-lock storage bags.
- Wear lightweight, quick-drying, dark-coloured clothing.
- Do not take part in water fights in temples, government buildings, or inside public transport.
- Do not splash monks, the elderly, babies, or figures of authority, such as police officers.
- Respect local customs and traditions, ensuring you do not offend Thai culture.
- Research local regulations before the festivities as some areas ban alcohol during Songkran or set up “safe zones”.
- Drink plenty of water throughout the day and avoid excessive amounts of alcohol to remain hydrated.
- Avoid overt displays of wealth and exercise vigilance against pickpocketing.
- Be alert to the risk of drink-spiking. Do not leave your drink unattended; if you do, purchase a new one when you return.
- Consider wearing ear and eye protection to minimise the risk of conjunctivitis or ear infections.
- Avoid taking part in water fights near stagnant bodies of water, as this water is often used and may contain pathogens.
- Ensure you wash thoroughly after water fights to avoid disease.
- Take the necessary precautions against sun- and heat-related illnesses, considering that water may remove sunscreen applied to the skin.
- Carry emergency contact details with you at all times.
- Due to the heightened risk of injury and illness, travellers should have comprehensive travel insurance in place.
SUPPORTING SAFE TRAVEL ACROSS THAILAND
Journey Management Services for Travel to Thailand
Songkran and other national festivals in Thailand can bring increased movement, road closures, and heightened risks. For organisations, this means planning travel with greater care and oversight.
Solace Global provides tailored journey management services to support safe and seamless movement across Thailand. We combine local insight with secure transport coordination, route planning, and real-time monitoring — all underpinned by intelligence from our Global Security Operations Centre (GSOC).
Subscribe to free weekly intelligence

Executive Summary
Americas (AMER)
Major anti-gang protests in Haiti likely reflect a deteriorating humanitarian situation, which the gangs are likely attempting to exploit to increase the population’s dependence on them.
The Colombian government’s unilateral end to peace talks with the ELN almost certainly indicates an end to “total peace” and marks a significant shift in its policy towards rebel and criminal groups.
Europe, Middle East & Africa (EMEA)
The sentencing of far-right leader Marine Le Pen almost certainly deepens political tensions in France and is likely to increase the risk of political violence and unrest.
It is highly likely that Russia is exploiting poorly defined ceasefire terms and is delaying negotiations to pursue further territorial advances in Ukraine.
There is a realistic possibility that an Israeli strike on a Hezbollah external attack planner in Lebanon indicates a shift in Hezbollah’s strategy to target Israeli and Jewish interests abroad.
The Israeli establishment of a new operational corridor in Gaza is highly likely meant to isolate the remaining Hamas units. There is a realistic possibility of a growing consensus in Tel Aviv regarding annexing parts of Gaza.
It is likely that, due to its vulnerable position, Tehran will pursue a relatively cautious approach after Trump’s threats to bomb Iran. However, military escalation would likely force retaliation, threatening a regional conflict.
There is a realistic possibility that Uganda will support the newly formed Convention for the Popular Revolution (CPR) in the DRC’s Ituri province, highly likely exacerbating humanitarian issues in the region.
Asia-Pacific (APAC)
Worst-case scenarios for an anticipated Nankai Trough megaquake in Japan predict mass casualties and the loss of almost half the country’s total GDP, almost certainly reaffirming the need for disaster planning.
Large-scale Chinese military drills around Taiwan are highly likely rehearsing a blockade of the island and almost certainly demonstrate the coordination of multiple PLA branches to conduct multi-domain operations.
North, Central and South America
Haiti: Major protests over surge in gang violence
On 2 April, thousands of Haitians protested in the capital, Port-au-Prince, to denounce a surge in gang violence. Protestors demonstrated outside of government buildings and demanded that the government do more to keep them safe. Gunfire was exchanged between armed protesters and the police outside the offices of the prime minister and the transitional presidential council, resulting in many protestors fleeing the area.
The protests follow an increase in gang activity, which has involved gangs like the Viv Ansanm gang coalition attempting to move into new parts of the capital, where gangs are estimated to control 85 per cent. Recent gang activity has forced more than 60,000 people to flee their homes in one month alone, according to the UN’s International Organization for Migration.
Solace Global Assessment:
Recent developments indicate that the gangs are attempting to expand their control and move out of their traditional areas of operations. Increased attacks in the capital likely suggest that the gangs are attempting to secure the remaining 15 per cent of Port-au-Prince and isolate the government to just a few areas of the city.
The 2 April protests followed a gang attack on the central Haitian commune of Mirebalais on 31 March. During the Mirebalais attack, which has been linked to the Viv Ansanm gang coalition, a prison was targeted, and over 500 inmates were released, many of whom were likely immediately recruited by the gangs.
The attack in Mirebalais, approximately 60 kilometres northeast of the capital, may indicate that the gangs are attempting to assert control and expand their territory outside of Port-au-Prince. This strategy would likely provide several benefits for the gangs.
Attacks outside of the capital will almost certainly help to further undermine both the government and the Kenyan-led international task force, which is already reporting increased casualties. Significant attacks outside the capital will likely act as a demonstration of strength for the gangs, bolstering their recruitment efforts.
If sustained, such actions could also pressure the government and international forces to divert resources from the capital, further overstretching their forces to the advantage of the gangs. Most importantly, if the gangs take control and expand their influence in central Haiti, this will likely enable them to assert greater influence in the capital.
The gangs have systematically targeted key elements of Haiti’s infrastructure, including aid distribution points and convoys, hospitals and healthcare facilities, and vital infrastructure such as the international airport, roads, and transport hubs. They have also attacked educational institutions and other critical services. These attacks have likely been conducted to disrupt the delivery of humanitarian aid, increase the population’s dependency on the gangs, and undermine the government’s inability to provide essential services.
Control of central Haiti will likely exacerbate these trends. Mirebalias is on the intersection of Route 305 and National Road 3 (Route Nationale 3), the main supply route that connects the capital to Cap-Haïtien. Gang attacks on Toussaint Louverture International Airport (PAP) and on aircraft have effectively rendered the airport non-operational, and the US Federal Aviation Administration (FAA) has banned flights to the airport until September 2025. This has led to Cap-Haïtien becoming an increasingly critical hub for both humanitarian aid and international support.
The gangs will likely continue to attack and attempt to assert control in central Haiti to cut off Port-au-Prince from humanitarian aid and international relief. As their territorial expansion increases, the humanitarian situation will almost certainly continue to deteriorate, likely further entrenching gang dominance, increasing internal displacement and migration flows, increasing unrest, and increasing the need for a coordinated international intervention.
Colombia: Government announces unilateral end of peace talks with ELN
Colombian President Gustavo Petro has announced the unilateral termination of peace talks with the left-wing guerrilla group, the National Liberation Army (ELN), following sustained fighting, which has primarily affected regions like Arauca and Norte de Santander on the Venezuelan border. President Petro also denounced the ELN as an “occupying army of foreign origin.”
Petro’s comments were reinforced by incumbent Colombian Defence Minister Pedro Sánchez, who condemned the ELN, labelling it as a “purely criminal group” responsible for a wide range of human rights abuses, including the mass displacement of 56,000 people, the forced confinement of 23,000, murder and kidnap.
Recent government operations have neutralised hundreds of ELN fighters, and awards amounting to approximately USD 400,000 have been offered that lead to the arrest of ELN leaders. ELN leaders have responded by declaring Petro’s “total peace” policy a failure and betrayal of the Colombian people. The group also justified the killing of Revolutionary Armed Forces of Colombia (FARC) dissidents, accusing them of collaboration with the government.
Solace Global Assessment:
Recent government statements and operations indicate a complete shift in the Petro administration’s strategy towards the ELN and other guerilla and criminal groups, which will highly likely result in a worsening of the conflict near the border with Venezuela and the humanitarian situation.
However, the effective dismantling of the ELN will likely prove to be a significant challenge. The group maintains a decentralised structure and is well entrenched in the rural and border regions of Colombia. The ELN has traditionally survived the killing or capturing of its leadership by quickly replacing them and operating through a network of decentralised cells.
Petro’s comments that the ELN is an occupying army of foreign origin is almost certainly a reference to how the group has developed ties with Venezuela, with widespread reports that the Maduro administration is directly profiting from the ELN’s illicit activities. These ties will help ELN sustain itself militarily and enable it to establish safe havens outside of Colombia.
Moreover, cross-border operations will complicate Colombian counter-insurgency efforts, limiting its ability to target ELN high-value targets within Venezuela without risking a diplomatic crisis or broader conflict. These challenges likely indicate that the conflict will last for the foreseeable future following the mutual acceptance of the failure of “total peace”.
It is estimated that the ELN operates in at least 231 municipalities across 19 departments in Colombia and in eight of Venezuela’s 24 states. In Colombia, the ELN’s main strongholds are in the departments of Chocó, Norte de Santander, and Arauca. However, the group also has a strategic presence in the departments of Antioquia, Bolívar, Cauca, Valle del Cauca, Nariño, and Vichada, where it engages in illicit activities such as drug trafficking, illegal mining, and extortion to sustain its operations.
The ELN’s widespread territorial control and illicit networks likely make it highly resilient to military pressure. This also puts the group in an advantageous position to escalate violence across the country, and there is a realistic possibility that sustained government operations against the ELN near the Venezuelan border will result in a migration of violence to other parts of Colombia.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
US administration announces “Liberation Day” tariffs
On 2 April, Washington highlighted the Trump administration’s plans to impose sweeping tariffs on its international trade partners. President Trump has held a long-standing belief that a comprehensive tariff regime will bolster the American economy by reducing the impact of “unfair” international trade practices.
The move is likely to drive anti-American sentiment abroad, particularly in the most severely hit states or regions, including the European Union, China, Cambodia, and Vietnam. In Europe, there is a realistic possibility that an increase in the perceived hostility of the US administration will contribute to drive further cases of vandalism of American assets and businesses.
Violent unrest in the Dominican Republic during anti-Haitian protests
On 30 March, an anti-Haitian protest in the Dominican Republic turned violent as the nationalist group Antigua Orden Dominicana (AOD) called for the expulsion of Haitian migrants. Violent unrest resulted in the police using tear gas and water cannons, and several arrests were made.
Protestors claimed that Haitians are responsible for an increase in crime in the country, demanded that mass deportations be conducted, and broke past barricades to enter Haitian communities in Hoyo de Friusa, Bavaro, close to the tourist resort of Punta Cana.
Due to the endemic violence and continued destabilisation in Haiti and its associated migrant flow into the Dominican Republic, future protests and unrest are likely to continue, with the AOD attempting to organise further demonstrations in April.
Security, Armed Conflict and Terror
New Mexico Republican HQ firebombed
On 30 March, the Republican Party state offices were set on fire, and slogans like “ICE=KKK” were spray-painted on the building. The damage to the premises was reportedly contained by responding firefighters, and as the attack occurred overnight, no injuries were reported.
The firebombing is almost certainly in response to the Trump administration’s drive to carry out mass deportation of undocumented migrants in the US. While available data suggests that the actual number of expulsions is similar to that recorded during the Democrat Biden administration, the Trump White House has strongly invested in public messaging on its migration policies, often highlighting and glorifying their most controversial aspects, such as the deportation of alleged gang members to prisons in El Salvador.
The high-visibility of the current administration’s policies is likely to drive further acts of vandalism, and possibly political violence, in the medium term.
Environment, Health and Miscellaneous
Floods result in evacuations in northeast Paraguay
Severe floods have affected the Alto Paraguay region since 1 April, following severe precipitation. The severe weather events have resulted in the evacuation of local towns and major traffic disruptions, and authorities have issued a state of emergency for the area. The Alto Paraguay department is sparsely populated and lacks comprehensive infrastructure, with few key roadways, like the PY16. Consequently, even localised floods can result in smaller towns being effectively cut off from receiving emergency help.
Europe, Middle East & Africa
France: Marine Le Pen found guilty of embezzlement, barred from running for president
On 1 April, a French court sentenced Marine Le Pen, the leader of the far-right National Rally (RN) and favourite in early polls for the 2027 presidential race, to four years in prison (two suspended, two on house arrest) over charges of embezzlement of EU funds. The court, which also sentenced other prominent RN officials, also barred Le Pen from running for office for five years, meaning that the sentence prevents her from partaking in the 2027 vote.
The sentence was met by the opposition of prominent international right-wing figures, including in Italy, Hungary, and the US. Jordan Bardella, RN’s party president, and other leaders called for a peaceful mobilisation in support of Le Pen, including a rally at 15:00 local time in Paris on 6 April.
Le Pen has appealed the verdict, and, on 2 April, court officials stated they plan to hold the appeal trial before the 2027 electoral campaign.
Solace Global Assessment:
The verdict is almost certainly a severe blow to RN. The party’s political appeal has been tied to the Le Pen family for generations, and if Marine Le Pen was unable to run, there is a realistic possibility that it would struggle to gain traction by fielding Bardella or another alternative candidate.
It is highly likely that RN supporters will stage demonstrations following the verdict, particularly on 4-6 April. Counterdemonstrations by anti-RN activists will highly likely take place in response, with a realistic possibility of violent clashes and police intervention.
There is likewise a realistic possibility that the sentencing will embolden radical groups and movements that share some ideological affiliation with RM’s platform to increase recruitment and messaging to RN’s voter base. It may be notable that RN won around 30 per cent of the youth vote at the last elections, matching a shift also seen elsewhere in Europe.
Finally, the judicial closing of a political path for RN to take power is likely to be exploited by extremists to increase calls to violence against public officials and left-wing politicians in France, possibly increasing the risk of lone wolf terrorism.
Ukraine: Russia continues to exploit ceasefire ambiguities to gain leverage in Ukraine conflict
Officials within the Trump administration have acknowledged that securing a peace deal in Ukraine within the next few months is unlikely. The officials stated that while the original intent was to secure a full ceasefire by April-May, both Ukrainian and Russian resistance to key elements proposed by the Trump administration are delaying efforts, leading to increasing frustration within the White House over President Putin’s refusal to compromise on his maximalist demands.
Washington has discussed renewed measures to coerce Moscow into accepting its proposals, which include secondary tariffs of 25-50 per cent on Russian oil buyers.
President Putin has continued to criticise US peace proposals through his chief negotiator Sergei Ryabkov, demanding several core demands that the Kremlin insists must be met to secure any potential ceasefire agreement.
These include Ukrainian recognition of the annexation of Crimea and the four partially occupied regions in southeastern Ukraine of Donetsk, Luhansk, Zaporizhzhia, and Kherson; a Ukrainian pledge to never join NATO or any other Western military alliance; a demilitarisation of Ukraine; the removal of President Volodymyr Zelensky; a suspension of US lethal aid and intelligence; and an easing of European sanctions, which the EU has rejected.
Solace Global Assessment:
By refusing to accept current ceasefire proposals advanced by the US or renege on its maximalist demands, it is highly likely that the Kremlin is delaying the ceasefire proposal in order to seize further Ukrainian territory, which will ultimately improve its bargaining power in future negotiation talks.
Moreover, Russia is unlikely to accept any meaningful ceasefire agreement while Ukraine retains forces in Russia’s Kursk Oblast. Ukraine’s Kursk offensive was a symbolic and operational success that buoyed Ukrainian morale, forced Russia to divert resources from other sectors of the line of contact and most importantly, placed Ukraine in a more advantageous position for future negotiations.
Recent reporting indicates that Russian ground forces are close to reclaiming the entirety of the Kursk Oblast after seizing the city of Sudzha in mid-March, Ukraine’s main defensive position. However, Moscow is unlikely to pursue ceasefire negotiations once it has fully reclaimed Kursk, as it has seized the momentum on multiple fronts.
Once the Kursk Oblast has been recaptured, Russia will likely stabilise its lines on this axis and laterally redeploy forces to parts of eastern Ukraine, in order to further consolidate territorial gains, improve its leverage, and maximise its chances of securing concessions from both Ukraine and the West.
Moscow is highly likely to accept poorly defined steps towards a ceasefire or limited ceasefires in order to project a willingness to pursue overall peace, a strategy that will continue to delay the conflict and may help to placate the Trump administration, which is under pressure to secure a resolution to the conflict.
By agreeing to vague, poorly defined or incomplete ceasefire proposals, Moscow can claim it is acting in good faith while exploiting the lack of clarity to continue military operations or adapt them to appear as if it is complying.
One example of this strategy currently in place is Russia’s interpretation of the moratorium on attacks on Ukraine’s energy-related critical national infrastructure (CNI). Russia has refrained from attacking these targets with long-range missiles and drones in accordance with the vaguely defined terms of the ceasefire. However, it has increased its targeting of energy infrastructure with shorter-range artillery, as it is unclear as to whether this is covered in the yet-to-be formalised ceasefire terms, which may only apply to long-range fires.
One of the objectives of this strategy is likely to provoke Ukraine into retaliatory actions, then exploit the ambiguity of the ceasefire terms to shift blame onto Kyiv for violating the ceasefire. Ultimately, this strategy will help Russia control the narrative, undermine Ukraine’s commitment to ongoing peace negotiations, help extend the conflict whilst Russia maintains the upper hand on the battlefield, and most importantly, help to foster division within the West, one of Russia’s primary strategic objectives.
Israel and Lebanon: IDF strike Hezbollah external attack planner to thwart future attack
On 1 April, the Israel Defense Forces (IDF) conducted an airstrike in the Hezbollah stronghold of the Dahieh area in southern Beirut, targeting Hassan Ali Mahmoud Bdeir. Israeli intelligence claims that Bdier was a senior Hezbollah commander who served in the militant group’s Unit 3900, which is responsible for external operations beyond Lebanon’s borders.
Bdeir was also responsible for the coordination between Hezbollah, Hamas and Iran’s Quds Force. According to Israeli sources, Bdier was planning a major attack on Jewish and Israeli targets overseas and had been monitored for months by the Israel Security Agency (Shin Bet), working in conjunction with Israel’s military intelligence and cyber surveillance units.
Solace Global Assessment:
Israeli defence sources claim that Bdeir was overseeing the recruitment of suicide operatives, logistic chains for weapons and explosives, the funnelling of funds through covert Iranian channels, and was responsible for target selection against Israeli diplomatic missions, Jewish community centres and other potential civilian targets.
If the foiled attack was credible, it may indicate a shift in Hezbollah’s strategy against Israel. Hezbollash has established a network of operatives across the globe and has previously demonstrated its ability to attack Israeli and Jewish interests outside of the Middle East. For example, in 1994, 85 people were killed after a vehicle-borne improved explosive device (VBIED) detonated outside of the Argentine Jewish Mutual Association (AMIA) building in Buenos Aires, an attack that has been linked to Hezbollah with Iranian backing.
There is a realistic possibility that Hezbollah may be seeking to adopt a strategy of external attacks to increase pressure on Israel and the US while achieving a high degree of plausible deniability. Such a strategy would also enable Hezbollah to target Israeli interests without directly engaging Israeli forces, with any Israeli response in Lebanon likely to provoke international condemnation.
However, the strike follows a series of expanded Israeli strikes in Lebanon, which have not been confined to the southern parts of Lebanon. Hezbollah is in a weakened position after Israel’s ground offensive and strikes on the group, and it has lost its critical supply lines from Iran through Syria since the fall of the Assad regime. However, the group still maintains thousands of fighters and a credible arsenal of missiles and rockets.
While Hezbollah likely has some tolerance for attacks on rank-and-file fighters and military equipment, Israeli strikes on senior leadership and within Beirut could force Hezbollah into resuming hostilities if sustained. Any major kinetic response from Hezbollah will likely result in a definitive end to the increasingly fragile ceasefire agreement and would likely lead to increased Israeli strikes in Lebanon and potentially a renewed ground offensive in southern Lebanon.
Given the current geopolitical climate, there is a realistic possibility that Israel may be seeking to capitalise on Hezbollah’s degradation, a weakened Iran, and the support of an increasingly pro-Israel, anti-Iran Trump administration to further its strategic goals.
Israel and Gaza: Israeli forces establish new Gaza corridor, threaten annexation
The Israel Defence Forces (IDF) have continued offensive operations in the Gaza Strip, with the aim of maximising pressure on Hamas and securing the release of the remaining Israeli hostages still in captivity. On 2-3 April, IDF channels issued evacuation orders for much of the southern city of Rafah, while Israel Katz, the minister of defence, stated that IDF operations are aimed at seizing territory for long-term occupation. This echoed Prime Minister Benjamin Netanyahu’s statements on 30 March that Israel is now seeking to implement Trump’s plan for the “voluntary migration” of Gazans from the Gaza Strip.
On 3 April, Netanyahu announced that IDF units have established the Morag Corridor, named after a former Israeli settlement in Gaza, between Rafah and Khan Yunis, calling it a “second Philadelphi”. Over 1,150 Palestinians are estimated to have been killed since hostilities resumed on 18 March.
Solace Global Assessment:
The establishment of the Morag Corridor almost certainly seeks to isolate Rafah from the rest of Gaza. The southern city was considered to be the key stronghold from Hamas forces and benefited from the proximity of the Gaza-Egypt corridor, through which the armed group received most of its equipment and resources.
IDF operations are likely aimed at “strangling” the remaining Hamas units by sectioning Gaza. It is highly likely that IDF units in the Morag area will immediately seek to identify and destroy the remaining tunnels linking Rafah and Khan Yunis, aiming to sever Hamas’ ground lines of communications and forcing it into more direct and costly confrontations.
The establishment of the new corridor, combined with the evacuation orders for Rafah, highly likely shows that the aid blockade will continue, which will in turn almost certainly worsen the humanitarian situation in southern Gaza.
Katz and Netanyahu’s statements are highly likely the clearest indications of a growing interest in the Israeli annexation of parts of the Gaza Strip. The far-right parties that support Netanyahu’s government have long considered the Israeli withdrawal from Gaza in 2005 a historic mistake and are likely interested in returning to some of the previous settlements in the area.
A more tangible set of measures to expel Gazans from the area would almost certainly precipitate tensions in the region, bringing both Tel Aviv and Washington at odds with regional powers like Saudi Arabia and Turkey, who see the removal of Gazans as an unacceptable “red line”.
Moreover, it would almost certainly result in severe civil unrest in Jordan and, especially, Egypt, who would be the likeliest destinations for displaced Gazans.
While likely still the main political force in Gaza, there are notable indications that Hamas has lost much of its administrative capacity and support. In the past month, there have been multiple cases of protests against the war in Gaza, some openly criticising Hamas’ policies in the war.
In addition, on 2 April, members of the Abu Samra clan, based in Deir al-Balah, carried out a public execution of a Hamas member who had allegedly killed one of their relatives. The execution, which was filmed and posted online, is almost certainly an open act of defiance against Hamas, and highly likely reflects a wider belief in Hamas’ relative weakness.
Iran: Tensions with US increase following Trump threats of bombing campaign
On 30 March, US President Donald Trump stated that if Iran does not agree to a deal on their nuclear program, ‘there will be bombing’, ‘the likes of which they have never seen before’. Trump additionally threatened secondary tariffs on countries that trade with Iran, giving an approximate timeline of ‘a couple of weeks’ for progress in nuclear talks until the tariffs would be imposed.
On 31 March, Iran’s Supreme Leader Ali Khamenei responded, stating that he did not believe the threats but that the US would ‘certainly receive a heavy blow in return’. A senior Iranian adviser also stated that US or Israeli strikes would ‘force’ Tehran to develop nuclear weapons, and Iranian media and senior military commanders threatened retaliation against US military facilities across the region (including a direct threat against the US base on Diego Garcia Island south of the Maldives) and the closure of the Strait of Hormuz.
Furthermore, on 3 April, the Telegraph reported that a senior Iranian official source briefed that Tehran had ordered a withdrawal of military personnel from Yemen, as part of a reorientation away from a strategy of supporting its network of regional proxies, the “axis of resistance”, to focus instead on direct threats from the US.
Solace Global Assessment:
The increase in rhetoric comes amidst a return to Trump’s “maximum pressure” approach to Iran, with Trump’s threats following Tehran formally responding to a 5 March letter Trump sent to Khamenei. In the letter, Trump set a two-month deadline to reach a nuclear deal, although it is unclear whether this countdown begins from the letter’s delivery or when negotiations hypothetically begin. Tehran’s rejection of Trump’s demands for direct negotiations, instead proposing indirect talks mediated by Oman, highly likely conditioned Trump’s direct threats of military force.
Iran has been classified as a “nuclear threshold state”, with estimates suggesting that it could take less than a week for Iran to enrich enough weapons-grade uranium to produce a nuclear weapon. Following the severe degradation of Lebanon’s Hezbollah and the October 2024 aerial strikes by Israel that highly likely heavily degraded Iran’s air defence network, Iranian deterrence in the region has almost certainly been significantly diminished.
Tehran, therefore, is highly likely to have far more incentive to develop a nuclear deterrent. There is likely considerable internal debate within the Iranian establishment, with a clear split between President Masoud Pezeshkian, who was elected on a mandate of reopening nuclear negotiations to enable the removal of sanctions that have crippled Iran’s economy, and hardliners who reject the possibility of any concessions to Washington.
Whilst the briefed withdrawal from Houthi-controlled Yemen may indicate a substantial shift in Tehran’s strategy, it is unlikely that they will fully abandon the Houthis, as the Yemeni group remains one of Iran’s most powerful and strategically positioned proxy forces.
Considerable escalation to open conflict between Iran and the US (with almost certain Israeli support), would highly likely increase the threat to US-aligned states across the region, notably Gulf states such as the United Arab Emirates (UAE), Kuwait, and Saudi Arabia, with Iranian-backed proxy forces having previously threatened attacks against US energy interests during periods of increased tensions.
It is likely that Tehran, due to Iran’s assessed highly vulnerable position, will pursue a cautious approach and is likely particularly susceptible currently to Trump’s coercive rhetoric. Nonetheless, Khamenei will likely be highly reluctant to overtly concede to US pressure and military escalation by Washington would likely force retaliation by Tehran.
Democratic Republic of the Congo (DRC): New rebel group created in the Ituri province
On 31 March, Ituri native Thomas Lubanga announced the creation of the Convention for the Popular Revolution (CPR), which aims to topple the government in the Ituri province. Lubanga, currently based in Uganda, claims that the group has political and military wings, with armed forces present in three areas of Ituri.
Lubanga was sentenced to 14 years in prison by the International Criminal Court (ICC) in 2012 for ‘enlisting and conscripting children under the age of 15 years and using them to participate actively in hostilities.’ Congolese President Felix Tshisekedi appointed him after his release in 2020 as part of a task force to restore peace in Ituri. However, after being taken hostage for two months by a rebel group in 2022, he blamed the government, severing ties with Tshisekedi.
Solace Global Assessment:
The CPR is the second rebel movement led by Lubanga, following the Union of Congolese Patriots (UPC), a rebel group involved in the Ituri conflict. While the conflict mainly occurred between 1999 and 2003 following the Second Congo War, it has continued at a lower intensity between the agriculturalist Lendu and pastoralist Hema ethnic groups.
The UPC, under the command of Lubanga, primarily supported the Hema ethnic group, and will almost certainly continue to do so under the new banner of CPR. Given that rebels under Lubanga’s command have previously been accused of human rights violations including ethnic massacres, murder, torture, rape, mutilation, and the forcible conscription of child soldiers, it is highly likely that CPR will engage in similar tactics, exacerbating humanitarian issues in the region, which has seen over 50,000 killed and 500,000 displaced. It is likely that aid workers will not be targeted, with Lubanga previously pledging security for humanitarian workers.
The UPC operated with the support of Ugandan forces, who are currently active in the Ituri region under Operation Shujaa, a joint offensive against insurgent forces in the Ituri province. In August 2002, the UPC captured Bunia with the assistance of the Ugandan military and subsequently began to receive support from Rwanda.
Uganda currently has a military presence in Bunia due to counterinsurgency efforts against the Islamic State-affiliated Allied Democratic Forces (ADF). Uganda also has an active interest in exploiting the abundant mineral resources in eastern DRC; in 2019, 95 per cent of its gold exports were highly likely sourced from the DRC.
There is a realistic possibility that Uganda will renew its ties with Lubanga, which would highly likely expand Ugandan access to mineral wealth attained by the rebel group, likely in exchange for military support from the Uganda People’s Defence Force (UPDF). Forming an alliance with CPR would also likely expand Ugandan influence in the region, counterbalancing Rwanda’s expanding influence in Kivu through AFC/M23.
The formation of the CPR will highly likely further stretch the Armed Forces of the Democratic Republic of Congo (FARDC), who are currently attempting to prevent an ongoing offensive by the AFC/M23 militia. This will likely also indirectly increase pressure on Congolese President Felix Tshisekedi, who is currently facing significant opposition regarding his perceived handling of the conflicts in eastern DRC.
Lubanga has an indirect link to the AFC/M23 through Bosco Ntaganda, founding member of M23 and former Chief of Military Operations in the UPC. The UN accused Lubanga last year of mobilising fighters to support AFC/M23. AFC/M23 are currently approaching the Ituri province in an ongoing offensive in North Kivu; currently in Lubero, they almost certainly aim to continue north into Ituri. The formation of CPR will highly likely facilitate this northern expansion.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Workers at London Heathrow Airport (LHR) to strike from 5 to 9 April
The strikes have been announced by Unite the Union and will be conducted by approximately 500 Heathrow workers who assist passengers with limited mobility. The dispute stems from the wage difference between staff performing the same role at London Gatwick Airport (LGR), despite being employed by the same company, Wilson James.
Further strike dates will reportedly be announced if an agreement is not reached. Travel disruptions are likely over the Easter period, potentially disrupting holiday flights. The strike announcement comes amid increasing pressure from airlines over the temporary airport closure due to a power outage caused by a substation fire nearby, which affected approximately 200,000 passengers.
There is a realistic possibility that airline pressure, combined with threats of further strike action, will mean that the workers succeed in attaining a pay increase and call off strike action.
More than 250 migrants displaced for the second time in weeks in Paris
On 1 April, French police removed a migrant encampment in central Paris on the Seine quays. Many of the displaced individuals had reportedly previously occupied the Gaite Lyrique theatre, also in central Paris, which had been raided by authorities on 18 March following months of occupation. There is a realistic possibility of civil unrest by left-wing groups following the second displacement in two weeks.
General strike grounds flights in Belgium
On 31 March, a general strike among both public and private sector workers took place in Belgium in protest of planned government austerity measures. The strikes severely disrupted public services and transport, grounding 244 flights across the country. The national railway operated a minimal service of fewer than half its trains running and several schools and public services have stopped. Eurostar was unaffected.
This is the second such nationwide strike and reflects a growing discontent with the newly formed “Arizona coalition”. In February, tens of thousands of people engaged in a multi-day strike in protest against pension reforms. The government’s measures are set to cut funding for pensions, healthcare, unemployment support, and social services. Given the widespread hostility of the country’s unions towards these measures, further strikes and demonstrations are highly likely.
Germany tries to deport four pro-Palestine activists
Three of the four individuals reportedly hold EU citizenship, and the fourth is American. None have been convicted or charged for a criminal offence, although this is not technically needed for the issuing of a deportation order under German law. The four are, however, accused of taking part in direct protest action in support of Palestine, including university and roadway blockades. The timing of the case will likely result in its association with similar efforts to deport pro-Palestine activists from the United States. It is highly likely that, if the planned deportations progress, these will result in anti-government protests in Berlin, particularly at local universities.
Alternative for Germany (AfD) dissolves youth wing
The termination of the “Young Alternative”, which had been classified as an extremist group in 2023, is likely meant to reduce the risk of legal challenges to the party, which is now the second strongest force in the German parliament. AfD has, at the latest elections, made some important gains in terms of the youth vote, so the party would be positioned to benefit from having a youth wing to capitalise on its new supporters. Likely, AfD will now launch a new formation to replace the Young Alternative. However, in the interval, there is a realistic possibility that other far-right youth groups who are not aligned with the party, such as the resurgent German chapter of Generation Identity (GI) will seek to recruit AfD supporters into their ranks.
Slovakia proposes draft of “anti-lobbyists” bill targeting NGOs
The law, which is supported by the Fico government, classifies NGOs that “directly or indirectly” influence politicians as “lobbies”, thus imposing more significant restrictions on their operations. As the definition of “influence” is vague, critics of the bill argue that it is effectively an attempt to curtail NGO operations in a manner similar to that seen in Russia or Georgia. Protests have occurred in Bratislava and other large cities in the aftermath of the law’s proposal. These protests are likely to continue next week, when the draft law is set to have its final vote.
Protests in Hungary over Pride ban
Large-scale demonstrations, resulting in widespread traffic disruptions, have erupted in Budapest following the Orban government’s new legislation, which bans Pride parades and authorises police to use facial recognition software to identify participants. The law is scheduled to come into effect in mid-April, in time for Pride month in June. Notably, 2025 is also the 30th anniversary of the first Pride parade in Budapest. The unrest is likely to continue on 4-6 April, and there is a realistic possibility of its increase in the short term. If the ban remains in place, a further wave of unrest is highly likely to occur in June.
National strike planned in Greece for 9 April
Several public sector unions in Greece have announced that they will participate in a 24-hour general strike beginning on 9 April. The strike is expected to cause widespread disruption, especially within the transport sector. All flights in Greece will be cancelled due to the participation of air traffic controllers in the strike, severely affecting domestic and international travel. Maritime industry unions have also announced their intent to participate, which will halt all shipping in the country, which may impact the country’s supply chains, tourism, and commerce. There is a realistic possibility of strike-related protests in major cities like Athens and Thessaloniki resulting in violent interactions with the police force.
UK sanctions pro-Russian group over Moldovan election interference
On 2 April, the UK government imposed sanctions on the pro-Russian group Evrazia, linked to Russian oligarch Ilan Shor, for attempting to rig Moldova’s October 2024 presidential election and its referendum on joining the European Union. The sanctions, which include asset freezes and travel bans on the group’s leaders, are likely part of a broader UK effort to counter Russian influence, combat corruption and safeguard democratic institutions in Europe, and will likely expand in response to Russian efforts to influence upcoming European elections, such as the Romanian presidential election in May.
Guinea’s junta sets September as a date for constitutional referendum
On 2 April Guinea’s military junta announced 21 September 2025 as the date for a constitutional referendum. This marks a significant step in the transition towards democracy after Mamady Doumbouya took power in a coup in September 2021. The military has so far missed the deadlines it set for a transition to civilian rule, having initially proposed a two-year transition period, which lapsed after 31 December 2024. The junta has engaged in significant political repression since gaining power, allegedly disappearing two prominent opposition figures in July 2024 and a journalist in December. The proposed constitution would introduce a two five-year term presidential limit but may enable Doumbouya to run for office, something forbidden in the transitional charter. It is highly likely that the constitution is engineered to enable Doumbouya to attain power legitimately.
Burkina Faso accelerates media crackdown
On 1 April, the security minister of Burkina Faso released a list of individuals who are wanted for “criminal association” and “terrorism”. Many of the figures listed are the heads or high-ranking members of Islamist terror groups operating in the country. However, alongside them, the junta listed prominent journalists and civil society opposition figures, many of whom are currently in exile. The crackdown on media figures has likely intensified following the reported massacre of civilians by Burkinabe forces in Solenzo on 11 March, and the publication of the lists likely represents an effort to systematise the efforts to silence opposition voices. In addition to this recent development, there is a high likelihood that Burkinabe security forces have been deployed to “disappear” critics still present in the country. For instance, local sources have reported that, on 30 March, security forces arbitrarily arrested the head of a civil society group based in Ouagadougou. No reports about the detainee’s location or state have been released since the arrest.
Approximately 95 arrested in demonstrations against Zimbabwe President Emmerson Mnangagwa
On 31 March, a muted planned protest demanding Mnangagwa’s resignation took place amid heavy security presence. Few people participated in the protests, likely due to fears of potential violent unrest, opting to stay home. The fear led to widespread closures of businesses, offices, and schools in Harare and Bulawayo. Security forces used tear gas to disperse protesters, and the demonstrators, identified through social media posts, were arrested on charges of “promoting public violence” and “breaching the peace”. The demonstrations were organised by Blessed Geza, a member of the ruling Zanu-PF party and part of a faction calling for Vice-President Constantine Chiwenga to replace Mnangagwa.
Zimbabweans have been calling for Mnangagwa’s resignation since a Zanu-PF announcement in January, which declared that he would be in office until 2030, despite the constitutional limit of two five-year terms, which would limit his rule to 2028. The calls for protests come amid hyperinflation, high unemployment, and widespread corruption, despite Mnangagwa’s early promises of political and economic reforms. While the population is generally wary of destabilising an already fragile country, it is highly likely that calls for Mnangagwa’s resignation will increase over the coming weeks and embolden currently wary opponents, potentially sparking widespread nationwide unrest.
Security, Armed Conflict and Terror
Man sets vehicle on fire in central Amsterdam, Netherlands, in possible failed car bomb attack
On 2 April, a man drove a vehicle to the centre of Dam Square and reportedly attempted to detonate it. This resulted in a fire that injured the driver but caused no casualties. As of the time of writing, the identity and motive of the individual remain unclear. However, there is a realistic possibility that the incident is linked to the recent lone wolf stabbing attack that occurred at the same location.
From the episode’s dynamic, it appears highly likely that the driver sought to achieve maximum visibility for his action, but it is still unclear whether the detonation was a failed terror attack attempt or whether it was carried out as a form of high-visibility suicide. Over the past year, there have been several cases of self-immolation carried out for political messaging. These included a man detonating a Tesla vehicle outside the Las Vegas Trump Hotel in January 2025, in an apparent protest of the incoming Trump administration.
Multiple Teslas torched in Rome
On 31 March, 17 vehicles manufactured by US billionaire Elon Musk’s company were burned at a dealership in the periphery of the Italian capital. The act of vandalism is highly likely the most severe incident targeting Tesla in Italy so far, and is highly likely linked to the string of attacks on the US automakers that have occurred in Europe in the last months. Tesla is a preferred target for anarchist groups, who retain a heavy presence in Italy, due to its high visibility and its association with the Trump administration.
In addition to Tesla, the is a realistic possibility that as US tensions with Europe increase, other high-visibility American companies could be targeted for vandalism. Moreover, the targeting of US assets in Italy could increase following the possible announcement of a visit by US Vice-President JD Vance to Rome for Easter, which appears likely to be announced following repeated contacts between the Italian government and the American embassy in Rome.
Israel intensifies strikes on Syria
On 2 April, the Israel Defense Forces (IDF) escalated its strikes in Syria, targeting air bases and military infrastructure near Damascus and in several other parts of the country, resulting in the near-total destruction of Hama Air Base and the Tiyas (T4) Air Base near Homs. The strikes also coincided with an IDF ground operation in southwestern Syria, where IDF forces clashed with militants.
The strikes were likely intended to send a strategic message to Syria’s new Islamist-led transitional government that Israel will not accept hostile forces establishing a presence on its borders. Israel also raised concerns over Turkey’s increasing influence in Syria, with Foreign Minister Gideon Saar accusing Ankara of attempting to turn Syria into a “Turkish protectorate.” Turkey has made attempts to secure the T4 Air Base, with reports circulating that it will deploy air defence to secure the base. Israel’s repeated targeting of T4 in recent weeks likely suggests a deliberate effort to degrade its operational capacity before Turkish forces can establish a presence.
Armed attack kills several dozen soldiers in Burkina Faso
On 31 March, “several dozen” soldiers and Volunteers for the Defense of the Homeland (VDP) members were killed by suspected jihadists in a military camp in Diapaga, eastern Burkina Faso close to the borders with Niger and Benin. Approximately 30 wounded security personnel were evacuated to a hospital. During the attack, militants set fire to shops and homes. The military retaliated, launching a sweep of the area and killing several militants.
Burkinabe authorities have not released a statement regarding the attack. Burkina Faso’s security forces have been battling insurgencies, primarily by the al-Qaeda linked Jama’at Nusrat ul-Islam wa al-Muslimin (JNIM) and Islamic State Sahel Province (ISSP). Based on the respective operating and attack zones, it is likely that the attack was conducted by JNIM, who typically operate along the border regions with Niger and Benin.
Environment, Health and Miscellaneous
Volcanic eruption in Iceland
On 1 April, a volcanic fissure opened north of Grindavik, causing the evacuation of the town and nearby Blue Lagoon. The fissure initially reached 500 metres; by midday, it had grown to 1,200 metres, moving southward toward Grindavik. Despite the dramatic initial activity, Icelandic authorities have recently observed a decrease in volcanic activity. On 2 April, local media reported no significant activity at the fissure site. An Icelandic meteorological official stated that the eruption is ‘more or less over,’ although they cautioned that future magma intrusions could occur. In the meantime, approximately six hundred earthquakes have been recorded in the magma chamber since April 3, but no new volcanic activity has been observed since the fissure opened.
Storm Nuria hits Iberian Peninsula
Storm Nuria continues to affect the Iberian Peninsula with heavy rain and winds, although no orange or red alerts have been issued in Spain as of the time of writing. In the Canary Islands, classes have resumed following the end of the wind alert. Previously, La Palma Airport remained closed, and flights at Tenerife North Airport were cancelled due to the storm. The storm had also caused landslides and road closures in Las Palmas, and injured individuals in Puerto de la Cruz. Additionally, a power outage affected 3,000 people in Fuencaliente, La Palma. The Spanish meteorology office had activated a yellow alert for Cádiz province due to forecasts of wind, rain, and storm surges.
Greek islands declare emergency due to flooding
Both Mykonos and Paros, two of the most visited islands in the Aegean Sea, announced a state of emergency following the storm that hit the Cyclades on 31 March. The weather system caused widespread flooding and severe traffic disruptions across the islands, with two months’ worth of rain falling on Paros in two hours on 31 March. The state of emergency will be in place for one month.
Nigeria warns of rising nationwide Lassa fever cases
According to the Nigerian Centre for Disease Control (NCDC), at least 118 people have been killed in Nigeria in the first quarter of 2025 due to an outbreak of Lassa fever, with 645 confirmed cases recorded and a current fatality rate of 18.3 per cent. The disease, which is spread primarily by rodents, is most prevalent in rural areas due to poor sanitation, resulting in the contamination of food and living spaces. The outbreak has likely been exacerbated by inadequate healthcare facilities and staffing shortages in rural areas, as well as the overreliance on traditional medication. Symptoms of Lassa fever appear 6 to 21 days after exposure and typically include fever, weakness, headache, muscle pain, sore throat, chest pain, abdominal pain, nausea, vomiting, and diarrhoea, with severe cases potentially leading to internal bleeding, facial swelling, low blood pressure, shock, and organ failure.
Asia–Pacific
Japan: Revised estimates from anticipated megaquake published by Cabinet Office
Japan’s Cabinet Office released a report on 31 March regarding the potential impact of a Nankai Trough “megaquake”, which typically refers to an earthquake of magnitude 8.0 and above, and the subsequent tsunami caused by such an earthquake. The megaquake is estimated to have an 80 per cent chance of occurring within the next 30 years, with the new estimates projecting potentially severe devastation.
In modelled worst-case scenarios, there could be approximately 300,000 fatalities, over 1.2 million evacuees, 2.35 million structures destroyed, and USD 1.81 trillion in economic losses, which is almost half of the country’s total gross domestic product (GDP). The worst-case scenarios involve a magnitude 9.0 and above earthquake occurring late at night in winter.
Solace Global Assessment:
The Nankai Trough, situated south of Japan, contains the prominent Nankai megathrust fault. Megathrust earthquakes, such as the 2011 Tōhoku earthquake (magnitude 9.1), which resulted in the Fukushima nuclear disaster, are the planet’s most powerful earthquakes. The most at-risk areas from a Nankai Trough megaquake are on Japan’s southern Pacific coast, particularly the prefectures of Miyazaki, Kochi, Tokushima, Wakayama, Mie, Aichi, and Shizuoka.
In August 2024, authorities issued a rare megaquake warning due to an assessment that the probability of a Nankai Trough megaquake was several times higher than usual following a magnitude 7.1 earthquake off the coast of Kyushu. Authorities then urged residents on Japan’s Pacific coast to reaffirm their preparedness and take precautions over the following week.
With Japan being so seismically active, the country has world-leading earthquake resiliency. The use of advanced earthquake-resistant technologies, infrastructure resilience, stringent building codes, and thorough disaster response plans all contribute towards making Japan highly resistant to the impact of earthquakes. However, extremely powerful earthquakes such as the 2011 earthquake are still capable of causing widespread damage and large numbers of fatalities.
A Nankai Trough megaquake would likely push Japan’s earthquake resilience to its absolute limits, and the latest projected figures will almost certainly reaffirm the need for companies and employees in at-risk areas to review business continuity plans, risk assessments, and crisis communications protocols and conduct drills.
Taiwan: China stages large-scale, multi-domain military drills around Taiwan
On 1 and 2 April, the Chinese People’s Liberation Army (PLA) Eastern Theatre Command conducted two days of large-scale military drills around Taiwan, including live-fire exercises. A PLA spokesperson stated that the drills were held as a ‘severe warning and forceful containment against Taiwan independence’, aimed at ‘testing the troops’ capabilities to carry out integrated operations, seizure of operational control and multi-directional precision strikes.
Named ‘Strait Thunder-2025A’, the exercises involved personnel from the PLA, the PLA Air Force (PLAAF), the PLA Navy (PLAN), the PLA Rocket Force (PLARF), and the China Coast Guard (CCG). Taiwan’s Ministry of National Defence (MND) stated that on 1 April, 76 PLA aircraft, 15 PLAN vessels and 4 “official ships” were detected operating around Taiwan, with 37 sorties crossing the median line and entering Taiwan’s Air Defence Identification Zone (ADIZ). On 2 April, they detected 53 PLA aircraft, 23 PLAN vessels and 8 official ships, with 31 sorties crossing the median line. The PLAN vessels detected included a CNS Shandong aircraft carrier group.
Additionally, the PLA conducted live-fire exercises, which included rocket strikes targeting a static object which resembles the Yongan Liquefied Natural Gas (LNG) Terminal in Kaohsiung, Taiwan. In propaganda released by the PLA to publicise the exercises, Taiwan’s staunchly pro-independence president, Lai Ching-te, was depicted as a parasite and labelled a separatist.
Solace Global Assessment:
While incursions into Taiwan’s ADIZ by PLA forces are an almost daily occurrence, the Strait Thunder-2025A exercises are particularly large-scale and almost certainly demonstrate the coordination of multiple different branches of China’s military to conduct multi-domain operations. In May and October 2024, the Joint Sword-2024 exercises were similar in scale but did not involve live-fire exercises.
The Strait Thunder exercises were more coordinated than usual and were almost certainly designed to enhance interoperability between different military branches for joint operations. They also likely aimed to integrate operations across multiple domains, including unconventional elements like information warfare, as evidenced by the simultaneous PLA propaganda campaign.
The exercises were highly likely a rehearsal for a blockade of Taiwan, which is assessed to be more likely in the coming years than a full-scale amphibious invasion as a means to compel the unification of Taiwan with mainland China.
The scale, frequency, coordination and use of live fire in Chinese exercises are likely part of a deliberate effort to normalise large-scale military activity in the region. This will almost certainly make it more challenging to identify clear indicators and warnings of a genuine military operation. Such a strategy will likely complicate decision-making and delay response times for Taiwan and its allies, allowing China to achieve strategic surprise.
A full-scale amphibious invasion of Taiwan, however, would highly likely require an operation that would dwarf WWII’s Normandy landings in scale and complexity, with a highly observable military and logistical build-up. A blockade may nonetheless be accompanied by more limited operations to seize the Taiwan-controlled Kinmen islands that are just three kilometres away from mainland China, which could be achieved with far fewer observable indicators and warnings.
Any significant escalation by Beijing is likely to cause a considerable pan-regional impact, in addition to a global economic crisis, with the head of the Philippines’ military stating on 1 April that the country would ‘inevitably’ be involved.
In US defence circles, the “Davison window” refers to Admiral Phil Davison’s comments to the US Congress that China could be capable of pursuing the seizure of Taiwan by 2027, with US intelligence reportedly believing that China’s leader Xi Jinping has given the PLA a 2027 deadline to reach capability for a full-scale invasion.
Some analysts assess that as the US nears semiconductor sovereignty, likely around 2030, Taiwan will lose strategic importance (due to its monopoly on advanced semiconductor manufacturing) and, therefore, Beijing will be less incentivised to take the risks involved to invade or blockade Taiwan. Alternatively, it is likely that US semiconductor sovereignty would dramatically lower the incentives for Washington to provide defence guarantees for Taiwan and would, therefore, increase the likelihood of Chinese military aggression. PLA exercises around Taiwan are almost certain to continue, with large-scale drills likely to be prompted by international and political developments, as well as important dates such as anniversaries of President Lai’s inauguration on 20 May or Taiwan’s National Day on 10 October.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Indian land management bill likely to cause civil unrest
On 3 April, the Indian parliament passed a bill, presented by the ruling Bharatiya Janata Party (BJP) one day prior, which entails significant changes to the administration of “waqf” lands. The term refers to land which is donated by Muslims for religious and charitable uses by other Muslims. These lands are usually administered by all-Muslim funds or boards.
The law would allow non-Muslims to enter these and would increase the government’s authority to resolve disputes involving waqf lands. Opponents of the law have accused the BJP of encroaching on Muslim minority rights. It is likely that, as it begins to be implemented, the bill will drive significant unrest. Past disputes over land have caused notable cases of sectarian violence, including mob violence involving Muslim and Hindu communities.
Bangladesh Nationalist Party (BNP) sabre-rattling showcases interim government’s fragility
The leaders of the (former) main opposition party in the country have warned that if the interim government fails to hold elections in 2025, this will result in “instability” and “strong resentment with the people”. Muhammed Yunus, who heads the government following the ousting of Prime Minister Sheikh Hasina in August 2024, has maintained that, due to ongoing instability, the vote could instead be held in early 2026.
The BNP’s remarks likely amount to a thinly veiled threat: following Hasina’s removal, the political vacuum left by her party – the Awami League (AL) – has resulted in violent competition between smaller groups and opposition parties, with mob violence now a regular occurrence. With AL still reeling from its loss of power, BNP is now the strongest political force in Bangladesh and therefore seeks to capitalise on an early vote. There is a realistic possibility of the BNP increasingly adopting a more aggressive messaging in the medium term, driving unrest or political violence.
Thai court issues arrest warrant for US academic
A Thai court has issued an arrest warrant for American academic Paul Chambers, a lecturer at Naresuan University, on charges of insulting the monarchy and violating the Computer Crimes Act. The charges were filed by the Thai military and relate to an article Chambers posted online last year, although the specific details have not been disclosed. The charges fall under Thailand’s stringent “lese majeste” laws, which are often used arbitrarily to repress the opposition or supress dissent. The laws are some of the harshest anti-monarchy laws in the world and can carry prison sentences of up to 15 years. Since the 2020 pro-democracy protests, almost 300 individuals have been charged under the law, reflecting its increasing application against critics.
South Korean Constitutional Court ruling
South Korean President Yoon Suk-yeol was removed from office on 4 April after the Constitutional Court upheld his impeachment over his December 2024 martial law declaration. The court ruled unanimously that Yoon violated his constitutional powers, with Acting Chief Justice Moon Hyung-bae condemning his actions as a “serious challenge to democracy” that resulted in both domestic and foreign instability.
The trial has been incredibly divisive, leading to protests both in support of and against the former president. Protests in reaction to the verdict are likely; however, they have so far remained localised and non-violent, leading to minimal disruption despite increased security measures. A snap presidential election must now be held within 60 days, likely leading to a period of political uncertainty.
The deepening divide between Yoon’s supporters and opponents, coupled with the urgent need to restore stability, will likely complicate governance in the short term and impact South Korea’s economic and foreign policy decisions, especially as it attempts to adapt to the 25 per cent tariff rates imposed on them by the Trump administration.
Security, Armed Conflict and Terror
Afghan anti-Taliban group releases overview of Islamic State Khorasan Province (ISKP) structure.
The National Mobilization Front (NMF) is a small anti-Taliban group that has claimed multiple attacks on Taliban officials and, notably, Chinese citizens in Afghanistan. On 3 April, NMF channels released information allegedly detailing major efforts by ISKP to restructure some key departments and purge the group from alleged “spies” or “moles”.
While it is currently difficult to assess the credibility of the claims made by NMF – which styles itself as a pro-Western and secular force opposed to both the Taliban and ISKP – the hypothesis of an internal reshuffle could provide an explanation for the recent lull in ISKP operations in Afghanistan and abroad.
Myanmar junta declares a ceasefire until 22 April
On 2 April, Myanmar’s ruling military junta declared a temporary ceasefire to enable relief efforts following the 28 March 7.7 magnitude earthquake, which killed at least 3,000. The decision followed unilateral ceasefires from rebel groups, including the People’s Defence Force and the Three Brotherhood Alliance, which are engaged in a civil war with the government.
While the ceasefire may provide an opportunity for further peace-making, it is unlikely to hold until 22 April. Despite the declaration, there were already reports of ceasefire violations on 3 April, with rebels accusing junta forces of conducting airstrikes in Bhamo and continuing attacks on Waingmaw and Indawgyi. Further reports list strikes in multiple villages of Homalin township on the same day and shootings in Shwegyin and Mone townships on 3 and 4 April.
For the ceasefire to contribute to broader peace efforts, it would likely require long-term measures, including safe zones and humanitarian corridors for aid, on top of a complete cessation of hostilities, something the military junta appears unwilling to accept.
Environment, Health and Miscellaneous
7.1 magnitude earthquake off the coast of Tonga
A magnitude 7.1 earthquake was recorded off the east coast of Tonga in the South Pacific on 30 March, triggering a tsunami warning for the region. The US Geological Survey initially reported a preliminary magnitude of 7.3 before downgrading it to 7.1. Tsunami waves between 0.3 to 1 metre above tide level were considered possible on the coasts of Niue and Tonga.
As a precaution, Tonga authorities activated tsunami sirens and advised coastal residents to move inland. However, the tsunami warning was lifted, and there are no immediate reports of injuries or damage in Tonga. There were also no tsunami threats to Japan, Chile, Guam, or Hawaii. No damage was caused by the earthquake. Several aftershocks have taken place and more are highly likely over the coming days and weeks.
Gas pipeline fire in Malaysia
A large fire broke out on 1 April at a gas pipeline in the Kampung Tengah Puchong area, south of Kuala Lumpur, Malaysia. Authorities have reported that 145 people were injured, though all are in stable condition. The fire, which started at a pipeline owned by Petronas, significantly diminished as gas pressure decreased. The possibility of a second explosion is considered very low, as no gas leaks have been detected after the closure of pipeline valves. An investigation involving up to 20 agencies is set to take place to determine the cause of the fire.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence

Disruptions Expected During March 29 Demonstrations in Chile
Intelligence cut off: 10:00 GMT 28 March 2025
On 29 March, Chile will observe the “Day of the Young Combatant” (Día del joven combatiente). The day commemorates the killing of the two Vergara Toledo brothers in Santiago in 1985 during the dictatorship of Augusto Pinochet. The two brothers were allegedly part of the Revolutionary Left Movement (MIR), a radical left-wing group that was at the forefront of the struggle against the dictatorship. The commemoration also extends to the other activists who were killed or imprisoned during the dictatorship. The anniversary has continued to be politically relevant, reflecting broader anti-government and anti-police sentiment.
There have been multiple notable instances of violence and vandalism during past anniversaries. In 2008, a series of bomb threats were sent to government offices and private businesses, including banks and media channels. In 2015, a police officer (Carabiniere) was shot and killed while carrying out an operation in La Victoria, Santiago. Even in years where similar incidents have not occurred, there are often reports of rioting and street violence, particularly at night after official commemoration events end. Activists frequently target businesses with improvised explosives and other weapons, as well as attacking police forces.
Due to its association with violent episodes and radical left-wing groups, the commemoration is politically controversial. Elements of the Chilean right have criticised the anniversary, with some publications calling it “Day of the Young Delinquent”.
Open-source intelligence (OSINT) investigations indicate that several protests are planned to occur in downtown Santiago on 29 March. A rally is scheduled for the Estacion Central area of Santiago starting at 15:30 local time. The area of Villa Francia in Estacion Central is a major focal point for protests, as it is the area where the two Vergara Toledo brothers were killed.
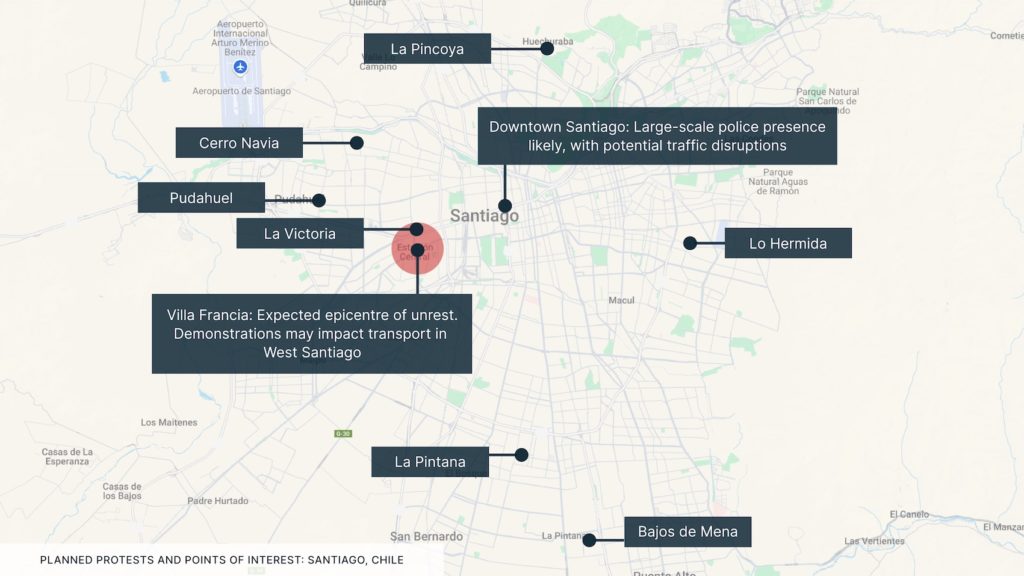
INTELLIGENCE ANALYSIS
High Likelihood of Violent Unrest During Day of the Young Combatant
There is a high likelihood of demonstrations coinciding with the commemorations. Unrest is likely to start in the late morning of 29 March and continue throughout the day, highly likely intensifying in the evening when organised rallies and protests conclude.
Santiago will almost certainly be the epicentre for protests and the city most impacted by traffic disruptions. The primary hotspot of unrest will almost certainly be Villa Francia in Estacion Central, where the 1985 killings occurred. Additionally, areas that will likely be affected include La Pincoya in Huechuraba, La Victoria in Pedro Aguirre Cerda, Lo Hermida in Penalolen, Bajos de Mena in Puente Alto, Pudahuel, La Pintana, and Cerro Navia.
Outside Santiago, unrest is possible in central districts of Valparaiso, Conception, Telmuco, and other Chilean cities. There is a realistic possibility that protests will be driven by other grievances disconnected from the commemoration. For instance, there are ongoing protests in Valparaiso over a controversial fishing sector law; local left-wing groups may seek to stage joint unrest during the Day of the Young Combatant to capitalise on visibility.
While protests during the morning and early afternoon will likely be peaceful, clashes with security forces are possible. Later in the day, particularly at night, the likelihood of violent unrest will increase considerably.
Past demonstrations during the Day of the Young Combatants have consisted of protesters erecting makeshift barriers, burning tyres, vandalising private businesses (particularly banks and the offices of foreign companies), firing projectiles including fireworks, and throwing Molotov cocktails at the police and other targets.
Some demonstrators will likely be armed and are likely to seek direct confrontation with police forces. Chilean police will almost certainly deploy violent crowd control measures in response to the unrest, including tear gas, pepper spray, water cannons, and possibly rubber bullets. Past demonstrations have resulted in dozens of arrests.
While protesters are unlikely to intentionally target bystanders, the nature of the unrest will likely increase the potential for incidental harm.
Travel Risk Advice: Safety Guidelines for Chile
- Avoid Estacion Central throughout 29 March.
- Closely monitor local news reports and government alerts.
- Monitor official public transport channels for updates on disruptions to mobility in Santiago and other affected cities.
- Plan for alternative routes and means of transport in Santiago and other large cities. Allocate more time for all transport.
- If caught in a protest area, try to leave quickly if it is safe to do so.
- If you are in a crowd and unable to leave, take precautions to minimise the risk of crowd crush. These include staying upright, moving away from all hard barriers, going with and not against the crowd, and holding your arms at chest level in a boxer-like stance to relieve pressure.
- Minimise all travel on foot.
- Avoid travelling after dark due to a greater risk of violence.
- Ensure that you always carry personal identification documents or copies.
- Have emergency contact numbers saved on your phone. These should include the local authorities, medical facilities, and any consular support.
- Ensure that mobile phones are charged.
- Monitor the Solace Secure platform and trusted local media.
Subscribe to free weekly intelligence

Executive Summary
Americas (AMER)
The Day of the Young Combatant, 29 March, is highly likely to be marked by protests and clashes in Santiago, and there is a realistic possibility of unrest in other Chilean urban centres.
The Brazilian Supreme Court’s decision to try former President Jair Bolsonaro for his alleged involvement in a coup will likely deepen political divisions and may result in large-scale demonstrations.
Europe, Middle East & Africa (EMEA)
Limited Black Sea ceasefire proposal highly likely to be leveraged by Russia to gain concessions while continuing to pursue its maximalist objectives against Ukraine on the battlefield.
Protests are likely to continue in the short term in Turkey, and there is a realistic possibility of an intensification on 28-30 March. Further arrests of journalists and opposition figures are highly likely.
Israeli strikes in southern Beirut likely targeted Hezbollah senior leadership and will likely force Hezbollah into retaliatory attacks on northern Israel.
There is a realistic possibility of a return to civil war in Syria as the interim government struggles to control its disparate forces, a nascent insurgency likely accelerates, and Israel continues aerial strikes.
The new wave of Israeli strikes in Gaza will almost certainly further worsen the humanitarian situation in the territory. Hamas’ leadership is highly likely to reduce its visibility to avert the threat of decapitation.
It is likely that South Sudan will return to civil war following the arrest of Vice President Riek Machar, with the power-sharing terms of the 2018 peace agreement having been effectively dismantled by President Salva Kiir.
Asia-Pacific (APAC)
The approaching deadline for the forced deportation of Afghan migrants from Pakistan is likely to result in security implications in both countries, including increased radicalisation, unrest and militancy.
Significant damage and casualties almost certain after 7.7 magnitude earthquake close to Mandalay, Myanmar’s second biggest city. Significant disruptions likely to persist in Thailand.
Further wildfires likely in South Korea due to particularly dry weather after the country experiences its largest wildfires on record.
North, Central and South America
Brazil: Supreme Court to trial Bolsonaro
On 26 March, Brazil’s Supreme Court unanimously ruled that former President Jair Bolsonaro will face trial for his alleged role in attempting to overthrow the government in a military coup following his electoral defeat in 2022.
The former president will face charges relating to his involvement in an armed criminal organisation, participating in a group formed to undermine democratic institutions, and attempting to violently abolish the democratic rule of law, alleging that he sought to overthrow Brazil’s democratic system through force. He is also charged with conspiring to execute a coup d’état to depose the legitimately elected government. Additionally, he faces accusations of causing damage to federal property during post-election unrest and making serious threats against the state that could “destabilise governmental functions”.
If convicted, Bolsonaro could face a substantial prison sentence. The trial is expected to take place in late 2025, but a specific date has yet to be announced.
Solace Global Assessment:
The trial of Bolsonaro will almost certainly have major political implications as it threatens to fracture Brazil’s powerful right-wing movement and will permanently end the former president’s political career. Consequently, much of his substantial support base will likely interpret this as a politically motivated move against the right ahead of the 2026 presidential election.
As recently as 16 March, thousands of supporters gathered at Rio de Janeiro’s Copacabana Beach to express support for Bolsonaro and demand a pardon for those accused of ransacking government buildings. While these protests did not attract as many as originally forecasted, the confirmation of a trial likely has the capacity to reinvigorate his support base, leading to larger and more frequent demonstrations.
There is a realistic possibility that the confirmation of a trial may provoke immediate rallies in several Brazilian cities that may result in violent interactions with the police or transport disruptions.
Chile: Day of the Young Combatant likely to result in large-scale protests
On 29 March, Chile will observe the 40th “Day of the Young Combatant” (Día del joven combatiente). The day commemorates the killing of the two Vergara Toledo brothers in Santiago in 1985 during the dictatorship of Augusto Pinochet.
The two brothers were allegedly part of the Revolutionary Left Movement (MIR), a radical left-wing group that was at the forefront of the struggle against the dictatorship. The commemoration also extends to the other activists who were killed or imprisoned during the dictatorship.
The anniversary has continued to be politically relevant, reflecting broader anti-government and anti-police sentiment.
Solace Global Assessment:
Several protests are planned to occur in downtown Santiago on 29 March. Unrest is likely to start in the late morning of 29 March and continue throughout the day, highly likely intensifying in the evening when organised rallies and protests conclude.
Past demonstrations during the Day of the Young Combatants have consisted of protesters erecting makeshift barriers, burning tyres, vandalising private businesses (particularly banks and the offices of foreign companies), firing projectiles including fireworks, and throwing Molotov cocktails at the police and other targets. Some demonstrators will likely be armed and are likely to seek direct confrontation with police forces. Chilean police will almost certainly deploy violent crowd control measures in response to the unrest, including tear gas, pepper spray, water cannons, and possibly rubber bullets. Past demonstrations have resulted in dozens of arrests.
While Santiago will almost certainly be the epicentre of the protests, unrest is possible in the central areas of Valparaiso, Conception, Telmuco, and other Chilean cities. There is a realistic possibility that protests will be driven by other grievances disconnected from the commemoration. For instance, there are ongoing protests in Valparaiso over a controversial fishing sector law; local left-wing groups may seek to stage joint unrest during the Day of the Young Combatant to capitalise on visibility.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
Canada’s new Prime Minister calls snap elections for 28 April 2025
Mark Carney succeeded Justin Trudeau after the latter resigned amidst extremely low polling numbers for his Liberal Party. In his short tenure, Carney has seen his party massively rising in the polls and matching the opposition, the Conservative Party. The unprecedented surge in Liberal support, which has almost certainly re-opened the electoral race, was highly likely driven by the trade war with the United States, with the Conservatives perceived as too “Trump-friendly” by parts of the centrist electorate. Carney highly likely called the vote to both benefit from the surge in popular support and to increase the political legitimacy of his leadership.
Peru to hold general elections in April 2026
On 26 March, Peruvian President Dina Boluarte announced that the country would hold general elections in April 2026 in an effort to resolve ongoing instability. A new president, 130 deputies and 60 senators will be up for election.
The current president has not stated whether she will stand, however, Boluarte’s approval rating has hit an all-time low, with 93 per cent of Peruvians stating that they disapprove of the president. Widespread dissatisfaction with the incumbent government has likely been influenced by a huge rise in violent crime across Peru. This has involved indiscriminate attacks on public transportation and businesses linked to extortion rackets controlled by powerful transnational gangs.
The violence has become so severe that a 30-day state of emergency covering the capital Lima, and the neighbouring province of Callao was imposed on 18 March. Similar measures are likely to be introduced to curb the rise of violent crime, with Boluarte recently replacing the Interior Minister with a retired police general, a move that likely indicates her government’s intention to take a more hardline approach to law enforcement.
10 April general strike to be held in Argentina against President Milei’s policies
Argentina’s largest trade union federation, the General Confederation of Labor (CGT), has announced a 24-hour general strike on 10 April to protest President Javier Milei’s austerity policies. This will be the third general strike since Milei took office in December 2023.
The CGT cited wage restrictions, declining purchasing power, job losses, and cuts to the public health system as reasons for the strike. The union also plans to participate in protests on 24 March to commemorate victims of Argentina’s last military dictatorship, as well as demonstrations on 9 April and International Workers’ Day on 1 May. Protests will likely result in disruption to key sectors such as transport, healthcare, banking, and public administration and could result in violent interactions with the police.
Security, Armed Conflict and Terror
FBI establishes task force to investigate vandalism across the US
The Federal Bureau of Investigation (FBI) has established a new task force to investigate escalating vandalism at Tesla dealerships and charging stations across the US. Some attacks have included incidents involving incendiary devices and assaults, leading the FBI to refer to some of the action as “domestic terrorism”.
The attacks are almost certainly linked to the divisive involvement of Tesla CEO Elon Musk within the Trump administration, which has led to budget cuts and the loss of thousands of federal jobs and will almost certainly continue in line with government policies.
Previous attacks on infrastructure powering Tesla-linked facilities have caused significant disruptions to other businesses that rely on the same infrastructure, affecting their operations and productivity, as demonstrated by the attack on energy infrastructure powering the Tesla Giga factory near Berlin, Germany.
Car driven into anti-Tesla protesters in Florida
On 22 March, a man reportedly drove his vehicle into a group of protesters gathered outside a Tesla dealership in Palm Beach. No serious injuries were recorded, and the man was arrested by police. It is highly likely that the incident was a targeted attack on the demonstrators. The episode is notable as it matches a trend, observed in the US as well as in some European countries, of car-ramming attacks against high-visibility protest crowds. For instance, during the 2020-2021 Black Lives Matter protests, more than 60 car-ramming attacks on crowds were recorded. As anti-Tesla protests are likely to remain highly visible, the threat of further attacks remains.
US mulls death penalty for notorious Mexican drug lord
The US is considering the death penalty for Mexican drug lord, Rafael Caro Quintero, following his extradition. Quintero, who has been linked to the killing of DEA agent Enrique Camarena, has been charged with continuing criminal enterprise and conspiracy to import cocaine, among other charges. The growing threat of extradition, long prison sentences, and the death penalty is likely to send a message to the Mexican cartels, who may adapt their operations or even respond with increased violence to shield themselves from this developing threat.
Environment, Health and Miscellaneous
Severe flooding continues to impact US-Mexico border
Severe flooding continues to impact communities along the US- Mexico border, causing widespread disruptions on both sides. Authorities have issued flash flood warnings in affected areas, with emergency responders conducting rescues as rising waters trap residents.
Schools have been forced to close, and non-emergency communication lines are down in some locations, though emergency services remain operational. In Mexico, multiple neighbourhoods are inundated, prompting the opening of emergency shelters. Reports indicate at least one fatality due to drowning, while infrastructure damage includes a hospital roof collapse.
Power outages are affecting thousands as utility crews work to restore service. Low-lying areas are at high risk with further rain forecasted, which is likely to disrupt emergency efforts and delay border crossings.
Europe, Middle East & Africa
Ukraine: Limited Black Sea ceasefire agreement announced by US following bilateral talks
Bilateral talks in Saudi Arabia between US-Russia and US-Ukraine have continued. On 25 March, the White House announced that an agreement had been reached with Russia to “eliminate the use of a force” and “prevent the use of commercial vessels for military purposes in the Black Sea”. In exchange, the US will “help restore Russia’s access to the world market for agricultural and fertiliser exports”, including a reference to enhancing access to “ports and payment systems for such transactions.”
The Kremlin stated that the limited Black Sea ceasefire would only come into force if specific demands were met, particularly: the lifting of sanctions from the agricultural bank Rosselkhozbank and its reconnection to the SWIFT international payment system.
Kyiv also agreed to a Black Sea ceasefire proposal but emphasised that any movement of Russian naval vessels outside of the “Eastern part of the Black Sea” would violate the agreement.
On 26 March, statements from both Kyiv and Moscow accused each other of breaching the earlier 18 March energy infrastructure ceasefire. Russian officials have accused Ukraine of striking energy infrastructure in Kursk Oblast, Crimea, and Bryansk Oblast between 25-26 March, while Ukrainian officials have accused Russia of conducting at least eight strikes on energy facilities since 18 March.
Solace Global Assessment:
The nature of the bilateral talks and limited ceasefire agreements, which have excluded any direct Russia-Ukraine talks and have not produced any jointly signed agreements, highly likely make their conditions challenging to enforce. It is almost certain that cyclical accusations of ceasefire violations will continue, with differing understandings of the specific conditions or terms of the agreements.
The Black Sea ceasefire proposal will highly likely only have a small impact on the overall strategic picture of the war, with the Russian Black Sea Fleet being only minimally active since the emergence of the Ukrainian uncrewed surface vessel (USV) threat to Russian vessels. Ukraine has leveraged USVs, in addition to anti-ship missile systems, to effectively challenge Russia in the maritime domain and force its retrograde from its home port of Sevastopol.
The Black Sea ceasefire, therefore, likely provides tangible advantages to Russia as its maritime threat has been successfully challenged. Additionally, there is a plausible scenario in which the Black Sea Fleet could exploit the ambiguous terms to launch ship and submarine-launched missiles from the Black Sea at land-based targets in Ukraine, intentionally interpreting the terms as applying solely to attacks against targets within the Black Sea.
A cessation of Ukraine’s USV threat may also enable Russia to resume its maritime resupply from mainland Russia to Crimea, which could help Russia sustain operations in places like Kherson and Zaporizhia. Russia may honour a deal which includes refraining from attacking merchant shipping, as this would help ensure global food security, enabling it to secure its geopolitical influence, particularly in developing countries that rely heavily on Ukrainian grain.
The US President Donald Trump’s administration is likely motivated to further a narrative that they are furthering progress towards peace in Ukraine, even if the limited ceasefire agreements are largely symbolic and lacking in specifically enforceable conditions that are mutually ratified. The Kremlin will highly likely continue to leverage ceasefire talks and proposals to gain concessions while continuing to pursue their maximalist objectives on the battlefield.
The Black Sea agreement has been specifically leveraged by Putin, for example, to gain the potential removal of SWIFT sanctions for Rosselkhozbank. In 2022, following the full-scale invasion of Ukraine, major Russian banks were removed from the SWIFT network, which is critical to facilitating cross-border payments in the international financial system. However, it is likely that the Trump administration will face significant challenges in complying with demands to remove such key sanctions, as EU cooperation would be necessary.
Moscow is almost certainly incentivised to further a split between the US and Ukraine’s European partners and will likely intensify hybrid operations against European targets as the transatlantic rift widens.
Turkey: Protests continue, multiple journalists detained
Turkish authorities have arrested and deported BBC journalist Mark Lowen over “threats to public order” and have detained at least seven other journalists, including those from AFP, over their coverage of the unrest. Protests have continued in Istanbul and other large urban centres a week after the arrest of opposition leader Ekrem Imamoglu.
Approximately 2,000 people have been detained so far due to the unrest, and more than 150 police officers have been injured. The municipality council of Istanbul elected an interim mayor on 26 March, preventing the government from appointing a trustee to oversee the city’s administration.
Ankara has likewise imposed bans on reporting on opposition television and radio channels, threatening them with closure if they do not comply.
Solace Global Assessment:
The protests have slightly decreased in intensity compared to the 19-21 March period but remain active, especially in Istanbul. There is a realistic possibility of another increase in intensity during the weekend of 29-30 March, with the Turkish opposition vowing that protests will continue in “every city.
The government of Turkey has sought to capitalise on its geopolitical successes to minimise the possibility of European pushback on its crackdown on the opposition, and, with Turkish financial assets plunging, Ankara likely assesses that Brussels will not take the politically risky choice of imposing sanctions.
It is likely that unrest will continue in the medium term and that Ankara will continue using the police to target the opposition and journalists covering the protests. Travellers are likewise at risk of arbitrary detention, and there is a high likelihood that authorities will use emergency powers, such as travel restrictions for participants in demonstrations, to quash voices perceived as dissenting.
There is a realistic possibility that Imamoglu’s arrest is just the initial step in a series of actions aimed at suppressing the opposition and securing the reform of the constitutional limit on presidential terms, ultimately paving the way for Erdogan’s victory at the polls. In such a case, Turkey is likely to experience episodic unrest in response to these moves until the run-up to the 2028 elections.
Lebanon: Ceasefire in jeopardy after resumed strikes
On 21 March, rockets were fired from southern Lebanon into northern Israel. The Israel Defense Forces (IDF) claim to have intercepted three rockets, and a further three landed in Lebanese territory. This marks the first rocket attack on northern Israel from Lebanon since early December.
The IDF responded with counter-battery fire and then conducted two waves of air strikes on 22-23 March against Hezbollah high-value targets across Lebanon, including weapons depots, headquarters, fighters, and rocket launchers. The attacks were confined to southern Lebanon and the Hezbollah stronghold of the Bekaa Valley near the Syrian border.
However, on 28 March, the IDF issued evacuation orders for residents of Hadath in southern Beirut to evacuate in the first such order for the Lebanese capital since the ceasefire was established.
Solace Global Assessment:
The limited nature of the rocket attack may suggest that this was not an attack authorised by Hezbollah’s senior leadership, indicating the possibility of a rogue faction or lower-ranking operatives acting independently. However, the initial response from the IDF likely indicates that Israel is seeking to exploit the attack to further degrade the Shia militant group.
IDF strikes on this scale have likely undermined any prospects for de-escalation between Israel and Hezbollah and are likely to lead to a renewed threat in northern Israel. Hezbollah likely has some tolerance for attacks on rank-and-file fighters or rocket launch sites. However, the evacuation order for parts of southern Beirut, a known Hezbollah stronghold, likely indicates that the IDF has conducted a strike on a high-value target, most likely the senior leadership.
If this is the case, this will almost certainly be beyond Hezbollah’s threshold for attacks and will highly likely result in retaliatory attacks that will undermine the already fragile ceasefire agreement.
Syria: Nationwide internet outage due to sabotage as Israeli strikes continue
The Syrian interim-government controlled Ministry of Information reported on 24 March that a cyberattack had targeted official government platforms and private social media accounts. The Ministry claims that the attack was an organised effort conducted by Assad-regime remnants.
On early 25 March starting at 02:40 local time, a nationwide total internet outage occurred, lasting for approximately 12 hours. Authorities stated that the outage was the result of sabotage, with two fibre optic cables being cut near Homs and Damascus.
Concurrently, on early 25 March, the Israeli Air Force (IAF) conducted aerial strikes on a former Syrian Arab Army (SAA) airbase near Palmyra. This was followed on 27 March by multiple IAF strikes against an ammunition warehouse in the White Harbour area of Latakia, with no casualties yet to be reported.
On 26 March, the former Grand Mufti of Syria, Sheikh Ahmed Badr al-Din Hassoun, who served in the official Sunni religious leadership post between 2005 and 2021, was arrested by Syrian security forces. Hassoun was arrested at Damascus International Airport (DAM) whilst attempting to depart Syria to Amman, Jordan for a surgical operation.
Solace Global Assessment:
The Transitional President of Syria and former Emir of the now officially dissolved Islamist militant group Hayat Tahrir al-Sham (HTS), Ahmed al-Sharaa, has to contend with a myriad of threats to Syria’s security. The Israeli strikes are indicative of a continuing strategic objective for the Israel Defense Forces (IDF) to degrade the future potential of Syria’s new armed forces, with the HTS-led interim government almost certainly perceived as a threat to Israel’s security.
It is estimated that al-Sharaa’s HTS group is comprised of only 20,000 fighters, including a notable contingent of jihadist foreign fighters, who now serve as the core of Syria’s new national armed forces. This relatively small size has almost certainly forced al-Sharaa to rely on fighters from other groups officially integrating into the Syrian Army for Syria’s defence, such as the Turkish-backed Syrian National Army (SNA).
As demonstrated by the retribution massacres conducted against Syrian Alawites in early March, it is highly likely that Damascus exercises minimal command and control over the disparate groupings of fighters that act on behalf of the new Syrian state.
The arrest of Hassoun follows an arrest warrant being issued, with Hassoun having been a firm supporter of the Assad regime. Whilst al-Sharaa has promised amnesty for surrendering SAA soldiers and lower-level officials, he has also promised to bring justice to leading regime figures and SAA commanders responsible for crimes against humanity.
In February, protesters stormed Hassoun’s home in Aleppo following sightings of the former Grand Mufti being publicised on social media, with anger being further catalysed by videos depicting him as the “Mufti of Barrels”, almost certainly in reference to the barrel bombs deployed by the regime against urban centres during the civil war.
Syrian security forces had protected Hassoun’s home and dispersed the protesters during the February protests, however, his arrest now is likely indicative of increasing efforts by Damascus to prosecute regime remnants with the threat of a nascent insurgency and likely increasing dissatisfaction from hardliners against al-Sharaa.
Although it is likely that both the past week’s cyberattacks and sabotage against critical telecommunications infrastructure were conducted by individuals associated with Assad-regime remnants, there is a realistic possibility that Israeli covert operations have also played a supporting role to further undermine the burgeoning but highly fragile post-Assad Syrian state. It is likely that in the pursuit of their objectives, leading Israeli military and intelligence figures are incentivised to support the fracturing of the new Syrian state.
There is a realistic possibility of a return to civil war in Syria if the interim government remains unable to control the latent extremist elements in its de facto irregular armed forces and regime remnant insurgent groups grow in popularity amongst the under-threat Alawite minority. A renewed civil war is likely to draw in both Hezbollah and Iran, a development that would benefit Israel by diverting the attention and resources of these hostile actors away from its borders.
Israel & Gaza: Israeli strikes continue as humanitarian situation deteriorates
Ten days after the collapse of the ceasefire, Israeli forces have continued to carry out airstrikes in the Gaza Strip with the aim of decapitating the remaining Hamas leadership and forcing the group to release the remaining hostages. More than 800 Palestinians have been reportedly killed since the resumption of hostilities.
On 23-24 March, Salah al-Bardawil, a senior member of Hamas’ political bureau, was killed in a strike in the al-Mawasi zone in Khan Yunis. Another member of the political bureau, Ismail Barhoum, was killed in a strike on Nasser Hospital. Since 2 March, the Gaza Strip has been under an aid blockade, causing food prices to surge, according to reports from the World Food Programme (WFP) and other humanitarian agencies.
Solace Global Assessment:
It is highly likely that the blockade, strikes, and evacuation orders (which reportedly have displaced over 130,000 since 18 March) will result in a sharp short-term increase in the severity of the humanitarian crisis in Gaza. Militarily, it is highly likely that Israeli forces’ sudden and coordinated wave of attacks starting on 18 March took advantage of Hamas’ operational security vulnerabilities. This likely enabled successful decapitation strikes against the group’s leadership. Furthermore, it is likely that Israel used the ceasefire period to conduct increased intelligence gathering, refining target lists and exploiting Hamas’ weaknesses to enhance the effectiveness of these strikes.
Israeli and Hamas officials have resumed truce talks in Qatar indirectly via an Egyptian delegation. On 27 March, Egyptian officials reported a series of further ceasefire terms being discussed by the two sides. There is a realistic possibility that the high intensity of Israeli strikes in Gaza is aimed at forcing Hamas officials into granting further concessions, such as a more expedited release of the remaining hostages. Hamas almost certainly retains a fundamental interest in remaining the key political force capable of exercising administrative functions in Gaza. Israeli strikes may put pressure on the group by forcing it to become less visible, thus threatening its political viability.
South Sudan: Country on precipice of return to civil war following Machar’s arrest
Late on 26 March, a heavily armed convoy comprising high-ranking security officials, including the defence minister, stormed the Juba residence of South Sudan’s First Vice President Riek Machar, disarmed his security personnel, and placed him under house arrest. The arrest follows a marked escalation in South Sudanese tensions since late February. These tensions have triggered fears of a return to civil war following heavy fighting between the national army and White Army militias in Nasir, Upper Nile State.
Clashes have continued, with a spokesman from Machar’s Sudan People’s Liberation Movement-in-Opposition (SPLM-IO) claiming on 24 March that South Sudanese military airstrikes struck an SPLM-IO base near Wun Aliet, Unity State. This followed an incident where SPLM-IO and government Sudan People’s Liberation Movement (SPLM) forces almost opened fire on one another near Wun Aliet following perceived hostile manoeuvring.
Both the UK Foreign Office and US State Department have advised their nationals to leave South Sudan immediately if safe to do so.
Solace Global Assessment:
The risk of a return to civil war has almost certainly significantly increased following Machar’s detention, with the SPLM-IO stating that his arrest has invalidated the 2018 peace deal. The fundamental power-sharing basis for the 2018 peace agreement has almost certainly been effectively dismantled by President Salvar Kiir in recent weeks.
It is likely that armed confrontations between SPLM and SPLM-IO ground forces will break out as troops continue to engage in brinkmanship, which would, in turn, likely lead to further nationwide escalation. It is highly likely that if the civil war resumes, fighting will break out in similar patterns to the 2013-2018 conflict, resulting in significant civilian casualties and displacement, including gun battles in the capital, Juba.
There is also a risk of regional escalation, with the deployment of Ugandan forces to Juba to support Kiir leading to significant condemnation from SPLM-IO figures.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
UK-based environmentalist group announces end to direct action
On 27 March, Just Stop Oil (JSO), an environmentalist group that has carried out multiple high-visibility protests in London and other large UK cities, announced it would cease direct action following a protest on 26 April. The group justified the move by stating that their demands had been satisfied by government policy. JSO is an important direct-action group, and the decision to end protests will likely create more opportunities for smaller movements to recruit and stage actions.
General strike to be held in Belgium on 31 March
A general strike is scheduled to take place in Belgium on 31 March, organised by the socialist trade union FGTB/ABVV and the Christian union CSC/ACV in response to cuts in the new Federal Government’s budget. The strike will almost certainly result in significant nationwide disruptions and coincide with widespread protests.
Key sectors, including education and public services, will be affected as workers take to the streets to protest what they consider anti-social measures, such as cuts to pensions and benefits. All passenger flights from Brussels Airport and Charleroi Airport will be cancelled, with Brussels Airlines set to suspend all its operations. Rail services will also face disruptions, and public transport across Brussels will be significantly affected.
German far right march in Berlin
Around 40 people were detained by police on 22 March during a march by far-right groups, including neo-Nazi formations, in the Friedrichshain area of Berlin. The march consisted of around 850 individuals and is assessed as being the largest neo-Nazi demonstration in Berlin in recent months. According to local media, at least 2,000 counterprotesters blocked the march’s path, resulting in its early end.
Austria uncovers large-scale information operations in German-speaking countries
According to Austrian authorities, shortly following the Russian invasion of Ukraine, a cell run by a Bulgarian national began spreading large quantities of disinformation with the goal of influencing popular opinion in Austria and Germany. The cell, which posed as a pro-Ukraine group, reportedly had ties to Jan Marsalek, the COO of the insolvent payment processing firm Wirecard, who is currently a fugitive and is alleged to be an asset for Russian intelligence.
The Austrian group reportedly used low-cost and low-sophistication tactics, both online and offline, such as vandalism. The case further highlights how Russia is exploiting internal divisions in Europe to sponsor highly deniable and low-cost acts of sabotage and violence to deter, disrupt and divide its adversaries, a trend that will likely increase if Europe increases its support for Ukraine in response to US disengagement.
Thousands continue to protest in Hungary over Pride parade banning
On 25 March, thousands of protestors in Budapest blocked major roads and bridges in response to the government’s decision to ban Pride events and restrict the right to assembly. The protest was the second in two weeks since the ruling Fidesz party used its two-thirds parliamentary majority to expedite the law. The authorities will now also be authorised to use facial recognition software to identify those who attend the prohibited event. Further protests will highly likely be organised in central Budapest in the run-up to the city’s 30th Pride parade anniversary, scheduled for 28 June. Any attempt to hold a parade will almost certainly to be met with police opposition.
Protests in North Macedonia over nightclub fire
On 24 March, thousands of protestors gathered in the North Macedonian capital of Skopje to demand greater accountability for those responsible for the 16 March nightclub fire that killed 59 people. The government has arrested at least 13 people, including a former finance minister and seven police officers, as part of a corruption investigation linked to the fire. However, public outrage remains high and over 100 victims of the fire remain in care in multiple European hospitals. Further deaths and he failure to hold those responsible to account will likely trigger further protests, which may evolve into a wider movement against perceived corruption in the country.
Niger’s junta government outlines a five-year transition to constitutional rule
On 26 March, General Abdourahamane Tchiani, who came to power in a military coup in July 2023, was sworn in under a new charter which replaced Niger’s old constitution. Under the new charter, Tchiani is set to be president for a transition period of five years, rejecting attempts by the Economic Community of West African States (ECOWAS) to hasten the return to democracy after Niger proposed a three-year transition period. The new charter allows flexibility on the five-year term, depending on the status of the insurgencies.
The move comes after Niger’s government left ECOWAS alongside Mali and Burkina Faso to form a trilateral Alliance of Sahel States (AES), which enables the conflict-ridden countries greater sovereignty and independence. Burkina Faso’s military junta has already extended the transition period to July 2029, while Mali postponed elections scheduled for February 2024 with no new date set.
Zimbabwean president dismisses army chief
On 26 March, Zimbabwean President Emmerson Mnangagwa fired the country’s head of the armed forces, General Anselem Sanyatwe, amid rising concerns about a potential coup from former allies. President Mnangagwa is facing increasing pressure from members of his ZANU-PF party and from war veterans, who accuse him of worsening the nation’s economic crisis and trying to extend his rule beyond 2028. The dismissal follows the reshuffling of the military, police, and intelligence positions, moves that have likely been conducted to help Mnangagwa consolidate his power and send a message to those demanding he is replaced.
Several influential veterans of the country’s war of independence have called for nationwide demonstrations to be organised on 31 March, demanding that Mnangagwa step down. If the protests materialise, there is a strong likelihood that the government will respond with violence, given that Zimbabwean security forces have previously used excessive force, including live ammunition, to suppress protests, as seen after the 2018 elections.
Security, Armed Conflict and Terror
Five wounded after knife attack in central Amsterdam, the Netherlands
On 27 March, a man reportedly carried out a knife attack in Dam Square in central Amsterdam, wounding five people, including a child. No deaths have been reported as of the time of writing, and the attacker was subdued by bystanders on the scene before being arrested. The attacker’s identity has not officially been confirmed as of the time of writing. There is a realistic possibility that the attack was an ideologically motivated case of lone wolf terrorism, due to both its dynamics and the attacker’s choice of a high-visibility area of Amsterdam’s centre.
US continue unilateral strikes on Houthi targets in Yemen
The US’ Central Command (CENTCOM) has continued to conduct unilateral strikes on a series of targets across Houthi-controlled Yemen. Yemeni media report that at least 44 US strikes were conducted on the night of 27-28 March, with targets hit across Sana’a, Amran, Sa’dah, Al Hudaydah and Al Jawf regions, purportedly including residential neighbourhoods in the capital Sana’a and the port city of Hodeida. This marks a major shift in strategy under President Trump, moving to targeting senior leadership and even rank-and-file personnel in major population centres, rather than strictly targeting military facilities in sparsely populated areas.
The strikes are likely a direct response to escalating Houthi attacks on Red Sea shipping and US military assets in the region, as well as renewed attacks on Israel. However, the strikes are likely to increase international condemnation, strengthen anti-US sentiment in the region and could provoke Iran into providing more support to the militant group. The Houthis’ immediate response will likely be to escalate attacks on merchant shipping, US military assets, and Israel in a show of defiance.
Sudanese Armed Forces (SAF) take Khartoum, ending a two-year-long battle
On 26 March, SAF officials claimed they had taken control of the entirety of the Sudanese capital after expelling the Rapid Support Forces (RSF) from their final strongholds in the city’s south. The capture of Khartoum concludes a two-month-long offensive and, more broadly, almost two years of fighting over control of the city. RSF leaders have pledged that they will continue to fight; they will highly likely concentrate most of their efforts in the country’s west, with the goal of establishing a viable political entity.
Taking Khartoum is not only a political victory but is likely also a strategic one. Establishing control over the city will allow the SAF to solidify its positions on the eastern banks of the Nile and subsequently concentrate their forces for a westward offensive into RSF-controlled territory.
Islamists kill over 40 in Niger mosque attack
On 21 March, Islamist militants surrounded the Fambita Mosque in Niger’s southwest Tillabéri Region and randomly shot at worshippers, killing 44 and injuring a further 11. The militants then reportedly set fire to a market and several homes in the area. The attack occurred during Friday prayers in the last ten days of the Muslim holy month of Ramadan.
Local sources have attributed the attack to the Islamic State’s Sahel Province (ISSP), formerly the Islamic State in the Greater Sahara (ISGS). The intent of the attackers was almost certainly to cause as many civilian deaths as possible to instil fear and could have been retaliation for supporting rival groups or the government.
The attack is a further indication of the destabilisation of the Sahel region and demonstrates how extremist groups are continuing to exploit the Niger, Mali, and Burkina Faso tri-border area as a safe haven due to its porous borders and lack of effective governance.
Islamists attack separate army facilities in Nigeria’s Borno State
On 24-25 March, Islamist militants launched coordinated attacks on an army base and a military outpost in Nigeria’s northeastern Borno State, killing at least 16 soldiers. The militants are expected to have belonged to both Boko Haram and the Islamic State West Africa Province (ISWAP), according to Nigerian military sources.
In a potential sign of growing sophistication, the militants reportedly reconnoitred the positions with drones before conducting a ground assault and successfully looted a stockpile of weapons. The attacks will likely embolden militants in the area, especially if there is developing coordination between Boko Haram and ISWAP, who have previously fought against one another.
The attack may indicate a temporal alliance between the rival Islamist groups, with both likely attempting to exploit Nigerian military defences or seize an opportunity to overstretch its forces.
Al-Shabab kill Kenyan police officers in cross-border attack
On 23 March, suspected al-Shabaab militants launched an attack on a police camp in Garissa County, Kenya, near the Somalia border. The assault resulted in six police officers being killed and four others injured. The attackers used a variety of weapons to overpower the camp housing police reservists. The US embassy in Kenya has issued a travel alert, warning citizens to avoid parts of Kenya, including Garissa, due to the threat of militancy. The attack demonstrates al-Shabab’s ability to cross porous borders to conduct attacks, which it likely uses to obtain international publicity, recruit from within Kenya and to deter Kenyan counter-insurgency efforts.
AFC/M23 backtrack from agreement to relinquish control of Walikale in the DRC’s North Kivu region
On 20 March, AFC/M23 captured the mining hub town of Walikale in North Kivu, which is the furthest west the group has advanced since their conception in 2012. However, in a reported peace gesture, they announced that they would withdraw their forces on 22 March. In exchange for the withdrawal, they requested that Walikale and its surrounding area remain demilitarised, stating that hostilities would resume if the Armed Forces of the Democratic Republic of the Congo (FARDC) returned.
They then changed their mind, stating that they would not pull out unless the FARDC pulled out first. Fighting has resumed in the territory; three people were reportedly killed following a shootout between AFC/M23 near Walikale on 27 March. The attempt to withdraw from Walikale while preventing a FARDC takeover of the city is highly likely indicative that AFC/M23 are overstretched and cannot hold Walikale while continuing to also advance north and south. Therefore, the withdrawal of troops from the town likely indicates that they will redeploy the forces to support an advance either north towards Butembo, south towards Uvira, or potentially both.
Environment, Health and Miscellaneous
Evacuations underway in Campania, Italy, over volcanic risk
At least 350 people have been evacuated so far from the area of Pozzuoli, near Naples, following tremors. The town is located on the Phlegraean Fields, a caldera volcano which is assessed as one of Europe’s major volcanoes. On 13 March, a 4.6 earthquake was recorded in the area, the strongest in 40 years and between 17 and 23 March, 42 localised earthquakes were recorded.
On 22 March, small-scale clashes were recorded between police forces and members of a local citizens’ group who were demonstrating to request government intervention to address the risks of growing seismic activity. An eruption at the Phlegraean Fields site could be extremely disruptive and endanger much of the resident populations of Naples and nearby areas. However, even smaller-scale seismic activity could affect the operations of the port of Pozzuoli and nearby infrastructure. Importantly, much of the residential infrastructure in the Campania region is not earthquake-proof, meaning that even intermediate-strength tremors can cause major damage.
Asia–Pacific
Pakistan: Deadline for illegal foreigners to leave country approaches
All “illegal foreigners” currently residing in Pakistan will be expected to exit the country by 31 March or face deportation, which is scheduled to start from 1 April. The order, which comes from Pakistan’s Interior Ministry, will extend to Afghan nationals holding Afghan Citizen Cards and is set to affect nearly 900,000 individuals. There are also approximately 1.3 million Afghan migrants legally residing in Pakistan with a proof of residence permit, and it is unclear as to how the directive will impact them.
The deportation order comes shortly after the reopening of the main border crossing between Pakistan and Afghanistan, which had been closed following border clashes in February 2023. Human rights groups like Amnesty International have condemned the deportation programme, labelling it a violation of international human rights law and the principle of non-refoulement.
Solace Global Assessment:
The deportation programme is part of a wider campaign against Afghans residing in Pakistan. This has involved widespread harassment, arbitrary detentions, deportations, human rights violations, and the bulldozing of Afghan homes and businesses. The Pakistani government has also engaged in the scapegoating of Afghans, blaming them for crime, drug trafficking, terrorism, and civil unrest, enabling it to achieve significant support for the deportations. However, the deportation programme is likely to have security implications in both Pakistan and Afghanistan.
In Afghanistan, the mass return of deported individuals will almost certainly place incredible strain on an already fragile state struggling with economic hardship and a dire humanitarian situation. The influx of returnees, many without support networks or a means of livelihood, will likely exacerbate poverty, fuel instability, and fuel radicalisation, especially as many originally fled from the Taliban. Militant groups, such as the Islamic State Khorasan Province (ISKP), will likely capitalise on this to expand recruitment, increasing the risks of terror attacks in Afghanistan and cross-border attacks into Pakistan.
In Pakistan, the removal of Afghans is unlikely to produce the security benefits the government claims. The directive is likely to risk exacerbating tensions with the Taliban, who are likely to interpret it as persecution of the Afghan diaspora. There is a realistic possibility that the Taliban will respond with increased attacks on Pakistani security services on the border or by supporting cross-border attacks in Pakistan by groups like Tehrik-i-Taliban Pakistan (TTP).
The targeting of Afghan nationals may also deepen sectarian and ethnic divides, increasing the likelihood of civil unrest. Moreover, Pakistan’s security forces are likely ill-equipped to deal with the logistical challenges of forcibly relocating hundreds of thousands of people. With ongoing sectarian violence and a surge in militancy across Balochistan, Khyber Pakhtunkhwa, and other regions, Pakistani forces are likely overstretched, a scenario militant groups may seek to exploit to further undermine the central government.
Myanmar & Thailand: Magnitude 7.7 earthquake in Myanmar; disruptions in Thailand
At 12:50 local time (06:20 UTC) on 28 March, a magnitude 7.7 earthquake struck the Sagaing Region of central Myanmar. The epicentre was located approximately 16 kilometres north-northwest of Sagaing City in Mandalay’s outskirts, at a depth of ten kilometres. The main tremor was followed by several aftershocks of above 5.0 magnitude. The earthquake caused widespread damage across the cities of Sagaing and Mandalay, with multiple high-rise buildings and bridges destroyed. Tremors have also been felt in neighbouring countries, including Vietnam, Bangladesh, China, and Thailand.
The impacts of the earthquake were felt strongly in Thailand, where shaking caused buildings to collapse in Bangkok. The Thai Prime Minister Paetongtarn Shinawatra declared a state of emergency within the first hours of the earthquake being felt and also ordered the evacuation of tall buildings in Bangkok, at least one of which collapsed while under construction. Communications were disrupted in Bangkok, and the Transport Ministry temporarily suspended flights nationwide for approximately 20 minutes; flights have since resumed. Train services were also suspended in the capital until further notice.
Official casualty figures are currently unclear. Myanmar’s military junta controls most radio, television, print, and online media; internet use is restricted; and communication lines are currently down. According to the US Geological Survey, thousands are likely dead as a result of the shaking, stating that ‘high casualties and extensive damage are probable, and the disaster is likely widespread.’ Myanmar’s national disaster management committee has declared a state of emergency in Sagaing, Mandalay, Magway, northeastern Shan State, Naypyitaw Council Area, and Bago.
Solace Global Assessment:
The earthquake is the strongest in Myanmar in over 150 years. The last comparable tremor occurred in 2012 when a magnitude 6.8 earthquake struck near Shwebo, 120 kilometres north of Mandalay. The 2012 earthquake resulted in 26 fatalities: a toll almost certain to be considerably exceeded by the latest quake. North-central, south-central, and central Myanmar frequently experiences seismic activity due to their location within the convergence zone of the Indian and Sunda Plates, where tectonic stress is periodically released as earthquakes.
Several aftershocks have already been felt in Myanmar; further aftershocks are highly likely in the coming days. While the aftershocks are unlikely to reach a similar magnitude to the initial earthquake, further aftershocks of over 5.0 magnitude may still occur. This could further damage structures that have already been weakened by the initial tremor and hinder relief efforts.
A humanitarian crisis has been ongoing in the country since the military conducted a coup in February 2021, deposing the democratically elected government. Several resistance groups formed in the aftermath, triggering a civil war. Significant civilian casualties and widespread displacement have occurred as a result of the conflict, and the nation faces a worsening humanitarian crisis. The earthquake will almost certainly exacerbate the ongoing humanitarian crisis by disrupting power and water infrastructure, trade routes, and agriculture, which accounts for between 25 and 30 per cent of Myanmar’s GDP.
The likely limited assistance will almost certainly be exacerbated by the presence of rebel groups in Mandalay. These groups include Mandalay People’s Defence Force (PDF), Ta’ang National Liberation Front (TNLF), Myanmar National Democratic Alliance Army (MNDAA), and Burma National Revolutionary Army (BNRA). On 14 March, at least 27 people were killed and at least 30 injured after Myanmar’s military junta conducted an airstrike on Singu Township, Mandalay. It is likely that rebel groups will take advantage of the damaged infrastructure and communications networks in the region to capture government-held territory near Mandalay.
South Korea: Country experiences largest wildfires on record
Wildfires which have been burning since 21 March have destroyed at least 118,000 acres. The fires originated in Uiseong and have moved rapidly eastward, fuelled by dry conditions, high winds, and an abundance of sap-filled pine trees. The counties of Uiseong, Andong, Sancheong and the city of Ulsan have been hit the hardest. At least 28 people have been killed so far, 37 injured, and thousands displaced. The fires have destroyed hundreds of structures, including houses, factories, and cultural properties, including a centuries-old Buddhist temple, and have led to the evacuation of around 38,000 residents, including in Andong, Uiseong, Sancheong, and Ulsan. Approximately 26,000 people remain displaced.
Firefighters are utilising approximately 120 helicopters to battle the fires across South Korea’s mountainous topography. One pilot crashed while attempting to contain a fire, and four other firefighters died after being trapped by flames. Efforts to combat the fires are being bolstered by the deployment of US Army helicopters to the North and South Gyeongsang regions. Overnight rainfall on 27 and 28 March has provided better visibility and cooler temperatures, enabling improved firefighting conditions, allowing firefighters to extinguish fires in Yeongdeok, Uiseong, Andong, Cheongsong, and Yeongyang. The latest figures show that wildfires in Uiseong and Andong are 98 per cent and 90 per cent extinguished, respectively.
Solace Global Assessment:
There are currently no reports indicating airport operations have been affected; Incheon International Airport (ICN) and Gimpo International Airport (GMP) are operating as normal. Human activities, including a lighter left on the ground at a funeral, waste burning, and sparks during welding work, are believed to be the root cause of multiple fires. Lee Han-kyung, the disaster and safety division chief, has pointed to climate change for exacerbating the situation.
In South Korea, unusually warm spring temperatures dried out the landscape and, when combined with strong winds, created optimal conditions for fast-moving fires to tear through the region’s dense forests; half the average rainfall has occurred in the affected areas. As the climate crisis worsens, it is driving hotter, drier conditions that cause fires to spread more rapidly and burn with greater intensity. So far this year, South Korea has reported 244 wildfires, 2.4 times more than during the same period last year, according to Prime Minister Han Duck-soo. Given the particularly dry weather, further wildfires are likely.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Royalist protesters set fire to the Unified Socialist Party office in Kathmandu, Nepal
On 28 March, royalist protesters entered the headquarters of the Unified Socialist Party in Aloknagar, strewing documents across the streets and setting fire to the office. The act comes amid planned rival republican and royalist protests on the same day. The republican demonstrators are largely affiliated with The Socialist Front, which comprises opposition parties including the Communist Party of Nepal (CPN)-Maoist Centre and CPN-Unified Socialist; the royalist protesters are led by Durga Prasai, a political activist who frequently calls for the overthrow of the current federal democratic government system.
The District Administration Office has attempted to keep the groups separate, designating the Exhibition Road-Bhrikutimandap for republican protesters and Tinkune for royalist protesters. Approximately 3,500 security personnel were deployed in preparation for the demonstrations. These measures almost certainly indicate the high potential for violence between the rival groups.
The burning of the Unified Socialist Party offices significantly increases the likelihood of clashes between royalists and republicans as demonstrations develop throughout the day. If clashes erupt, it is likely that they will continue into the weekend, given the animosity between the rival groups.
Protests against law expanding military control continue in Indonesia
Protests against the introduction of a new law that enables the military to have more control within the Indonesian government have continued to be organised in multiple cities, including Jakarta, Surabaya in East Java, Aceh, and South Kalimantan. Multiple protests, including ones held outside the parliament building in Jakarta, have escalated to violence, with security forces responding with tear gas, water cannons, and other crowd dispersal measures.
In Surabaya, at least 14 journalists were attacked while covering the anti-government protests, resulting in condemnation from international NGOs. As a result of the police’s response and the fears of Indonesia reverting to its authoritarian past, protests are likely to continue throughout the weekend of 29-30 March.
Australia to hold federal elections on 3 May
On 28 March, Australian Prime Minister Anthony Albanese announced that the country would hold federal elections on 3 May. The vote will select all 150 members of the House of Representatives and a majority of the 76 Senators. Currently, the Labor Party, which is in government, is polling slightly behind the centre-right Coalition. The primary concern continues to be the cost of living crisis, which, as seen in other Western nations, has gained significant political traction in the aftermath of the COVID-19 pandemic. While Australian elections are typically peaceful and well-organised, there remains a potential for civil unrest, particularly in response to major domestic or international political developments.
Security, Armed Conflict and Terror
Militants conduct wave of attacks in Pakistan’s restive Balochistan
Militants belonging to the Balochistan Liberation Army (BLA) have conducted a wave of attacks throughout Balochistan against both Pakistani security services and civilians. On 26 March, Baloch militants reportedly killed five passengers on the N10 highway near Ormara after checking their IDs and targeting those from the Punjab region. On 27 March, an explosion targeting a police van in Quetta killed at least three and injured 21. Earlier, on the same day, another explosion near a police vehicle in Quetta injured four officers.
The attacks likely demonstrate an emboldened BLA since the hijacking of the Jaffar Express on 11 March and indicate that the militant group is likely seeking to exploit a consistently overstretched and underprepared Pakistani military. There are also early indications that the BLA has increased its recruitment of women, which it has used to conduct suicide attacks, a development that will almost certainly increase the BLA’s ability to instil terror and evade security measures.
Taiwanese warship collides with Chinese fishing vessel off central Taiwan
On early 27 March, a Taiwanese Republic of China Navy (ROCN) vessel collided with a Chinese fishing vessel off central Taiwan, with no injuries reported. The naval vessel, a Chung-Ho-class tank landing ship (hull number LST-232), sustained some unspecified damage, which did not compromise its navigational safety, according to the ROCN. Taiwan’s Coast Guard Administration (CGA) dispatched two patrol vessels to the scene at the Navy’s request.
The incident has occurred in the context of continued regular military exercises conducted by China’s People’s Liberation Army (PLA) and navy (PLAN) that cross the median line in Taiwan’s Air Defence Identification Zone (ADIZ). For example, on 26 March, a sortie of 27 PLA aircraft, 6 PLAN vessels and 2 “official ships” were identified by Taiwanese forces. These intrusions occur several times a week. There is a realistic possibility that the vessel collision was the result of aggressive action from either or both the Chinese fishing vessel and the Taiwanese warship.
Chinese fishing vessels, in addition to China Coast Guard (CCG) vessels, are regularly used by Beijing to assert maritime control as part of People’s Armed Forces Maritime Militia (PAFMM), and are often equipped with intelligence, surveillance and reconnaissance equipment and other military hardware. While the vessel collision has passed with minimal diplomatic impact or media coverage, almost certainly due to the lack of injuries, it reaffirms the risk of escalation posed by small-scale maritime incidents should casualties result.
Environment, Health and Miscellaneous
Thousands on standby in expectation of more flooding in Malaysia
Over a thousand members of the Johor Civil Defence Force remain on standby due to the ongoing monsoon transition, which has already resulted in widespread flooding in southern Malaysia, the evacuation of thousands, and disruption on the Malaysia-Singapore border. Despite the official end of the northeast monsoon, forecasts indicate that unpredictable weather during the southwest monsoon transition could lead to flash floods, especially in low-lying areas and landslides in the more mountainous areas. Less severe flooding has also been reported in Malaysian Borneo, in both Sabah and Sarawak states.
6.8 earthquake registered off the coast of New Zealand
On 25 March, a magnitude 6.8 earthquake struck off the coast of New Zealand’s South Island, near Fiordland National Park, at a depth of 33 kilometres. In response, the National Emergency Management Agency issued a tsunami advisory and advised people to avoid beaches due to the risk of strong currents. While no tsunami followed, the depth of the earthquake and historical seismic activity in the region indicate a moderate likelihood of aftershocks, which could persist for several weeks.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence

Emergency Declared as Earthquake Devastates Sagaing and Mandalay
Intelligence cut off: 10:00 GMT 28 March 2025
At 12:50 local time (06:20 UTC) on 28 March, a magnitude 7.7 earthquake struck the Sagaing Region of central Myanmar. The epicentre was located approximately 16 kilometres north-northwest of Sagaing City in Mandalay’s outskirts, at a depth of 10 kilometres. The main tremor was followed by several aftershocks of above 5.0 magnitude. The earthquake has caused widespread damage across the cities of Sagaing and Mandalay, with multiple high-rise buildings and bridges destroyed. Tremors have also been felt in neighbouring countries, including Vietnam, Bangladesh, China, and Thailand.
The impacts of the earthquake were felt strongly in Thailand, where shaking caused buildings to collapse in Bangkok. The Thai Prime Minister Paetongtarn Shinawatra declared a state of emergency within the first hours of the earthquake being felt and also ordered the evacuation of tall buildings in Bangkok, at least one of which collapsed while under construction. Communications were disrupted in Bangkok, and the Transport Ministry temporarily suspended flights nationwide for approximately 20 minutes; flights have since resumed. Train services were also suspended in the capital until further notice.
Official casualty figures are currently unclear. Myanmar’s military junta controls most radio, television, print, and online media; internet use is restricted; and communication lines are currently down. According to the US Geological Survey, thousands are likely dead as a result of the shaking, stating that ‘high casualties and extensive damage are probable, and the disaster is likely widespread.’ Myanmar’s national disaster management committee has declared a state of emergency in Sagaing, Mandalay, Magway, northeastern Shan State, Naypyitaw Council Area, and Bago.
Local reports have confirmed several casualties. In Mandalay, the collapse of a mosque resulted in 10 deaths, and several monks were injured when a monastery also collapsed. In Taungoo Township, a school collapse claimed the lives of five children, and 14 others died when a mosque collapsed. Two fatalities were reported in Pyawbwe Township following the collapse of both a mosque and a university building. In Taungoo Township, a school acting as a shelter for displaced people collapsed, trapping over 20 individuals. In Aungban, Shan, the collapse of a hotel killed two people and left 20 others trapped.
INTELLIGENCE ANALYSIS
Relief Efforts Hindered by Conflict, Terrain, and Aftershocks in Myanmar
The earthquake is the strongest in Myanmar in over 150 years. The last comparable tremor occurred in 2012 when a magnitude 6.8 earthquake struck near Shwebo, 120 kilometres north of Mandalay. The 2012 earthquake resulted in 26 fatalities: a toll almost certain to be considerably exceeded by the latest quake. North-central, south-central, and central Myanmar frequently experiences seismic activity due to their location within the convergence zone of the Indian and Sunda Plates, where tectonic stress is periodically released as earthquakes.
The Sagaing Fault is a major geological feature running north to south through central Myanmar, which likely explains why Bangkok was more affected than areas in Bangladesh. Its positioning induces east-west compression, leading to crustal shortening and uplift, while also generating north-south stress that drives lateral crustal movement. Given its proximity to Myanmar’s largest urban centres, including Mandalay and Yangon, the fault poses a significant risk of damage in the event of future seismic activity.
Several aftershocks have already been felt in Myanmar; further aftershocks are highly likely in the coming days. While the aftershocks are unlikely to reach a similar magnitude to the initial earthquake, further aftershocks of approximately 5.0 magnitude may still occur. This could further damage structures that have already been weakened by the initial tremor and hinder relief efforts.
A humanitarian crisis has been ongoing in the country since the military conducted a coup in February 2021, deposing the democratically elected government. Several resistance groups formed in the aftermath, triggering a civil war. Significant civilian casualties and widespread displacement have occurred as a result of the conflict, and the nation faces a worsening humanitarian crisis. The earthquake will almost certainly exacerbate the ongoing humanitarian crisis by disrupting power and water infrastructure, trade routes, and agriculture, which accounts for between 25 and 30 per cent of Myanmar’s GDP.
Given the mountainous topography of the region, limited capabilities of the authorities, and potential aftershocks, relief efforts will likely be hampered. This will likely be exacerbated by the ongoing conflict, whereby the military junta will almost certainly prioritise regime survival over humanitarian assistance, likely using limited resources to assist the affected regions not under its control. The government has implemented a state of emergency in the aftermath, which may be used to conduct arbitrary detentions, impose curfews, and censor media.
The likely limited assistance will almost certainly be exacerbated by the presence of rebel groups in Mandalay. These groups include Mandalay People’s Defence Force (PDF), Ta’ang National Liberation Front (TNLF), Myanmar National Democratic Alliance Army (MNDAA), and Burma National Revolutionary Army (BNRA). On 14 March, at least 27 people were killed and at least 30 injured after Myanmar’s military junta conducted an airstrike on Singu Township, Mandalay. It is likely that rebel groups will take advantage of the damaged infrastructure and communications networks in the region to capture government-held territory near Mandalay.
Travel Risk Advice: Safety Guidelines for Myanmar
- Closely monitor local news reports and government alerts.
- Expect aftershocks. Be prepared to Drop, Cover, Hold On in case of further tremors.
- During a tremor, if outside, do not enter buildings and move away from buildings, trees, streetlights and overhead lines.
- If inside, pick a safe place (under a sturdy table or desk or against an interior wall and away from windows and heavy furniture). Do not leave until the shaking stops.
- If evacuating a building, always use the stairs. Look out for fires and falling debris.
- Prepare an emergency ‘go bag’ with essentials such as bottled water, batteries, important documents, and medications.
- Confirm booked flights are running before checking out of hotels or travelling to the airport.
- Management should maintain communication with the individuals affected until the event is concluded.
- Heed evacuation orders and travel to government-issued shelters if it is safe to do so.
- Adhere to all instructions issued by authorities.
- Ensure important documents and medications are appropriately stored.
- Prepare for power outages, communication disruptions, and travel delays. Stay away from damaged buildings and affected areas until authorities deem them safe.
Subscribe to free weekly intelligence

Disruptions Expected as Direct Action Campaign Hits UK Insurance Sector
Intelligence cut off: 10:00 GMT 25 March 2025
On the morning of 25 March, starting at 10:00 UK time, a consortium of 12 pro-Palestine, environmentalist and left-wing groups are staging coordinated protests at the headquarters and offices of major insurance companies in London, Birmingham, Glasgow, and Manchester.
The protests, dubbed “Boycott Bloody Insurance” are aimed at opposing companies that the organisers deem to be “complicit in genocide” in Gaza and to be supporting the Israeli war efforts. The latest protests are part of a larger campaign that was launched on 10 March 2025, following the release of a report documenting the companies’ alleged ties to entities operating in Israel or providing munitions and arms to Israel.
The 10 March report has already had some impact in driving civil unrest and direct action targeting insurance companies. The Palestinian Youth Movement used the report to justify action against the global logistics company Maersk. Other groups that endorsed or supported the report include the Palestine Solidarity Campaign, the Palestinian Boycott Divestment Sanction (BDS) Committee, and the Watermelon Index.
Insurance companies have already been targeted by groups like Palestine Action. For instance, on 17 March, Palestine Action activists sprayed the front of the Allianz company offices in Manchester with red paint
INTELLIGENCE ANALYSIS
Security Concerns Rise as UK Protesters Target Insurance Sector Over Gaza Links
The 25 March protests are highly likely to be comprised of small-scale actions and are unlikely to significantly disrupt travel and services in the City of London and near the targets in Manchester, Birmingham, and Glasgow. Groups of activists will likely consist of a few dozen individuals at most. However, attendees are likely to be trained in direct action and may have some tools that could be used as weapons in a confrontation.
Based on previous protests, it is highly likely that the methods employed by the activists will be aimed at obtaining maximum media visibility through direct action. Consequently, it is highly likely that protesters will seek to spray paint on the entrances to the companies’ office buildings, smash windows, and may seek to physically disrupt entry to them by either forming human chains, “locking on” (attaching themselves to the buildings, their doors, or the ground immediately in front of them), or installing locks or chains to doors to prevent access.
Employees and bystanders entering the buildings or transiting in their vicinity are likely to face harassment and may be at a greater risk of violence, especially if they try to confront the protesters. There is also a realistic possibility of company and employees’ vehicles being vandalised, especially if they have clearly visible company logos.
Travel Risk Advice: Safety Guidelines for the United Kingdom
- Avoid all large gatherings.
- Closely monitor local news reports and government alerts.
- Monitor the local transport authority websites for reports of possible disruptions in London, Manchester, Birmingham, or Glasgow.
- Plan for alternative routes and means of transport.
- If caught in a protest area, try to leave quickly if it is safe to do so.
- Reconsider travel to company offices if possible.
- Ensure that you always carry personal identification documents or copies.
- Have emergency contact numbers saved on your phone. These should include the local authorities, medical facilities and any consular support. Ensure that mobile phones are charged in case of any loss in electricity.
- Consider relocating company vehicles away from areas likely to be targeted by protesters. Prioritise secure, indoor parking locations.
- Monitor the Solace Secure platform and trusted local media for updates relevant to the conflict.
Subscribe to free weekly intelligence

Executive Summary
Americas (AMER)
The introduction of a state of emergency in Peru is unlikely to curtail the influence of transnational organised crime groups operating in the country.
Protests are likely in Brazil as the Supreme Court considers charges against former president Jair Bolsonaro. Protests will likely escalate if the indictment phase decides to proceed with the case.
Europe, Middle East & Africa (EMEA)
The Kremlin will almost certainly manipulate the limited ceasefire proposal in Ukraine to pressure concessions, and long-range strikes against medical facilities and transport infrastructure will likely increase.
The largest-ever protest in Serbia is almost certainly reflective of widespread public disillusionment with government corruption and will likely continue until a change of government.
There is a realistic possibility that demonstrations provoked by a nightclub fire in North Macedonia will evolve into a wider protest movement against government corruption and a lack of accountability.
The arrest of leading Turkish political opposition figure Imamoglu is almost certain to drive large-scale unrest in Istanbul and other cities. Police will highly likely respond violently, with travellers also at risk of arrest.
The Israeli airstrikes on Gaza have almost certainly ended the ceasefire. The strikes will highly likely be followed by a major ground offensive. Civil unrest in Israel and abroad will almost certainly increase.
The Yemen-based Houthi movement will likely resume attacks against commercial shipping and highly likely continue attacks against US naval vessels and Israeli territory.
Asia-Pacific (APAC)
There is a realistic possibility that student-led demonstrations over controversial reforms in Indonesia that favour the military could evolve into a wider and potentially violent protest movement.
North, Central and South America
Peru: State of emergency declared in response to major crime wave
On 17 March, the Peruvian government declared a state of emergency to combat a recent crime wave, that will cover the capital Lima and the neighbouring province of Callao. The state of emergency was imposed after musician Paul Flores was killed on 16 March after unknown assailants ambushed his band’s tour bus, resulting in nationwide outrage.
The emergency measures will last for 30 days and were announced by President Dina Boluarte who also called for the reintroduction of the death penalty, with Peru currently only sanctioning the death penalty for cases of treason. Under the terms of the state of emergency, the authorities will be granted the right to deploy Peru’s Armed Forces to support the National Police and will have the power to detain people with few limitations, search homes without warrants and deny the freedom of assembly.
Solace Global Assessment:
The killing of Flores was likely the immediate trigger for the state of emergency but not the underlying justification. There has been a significant increase in killings in Peru, particularly in Lima, many of which have been linked to extortion rackets. This has involved multiple shooting attacks and the use of explosives targeting businesses that refuse to pay extortion demands.
These attacks frequently target establishments with high civilian footfall, such as bus operators and restaurants, as well as offices and private businesses in public areas. As a result, there has been a substantial rise in civilian casualties, further fuelling public anxiety and pressure on the government to take action. Recent police reporting indicates that there were at least 459 killings from 1 January to 16 March and almost 2000 individual cases of extortion in January alone.
Declaring states of emergency has become a routine strategy for the Peruvian government in response to surges in criminal activity or civil unrest. However, previous deployments of the military and the use of expanded powers have only resulted in temporary relief and failed to dismantle organised crime networks or prove to be an effective long-term deterrence.
The rise in crime has been attributed to multiple factors, many of which are unlikely to improve in the near future. Economic issues, political instability, corruption and weak law enforcement have all been significant contributors to the deteriorating security situation. However, the primary driver has likely been the growing influence of transnational organised crime groups, which view Peru as a crucial hub for their operations.
If crime rates continue to rise at a similar rate, there is a realistic possibility that the Peruvian government will be forced into implementing severe security measures, similar to those seen in El Salvador and Ecuador. This could involve mass arrests, prolonged military deployments, and the suspension of civil liberties in an attempt to quash the influence of organised crime groups.
Brazil: Supreme Court considers Bolsonaro trial
On 25 March, the Brazilian Supreme Court will convene to consider charges against former President Jair Bolsonaro for his role in attempting a coup after the 2022 election. Bolsonaro, who lost to Luiz Inácio Lula da Silva, refused to accept the result and left the country before Lula’s inauguration in January 2023. This led to Bolsonaro supporters storming government buildings in an attempted coup. Additional investigations claim to have uncovered plots that indicate Bolsonaro was attempting to assassinate opposition figures and if found guilty, he could face up to 40 years in prison.
Solace Global Assessment:
Despite the proceedings and allegations, Bolsonaro remains incredibly popular within Brazil. As recently as 16 March, thousands of Bolsonaro supports gathered on Rio de Janeiro’s Copacabana Beach to show support for him and to demand a pardon for supporters of the former president, who were accused of ransacking government buildings days after the inauguration of da Silva.
If the trial goes ahead, thousands of Bolsonaro supporters will likely protest in the vicinity of the courthouse in Brasilia and other protests will likely be organised outside major government buildings in other Brazilian cities. Protests will likely escalate if the indictment phase decides to proceed with the charges. If the case moves ahead to a full trial, it may last months or even years.
A full trial is likely to further polarise Brazilian society and deepen divisions between Bolsonaro supporters and the incumbent government, likely leading to episodic and often violent unrest ahead of the 2026 presidential election. In the long term, if Bolsonaro is convicted, widespread demonstrations across Brazil are likely to take place.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
Violent protests in Dominica over series of controversial reforms
On 19 March, protests in Dominica escalated into violence as police clashed with demonstrators opposing three electoral reform bills, the Electoral Commission Bill 2024, the House of Assembly Elections Bill 2024, and the Registration of Electors Bill 2024. Clashes took place when protestors attempted to bypass barriers near Parliament in the capital Roseau, which led to the police firing tear gas and rubber bullets at the protestors. Further protests are likely as the opposition, which has condemned the electoral reform bills, continues to encourage demonstrations.
Nationwide protests in Guatemala over mandatory car insurance law
Nationwide protests erupted on 17 March in Guatemala after the Central American country decided to introduce a new law mandating compulsory car insurance. Protestors blocked several major roads throughout the country and clashed with the police, leading to the deployment of riot police and the use of tear gas.
Protests ended on 19 March, after a decree from President Bernado Arévalo repealed the mandate. However, the government has stated that road traffic accidents are the main cause of death in the country and that things “must change”, potentially signalling the introduction of alternative measures to reduce deaths; however, future attempts to introduce similar legislation are likely to provoke further resistance that may evolve into major demonstrations.
US expels South African ambassador
Ebrahim Rasool was declared persona non grata and has been ordered to leave the country by 21 March. The announcement was posted by US Secretary of State Marco Rubio on social media on 14 March, where he accused Rasool of being a “race-baiting politician”.
The development follows an executive order by the White House in early February, which froze assistance funding to South Africa. The current US administration has accused the South African government of discriminating against the country’s white minority.
There is a realistic possibility that the announcement will result in protests and other unrest, including possible vandalism of US-linked assets, in South Africa. Likewise, the US has a large South African diaspora of around 140,000, particularly concentrated in California and Florida, which could drive protests if relations between the two countries continue to worsen.
Security, Armed Conflict and Terror
Canada to boost military presence in the Arctic
Prime Minister Mark Carney has announced plans to strengthen Canada’s military presence in the Arctic, committing CAD 420 million to expand training and deployment for year-round operations. Canada will also partner with Australia to build an early-warning radar system at a cost of CAD 6 billion. The decision likely follows increased geopolitical interest in the Arctic, with China and Russia increasing activity in the region and US President Trump criticising Canada’s defence spending and signalling his interest in acquiring Greenland. However, the investment is unlikely to enable Canada to effectively monitor the vast region. Most importantly, the radar system will be deployed under the North American Aerospace Defense Command (NORAD) and will improve the US’ early warning of potential airborne threats, a move that has likely been engineered to appease the Trump administration.
MS-13 leader arrested in Mexico and extradited to US
On 17 March, Mexican authorities arrested Francisco Javier Román-Bardales near Veracruz, an alleged Mara Salvatrucha (MS-13) gang leader and one of the FBI’s Ten Most Wanted Fugitives. Bardales was then extradited to the US, where he faces charges related to violent crime, drug distribution and extortion in the Eastern District of New York. The arrest and extradition follow the designation of MS-13 as a foreign terrorist organisation (FTO) by the Trump administration and is likely further proof of the Mexican government responding to the threat of US tariffs by intensifying its operations against organised crime. However, MS-13 has evolved to become a highly decentralised transnational organised crime group, and the arrest is unlikely to disrupt the gang’s operations.
Four Doctors Without Borders vehicles came under fire in Haiti
On 15 March, four Doctors Without Borders vehicles came under fire as they attempted to evacuate staff from the Turgeau Emergency Center in Port-au-Prince. The incident resulted in some minor injuries but no deaths. The incident reportedly occurred despite prior coordination with the authorities. As a result of the incident, the aid group has suspended operations at the hospital for the second time in four months. Gangs control approximately 85 per cent of Port-au-Prince and will highly likely continue to conduct attacks against aid workers, particularly those affiliated with international NGOs, and security forces as they attempt to consolidate and expand their control and dissuade foreign intervention.
Environment, Health and Miscellaneous
Protracted power outages affect millions in Cuba
The outages, which began on 14 March affected the entire island for more than 36 hours, with power only gradually returning to Havana and the east on 16 March. The blackout was the fourth in six months and was reportedly caused by a substation failure. It not only affected electricity but also phone lines and water services. Cuba is undergoing a severe economic crisis, worsened by the US blockade and the protracted effect of the COVID-19 pandemic, which significantly damaged its tourism economy. Power outages, as well as austerity measures implemented by the government, have been drivers of protests in recent months. While demonstrations are rare in Cuba, further large-scale outages are likely to increase resentment towards the government and may increase the long-term risk of civil unrest.
Plane crash off Roatan in Honduras’ Bay Islands
On 18 March, a Lanhsa Airlines plane crashed into the sea off Roatán in Honduras’ Bay Islands, killing 12 people, including the musician Aurelio Martínez Suazo. Five survivors have been reported, and one person remains missing. The incident was caused by the plane skidding off the runway at Juan Manuel Gálvez International Airport (RTB). While rescue efforts are ongoing, adverse weather conditions have complicated search and rescue efforts. An investigation into the crash has been launched by authorities.
Europe, Middle East & Africa
Serbia: Anti-corruption protest leads to largest-ever demonstration
On 15 March, an estimated 300,000 to 500,000 protesters gathered in the Serbian capital of Belgrade. The protests marked the largest gathering in the nation’s history and the climax of anti-corruption protests that began in November 2024, after 15 people were killed in Novi Sad after the collapse of a railway station roof.
On 19 March, Serbia’s parliament formally accepted the resignation of Prime Minister Milos Vucevic, triggering a 30-day deadline for the formation of a new government or the calling of a snap election. Vucevic, a major ally of President Aleksandar Vučić and head of the ruling Serbian Progressive Party (SNS), resigned on 28 January but had delayed his resignation until the formal parliamentary acceptance.
Solace Global Assessment:
The political situation has become increasingly volatile and polarised, adding extreme pressure on President Vučić to resign. Vučić is likely hoping that the formal resignation of Prime Minister Vucevic will help quell the protests. However, during the recent protests, there was potential video evidence of a “sonic cannon” being used to disperse protestors, rumours that the government enlisted the help of football hooligans in counter-protests and a purported government supporter drove a vehicle into the protestors. These developments not only underline how dangerous the protests are becoming but have almost certainly inflamed tensions and increased mistrust in the government.
The continuation of the protests and their intensification makes it increasingly likely that the only measure that will quell the unrest is the resignation of President Vučić, who has governed Serbia for 14 years and has been widely implicated in both corruption and mismanagement. However, it is unlikely that Vučić will step down soon, especially as the SNS still command a lot of support in Serbia.
Alternatively, Vučić will likely exploit the formal resignation of Vucevic to delay the political crisis further by attempting to form a new government. Additionally, by promising snap elections as early as June, Vučić is likely aiming to buy time and maintain his grip on power, all while avoiding immediate concessions to the growing public unrest.
This strategy is likely to prolong the current cycle of protests in Serbia, with major protests likely being organised in response to any political development that favours Vučić or the SNS. If elections fail to materialise in June, or if they go ahead and the SNS maintains power, it is likely that widespread and potentially violent unrest will erupt throughout Serbia.
North Macedonia: 59 killed in worst fire in country’s history
On 16 March, at least 59 people aged between 14 and 24 were killed in the North Macedonian city of Kočani after a fire started at a local nightclub. According to the country’s interior minister, the cause of the fire was pyrotechnics. The majority of those killed died as a result of a stampede caused by people trying to exit the club.
Initial investigations suggest that the club was operating without a licence, had only two fire extinguishers, no fire alarm or sprinkler system, was over capacity and had only one effective exit as the back door was locked during the event.
The authorities have now closed multiple nightclubs and entertainment venues after inspections identified many operating without licences and in violation of numerous safety regulations. 15 individuals have also been detained for questioning on suspicion of bribery and corruption.
Solace Global Assessment:
Protests and vigils have already taken place in response to the nightclub fire, which is being described as the worst fire in North Macedonian history. Initially, these protests have been led by students, with minor clashes between demonstrators and the police observed in Kočani, whereas mainly peaceful vigils have been held in the capital, Skopje.
The government has likely initiated investigations and made arrests in an attempt to control the situation, and has declared a seven-day mourning period. However, as investigations continue to expose safety violations across the country, many likely linked to bribery or corruption, it is likely that these protests will escalate.
The initial student-led protests could evolve into a wider movement, similar to the anti-corruption demonstrations seen in neighbouring Serbia, where public frustration at government malpractice and corruption has led to mass protests. Once the mourning period concludes, public anger over both the fire and the broader systemic issues will likely fuel larger-scale protests, which may result in widespread disruption and violent interactions with the police.
Ukraine: Limited ceasefire marked by confusion and alleged violations
On 18 March, US President Donald Trump and Russian President Vladimir Putin spoke via a telephone call for over two hours, during which Trump attempted to persuade Putin of a full and immediate 30-day ceasefire in the Ukraine war. This was rejected by Putin, who reportedly set a list of preconditions for the US proposal, primarily the cessation of US military aid and intelligence sharing with Ukraine.
Trump subsequently proposed a limited 30-day ceasefire on all “energy and infrastructure”, which Putin agreed to. On 19 March, Trump spoke with Ukrainian President Volodymyr Zelensky and Kyiv agreed to a limited ceasefire applying to all energy, infrastructure and civilian targets.
The Russian Ministry of Defence (MoD) claims that following the Trump-Putin call, they executed an order to halt long-range strikes against Ukrainian “energy infrastructure facilities” and intercepted their airborne one-way attack uncrewed aerial vehicles (OWA-UAVs), which has been disputed by Zelensky. In contrast, the Russian MoD claims that Ukrainian OWA-UAVs hit an oil transshipment facility in Krasnodar Krai and Ukraine is therefore violating the limited ceasefire.
Waves of Russian long-range strikes against civilian targets continued, including strikes against railway infrastructure in the Dnipropetrovsk Oblast. Ukrainian long-range strikes also continued, including a successful OWA-UAV swarm attack against the Engels-2 strategic bomber airbase in Saratov Oblast, Russia. Early on 21 March, the Sudzha gas pumping station in Kursk Oblast was attacked. The Ukrainian General Staff claimed Russian forces shelled the energy infrastructure facility themselves, while the Russian military claimed that Ukraine was responsible and had therefore violated the limited ceasefire.
Solace Global Assessment:
The days following the agreed limited 30-day ceasefire have been marked by confusion, contradictory statements and several accusations of violations. This is highly likely intended by Moscow, who are highly likely deploying reflexive control to exploit the ceasefire proposal, manipulate the narrative and gain concessions to further its goals without making any concessions of their own. By demanding preconditions, Putin has de facto rejected the Trump proposal for a full and immediate ceasefire that can act as a precursor to peace negotiations. It is almost certain that the Kremlin will attempt to manipulate as far as possible a narrative of the limited ceasefire to influence the Trump administration into renewing the cessation of US military aid and intelligence sharing.
The Trump administration is likely incentivised to end attacks on critical national infrastructure (CNI) in both Ukraine and Russia, with global oil prices already having slightly decreased following the limited 30-day ceasefire announcement. Ukrainian strikes against Russian energy facilities have intensified in the past months, likely intended to both demonstrate strength to the Trump administration and capability to continue engaging Russia in a longer-term war with operations against strategic targets.
Although Russian forces have considerably more vast long-range strike capabilities than Ukrainian forces, Kyiv has leveraged its rapidly developing domestic advanced drone manufacturing capabilities to asymmetrically compete in the aerial domain. The Kremlin does therefore likely have a notable incentive for a ceasefire against CNI strikes. However, Moscow is also almost certainly incentivised to continue the depletion of Ukrainian interceptor munition stockpiles and will highly likely continue layered large-scale long-range strikes against urban centres in Ukraine. A reduction in Russian attacks targeting energy infrastructure will likely result in an increase in the targeting of other high-value targets (HVTs), including medical facilities, transportation infrastructure and potentially indiscriminate attacks on major towns and cities.
Turkey: Opposition leader arrested
On the morning of 19 March, the Mayor of Istanbul and head of the opposition Republican People’s Party (CHP), Ekrem Imamoglu, was arrested on suspicion of being the head of a “criminal organisation” as well as aiding the banned Kurdistan Workers’ Party (PKK). The day before, the University of Istanbul had annulled Imamoglu’s degree, citing irregularities with his transfer from another university during his studies.
Authorities also reported that “100” other suspects had been arrested alongside Imamoglu, including prominent journalists. In addition to restrictions on protests in Istanbul, confirmed reports indicate the imposition of widespread internet restrictions, limiting access to platforms including X, YouTube, Instagram, and TikTok. Significant protests have been recorded following the arrest in Istanbul, Izmir, and Ankara, as well as other urban centres. Authorities have responded violently, with multiple arrests carried out by the police. At least 37 individuals were arrested for their posts on social media by 20 March.
Solace Global Assessment:
Imamoglu’s arrest is almost certainly politically motivated. First, the timing of the arrest is notable. CHP was scheduled to hold its candidate selection process on 23 March, and Imamoglu was largely expected to emerge as the party’s official candidate at the event before being stripped of his university degree (as only graduates can become president in Turkey) and arrested.
Second, the rapid and coordinated approach by Turkey’s police and by pro-Erdogan political figures highly likely illustrates how the government had carried out prior assessments of the arrest’s impact. The almost immediate identification and arrest of 37 individuals for social media posts almost certainly demonstrates this high level of preparation.
Third, the profile of those arrested, which not only included Imamoglu and his associates but also prominent journalists and online personalities, likely indicates an aim to cripple the opposition beyond the CHP leadership.
It is likely that Ankara’s decision to arrest Imamoglu reflects an improving outlook for President Erdogan. The removal of Assad in Syria has been an important victory for Turkey and made Ankara the key link in communications between the new regime in Damascus and Brussels. Moreover, the recent PKK calls for a ceasefire have diminished, at least for the moment, the political threat from the Kurdish militants.
The arrests will likely be followed by political moves to secure Erdogan’s next term. While Erdogan technically cannot run for president again, his allies have long aimed to pass a constitutional amendment to change this or have raised the possibility of calling early elections to bypass the term limit. There is a realistic possibility that the arrests are meant to proactively damage the opposition, making it unable to mount a coherent challenge to these further reform proposals once they are more clearly formulated.
It is highly likely that protests will continue and intensify on 21-23 March. Police are likely to respond extremely harshly, focusing on protest hotspots like Istanbul University and Taksim Square. There is a realistic possibility of short-term internet limitations in the coming weeks. Turkish police have at times also targeted foreigners, and there is a realistic possibility of a greater threat of arrest and violence to travellers. Finally, if the disorders persist there is a realistic possibility that transnational terrorist groups like the Islamic State (IS) will seek to capitalise on them by staging attacks. In this sense, it is notable that IS carried out a series of deadly attacks in Turkey in 2017, just months after the July 2016 failed coup.
Israel & Gaza: Ceasefire collapses following largest Israeli strike in months
On 18 March, the ceasefire between Israel and the various Palestinian militant groups in the Gaza Strip collapsed, after Tel Aviv launched a wave of surprise airstrikes.The strikes killed more than 400 people, with Hamas-linked channels stating that most of the victims were civilians. Further airstrikes have continued on 19, 20 and 21 March, and have killed an additional 100 people, making the latest wave of strikes the deadliest since late 2023.
The strikes killed Mahmoud Abu Watfa, the head of Hamas’ interior ministry. Israeli Defence Forces (IDF) units have also begun ground operations in Gaza, seeking to expand the Netzarim corridor in the centre of the Gaza Strip. The IDF’s 252nd Division has advanced down from Gaza’s northern border towards Beit Lahiya.
Israeli officials have issued evacuation orders for Gaza’s border areas, and have declared the Salah al-Din road, the main roadway connecting south and central Gaza, closed. Hamas reportedly fired at least three rockets into Israel, but these were either intercepted or landed in empty areas near the Gazan border. Israeli Defence Minister Israel Katz has called on Hamas to release all the remaining hostages, threatening to annex parts of the Gaza Strip in case of non-compliance.
The strikes in Gaza coincided with important political developments in Israel. On 19 March, Itamar Ben Gvir, the head of the far-right Otzma Yehudit party, returned to his cabinet position. On 20 March, the Israeli Knesset passed the first budget framework vote. Moreover, the Knesset also voted in favour of Prime Minister Netanyahu’s call to remove Ronen Bar, the head of the Israeli Security Agency (ISA), from his post. Protests were recorded in West Jerusalem, Tel Aviv, and other Israeli urban centres.
Solace Global Assessment:
The latest Israeli strikes have almost certainly ended the ceasefire process. The stated Israeli goal for resuming the war is that the killing of senior Hamas figures will force the group to release the remaining hostages, and possibly dissolve as a political and military entity. It is however more likely that it reflects both the Netanyahu administration’s need to appease the hawkish figures in its coalition to survive the budget vote and remove the head of ISA, who is an important political opponent and is in charge of investigating some of Netanyahu’s closest aides for alleged national security breaches.
It is highly likely that the strikes will be followed by a ground operation targeting Gaza’s urban centres. Current advances suggest that Israeli forces will focus on the area north of the Netzarim corridor, at least in the short term. Hamas and other groups like Palestinian Islamic Jihad (PIJ) have almost certainly capitalised on the ceasefire to replenish some of their ranks and re-infiltrate previously cleared areas.
However, with the flow of weapons from Egypt largely interrupted by the Israeli presence in the Philadelphi Corridor, it is unlikely that these groups have been able to significantly replenish their stocks of rockets or missiles. The firing of only three rockets in response to the Israeli strikes likely reflects these limitations.
IDF advances in Gaza, airstrikes, and engagements with Palestinian militias are almost certain to result in a significant short-term degradation of Gaza’s already severe humanitarian situation.
The restart of the war is almost certain to result in civil unrest and political violence abroad. In Israel, there is a high likelihood of protests in the 21-23 March period and beyond. Moreover, both organised and lone-wolf terror attacks are likely to continue, especially in Tel Aviv, Haifa and Jerusalem. Protests are also almost certain to occur in large European and North American cities. Likewise, there is a realistic possibility that the renewed hostilities will drive lone-wolf attacks in the West, particularly around the major Christian and Jewish holidays in April.
Yemen & The Red Sea: Conflict between Yemen-based Houthis with US and Israel resurges
Over several consecutive days starting 15 March, United States Central Command (US CENTCOM) forces conducted long-range strikes against targets across Houthi-controlled Yemen. Strikes targeted Houthi assets in the cities of Sanaa and Sa’dah, and in the provinces of al-Bayda, Hajjah and Dhamar. Targets have included radar systems, air defence systems, uncrewed aerial vehicle (UAV) launch sites, and command and control (C2) centres assessed to be housing senior Houthi leadership.
Washington claims that multiple Houthi “leaders” were killed, and funerals were held for 16 Houthi officers including a colonel, two majors and two captains. The Houthi-controlled Health Ministry stated that at least 53 people were killed and 98 wounded in the strikes so far.
In response, the Houthis conducted layered attacks against the USS HARRY S. TRUMAN carrier strike group (CSG) over five consecutive days, using anti-ship ballistic missiles (ASBMs), anti-ship cruise missiles (ASCMs), and one-way attack UAVs (OWA-UAVs).
Following last week’s ultimatum issued by the Houthis that strikes against Israel and Israeli-linked commercial vessels would resume if the flow of aid did not resume in Gaza, the ceasefire has de facto collapsed with the renewal of significant Israel Defense Forces (IDF) operations.
The Houthis subsequently launched claimed “Palestine 2” hypersonic ballistic missiles against Israel on 18 and 20 March, targeting Nevatim air base in southern Israel and Tel Aviv’s Ben Gurion Internation Airport (TLV) respectively. Both missile attacks were reportedly intercepted outside Israeli airspace with the Arrow missile defence system.
Solace Global Assessment:
It is likely that as the Trump administration escalates a military campaign against the Houthi movement and the IDF resumes large-scale operations in Gaza, the Houthis will resume attacks against commercial shipping transiting the Red Sea and highly likely continue attacks against US naval vessels and Israeli territory.
The 19 January 2025 Gaza ceasefire led to Houthis announcing a halt in the campaign against all but Israeli-flagged vessels and vessels wholly owned by Israeli individuals or entities. However, the Houthis had not conducted an attack against commercial shipping since 19 December 2024, likely conditioned by the degradation of Houthi launch capabilities by US-led coalition efforts and the depletion of Houthi weapon stockpiles.
The Houthis have likely used the months since to replenish stockpiles and construct new launch sites. Advanced Houthi weapon systems are almost certainly heavily reliant on Iranian supply, although it is likely that systems such as uncrewed surface vessels (USVs), whether they be improvised skiff designs or the purpose-built Toofan-series, are domestically assembled in workshops using Iranian-derived components. It is likely that Tehran has devoted considerable resources to resupplying the Houthis, who have gained even greater strategic importance for Iran following the severe degradation of Lebanon’s Hezbollah and the overthrow of the Assad regime in Syria.
Tehran, however, almost certainly exercises far less control and influence over the Houthis than it does other Iranian-backed proxy forces such as the Iraqi Popular Mobilisation Forces (PMFs) or Lebanese Hezbollah. Iranian officials have reportedly attempted to pressure the Houthis to reduce tensions with the US and Israel, with Houthi leadership rejecting these requests.
US President Donald Trump has threatened Iran with “dire” consequences if Houthi attacks continue. It is highly likely that the Iranian regime is in its most vulnerable geostrategic position in decades, and Tehran is highly likely inclined to avoid escalation.
However, the Houthis likely rely on the domestic support afforded by external conflict despite their failures to provide effective governance, with large-scale demonstrations against the US and Israel in support of the Houthis occurring in both Sanaa and Sa’dah this past week.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Pro-Palestine protests are highly likely to occur across Europe following latest Israeli strikes
Pro-Palestine protests are likely to be organised in major European cities like Paris, London, Amsterdam, Berlin, and Barcelona on the weekend of 21-23 March, following smaller gatherings throughout the week. The unrest would follow the 17-18 strikes on the Gaza Strip by Israeli forces, which have been the deadliest in more than a year and have collapsed the ceasefire (see main piece in EMEA section), as well as broader developments such as the arrest of a US-based pro-Palestine activist. These protests could become violent with little warning, and result in localised travel and services disruptions.
Protests triggered after Hungary bans pride parade
The Hungarian parliament has fast-tracked legislation that has led to the ban on the annual Pride parade, a move that has triggered protests in central Budapest and resulted in the ignition of smoke bombs within the parliament building. The law was proposed by Prime Minister Viktor Orban’s Fidesz party on 17 March and signed into effect by the Hungarian president on 19 March, under the justification that the annual parade violates the country’s strict child protection laws. The new law will allow authorities to use facial recognition technology to identify and fine participants. However, it is likely that thousands will still attempt to hold a parade on 28 June, to mark the 30th anniversary of the Budapest Pride March, which will likely provoke a violent crackdown from the authorities.
Greek government workers set to strike on 21 March
Union workers in Greece have called for a 24-hour strike to commence on 21 March to demand improved working conditions and long-term contracts for employees for those working in social services. The rally will take place in central Athens outside of government buildings and is likely to result in transport disruptions. Police presence is expected to be high after recent protests on the two-year anniversary of the Tempi train crash that provoked multiple violent interactions with the police, leading to multiple arrests and injuries.
Alliance of Sahel States (AES) juntas leave Francophonie (OIF)
Burkina Faso, Mali, and Niger officials announced the decision on 18 March. The OIF is a cultural and political organisation that promotes the French language and includes numerous French colonies. OIF had suspended the three juntas following their coups. The move is almost certainly a further political signal of the decoupling of the AES members from the West.
Security, Armed Conflict and Terror
Estonia, Latvia, Lithuania and Poland to withdraw from Ottawa Convention.
The three Baltic nations and Poland have announced their intent to withdraw from the Ottawa Convention, an international treaty that bans anti-personnel mines, citing security concerns over a resurgent Russian military threat. The decision is likely to be emulated by other nations, such as Finland, and is also likely a precursor for a broader shift in regional defence policies that will result in the acquisition of new defence capabilities. The decision follows Poland’s recent statement that it will build a half-million-man army and is looking at staging US nuclear weapons within its borders to serve as a deterrent to Moscow.
Clashes in Syria at Lebanon border and in Kurdish-controlled northeast
Armed clashes erupted at the Lebanon-Syria border on 16 March following accusations by the Syrian interim government that Hezbollah had kidnapped and killed three Syrian soldiers on Lebanese soil. Syrian forces shelled Lebanese border territory, reportedly killing seven Lebanese civilians and injuring 57 others, and the Lebanese Armed Forces (LAF) deployed to counter the threat.
A ceasefire agreement was reached on 18 March between Beirut and Damascus, with stipulations to enhance coordination and cooperation. Due to Hezbollah’s support for the overthrown Assad regime, it is highly likely that tensions will remain high at the border, with the Beqaa Valley being a Hezbollah stronghold.
Clashes also continued in northeast Syria, controlled by the Kurdish-led Syrian Democratic Forces (SDF), between the SDF and Turkey-backed Syrian National Army (SNA). The SDF allege that Turkish-led forces committed a massacre in the village of Barkh Botan overnight on 16 March, and carried out a series of retaliatory strikes.
Burkina Faso forces accused of massacre of ethnic minority groups
On 14 March, Human Rights Watch reported on a massacre of dozens of people, mostly women and children, in the western town of Solenzo, which occurred on 10-11 March. According to the humanitarian group, the victims of the massacre were Fulani/Peul people, who are often blamed as supporters of Islamist groups like the Islamic State (IS) or Jama’a Nusrat ul-Islam wa al-Muslimin (JNIM). Government officials called the report “disinformation” and stated they had engaged fighters, although footage from the town may disproves this.
On 18 March, Burkinabe opposition channels reported that a member of an anti-government civil society group who had reported on the massacres was “kidnapped” in Saaba, near Ouagadogou. Burkinabe forces are almost certainly unable to deal with the growing Islamist insurgency, and their attacks on Fulani communities likely represent retaliatory violence on groups that Ouagadogou considers to be vital to IS and JNIM’s bases. It is highly likely that these attacks play in the hands of the two groups.
JNIM does not exploit ethnic divisions in the Sahel, and they are almost certain to capitalise on government brutality to increase their recruitment and propaganda operations. JNIM, for instance, pledged to send “humanitarian aid” to the survivors of the massacre in Solenzo, and swore to carry out revenge attacks on the government.
State of emergency declared in Nigeria’s Rivers State
On 18 March, Nigerian President Bola Tinubu declared a state of emergency in Rivers State, suspending the governor, deputy, and lawmakers, citing their failure to curb recent pipeline vandalism by militants. The move allows the federal government to assume direct control of the state government, with a retired vice admiral appointed as caretaker for an initial six-month period.
Pipelines and other infrastructure are often targeted by militants in the oil-rich Niger Delta region, disrupting both the production and shipment of oil, Nigeria’s most important export. While the state of emergency may enable the federal government to stabilise the region and curb attacks, there is a realistic possibility that the move will be interpreted as a federal overreach, which would likely deepen tensions and potentially provoke civil unrest.
Sudanese government forces recapture presidential palace
On 21 March, the Sudanese Armed Forces (SAF) announced that they recaptured the presidential palace in Khartoum from the Rapid Support Forces (RSF). This will almost certainly be perceived as a major symbolic victory in the battle for the capital and central Sudan.
There have been mass reports of the RSF indiscriminately killing civilians in Khartoum, a trend that is likely to continue as the paramilitary forces conduct a fighting withdrawal from the capital, targeting anyone it deems to be in support of the SAF. Moreover, the RSF still maintains control over most of the Darfur region and the gradual loss of the capital may provoke more war crimes targeting government supporters and ethnic groups in the region in retaliatory attacks.
Al-Shabab target presidential convoy in Somali capital
On 18 March, a roadside improvised explosive device (IED) was detonated near Somalia’s presidential palace in an attack targeting President Hassan Sheikh Mohamud’s convoy. The president was unharmed, and the attack was quickly claimed by the al-Qeada-aligned Islamist group, al-Shabab. The attack occurred just after the president’s convoy left the palace en route to the airport, ahead of his planned visit to Middle Shabelle to oversee military operations against the group.
On 19 March, al-Shabab militants fired mortars into the Halane compound near Aden Adde International Airport in Mogadishu, one of the most heavily secured zones in Somalia that houses the United Nations, African Union officials, and multiple foreign embassies. The twin attacks clearly demonstrate al-Shabab’s ability to conduct attacks in the most secure parts of the country and have likely been ordered in response to government attempts to launch an offensive against the group in other parts of the country.
M23 rebels capture major town in eastern DRC and reject ceasefire talks
On 20 March, the M23 rebel group announced that they had captured the strategic town of Walikale in the east of the Democratic Republic of Congo (DRC), which lies on both the N3 and R29 main supply routes, as well as the Lowa River. M23 have rejected government calls for a ceasefire and have reiterated their motivations to march towards the capital Kinshasha. The fall of Walikale now puts the rebels within 400km of Kisangani, the DRC’s fourth largest city and major port and the farthest navigable point upstream of the capital Kinshasa on the River Congo. Its fall may have also dislocated government forces from major supply routes and restricted their ability to mutually reinforce other units, a development that is likely to place increased pressure on Kinshasa to push for ceasefire talks.
Environment, Health and Miscellaneous
Fire at electrical substation shuts down UK’s and Europe’s busiest airport
On 21 March, Heathrow Airport was closed due to a massive fire at a nearby electrical substation, causing a significant power outage and disrupting flight schedules globally. The fire, which also destroyed the backup power system, led to flight diversions, cancellations, and widespread chaos, with over 120 flights rerouted to other airports. As a result, at least 1,300 flights were affected, and thousands of passengers were stranded or redirected, impacting global flight networks. Assessments indicate that the airport will remain closed until midnight, and experts warn of continued disruptions and significant delays as airlines scramble to reconfigure schedules.
Severe floods in Tuscany cause EUR 100 million in damages
Flooding was reported in multiple towns in the central Italian region starting on 14 March, following heavy rains which, in some towns, exceeded a volume of more than 250mm in 72 hours. Florence, Pisa, Prato, and Livorno have been affected by the floods, and severe travel disruptions were recorded in the region between 14 and 17 March.
Parts of the region that were flooded had been also severely affected by the 2023 floods. The neighbouring Emilia Romagna region, which had three severe floods in the last two years, was less affected. Central-west Italy, from northern Lazio to the Po Valley, has a high risk of flooding. This is likely in part due to changing weather patterns, which can, as in the case of past floods in Emilia Romagna, “trap” weather systems under the Alps, resulting in long periods of heavy rain.
5.5 magnitude earthquake strikes Ethiopia close to capital
A moderately strong earthquake registering 5.5 magnitude on the Richter scale struck Ethiopia on 16 March, with the epicentre less than 200km from Addis Ababa, in the Afar region. Minor tremors were felt in the capital and in several other towns.
The quake is part of the ongoing seismo-volcanic crisis that is affecting the Dofen volcano region since December 2024, which have resulted in thousands of evacuations. Concerns have been raised over the structural integrity of the Kesem Dam, which is only designed to withstand earthquakes up to 5.6 on the Richter scale.
Experts have warned that the ongoing series of quakes could result in a structural failure, resulting in catastrophic flooding that is likely to affect hundreds of thousands of people. Alerts have also been issued warning of aftershocks, that may occur weeks after the initial quake and are sometimes equal or larger in magnitude.
Large acid spill from Chinese-operated mine “kills” Zambian river
During this reporting period, local Zambian and international sources published reports on a large spill of acid waste into the Kafue River, which occurred in February. The spill reportedly started after a dam, which contained massive quantities of acid waste originating from a copper mine in Kitwe, in the country’s north, broke. Signs of contamination were recorded up to 100 kilometres downstream from the leak.
Zambia’s economy has historically been heavily reliant on copper exports from its northern Copper Belt, and, in recent years, China has increasingly played a vital role in controlling national extraction operations, including the Sino-Metals Leach Zambia mine, where the leak started.
The Kafue runs through Zambia, and around 60 per cent of the country’s population lives on or near its banks. The river also supplies drinking water to around 5 million people, water for irrigation and industry, and is a key source of food.
Asia–Pacific
Indonesia: Protests over new law that increases military involvement in government
On 20 March, the Indonesian parliament ratified changes to its military law that will allocate more civilian posts within the government for military officers. The proposed changes would expand the number of government agencies where military officers can serve from 10 to 16, including the Supreme Court, the national disaster agency, and the Attorney General’s Office. The changes have been condemned by many activists and civil society groups within Indonesia, citing fears that the world’s third largest democracy is slowly returning to its “New Order” era under President Suharto, which was effectively a military dictatorship characterised by human rights abuses, repression and the mass killing of government opponents.
The legislative changes have provoked student-led protests outside of the Indonesian parliament. The government has defended the changes, stating that geopolitical and technological changes have warranted the amendments.
Solace Global Assessment:
The changes have almost certainly provoked fears that incumbent President Prabowo Subianto, an ex-special forces general and former Suharto son-in-law, is attempting to reform the Indonesian government in favour of the military and to consolidate his power. The revisions will also enable the military to assume posts within the government without first retiring or resigning from the military. This will likely ensure that the armed forces maintain direct influence over civilian governance, increase its role in policy making and weaken Indonesia’s democratic institutions. Many will also likely see this as the nascent steps towards an authoritarian role under Subianto, especially given his past military ties and connections to Suharto, who is widely considered a dictator.
Attempts to reverse a constitutional court ruling in August 2024 resulted in tens of thousands of protestors amassing in Jakarta and proposed economic reforms in February 2025 triggered student-led protests across the archipelagic nation, including in Jakarta, Medan, Makassar and Yogyakarta. These protests are likely indicative of a broader disillusionment with the Subianto administration, whose militarisation of government and authoritarian-style reforms are increasingly viewed as a threat to democratic freedoms.
The student-led protests that have emerged in response to the current amendments are likely reflective of growing discontent with the Subianto administration and there is a realistic possibility that as the protests gain traction, they will attract a wider segment of society, including labour unions, civil society groups, political activists, etc. and could spread to other parts of the country. If major protests are organised, there is a high likelihood of violent clashes, with the potential deployment of riot police, mass arrests, and the use of tear gas to disperse crowds. These measures could further escalate tensions, leading to widespread disruption and potentially more intense confrontations between demonstrators and security forces.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Second hearing to start against impeached South Korean president
On March 24, the second hearing in the criminal case against impeached South Korean President Yoon Suk Yeol will take place over his short-lived martial law declaration. Yoon, the first sitting president to be indicted for criminal charges, faces allegations of insurrection, a charge for which a president has no immunity. The case has divided South Korea, resulting in multiple protests both in support and against Yoon, with major developments in the case likely to spark further demonstrations. The police are expected to deploy 14,000 riot police officers and anti-drone equipment and will lock down the areas near the Constitutional Court during the hearing.
Security, Armed Conflict and Terror
Baloch separatists continue to target Pakistani government forces
On 16 March the Baloch Liberation Army (BLA) launched a suicide attack in Noshki, Balochistan, targeting a Pakistani Army convoy. A vehicle-borne improvised explosive device (VBIED) destroyed a military bus, followed by a coordinated assault by the BLA’s Fateh Squad, resulting in claims that 90 Pakistani soldiers were killed according to the BLA, while the government reported a lower death toll of five.
The attack likely marks a shift in the BLA’s tactics, combining suicide bombings with direct engagement, and is another example of the BLA moving away from sporadic violence to well-coordinated military engagements, often targeting government forces when in transit. This latest attack follows the hijacking of the Jaffar Express, further showcasing the BLA’s growing operational sophistication and orchestration of attacks likely designed to increase publicity and bolster recruitment.
Communal clashes in Nagpur, India
On 17 March, communal tensions escalated into violent protests in the Mahal area of Nagpur city with demonstrators setting vehicles alight and throwing stones. The events escalated when two Hindu groups, Vishwa Hindu Parishad and Bajrang Dal, burned an effigy of Mughal Emperor Aurangzeb, a devout Muslim accused of razing Hindu temples, calling for his tomb to be removed. Rumours that a copy of the Quran had been desecrated sparked approximately 250 Muslims to start a counter-demonstration which spiralled into clashes. At least 50 people were detained, 33 police officers were injured, and 32 vehicles set on fire.
In response to the communal violence, authorities imposed a curfew in parts of Maharashtra. Tensions have been high in recent weeks due to the release of the Bollywood film “Chhaava”, which depicts the life of the Maratha ruler Chhatrapati Sambhaji Maharaj, who resisted Aurangzeb but was captured, tortured, and executed. The depiction of Aurangzeb as a tyrant has reinforced an anti-Muslim narrative among the Hindu community. Further clashes are likely.
Environment, Health and Miscellaneous
Severe rainfall leads to mass evacuations and disruptions in southern Malaysia
Heavy rainfall across the Malay Peninsula has caused widespread flooding, particularly in Johor State, where approximately 15,000 people have been evacuated and relocated to temporary shelters. Major disruption has occurred, with key roads submerged in areas such as Tebrau, Pandan, Larkin, and Skudai. The disruption has resulted in major congestion at the Woodlands and Tuas checkpoints between Malaysia and Singapore, forcing the Singaporean authorities to issue an alert suggesting to avoid all non-essential cross-border travel.
The floods have forced the closure of schools and businesses, and dangerously high river levels have been reported. Forecasted continued heavy rainfall over the next 72 hours will likely result in further flooding, evacuations, landslides, and major transport disruptions. Less severe flooding has also been reported in the Malaysian provinces of Sabah and Sarawak on the island of Borneo.
Bushfire warnings following extreme heat in Australia’s east coast
New South Wales locations, including Sydney, recorded temperatures of above 39 degrees Celsius starting on 15 March. Similarly high temperatures were also recorded in Victoria state, where at least one house was destroyed by a bushfire near Melbourne. In addition to the extremely high temperatures, low levels of humidity and windy conditions are likely to create a protracted threat of wildfires in the short term. These conditions are notable in March, which is in Australia’s autumn and past the hottest season of December-February. On average, cities like Sydney have maximum daily temperatures between 23 and 27 degrees.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence

Transport Hubs Closed as Protests and Restrictions Hit Istanbul
Intelligence cut off: 11:00 GMT 19 March 2025
On the morning of 19 March, the Mayor of Istanbul and head of the opposition Republican People’s Party (CHP), Ekrem Imamoglu, was arrested on suspicion of being the head of a “criminal organisation” as well as aiding the banned Kurdistan Workers’ Party (PKK).
On 18 March, Imamoglu was stripped of his university degree by Istanbul University, over reports of administrative irregularities during his studies. As university degrees are required for presidential candidates in Turkey, Imamoglu who is widely regarded as the most popular opposition candidate for the 2028 elections, has effectively been excluded from running by the university’s decision.
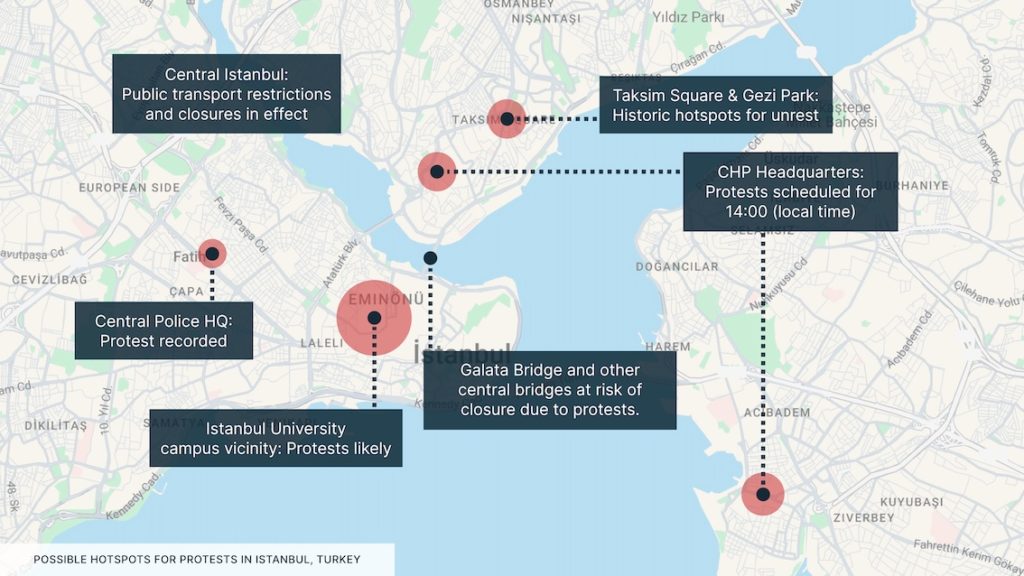
CHP is holding its candidate selection process on 23 March. In addition to Imamoglu, authorities reported that “100” other suspects had been arrested in the operation, including prominent journalist Ismail Saymaz.
Turkish media reported, following the arrest, that authorities have imposed a four-day restriction period on meetings, demonstrations, and press releases in the city. There are confirmed reports that Turkish authorities have imposed widespread internet restrictions, blocking access to platforms including X, YouTube, Instagram, and TikTok. In central Istanbul, multiple metro stations, including Taksim station, are reported to be closed on orders of the governor.
CHP leaders have organised multiple protests for 14:00 local time, including in Istanbul and Ankara. A gathering of protesters has been recorded at the central Istanbul police station as of the time of writing.
INTELLIGENCE ANALYSIS
Turkey Braces for Unrest as Opposition Vows Mass Protests
The arrest of Imamoglu is highly likely to provoke significant unrest, and it is almost certain to be perceived by opposition supporters as a move by the government of Recep Tayyip Erdogan to consolidate power and neutralise the opposition. Erdogan is constitutionally barred from running for president again, but it is likely that his Justice and Development Party (AKP) will field a constitutional amendment to prolong Erdogan’s presidency.
Protests are highly likely to concentrate in the centres of large cities, especially Istanbul. The CHP call for protests at the local party headquarters will almost certainly mean that these will be hotspots for gatherings of Imamoglu’s supporters. In addition to party offices, local universities are highly likely to be affected by unrest. Istanbul University is generally considered particularly liberal and is especially at risk as its students have in recent years launched several protests against its rectors, who are appointed directly by the president and are perceived to be excessively friendly to the government.
The authorities have closed Taksim Square metro station to limit the size of protests being organised near Taksim Square and are likely to close other stations.
Turkish police are highly likely to respond violently to any large gatherings and will also likely target isolated groups of protesters to prevent the formation of larger crowds. Turkish police employ harsh crowd-control measures including the use of tear gas, water cannons, and pepper spray. Arbitrary detentions of bystanders have been reported. Turkish authorities have previously used increased powers during periods of increased instability to detain foreign nationals who have engaged in or been near major protests.
Travel Risk Advice: Safety Guidelines for Greece
- Avoid all large gatherings. Limit travel in central Istanbul and Ankara due to the threat of protests. Avoid travelling to the vicinity of university campuses.
- Closely monitor local news reports and government alerts.
- Monitor the IETT website for live updates on transport in Istanbul.
- Plan for alternative routes and means of transport in Istanbul and Ankara. Allocate additional time for all travel
- If caught in a protest area, try to leave quickly if it is safe to do so.
- If you are in a crowd and unable to leave, take precautions to minimise the risk of crowd crush. These include staying upright, moving away from all hard barriers, going with and not against the crowd, and holding your arms at chest level in a boxer-like stance to relieve pressure.
- Increased security deployments are likely to continue throughout the four-day restrictions period (19-22 March). Disruptions are highly likely to be particularly severe during the weekend.
- Ensure that you always carry personal identification documents or copies.
- Have emergency contact numbers saved on your phone. These should include the local authorities, medical facilities and any consular support. Ensure that mobile phones are charged in case of any losses in electricity.
- Consider options to bypass internet restrictions or mitigate their impacts. This could include downloading useful resources ahead of travel and using a VPN and Tor Browser while in-country.
- Monitor the Solace Secure platform and trusted local media for updates relevant to the conflict.
Subscribe to free weekly intelligence

Executive Summary
Americas (AMER)
The arrest of a Green Card holder for his partaking in pro-Palestine protests is highly likely to drive demonstrations at US universities.
The ELN’s threat of “total war” is almost certainly a further indication of a deteriorating security environment in Colombia and could suggest that violence will migrate to other parts of the country.
There is a realistic possibility that President Noboa’s “strategic alliance” with a US private military company will escalate violence in Ecuador, which has become the homicide capital of Latin America.
Europe, Middle East & Africa (EMEA)
Russia will likely attempt to leverage the US ceasefire proposal with Ukraine to gain concessions, while the Kursk salient is highly likely to be imminently lost by Ukrainian forces.
The rejection of Calin Georgescu’s candidacy for the Romanian presidential elections is almost certainly going to cause unrest in the country. Moscow is likely to intensify hybrid operations in Romania to exploit the crisis.
Sectarian violence in Syria likely represents a critical failure in the HTS-led transitional government’s ability to control its allied militias and armed forces and will likely be exploited by both Israel and Iran.
There is a realistic possibility of a return to civil war in South Sudan, with tensions likely at their highest since the 2018 peace agreement. Renewed conflict would highly likely involve fighting in Juba.
There is a realistic possibility that the recent hostilities in the Tigray region of Ethiopia will result in greatly increased tensions between Ethiopia and Eritrea, threatening the start of an interstate conflict.
Asia-Pacific (APAC)
The BLA’s high-profile hijacking of a train in Pakistan carrying government troops has almost certainly undermined the central government and will likely force it to increase operations in Balochistan.
Twin Ramadan attacks in Thailand’s Deep South are likely to force the government into reassessing its strategy and result in increased counter-insurgency measures that may escalate tensions.
North, Central and South America
United States: Pro-Palestine protest leader arrested by ICE
One of the key figures in Columbia University’s post-October 7 pro-Palestine protests was arrested on 9 February by US immigration agents, who said they were acting on State Department orders reflecting a presidential executive order against anti-Semitism.
Mahmoud Khalil is a permanent US resident, a Green Card holder, and does not face any criminal charges. Federal authorities are seeking to deport Khalil, who is currently held at a detention facility in Louisiana. A federal judge temporarily blocked the deportation proceedings on 10 February.
On 13 February, a progressive Jewish group staffed a peaceful sit-in at Trump Tower in Manhattan against the deportation proceedings. Police reported around 100 arrests following the demonstration.
Solace Global Assessment:
The case is extremely high-profile and high-visibility due to the major protests in the United States and the central role Columbia has played in them.
Moreover, the political relevance of the case is increased by how unusual it is, as Green Card holders are seldom deported in the absence of a criminal charge and instead on the basis of a foreign policy provision – with the State Department stating that the deportation order is based on a “reasonable ground to believe that [Khalil’s] presence or activities in the United States would have potentially serious adverse foreign policy consequences for the United States”.
It is highly likely that the case will be a major driver of protests in the short term, particularly in cities that have large university campuses and that have had pro-Palestine demonstrations.
The final decision on the case is likely to be extremely consequential, as it may either halt or, conversely, accelerate the Trump administration’s stated efforts to target high-profile figures of the pro-Palestine protest movement.
Colombia: ELN leaders threaten “total war”
Senior leaders within the leftist guerilla group, the National Liberation Army (ELN), have warned that Colombia is heading towards “total war”, claiming that President Petro’s “total peace” plan has exacerbated conflict and have vowed to resist the government’s counteroffensive. ELN comments follow the government’s deployment of 10,000 troops to the Catatumbo border region and a recent statement made by Colombia’s newly appointed Defence Minister, who has vowed to reclaim territory lost to rebel groups.
Solace Global Assessment:
Colombia is currently experiencing its worst levels of violence since the 2016 ceasefire agreement and eventual disbandment of the Revolutionary Armed Forces of Colombia (FARC). However, rival groups like the ELN have filled the power vacuum left by FARC, especially in rural and border areas, and have secured profitable drug trafficking routes. The ELN’s sustained resistance to the peace process and recent offensives have resulted in tens of thousands being displaced, almost 100 civilian deaths, the imposition of armed strikes and a deterioration in the humanitarian situation in rural and border areas.
Government attempts to dislodge the ELN from rural areas are likely to face multiple setbacks. The ELN remains heavily entrenched, controls strategic and hard-to-access rural areas, is afforded support from the local community, is well-funded, well-armed and purportedly supported to some degree by Venezuela.
Moreover, the ELN has a considerable presence throughout much of Colombia and can conduct its concept of “total war” on multiple fronts. Should the ELN suffer setbacks in the northeast, there is a high likelihood that it will escalate attacks on the government, police, military and even the civilian population across Colombia as part of its doctrine of “total war”.
The group is known for its expertise in asymmetric warfare, often using bombings, ambushes, hit-and-run tactics and increasingly, drones to target security forces, government installations and infrastructure. These attacks can often result in high levels of collateral damage, and the ELN has demonstrated its ability to strike high-value targets in Bogota and other major cities.
Kidnapping for ransom is another key tactic of the ELN, and there is a realistic possibility that the deployment of this tactic will increase in order to help the guerilla group sustain its operations against the government.
Ecuador: President Noboa enlists help of US PMC founder
Ecuadorian President Daniel Noboa has announced that his administration is seeking to establish a strategic alliance with Erik Prince, the founder of the controversial US private military company (PMC) Blackwater, which now goes by the name Constellis.
The specifics of the alliance have yet to be disclosed; however, it is widely believed that its aim will be to combat organised crime, which has led to Ecuador becoming one of the most dangerous countries in Latin America.
Noboa has also stated that Ecuador will soon receive international assistance in the form of “special forces abroad.” However, he has not clarified where they will come from or under what legal framework they will operate. The move to enlist security assistance from abroad has been condemned by some within Ecuador’s security apparatus.
Solace Global Assessment:
Enlisting the help of a foreign PMC, especially one implicated in human rights abuses, is likely to provoke both public and political backlash, with many interpreting it as an erosion of Ecuadorian sovereignty and a move that could undermine the authority of Ecuador’s military and law enforcement.
However, President Noboa likely feels that the decision to turn to PMCs is one of his few remaining options. Noboa has introduced multiple draconian measures to counter organised crime, emulating many of the policies of President Bukele in El Salvador. This has involved the imposition of strict curfews and states of emergency, increasing military deployments, expanding the powers of the armed forces, increasing surveillance and raiding prisons to dismantle the leadership of organised crime groups.
However, Noboa has failed to achieve the same levels of success as witnessed in El Salvador. Ecuador now has the highest homicide rate in Latin America, assessed at 38.8 homicides per 100,000 inhabitants.
Noboa has likely underestimated the strength of the gangs and cartels that operate within Ecuador, which has become a “superhighway” for Peruvian and Colombian cocaine. The strategic significance of Ecuador has resulted in foreign organised crime groups arming and financing local gangs, which are often better equipped and more heavily armed than the country’s security forces.
The extent of foreign PMCs’ involvement has not been disclosed and may range from non-combat operations, such as training, to direct action. However, there is a high likelihood that the involvement of foreign PMCs will escalate violence, which has been observed before in countries like Iraq, Nigeria and Mozambique.
Criminal groups may respond with more violence to what they perceive to be foreign intervention, escalating attacks on the security forces, the government and even the civilian population. Furthermore, PMCs’ aggressive and often unregulated tactics are likely to provoke retaliatory violence from Ecuador’s criminal organisations.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
Canada’s new PM almost certain to prioritise trade war with Washington
Mark Carney is to take office as the next prime minister of Canada on 14 March. Carney won his bid to succeed Justin Trudeau, who resigned due to record-low polling numbers, at the Liberal Party’s primaries that ended on 9 March. Carney has stated that his first priority will be to “win” the trade war with the United States. Despite the Liberal Party falling behind the opposition Conservative Party in recent polls and its heading to anticipated elections from a position of weakness, Carney enters office with significant bipartisan consensus to address Washington’s economic threats. It is thus highly unlikely that the inauguration will result in notable civil unrest.
Opposition wins elections in Greenland
The centre-right Democratic Party won around 30 per cent of the vote and will now almost certainly lead coalition talks. The elections had been called by the previous government, led by the Inuit Ataqatigiit party, as a reaction to Washington’s interest in gaining sovereignty over the territory, which is part of Denmark but retains considerable independence. Most parties in the Greenlandic parliament, including the Democratic Party and the Naleraq party, which won the second most votes, are pro-independence (and against US annexation) but disagree on the timeline and mode for achieving it. The Democratic Party is in favour of a more moderate and long-term process, focusing on carrying out domestic reforms first.
Teslas vandalised as US House Republicans call for investigation
On 12 March, US representatives signed a letter calling for authorities to investigate vandalism on Tesla cars as “domestic terrorism” incidents. In the past weeks, there have been dozens of reported firebombings and other cases of damage against the US carmaker’s dealerships as well as private vehicles.
It is almost certain that the cases reflect opposition to Elon Musk, the owner of Tesla, who has so far played an important role in the Trump administration’s government restructuring efforts and has supported various far-right parties throughout Europe. The attacks are highly likely difficult to stop due to how dispersed the targets are, and the deployment of government forces to protect key targets, such as Tesla offices or dealerships, may be counterproductive by increasing the company’s visibility.
Tesla assets – including the “gigafactory” near Berlin, Germany – have also been targeted for vandalism in Europe in the past, and it is highly likely that the cases in the US will drive copycat actions on the other side of the Atlantic.
Protests erupt in Argentine capital over government austerity measures
On 12 March, police clashed with protestors outside of the Argentine Congress in Buenos Aires after demonstrations were held in response to new austerity measures introduced by the government of President Javier Milei. The police deployed water cannons, tear gas and batons to disperse protesters and made over 100 arrests. The protests were caused by reforms that the opposition claimed are unfairly targeting pensioners, and were attended by a large cross-section of society, including football fans who put historic rivalries aside to participate. Further protests are likely, with retirees currently protesting every week against cuts to their pensions.
Security, Armed Conflict and Terror
Islamic State (IS) lone wolf arrested in Sao Paolo, Brazil
Brazilian special counterterrorism forces arrested a man in Sao Paolo on 12 March. The individual was found to have “firearms, ammunition, fragmentation grenades, explosive material, gas masks, knives and crossbows” as well as IS propaganda and was subdued by police after attacking them with a knife. Images from the suspect’s house, as well as reports of the content of a “diary” in his possession, also show elements that may be linked to far-right ideology and other miscellaneous extremist positions. The case highly likely demonstrates the growing threat of self-radicalisation in Latin America and possibly further shows how lone wolves often combine different ideologies to justify their violent attacks.
Environment, Health and Miscellaneous
Flash flooding warning issued for Puerto Rico
On 14 March, a flash flooding warning was issued for Bayamón and Toa Baja in Puerto Rico, due to heavy rainfall, which could affect over 200,000 residents. The National Weather Service (NWS) reported 3 to 6 inches of rain, with an additional 2 inches possible, causing life-threatening flash flooding. Residents have been urged to avoid low-flying areas due to the risk of life-threatening flash flooding. Flooded roads and potential landslides are likely to lead to significant transport disruptions.
Flooding in Argentina kills at least 16
The city of Bahia Blanca and the nearby town of Cerri were hit by severe floods on 7 March following protracted rainfall, with 400mm of rain recorded in eight hours. The floods resulted in severe disruptions throughout the area, with almost 100 people declared missing in addition to the 16 fatalities. The flooding has resulted in significant anti-government sentiment, as reports indicated that the Argentine National Emergency Directorate, the body which is responsible for providing disaster relief, was shut down three days before the severe weather event. Local authorities have stated that Bahia Blanca “needs to be rebuilt” and that the storm caused severe infrastructural damage.
Europe, Middle East & Africa
Ukraine: US support resumes as Kyiv agrees to 30-day ceasefire proposal
Following the cessation of US military aid and intelligence sharing to Ukraine, Russian forces launched a series of long-range aerial strikes against critical Ukrainian national infrastructure (CNI) and major population centres.
On 11 March, just hours before a key meeting between the US and Ukraine in Jeddah, Saudi Arabia, Ukrainian forces launched their largest-ever drone attack against targets in Russia. According to the Russian Defence Ministry, 343 one-way attack uncrewed aerial vehicles (OWA-UAVs) were intercepted across Russia, including 91 over the Moscow region. At least three people were killed due to debris caused by interceptions, and all four of Moscow’s airports were temporarily shut down.
At the Jeddah meeting, the US delegation, led by Secretary of State Marco Rubio and national security advisor Mike Waltz, spoke for over five hours with the Ukrainian delegation led by President Volodymyr Zelensky’s chief of staff, Andriy Yermak. A US proposal for an immediate 30-day ceasefire with Russia was accepted by Ukraine, and the US agreed to lift the suspension of intelligence sharing and military aid.
On 13 March, in a joint conference with the President of Belarus, Alexander Lukashenko, Russian President Vladimir Putin questioned the ceasefire proposal and indicated that it would only be acceptable if a series of conditions were met, de facto rejecting the proposal. One of the key questions Putin raised was the status of the Kursk salient, with Ukrainian forces having been forced out of most of the salient by Russian counteroffensives in recent weeks.
On 13 March, the Russian Defence Ministry announced that Sudzha, the last remaining major settlement held by Ukrainian forces in Kursk, had been successfully retaken by Russian forces.
Solace Global Assessment:
As a centre of gravity (COG) for Ukrainian military efforts, the cessation of US military aid and intelligence sharing likely posed an existential threat to Ukraine’s position in the conflict. The most immediate impact from the loss of critical intelligence, surveillance and reconnaissance (ISR) capabilities was likely in the Kursk salient. The Trump administration was highly likely able to compel Kyiv to accept a proposal for an immediate 30-day ceasefire by leveraging the military value of its military aid and intelligence sharing. With Kyiv now compliant, it is highly likely that the resumption of US support is intended to apply renewed pressure on the Kremlin to now agree to a ceasefire agreement that likely favours Washington.
It is highly unlikely, however, that Moscow will agree to a ceasefire while counteroffensive operations are ongoing in Kursk. The Kursk offensive was almost certainly intended by Kyiv to provide a bargaining chip in future peace negotiations. However, Russian forces have seized the initiative on this axis and have almost certainly benefitted from the suspension of US intelligence, which has denied Ukraine early warning of Russian movements and reduced its ability to target Russian high-value targets. The Kursk salient is now highly likely to be lost imminently by Ukrainian forces, as failing to withdraw would risk the encirclement of critical troops and resources.
It is likely that the Kremlin will attempt to leverage the ceasefire proposal to gain concessions by deploying reflexive control (the use of deception and other techniques to alter an opponent’s behaviour so they voluntarily behave in a desired way). Having likely successfully presented itself as desiring serious peace talks to the Trump administration, Moscow will now likely attempt to extract concessions as conditions for a hypothetical ceasefire, concessions which will enable greater success on the battlefield to achieve its war goals and may delay the war until concessions that favour Russia are proposed.
Romania: Protests after Electoral Court bars Georgescu from running
Calin Georgescu, the populist anti-NATO and anti-EU outsider who surprisingly won the, later annulled, first round of the Romanian presidential elections in December 2024, was barred from running at the re-do vote in May. The decision, which was issued by the Central Election Bureau on 10 March, resulted in protests and clashes in Bucharest on 10 and 11 March. The court’s decision was criticised by both Washington and Moscow and has driven an increase in calls for political violence. Prior to being barred from running, Georgescu was polling at around 40 per cent and was the clear favourite for May’s vote. This is not the first time a candidate has been barred from running in the election: in October 2024, Diana Sosoaca, leader of the SOS Romania party, had her candidacy rejected over “incompatibility” with Romania’s constitutional values.
Solace Global Assessment:
It is highly likely that protests will continue in the short term, and is likewise highly likely that tensions will increase as the vote approaches. If elections were to be held today, Georgescu would likely win. Since the first vote’s annulment and his later arrest, he has become a unifying figure for Romania’s populist and anti-establishment forces, such as the Alliance for the Union of Romanians (AUR). AUR’s leader George Simion had previously refrained from running for president so as not to interfere with Georgescu’s bid but has changed his stance after Georgescu’s disqualification.
In addition to protests, there is a realistic possibility of intensified hybrid operations being carried out in Romania by Moscow to politically destabilise the country at a key moment. Russia has increasingly adopted a sabotage and espionage “gig economy”, relying on citizens of target countries to carry out low-sophistication operations. It is highly likely that Russian intelligence will seek to take advantage of a growing number of Romanians who are disappointed with their political institutions following the recent developments. The recent arrest of six individuals who had reportedly previously travelled to Moscow and were planning to carry out destabilisation operations in Romania likely demonstrates Russia’s proactive approach to capitalise on the crisis.
Syria: Massacres against Alawite minority worst violence since fall of Assad regime
According to the Syrian Observatory for Human Rights (SOHR), over 1,300 civilians were killed by security forces supporting the Syrian transitional government between 6 and 12 March, with particularly severe massacres occurring in the Latakia and Tartus governorates. Most of the civilians were Alawite, with former President Bashar al-Assad being a member of the minority group. The violence was reportedly perpetrated by forces linked to Syria’s new government, including the official Syrian Ministry of Defence and General Security Service members, allied Turkey-backed Syrian National Army (SNA) militias, and other armed individuals described by witnesses as including “foreigners” of Turkmen and Chechen origin. Syria’s interim President, Ahmed al-Sharaa, has denied government responsibility for the killings and has vowed to hold the perpetrators accountable.
Solace Global Assessment:
It is almost certain that these massacres represent a significant escalation in sectarian violence that will undermine Syria’s already fragile post-Assad transition. The systematic targeting of Alawites almost certainly indicates retribution killings. The violence likely represents a critical failure in the Hayat Tahrir al-Sham (HTS)-led transitional government’s ability to maintain command and control over its allied militias and security forces.
The massacres will highly likely accelerate a nascent insurgency against the HTS-controlled interim government and will likely be exploited by both Israel and Iran to pursue their objectives in Syria. Moreover, successful attacks by the resistance will likely result in more retaliatory attacks on the Alawite community. An appeal by Alawite leaders was read on Israeli TV on 10 March, which called for intervention by the Israel Defence Forces (IDF). As Israel has likely exploited the status of Syria’s Druze minority in southern Syria to justify its Syrian incursion, the treatment of Syria’s Alawite minority will likely be exploited to further its aims. Moreover, Tehran is highly likely to support efforts by Assad-regime remnants to launch an insurgency, with the loss of Syria being a critical blow to its influence across the Middle East and its ability to sustain its primary proxy force, Hezbollah. The confluence of internal sectarian tensions and foreign interests highly likely presents a significant challenge to stability and peace in the new post-Assad Syria.
South Sudan: Fears increase of imminent return to civil war
On 8 March, the US Department of State ordered the departure of non-emergency US government employees from South Sudan. The order comes within the context of heavy fighting in Nasir, Upper Nile State, between the national army and White Army militias, and the arrests of several key military and political figures allied with former Vice President Riek Machar.
A day prior, on 7 March, a United Nations (UN) helicopter rescue mission in Nasir was attacked, resulting in the deaths of General Majur Dak, a UN crewmember, and approximately 27 troops.
The Intergovernmental Authority on Development (IGAD) warned on 12 March that the escalation in South Sudan is pushing the country dangerously close to renewed civil war. The 2013-2018 civil war fought between President Salva Kiir’s Sudan People’s Liberation Movement (SPLM) and Machar’s Sudan People’s Liberation Movement-In Opposition (SPLM-IO) resulted in the deaths of almost 400,000 people and displaced four million.
Uganda’s Chief of the Defence Forces, Muhoozi Kainerugaba, announced that Ugandan special forces had been deployed to South Sudan’s capital Juba to “secure it” on 11 March, although their presence is unconfirmed and has been denied by South Sudan’s government.
Solace Global Assessment:
The South Sudanese civil war was largely fought along ethno-sectarian lines, with members of the Dinka ethnic group from Northern Bahr al-Ghazal state generally aligned with Kiir and the Nuer ethnic group from the Greater Upper Nile region generally aligned with Machar. Due to the prevalence of oil fields, fighting was particularly concentrated in the Upper Nile states.
Almost certainly exacerbated by ethnic sectarianism, the conflict was characterised by the frequent targeting of civilians, mass sexual violence, looting and the destruction of property. The White Armies are formed from Nuer communities and fought alongside SLPM-IO during the civil war.
However, the SPLM-IO leadership highly likely does not exercise full command and control over these militias, and there is a realistic possibility that the recent increase in White Army attacks has occurred without direction from Machar and his allies.
The Revitalized Agreement on the Resolution of the Conflict in the Republic of South Sudan (R-ARCSS) signed in 2018 between Kiir and Machaar promised to bring an end to the civil war, but tensions and levels of violence have remained relatively high since. Several stipulations from the peace agreement have yet to be implemented, including an election (with elections currently postponed until 2026), a new constitution, and the integration and reunification of armed groups into a singular national military.
Tensions are likely the most severe since 2018, and there is a realistic possibility that a full-scale civil war could once again break out. A return to full-scale civil war would likely see gun battles erupt in the capital, Juba.
Kampala is almost certainly heavily incentivised to protect its interests in South Sudan, having invested heavily in infrastructure projects and being a major trading partner. However, there is a realistic possibility that Kainerugaba’s announcement made on X of troop deployment is false.
Kainerugaba, who is the son of President Yoweri Museveni and widely considered the heir-apparent, is a prolific user of X and has on numerous occasions posted controversial and bizarre statements. It is likely, however, that even if false, the announcement has further increased tensions with calls being made by opposition groups for the “immediate withdrawal of all foreign troops”.
Ethiopia and Eritrea: Tensions rise in Tigray
On 11 March, factions of the Tigray People’s Liberation Front (TPLF) carried out multiple attacks on units of the Tigray Interim Administration (TIA) and seized towns in the Tigray region and key offices in the Tigray capital of Mekelle. The TIA is the government that emerged from the 2022 Pretoria Peace Treaty and is backed by Ethiopia. While part of the TPLF has recognised its legitimacy, factions within the paramilitary group have accused it of acting as a proxy of Ethiopia.
Solace Global Assessment:
Both Ethiopia and Eritrea fought against TPLF during the 2020-2022 civil war. However, since the 2022 treaty, relations between the two neighbouring states have become increasingly unstable. Last year, Eritrea signed a security deal with Somalia and Egypt, which was likely a response to Ethiopia’s stated interest in gaining a direct access seaport and reducing its reliance on the Port of Djibouti.
In late February, reports emerged that Eritrea had started mobilising its forces in response to the increasing tensions. Ethiopia has accused Asmara of undermining the peace and destabilising Tigray and has, according to Tigray channels, sent troops to its northern border. There is a realistic possibility of the tensions between Eritrea and Ethiopia resulting in a conflict between the two states, with each nation state supporting rival Tigray factions.
Despite being the much smaller and militarily weaker nation of the two, Eritrea has previously been successful at sustaining long-term military operations against Ethiopia. This has largely been achieved by external support and the adoption of guerilla tactics. However, weaknesses within the Ethiopian state have played to Eritrea’s advantage.
Should a renewed conflict erupt, there is a realistic possibility that other separatist forces in Ethiopia will seek to exploit the situation by conducting their own operations against state forces, which may become increasingly overstretched.
However, a renewed conflict Ethiopia and Eritrea is not in the interest of external powers due to the potential for regional instability, humanitarian crises, and the disruption of vital trade routes in the Horn of Africa. External actors, including the UN, African Union and the European Union, will likely champion diplomatic efforts to prevent a return to conflict and on 14 March, 24 embassies based in Addis Ababa issued a joint statement urging for the protection of the Pretoria Agreement.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Protests continue in Greece over controversial fatal train crash
Protests continued in several Greek cities on the weekend of 7-9 March to mark the anniversary of the 2023 Tempi train crash. Violent clashes erupted, and Molotov cocktails were thrown in both Athens and Thessaloniki, resulting in the police using tear gas and making multiple arrests. There is a realistic possibility that further protests will be organised on the weekend of 14-16 March as a result of ongoing investigations and the police’s response to the protests.
Serbian anti-corruption protests target state media
Anti-corruption protests have continued throughout Serbia, with recent demonstrations aimed at state-run media institutions. On 10 March, protesters blocked entrances to the headquarters of Serbia’s state-owned broadcaster RTS in Belgrade, vowing to stay for 22 hours. On 11 March, a protest was organised outside the RTS buildings in both Belgrade and Novi Sad, as well as outside the N1 television channel office in Belgrade.
The protests likely reflect a deep dissatisfaction with the way state-run media organisations have been reporting the anti-corruption protests, the lack of independent journalism and the lack of freedom of the press in Serbia. However, the demonstrations likely do not reflect a major change in strategy of the wider protest movement, which has been blocking major transport networks across the country and organising huge protests in the country’s major cities.
A major protest has been organised in Belgrade on 15 March, which may attract protestors as early as 14 March. These protests may spread to other parts of the country and are likely to involve violent confrontations with the security forces.
Syrian Kurds strike deal with Damascus
The Kurdish Syrian Democratic Forces (SDF), which control much of the country’s northeast and are backed by the US, agreed on a deal to join Syria’s new government institutions on 10 March.
The deal is almost certainly a major breakthrough which will shape the political future of post-Assad Syria, and it is likely to decrease the risk of a conflict between the SDF and Damascus. The deal entails the integration of SDF institutions within the Syrian state and grants the Kurdish community comprehensive minority rights, a long-standing political demand that had been denied under Assad. The deal was almost certainly backed by the US, which is trying to reduce its footprint in Syria.
It also highly likely complicates Turkey’s position. Ankara classifies the SDF as a terrorist organisation and backs the Syrian National Army (SNA) operations against SDF-controlled areas. Turkey, whose government has recently made overtures to its domestic Kurdish community, may find tolerating the deal beneficial.
Although, with increased sectarian violence and the threat of a nascent insurgency launched by Assad-remnants which would likely be backed by Iran, there is a realistic possibility that the deal will collapse in the face of a return to civil war.
Security, Armed Conflict and Terror
Tehreek-e-Labbaik Pakistan (TLP) supporters arrested in Spain
On 10 March, a coordinated operation between Spanish and Italian police that lasted for three years led to the arrest of 11 alleged TLP supporters in Barcelona. According to authorities, the group was engaged in the spread of information and propaganda encouraging violence in Europe.
TLP, which remains extremely popular in Pakistan, has called for violence against European politicians perceived as attacking the Islamic faith. Among other actions, TLP leaders called for violence in the Netherlands following the 2018 publication of caricatures of the Islamic Prophet Mohammed, and praised the murder of French school teacher Samuel Paty in 2020 over (false) accusations of blasphemy.
The case highlights ongoing TLP efforts to increase support in Europe, including in countries with smaller Pakistani diasporas like Spain and Italy.
Armenia and Azerbaijan agree to peace treaty
On 13 March, negotiations concluded between Armenia and Azerbaijan, with both sides agreeing on key terms for a draft peace treaty deal. This follows almost four decades of territorial disputes between the two nations that have been marred in conflict since the fall of the Soviet Union.
The most significant conflict occurred in 2020 when Azerbaijan reclaimed large parts of the Armenian-dominated Nagorno-Karabakh region. Azerbaijan seized the territory in September 2023, leading to the exodus of over 100,000 Armenians from the region.
The peace treaty could bring lasting peace in the South Caucasus; however, the timeline is uncertain as amendments are expected to Armenia’s constitution from Azerbaijan, which would require a referendum. Azerbaijan demands that Armenia eliminate any territorial claims over Nagorno-Karabakh, which is highly likely to cause discontent and resistance in Armenia.
Hezbollah leader warns of continued resistance if Israel refuses to withdraw from Lebanon
Hezbollah’s Secretary-General Naim Qassem has warned Israel that if it continues its occupation of southern Lebanon, it will be confronted by Hezbollah as well as the Lebanese people and the Lebanese Army, accusing Israeli forces of over one thousand violations of the ceasefire.
Qassem also warned that despite suffering several setbacks during its previous confrontations with Israel, such as the loss of two leaders, Hezbollah remains vast, capable and has addressed previous security vulnerabilities.
Regarding domestic politics, Qassem reaffirmed Hezbollah’s commitment to state-building and participation within the electoral process, a move that is likely aimed at reducing pressure from the central government whilst it struggles to regroup after losing critical ground lines of communication through Syria.
Clashes as Malian migrants attack Mauritanian border police station
The violence erupted on 8 March near the Gogi crossing in Hodh al Gharbi province. According to local media, the migrants were scheduled to be deported from Mauritania after entering the country illegally, almost certainly en route to Europe. After arriving at the border post, the migrants refused to cross it and clashed with police, prompting the intervention of the Mauritanian gendarmerie. In the past week, Mauritania has carried out a wave of arrests and deportations. The government of Mauritania is seeking to build stronger economic ties with the EU, and the recent raids are likely an attempt to send a signal to Brussels.
Al-Shabab lay siege to Somali hotel
On 11 March, militants belonging to al-Shabab stormed the Qahira Hotel in the city of Beledweyne in central Somalia, approximately 335km (208 miles) north of Mogadishu. The militants detonated a vehicle-borne improvised explosive device (VBIED) and then entered the hotel with small arms. The attack is thought to have killed 15 people, including six militants, after Somali security forces ended the siege. The attack was likely a strategic message sent to the central government as it reportedly took place while politicians, security officials, and traditional elders were gathered to discuss strategies for an upcoming offensive against the group in central Somalia.
Islamic State plan to strengthen affiliates in DRC and Mozambique
Uncorroborated reports from within the Islamic State indicate that the terrorist organisation is planning on deploying senior leaders to one of its lesser-known affiliates, Islamic State Central Africa Province (ISCA), which primarily operates in the DRC and Mozambique. This likely reflects an attempt to exploit the current instability of both countries, porous borders, lack of governance and the intent to establish a largely peripheral affiliate into a more capable operational force, potentially with the ability to conduct external attacks into some of the regions more stable countries.
South Africa discloses information on dismantled criminal group and extremist cell
South African authorities have revealed details about a series of arrests that occurred in July 2024. Five individuals were arrested by South African authorities, three of whom are accused of having ties to an extremist group, likely the Islamic State (IS). According to prosecutors, the five were linked to at least two separate cases of kidnapping of businessmen for ransom.
During the operation, a 72-year-old captive was freed. Moreover, authorities claim that the cell was linked to kidnapping cases dating as far back as 2020. The case, while not recent, is extremely notable as South Africa, despite not having had a history of IS attacks, is a key source of funds that the group uses to finance its activities elsewhere in Africa. The inquiry into the kidnapping cell could shine further light on the interplay between South African organised crime and transnational extremism.
Environment, Health and Miscellaneous
Storm Jana causes disruptions in southern Spain and Portugal
The weather system hit southern Iberia and the Balearic Islands between 6 and 12 March. The storm caused significant flooding, with cities like Granada, Malaga and Seville being particularly affected. Local media indicates that at least five flights were diverted from landing at Malaga airport due to the strong winds, which reached speeds of up to 90 kph. In the Balearics, the severe rain caused by the storm resulted in localised flooding and travel disruptions.
First case of cholera confirmed in Namibia after decade-long absence
Namibia has confirmed its first case of cholera in ten years, according to the Africa Centres for Disease Control and Prevention (Africa CDC). The case has raised concerns, prompting health officials to strengthen their response efforts. The outbreak is believed to be linked to a cholera epidemic in neighbouring Angola, which has killed 237 people since January. The Africa CDC has sent 2,000 oral cholera vaccines to Angola to protect healthcare workers, though far more resources are likely needed to contain the outbreak.
Asia–Pacific
Pakistan: BLA militants hijack train carrying hundreds of Pakistani security personnel
On 11 March, militants belonging to the Balochistan Liberation Army (BLA) derailed the Jaffar Express train in the Bolan district while it was travelling from Quetta in Balochistan Province to Peshwar, Khyber Pakhtunkhwa Province. BLA militants bombed the tracks, then fired upon the train and then stormed the carriages. The train was carrying approximately 450 passengers, including at least 100 off-duty security personnel travelling home on leave. Militants took control of the train and held hundreds of passengers hostage. The BLA threatened to kill them unless their demands for the release of imprisoned BLA members were met.
Pakistani security forces conducted a rescue operation that lasted approximately 27 hours and resulted in the deaths of all 33 insurgents. Unconfirmed reports from the Pakistani military indicate that the assailants killed 21 hostages, but no hostages died because of the rescue operation. However, BLA statements contradict official reports, suggesting that more than 100 people were killed, including dozens of Pakistani soldiers, during the rescue operation and multiple hostages were taken into the neighbouring mountains in small groups. Pakistani authorities have accused the Taliban in Afghanistan of facilitating the attackers, a claim that Taliban officials have denied.
Solace Global Assessment:
The scale, sophistication and target of the attack suggest that this was a well-planned operation and may indicate that the BLA has infiltrated Pakistan’s security apparatus, allowing them to obtain intelligence on the movements of Pakistani security personnel.
Targeting transport infrastructure has become an established tactic, technique and procedure of the BLA, with this attack following multiple attacks on ports, roads and the rail network. The BLA advocates for Baloch independence and opposes what it sees as the exploitation of Balochistan’s natural resources. Therefore, attacks on transport infrastructure have become highly symbolic, as they represent the mass movement of people and goods from Balochistan to other parts of Pakistan and are likely aimed at deterring foreign, particularly Chinese, investment.
Consequently, BLA attacks on transport infrastructure and foreigners in the region will almost certainly continue, despite the risk of economic losses for the Baloch community. These attacks are likely to occur in hard-to-access areas with limited mobile and internet signals, which will hinder timely communication and coordination, resulting in increased response times for security services, helping to maximise the success of attacks.
This attack likely marks a major escalation. The operation has gained worldwide publicity and will almost certainly serve as a major embarrassment, undermining Pakistan’s claims of its ability to guarantee security. If the BLA has successfully managed to keep some security personnel hostage, it will likely leverage this for further concessions.
Furthermore, the BLA reportedly filmed the attack and released it for propaganda, a move that will likely help it achieve greater publicity and buttress recruitment. In response to the attack, Pakistan will likely be forced to intensify its counterterrorism operations in Balochistan, including increased military deployments, intelligence gathering and increased security measures on transport infrastructure.
However, the Pakistani military is facing significant strain as it grapples with sectarian violence, militancy in multiple regions, and ongoing border clashes with the Taliban, creating an opportunity that the BLA is likely to exploit in the near term. Moreover, the strategic aim of the BLA may be to force Pakistan into increasing its operations against it. This would likely provide the militant group with more opportunities to conduct similar attacks and to undermine the central government’s legitimacy, expose weaknesses in security forces and disrupt local economic activity, all of which will enable it to increase propaganda, recruitment and funding.
Thailand: Twin Ramadan attacks on security services in Deep South
On 8 March, twin attacks targeted the Thai security services in the Sungai Kolok district on the Malaysian border in the Narathiwat province and the Sai Buri district in the Pattani province, in Thailand’s restless Deep South region. In Sungai Kolok, masked assailants dismounted from a pick-up truck, fired small arms and threw incendiary devices at on-duty security volunteers. The attackers also detonated explosives hidden inside a car and a motorcycle, which were parked outside the district office compound. The attack killed at least two security personnel and injured several more. In Sai Buri, a bomb was detonated outside a local government site, killing three officials.
Solace Global Assessment:
Thailand’s Deep South has struggled with a low-intensity conflict since 2004. Attacks from Islamist groups like the Barisan Revolusi Nasional are common during Ramadan and typically target local government and security forces. Many of the defence volunteers are Muslims from the local community, and the attack was likely coordinated to target personnel while they were breaking their fast. However, the attack was unusually early in the Ramadan period, with attacks traditionally increasing during the last ten days of the Holy Month. This may indicate that militants have adapted their tactics to exploit decreased security measures during the start of the period or may indicate that this year’s Ramadan will involve a higher rate of attacks than what is usually observed.
The deadly twin attacks follow a series of largely non-fatal attacks in Pattani, Yala, Narathiwat and Songkhla. These attacks are often underreported by the Thai government, which fails to reflect the deteriorating security environment in the Deep South. The current Thai administration, led by Prime Minister Paetongtarn Shinawatra, has made achieving peace in the Deep South a top priority, which was also championed by her father and former prime minister, Thaksin Shinawatra. It is likely that militant groups in the Deep South are attempting to undermine this process and will continue to conduct attacks in the Deep South. The attacks have already resulted in prominent Thai politicians calling for a reassessment of peace negotiations and allegations that those involved do not represent the militant groups.
In response to the attacks, the Thai Interior Minister has ordered increased security in the Deep South, with further security meetings planned. This will likely involve increased military and police deployments, increased raids and arrests, increased security at government locations, increased vehicle inspections, tighter border security and potentially the imposition of curfews. Malaysia has also increased its border security and has warned its citizens not to travel to southern Thailand, with fears that the attack may have been a cross-border attack conducted by Malaysia-based militants. However, increased counter-insurgency operations are likely to exacerbate tensions and may result in an increase in militant attacks. Furthermore, militant groups have previously conducted high-profile attacks in other parts of Thailand. If the Thai government intensifies its operations in the Deep South, there is a realistic possibility of reprisal attacks migrating to other parts of Thailand, including major tourist resorts.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Large Hizb ut-Tahrir (HT) protest broken up by Bangladeshi police
Around 4,000 supporters of the Islamist movement, which is currently banned in Bangladesh, gathered in Dhaka to call for the country to become a caliphate. The police intervened after supporters reportedly attempted to break through the police barricade. Videos show the deployment of tear gas by police forces, and at least 39 people were arrested. The rally is likely an important show of force by HT. The group was banned under the government of long-serving Prime Minister Sheikh Hasina, who was ousted in August 2024. It is highly likely that banned groups like HT are seeking to increase pressure on the interim government as a means to re-enter mainstream politics and advance their, in this case, politico-religious message.
Former president arrested in the Philippines
Former Philippines President Rodrigo Duterte was arrested at Manila Airport on 11 March in response to the International Criminal Court (ICC) issuing a warrant for his arrest relating to Duterte’s war on drugs. The former president was then forced onto a plane heading to the ICC court at the Hague. Duterte faces charges for “the crime against humanity of murder” after his presidency oversaw the killing of thousands of people associated with the narcotics trade. Many of these killings are believed to have been extra-judicial and lacked due process. However, Duterte largely won his presidency on the promise of combating the drug trade and still commands a lot of support in the Philippines. Supporters have protested outside the locations where Duterte has been held, and there is a realistic possibility that major developments in his trial will trigger major unrest in the Philippines.
Security, Armed Conflict and Terror
Pakistan sets 31 March deadline for illegal foreigners to leave the country
The announcement, issued on 7 March by the Ministry of the Interior, is almost certainly aimed at Afghans and singles out holders of an Afghan citizen card. Currently, UN estimates put the number of Afghans residing in Pakistan at above two million. Since Pakistan started its deportation drive in 2023, up to 800,000 have returned to the neighbouring country. There is a high likelihood that the ultimatum will drive civil unrest in Pakistan and may cause sectarian strife. Islamabad has increasingly blamed Afghan residents for threats to its security. Although this is mostly inaccurate, there is a significant likelihood that groups such as the Islamic State Khorasan Province (ISKP), which primarily operates in Afghanistan and has a lot of influence in Pakistan, may target the diaspora for radicalisation and recruitment. These efforts could be further facilitated by the Pakistani government’s increased focus on repatriation and deportation measures.
Myanmar junta looks to Russia for military cooperation
Myanmar’s junta government has reportedly turned to Moscow for military cooperation, a development that has likely materialised due to General Min Aung Hlaing’s recent round of high-level talks with President Putin at the Kremlin. The junta is hoping to obtain high-tech drones from Russia as well as access to Russian satellite-derived imagery intelligence (IMINT). Improved access to these technologies will almost certainly improve the junta’s surveillance, intelligence gathering and targeting of rebel forces and could help shift the balance in the current civil war.
Environment, Health and Miscellaneous
Healthcare access affected by nationwide physician shortage in South Korea
The US Embassy in South Korea has issued an alert relating to reduced access to healthcare across the country. The alert indicates that the embassy has received reporting suggesting that there have been complications involving access to emergency care, with major hospitals prioritising care based on the severity of injury or illness, resulting in delays to care or even denials in less urgent cases. The shortages have impacted private healthcare facilities less. The shortages in physicians are almost certainly linked to the ongoing doctors’ strike in South Korea, which has led to thousands of doctors going on strike to protest government plans to increase medical school admissions, arguing it will lower the quality of healthcare and strain resources.
Cyclone Alfred causes traffic and power disruptions in east Australia
More than 200,000 homes were reported to be without power on 10 March, most of them in the Gold Coast area of Queensland and New South Wales, due to the cyclone. Cyclone Alfred formed at sea northeast of Queensland on 23 February and first made landfall over Bribie Island on 8 March, dissipating the following day. The significant interval between the cyclone’s formation and its landfall has almost certainly allowed Australian authorities to take proactive measures to minimise its impact. Nevertheless, at least one death was caused by the cyclone in Dorrigo, New South Wales, and dozens of people were injured. At least four people are considered missing as of the time of writing.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence

Executive Summary
Americas (AMER)
Mexico’s unprecedented extradition of cartel members to the US is almost certainly anattempt to appease the Trump administration and will likely involve an increase in counter-cartel operations.
Nicaragua’s withdrawal from the UN Human Rights Council is almost certainly indicative of a broader effort to limit foreign oversight of human rights abuses and government repression.
Europe, Middle East & Africa (EMEA)
Russia will almost certainly exploit the US decision to suspend military aid and intelligence sharing with Ukraine by increasing the scale and frequency of its long-range attacks.
Significant armed clashes in Syria are likely indicative of a nascent insurgency, which would highly likely receive support from Iran.
The US government has almost certainly rejected the Arab League’s Gaza plan. Washington’s pressure on Hamas, as well as the ongoing blockade in Gaza, are likely to destabilise the ceasefire.
Terror attack highly likely in Mogadishu amid an ongoing al-Shabaab offensive in Somalia.
Ghanaian MPs’ resubmission of a controversial anti-LGBT bill is likely to be passed by parliament and will likely result in increased violence and repression of the LGBT community.
Asia-Pacific (APAC)
Reprisal attacks by ISKP highly likely in Pakistan after regional commander arrested in joint US–Pakistan operation.
An investment deal between the US and Taiwan’s TSMC is highly likely indicative of a strategic priority for the Trump administration to mitigate against the potential impact of Taiwan’s invasion.
North, Central and South America
Mexico: US receives 29 high-ranking cartel members in unprecedented extradition
In an unprecedented move, Mexico City has authorised the extradition of 29 high-ranking cartel members to the US, many of whom are alleged to have committed serious crimes, including murder. The most high-profile extradition was that of Rafael Caro Quintero, or the “Narco of Narcos”, who allegedly ordered the kidnap, torture and killing of DEA special agent Enrique “Kiki” Camarena in the 1980s which placed him on the FBI’s most wanted list until his capture in 2022. If convicted, many of those extradited could face the death penalty, according to the US Department of Justice. The extraction follows the designation of several Mexican drug cartels as Foreign Terrorist Organizations (FTO) by US President Donald Trump in January.
Solace Global Assessment:
Mexico’s compliance with US demands was almost certainly a reaction to the threat of economically devastating tariffs imposed by the Trump administration. However, Trump imposed tariffs on Mexico on 4 March and declared a “war” on Mexican cartels the same day. These moves likely indicate that Trump’s war against the cartels has only just begun, and his administration will leverage tariffs to exert pressure on Mexico City to sustain its commitment to counter-cartel operations.
In a recent visit to the southern border, US Vice President JD Vance dismissed the idea of the US military “invading” Mexico. However, US strategic intelligence, surveillance and reconnaissance (ISR) airborne assets, such as the RC-135 “Rivet Joint”, have continued to fly missions close to the Mexican border. This likely suggests that the US military has intensified its surveillance of the cartels. The US may also be sharing some of this intelligence with Mexico to support Mexican counter-cartel operations, which could explain a series of recent high-profile arrests of major cartels designated as FTOs.
Reporting indicates that the cartels, especially the notorious Sinaloa cartel, have been significantly impacted by the recent government crackdowns, which have involved arrests, drug seizures and raids on fentanyl labs. This has forced the Sinaloa cartel to scale back fentanyl production and move labs to other parts of Mexico. Anecdotal reporting from cartel members indicates that they have linked this to increased US operations, especially drone surveillance. Cartels are beginning to invest in drone-detection technology and have expressed that they genuinely feared arrest or death for the first time in years.
However, cartel members have also suggested that they are unlikely to cease operations and will not go down without a fight, especially when confronted with the prospect of extradition and the death penalty. Sustained pressure from both the US and Mexican governments is likely to result in a shift in cartel operations. Cartels are likely to employ more violence to deter the Mexican government, and increased arrests could result in the splintering of cartels, posing the risk of greater competition and more violence. If the cartels start to view US involvement as an existential threat, there is a realistic possibility that cartels might deliberately target US citizens and interests. This could include attacks on American businesses, kidnappings of US citizens, or attempts to increase narcotics shipments to the US.
Nicaragua: Ortega regime withdraws from UN Human Rights Council
Nicaragua has announced that it will withdraw from the United Nations Human Rights Council (UNHRC) following a UN report which urged the international community to address human rights abuses committed by the government of President Daniel Ortega. The UN report alleged that the Ortega regime had engaged in a systematic crackdown on human rights, democratic norms and had increased its repression of religious groups.
Solace Global Assessment:
Nicaragua’s withdrawal from the UNHRC was quickly followed by an announcement that it will also quit the International Organization for Migration (IOM) and the International Labour Organization (ILO). These withdrawals likely indicate a broader trend of Nicaragua attempting to reduce foreign oversight of its abuses, which have been preceded by several major reforms that have enabled Ortega and his family to consolidate power in the country. These have included changes to the constitution that have expanded presidential powers, allowing him to exert more control over the judicial and the legislative branches of government, more control over the police and military, and more state control over the media.
These moves indicate that Ortega is further isolating Nicaragua from international scrutiny and consolidating his grip on power. This will almost certainly result in increased oppression of NGOs, civil society groups, independent media, the Catholic Church and other organisations critical of the regime.
In August 2024, Ortega banned approximately 1,500 NGOs in Nicaragua that were deemed to be hostile towards the government, which included the Nicaraguan Red Cross and several charities associated with the Catholic Church. Future repressive measures will likely involve arbitrary detentions, expulsions and the use of state-sponsored physical and psychological violence, including threats, beatings, solitary confinement and even extrajudicial killings.
This repression and reduction in foreign assistance will almost certainly lead to a deterioration of humanitarian conditions and likely increase migration flows out of Nicaragua.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
US tariffs on Canada and Mexico go live, then get postpone
Tariffs of 25 per cent on goods entering the US from Mexico and Canada took effect on 4 March, only to then get rolled back on 6 March, following direct calls between Trump and the leaders of Mexico and Canada.
In addition to driving significant market fluctuations, the moves are likely to have a political impact on the two US neighbours. In Canada, Trump’s adversarial stance has “resurrected” the ruling Liberal Party’s 2025 electoral bid, with the centre-left party gaining 10 points in the polls in little more than a month and planning to elect a new party leader on 9 March.
In Mexico, Washington’s crackdown on migration at the southern border has been a driver of unrest. Further unrest in large Canadian and Mexican cities in response to future US trade policy shifts remains a realistic possibility.
Police clash with protestors in Argentine capital over pension reforms
On 6 March, protestors clashed with the police in Buenos Aires after attempting to march around the Argentine Congress to demand higher pensions and a reversal of medication cuts. The protests were organised in response to austerity measures introduced by President Javier Milei, who has overseen sweeping reforms aimed at reducing public expenditure, debt and inflation.
However, reports from February suggest that Milei’s reforms have drastically cut Argentina’s inflation, reducing it to a five-year low, likely indicating that further controversial reforms and cuts are on the horizon.
Major protests are likely to be organised on 8 March to coincide with International Women’s Day. The “Ni Una Menos” (“Not One [Woman] Less”) movement typically organises protests in the capital and other cities to protest issues like femicide, gender-based violence and women’s rights. The protests are likely to attract more protestors than usual due to Milei’s views on topics like abortion and in response to some of his reforms which have negatively affected childcare subsidies, women’s labour rights and the dismantling of organisations within government such as the Ministry of Women, Genders, and Diversity.
Security, Armed Conflict and Terror
Haitian police increasingly using drones to fight gangs
During this reporting period, Haitian police forces in Port-au-Prince have carried out multiple successful strikes on gang members using first-person-view (FPV) drones. On 4 March, a police FPV drone reportedly injured the leader of the 5 Segonn Gang, “Izo”, during a Carnival celebration. The use of drones is likely to allow Haitian police, and possibly the international police forces supporting them, to carry out more effective decapitation strikes on high-ranking gang members, particularly in areas where the large presence of gang members makes ground operations risky. However, as previous cases illustrate, there is a realistic possibility that such strikes will result in retaliatory actions by gangs, including the indiscriminate targeting of the civilian population.
Guyana accuses Venezuela of entering oil block in Guyanese waters
On 1 March, Guyanese President Mohamed Irfaan Ali accused a Venezuelan coast guard patrol of entering Guyanese waters. The vessel allegedly approached an offshore oil facility in an oil block operated by Exxon Mobil and sent out a message claiming the Guyanese output vessel was in “disputed international waters”. In response to the incident, Ali summoned the Venezuelan ambassador and instructed Guyana’s embassy in Caracas to file a formal protest with the government. He also deployed air assets and the country’s coastguard to ward off the threat. This constitutes the latest incident in a diplomatic spat whereby Venezuela claims the Essequibo region, which comprises approximately two-thirds of Guyana. Further tensions are highly likely amid ongoing brinkmanship by Venezuela.
Environment, Health and Miscellaneous
Windstorm-fuelled wildfires in south and central Texas
Windstorm-fuelled wildfires have broken out in south and central Texas. The latest reports indicate that the Twin Oryx Fire in La Salle County is 60 per cent contained, covering approximately 900 acres. The Onion Creek Fire in west Buda is 80 per cent contained at about 190 acres, with a containment line established. Additionally, the Duke Fire in Bexar County has been fully contained across 244 acres. The Welder Complex Fire in Sinton is at 75 per cent containment and spans an estimated 785 acres. Evacuation orders in Sinton have been lifted after the wildfire destroyed at least 20 homes. A red flag warning has been issued for critical fire weather conditions across parts of Texas and neighbouring states.
Widespread power outages across Honduras
Honduras experienced widespread power outages impacting multiple regions and major cities, including Tegucigalpa and San Pedro Sula, on 1 March. The outages were initially reported without a known cause. The Honduran energy minister ruled out a failure at the El Cajon hydroelectric dam; it was later confirmed that the outages resulted from a ‘temporary and atypical failure in the interconnection between Honduras and Nicaragua.’ The outages also affected regional energy lines connected to neighbouring countries, but no widespread outages were reported outside of Honduras. All power was restored later on 1 March.
Europe, Middle East & Africa
Ukraine: US suspends military aid and intelligence sharing
On 4 March, US President Trump suspended all military aid to Ukraine with the reported aim of pressuring Ukrainian President Zelensky into agreeing to a ceasefire agreement with Russia. The suspension reportedly includes any further drawdown from the most recent USD 3.85 billion of military aid approved by Congress under former President Biden and a halt in deliveries already approved by Biden, inclusive of aid currently in transit or pre-staged in Poland. The decision to suspend military aid was followed by a ban on US intelligence sharing with Ukraine, which extended to US-derived intelligence being shared via third parties like the United Kingdom.
Solace Global Assessment:
The Trump administration’s decision to suspend both military aid and intelligence sharing is almost certainly a mechanism to exert pressure on Zelensky to agree to ceasefire terms that would significantly benefit the US, especially regarding favourable terms for US access to Ukrainian mineral resources. Should Zelensky acquiesce to Trump’s demands, there is a realistic possibility that the US will reverse these decisions in order to apply renewed pressure on Russia to agree to terms that align with US strategic interests.
The suspension of military aid and intelligence sharing will almost certainly result in an increase in Russian long-range missile and UAV strikes on Ukrainian population centres, critical national infrastructure and high-value targets in rear areas. Ukraine’s ability to intercept Russian aerial threats, particularly ballistic missiles, relies heavily on US aid and intelligence.
The US-derived Patriot surface-to-air missile (SAM) system is Ukraine’s most capable air defence system and Kyiv’s European allies are unable to support Ukraine with a comparable system that can provide as effective an air defence umbrella. Russia will almost certainly exploit current developments to deplete Ukraine’s Patriot missile stocks by increasing its layered, near-simultaneous long-range aerial attacks on multiple axes.
A critical shortage in Patriot interceptors will almost certainly make Ukraine more vulnerable to long-range Russian attacks, severely degrade its ability to intercept Russian ballistic missiles, and enable Russian air with more freedom of movement. Kyiv will likely be forced to prioritise its remaining air defence resources to defend major cities like Kyiv, leaving smaller cities, rear areas and frontline positions more vulnerable to Russian attack.
The suspension in intelligence sharing will further expose Ukraine to Russian aerial attacks. The US provides Ukraine with satellite reconnaissance, radar tracking, and signals intelligence (SIGINT) to detect missile launches and drone movements. This allows Ukraine to issue air raid alerts, prepare air defence and increase its ability to intercept incoming threats.
A loss of this vital intelligence will degrade Ukraine’s situational awareness, reduce reaction time, overwhelm air defence and likely force Ukraine to adopt a more reactive rather than proactive air defence strategy. Ukraine will also likely be forced to rely more on its own air defence radars to compensate for the loss of early warning.
These radar systems are high-value targets (HVTs) for Russia. If forced to radiate for extended periods, Ukrainian radars will be more detectable to Russian SIGINT and thus easier to target, jam, deceive or map out, further degrading Ukraine’s aerial defences.
Ukraine’s frontlines are unlikely to be immediately affected by the suspension of military aid. 90 per cent of US-derived weapons and munitions are already in-country, and Ukraine has increased the domestic production of UAVs, which it is using extensively for frontline operations.
Assessments in late February indicated that Ukraine could maintain its current operational tempo until approximately mid-2025 (around June), provided that the US continues delivering the aid previously agreed upon under the Biden administration’s planned schedule. However, if the suspensions on military aid and intelligence are sustained, Ukraine’s ability to defend its frontlines and the effectiveness of its counteroffensives will almost certainly be severely degraded.
Ukraine is still heavily dependent on US-derived long-range systems such as the High Mobility Artillery Rocket System (HIMARS) and the Army Tactical Missile System) (ATACMS) to target Russian dynamic HVTs in rear areas. Whilst Ukraine still has access to these systems, it lacks the intelligence, surveillance and reconnaissance (ISR) assets to effectively find, fix and finish Russian HVTs in the deep battlespace.
Without this targeting capability, Ukraine’s ability to strike Russian logistic nodes, command and control centres (C2), force concentrations, ammunition depots and other HVTs will be severely degraded, further allowing Russia to seize the initiative on the ground.
Syria: Armed clashes erupt following operations against Assad regime loyalists
At least 70 people were killed during a series of armed clashes between security forces and Assad-loyalists between 4 and 6 March, including at least 13 Syrian security officers. The fighting was most intense in the northwestern coastal governorates of Latakia and Tartus, and in the Daraa Governorate in southwestern Syria. Unconfirmed reports also indicate that clashes took place in Homs and Aleppo.
These mark the deadliest attacks against the security forces of Syria’s new Hay’at Tahrir al-Sham (HTS)-led interim government since the December 2024 overthrow of the Assad regime. The clashes followed operations targeting Assad-regime remnants, with armed groups in many cases ambushing security forces.
Anti-government protests took place in the port cities of Latakia and Tartus, with authorities imposing curfews which are ongoing as of 7 March. Moreover, supporters of the HTS-led government participated in demonstrations in numerous cities, including Damascus, Manbij and Idlib.
Solace Global Assessment:
In addition to the Syrian Arab Army (SAA), a nexus of sectarian militias and decentralised armed groups supported the Assad regime. Following the HTS-led lightning advance that toppled the regime, the SAA collapsed with many personnel and senior officers going into hiding or fleeing into neighbouring Iraq. HTS has highly likely taken a “carrot and stick” approach, by offering clemency for lower-level officers and soldiers if they hand in their weapons to the state, while simultaneously conducting combing operations to root out armed remnants and higher-level officers that are implicated in war crimes. It is highly likely that many units have simply gone underground and integrated into local militia groups.
It is likely that the clashes are indicative of a nascent insurgency by these groups, which would highly likely receive support from Iran. The loss of Syria has been a critical strategic defeat for Tehran. In the past week, an official declaration was made for the creation of a new group named the “Islamic Resistance Front in Syria”, which is highly likely an Iranian Islamic Revolutionary Guard Corps (IRGC)-linked project. It is likely that Iranian support for regime remnants groups and insurgent activity will operate primarily out of Iraq, which can be used as a staging post for the infiltration of Shia militia fighters and the smuggling of arms. It is likely that clashes will continue to occur in response to combing operations, particularly in the Alawite stronghold governorates of Latakia and Tartus.
Israel & Palestine: US rejects Egypt Gaza plan, growing violence in the West Bank
The 4 March Arab League summit in Cairo produced a new, three-stage plan for the reconstruction of Gaza. The plan envisions a three-year reconstruction period, and the creation of a Palestinian Authority (PA)-backed “technocratic government” supported by an Egypt- and Jordan-trained police force. The Gaza Strip is currently undergoing a week-long aid blockade, which has resulted in worsening conditions for the civilian population and growing fears of collapse in the ceasefire.
The US has so far ignored the Arab League plan and remains committed to the controversial “Riviera” plan, which envisions the displacement of Gaza’s population. Washington has, for the first time since 1997, established direct communication channels with Hamas and increased pressure on the group, pledging to collapse the ceasefire if all remaining Israeli hostages are not released. At the same time, US Middle East envoy Steve Witkoff has renewed calls on Israel to respect the ceasefire at least until his visit to the region.
Israel Defence Forces (IDF) operations in the West Bank, which started on 21 January, have continued. More than 50 Palestinians have been killed during the ongoing operations. IDF units are continuing to demolish homes in the Nur Shams refugee camp and to carry out raids in Tulkarm, Tubas, and Jenin. Israeli settler groups have attacked Palestinian villagers in the Masafer Yatta area.
Solace Global Assessment:
The Arab League peace plan likely contains important concessions to Tel Aviv and Washington. It effectively sidelines Hamas by vesting authority in PA technocrats and possibly establishes a deterrence in the form of a local police force trained by Egypt and Jordan. At the same time, however, the plan clashes with US calls to displace, likely permanently, Gaza’s civilian population, which is almost certainly unacceptable to Cairo and Amman, as well as other Arab states. The US’s approach towards Hamas likely combines inducements and, more importantly, threats.
While the direct channel of communication offers Hamas a way to negotiate a deal bypassing Israel, the renewed threats of collapsing the ceasefire are almost certainly deepening the group’s worries about its future after losing its main source of political leverage on Tel Aviv, the hostages. The impasse is likely to further destabilise the ceasefire, particularly if Hamas leaders in Gaza feel that their negotiating position is unrecoverable.
In the West Bank, the continuation of Israeli operations likely reflects Israeli assessments of Washington’s support. The Trump administration removed sanctions on Israeli settler groups and has made important overtures to the Israeli far-right. Most notably, on 6 March, Israeli Finance Minister Bezalel Smotrich, leader of the ultra-nationalist Religious Zionism party, met with his American counterpart in Washington. This represents a notable shift from the Biden administration, which had refrained from inviting Smotrich for bilateral talks. Further Israeli operations and settler violence are highly likely to further damage the already precarious position of the PA in the West Bank.
Ghana: Government reintroduces repressive anti-LGBT bill
A group of ten Ghanian members of parliament have resubmitted a controversial bill that, if signed into law, will impose strict restrictions on LGBT rights and the LGBT community. The bill will impose a three-year jail term for individuals who identify as LGBT and five to ten years for promoters or advocates of LGBT rights. The bill passed a parliamentary vote in 2024 but was not signed into law by former President Nana Akufo-Addo, who cited legal challenges, and was then dropped following the dissolution of parliament in 2024 ahead of the general election.
Solace Global Assessment:
The initial legal challenges against the bill have been dismissed by the Supreme Court of Ghana, clearing the way for the bill’s resubmission and likely approval. The majority of Ghanaian political parties, including the National Democratic Congress (NDC), which controls parliament and the New Patriotic Party (NPP), which constitutes the largest opposition party, have expressed support for the bill, suggesting that it is highly likely to pass. If passed, the bill is likely to be part of a wider and more sustained attempt to suppress LGBT rights which has attracted widespread support in Ghana. Moreover, politicians in Ghana have expressed that they no longer need to fear economic sanctions in response to the bill, likely assessing that the current geopolitical climate favours conservatism and that Western nations are likely reticent to jeopardise relations with Ghana over a domestic issue.
The bill is likely to legitimise anti-LGBT views in Ghana and result in a significant rise in violence against LGBT individuals, particularly outside of Accra. This was observed in 2022 when the bill was originally drafted. This involved higher rates of physical attacks, arrests, police extortion and incidents of “corrective rape”. By criminalising advocacy for LGBT rights, the bill will almost certainly result in the closure of support centres and other resources for the LGBT community. While the majority of these attacks will likely target local nationals, there is a high likelihood that foreign workers or travellers in Ghana may also become targets, particularly if suspected of promoting LGBT rights within the country.
Somalia: Warning of imminent terror attacks in Mogadishu amid al-Shabaab offensive
On 2 March, the Somali National Army, alongside international partners, killed at least 40 al-Shabaab members in the Biya Cadde region of Hirshabelle State. The successful operation comes amid strategic gains by al-Shabaab, who launched an offensive on the Middle Shabelle and Hiraan regions on 20 February, recently encircling Jowhar, a town 91 kilometres north of Mogadishu and the capital of Hirshabelle State. On 4 March, Somali forces clashed with al-Shabaab in Middle Shabeele, repelling an attack in the Boos-Hareeri area of the Aadan-Yabaal district, which the Somali government has held for several years. Aerial strikes, highly likely conducted by the US, reportedly targeted al-Shabaab forces in Al-Kowthar, a town in Middle Shabelle that was seized by al-Shabaab militants last week. Ceelbaraf, an important transportation hub in the region, fell to al-Shabaab militants, despite being targeted by aerial strikes.
On 4 March, the US embassy in Somalia issued a security alert claiming that it is ‘tracking credible information related to potential imminent attacks against multiple locations in Somalia including Mogadishu’s Aden Adde International Airport.’ The warning stated that attacks may target ‘airports and seaports, checkpoints, government buildings, hotels, restaurants, shopping areas, and other areas where large crowds gather and Westerners frequent, as well as government, military, and Western convoys.’ The intelligence spurred the US embassy to cancel all personnel movements; Turkish Airlines and EgyptAir have suspended all flights to Aden Adde International Airport in Mogadishu.
Solace Global Assessment:
The renewed al-Shabaab offensive has killed at least 60 pro-government forces and aims to recapture areas taken from the insurgent group after the Somali government’s counteroffensive from 2022 to 2023. By launching an offensive, al-Shabaab highly likely aims to take advantage of the security gaps in the region caused by inter-clan fighting and Burundi’s lack of participation in the African Union Support and Stabilization Mission in Somalia (AUSSOM). Despite joint US counterterrorism efforts almost certainly slowing al-Shabaab’s ongoing offensive, al-Shabaab will highly likely continue to make territorial gains.
Since President Donald Trump took office, the US has participated in air strikes against al-Shabaab, the latest supporting Somali forces in their 2 March operation. While the embassy statement did not accuse a specific group, the intelligence was highly likely linked to al-Shabaab, who have conducted several bombings and shootings in Mogadishu in recent years. By targeting Mogadishu, the group likely aims to undermine public confidence in the Somali government and divert resources from counteroffensive capabilities to shoring up security in the capital. Furthermore, the group will likely also particularly target US personnel in an attempt to retaliate against US counterterrorism efforts and raise the profile of the attacks. While al-Shabaab are the most likely culprit, there is a realistic possibility that the intelligence was linked to Islamic State Somalia (ISS), who are currently being pushed back by Puntland forces and US air strikes.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Germany’s Christian Democrats (CDU/CSU) and Social Democrats (SPD) to start coalition talks
The return to a “Grand Coalition” between the two main centre-right and centre-left parties was made almost certain by the failure of the Free Democratic Party (FDP) to enter parliament.
The talks will highly likely result in a workable coalition, especially as, on 5 March, the two parties overcame a significant disagreement over reforming the “debt brake”. While the decision to create a EUR 500 billion infrastructure fund and to overhaul borrowing limits was hailed by the CDU/CSU as a necessary decision due to Washington’s shift in Ukraine, it likely represents an SPD victory.
As the opposition (comprised of the far-right and far-left) will only acquire its “blocking” privileges following the creation of a new government, the next SPD-CDU/CSU moves are highly likely forced: the two parties will begin talks on 7-9 March, submit the debt brake proposal for a vote early next week, and announce the coalition following that. There is a realistic possibility that the manoeuvre will drive a response from the left, including protests in Berlin and other major cities.
General strike planned for 7-8 March in Italy
Several public and private sector labour unions have announced strike action to coincide with International Women’s Day. Striking workers include railway and airport personnel. The strikes are almost certain to result in severe traffic disruptions throughout Italy starting on the evening of 7 March. On 8 March, authorities agreed with airport workers on two periods of activity, where flights will go ahead, between 07:00 and 10:00 and between 18:00 and 21:00 local time.
Flares and tear gas released in Serbian parliament
On 4 March, opposition coalition lawmakers, led by the Serbian Progressive party (SNS), discharged flares and tear gas on the first day of parliament. Three lawmakers were injured, with one experiencing a stroke and in critical condition. The incident occurred during a vote on a bill to increase university funding and was in support of the student-led anti-corruption protests, which have been ongoing since November 2024 after the Novi Sad railway station roof collapsed, resulting in 15 fatalities. This highly publicised incident will highly likely have an invigorating effect on the protests, which constitute a significant threat to President Aleksandar Vucic’s power.
Greek government faces no-confidence vote over fatal train crash
Greek Prime Minister Kyriakos Mitsotakis’ government is facing a no-confidence vote over the 2023 railway disaster that killed 57 people, with opposition parties accusing the government of shielding officials from accountability. Major nationwide protests erupted on 28 February to mark the second anniversary of the train crash. However, protests have continued in major Greek cities, including in Athens and Thessaloniki, resulting in clashes with the police and the use of tear gas and other crowd dispersal methods. Failure of the government to take action is likely to sustain protests, which may intensify on the weekend.
Tunisian opposition members tried on terrorism charges
On 4 March, a mass trial of around 40 members of the Tunisian opposition, including lawyers, journalists, and politicians, began in Tunis. Many of the defendants have charges such as “belonging to a terrorist group” or “plotting against state security”. Human rights and civil society groups have claimed that the trial is politically motivated and aims at silencing opposition voices. The trial almost certainly represents part of President Kais Saied’s broader efforts to sideline and silence opposition and civil society voices. There is a realistic possibility that the trial will drive protests in Tunis, and other urban centres.
Refugee clashes with Kenyan police amid food ration protests
On 4 March, clashes broke out between refugees and security forces in Kenya’s Kakuma refugee camp following the imposition of food and water rationing, which left many struggling to obtain essential resources. Four people were injured after security forces used live ammunition to disperse protesters. The camp is one of the largest in the world and houses approximately 200,000 refugees from various countries, including South Sudan, Ethiopia, Burundi, and the DRC. The rationing was imposed amid shortages triggered by USAID cuts, which have reportedly contributed to rising insecurity in the camp. Further unrest at refugee camps is likely amid further humanitarian aid shortages. There is a realistic possibility that it will contribute to anti-US sentiment in towns and cities close to the refugee camps.
At least 16 protesters injured during march in Maputo, Mozambique
On 5 March, security forces shot and injured at least 16 protesters during a march in Mozambique’s capital, Maputo. Opposition figure Venâncio Mondlane was leading the demonstrations, which took place hours before the controversially elected President Daniel Chapo signed a political agreement with opposition parties which would end the post-election protests. Mondlane’s current whereabouts is reportedly unknown.
Despite the winding down of the unrest that has so far led to at least 353 deaths since October and Mondlane’s agreement to engage in opposition via political means, the continued demonstrations reflect the continued frustration with the government. Security forces’ use of live ammunition has typically triggered unrest to spiral into clashes and the well-publicised incident will likely trigger further anti-government demonstrations. Given Mondlane’s involvement in this protest, there is a realistic possibility that supporters will view this as an attempt to assassinate Mondlane, also spurring further unrest.
Security, Armed Conflict and Terror
Car-ramming attack in Mannheim, Germany, kills two, wounds dozens
On 2 March, a car-ramming attack occurred in the southwestern German city during a Carnival parade. The perpetrator of the attack was a 40-year-old German citizen who has previously been fined for a hate speech offence in 2018. Local authorities have not disclosed a possible motive for the attack as of the time of writing.
The attack follows multiple similar car-ramming attacks that have occurred in Germany over the past few months. These have been inspired by different ideologies, from Islamist extremism (as in the case of the February attack in Munich) to far right and anti-Islam ideology (as in the attack at the Magdeburg Christmas market).
Moreover, OSINT shows a rise in extremist calls for attacks on German Carnival events in the days prior to the recent attack, including from Islamic State-linked media. There is a realistic possibility that, even if not ideologically aligned, the Mannheim attacker was influenced or inspired by notable past car-ramming attacks.
Cyberattack at Poland’s Space Agency (POLSA)
On 2 March, unauthorised access to POLSA’s IT infrastructure was detected by Polish cybersecurity, who secured the affected systems. While the perpetrators have not yet been identified, there is a realistic possibility that foreign political actors perpetrated the attack. Poland’s digital minister, Krzysztof Gawkowski claimed in January that Poland is the most frequently targeted country for cyberattacks in the European Union, having doubled since 2023, with Russia allegedly perpetrating most attacks. POLSA was highly likely targeted due to space agencies’ collaboration with military and intelligence agencies; sensitive security data was likely targeted. Further attacks on Polish cyber infrastructure are highly likely in the coming months.
Russian security kills Islamic State militants near Moscow and in Dagestan.
The Federal Security Service (FSB) reported on 3 March the killing of a Russian national who had allegedly been planning attacks on the metro service in the Russian capital, as well as on Jewish places of worship. The man had allegedly been planning to travel to Afghanistan for training. This, alongside the pro-Islamic State (IS) propaganda and the IS flag found at his apartment, make it highly likely that the man was planning his attack on behalf of the Islamic State Khorasan Province (ISKP).
On 5 March, Russian security forces also killed four alleged ISKP militants in Dagestan. According to state reports, the four were planning to conduct a bombing attack on a regional interior ministry branch. The two cases continue to highlight ISKP’s efforts to expand its attacks to Russia and replicate its 2024 Crocus Hall attack.
ISKP sees Russia as a desirable target as it likely assesses that its security services are overstretched due to the war in Ukraine. Moreover, ISKP continues to successfully radicalise Russian citizens from the Caucasus region, as well as citizens of central Asian states who can enter Russia with relative ease as migrant workers.
Turkish forces continue to target Kurdish militants despite disarmament calls
Turkey’s Defence Ministry has stated that it has killed almost 30 Kurdish militants in Iraq and Syria in the week following calls to disarm by Abdullah Ocalan, a key leader within the Kurdistan Workers Party (PKK). Turkey considers the Syrian Kurdish People’s Defense Units (YPG/J) and the Iraqi Peshmerga as extensions of the PKK and has warned that military operations will continue if disarmament efforts fail to progress. However, the US-backed Syrian Democratic Forces (SDF), which includes the YPG, has distanced itself from the PKK and Ocalan’s call, indicating that Turkish offensive operations in Syria are likely to continue regardless of developments on the domestic front.
One killed after stabbing attack in Haifa, Israel
The attack occurred on 3 March at a bus and train station. In addition to one death, the attack resulted in at least four injuries. The perpetrator was reportedly an Israeli citizen of Druze Arab origin, who recently entered Israel from Germany. The motive of the attack was not officially disclosed by authorities, but it is highly likely that it was linked to Israeli operations in Gaza, the West Bank, and Syria. Low-sophistication, “lone-wolf” attacks continue to pose a significant security threat in Israel. As other recent cases have highlighted, perpetrators frequently target high-traffic locations, including transport hubs.
Jordanian border forces clash with smugglers
On 6 March, Jordanian border forces clashed with smugglers attempting to cross into the kingdom from Syria, resulting in the deaths of four smugglers. The smugglers were attempting to exploit poor weather conditions to enter Jordan illegally, and large quantities of weapons and narcotics were seized. The incident follows recent meetings between the King of Jordan and Syria’s interim President Ahmed al-Sharaa, who have agreed to bolster border defences to combat arms and narcotics trafficking. Syria has been a key producer of captagon, while Jordan serves as a transit route for narcotics destined for the Gulf and beyond. Efforts to combat smuggling are likely aimed at preventing the resurgence of the Islamic State, which has historically profited from the trade.
Jama’at Nusrat al-Islam wa al-Muslimin (JNIM) ends blockade of Lere, Mali
On 3 March, the al-Qaeda-affiliated JNIM ended the blockade of Lere. The blockade lasted approximately three months and disrupted supply routes and movement in Timbuktu. Lere is a significant crossroad town in the region and serves as a market as well as a base for humanitarian groups operating in the region. Residents faced significant resource scarcities and those travelling from Timbuktu were forced to take a detour via Douentza and Mopti.
Despite the lifting of the blockade, residual effects are highly likely in the coming months as seasonal economies including agriculture can be negatively affected by blockades, impoverishing families for years. Siege tactics have increasingly been deployed by insurgent groups in Mali to disrupt local economies and restrict access to humanitarian organisations. Furthermore, blockades aim to force local militias to disarm and undermine local governance to create a security vacuum, which armed groups aim to fill.
Opposition party figures arrested in South Sudan after being accused of allying with militia
On 4 March, Petroleum Minister Pout Kang Chol, General Gabriel Duop Lam, and several other Sudan People’s Liberation Movement-in-Opposition (SPLM-IO) members allied with First Vice President Riek Machar were arrested in their homes. Military personnel were also deployed around Macher’s residence.
An SPLM-IO spokesperson has labelled the act a “grave violation” of the fragile 2018 peace agreement that ended the civil war by establishing a power-sharing arrangement between rival factions. The arrests follow significant fighting in Nasir between national forces and the White Army militia, who are mostly made up of the Nuer ethnic group in common with Machar.
Information Minister Michael Makuei, in justification for the arrests, accused Machar loyalists of collaborating with the White Army to attack Nasir on 4 March. This incident marks a significant escalation in internal tensions and increases the likelihood of a renewed civil war.
Puntland forces continue to make gains against the Islamic State Somalia Province (ISS)
The armed forces of the breakaway territory of Somalia continued their offensive in the Cal Miskaad mountain range. Puntland forces took the stronghold of Dhasan and completed the “second phase” of “Operation Hilaac”, as the offensive has been named. The high presence of foreign nationals, especially from the Arab Peninsula, among ISS forces continues to be noted by advancing Puntland forces.
The offensive, which has been ongoing for weeks, has likely significantly damaged ISS’s capabilities in the area, and there are reports that ISS forces have split in three groups, retreating towards the mountainous Karinka Qandala area, Tog Miraale and Tog Curaar respectively. US and UAE airstrikes have almost certainly played a fundamental role in the successes of the operation so far.
The airstrikes are likely to help prevent ISS units from reforming in more remote areas where the ground-based Puntland units are likely to find considerable logistical and operational difficulties. ISS controls the al-Karrar office, one of IS’s nine regional offices and increasingly a key hub for the financing of IS affiliates in Africa and Afghanistan.
Environment, Health and Miscellaneous
Isolated Depression at High Levels (DANA) causes heavy rain and flooding in eastern Spain
Eastern Spain continues to grapple with severe weather conditions as a DANA, a high-altitude isolated depression, persists, bringing heavy rain and flooding to several regions. The lowest level emergency alert has been issued for residents living along the Hozgarganta River in Andalusia due to anticipated heavy rainfall.
Additionally, Madrid is under a yellow alert for heavy rain expected between 18:00 and 21:00 local time. The Canary Islands have reported around 20 vehicles affected by floods, while flight operations at Gran Canaria Airport have resumed normality after being disrupted by floodwaters.
An orange alert remains active for heavy rain in Valencia, Castellón, and Almería, with yellow warnings for areas including Albacete and Navarre. The Spanish authorities have also initiated a “pre-emergency phase” of the flood plan in Andalusia. Flooding has already impacted infrastructure, with at least 11 roads affected in Castellón and Valencia, and the road between Alcalà de Xivert and Coves de Vinromà entirely cut off.
Flooding in greater Johannesburg, South Africa
Flooding in greater Johannesburg on 5 March has caused significant disruptions. A bridge on Platina Street in the Jukskei Park area of Randburg has suffered considerable damage due to the overnight flooding. The local utility company has reported power outages in the Hurst Hill neighbourhood and indicated that restoration efforts are hampered by the ongoing weather conditions. Emergency services have shared videos of roads inundated by floodwaters in the Newlands area, advising motorists to exercise caution. The Klein Jukskei River has overflowed, leading to at least one vehicle becoming stranded. The flooding has predominantly affected the Randburg area, with several low-lying roads being impacted and reports of structural damage in residential neighbourhoods.
Asia–Pacific
Pakistan: Islamic State Khorasan Province (ISKP) regional commander charged by US
On 2 March, the Mohammad Sharifullah, or “Jafar”, a regional ISKP commander, was charged by the US with “providing and conspiring to provide material support and resources to a designated foreign terrorist organization resulting in death.” The charge comes after Pakistani security forces captured Sharifullah along the Pakistan-Afghan border region in late February before transferring him to the FBI for extradition. US President Donald Trump thanked the Pakistani government for their cooperation, stating, “I want to thank, especially, the government of Pakistan for helping arrest this monster.”
According to an interview with the FBI on the same day he was charged, Sharifullah admitted to helping plan the August 2021 bombing in Afghanistan, also known as the Abbey Gate attack, which killed 170 Afghans and 13 US troops. Sharifullah reportedly scouted a route to the airport for the attacker and checked for law enforcement and security checkpoints, giving the all clear to the attacker. Sharifullah also admitted to conducting surveillance to prepare the suicide bomber behind the 20 June 2016 attack on the Canadian embassy in Kabul as well as sharing instructions on how to use weaponry to the 22 March 2024 Crocus City Hall attackers.
Solace Global Assessment:
If Sharifullah is convicted, he faces a maximum penalty of life imprisonment. The arrest is hailed as a major victory against ISKP, Sharifullah being ‘the top terrorist responsible for that atrocity’ (referencing the Abbey Gate attack), according to Trump. US officials have announced that Sharifullah was one of two members involved in the planning of the bombing. Sharifullah’s arrest marks a symbolic victory for the Trump administration, who likely wants to portray his counterterrorism operations as a continuation of the hardline approach that led to the territorial defeat of Islamic State in Iraq and Syria (ISIS) and the killing of ISIS leader Abu Bakr al-Baghdadi in 2019.
The arrest and extradition of Sharifullah are likely indicative of renewed cooperation between the US and Pakistan over counterterrorism. In response to Trump’s comments regarding the government of Pakistan, Pakistani Prime Minister Shehbaz Sharif emphasised that ‘we will continue to partner closely with the United States in securing regional peace and stability’. This is highly likely because of pressure from the US to increase counterterrorism operations and will likely trigger ISKP reprisal attacks in Pakistan.
The operation follows a period of limited bilateral cooperation since 2021, stemming from US concerns over Pakistan’s alleged support for the Afghan Taliban, which Pakistan denies. The Pakistani government’s cooperative role in the operation, which involved the CIA and FBI, was almost certainly a signal to the Trump administration, indicating that Islamabad wants to strengthen counterterrorism relations. If bilateral cooperation increases significantly, this will almost certainly bolster Pakistani security forces’ counterterrorism capabilities and assist in their counterinsurgency operations in the restive Balochistan and Khyber Pakhtunkhwa regions.
Taiwan: Chinese military exercises continue as TSMC announce more investment in US
On 3 March, the Taiwan Semiconductor Manufacturing Company (TSMC) announced a deal with US President Donald Trump to invest an additional USD 100 billion into the US, with plans to build five additional chip fabrication plants. The TSMC chief executive CC Wei stated that the deal will mean that TSMC will produce the most advanced chips on US soil. A Taiwanese government spokesperson, however, promised that Taipei will ensure that the most advanced manufacturing processes will be kept in Taiwan.
On 4 March, the Taiwanese Ministry of National Defence reported that 19 sorties of People’s Liberation Army (PLA) aircraft, five People’s Liberation Army Navy (PLAN) vessels and three “official ships” were detected operating around Taiwan. 11 of the 19 PLA sorties are claimed to have crossed the median line, entering Taiwan’s southwestern Air Defence Identification Zone (ADIZ).
Solace Global Assessment:
TSMC produces approximately 90 per cent of the world’s most advanced semiconductor chips, which are critical for technologies such as smartphones and artificial intelligence (AI). A Chinese invasion of Taiwan would highly likely cause a global economic crisis, with some estimates predicting a loss of approximately ten per cent of global GDP, significantly worse than the 2008 global financial crisis, the Covid-19 pandemic, and the war in Ukraine. With major US companies such as Apple and Nvidia so critically dependent on TSMC semiconductor manufacturing, in addition to advanced military technology, it is highly likely a strategic priority for the Trump administration to increase chip fabrication on US soil to mitigate against the impact of Taiwan’s potential invasion or blockade.
For Taiwan, the monopoly on advanced semiconductor manufacturing is almost certainly a key strategic deterrence against a Chinese invasion, with the US being economically motivated to contribute to Taiwanese deterrence with security guarantees. This highly likely explains Taipei’s desire to restrict the production of the most advanced chips in US facilities. The Trump administration, however, has likely compelled TSMC’s compliance with the threat of tariffs, with Trump stating that the deal will mean that TSMC will be excluded from industry-wide 25 per cent tariffs.
The regularity of PLA exercises around Taiwan is increasing. In February, 480 PLA aircraft and 223 PLAN vessels were detected around Taiwan, a 40 per cent increase from January. The exercises are also becoming increasingly complex, with warnings from senior Indo-Pacific US military commanders that PLA activity now often resembles rehearsals for an invasion involving multi-domain operations. In addition to the training benefits for the Chinese military, the exercises are highly likely intended to make it more difficult to discern between drills and a genuine invasion of Taiwan, complicating response. There is also a realistic possibility that the recent increase in exercises is due to a desire in Beijing to test Donald Trump’s willingness to defend Taiwan, with the US’s reliability as a military ally likely brought into question by Trump’s more isolationist foreign policy posture.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Crime soars in Bangladesh due to widespread insecurity
Several reports have indicated that crime rates in Bangladesh have noticeably increased in late 2024 and early 2025, with the country recording the highest number of robberies in six years in January 2025. Moreover, there are increasing reports of police corruption, as well as security forces’ growing inability to deal with both petty and violent criminality. These trends have likely been partly worsened by the administrative and political instability that followed Sheikh Hasina’s ousting in August 2024. While nominally independent, the Bangladeshi police, alongside other state institutions, had been previously controlled by Hasina’s Awami League (AL), and the parties that support the post-Hasina government are currently seeking to purge it of pro-AL elements. This, in turn, has likely weakened the police and has opened more space for institutional corruption.
15 injured in accidental bombing by South Korean air force jets
On 6 March, eight bombs were dropped by two jets on the civilian district of Pocheon, South Korea, injuring 15 and damaging several houses and a church. The bombs were mistakenly dropped during military exercises near the demilitarised zone along the border with North Korea. The accident reportedly occurred because the pilot entered the incorrect coordinates. Further live-fire exercises have been suspended until a review of the incident has taken place. Residents in the area have protested the exercises for years; demonstrations will likely take place as a result of this incident.
Security, Armed Conflict and Terror
President Putin hosts Myanmar junta leader at the Kremlin
On 4 March, Putin held talks with General Min Aung Hliang, the head of Myanmar’s junta government, to discuss increased cooperation amid sanctions and isolation from the West. Russia remains a major supporter of Myanmar and one of the country’s primary arms suppliers. Russian-made fighter jets and other weapon systems have been used extensively by the junta in attacks on rebel forces and the civilian population across Myanmar. While many of the topics discussed centred on economic cooperation, it is likely that military and security collaboration were also key areas of discussion. Russia is expected to continue supplying Myanmar with advanced weaponry, including aircraft, air defence systems, and other military technology in exchange for a strategic foothold in Southeast Asia and improved access to the Indian Ocean, especially if it senses that an end to the Ukraine war is drawing closer. Russian military aid to the junta will likely prolong the current civil war and result in higher rates of civilian casualties.
Environment, Health and Miscellaneous
Severe weather causes avalanche in northern India
On 28 February, an avalanche hit the town of Badrinath in India’s Uttarakhand state. Rescue operations concluded on 2 March with the recovery of the last missing person from the avalanche site. The final death toll stands at eight, while 46 individuals have survived the incident. The avalanche initially left several people trapped, prompting a large-scale search and rescue effort. In addition to the avalanche, severe weather conditions, including heavy snow and rain, have caused further disruptions in the region, such as landslides blocking highways and flash flooding damaging homes and infrastructure in Himachal Pradesh.
On the east coast of China, unusual weather conditions cause snowfall and heat waves
During the 1-3 March period, severe blizzards and snowfall were recorded in the province of Shandong, south of Beijing. The severe weather caused widespread travel and business disruptions, including office and school closures and multiple red alerts. At the same time, the area of Shanghai reported record heat for this time of the year, with temperatures of up to 28.5 degrees Celsius. Last year was reported as being the hottest on record in China.
Flooding in Indonesia’s Western Java Island
Recent severe weather in Indonesia has triggered flooding in West Java. Flooding has been widespread across western Java, with significant impacts reported in East Jakarta, Tangerang, and Depok City, where evacuations were underway. On 3 March, two bridges collapsed in Cisarua due to rising river levels, though no injuries were reported.
The flooding has also affected Baureno in Bojonegoro Regency, preventing residents from leaving their homes. On 4 March, flash floods in Cisarua, Bogor, resulted in one fatality and affected over 300 people. On 7 March, a landslide in Sukabumi City killed at least one person, with seven others missing.
Flooding in Simpenan, Sukabumi Regency, led to one death and injured seven others, with around 200 people displaced in shelters. Severe flooding in Bekasi submerged areas with waters reaching up to nearly 10 feet, prompting evacuations. Further flooding and disruptions are highly likely.
Cyclone Alfred approaching landfall on Australia’s east coast
Cyclone Alfred is set to make landfall on Australia’s east coast on 8 March at approximately 00:00 UTC with sustained wind speeds of approximately 80 km/h. The cyclone caused significant disruptions and damage across parts of Australia, particularly in New South Wales and Queensland. More than 38,000 homes and businesses in New South Wales and 56,000 customers in southeast Queensland are without power due to the cyclone’s impact. Emergency crews are working to restore power where it is safe.
Residents in areas such as Moreton Island, Redland City, and the Gold Coast have been advised to take shelter due to heavy rain and winds. Evacuations have been ordered in several locations, including Kings Point Park in Macksville and Belongil Beach, due to flooding concerns. One person is reported missing after being swept into floodwaters near Megan, Australia.
Supermarkets and distribution centres in Queensland are gradually closing as the cyclone approaches Brisbane. Additionally, public transport from Noosa to the New South Wales border will be closed.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence

Executive Summary
Americas (AMER)
The recent attacks by the Viv Ansanm gang coalition in Port-au-Prince, Haiti, highly likely demonstrate the vulnerabilities of the Kenya-led multinational police force in terms of manpower and resources.
In Colombia, the ELN’s continued offensive has almost certainly resulted in a collapse of President Petro’s total peace plan, and the government’s response will likely result in increased attacks across Colombia.
Europe, Middle East & Africa (EMEA)
The is a realistic possibility that Islamic State-affiliated media calling for attacks on festivals in Germany and the Netherlands will inspire lone-wolf attacks during the carnival season.
The release of a damning report on the eve of the Tempi train crash disaster anniversary has almost certainly intensified anti-government protests in Greece that have resulted in multiple arrests and violent clashes.
The approval of a draft minerals agreement between the US and Ukraine likely increases Trump’s interest in supporting Ukraine but is highly unlikely to satisfy Kyiv’s key objective of security guarantees.
The deployment of IDF tanks to the West Bank is almost certainly indicative of a long-term operation that will likely jeopardise ceasefire negotiations, increase the terror threat in Israel and draw Iranian attention.
Syria’s National Dialogue Conference was highly likely rushed and HTS-dominated. The exclusion of SDF representatives likely increases the risk of a confrontation between Syria’s Kurdish factions and Damascus.
There is a realistic possibility that Israeli operations in southern Syria will further expand by exploiting Druze divisions and dissatisfaction with Syria’s HTS-led authorities.
Rapid Support Forces (RSF) will highly likely cement control over Sudan’s Darfur region after forming a parallel government and losing territory around Khartoum.
Unrest likely following Cyclone Garance’s landfall on the French territory of Réunion.
Asia-Pacific (APAC)
Pakistani authorities are on high alert after the release of credible intelligence indicating that extremists are likely to kidnap foreign nationals during the ICC Champions Trophy cricket tournament.
North, Central and South America
Haiti: Gangs launch another wave of attacks on capital
On 25 February, gangs reportedly associated with the coalition Viv Ansanm launched an attack in the Delmas 19 and Delmas 30 neighbourhoods of Port-au-Prince, killing at least 15 civilians. Further clashes in the previous days resulted in one policeman of the international Kenya-led mission being killed, as well as two local soldiers. On 27 February, Viv Ansanm members launched a further attack in the Rue Chavannes area of the capital. According to UN sources, more than 6,000 people have been forced to leave the areas of Kenscoff and Delmas in recent days.
Solace Global Assessment:
The Viv Ansanm coalition of gangs likely remains the strongest criminal group in the capital. While the group’s leaders have at times called for its recognition as a political party, the gang continues to adopt a terror-focused strategy which is likely aimed at ensuring the breakdown of all administrative authority in Haiti, thus forcing civilians to rely on them for support. The recent gains and offensives made by the gangs are likewise highly likely indicative of the continuing difficulties of the international policing mission. The Kenya-led contingent currently has about 1,000 officers, less than half of the 2,500 initially planned. Moreover, UN Secretary-General Antonio Guterres has ruled out the deployment of a military peacekeeping mission to Haiti and has instead proposed increasing the amount of non-lethal UN support to the police force. This is likely a direct rejection of the recent Human Rights Watch report calling for the UN to establish control over the mission.
Colombia: ELN close to securing major cocaine hub
After initiating an offensive against government forces in January, the National Liberation Army (ELN) is close to securing full control of the Catatumbo region in the department of Norte de Santander on the border with Venezuela. The area is a major cocaine production hub and lies on vital smuggling routes. The ELN’s campaign has resulted in the near-total destruction of its last major rival in the area, the 33rd Front, a dissident group of the Revolutionary Armed Forces of Colombia (FARC). As part of a wider offensive against both government forces and rival armed groups, the ELN has conducted attacks in other parts of Colombia. In Cúcuta, the capital of the department of Norte de Santander, a 48-hour curfew was imposed on 23 February following a series of violent attacks by the ELN that injured several people.
Solace Global Assessment:
The scale of violence in Colombia almost certainly represents an end to President Petro’s policy of total peace and the championing of ceasefire agreements. Political rivals have indicated that armed groups have simply exploited the peace talks to regroup, rearm and consolidate power and control over illicit activities. This has placed armed groups like the ELN in a much stronger position to challenge the government’s authority and take on government forces. The scale of violence has almost certainly left the Petro administration with no choice but to confront the ELN and other armed groups with force, with external pressure also likely coming from the Trump administration which has called for an aggressive crackdown on drugs and criminal groups in Latin America.
Currently, the violence is primarily concentrated in the border regions. However, the ELN has a major presence across multiple departments in Colombia and has demonstrated its ability to conduct attacks in major cities like Bogotá, Cali, Medellín and Barranquilla. As the government deploys more troops to counter the ELN in the border regions, the ELN will likely increasingly target Colombian cities. These attacks have traditionally involved IED attacks against Colombian police and military installations, with previous attacks also resulting in high levels of civilian casualties. Furthermore, there is already evidence that other armed groups are exploiting the current destabilisation of Colombia to stage attacks and exert control in other areas, which has prompted a warning from the UN Human Rights Office. On 24 February, a bomb injured 17 people, including several children, in the town of Morales in the Cauca department in Colombia’s southwest. This attack has been attributed to the Central General Staff (EMC) – a splinter group of the FARC that rejected the peace agreement.
As the violence increases, the ELN are likely to impose more “armed strikes” and the government are likely to introduce more curfews. These will almost certainly involve restrictions on movement, disruptions to essential services and shortages in critical goods. ELN armed strikes have traditionally involved strict penalties for anyone not complying with their rules, including executions, which can extend to individuals with non-combatant status including healthcare workers and aid workers. They have also involved attacks on key infrastructure, such as bridges, electricity, and communication networks, designed to hinder the government’s ability to restore order but also result in further disruptions and shortages. In Norte de Santander department alone, it is now estimated that the violence and displacement have left over 122,000 people in critical need of humanitarian aid, with 36 per cent of surveyed shelters reporting no health services available.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
New round of 50501 protests to coincide with State of the Union Address in US
50501 (“50 states, 50 protests, one day”) is a decentralised protest movement which originated on the social network Reddit and has received considerable support from mainstream Democrat Party figures. The group staged protests in February and has announced a new round of unrest to occur on 4 March, the day US President Donald Trump is scheduled to deliver a speech at a joint session of Congress. Open-source intelligence (OSINT) indicates that multiple protests are organised to occur in the proximity of state capitol buildings in multiple cities. As of the time of writing, protests are scheduled to occur at 43 state capitals. Moreover, further demonstrations are scheduled to occur in Vancouver and other cities in Canada, also on 4 March.
US threatens 25 per cent tariffs on EU imports
US President Donald Trump stated on 26 February that the US is planning to impose cross-sector tariffs of around 25 per cent on EU imports. Trump singled out carmakers as a potential target and remarked that the EU bloc was formed to “screw” the US. Brussels has pledged to impose immediate retaliatory sanctions if Washington proceeds with the threats. According to US media, French President Macron tackled the issue of tariffs during his meeting with Trump on 26 February. Trump’s statement may result in further anti-US demonstrations in EU capitals, with some having already occurred following the US change in its policy towards Ukraine and Russia.
Security, Armed Conflict and Terror
Senior Sinaloa cartel member arrested in Mexico
The Mexican army said it had arrested Jose Angel Canobbio, the head of security for one of the sons of jailed drug lord Joaquin “El Chapo” Guzman, in Culiacan. The arrest is likely an important political victory for the Mexican government, which is almost certainly in the process of taking a harder stance towards the cartels to appease the demands of the US government. During this reporting period, Mexican authorities made further gestures towards Washington, including allowing the extradition of H-2 cartel leader Jesus Ricardo Patron Sanchez to the US. Mexican President Claudia Sheinbaum has maintained a more balanced public rhetoric, stating that she would support a constitutional reform to reinforce Mexico’s sovereignty in response to US drone flights in Mexican airspace, and pledging to scrutinise US weapons manufacturers, due to their firearms reaching Mexican criminal organisations.
Environment, Health and Miscellaneous
Texas records first US measles death in more than a decade
US health authorities have recorded an outbreak of measles in West Texas, with at least 130 cases reported as of the time of writing. The child, who died on the night between 25 and 26 February, was reportedly not vaccinated against the disease. According to US media sources, the disease outbreak has primarily affected “under-vaccinated” Mennonite communities in the Gaines County area. Measles has a mortality rate of between one and three per 1,000 cases on average according to the US Centres for Diseases Control and Prevention (CDC). Due to the disease’s high transmissibility, further cases are likely to occur.
Blackout in Chile affects 90 per cent of the population
On 25 February, Chile experienced a major blackout that affected over 90 per cent of the population, disrupting critical services, industries, and infrastructure across the country, impacting 14 out of 16 regions. The outage was caused by a malfunction in the protection systems of ISA Interchile, a subsidiary of the Colombian state-owned company ISA. This led to the disconnection of a key high-voltage transmission line, triggering a nationwide power failure. Power was restored to 94 per cent of households by 26 February, however, millions of people still remain without power.
Europe, Middle East & Africa
Germany and the Netherlands: Police warn of threat to carnivals
German police have stated that they are on high alert ahead of the annual pre-Lent carnival season, in response to social media content linked to the Islamic State (IS) calling for attacks on revellers. A German-language propaganda site purportedly associated with IS published an image which encouraged supporters to “choose your next target” next to a listing of carnival events in Germany and the Festival of Love event in Rotterdam, the Netherlands. Germany is set to hold major carnival festivals from late February to early March in Cologne, Nuremberg, Düsseldorf, Mainz and multiple other locations across the country. While no specific plot has been identified, German and Dutch police have stated that security will be enhanced and that they are monitoring the situation. Munich has cancelled its carnival after the recent car-ramming attack.
Solace Global Assessment:
There is a high likelihood that the propaganda image published has no direct association with IS and is instead an attempt by sympathisers or unaffiliated extremists to spread fear and disruption. However, in the aftermath of the German election, which was characterised by the far-right Alternative for Germany (AfD) party achieving its greatest-ever result, strong anti-migrant rhetoric and policies as well as a series of high-profile Islamist-linked attacks, the terrorist threat in Germany is likely significantly higher than usual. Even if the image is not directly linked to IS itself, the effect it may have cannot be discounted given the heightened tensions across the country. The carnival, with its historic links to Catholicism, provocative symbolism, and large, often inebriated and vulnerable crowds, would almost certainly be viewed as a high-profile and coveted target for extremists.
Previous carnivals, such as the 2015 carnival in Braunschweig, Bavaria, have been cancelled due to concrete evidence of a planned terror attack, and previous carnivals in Cologne and Düsseldorf have enhanced security measures in response to credible threats. There is a high likelihood of further material being disseminated online in both public and private channels before the events. As a result, the threat is likely to be taken seriously by the authorities and will almost certainly result in enhanced security measures involving stricter crowd control measures, increased screening, an increased law enforcement presence and potential transport disruptions.
Greece: Anniversary of fatal train accident sparks major protests
Protests have been organised across Greece on 28 February to mark the two-year anniversary of the Tempi train crash that resulted in the deaths of 57 people and 85 injuries. Almost 400 protests have been organised, with at least 262 planned in Greece and 121 planned internationally. In Athens, the focal point for the protests will be Syntagma Square. Greek transport workers have declared a 24-hour strike, which has already left ships docked, train services suspended, and several flights cancelled. Public services, healthcare facilities, schools, cultural institutions, restaurants, shops, and other businesses will be shut down or run at limited capacity. Security measures have been heightened in Athens, including the deployment of over 6,000 police officers and the use of drones and helicopters to bolster surveillance.
Solace Global Assessment:
The primary catalyst for the protests has likely been the release of a 180-page report on 27 February, which identified that the Tempi train crash was the result of human error, which routed the train onto the same track as an incoming freight train. Independent investigators also identified that poor training, staff shortages, and infrastructural issues such as a lack of modern safety controls plagued Greece’s railway system. However, the most controversial element has likely been the release of an audio recording, which indicates that 30 of the fatalities survived the original crash but were then killed by either asphyxiation or an explosion caused by chemical solvents illegally transported on the freight train. This has almost certainly eroded trust in the government, with many Greeks expressing the belief that the government has not done anything to achieve justice for the victims. Recent polling even indicates that over 80 per cent of Greeks feel that the Tempi train disaster was one of or the worst issues in Greece, with the vast majority also expressing that they were dissatisfied with the investigations into the incident.
The convergence of the anniversary and the release of the report and the audio recording, combined with wider discontent with the government, will almost certainly energise the current round of protests. Earlier demonstrations culminated in one of the largest protest movements in Greek history, attracting an estimated 2.5 million people in Greece and within the Greek diaspora around the world. Multiple clashes between protestors and the police were observed, particularly in Athens and Thessaloniki, resulting in the use of tear gas and stun grenades to disperse crowds. While this round of protests is unlikely to attract as many participants, the heated nature of the demonstrations will likely result in violent clashes, especially as the protests have been organised on the weekend. On 1 January, Greek police were forced to use tear gas and stun grenades after protestors threw Molotov cocktails and demanded a fresh inquiry into the disaster after the release of the audio recording, demonstrating the potential for the movement to generate violent unrest. If the government fails to conduct a thorough investigation or hold anyone accountable for the disaster, there is a strong likelihood that the protests will escalate, particularly if supported by the country’s powerful trade unions.
Ukraine: Draft minerals deal agreed with US
Amid ongoing bilateral US-Russia talks which exclude Ukraine, US President Donald Trump stated on 26 February that the US and Ukraine have agreed to a minerals deal. Following two weeks of negotiations, the Ukrainian justice, economy and foreign ministers have reportedly approved a draft agreement. A previous US demand for rights to USD 500 billion of potential revenue has been dropped from the agreement. The draft agreement calls for the establishment of a jointly managed ‘Reconstruction Investment Fund’, with Ukraine contributing 50 per cent of all revenues earned from the future monetisation of all state-owned mineral, oil and gas resources (excluding current sources of revenue). Ukrainian President Volodymyr Zelensky arrived in Washington late on 27 February, scheduled to meet Trump on 28 February and sign the deal.
Ahead of the meeting, Trump appeared to backtrack on previous comments calling Zelensky a “dictator”, responding to a journalist by saying, “did I say that? I can’t believe I said that”. Trump also suggested that the US would endeavour to reclaim for Ukraine many of the “sea areas” occupied by Russia in negotiations, almost certainly in reference to the occupied areas of Zaporizhzhia Oblast and Donetsk Oblast, including Mariupol and Berdiansk.
Solace Global Assessment:
The deal will need to be approved by Ukraine’s parliament (Verkhovna Rada), with opposition MPs having already indicated substantial concerns. However, it is likely that if Zelensky’s government continues to support the deal, the Verkhovna Rada will approve it given both the majority held by Zelensky’s Servant of the People party and the pressing need to appease Trump.
The Trump administration almost certainly has two key strategic objectives in mind with the deal. Firstly, Trump has repeatedly condemned the expenditure of US support to Ukraine and wishes to recoup the losses and gain transactional benefits for the US economy. Secondly, Trump wishes to challenge China’s dominance of the global supply and processing of rare earth elements (70 and 90 per cent, respectively), which are essential components in many modern technologies. The actual quantity of efficiently accessible rare earth elements in Ukraine is, however, highly contested. Much of Ukraine’s mineral resources are also currently in Russian-occupied territory. The draft agreement refers to projects in areas “temporarily occupied by [Russia], in the event such areas are de-occupied.” There is a realistic possibility that this has conditioned Trump’s comments regarding the possibility of reclaiming some of these areas for Ukraine through negotiations, though it is highly likely that the Kremlin would never agree to give up currently occupied territory.
The deal notably only contains one phrase referencing security guarantees, saying the “US will support Ukraine’s efforts to obtain security guarantees”. Trump’s suggestion that US access to the minerals would be “automatic security” for Ukraine is highly unlikely to satisfy Kyiv’s key strategic objective of security guarantees that can deter future Russian aggression. Zelensky likely calculates, however, that by giving Trump economic interests in Ukraine, the White House will be more amenable to Kyiv’s strategic goals.
Israel and Palestine: IDF expand operations in the West Bank
On 23 February, the Israel Defense Forces (IDF) deployed armoured units, including main battle tanks, to the West Bank, marking the first time it has deployed tanks to the area in over 20 years. Tanks and armoured personnel carriers were first deployed to the Jenin refugee camp in the north of the West Bank and have since been deployed to other Palestinian refugee camps. It is estimated that 40,000 Palestinians have been displaced from the refugee camps in Jenin, Tulkarem, Nur Shams and Farea, which are now reportedly “empty of residents”. There are also reports that the IDF is destroying roads, imposing curfews, blocking access points to towns, arresting people and commandeering properties for military use. Israel’s Defence Minister has stated that the IDF will remain there for the coming year to degrade Iranian-backed groups, including Hamas and Palestinian Islamic Jihad (PIJ). PIJ have claimed that the Israeli incursions are part of a broader effort to annex parts of the West Bank.
Solace Global Assessment:
The IDF regularly raids the West Bank to kill or capture militants but normally withdraws its forces almost immediately. The use of tanks and other armoured vehicles likely signals a shift in strategy characterised by longer IDF deployments to suppress Palestinian militancy. Israel has likely partially justified its expanded operations in the West Bank after a failed terror attack on the Tel Aviv bus network. The attack was quickly attributed to militants in the West Bank by Israeli intelligence. Moreover, Iran is reportedly attempting to establish a separate front against Israel by funnelling weapons into the West Bank through its remaining supply lines. The recent escalation likely suggests that Israel is not only targeting immediate militant threats but also aiming to disrupt long-term efforts by Iran to establish a credible military threat in the West Bank.
However, Israel’s operations in the West Bank are likely to have several negative ramifications. A prolonged IDF presence and the displacement of Palestinians will almost certainly be interpreted as shaping activity for the annexation of parts of the West Bank and increased Israeli settlements. Discussions are ongoing regarding the approval of nearly 1,200 new settlement units, some of which are planned for construction deep within the West Bank. These developments are likely to provoke more settler violence, especially when emboldened by an increased IDF presence. Operations in the West Bank are also likely to fuel further militancy, which is likely to increase the threat of terror attacks within Israel, with a likely terrorist attack already occurring in Haifa on 27 February. Ongoing ceasefire negotiations with Hamas are also likely to be jeopardised, with Palestinians viewing Israeli operations in the West Bank as part of a broader effort against Palestinian resistance. Long-term, this may risk bringing Iran and its proxies more into the fight and Israeli attempts to annex the West Bank will likely energise pro-Palestinian protest movements around the globe.
Syria: National Dialogue Conference sets out principles for the new Syria.
On 25 February, hundreds of participants (with thousands attending remotely) took part in a two-day National Dialogue Conference held in Damascus. The Hayat Tahrir al-Sham (HTS)-led interim government advertised the conference as being an initial step towards the drafting of a new Syrian constitution, intended to hear the views of representatives from Syria’s highly diverse communities. At the end of the conference, a final statement made non-binding recommendations including Syrian territorial unity and sovereignty, the acceleration of government formation, the preservation and respect for minority rights, and immediate Israeli withdrawal from southern Syria.
Solace Global Assessment:
Syria, currently led by interim president and HTS leader Ahmed al-Sharaa, is set to have a new transitional government formed on 1 March. There are several key issues facing the new HTS-led authorities in Damascus, including the Kurdish-led Syrian Democratic Forces (SDF) which control northeast Syria and are actively engaged in conflict with Turkish-led forces, continuing resistance from Assad regime remnants and the status of the Alawite minority group, and the Israeli incursion in the south with recently intensified aerial strikes.
The conference was a key opportunity to engage with these issues. The conference, however, was highly likely rushed, HTS-dominated and lacking in transparency. Many attendees were reportedly invited only one to two days earlier, with some only seven hours earlier. Of the seven-member preparatory committee, five were HTS members or HTS-aligned, with no Druze or Alawite members. Only a low number of Alawis ultimately attended the conference. Crucially, no members of the SDF or the Kurdish-led autonomous administration were invited, which was justified by organisers as being due to the exclusion of armed groups. Following the fall of the Assad regime, HTS made overtures to Kurdish groups, differentiating themselves from the Turkey-led Syrian National Army (SNA) rebel group, who continue to launch operations against the SDF with conventional Turkish air support.
However, the proposed state monopoly on arms likely poses a perceived existential threat to the continued existence of autonomous Kurdish-controlled Syria, called Rojava (Western Kurdistan), in the face of Turkish-led aggression. There is a realistic possibility that if Kurdish authorities continue to be excluded and attempts are made to forcibly disarm the SDF and the People’s Defence Forces (HPG), Kurdish groups will attempt secession, which would almost certainly lead to an escalation in conflict.
Syria and Israel: Netanyahu demands complete demilitarisation of southern Syria
On 23 February, the Prime Minister of Israel, Benjamin Netanyahu, demanded the complete demilitarisation of southern Syria in the provinces of Quneitra, Deraa and Suweida “from the forces of the new regime”, further adding that no threat would be tolerated “to the Druze community in southern Syria”. This was followed by a series of Israel Defense Forces (IDF) airstrikes on 25 February, reportedly targeting former Syrian Arab Army (SAA) division bases close to Damascus and in Daraa Province. Israel’s Defence Minister Israel Katz stated that the strikes were conducted “as part of the new policy we have defined as pacifying southern Syria”. Katz added that any attempts by Syrian forces to “establish themselves in the security zone in southern Syria will be met with fire”. As a result of the developments, relatively small anti-Israel protests took place in Damascus, Aleppo, Quneitra and Daraa provinces.
Solace Global Assessment:
Following the rapid Hayat Tahrir al-Sham (HTS)-led advance that toppled the Assad regime in December 2024, the IDF launched an incursion into the UN-patrolled buffer zone in southern Syria. The IDF also conducted a significant series of aerial strikes targeting Syrian Arab Army (SAA) assets, which destroyed the majority of Syria’s sophisticated weaponry. The decades-long ceasefire between Syria and Israel is partly predicated on the buffer zone established by a 1974 UN Security Council resolution. The incursion is likely intended by Israeli authorities as strategic messaging to the new HTS-controlled Syrian government, described by one analyst as “don’t mess with us”. The move has been criticised, however, as a provocation that will generate further insecurity on Israel’s borders.
Since their ascent to power, HTS spokesmen, as well as interim President Ahmed al-Sharaa have made a distinct effort to evade questions about Israel. This week’s National Dialogue Conference did, however, conclude with demands for an immediate Israeli withdrawal from southern Syria. Al-Sharaa almost certainly wishes to present the new Syrian authorities as peaceful and does not wish to antagonise the US Donald Trump administration. However, domestic pressures demanding a greater level of resistance against Israel will highly likely increase, with anti-Israel protests likely to grow.
Additionally, Israeli leaders are almost certainly instrumentalising southern Syria’s Druze population to justify the incursion. Israel has the world’s third-largest Druze population, and in the past week launched a pilot program allowing Syrian Druze to work in the Israeli-occupied Golan Heights. There are likely growing divisions between Syrian Druze leaders. The spiritual leader of Syria’s Druze community, Sheikh Hikmat al-Hajri, expressed dissatisfaction with the National Dialogue Conference. On 23 February, a group of formerly pro-Assad Druze fighters formed the Suwayda Military Council, with the stated goal of uniting Druze militias and integrating into the new national army of the Syrian state. Al-Hajri, however, has denounced the group and called them “separatists”. There is a realistic possibility that Israel will exploit these divisions and Druze dissatisfaction with HTS governance to extend their control in southern Syria, under the stated purpose of protecting Syrian Druze.
Sudan: Rapid Support Forces (RSF) form parallel government amid territorial losses.
23 February, the RSF signed a charter in Nairobi with allied groups to form a parallel government. Meanwhile, the Sudanese Armed Forces (SAF) broke the El-Obeid siege imposed by the RSF on 23 February, which had been ongoing since April 2023. Sudanese Finance Minister Jibril Ibrahim has declared that the lifting of the siege would allow the delivery of humanitarian aid to Kordofan. In Central Sudan, the SAF made significant gains in the capital, Khartoum, pushing RSF forces out of Khartoum, Khartoum Bahri, and Omdurman. On 24 February, the RSF announced a new assault on El-Fasher, the provincial capital of North Darfur, which has been under siege since April 2023. Intense fighting around the city has impacted the Zamzam camp, which houses approximately 500,000 displaced people, making it too dangerous for Médecins Sans Frontières / Doctors Without Borders (MSF) to operate.
Solace Global Assessment:
The recent SAF gains constitute a strategic shift in the conflict, with the SAF steadily asserting control over the capital city. There is a realistic possibility that this latest offensive will lead to the SAF retaking the entirety of Khartoum for the first time since the conflict began. Breaking the siege at El-Obeid constitutes another significant victory for the SAF since it connects RSF-controlled western and southern regions of Sudan to Khartoum. The SAF will almost certainly use the strategic city as a launchpad into the RSF-controlled western regions, primarily in Darfur. The two-year siege led to significant shortages of food, water, and medical supplies for the city’s population. Lifting the siege will enable the SAF and humanitarian groups to provide much-needed relief to the population.
The RSF’s formation of a parallel government was highly likely spurred by their territorial losses in Khartoum and the weakening of their position at El-Obeid. Rumoured internal divisions within the paramilitary group have reportedly led to several high-level RSF commanders defecting to the SAF, which have likely contributed to the group’s recent territorial losses. The signing of the charter indicates that the RSF are choosing to entrench their rule over regions under their control to maintain their legitimacy amid territorial losses. By presenting themselves as a governing body, the RSF are legitimising their territorial control in a way that they are unable to do militarily by defeating the SAF.
To further legitimise its control of Darfur, the RSF will almost certainly make the seizure of El-Fasher its primary military objective, as the largest city in North Darfur and a key transport hub that will help it consolidate power over the region.
Réunion: Tropical Cyclone Garance makes landfall
On 28 February, Tropical Cyclone Garance made landfall near Saint-Andre on the French territory of Réunion. The cyclone, which has maximum wind speeds of approximately 155 km/h, has caused significant disruptions, with approximately 30 per cent of the population, or 145,000 people, experiencing power outages and 82,000 lacking access to drinking water. The highest level, Purple Alert, was issued just before landfall. After landfall, the alert was downgraded to Red, and a videoconference by the Prefecture of Réunion is scheduled to provide updates. Over 100 people are currently in evacuation centres, and 137 emergency accommodation centres have been established. In Mauritius, on the outskirts of the cyclone’s path, authorities have warned of potential storm surges and flooding, urging citizens to avoid beaches. The island’s airport remains closed due to the cyclone warning.
Solace Global Assessment:
In the aftermath of the cyclone, it is likely that significant unrest will occur. In Mayotte, a French overseas territory to the West of Madagascar, damage caused by Cyclone Chido in December 2024, which left many residents without basic necessities, triggered protests over the perceived inadequate and delayed response from the French government. While Réunion is a wealthier island and has stronger infrastructure and emergency response capabilities, it is directly in the path of the cyclone. Furthermore, the island is a popular holiday destination for French citizens and will likely receive significant media coverage; France24 has an article covering the cyclone as the top news story of 28 February.
Réunion has a history of demonstrations voicing frustrations against the French government. In November 2018, widespread violent demonstrations occurred over the cost of living as part of the “Yellow Vest” movement in France. More recently, in September 2024, protests and strikes occurred over the high cost of living. With the recent unrest in Mayotte and history of unrest in Réunion in mind, the French government will likely make a show of reacting quickly to the anticipated devastation on the island.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
German elections end in Christian Democratic victory, far-right gets best ever result
The German parliamentary elections saw the Christian Democrats union parties (CDU/CSU) secure 28.5 per cent of the vote, while the incumbent Social Democrats (SPD) fell to 16.4 per cent. The far-right Alternative for Germany (AfD) won across eastern Germany and obtained 20.8 per cent of the total vote, becoming the second force in parliament. Minor parties, like the liberal FDP and the populist-left BSW, narrowly failed to enter parliament. The far-left Die Linke unexpectedly won 8.8 per cent of the vote, likely thanks to a surge in youth support. The election results are positive for the CDU/CSU, which will almost certainly form a coalition government with a weakened SPD. The AfD, while unlikely to enter government, will likely seek to attack the CDU/CSU from the right and will seek to continue its rise as the main anti-establishment force in German politics.
Austrian coalition talks reach a deal
The talks between the centre-right Austrian People’s Party (ÖVP), the Social Democrats (SPÖ), and the liberal Neos party reached a positive conclusion, Austrian media reported on 27 February. The talks were the third attempt at forming a workable coalition government following the legislative elections in September 2024. Despite the far-right Freedom Party (FPÖ) winning the most seats, the ÖVP was tasked with leading the first round of talks, which involved both SPÖ and Neos. The first attempt by the three parties to form a coalition failed because of unresolvable disagreements. While the new talks involved the same three parties, their success was likely ensured by the risk of provoking new elections, where the FPÖ would have almost certainly increased its vote share. As part of the deal, the ÖVP is set to get the chancellorship, which will go to Christian Stocker, and the SPÖ’s Andreas Babler will be appointed vice-chancellor. To be finalised, the deal will need the approval of the Neos party, whose members are set to vote on it on 1 March.
Romanian presidential candidate Calin Georgescu arrested in large-scale operation
Georgescu was briefly detained by authorities on 26 February. Prosecutors stated they launched an investigation into Georgescu over a series of accusations, including campaign funding fraud, hate speech, and anti-constitutional acts. In addition to detaining Georgescu, Romanian security forces raided 47 properties used by the candidate’s associates, including a former French Foreign Legion member who owns the security firm providing security to Georgescu. Here, authorities reportedly found hundreds of thousands of dollars in cash, as well as a cache of heavy weapons, including grenade launchers. Some small-scale protests by Georgescu supporters were recorded after the arrest, and there is a realistic possibility of more intense unrest during the weekend.
Bosnian court sentences separatist Bosnian Serb President Dodik to one year in prison
A Bosnian court has sentenced the pro-Russia Bosnian Serb president, Milorad Dodik to one year in prison and has banned him from politics for six years for defying the top international envoy overseeing Bosnia’s peace. President Dodik has been accused of separatist actions, including an attempt to force the secession of the Republika Srpska, the Serb-run half of Bosnia, and unite it with Serbia. Dodik, who is backed by Russia, Serbia and Hungary may avoid prison by fleeing the country. However, the ruling will almost certainly aggravate ethnic tensions, potentially inciting unrest in the Republika Srpska and could potentially provoke inter-ethnic clashes. The ruling will also have geopolitical tensions, with Serbian President Vuciv calling an emergency session on 26 February.
Anti-Eurozone protests erupt in Bulgarian capital
Since 22 February, protests have been organised by supporters of Bulgaria’s far-right Vazrazhdane party in response to the country’s plans to join the eurozone. On 26 February, protestors gathered in front of the Bulgarian parliament in Sofia to voice their opposition. Previous protests have resulted in altercations with the police and multiple injuries and arrests. On 22 February, thousands of protestors demanded the government scrap the plan to join the euro, and some threw Molotov cocktails at the local office of the European Commission.
Kurdistan Workers’ Party (PKK) leader calls on the movement to disarm
On 27 February, Abdullah Ocalan, the leader of the PKK who has been imprisoned on Turkey’s Imrali island since 1999, issued an appeal to the group to disarm and transition to a democratic process to resolve the long-standing conflict in Turkey’s southeast. The appeal was read by members of the Kurdish-majority Dem party. The appeal is almost certainly a response to the recent overture made by Turkish government allies, who noted that clear steps towards ending the conflict could be supported by Ankara. While certainly historic, it is likely still too soon to assess whether the announcement will result in lower tensions in Turkish Kurdistan. Sections of the PKK still distrust Ankara, and there is a realistic possibility that they will split from the position of their jailed leader. Moreover, it is also unclear if Ocalan’s appeal will impact PKK affiliates in Syria. So far, the Syrian wing of PKK, PYD, stated they agree with the statement in principle but have not yet committed to a shift in their posture.
Ugandan opposition figure charged with treason
On 21 February, opposition politician Kizza Beslgye was charged with treason. The court rejected pleas from Beslgye’s lawyer that he be transferred to a hospital following his attempted hunger strike. The court ruling comes after Beslgye’s case was moved to a civilian court after Uganda’s Supreme Court barred the government from trying civilians in military courts. Despite the change of court, Beslgye was kept in military detention, triggering his hunger strike. In the aftermath of the verdict, minor protests broke out demanding the release of Beslgye. A video went viral on X depicting large protests marked with the description “Yoweri Museveni is playing with fire. Dr. Kizza Besigye’s detention will trigger a revolution in Uganda. It is getting started!” While the video itself actually depicted a protest from 2023, its virality may spur further solidarity protests against Museveni’s repressive leadership.
Security, Armed Conflict and Terror
Islamist lone wolf attack in Mulhouse, France, highlights Paris-Algiers rift
On 22 February, an Algerian citizen carried out a knife attack in the town centre of Mulhouse, killing one civilian and wounding five police officers. The attacker reportedly suffered from mental health issues and had espoused extremist Islamist ideology. French channels noted that the attacker had been under an obligation to leave French territory, but that Algerian authorities had refused multiple French attempts to repatriate him. Senior French politicians, including Interior Minister Bruno Retailleau, have called for the establishment of Europe-wide sanctions on Algeria and other countries that refuse to cooperate with the repatriation of non-EU nationals. A month ago, another high-profile diplomatic spat between Paris and Algiers occurred when the latter rejected the repatriation of an Algerian national who had called for targeted violence against a France-based anti-government activist.
Two arrested in France over firebombing of Russian consulate
On 24 February, two individuals allegedly threw multiple Molotov cocktails at the Russian consulate building in Marseilles. The attack, which occurred during the day, only caused limited material damages and did not result in any injuries. It is almost certain that the attack is linked to anti-Russian sentiment driven by the Russian invasion of Ukraine as it occurred on the three year anniversary of the invasion and on the eve of French President Emmanuel Macron’s meeting with US President Donald Trump at the White House.
US considers shutting down base in Alexandroupolis, Greece
The facility is an important logistical hub for US-NATO operations in southeastern Europe, and for the delivery of supplies to Ukraine. While technically not a US “base”, it is a Greek facility that the US military can access under the Mutual Defense Cooperation Agreement. There is a realistic possibility that the cessation of US usage of the facility is a diplomatic gesture towards Moscow and Ankara, the latter having repeatedly called for its closure. Moreover, the move likely reflects Washington’s drive to reduce commitments in Europe to instead prioritise the Pacific theatre.
Islamic State (IS) supporter arrested over attack plan in Turkey
Turkish authorities have arrested an Uzbek citizen who had allegedly been planning attacks at a synagogue and Jewish schools in the city of Istanbul. IS-linked or -inspired attackers have previously targeted non-Muslim places of worship in Istanbul. Most notably, in January 2024 two gunmen attacked a Catholic church in the city and killed one worshipper. IS later claimed responsibility for the attack. Authorities have stated that the Uzbek suspect had received “orders” to carry out the attack and that they identified him by infiltrating online channels where other IS supporters used “coded” language and “encryption” to carry out attack planning. This level of sophistication is indicative of IS’ renewed efforts to carry out attacks in third countries outside of its primary areas of operations. Turkey likely remains a desirable target for IS due to its participation in counterterrorism operations, its NATO membership, its relations with Israel, and its geographical proximity to the “core” IS territories of Syria and Iraq.
France withdraws from last remaining base in Ivory Coast
France has officially handed over control of its last military base in the Ivory Coast, although a small contingent of 80 troops will remain in the country in an advisory capacity, indicating that the two countries will still maintain a military relationship. The Port-Bouet base was under France’s control for almost 50 years and housed the largest remaining contingent of French forces in the region since its forced withdrawal from Burkina Faso, Chad, Mali and Niger. France’s withdrawal and the loss of key military capabilities will likely place extra pressure on Ivorian forces to arrest the spread of militantism from the neighbouring Sahel region. Extremist groups have sought to expand into and destabilise coastal West African countries, including in the Ivory Coast’s more restless northern regions.
Puntland forces continue anti-IS advances in Cal Miskaad region of Somalia
The breakaway territory’s forces continued their advances in the highly mountainous region which serves as the stronghold of the Islamic State Somalia Province (ISS), taking on 23 February the village of Shebaab, and entering Dhasaan two days later. US and UAE airstrikes have continued, likely preventing ISS forces from reorganising. Pictures from the newly captured villages show how ISS forces had been constructing infrastructure, including water wells and bakeries, indicating the group’s efforts to establish parallel governance structures and win “hearts and minds”. Puntland advances are now likely to continue towards the next ISS stronghold of Wangable.
Explosions in Bukavu, South Kivu in Eastern Democratic Republic of the Congo (DRC)
At least 11 were killed and 60 injured in an explosion in Bukavu on 27 February. The blast happened during an AFC/M23 rally in Independence Square, where a large crowd was gathered. In the panic immediately following the blast, shooting reportedly started. President Felix Tshisekedi blamed ‘a foreign army illegally present on Congolese soil’, almost certainly alluding to AFC/M23 and Rwanda. AFC/M23 have rejected responsibility, instead accusing Kinshasa of being behind the attack, claiming the grenades used were the same type used by Burundian forces. Two people have been arrested. While the origin of the blast is unconfirmed, there is a realistic possibility that it was perpetrated by AFC/M23, who will likely use it as an example of government atrocities against the DRC’s population to be used as a pretext for advancing into Uvira, near the Burundian border. Before the blast, Corneille Nangaa Yubeluo, leader of the AFC alliance, vowed, “I promise you that in two days, we will be at Uvira to restore security.” Burundian military forces have deployed along the N5 Highway leading from Bukavu to Uvira in anticipation of the group’s advance.
Environment, Health and Miscellaneous
At least 50 deaths in the Democratic Republic of the Congo due to unidentified illness
At least 415 cases of a yet-unidentified illness have been recorded in the northwestern DRC since it was first recorded in three children on 21 January. According to medical reports, the illness’ symptoms include fever, vomiting, and internal bleeding, and the interval between their onset and death is around 48 hours. The symptoms resemble those of haemorrhagic fevers caused by viruses such as dengue, Ebola, yellow fever, and Marburg. However, tests have so far shown that the illness is not caused by these. Some of the samples tested did, however, return a positive result for malaria.
Widespread power cuts in South Africa
On 22 February, South Africa’s national energy operator Eskom implemented large scale power cuts, amounting to approximately 3,000 megawatts, following failures at the Majuba and Camden power stations. Saturday’s Stage 3 power cuts were subsequently raised to the highest level, Stage 6, as Eskom reported that 6,000 megawatts would be taken offline. It is the first time Stage 6 is reached since February 2024. Eskom’s progress over the past 12 months has been driven by significant repairs being carried out at the country’s coal-fired power plants, which supply most of South Africa’s electricity. However, the recent failures likely demonstrate ongoing issues, including obsolescent infrastructure and lack of funding. Power cuts in South Africa often lead to civil unrest and increased crime rates. While no large-scale protests have been recorded as of the time of writing, there is a realistic possibility of unrest being triggered if large-scale load shedding continues.
Asia–Pacific
Pakistan: Intel warns of plan to attack international cricket tournament
Authorities in Pakistan are on high alert after obtaining credible evidence that violent extremist organisations (VEOs) have plans to target the 2025 International Cricket Council (ICC) Champions Trophy. Pakistan’s intelligence bureau has issued a high alert, which has warned security forces about a possible plot to target foreigners at the ICC event, which will be held in Karachi, Lahore, and Rawalpindi. The alert specifically names the Tehrik-e Taliban Pakistan (TTP), the Islamic State Khorasan Province (ISKP), and Balochistan-based outfits such as the Balochistan Liberation Army (BLA). The threat reportedly includes the kidnapping of foreign visitors for ransom. In response, Pakistan’s security forces have increased protection for teams and players.
Solace Global Assessment:
Pakistan’s hosting of its first major international cricket tournament since the 2009 terror attack on the Sri Lankan national team almost certainly remains a highly coveted target for VEOs attempting to undermine the central government. Direct attacks on stadiums or other high-profile targets like international hotels or training grounds cannot be discounted, especially as VEOs have consistently demonstrated their ability to attack targets outside of their usual area of operations.
However, the latest intelligence alert may indicate that VEOs are not seeking to directly attack the tournament as a result of the government’s increased security posture. Alternatively, VEOs may be seeking to target softer targets, such as kidnapping foreign nationals in less secure and monitored parts of the host cities of Karachi, Lahore, and Rawalpindi. This could include the kidnapping of foreign nationals in less secure accommodations or entertainment venues like restaurants in less central parts of the cities with a decreased police presence and a reduction in CCTV coverage.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Anti-Hasina student group forms political party in Bangladesh
Leaders of the student group Students Against Discrimination (SAD), which was crucial in leading the protests that led to the ousting of Prime Minister Sheikh Hasina in August 2024, announced on 23 February that they would transition the group into a political party. The announcement follows clashes last week where SAD members were injured by students from the youth wings of other opposition parties, including the Islamist party Jamaat-e-Islami (JI). On 25 February, local media reported that the house of one of SAD’s secretaries in Kumarkhali was attacked and vandalised by a large crowd, likely consisting of JI members. The case continues to highlight how, with Hasina and the previously hegemonic Awami League (AL) removed from power, opposition groups continue to clash to fill the political vacuum. The creation of a SAD party is likely to destabilise the interim government led by Muhammad Yunus, as the new political entity is likely to call for elections earlier than the stated date of “early 2026” in order to capitalise on its momentum.
Crypto exchange hack labelled the largest ever theft attributed to North Korea
The FBI have stated that North Korean hackers are responsible for the theft of approximately USD 1.5 billion of cryptocurrency from the Dubai-based ByBit crypto exchange company. The heist has been described as the world’s largest ever theft. The operation was likely conducted by the Lazarus Group, a hacker group that is almost certainly run by the North Korean state. The Lazarus Group are thought to be responsible for the high-profile hacking of Sony Pictures Entertainment in 2014. As a heavily sanctioned rogue state, North Korea has invested considerable resources into illicit means of acquiring capital, largely to fund its military and nuclear program. The Lazarus Group has highly likely proven itself to be the most effective of these endeavours. Previously, targets have included banks such as the Bangladesh Bank in 2016. Cryptocurrency exchanges now, however, are likely the most desirable target, due to perceived vulnerabilities in the rapidly expanding sector and the lack of traceability in cryptocurrency.
Security, Armed Conflict and Terror
Explosion at seminary in Akora Khatak, Pakistan
On 28 February, an explosion caused by a suspected suicide bombing occurred at the Darul Uloom Haqqania seminary. The blast reportedly occurred in the front row during Friday prayers. At least four people were killed and 12 seriously injured. Hamid Ul Haq Haqqan, head of Jamiat Ulema-e-Islam-Sami with connections to the Taliban, was killed in the blast. Given that the blast occurred in the front row, it is highly likely that he was the target. No group has claimed responsibility for the attack. Police have cordoned off the surrounding area while they investigate the blast.
China conducts live-fire exercises in Gulf of Tonkin
China’s People’s Liberation Army Navy (PLAN) began live-fire military exercises in the Gulf of Tonkin on 26 February, following Vietnam’s announcement on 23 February of a new map defining its territorial waters and exclusive economic zones in the region. The Chinese drills focused on the Beibu Gulf area closer to China’s side and are almost certainly part of an aggressive policy to assert its territorial claims in the disputed waters. China will likely adopt this practice in other disputed waters. The drills have previously not been declared in advance and have resulted in flight diversions at short notice.
Taiwanese authorities detain vessel over suspected undersea cable sabotage
On 25 February, an undersea cable connecting Taiwan and Penghu, an island in the Taiwan Strait, was severed. Taiwanese authorities subsequently detained the crew of a Togolese-flagged cargo vessel manned by Chinese personnel which was suspected of having intentionally damaged the cable. The damage to the cable did not result in major disruptions as communications between Taiwan and Penghu were rerouted using alternative infrastructure. If proven to be intentional, the case would further highlight the growing threat of highly deniable underwater sabotage conducted by authoritarian states like China and Russia. China is likely severing Taiwanese underwater cables in order to incur costs on Taiwan, assert dominance, assess international reactions, and to ascertain Taiwanese response times, which could provide vital intelligence in the case of a future war.
Southern Thai insurgents attempt to undermine former prime minister’s visit
On 22 February, a bomb exploded in front of a convenience store in Bannang Sata, Yala Province, injuring over ten people, including seven police officers and four civilians. The bomb detonated while security forces were patrolling the area. Then, on 23 February, a car bomb detonated at Narathiwat airport in Narathiwat Province, another one of Thailand’s restless southern provinces. The airport explosion occurred just before the plane carrying former Thai Prime Minister Thaksin Shinawatra was set to arrive at the airport. Authorities have suggested that both bombs were planted by Islamist separatists and were designed to undermine Shinawatra’s first trip to the southern provinces in 20 years, while his daughter Paetongtarn, the current prime minister of Thailand, attempts to achieve long-lasting peace in the region.
Environment, Health and Miscellaneous
Dozens of people killed by heavy flooding in Afghanistan
Save the Children reported on 27 February that at least 29 people, including four children, had been killed by floods following heavy rain in the provinces of Kandahar, Farah, and Kunar. In the former two provinces, the flood also caused significant infrastructural damage, destroying dozens of houses and displacing hundreds. In Afghanistan, significant deforestation, obsolescent infrastructure, and the severe damages sustained in decades of war make flash floods particularly damaging. Taliban officials have avoided commenting on the floods, and it is highly likely that Kabul lacks the means to provide significant relief to the affected areas.
Strong earthquake in Kathmandu, Nepal
On 28 February, the Bhairab Kunda in the Sindhupalchok District of Kathmandu was hit by a magnitude 6.1 earthquake, according to Nepal’s National Earthquake Monitoring and Research Centre. The epicentre was close to the Himalayan Mountain range bordering Tibet. Other meteorological readings, including from the German Research Center for Geosciences and the U.S. Geological Survey place the earthquake at a magnitude 5.6 and 5.5, respectively. There have been no reports of damage or casualties. However, aftershocks are highly likely in the coming days and weeks.
Severe Tropical Cyclone Alfred due to make landfall in Australia
Severe Tropical Cyclone Alfred has intensified into a category 3 storm off the coast of Queensland, Australia, as it continues its southward trajectory towards land. The Australian Bureau of Meteorology reports that Cyclone Alfred is strengthening over the Coral Sea, but its path remains highly uncertain. The cyclone, which initially formed on 23 February, is currently located off the coast and may move closer to Queensland by 2 March. Authorities are monitoring the situation closely as the storm progresses.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence

Greece Shuts Down as Protests Mark Train Tragedy
Intelligence cut off: 11:00 GMT 28 February 2025
As of 28 February, large-scale protests and widespread service and transport disruptions are ongoing across Greece. The unrest falls on the second anniversary of the worst train crash in Greek history. On 28 February 2023, a freight train crashed head-on into a passenger train in the Tempe Valley area of Thessaly, killing 57 and injuring 85. Protests are scheduled to occur at more than 350 locations across Greece, as well as in more than 100 cities that have a large Greek diaspora.
In addition to a 24-hour general transport strike, multiple other strike actions are planned. Public services, healthcare facilities, schools, cultural institutions, restaurants, shops and other businesses will be shut down or run at limited capacity. Security measures have been heightened in Athens, including the deployment of over 6,000 police officers and the use of drones and helicopters to bolster surveillance.
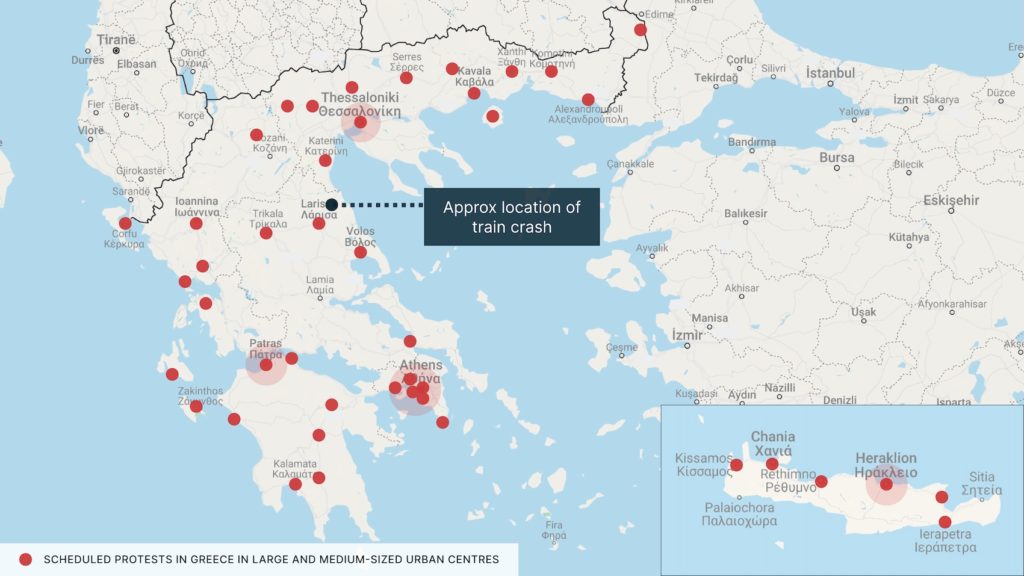
In the weeks and days before the protests, there have been significant updates concerning the crash. In January, leaked recordings from inside the passenger train showed that several passengers had survived the initial impact and had later died of asphyxia caused by chemical solvents illegally transported on the freight train. On 27 February, Greek authorities released a 180-page report that assessed that the crash had been caused by human error. According to the report, the passenger train was accidentally routed onto the same track as the incoming freight train.
INTELLIGENCE ANALYSIS
Government Under Fire as Greeks Demand Train Crash Justice
The crash has likely resulted in a severe and generalised loss of confidence in the government and other Greek political institutions, with many Greeks expressing the belief that the government has not done anything to achieve justice for the victims. Recent polling even indicates that over 80 per cent of Greeks feel that the Tempi train disaster was one of or the worst issues in Greece, with the vast majority also expressing that they were dissatisfied with the investigations into the incident and linking it to other issues, including socioeconomic grievances and corruption.
There is a high likelihood that today’s protests will result in significant levels of violence. Clashes between protesters and police were recorded in Thessaloniki on 27 February, and, as of the time of writing, there have been cases of improvised explosives being retrieved by authorities in the areas near the main rallying points. Violence at the protests is likely to take the form of vandalism, attacking local government and police buildings, as well as banks and other financial institutions. There is a remote possibility of protesters targeting diplomatic offices.
Greek police respond violently to severe unrest. Police are likely to deploy pepper spray, water cannons and tear gas, which may pose a threat to bystanders. While 28 February is likely to be the most severe day for unrest, it is likely that demonstrations will continue throughout the weekend, particularly in Athens and Thessaloniki.
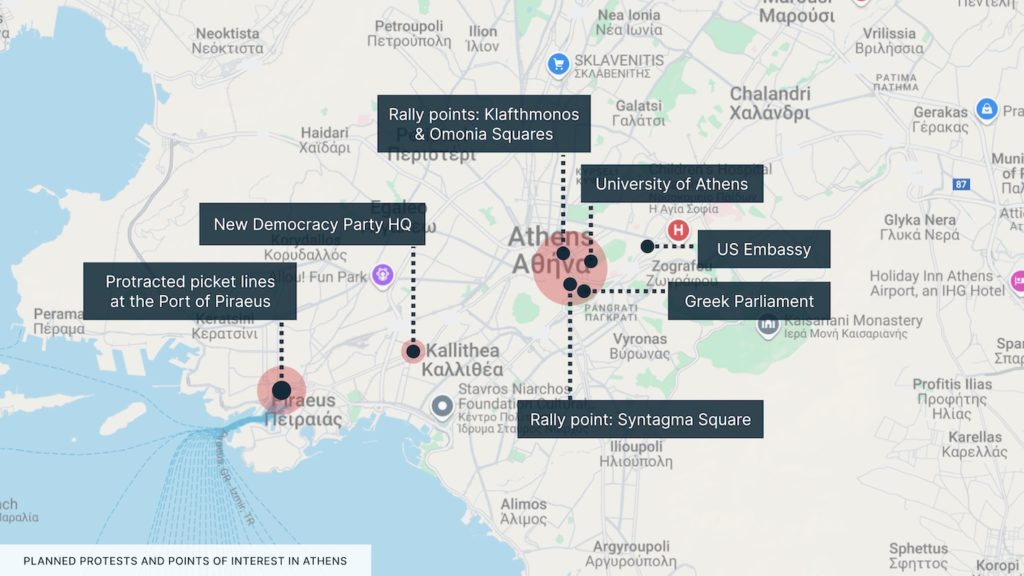
Travel Risk Advice: Safety Guidelines for Greece
- Avoid the area of Omonia, Parliament and Syntagma Square. Avoid the Piraeus area.
- Closely monitor local news reports and government alerts.
- Monitor the OASA website for live updates on transport in Athens.
- Plan for alternative routes and means of transport in Athens and other large cities. Allocate more time for all transport.
- If caught in a protest area, try to leave quickly if it is safe to do so.
- If you are in a crowd and unable to leave, take precautions to minimise the risk of crowd crush. These include staying upright, moving away from all hard barriers, going with and not against the crowd, and holding your arms at chest level in a boxer-like stance to relieve pressure.
- Increased security presence is almost certain to continue beyond 28 February. This will likely result in protracted transport disruptions.
- Ensure that you always carry personal identification documents or copies.
- Have emergency contact numbers saved on your phone. These should include the local authorities, medical facilities and any consular support. Ensure that mobile phones are charged in case of any losses in electricity.
- Monitor the Solace Secure platform and trusted local media for updates relevant to the conflict.
Subscribe to free weekly intelligence

Executive Summary
Americas (AMER)
The deployment of US airborne intelligence, reconnaissance and surveillance assets to Mexico is almost certainly indicative of the Trump administration’s strategic priority to counter the cartels.
The ELN’s imposition of an “armed strike” in Colombia’s Chocó Department will almost certainly disrupt the provision of essential services and increase pressure on the central government.
Europe, Middle East & Africa (EMEA)
The upcoming German elections will highly likely result in the Christian Democrats winning the most votes, but will likely be followed by a period of instability due to a fractured parliament.
The beginning of bilateral US-Russia talks that exclude Ukraine, and the public dispute between President Trump and President Zelensky, likely puts the Ukrainian president in a lose-lose situation.
The ceasefire in Lebanon is holding, however, there is a realistic possibility that Israel will challenge the terms of the ceasefire, assessing that other parties are in too weak a position to retaliate.
A suspected failed terror attack in Israel will almost certainly be used to justify expanded IDF operations in the West Bank.
There is a realistic possibility that increased IDF operations in the West Bank are shaping activity for increased settlement, a development that could undermine the ceasefire and fuel unrest.
The detention of two British nationals in Iran under charges of espionage is highly likely an example of hostage diplomacy, reaffirming the threat posed by arbitrary detention in adversarial states.
AFC/M23 rebels are highly likely to continue their advance in eastern Democratic Republic of the Congo, which could trigger further unrest in Kinshasa.
Asia-Pacific (APAC)
Pakistan’s hosting of its first international cricket tournament since 2009 is almost certainly a coveted target for multiple terrorist groups operating in the country.
In Bangladesh, both the arrests of Awami League supporters and the clashes between student groups are almost certainly driven by ongoing power struggles for political primacy post-Hasina.
There is a realistic possibility that student-led protests in Indonesia could evolve into a wider movement if joined by other sections of society, potentially leading to violent clashes with the police.
North, Central and South America
Mexico: US strategic ISR assets deployed against the cartels
Since early February, the US military and intelligence community has significantly increased its surveillance of Mexican cartel activity. This has primarily been achieved by deploying a range of tactical to strategic intelligence, surveillance and reconnaissance (ISR) airborne assets to monitor cartel activity.
The US Navy has deployed P-8 Poseidon maritime patrol and reconnaissance aircraft to identify vessels of interest, monitor surface activity and intercept communications. Assets from the US Coast Guard have supported US Navy missions.
The US Air Force (USAF) has deployed RC135 Rivet Joint, a dedicated signals intelligence (SIGINT) aircraft capable of intercepting, geolocating, and classifying electronic emissions. The USAF has also deployed U-2 high-altitude reconnaissance aircraft, primarily for wide-area imagery intelligence collection.
Neither the Pentagon nor the White House have confirmed the deployment of RC-135 reconnaissance aircraft. However, US Northern Command (NORTHCOM) has stated that 140 military intelligence personnel have been assigned to the border mission. Their role includes full-motion video analysis, counter-network analysis, and Spanish language translation in support of the US Border Patrol Office of Intelligence.
Reports also indicate that US military operations are being supported by the Central Intelligence Agency (CIA), which is reportedly flying unarmed MQ-9 Reaper uncrewed aerial vehicles (UAV) ISR missions directly over Mexican airspace.
Solace Global Assessment:
The use of strategic military assets like Rivet Joint against the cartels is an unprecedented shift which has likely been authorised following President Trump’s 20 January executive order to designate several of the cartels as foreign terrorist organisations (FTOs), which came into effect on 19 February.
The designation has likely permitted other forms of more covert intelligence collection, such as directed surveillance, which is hard to identify in the open-source domain. The use of strategic assets combined with the scale and frequency of US ISR missions over Mexico, the US-Mexico border and maritime approaches indicates that this activity is unlikely to be simply strategic messaging towards the cartels.
SIGINT platforms will be able to provide US intelligence with information relating to phone signals, radio transmissions, encrypted devices, satellite signals, radar emissions from vessels, and other electronic communications.
When layered with imagery collection and other forms of intelligence collection, such as human intelligence (HUMINT), this data will allow for a comprehensive understanding of cartel operations. When analysed, US intelligence will likely be able to uncover cartel patterns of life, identify key locations such as fentanyl labs, trace drug trafficking routes, map cartel networks and leadership structures, identify enablers, track financial operations, and gather other critical insights into cartel activity.
How this intelligence will be used remains unknown. The CIA has conducted ISR missions against the cartels in the past, but this has often been done with authorisation from the Mexican authorities. Moreover, it is unlikely that the US will be operating within Mexican airspace without approval from the Mexican government.
Trump has posited the idea of using US special forces to conduct targeted operations against the cartels, a policy that is unlikely to require congressional approval. However, the most likely scenario is that the US is fulfilling a sophisticated intelligence capability that Mexico currently lacks. By delivering surveillance, signals intelligence, and analytical support to Mexican authorities, the US is likely enhancing Mexico’s ability to more effectively target cartels and disrupt their operations as part of a partnered operation.
This has likely placed enormous pressure on Mexico to adapt its strategy towards the cartels or face a reaction from the Trump administration, such as tariffs.
However, such a shift could precipitate a change in the security environment in Mexico which may threaten US interests. The cartels may be forced to alter their tactics, which could involve more sophisticated counter-surveillance measures, more innovative ways to smuggle illicit goods into the US or an escalation in violence.
If the cartels perceive increased US involvement as an existential threat to their operations, they may respond with a range of retaliatory actions to deter further intervention. There is a realistic possibility that this could include increased cartel violence on the border, attacks on Mexican security services and assassinations of high-profile civilian targets such as politicians and journalists.
A more extreme response could involve cartels deliberately targeting US interests in Mexico or beyond. This might include attacks on American businesses, kidnappings of US citizens or deliberate attempts to flood the US with higher volumes of narcotics and potentially more lethal varieties.
Colombia: ELN declares armed strike in Chocó Department
On 17 February, members of the National Liberation Army (ELN) declared that a three-day “armed strike” would be enforced in the Chocó Department. The strike began on 18 February at midnight and is set to end on 21 February at midnight.
Under the terms of the strike, no public activities will be allowed to take place, public transportation will cease to operate, no one will be able to travel on public roads, and civilians will be forced to remain indoors for the entire period. The ELN has stated that the strike has been imposed in order to expose collusion between the state, military forces and mercenary groups operating in the region.
This is the ninth armed strike that the ELN have imposed but is considerably larger than the previous strikes.
Solace Global Assessment:
The ELN’s imposition of an armed strike likely serves several purposes. The ability to impose an armed strike largely unchallenged will almost certainly be perceived as a direct challenge to the government, likely weakening public confidence in state security forces.
Public confidence in the government will be further tested if the ELN can expose collusion between the state and other armed groups, such as the Gulf Clan. If the ELN succeeds in these efforts, it will likely increase pressure on the Petro administration to concede to more favourable terms in the ongoing peace negotiations.
If successful, it is highly likely that the ELN will impose similar armed strikes in other parts of Colombia, with the group having a major presence in departments such as Norte de Santander, Arauca, Cauca, and Nariño, where it has long-established control and influence. The armed strikes will likely disrupt the provision of essential services, including food, medicine and health care, especially if they increase in scale and duration. Furthermore, anyone contravening the ELN’s orders is likely to be apprehended or executed, including individuals who are typically afforded protection, such as healthcare professionals and humanitarian workers.
The government claims that the ELN is using the armed strike to limit traffic on the area’s roads and waterways. This strategy will enable the ELN to transit illicit goods such as cocaine and illegally mined materials out of the region, ultimately helping to fund future operations. In response, the Colombian government will likely increase military and police deployments in key areas and along major transport routes in an attempt to restore order, interdict smuggling, and prevent the ELN from expanding its influence. However, given the ELN’s entrenched position in the rural Chocó Department and its preference for asymmetric warfare, it is unlikely that government forces will be successful in dislodging the ELN from its area of operations.
AMER Summary and Forecast
Politics, Economics and Civil Unrest
Former Brazilian president charged over coup attempt
Brazilian prosecutors have charged former President Jair Bolsonaro over an alleged coup plot to poison his successor, current President Luiz Inacio Lula da Silva and to kill a Supreme Court judge. The prosecutor general stated that Bolsonaro and 33 others were complicit in the plot.
Bolsonaro has rejected the accusation, labelling the incumbent government as an authoritarian regime. The former president still commands significant support in Brazil and is attempting to rekindle his political career, despite being banned from holding public office until 2030.
Bolsonaro is unlikely to be arrested before his trial, but his future arrest or any major developments in the case are likely to provoke major unrest, with many of his supporters previously attempting to storm government buildings in the capital, Brasilia, after his defeat in the 2022 presidential election.
Argentine President Javier Milei receives backlash following crypto scandal
On 14 February, Milei posted a link to a website selling the cryptocurrency $Libra, leading to it quickly appreciating in value before suddenly dropping, losing up to USD 4 billion, after early investors sold their coins. The main opposition coalition, led by the Socialist Party, has accused Milei of fraud and has called for the start of impeachment proceedings.
Milei defended his actions stating that he did not advertise the coin, shared it from his personal account, and that investing in crypto is like gambling, so he is not responsible for investors’ losses. Milei’s seeming promotion of the little-known cryptocurrency follows similar actions by other politicians. On the eve of the inauguration, US then-President-elect Donald Trump launched a personal crypto coin and was shortly followed by First Lady Melania Trump.
Security, Armed Conflict and Terror
Six Guyanese soldiers injured in suspected gang attack across Venezuela’s border
On 18 February, armed men on the Venezuelan side of the Cuyuni River opened fire on soldiers on a resupply mission along the Guyana side, injuring six. While there was an exchange of fire, it is unclear whether any attackers, who were suspected gang members, were hit.
Guyana’s defence force has released a statement claiming that it ‘remains committed to protecting its borders and will take all necessary measures to address any threats to national security’. The incident is expected to raise tensions between the two countries and is the latest in a diplomatic feud over the shared border.
Venezuela has claimed that it has been cheated out of the mineral rich Essequibo region, which makes up two-thirds of Guyana, and Venezuelan President Nicolas Maduro has threatened to forcefully annex the region. Protests are likely in Guyana’s capital Georgetown amid public anger at Venezuela’s actions.
Colonel killed in likely cartel-mandated assassination in Ecuador
Colonel Porfirio Cedeño was shot and killed in the town of Guayaquil. According to local media, “multiple” gunmen ambushed the colonel’s vehicle as he was en route to a military ceremony in Manta. Cedeño was the leader of a special armed forces unit, the Special Operations Group, tasked with carrying out operations against drug traffickers in the country. The shooting, almost certainly mandated by local cartels, is the latest in a series of high-profile assassinations of figures within the Ecuadorean government.
Environment, Health and Miscellaneous
Brazilian forces launch large-scale operation against illegal logging
Brazilian forces seized at least 5,000 truckloads of timber during Operation Maravalha, a series of large-scale raids targeting illegal logging in the states of Para, Amazonas, and Rondonia. In addition to the seizures, authorities closed multiple sawmills.
The Lula government has made some considerable progress in curbing illegal logging in the Amazon rainforest, with levels of illegal deforestation falling since the 2022 elections. Deforestation, including logging and deliberate wildfires, is mostly carried out to turn portions of the rainforest into pastures, making them more profitable.
While the government raid, the largest in five years according to government sources, is a notable win for the Lula government, Brasilia likely continues to face significant difficulties in curbing illegal deforestation, which is both widespread and difficult to monitor.
Dengue cases continue to rise in Brazil
On 19 February, the government of São Paulo declared a state of emergency due to a significant rise in dengue cases, with 124,000 infections and 113 deaths reported since the beginning of the year. While the numbers are lower than last year, the state is nearing the epidemic threshold set by the WHO. Almost one-third of Brazil’s dengue cases have been identified in São Paulo, which has necessitated the allocation of more resources to the area. At least five people have also died in the state of Minas Gerais since the start of 2025, which has also recorded over 13,000 cases. One of the primary drivers of the case increases has been the low uptake in vaccinations, which has prompted the Ministry of Health to expand vaccine eligibility and allow doses close to expiration to be administered to a wider population.
Europe, Middle East & Africa
Germany: 23 February elections to likely lead to further instability
On 23 February, German citizens vote to elect the 630 members of the Bundestag. Currently, the Christian Democratic sister parties CDU/CSU are leading the polls with an estimated 29 per cent of overall public support. The incumbent Social Democrats (SPD) are far behind with 16 per cent support. The far-right Alternative for Germany (AfD) is second in the polls, at around 21 per cent.
The electoral campaign in Germany has been extremely tense and has attracted significant international attention. Most notably, the AfD, which was previously endorsed by presidential advisor and the world’s richest man Elon Musk, also recently received a less vocal endorsement by US Vice President JD Vance, who met AfD leader Alice Weidel in Munich. Large-scale anti-AfD rallies have occurred with some regularity in Berlin as well as other large urban centres.
The campaign has also been characterised by several cases of violence. Multiple terror attacks inspired by Islamist ideology have occurred in Germany in recent months, including in Munich, Solingen, and Mannheim. A further mass casualty attack, a vehicle ramming attack on a Christmas market in Magdeburg, was carried out by a Saudi national who espoused anti-Islam and anti-government extremist beliefs. These attacks have made migration one of the key issues of the campaign.
Solace Global Assessment:
The elections will highly likely see the Christian Democrats emerge as Germany’s main force in parliament. The AfD will highly likely be the second-largest party in the Bundestag, securing their best-ever result.
However, the leader of the CDU/CSU, Friedrich Merz, is likely to uphold the “firewall” against the AfD, despite having previously sought the far-right party’s support to pass legislation. Instead, the CDU/CSU will likely look to the left for support in forming a government. This would likely take the form of a Merkel-era “Grand Coalition” with the SPD.
This development would almost certainly result in short-term uncertainty and potentially long-term instability, with the coalition likely to have fewer seats than previous Grand Coalitions due to the forecasted success of the AfD.
This scenario, with the AfD more powerful than ever but still exiled from government, would almost certainly aggravate and embolden the far right, which may have material impacts on Germany’s risk environment. A stronger and more visible AfD is almost certainly going to result in more civil unrest. Alternatively, If Merz tries to pass further laws with the AfD’s support, more protests like those recently seen in Berlin and other cities are almost certain to occur. Alongside civil unrest, there is a realistic possibility of increased political violence, including attacks on politicians and activists, as well as acts of vandalism and sabotage.
It is notable that the AfD is now both openly endorsed by elements of the US administration and American-based pro-Trump channels, as well as Russian information operations. These efforts raise a credible risk of sabotage and activist violence against US businesses in Germany, driven by perceptions of US backing for the far-right. Last year’s sabotage of the Tesla “Gigafactory” near Berlin likely represents an early case of US politics driving activist sabotage in Germany, likely serving as inspiration for similar future actions.
Ukraine: US-Russia talks begin as Zelensky and Trump have public dispute
On 18 February, the US and Russia engaged in bilateral talks in Riyadh, Saudi Arabia. The US delegation was headed by the Secretary of State Marco Rubio, who was joined by national security advisor Mike Waltz and Middle East envoy Steve Witkoff. The Russian delegation was headed by Foreign Minister Sergei Lavrov, joined by Vladamir Putin’s advisor Yuri Ushakov.
The meeting, mediated by senior Saudi officials including the foreign minister, discussed conditions for a possible Trump-Putin summit and agreed to start negotiations to end the war in Ukraine. The talks notably excluded any Ukrainian representatives. President Zelensky had been scheduled to also visit Saudi Arabia but has postponed the visit to 10 March as Kyiv does not want to give legitimacy to the US-Russia talks.
In response to Kyiv’s concerns about being excluded from the talks, US President Donald Trump told reporters that Ukraine should have never started the war and Zelensky’s popularity ratings are as low as four per cent. Zelensky then publicly stated that Trump is “living in a disinformation space” created by Russia. Trump subsequently posted on social media that Zelensky, a “modestly successful comedian”, is a “Dictator without Elections” and “has done a terrible job”.
Solace Global Assessment:
Following the initial bilateral US-Russia talks, briefings to the press from both Russian and American delegation members give some early indications of possible core principles and red lines for peace negotiations. Waltz specified that a peace deal would require a permanent end to the war, security guarantees for Ukraine, and will have to include talks on territory. The latter condition almost certainly refers to the ceding of Ukrainian territory to Russia, namely Crimea, the Donbas and highly likely the occupied parts of Kherson and Zaporizhia Oblasts. This would be an immediately offered concession to Ukraine’s stated strategic objectives of full Russian withdrawal from internationally recognised Ukrainian territory.
Lavrov, on the other hand, stated that any deployment of NATO troops to Ukraine, “even under other flags”, would be unacceptable. This condition was almost certainly set in the context of proposals for NATO-member peacekeeping forces that could serve as a security guarantee for Ukraine, with UK Prime Minister Keir Starmer stating that he is “ready and willing” to deploy British troops as peacekeepers, with French President Macron making similar pledges in the past.
It is highly likely that peace negotiations, with the aforementioned core principles, already have built-in issues. While the US delegation expresses a desire for security guarantees sufficient to make peace permanent, the Kremlin has so far not expressed any indications of possible concessions that could enable this.
One possible scenario that Moscow would be more amenable to may be the deployment of forces from a non-NATO member such as China, although it is unlikely this would provide a sufficient guarantee against future Russian re-invasion.
Fundamentally, while Ukraine (and European partners) have been excluded from these talks thus far, Kyiv would need to accept any proposals for them to be effective. If determined, however, there is a realistic possibility that the Trump administration could force Kyiv to accept an imposed peace due to a threat of total defeat without any US support.
Zelensky is likely in a lose-lose situation, with any statements against Trump leading to a severe backlash, but silence enabling the imposition of an unfavourable peace.
Lebanon: Ceasefire holds, but delays and incidents demonstrate its fragility
The ceasefire agreement between Israel and Hezbollah, reached in November 2024, has largely held despite notable challenges and incidents. On 18 February, Israel Defense Forces (IDF) units withdrew from positions along the southern border, with Lebanese Armed Forces (LAF) units moving in to replace them. However, IDF troops remained stationed on five strategic hills, where they have established observation posts.
On 19 February, an Israeli drone strike in the town of Aita al-Shaab resulted in one fatality, marking the first casualty since the IDF’s withdrawal. Both the UN and the Lebanese government have condemned the continued IDF presence at these locations as a violation of the ceasefire terms. However, Tel Aviv maintains that the deployments are temporarily necessary to ensure border security.
Solace Global Assessment:
The continuation of the ceasefire agreement, despite Lebanon’s protests and Israeli strikes, is largely due to the positions of the three main parties involved: Israel, Hezbollah, and the Lebanese government.
Israel is likely pursuing two main objectives. Firstly, Israel is attempting to facilitate the return of 60,000 residents to northern Israel, the failure to do so has placed significant pressure on Tel Aviv. Secondly, Israel almost certainly wants to maintain a ground presence in Lebanon to monitor Hezbollah in case it attempts to reestablish a military presence south of the Litani River.
The threat of a sustained and likely destabilising IDF presence in Lebanon is also likely placing pressure on Beirut to adopt a more proactive role in containing the militant group.
Hezbollah, severely degraded after IDF operations and the loss of its Syrian supply lines likely has little choice but to accept Israel’s presence or risk a collapse of the ceasefire and renewed IDF operations. The Lebanese government has demonstrated an increased willingness to contain Hezbollah. However, with political and economic challenges, and a Lebanese Armed Forces (LAF) ill-equipped to directly challenge Hezbollah, the central government will likely have to accept the IDF’s continued presence within its borders.
Given Israel’s position of strength and the relative weakness of other parties involved, it is likely that it will continue to challenge the terms and push the boundaries of the ceasefire agreement. Israel will likely calculate that it can continue to strike at targets of opportunity within southern Lebanon, assessing that any major retaliation is unlikely.
Israel: Suspected terror attack on Tel Aviv bus network
On the night of 20 February, three bombs detonated on empty buses on the wider Tel Aviv bus network. Two explosions occurred in Bat Yam, a city south of Tel Aviv, while a third was reported in the nearby town of Holon. At least one additional explosive device was discovered on another bus in Holon. No injuries were sustained during the blasts.
Israeli police have stated that the bombs were detonated with a timer and were non-standard explosives. The police also commented that the bombs looked similar to those engineered in the West Bank. Israel’s Shin Bet internal security agency stated that it was taking over the investigation.
Solace Global Assessment:
The timing and placement of the explosive devices strongly suggest that they were intended to detonate during rush hour traffic, likely aiming to cause mass casualties. Furthermore, bus bombings have been a recurrent tactic used by Hamas and other Palestinian militant groups during past hostilities.
A group on Telegram, claiming to be a branch of the Qassam Brigades, the military wing of Hamas, based in the northern West Bank city of Tulkarem stated “We will never forget to avenge our martyrs as long as the occupation remains on our land.” This could suggest that the failed attack was Hamas’ revenge for Israeli operations in Palestine or potentially indicative of an internal split within Hamas, both of which are likely to undermine ceasefire negotiations.
However, the failure of three separate explosive devices to detonate at the correct time, coupled with the fact one device reportedly carried a message declaring “Revenge from Tulkarm”, is likely to generate suspicion and fuel speculation that the attack was a false flag operation. Many will likely believe that Israel engineered the incident to undermine ceasefire negotiations and justify continued Israeli military operations in both the West Bank and the Gaza Strip.
Regardless of the attack’s origins, when combined with Hamas’ recent public display of deceased Israeli children, it will almost certainly be used as justification for expanded Israeli operations in the West Bank and will likely be widely supported. Early indications suggest that Israel’s Defence Minister has already instructed the Israel Defense Forces (IDF) to intensify operations in the West Bank, especially in the Tulkarem refugee camp.
This escalation is likely to jeopardise ceasefire efforts and provoke further retaliatory attacks from the West Bank into Israel, increasing the risk of a broader cycle of violence. If sustained, there is a realistic possibility that it will draw Iran further into the conflict, with senior figures within Iran’s Islamic Revolutionary Guard Corps (IRGC) recently renewing threats towards Israel.
Palestine: IDF expands operations in the West Bank
The Israel Defence Forces (IDF) has increased the tempo of its operations in the West Bank, conducting multiple raids as part of its operation “Iron Wall” which started on 21 January. Raids intended to target militants and dismantle “terrorist infrastructure” have taken place in major Palestinian refugee camps, including in Jenin, Nur Shams, and Nablus and have also been conducted in smaller settlements near Jerusalem, Ramallah and Bethlehem. Some raids were reportedly conducted by Israeli settlers supported by the IDF.
The Palestinian Authority’s (PA’s) Deputy Prime Minister and Minister of Information Nabil Abu Rudeineh denounced the international community for remaining silent about Israel’s plans for “racist annexation and territorial expansion,” and called on the US to intervene to stop Israeli aggression, warning that failure to do so would only embolden Israel and lead to an uncontrollable escalation in violence.
Solace Global Assessment:
Israel has likely been emboldened by the initial steps of the new Trump administration. Trump has sanctioned the International Criminal Court for its issuing of an arrest warrant for Israeli Prime Minister Netanyahu; proposed the US control and redevelopment of Gaza; increased military support for Israel; and has threatened to unleash “hell” unless Hamas releases the remaining hostages. Israel is likely exploiting a more favourable White House and the current Gaza ceasefire to expand operations in the West Bank. Tel Aviv will also almost certainly exploit the recent failed terror attack and Hamas’ treatment of deceased Israeli hostages as a pretext for increased operations in the West Bank.
The primary objective of Operation Iron Wall is to dismantle militant networks that are likely receiving increasing support from Iran, which is attempting to establish another front against Israel, an objective that has almost certainly been prioritised since the collapse of the Assad regime in Syria. However, there is a realistic possibility that the increase in operations and consequent displacement of Palestinians, especially in areas near East Jerusalem, are shaping activity for an expansion of Israeli settlements. The previous Trump administration shifted US policy towards Israeli settlements, no longer viewing them as inconsistent with international law, a policy that is likely to provide Israel with diplomatic cover for continued expansion. For example, on 17 February, Israel issued a tender for the construction of nearly 1,000 additional settler homes in the Efrat settlement near Jerusalem.
The expansion of Israeli settlements in the West Bank is likely to jeopardise ceasefire agreements, undermine hostage exchanges and increase both radicalism and militancy throughout Palestine. Militant groups like Hamas are likely to exploit settlement growth as a justification to abandon talks with Israel, making negotiations and any long-term solution much harder to achieve. Increased settlement is also likely to severely undermine the PA’s credibility. The PA is already struggling with declining legitimacy and a weakened security apparatus, which it has often used to suppress Palestinian militancy, developments that will ultimately play into the hands of the militant groups. Despite a lull in fighting in Gaza, intensified Israeli operations and settlement expansion in the West Bank will likely fuel anti-Israeli sentiment and global protests. Perceived US backing for Israel is also likely to drive anti-US protests, especially in the Middle East, potentially increasing security risks for American citizens and interests abroad.
Iran: Detained British couple charged with espionage by authorities
On 18 February, two detained British nationals were charged with espionage by Iranian authorities. According to a judiciary spokesman, the couple had “entered Iran under the guise of tourists” and “collected information in several provinces of the country”. The British couple, Mr and Mrs Foreman, were on a worldwide motorbike trip.
The couple intended to stay in Iran for five days, having crossed into Iran from Armenia on 30 December, having earlier admitted that they were ignoring warnings from the UK’s Foreign, Commonwealth & Development Office (FCDO) not to travel to Iran. In January, the couple were arrested in the city of Kerman. The FCDO has stated that they are providing consular assistance to the couple and are in contact with Iranian authorities.
Solace Global Assessment:
The case is highly likely an example of ‘hostage diplomacy’, the practice of a state using arbitrary detention for geopolitical purposes and to gain transactional rewards. In recent years, numerous British nationals have been arrested in Iran. In a high-profile example, the British-Iranian dual national Nazanin Zaghari-Ratcliffe was arrested in 2016 by Iran’s Islamic Revolutionary Guard Corps (IRGC) at Imam Khomeini International Airport (IKA) in Tehran after visiting Iran on holiday. Zaghari-Ratcliffe was detained for six years, only being released once the British government agreed to settle an outstanding GBP 400 million debt that dated back to the 1970s.
Due to the likely increasing phenomenon of hostage diplomacy, there is almost certainly a severe risk of arbitrary detention posed to nationals travelling to countries hostile to the West, such as Iran, North Korea, Venezuela, and Russia. On 7 February, a US citizen was detained in Russia due to allegedly possessing cannabis-infused marmalade. With the talks being conducted between Russian and US officials in Saudi Arabia regarding Ukraine, the Russian government released the US citizen in what has been perceived as a gesture of goodwill. Such events are indicative of how travellers can be subjected to detention in adversarial states, with their continued imprisonment or release being then subject to globally significant geopolitical developments.
Democratic Republic of the Congo (DRC): AFC/M23 militants capture Bukavu
On 14 February, AFC/M23 entered the outskirts of Bukavu after capturing the airport in Kavumu, the second major airport to fall to the AFC/M23. On 16 February, AFC/M23 took full control of the provincial capital. Following minimal resistance in Bukavu, AFC/M23 continued south along the N2 Highway, capturing Kamanyola on 18 February. In North Kivu, AFC/M23 militants reportedly captured the city of Kitsumbiro on 20 February, approximately 27 kilometres from the centre of the Lubero region. Having attempted to push along the N2 Highway to Lubero but facing resistance, the group strategically diverted East to Kipese on 20 February.
Uganda’s military has confirmed that its forces entered Bunia in the Ituri region of North Kivu after consulting with FARDC leadership. Their purpose in the town is reportedly to “avert evolving genocide” amid alleged killings by armed groups along ethnic lines. This is likely linked to the ongoing intercommunal conflict between the Lendu farming community and Hema pastoralists. The DRC government has reportedly requested military support from Chad to assist against AFC/M23.
Solace Global Assessment:
Following the capture of Kamanyola in South Kivu, AFC/M23 now controls all three border crossing points between the DRC and Rwanda. It is highly likely that group will continue to push south towards the city of Uvira, enabling them control of the border crossing between the DRC and Burundi. Burundi, whose government is hostile to Rwanda and AFC/M23, will almost certainly see this as a security threat, risking an escalation of the conflict.
Following AFC/M23’s capture of Kitsombiro in North Kivu, they will highly likely push on to the mineral-rich Butembo, approximately 70 kilometres north. There is a realistic possibility that the capture of more major regional cities will result in further unrest in Kinshasa, which has, so far, remained relatively quiet since 29 January.
AFC/M23 increasingly threaten to encroach into regions where Ugandan forces are operating. Beni, 55 kilometres north of Butembo, has been the site of intense counterinsurgency efforts by Ugandan forces against the ADF Islamist rebel group in recent years. Uganda’s deepening involvement is almost certainly linked to the widening security gap along the Congolese border due to the diversion of FARDC resources to combat AFC/M23 militants.
Because of the importance of its military presence in Eastern DRC, Kampala would likely be reluctant to antagonise Kinshasa. An AFC/M23 advance on Beni would highly likely test Uganda’s tentative backing of the rebel group, which has so far been fragmented with senior military figures voicing support while government figures have been muted. There is a realistic possibility that if AFC/M23 do not directly threaten Ugandan troops or their ongoing counterinsurgency against the ADF, Uganda will assume a mediating role.
Fears of M23’s advancement have led to repeated reports of approaches towards Kinshasa. On 17 February, rumours claimed that M23 rebels had established a presence in the Kindu region and that the FARDC abandoned the airport. On 19 February, rumours proliferated that AFC/M23 members had been arrested in Kinshasa, something that was denied by FARDC. On the same day, a FARDC commander released a statement denying rumours that AFC/M23 rebels have a presence in Kisangani or the Tshopo province, significantly west of their current area of operations. Given the prevalence of inaccurate claims of AFC/M23 presence west of Kivu, the disinformation is likely deliberate but could influence public opinion, placing pressure on the government or triggering unrest.
EMEA Summary and Forecast
Politics, Economics and Civil Unrest
Lebanese government scraps recognition of Hezbollah from yearly ministerial statement
The document, the first to be issued by the government of Prime Minister Nawaf Salam, usually formally recognises the role of “armed resistance” to Israel as a legitimate part of the Lebanese political framework. Its omission is likely an important symbolic show of the government’s willingness to take advantage of Hezbollah’s post-conflict (and post-Assad) weakness to diminish the Shia militia’s political and military clout.
Beirut continues to face significant pressures domestically and from abroad; it is not only looking to improve ties with the Gulf states and the new administration of Syria but also aims to secure a new agreement with the International Monetary Fund (IMF). Hezbollah nevertheless remains a powerful force and is unlikely that Beirut will tackle it head-on. Instead, there is a realistic possibility that the government is pivoting towards a long-term strategy, meant to “starve” Hezbollah in both material and political terms.
The funeral of Hezbollah leader Hassan Nasrallah, killed by Israeli strikes in September 2024, is set to be held on 23 February, and will likely be used by the group as a show of force and political legitimacy.
Ethiopia and Somalia hold first round of technical talks in Turkey
On 18 February, Ethiopian and Somalian diplomats held the first round of talks aimed at resolving a dispute over Ethiopia’s access to Somaliland’s port. Somaliland agreed to lease access to its port to the landlocked Ethiopia after Addis Ababa agreed to become the first country to formally recognise its independence on 1 January 2024. Mogadishu, viewing the breakaway Somaliland as illegitimate, has viewed Addis Ababa’s deal with the regional government as infringing on Somalia’s sovereignty and integrity, threatening a regional conflict. The talks aim to reach a potential agreement upholding Somalia’s territorial integrity while granting Ethiopia access to its port. The second round of talks is set to take place in March.
Security, Armed Conflict and Terror
Four charged in Sweden over Islamic State links
The four individuals had been arrested in Tyresö last March, during a raid at a local Islamic cultural association. According to prosecutors, the four, two of whom are brothers, were radicalised during visits to Somalia, where the Islamic State (IS) has a growing branch (the Islamic State Somalia Province, or ISS). Moreover, prosecutors note how the cultural association had become a vehicle of radicalisation, with local preachers espousing pro-IS rhetoric. The suspects’ sentences reflect a 2023 law on terrorism, which more heavily sanctions individuals convicted of participating with a terrorist organisation. The case further highlights the threat posed by transnational IS ideology and how smaller IS branches are leveraging connections to foreign diasporas to recruit and plot external operations.
Attempted “Incel” lone wolf attack in Annecy, France
On 16 February, a 17-year-old tried to carry out a knife attack in the central square of the French town of the Haute-Savoie department. The attacker, who was shot and wounded by responding police before he could injure anyone, reportedly tried to livestream his attack on TikTok and stated that he intended to target women. The attack is almost certainly tied to “Incel” (or “involuntary celibate”) ideology, a set of beliefs characterised by extreme sexism and misogyny, which has in the past driven multiple lone wolf attacks. In France, another possible Incel attack was thwarted in May in Bordeaux, where an individual was arrested for planning an attack during the relay of the Olympic flame.
Deadly shooting at Brussels Metro highlights growing organised crime threat
On 15 February, a 19-year-old was shot and killed in a shooting at Clemenceau metro station in the Anderlecht district of Brussels. The attack is the latest in a series of violent incidents linked to drug-related territorial conflicts, which have escalated in recent weeks and resulted in two deaths. The brazen nature of these attacks likely indicates that organised crime groups feel emboldened, with the heavily trafficked metro system being exploited for the attacks and as an escape route. Belgian officials have called for stricter measures, with an emergency meeting scheduled with federal police.
IS-inspired knife attack in Villach, Austria, kills one
The attack occurred on 15 February in the main town square of Villach. The attacker was a 23-year-old Syrian national, who targeted random pedestrians, injuring five and killing a 14-year-old. According to security sources, the attacker became self-radicalised online within only three months, espousing IS ideology. IS channels have claimed responsibility for the attack, despite no known direct communication between the attacker and the group.
The case likely further proves the point made by MI5 head Ken McCallum, that lone wolf attackers are becoming radicalised increasingly quickly, making it harder for authorities to prevent attacks. There is a realistic possibility of further copycat attacks following the stabbing, as well as “retaliatory” violence against Muslim communities in Austria. Indeed, an early example of a copycat attack was likely thwarted by Austrian authorities on 19 February, as they arrested a 14-year-old who was planning to carry out a knife attack at the Vienna train station on behalf of IS.
Another large-scale Moroccan raid on IS cells highlights growing threat from the Sahel
On 19 February, reports emerged of multiple raids by Moroccan special forces, in at least eight cities, aimed at dismantling IS-affiliated networks. Authorities secured explosive materials, bladed weapons, and firearms. Local media also claimed that security forces found improvised explosive devices (IEDs) planted at sites just outside Rabat. The raids, which follow multiple counterterrorism operations in recent weeks, have been linked to the Islamic State Sahel Province (ISSP), which is increasingly attempting to expand its areas of influence. Moroccan authorities have expressed growing concerns over the ISSP’s attempts to establish operational cells within the country, particularly as instability in the wider Sahel region provides a fertile ground for jihadist recruitment and cross-border operations. Moreover, the sophistication of the recent plots suggests coordinated planning and guidance, rather than isolated groups.
Wagner/Africa Corps forces massacre Tuareg civilians in Mali
On 17 February, reports from pro-Azawad channels indicated that a convoy of Russian mercenary and Malian government forces, departing from Gao towards the Algerian border, massacred at least 20 civilians in the Tilemsi region. According to reports, the convoy opened fire on two civilian vehicles, killing the occupants. The case further highlights the contradictory and brutal, and so far, ineffective, counterinsurgency tactics used by the Wagner-supported Malian forces in the predominantly Tuareg northern regions of the country. It is highly likely that the case will further drive local opposition to the junta government.
Sahelian militants attack army post in northern Benin
A militant attack on an army post in northern Benin on 17 February killed six soldiers and 17 militants. This follows a deadly attack in January that claimed the lives of dozens of soldiers in the northern Alibori department, a region bordering Niger and Burkina Faso, which are struggling to contain Islamist insurgencies. The attack likely underscores the growing threat of armed extremist groups expanding from the Sahel into coastal West Africa, with Benin and neighbouring Togo increasingly targeted. Violent extremist organisations like the al-Qaeda-affiliated Jama’at Nusrat al-Islam wal-Muslimin (JNIM) and are likely attempting to destabilise the northern region of these countries, fuel an insurgency, expand recruitment, and force national governments to divert resources internally rather than conduct operations in the Sahel.
Rapid Support Forces (RSF) escalate attacks after Sudanese Armed Forces (SAF) advances
The SAF is currently dislodging the RSF from its positions in the capital Khartoum, forcing the paramilitary group to retreat west towards Darfur where it controls much of the region. However, the SAF is targeting the route out of the capital with drones and fighter jets, which is resulting in high rates of collateral damage.
In response to the SAF’s progress, the RSF has increased its attacks on the civilian population. The RSF reportedly killed 200 unarmed civilians in a cluster of villages in El Geteina in the White Nile State.
Attacks have also intensified in Darfur, with the RSF attacking the Zamzam camp, Sudan’s largest refugee camp, apparently turning it into a “killing field”. Attacks on civilians have likely become a deliberate RSF tactic and are expected to escalate as the group retreats west to Darfur. This strategy appears aimed at undermining the Sudanese government by instilling fear, destabilising communities, and disrupting governance structures in regions where the RSF maintains influence.
Environment, Health and Miscellaneous
Turkey conducts nationwide operations against Kurdistan Workers’ Party (PKK)
Turkish police have detained almost 300 individuals accused of having ties to the Kurdistan Workers’ Party (PKK), a group designated by Turkey and many of its allies as a terrorist organisation. The arrests have included journalists, politicians, academics, and members of other pro-Kurdish groups. The arrests, which occurred over five days in 51 provinces, coincide with a wider effort to curb Kurdish influence. This has involved the removal of pro-Kurdish mayors and major military action against allegedly related Kurdish groups in Iraq and Syria.
The arrests have received criticism from human rights groups, journalists, and Kurdish groups, who characterise them as authoritarian and likely to undermine peace talks. There is a realistic possibility that the arrests will provoke protests in major Kurdish settlements and could incite attacks on Turkish security services.
Magnitude 6.0 earthquake in Ethiopia causes light shaking in Addis Ababa
Late on 14 February, a strong magnitude 6.0 earthquake at a shallow depth of 10 kilometres struck 6 kilometres northeast of Metahāra. Approximately 120 kilometres east of Addis Ababa, the earthquake caused light shaking in the capital. Despite the earthquake’s strength and shallow depth, however, the tremblor highly likely only caused minimal impact due to limited population exposure near the epicentre.
Since late September 2024, Ethiopia has experienced a series of earthquakes that have raised concerns about volcanic eruptions being triggered. In early January, authorities announced the evacuation of 80,000 people in the Afar, Oromia, and Amhara regions due to the increased risk. Additionally, a task force was set up to assess the risk of seismic activity to Addis Ababa and bolster disaster preparedness.
While Addis Ababa has not historically suffered from significant earthquake damage, the ongoing earthquake “swarm” likely increases the risk of such an event.
Over 40 killed in mine collapse in western Mali
On 15 February, over 40 people, most of whom were women, were killed after an artisanal gold mine collapsed near the town of Kenieba in western Mali. The individuals had reportedly climbed down into open-pit areas left by industrial miners to look for scraps of gold when the earth collapsed around them. This is Mali’s second major mining accident in three weeks, following a flooded tunnel collapse in late January that killed at least 10 miners.
Unregulated artisanal mining of abandoned mines has increased as a result of foreign mining companies leaving Mali due to security concerns, political instability, and the junta targeting foreign companies in revenue disputes. Accidents are likely to increase as international gold prices continue to increase while domestic economic conditions deteriorate, further driving the demand for gold extraction in dangerous and unregulated mines.
Major flooding across Botswana
Botswana is experiencing severe flooding across multiple regions, including the capital, Gaborone, and the Ghanzi District. The flooding has caused widespread disruptions, leading to the closure of all public schools until 24 February. President Duma Boko confirmed that heavy flooding continues in Gaborone and surrounding areas, with at least one reported death. In the Ghanzi District, local media report that hundreds of residents have been displaced. Additionally, the airport in Ghanzi has been closed due to the extreme weather conditions.
Widespread flooding in South Africa’s KwaZulu-Natal
Heavy rainfall has resulted in major flooding and landslides in several parts of South Africa’s KwaZulu-Natal province. As of 21 February, at least three fatalities have been confirmed due to the adverse weather conditions. Flooding and landslides have disrupted businesses, forced the closure of schools and caused major traffic disruptions, particularly along the M4 highway in Durban. Further rainfall is predicted, with the South African Weather Service (SAWS) issuing two weather warnings for KwaZulu-Natal, predicting rainfall between 40mm and 100mm.
Asia–Pacific
Pakistan: First major cricket competition since 2009 terror attack
Pakistan will host the ICC Champions Trophy 2025 from 19 February to 9 March, with the tournament taking place across four venues. The National Stadium in Karachi, the Gaddafi Stadium in Lahore and the Rawalpindi Cricket Stadium in Rawalpindi will host games played within Pakistan. Any matches involving India will be played at the Dubai International Cricket Stadium, with India refusing to play in Pakistan due to security concerns.
This will be the first major international cricket tournament held in Pakistan since the 2009 terror attack on the Sri Lanka national cricket team in Lahore, Pakistan. During the attack, 12 gunmen armed with AK-47s, RPGs, and hand grenades attacked the team while they were en route to the stadium. Six members of the Sri Lankan team were injured, and six Pakistani policemen and two civilians lost their lives. The attack was believed to be conducted by the violent Islamist extremist group, Lashkar-e-Jhangvi (LeJ), which has links to al-Qaeda and other militant groups like Tehrik-i-Taliban Pakistan (TTP).
Solace Global Assessment:
Hosting a successful international cricket tournament in Pakistan would be a huge victory for the government for several reasons. It would not only signal a return to normalcy after years of security concerns but would also bolster Pakistan’s global image, economy, and internal stability. This will almost certainly make it a coveted target for terrorist groups seeking to undermine the government and gain international publicity, especially if they can successfully attack international cricket teams or sites frequented by foreign nationals.
Pakistan is currently contending with border skirmishes with the Afghan Taliban, sectarian violence in Khyber Pakhtunkhwa, and a resurgence in militancy in Khyber Pakhtunkhwa and the restive Balochistan region. The authorities have stressed that the violence is nearly entirely limited to the remote border regions, far away from the stadiums. However, militant groups have demonstrated their ability to strike way beyond their primary areas of operations. As recently as October 2024, the Baloch Liberation Army (BLA) killed two Chinese nationals and one Pakistani in an attack near Jinnah International Airport in Karachi, demonstrating the BLA’s ability to attack areas that typically have a heightened security presence.
While security has been increased to protect the tournament, with so many groups likely seeking to conduct an attack, combined with the overstretching of Pakistan’s security services, the hosting of a major international event will invariably be a significant challenge. Moreover, if internal security is diverted to protect the tournament, this may present an opportunity for militant groups to escalate attacks in the border regions or other areas with less security oversight.
Bangladesh: Government cracks down on Awami League, mob violence continues
Operation Devil Hunt, a series of raids by police and security forces across the country, resulted in 532 reported arrests in only 24 hours. Most of the arrested were members or supporters of the Awami League (AL). The operation was reportedly triggered by clashes in Gazipur on 7 February, the city being considered a stronghold of the party of ousted Prime Minister Sheikh Hasina. Hasina has recently attacked the interim government of Muhammad Yunus from her exile in India, accusing it of releasing “terrorists” and refusing to punish perpetrators of the violence that accompanied the July-August 2024 protests.
On 19 February, more than 150 students were injured in clashes in Khulna. The violence erupted while student supporters of the Bangladesh National Party (BNP) were carrying out recruitment efforts and were confronted by supporters of the Students Against Discrimination group, one of the key formations that led the anti-Hasina protests in August 2024.
Solace Global Assessment:
Political forces and vigilante groups supporting the new government have continued to carry out attacks on AL members or perceived supporters, as well as on local religious minorities. The AL sought to stage large-scale protests in early February, the first since losing power, but these plans have likely been crushed via a joint government and mob intervention. The latest arrests are likely part of the interim government’s efforts to displace AL from local institutions and positions of influence.
The clashes in Khulna likely showcase the tense, violent, and unstable state of the Bangladeshi political system at the present moment. BNP channels have blamed the clashes on members of the Islamist Jamaat-e-Islami (JI), while other student groups retaliated by staging anti-BNP demonstrations in Dhaka. Parties that were previously members of the opposition, like BNP or JI, likely continue to compete to fill the vacuum left by the overthrow of AL, including the control of local police, academic institutions, and bureaucracy. With the Yunus government unable (and likely unwilling) to intervene due to its dependence on the opposition’s political support, this competition is highly likely to continue taking the form of mob violence and targeting of political opponents. The arming of student groups – the groups that clashed in Khulna were armed with machetes and other bladed weapons – is likely to make universities particularly at risk for severe violence.
Indonesia: Widespread protests in response to government cuts
Student-led protests have erupted in multiple cities across Indonesia in response to President Prabowo Subianto’s budget cuts and policies. The protests, which have been given the moniker “Dark Indonesia”, have been organised over fears that the budget cuts will weaken social support systems in favour of supporting the president’s policies such as a new school lunch programme. Protests were organised on 17 and 18 February by the All-Indonesian Students’ Union (BEM SI) and were observed in Jakarta, Medan, Yogyakarta, Denpasar, and several other cities across multiple Indonesian islands. The Civil Society Coalition has called for civilians to demonstrate on 21 February following Friday prayers.
Solace Global Assessment:
These are the first major protests to occur under President Subianto and have so far remained relatively peaceful, with only a handful of arrests and injuries reported. However, the attendance and geographical spread of the protests likely indicate a wider dissatisfaction with the incumbent government’s austerity-laden economic policies. The movement has also called for the removal of the military’s role in civil posts, with many Indonesians likely fearing that the president’s former role as Minister of Defence and military career has disproportionately benefitted the military over ordinary Indonesians.
Students have promised to continue to protest the budget cuts but the real litmus test for the government will be on 21 February. If large sections of society join the demonstrations, it could indicate broader public discontent beyond the student movement. Given President Subianto’s strong approval ratings, the government is unlikely to make significant concessions unless protests escalate in size or intensity. However, if the protests continue to gain momentum, there is a high likelihood of clashes with the police. Under such circumstances, the Indonesian police will likely use tear gas, rubber bullets, and water cannons to disperse protests, especially if violent or causing major disruptions.
APAC Summary and Forecast
Politics, Economics and Civil Unrest
Afghanistan pulls out of the International Criminal Court (ICC)
On 20 February, Taliban channels issued a declaration that the 2003 decision by their predecessor governments to join the ICC was illegal and that Afghanistan would subsequently be outside of the ICC’s jurisdiction. Kabul notably quoted the fact that ‘many of the world’s major powers are not signatories’, likely referencing the US and Russia, which, although being signatories to the Rome Statute, have not ratified it. In January, the ICC stated it was seeking arrest warrants for senior Taliban leaders, including Supreme Leader Hibatullah Akhundzada over persecution of ‘Afghan girls and women’, citing the extremely strict rulings and bans on social participation that the Taliban government has issued. The move is likely to further damage Afghanistan’s government’s chances of re-establishing ties with Western powers and improve its international legitimacy.
Philippine Vice President Sara Duterte asks for impeachment to be thrown out
On 18 February, Duterte’s lawyers asked the Supreme Court to revoke her impeachment ruling and block a Senate trial. Duterte was impeached on 5 February after being accused of plotting to assassinate the president, engaging in corruption, and misusing confidential funds. Lawyers argued that the impeachment was sent to the Senate too quickly to be studied and ‘was procedurally defective, constitutionally infirm, and jurisdictionally void.’ Duterte will highly likely be convicted in the Senate trial, which would bar her from holding public office.
Beijing pens new agreement with the Cook Islands
The Pacific nation, the Cook Islands has released details regarding its new strategic partnership deal with China. Under the terms of the deal, Beijing will contribute more funding towards infrastructure and educational projects and will cooperate with seabed mineral mining. The deal has provoked a diplomatic dispute with New Zealand, Cook Island’s primary benefactor and military ally. Unlike other deals Beijing has signed in the region, the agreement does not include security cooperation. However, the growing Chinese influence in the South Pacific is raising mounting concerns, as it points to an expansion of China’s economic presence and potential future military footprint in the region, which could destabilise the area and lead to increased militarisation.
Security, Armed Conflict and Terror
Attack on aid convoy in Khyber Pakhtunkhwa, Pakistan
On 17 February, at least 20 gunmen attacked a convoy of aid trucks carrying food supplies to Parachinar in the Kurram district, killing a truck driver and security escort and injuring seven. The attackers also ambushed a paramilitary reinforcement unit, setting three border force vehicles on fire and killing four soldiers. In total, six people were killed and 15 people were injured. The Pakistani military deployed helicopter gunships to target mountain hideouts in the region after the attack. The military reported the militants to be from the Tehrik-e-Taliban Pakistan (TTP). Evacuation orders have been issued for residents in four villages of Lower Kurram due to the recent violence. Approximately 250 people have been killed in the region since July 2024, according to local officials. Numerous truces have failed to quell the violence.
Tajik court sentences 30 individuals in poisoning plot linked to Islamic State
A court in Tajikistan has sentenced over 30 individuals to prison for attempting to poison attendees of a Nowruz festival in 2023. Authorities have linked the plot to Islamic State Khorasan Province (ISKP), the primarily Afghanistan-based offshoot of the Islamic State. In 2024, there were three ISKP-linked attacks in Tajikistan and the security services thwarted at least two other attacks. These trends likely allude to an expansion of ISKP’s operations, with the group increasing its influence in Central Asia and Russia. ISKP is likely attempting to position itself as more of a transregional organisation, a development that will enable it to spread its propaganda, increase recruitment, and conduct attacks beyond its traditional area of operations.
Environment, Health and Miscellaneous
Guillain-Barre Syndrome (GBS) outbreak in Maharashtra, India
The GBS outbreak in Maharashtra, India, has resulted in 11 deaths, the first one on 26 January. The rare neurological disorder causes the body’s immune system to attack the peripheral nervous system, causing muscle weakness, paralysis, or death. The state has confirmed four cases and is investigating seven suspected cases. The outbreak has spread to Mumbai, with the first death reported there involving a 53-year-old patient. Overall, the region has detected 197 cases, with Pune being significantly affected. In response, authorities have shut down 30 private water supply plants in Pune and advised the public to consume clean and boiled water and avoid stale or partially cooked food. Investigations into the cause of the outbreak are ongoing, with water contamination being a potential factor.
Cyclone Zelia causes flooding in Western Australia
Cyclone Zelia has caused severe flooding in remote areas of Pilbara, Western Australia, particularly affecting cattle farms. The cyclone, which made landfall near Port Hedland on 14 February, initially brought destructive winds and heavy rains, leading to emergency warnings and evacuations in the region. Ports in Dampier and Varanaus Island have since reopened after the cyclone passed through Pilbara. Authorities have been actively managing the situation, with evacuations conducted in areas like Warralong. The De Grey River catchment has experienced rising water levels, prompting warnings of potential isolation for residents.
Copyright © 2025 Solace Global Risk Limited. All rights reserved. No part of this document or content may be reproduced, copied, translated, sold, or distributed, in whole or in part without the consent of Solace Global Risk Limited.
Subscribe to free weekly intelligence